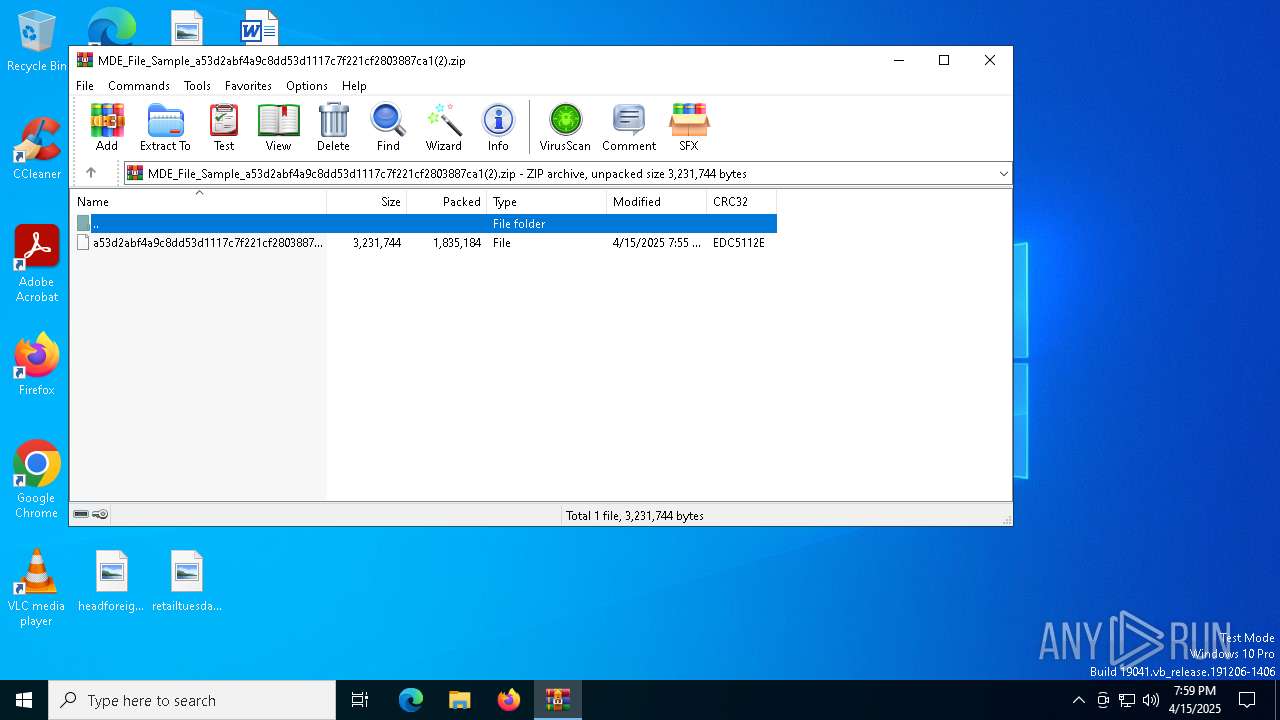
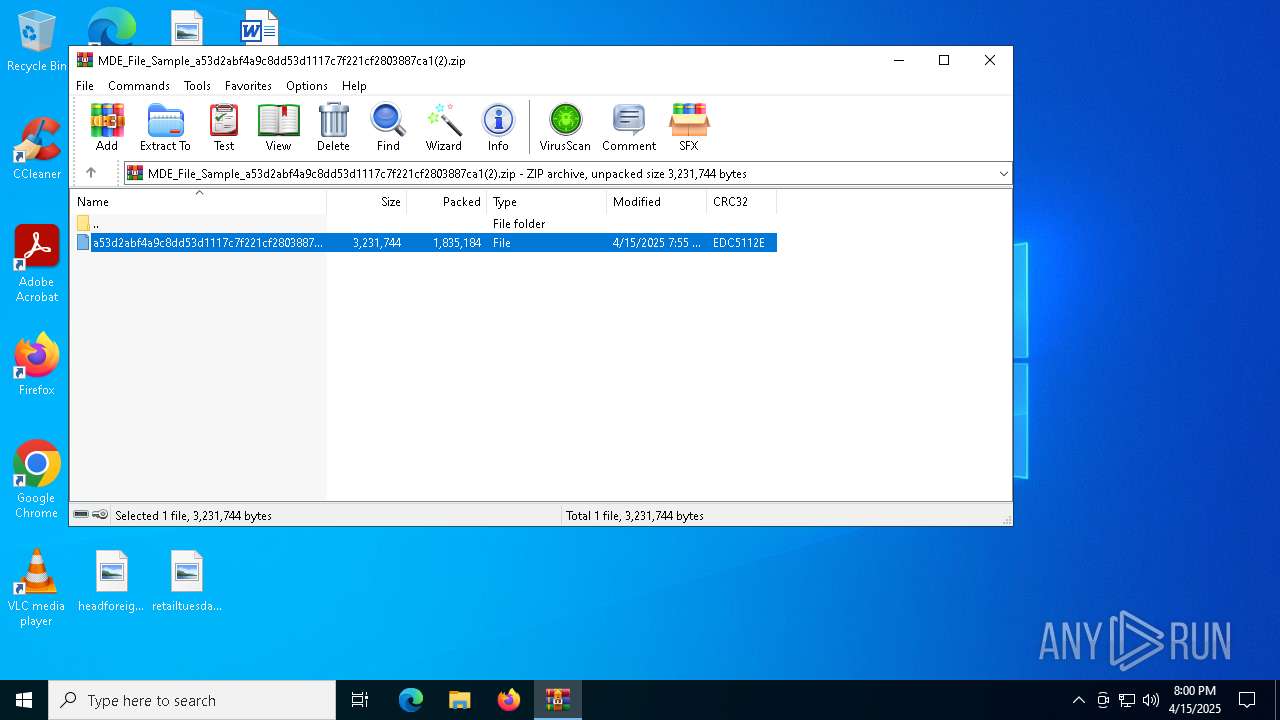
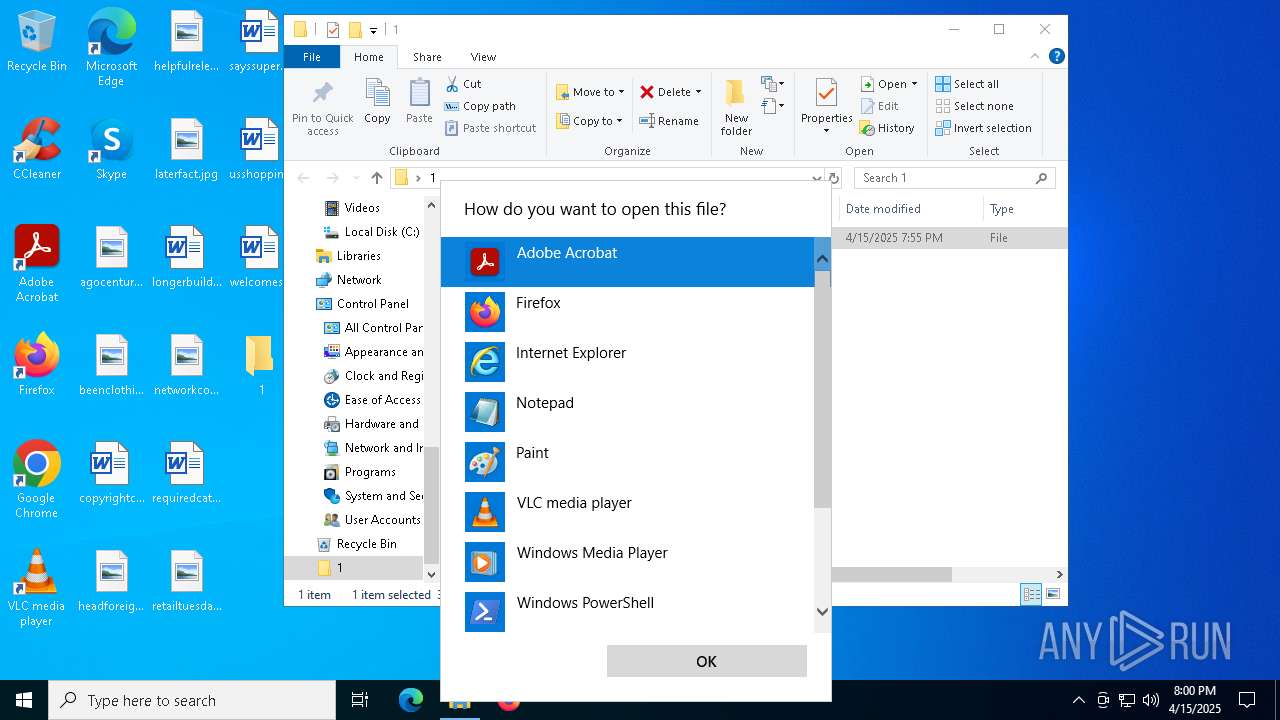
| File name: | MDE_File_Sample_a53d2abf4a9c8dd53d1117c7f221cf2803887ca1(2).zip |
| Full analysis: | https://app.any.run/tasks/700164ce-40e1-4e9d-8c4b-e2ef02f12ae1 |
| Verdict: | Malicious activity |
| Analysis date: | April 15, 2025, 19:59:27 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract, compression method=deflate |
| MD5: | 33D176CA7C250FEC0F3D9121DD426B81 |
| SHA1: | 98B553F50786531010153F7A15066D4C6EF6E267 |
| SHA256: | 91A2C401855DE6380C05917DF5F3491B75682B3C318A38A807F380CAEB3FC5EF |
| SSDEEP: | 98304:xKL1dmnXjStR23tjYWtSy9NDiAeUxwarcJGIl/QfUTWAS0esayOP44nYfeDMYcr9:tm |
MALICIOUS
No malicious indicators.SUSPICIOUS
Process drops legitimate windows executable
- WinRAR.exe (PID: 920)
- msiexec.exe (PID: 5384)
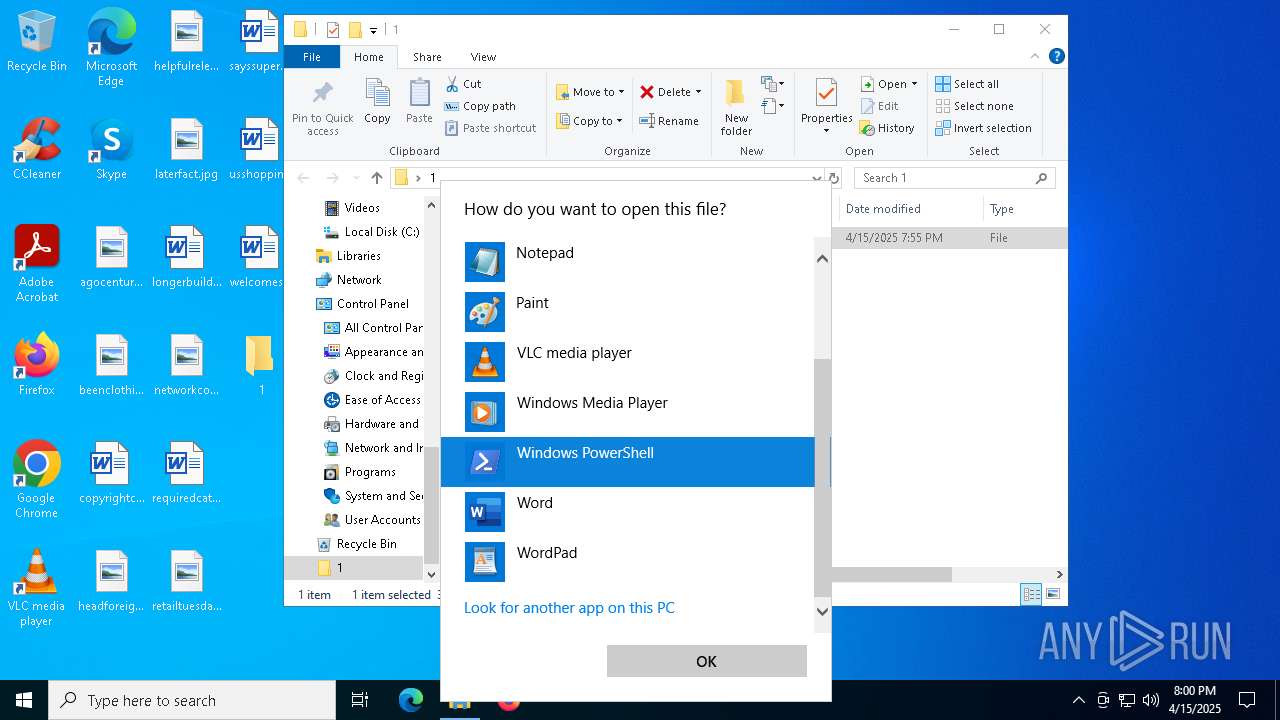
Starts POWERSHELL.EXE for commands execution
- OpenWith.exe (PID: 3760)
Executes as Windows Service
- VSSVC.exe (PID: 6248)
Reads the Windows owner or organization settings
- msiexec.exe (PID: 5384)
Reads security settings of Internet Explorer
- msiexec.exe (PID: 1128)
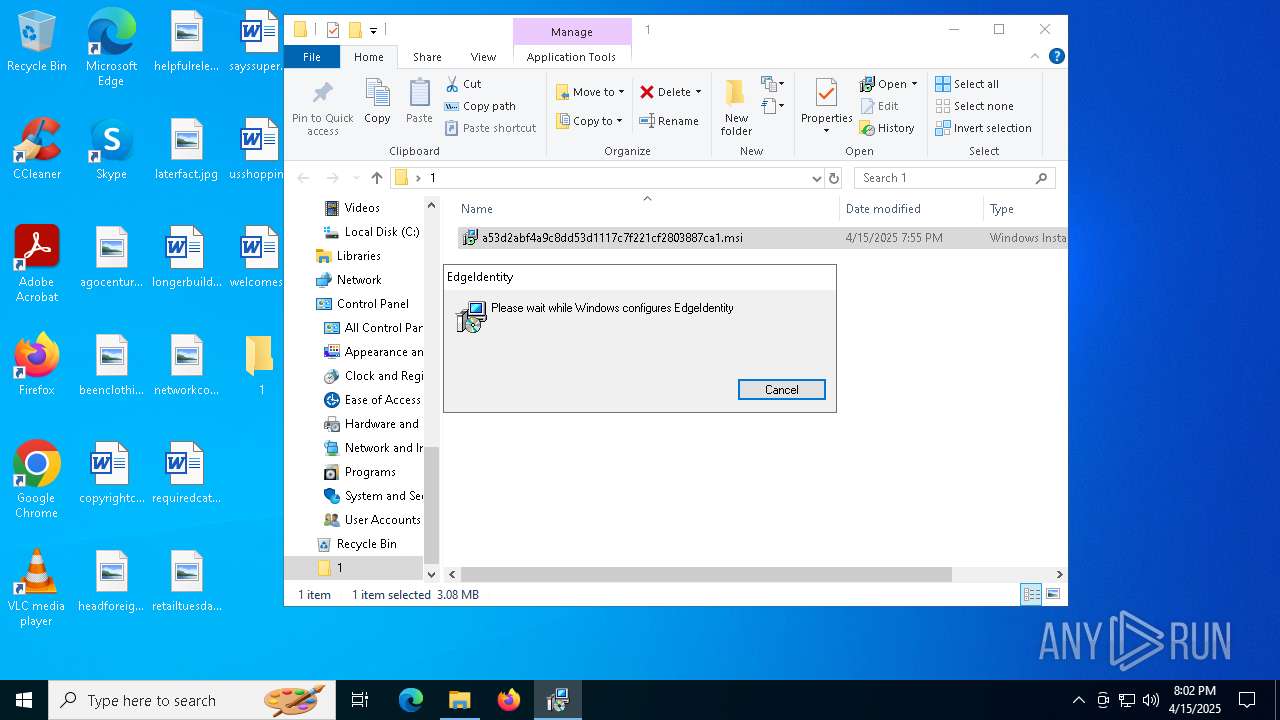
Starts a Microsoft application from unusual location
- cookie_exporter.exe (PID: 1196)
INFO
Reads Microsoft Office registry keys
- OpenWith.exe (PID: 3676)
- OpenWith.exe (PID: 3760)
- OpenWith.exe (PID: 5408)
Reads security settings of Internet Explorer
- OpenWith.exe (PID: 3676)
- OpenWith.exe (PID: 3760)
- msiexec.exe (PID: 6300)
The sample compiled with english language support
- WinRAR.exe (PID: 920)
