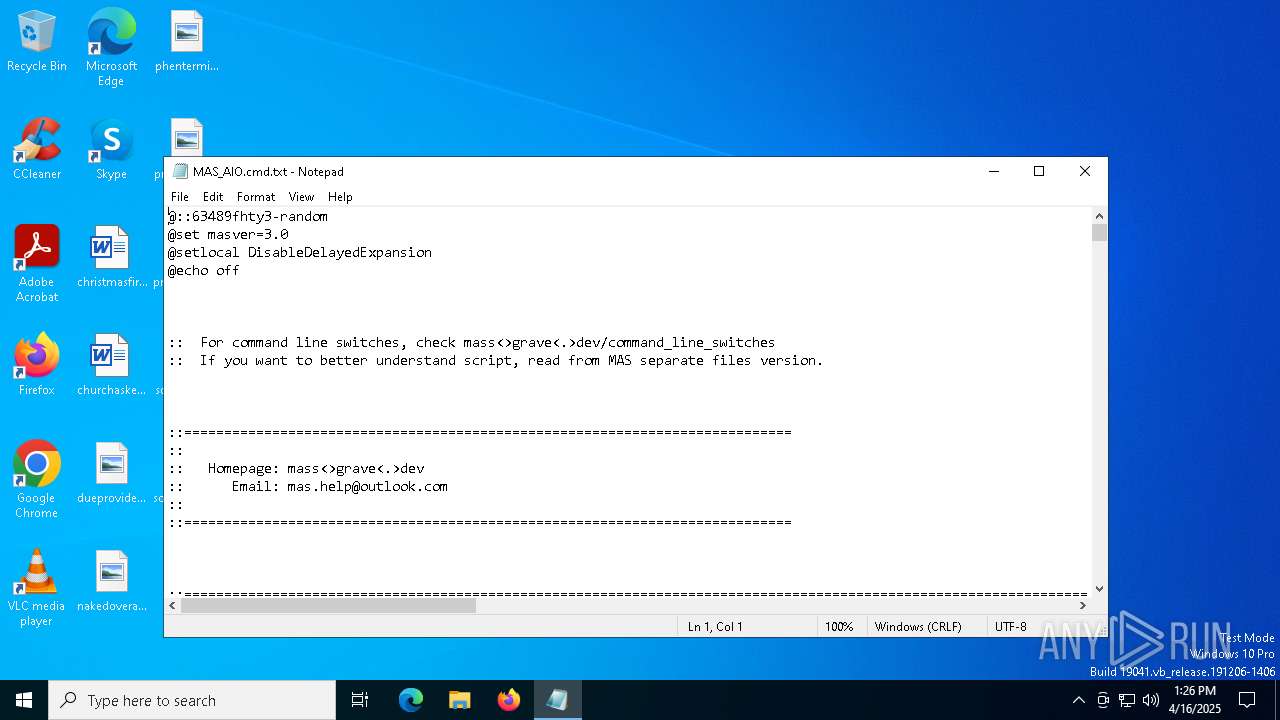
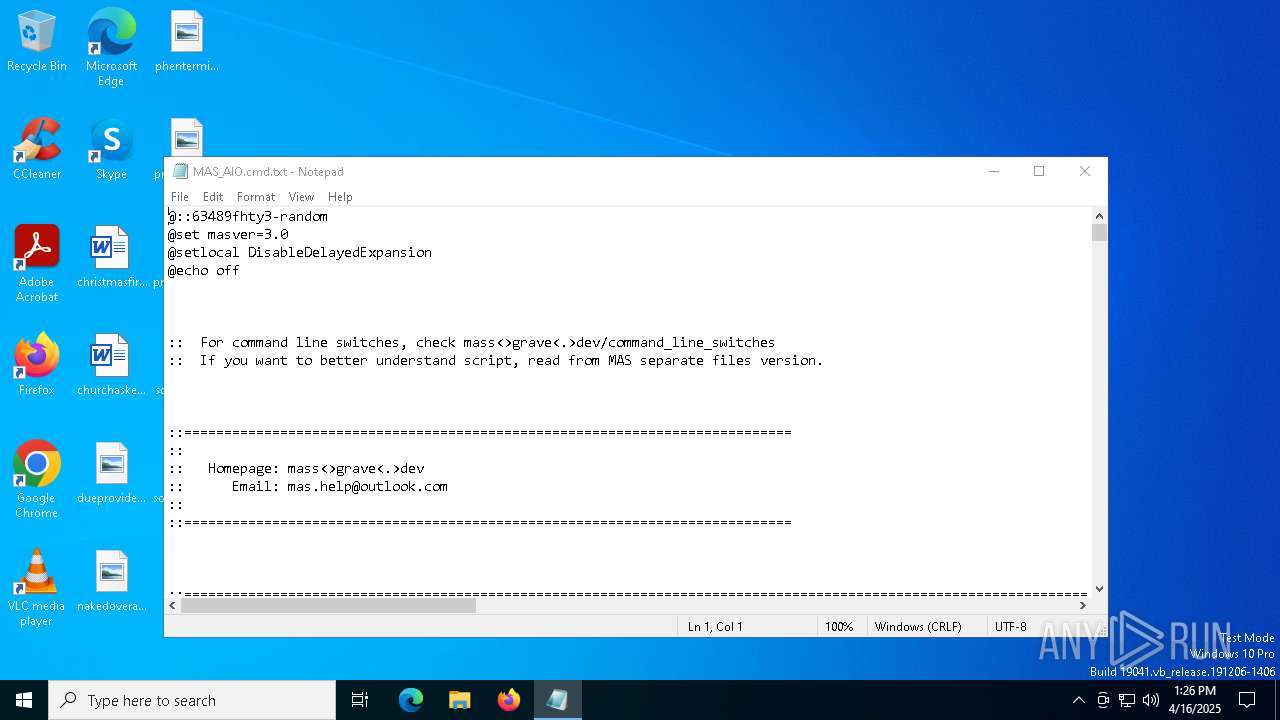
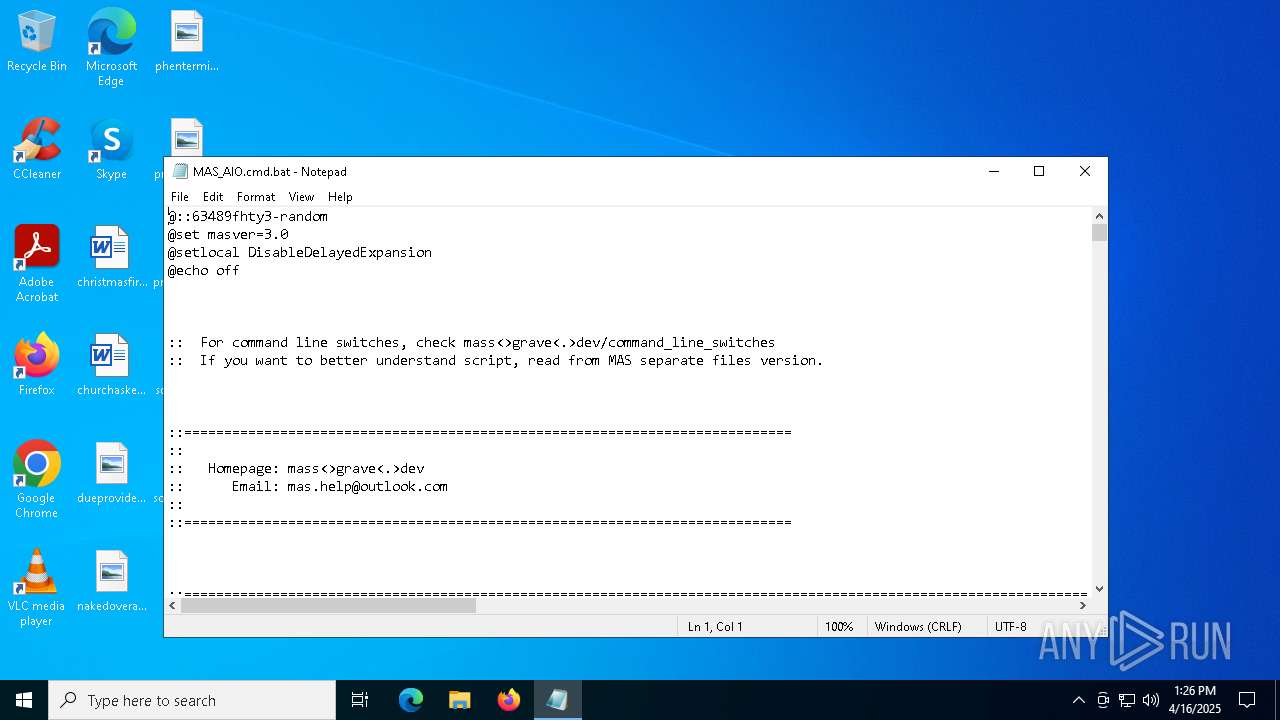
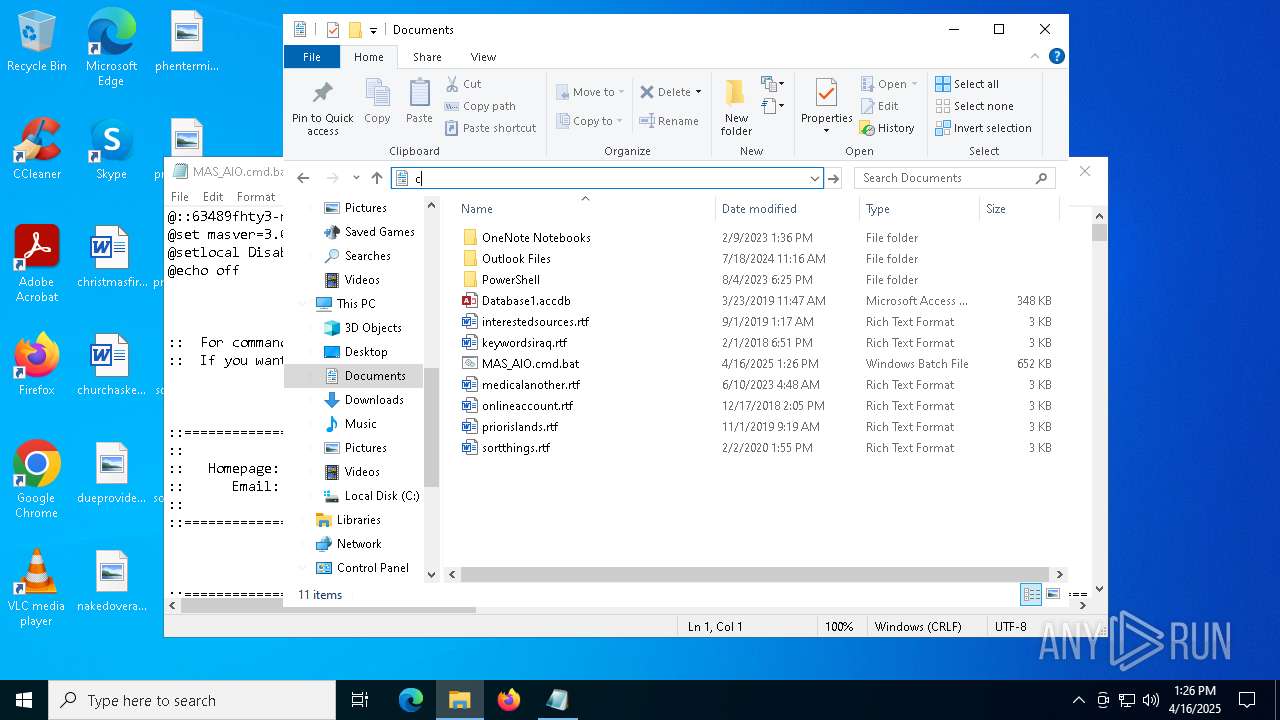
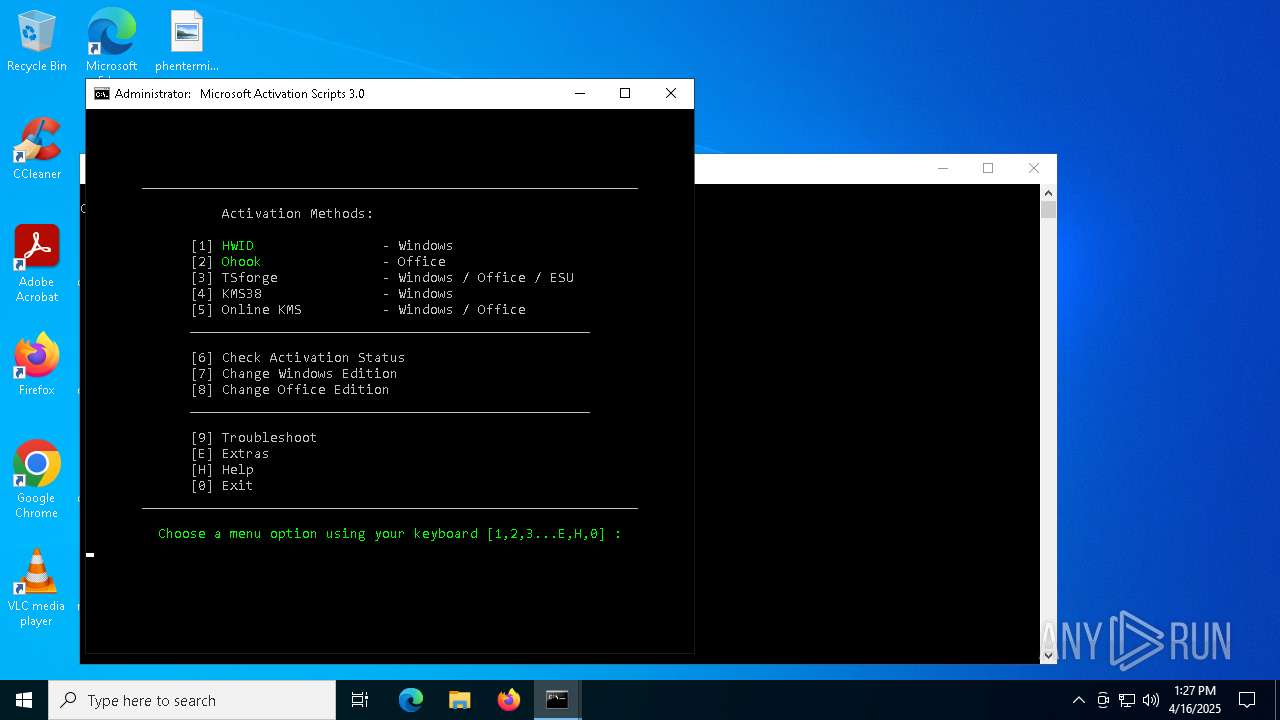
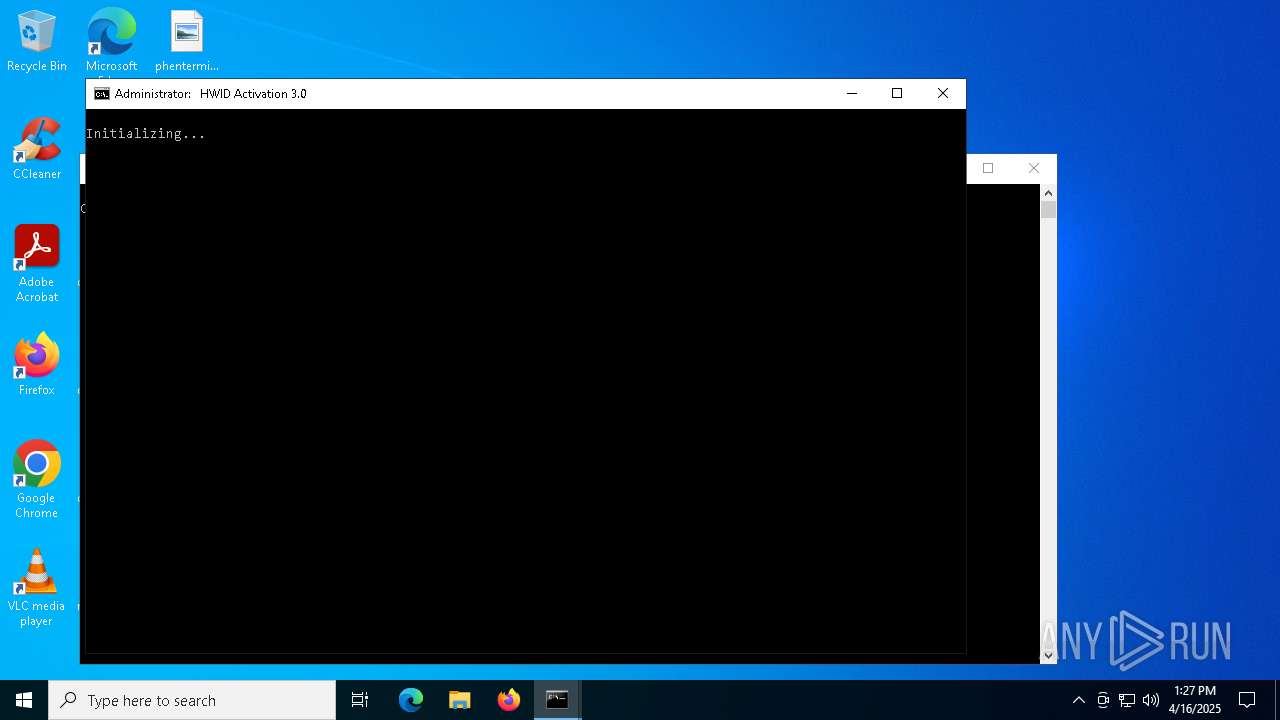
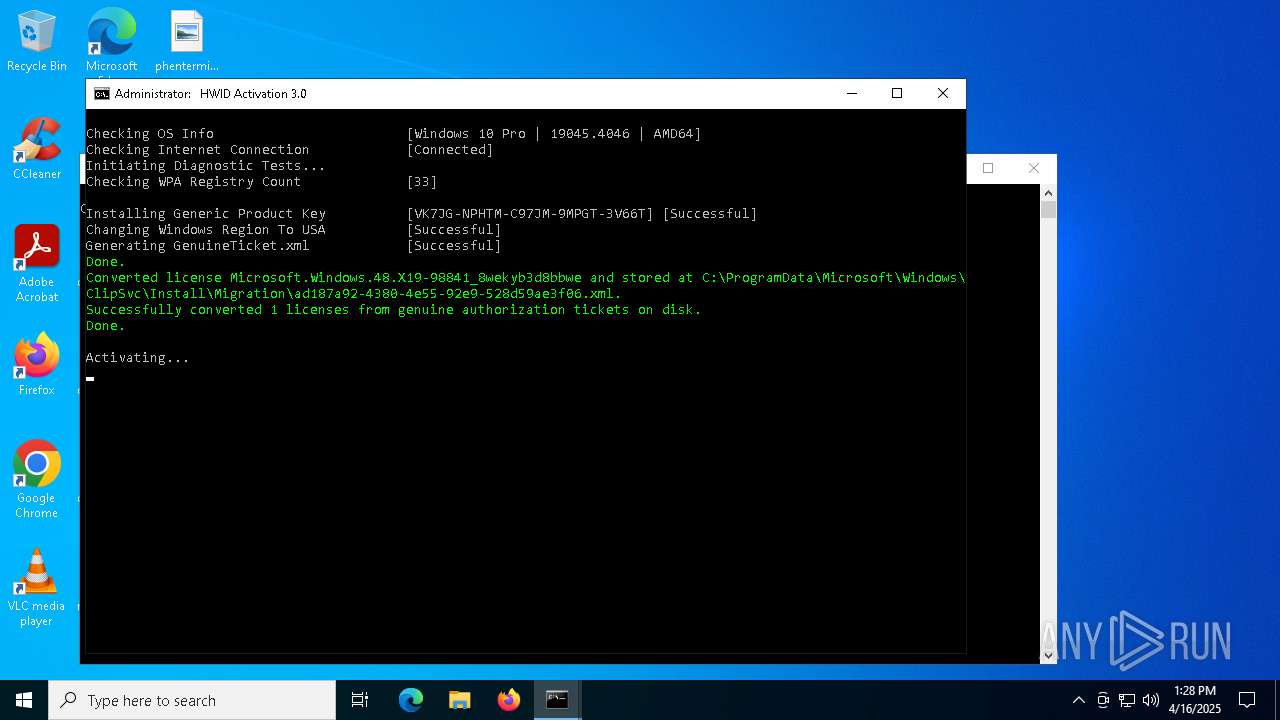