- msiexec.exe (PID: 5384)
- msiexec.exe (PID: 6300)
- msiexec.exe (PID: 5200)
- msiexec.exe (PID: 2340)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 920)
- msiexec.exe (PID: 6300)
- msiexec.exe (PID: 5384)
- msiexec.exe (PID: 5200)
- msiexec.exe (PID: 2340)
Application launched itself
- Acrobat.exe (PID: 2420)
- AcroCEF.exe (PID: 4932)
Reads the software policy settings
- slui.exe (PID: 6972)
- msiexec.exe (PID: 6300)
- slui.exe (PID: 5624)
- msiexec.exe (PID: 5384)
Manual execution by a user
- msiexec.exe (PID: 6300)
- msiexec.exe (PID: 5200)
- msiexec.exe (PID: 2340)
Checks proxy server information
- msiexec.exe (PID: 6300)
- slui.exe (PID: 5624)
Creates files or folders in the user directory
- msiexec.exe (PID: 6300)
Reads the computer name
- msiexec.exe (PID: 5384)
- msiexec.exe (PID: 1128)
- msiexec.exe (PID: 1532)
- msiexec.exe (PID: 4284)
- msiexec.exe (PID: 5868)
- msiexec.exe (PID: 7012)
- msiexec.exe (PID: 1852)
- cookie_exporter.exe (PID: 1196)
Checks supported languages
- msiexec.exe (PID: 1532)
- msiexec.exe (PID: 5384)
- msiexec.exe (PID: 1128)
- cookie_exporter.exe (PID: 1196)
- msiexec.exe (PID: 5868)
- msiexec.exe (PID: 4284)
- msiexec.exe (PID: 7012)
- msiexec.exe (PID: 1852)
Manages system restore points
- SrTasks.exe (PID: 4236)
Reads the machine GUID from the registry
- msiexec.exe (PID: 5384)
Create files in a temporary directory
- msiexec.exe (PID: 1128)
- msiexec.exe (PID: 5384)
- msiexec.exe (PID: 4284)
- msiexec.exe (PID: 1852)
Creates a software uninstall entry
- msiexec.exe (PID: 5384)
Process checks computer location settings