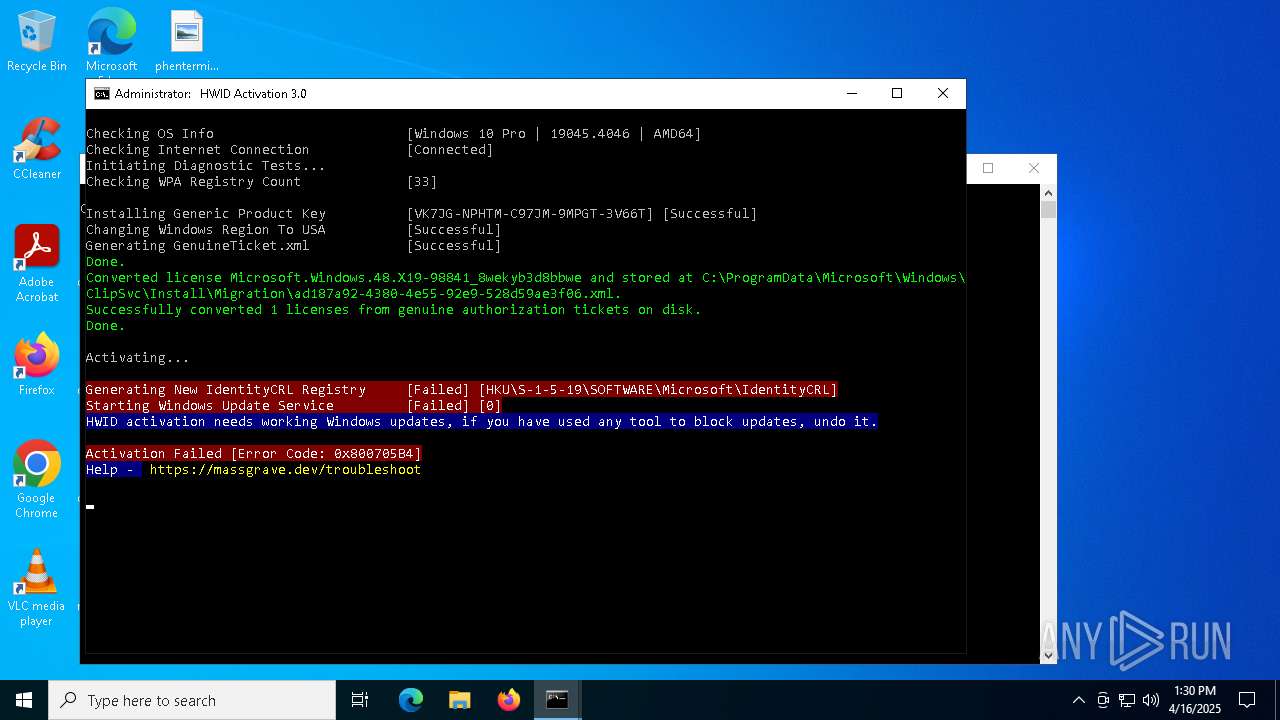
| download: | /massgravel/Microsoft-Activation-Scripts/313f240448953cd5fe3c5631f4e4de502f23fc9a/MAS/All-In-One-Version-KL/MAS_AIO.cmd |
| Full analysis: | https://app.any.run/tasks/a9511d2e-c4f1-4a5a-bbfc-4332a9042469 |