- msiexec.exe (PID: 1128)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | 0x0001 |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2025:04:15 19:55:04 |
| ZipCRC: | 0xedc5112e |
| ZipCompressedSize: | 1835184 |
| ZipUncompressedSize: | 3231744 |
| ZipFileName: | a53d2abf4a9c8dd53d1117c7f221cf2803887ca1 |
Total processes
168
Monitored processes
34
Malicious processes
0
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 664 | C:\WINDOWS\System32\rundll32.exe C:\WINDOWS\System32\shell32.dll,SHCreateLocalServerRunDll {9aa46009-3ce0-458a-a354-715610a075e6} -Embedding | C:\Windows\System32\rundll32.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
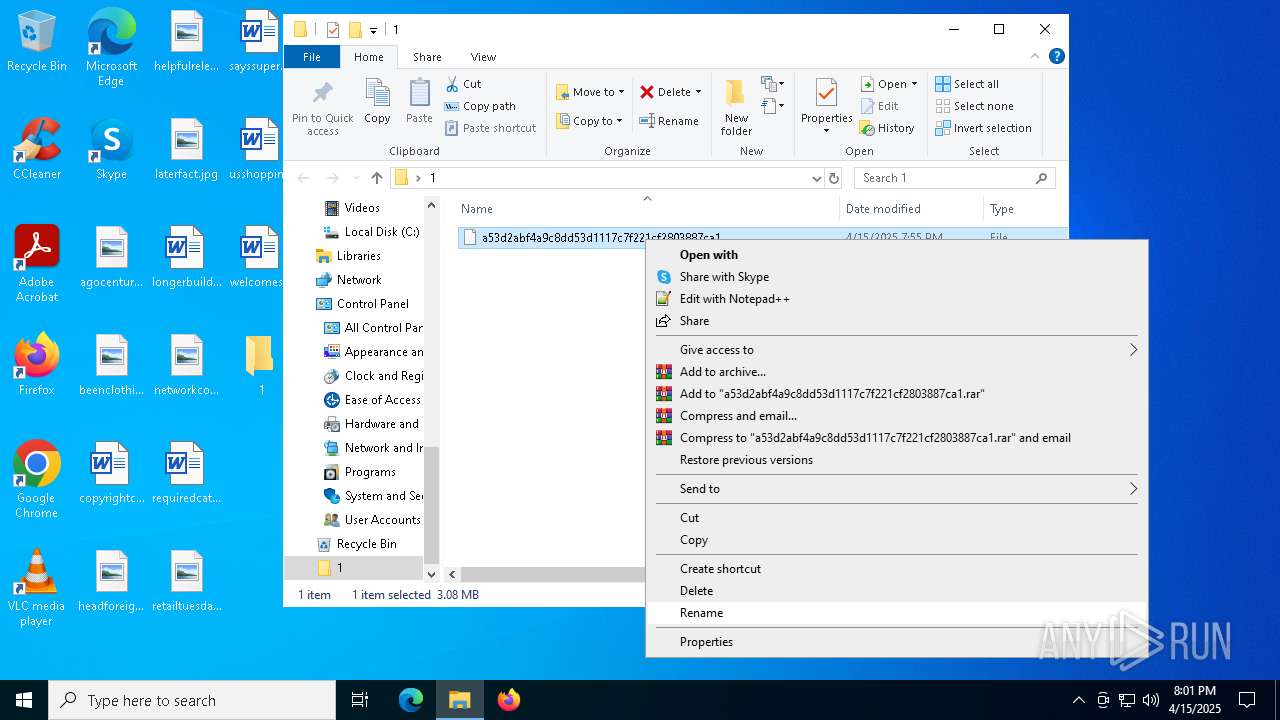
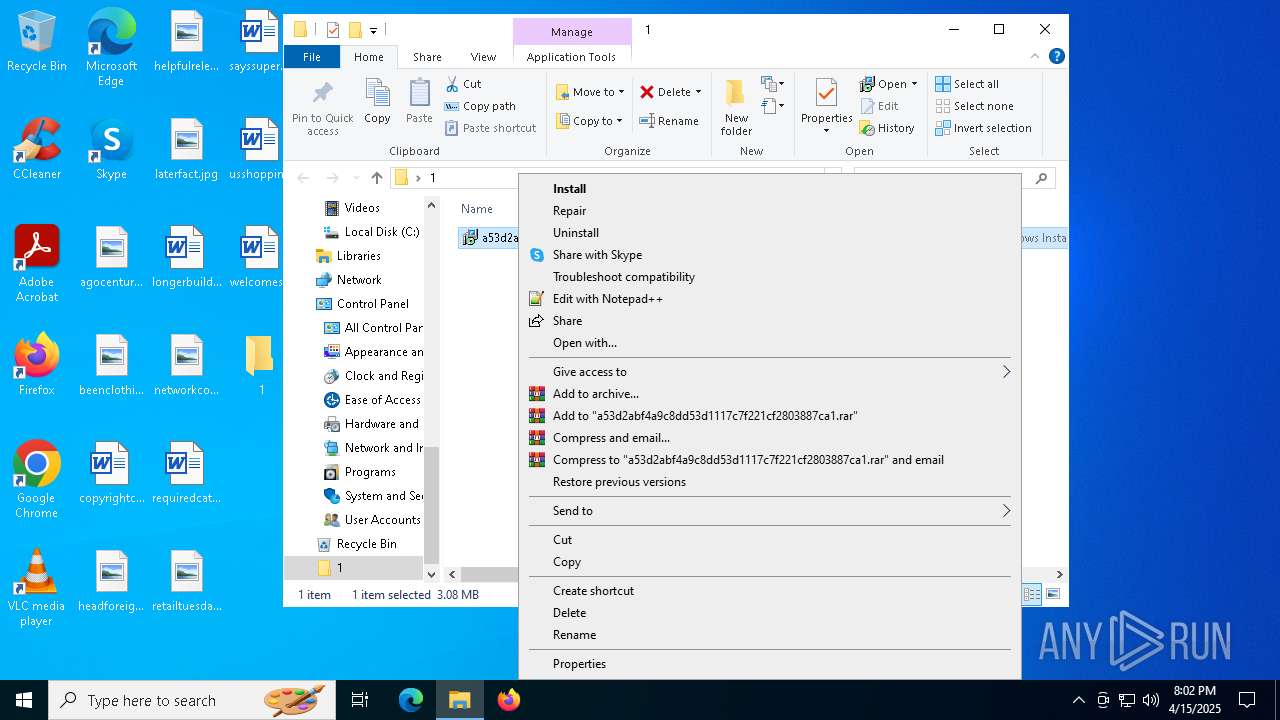
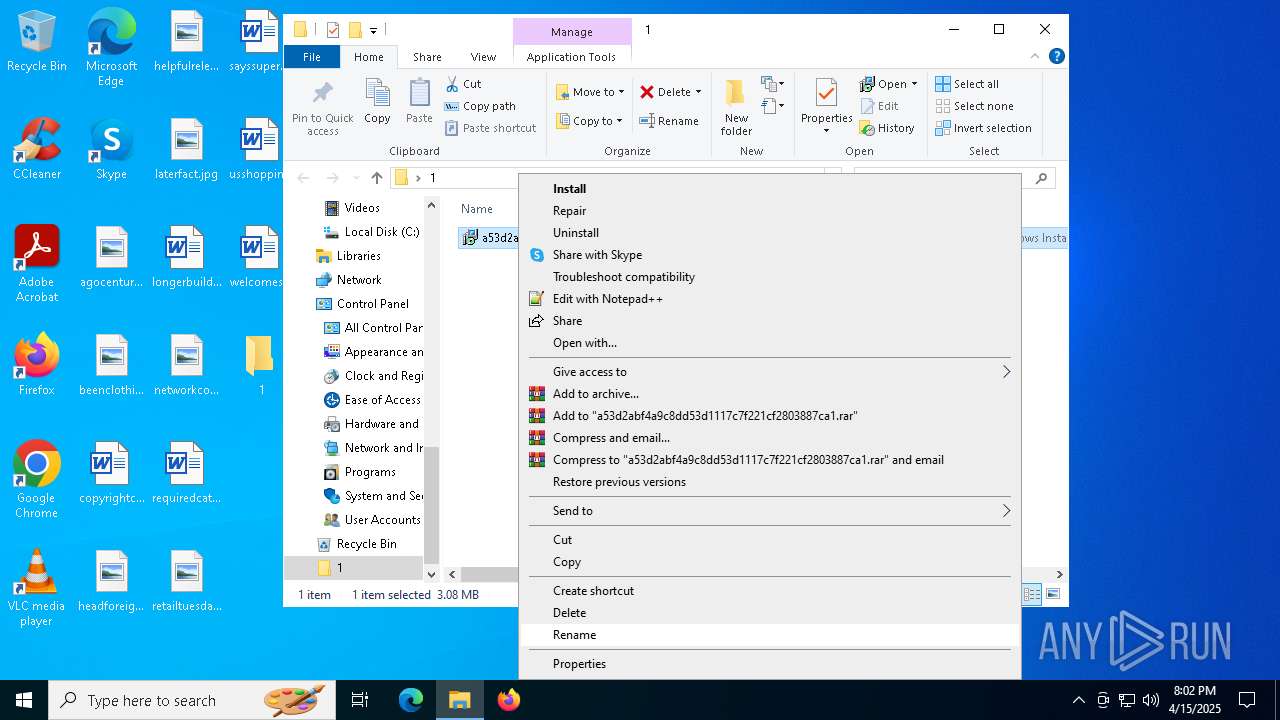
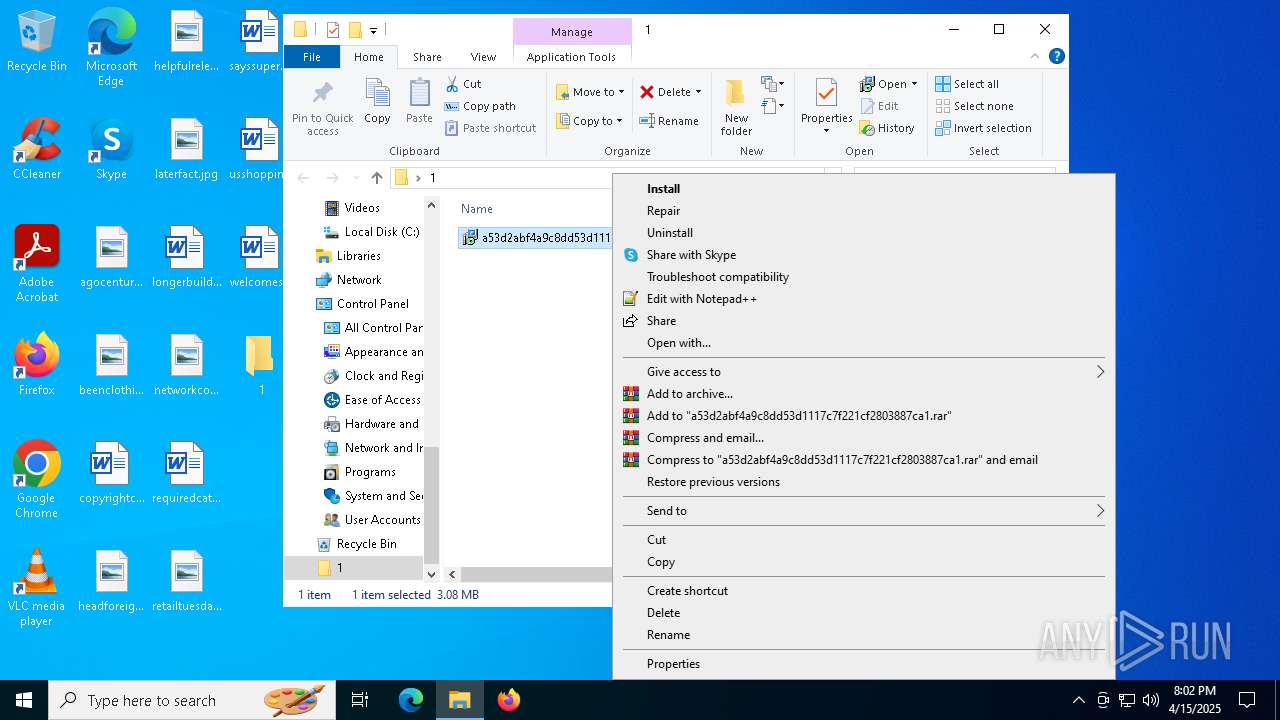
| 920 | "C:\Program Files\WinRAR\WinRAR.exe" C:\Users\admin\Downloads\MDE_File_Sample_a53d2abf4a9c8dd53d1117c7f221cf2803887ca1(2).zip | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
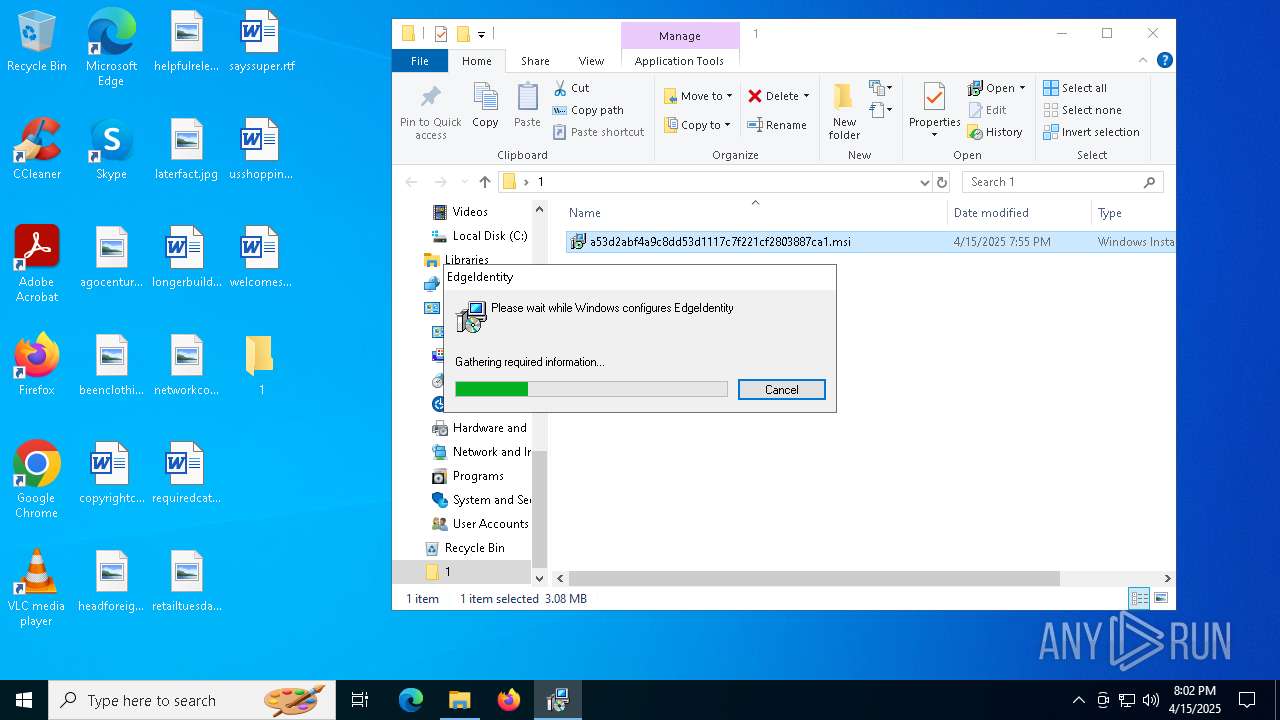
| 1128 | C:\Windows\syswow64\MsiExec.exe -Embedding 0A643ADDE5288177CCBEA01203FDA550 | C:\Windows\SysWOW64\msiexec.exe | — | msiexec.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows® installer Exit code: 0 Version: 5.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
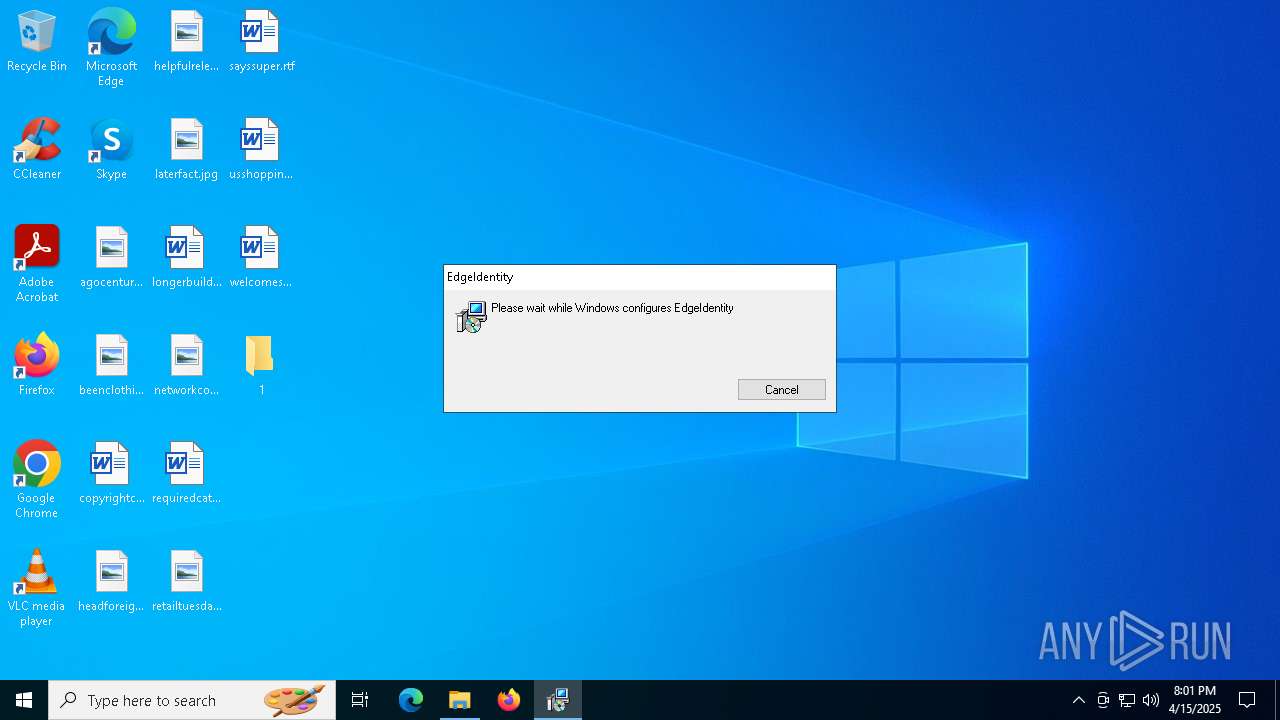
| 1196 | "C:\Users\admin\AppData\Local\Temp\EdgeIdentity\cookie_exporter.exe" | C:\Users\admin\AppData\Local\Temp\EdgeIdentity\cookie_exporter.exe | msiexec.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft Edge Version: 116.0.1938.81 Modules
| |||||||||||||||
| 1388 | "C:\Program Files\Adobe\Acrobat DC\Acrobat\acrocef_1\AcroCEF.exe" --type=renderer --log-severity=disable --user-agent-product="ReaderServices/23.1.20093 Chrome/105.0.0.0" --log-file="C:\Program Files\Adobe\Acrobat DC\Acrobat\acrocef_1\debug.log" --touch-events=enabled --disable-gpu-compositing --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=8 --mojo-platform-channel-handle=2824 --field-trial-handle=1608,i,17500984343611981626,1926731022821962041,131072 --disable-features=BackForwardCache,CalculateNativeWinOcclusion,WinUseBrowserSpellChecker /prefetch:1 | C:\Program Files\Adobe\Acrobat DC\Acrobat\acrocef_1\AcroCEF.exe | — | AcroCEF.exe | |||||||||||
User: admin Company: Adobe Systems Incorporated Integrity Level: LOW Description: Adobe AcroCEF Exit code: 0 Version: 23.1.20093.0 Modules
| |||||||||||||||
| 1532 | C:\Windows\syswow64\MsiExec.exe -Embedding 1FEA19023387E4D22B533E40EF320479 C | C:\Windows\SysWOW64\msiexec.exe | — | msiexec.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows® installer Exit code: 0 Version: 5.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1852 | C:\Windows\syswow64\MsiExec.exe -Embedding E9D36E94C0B97B5AB34CCD6B19EBD77A | C:\Windows\SysWOW64\msiexec.exe | — | msiexec.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows® installer Exit code: 0 Version: 5.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2288 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | SrTasks.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
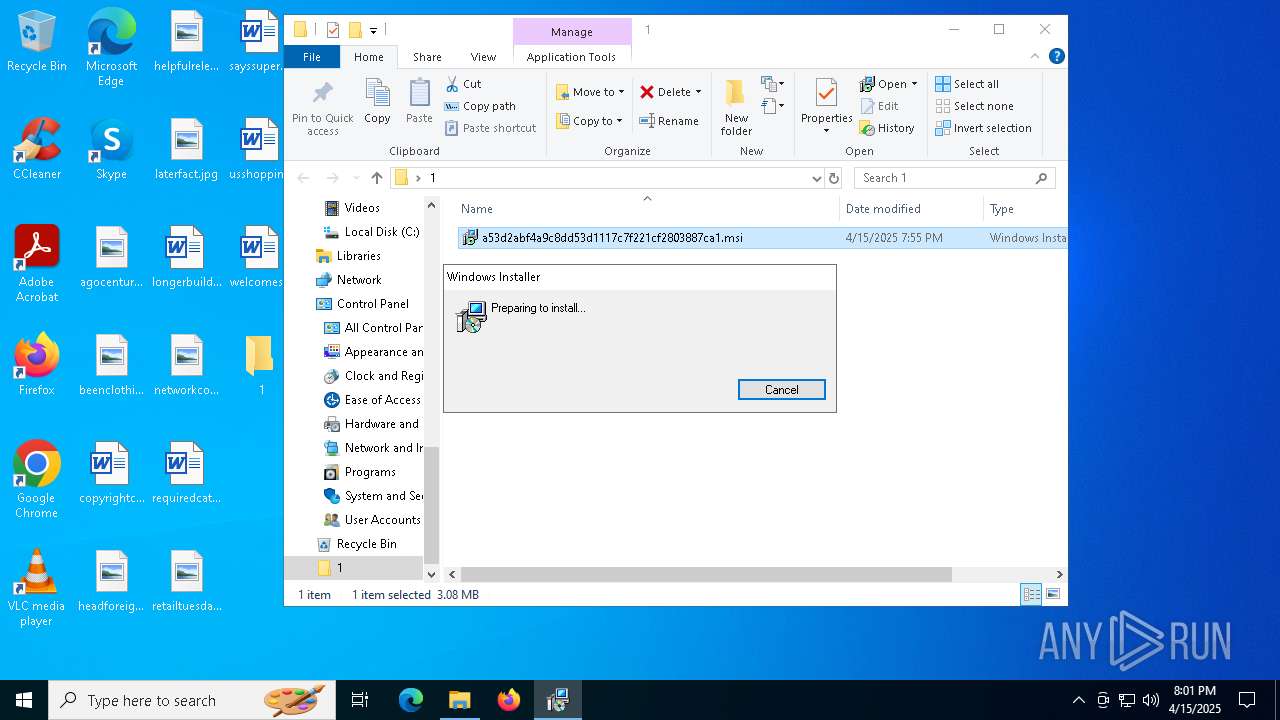
| 2340 | "C:\WINDOWS\System32\msiexec.exe" /i "C:\Users\admin\Desktop\1\a53d2abf4a9c8dd53d1117c7f221cf2803887ca1.msi" | C:\Windows\System32\msiexec.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows® installer Exit code: 0 Version: 5.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
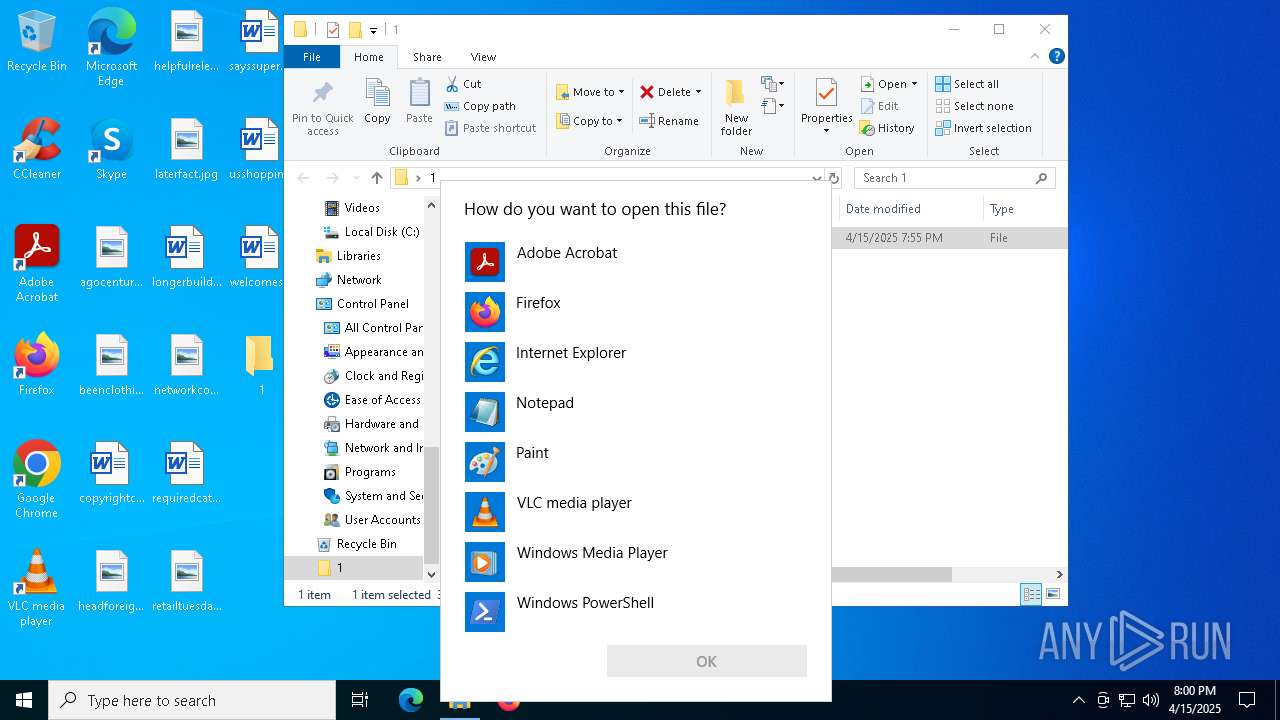
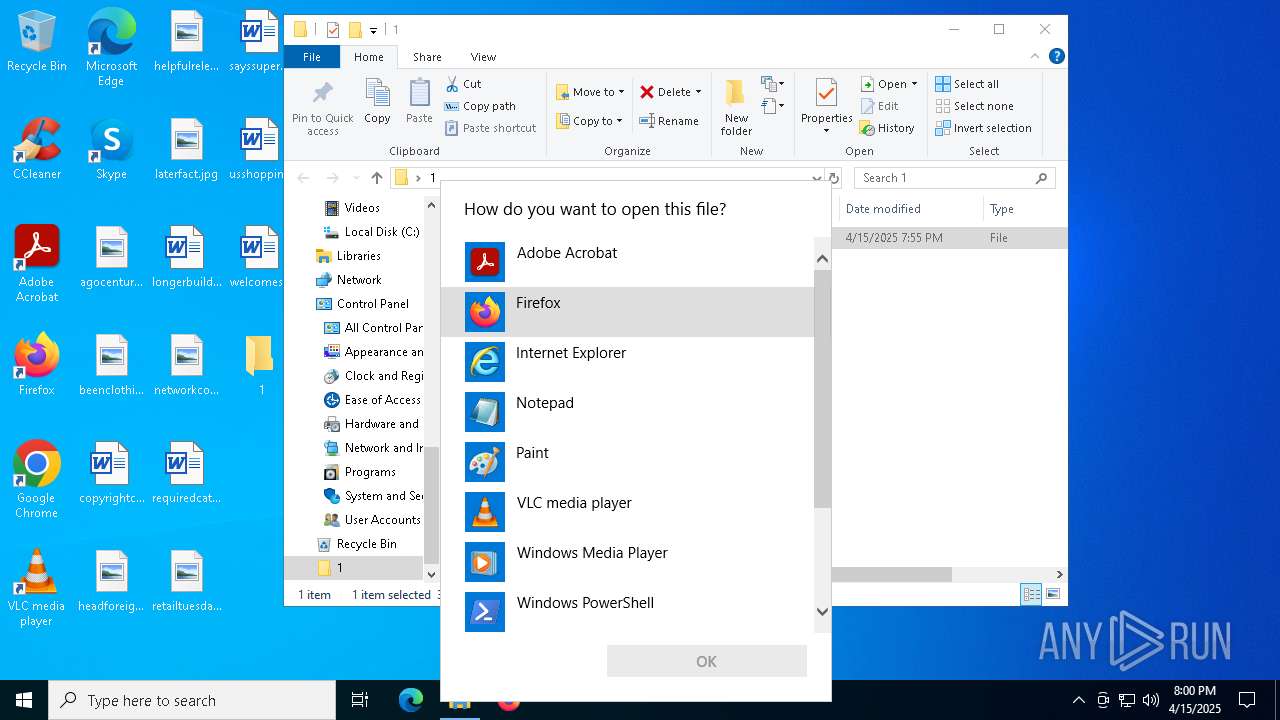
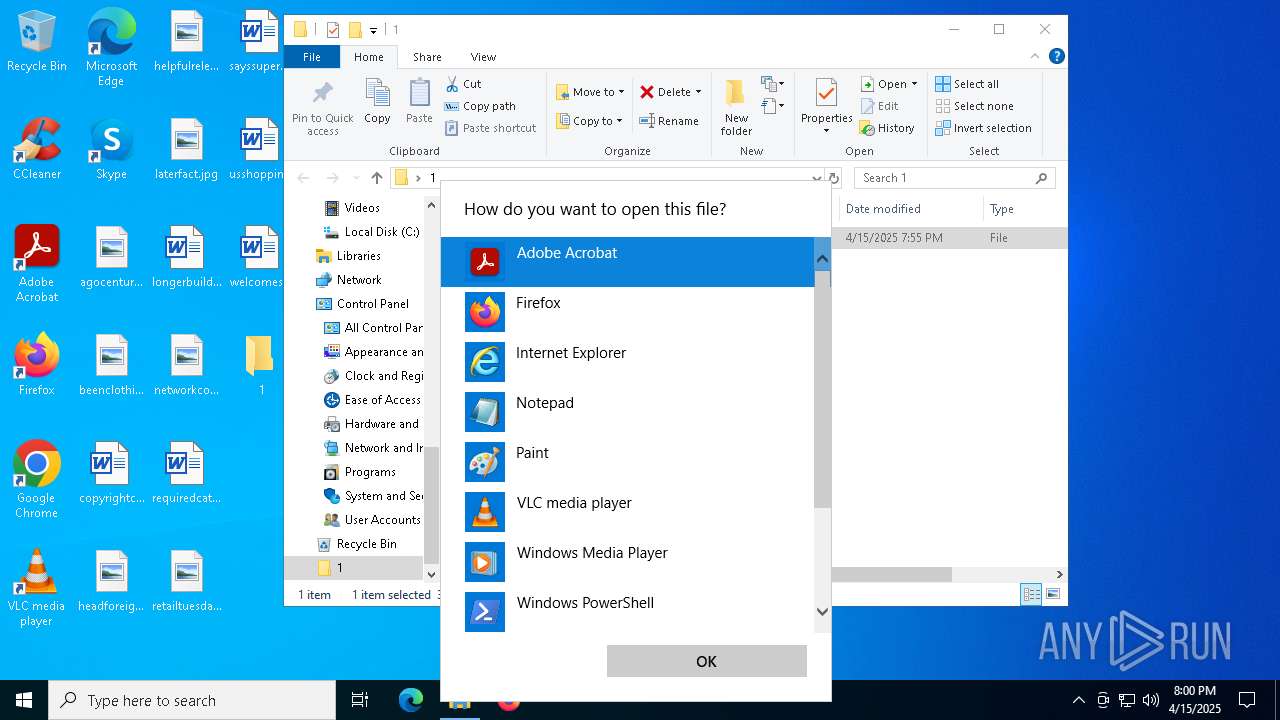
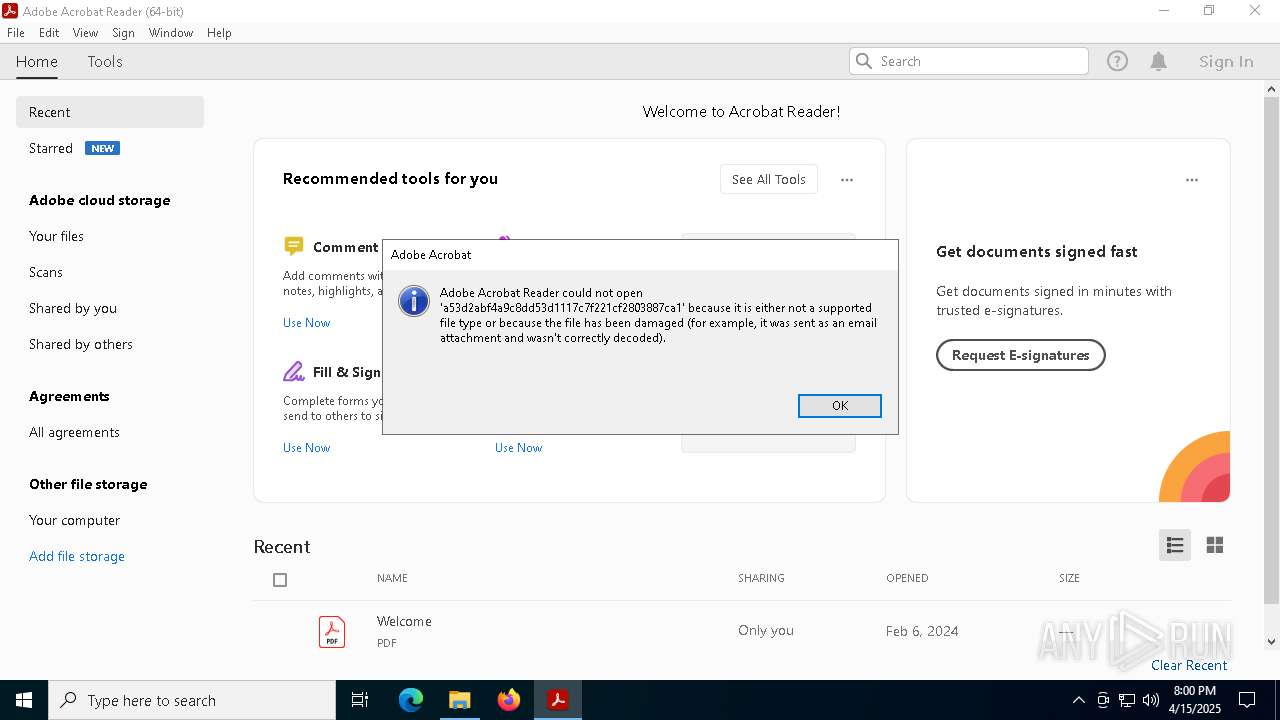
| 2420 | "C:\Program Files\Adobe\Acrobat DC\Acrobat\Acrobat.exe" "C:\Users\admin\Desktop\1\a53d2abf4a9c8dd53d1117c7f221cf2803887ca1" | C:\Program Files\Adobe\Acrobat DC\Acrobat\Acrobat.exe | — | OpenWith.exe | |||||||||||
User: admin Company: Adobe Systems Incorporated Integrity Level: MEDIUM Description: Adobe Acrobat Exit code: 1 Version: 23.1.20093.0 Modules
| |||||||||||||||
Total events
31 935
Read events
31 438
Write events
434
Delete events
63
Modification events
| (PID) Process: | (920) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (920) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (920) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (920) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Downloads\MDE_File_Sample_a53d2abf4a9c8dd53d1117c7f221cf2803887ca1(2).zip | |||
| (PID) Process: | (920) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (920) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (920) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (920) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (920) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\DialogEditHistory\ExtrPath |
| Operation: | delete value | Name: | 15 |
Value: | |||
| (PID) Process: | (920) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\DialogEditHistory\ExtrPath |
| Operation: | delete value | Name: | 14 |
Value: | |||
Executable files
36
Suspicious files
166
Text files
20
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 5964 | Acrobat.exe | C:\Users\admin\AppData\Local\Adobe\Acrobat\DC\SOPHIA\Acrobat\Files\TESTING | binary | |
MD5:DC84B0D741E5BEAE8070013ADDCC8C28 | SHA256:81FF65EFC4487853BDB4625559E69AB44F19E0F5EFBD6D5B2AF5E3AB267C8E06 | |||
| 5964 | Acrobat.exe | C:\Users\admin\AppData\Local\Adobe\Acrobat\DC\SOPHIA\Acrobat\SOPHIA.json | binary | |
MD5:837C1211E392A24D64C670DC10E8DA1B | SHA256:8013AC030684B86D754BBFBAB8A9CEC20CAA4DD9C03022715FF353DC10E14031 | |||
| 4932 | AcroCEF.exe | C:\Users\admin\AppData\LocalLow\Adobe\AcroCef\DC\Acrobat\Cache\Code Cache\js\0786087c3c360803_0 | binary | |
MD5:47F18843AA5F0F7F5C8B9C917D5DC1CB | SHA256:57FFEBFB22A5C6791DA2E5AD95FA3A53BA6B3872A31793A1F3B066082815CAFD | |||
| 4932 | AcroCEF.exe | C:\Users\admin\AppData\LocalLow\Adobe\AcroCef\DC\Acrobat\Cache\Local Storage\leveldb\LOG.old | text | |
MD5:8412AEEF2309E13FC954061D9BCEFFF4 | SHA256:D062D7B5DF5F3BCB753E97AB5D1DCD9CF62058D9103DA383DBE1F482FC1D4644 | |||
| 4932 | AcroCEF.exe | C:\Users\admin\AppData\LocalLow\Adobe\AcroCef\DC\Acrobat\Cache\Local Storage\leveldb\LOG.old~RF11aa66.TMP | text | |
MD5:ED7D8AAE48211E2BFAF557130572C62A | SHA256:A5CF8D8ADC86DCA357396AF7E3A24A116072D5C1E5552EEB76601AE2673DED6E | |||
| 4932 | AcroCEF.exe | C:\Users\admin\AppData\LocalLow\Adobe\AcroCef\DC\Acrobat\Cache\Session Storage\LOG.old | text | |
MD5:EB1590F2607E1CE46DBF6A521F772EA0 | SHA256:4355D9A8A115BA4E41178B456A8A5578846EB1F7EC9509249C2405F758F31731 | |||
| 4932 | AcroCEF.exe | C:\Users\admin\AppData\LocalLow\Adobe\AcroCef\DC\Acrobat\Cache\Session Storage\LOG.old~RF11aa56.TMP | text | |
MD5:7383516745DEC1E86152192435F92D1F | SHA256:E22D34BBD915EEB277D4F4138D176EACE5577CF035EF7C2C80A4BC4D9B6C0E1D | |||
| 4932 | AcroCEF.exe | C:\Users\admin\AppData\LocalLow\Adobe\AcroCef\DC\Acrobat\Cache\Code Cache\js\4a0e94571d979b3c_0 | binary | |
MD5:E5CBFC7AB8944B646B8A198E9AFAA564 | SHA256:F9CFFD1148C1786FBF9AD5975AB43A68E7F3C2FC1405A21B1BC0EE5CF25D5B99 | |||
| 4932 | AcroCEF.exe | C:\Users\admin\AppData\LocalLow\Adobe\AcroCef\DC\Acrobat\Cache\Code Cache\js\2a426f11fd8ebe18_0 | binary | |
MD5:2109078E1321E84DDE7EDD97F56D8788 | SHA256:AE324AFAE34778D273E72B794CBAF8D248F97F8BD88F1B1F5EED43A278391F7B | |||
| 4932 | AcroCEF.exe | C:\Users\admin\AppData\LocalLow\Adobe\AcroCef\DC\Acrobat\Cache\Code Cache\js\bba29d2e6197e2f4_0 | binary | |
MD5:686F721BC09C45C5DAFB19FF108306AF | SHA256:AAF07958A373E1053F7F1C449DDF918D8360A2F8014FAC0E58F4B2619A581DE1 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
13
TCP/UDP connections
47
DNS requests
2 342
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 23.48.23.173:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
6544 | svchost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
1228 | SIHClient.exe | GET | 200 | 2.23.246.101:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
1228 | SIHClient.exe | GET | 200 | 2.23.246.101:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
2924 | SearchApp.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
2924 | SearchApp.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
6300 | msiexec.exe | GET | 200 | 18.173.205.76:80 | http://ocsps.ssl.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQg3SSkKA74hABkhmlBtJTz8w3hlAQU%2BWC71OPVNPa49QaAJadz20ZpqJ4CEEJLalPOx2YUHCpjsaUcQQQ%3D | unknown | — | — | whitelisted |
6300 | msiexec.exe | GET | 200 | 18.173.205.76:80 | http://ocsps.ssl.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQg3SSkKA74hABkhmlBtJTz8w3hlAQU%2BWC71OPVNPa49QaAJadz20ZpqJ4CEEJLalPOx2YUHCpjsaUcQQQ%3D | unknown | — | — | whitelisted |
6300 | msiexec.exe | GET | 200 | 95.100.110.12:80 | http://sslcom.ocsp-certum.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTYOkzrrCGQj08njZXbUQQpkoUmuQQUCHbNywf%2FJPbFze27kLzihDdGdfcCEGL4EqNfUr10txjWEKxLR4M%3D | unknown | — | — | whitelisted |
756 | lsass.exe | GET | 200 | 142.250.184.227:80 | http://c.pki.goog/r/r4.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 23.48.23.173:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
3216 | svchost.exe | 172.211.123.248:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
6544 | svchost.exe | 40.126.32.74:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
6544 | svchost.exe | 2.17.190.73:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
2104 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
1228 | SIHClient.exe | 172.202.163.200:443 | slscr.update.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | GB | whitelisted |
1228 | SIHClient.exe | 2.23.246.101:80 | www.microsoft.com | Ooredoo Q.S.C. | QA | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
geo2.adobe.com |
| whitelisted |