| Verdict: | Malicious activity |
| Analysis date: | April 16, 2025, 13:26:19 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Indicators: | |
| MIME: | text/plain |
| File info: | ASCII text, with very long lines (348), with CRLF line terminators |
| MD5: | 792AA716B87B5B6591B43B6FC8C64CE4 |
| SHA1: | 0734B56937F4028C7A6AFC20AB4F3351DC9CD7B6 |
| SHA256: | 919F17B46BF62169E8811201F75EFDF1D5C1504321B78A7B0FB47C335ECBC1B0 |
| SSDEEP: | 6144:ToIjH+imAc5g+9YCMD0a9g7nc/4IsK0ykpBwuI:ToIjHOAWYCMDF0c/psK0ykpBm |
MALICIOUS
No malicious indicators.SUSPICIOUS
Starts SC.EXE for service management
- cmd.exe (PID: 6712)
- cmd.exe (PID: 3008)
- cmd.exe (PID: 7084)
Windows service management via SC.EXE
- sc.exe (PID: 2420)
- sc.exe (PID: 4464)
- sc.exe (PID: 5176)
- sc.exe (PID: 2332)
- sc.exe (PID: 3096)
- sc.exe (PID: 1764)
- sc.exe (PID: 4272)
- sc.exe (PID: 5736)
- sc.exe (PID: 6112)
- sc.exe (PID: 6740)
- sc.exe (PID: 1180)
- sc.exe (PID: 5084)
- sc.exe (PID: 1312)
- sc.exe (PID: 4008)
- sc.exe (PID: 4208)
- sc.exe (PID: 4380)
- sc.exe (PID: 4452)
- sc.exe (PID: 7000)
- sc.exe (PID: 6252)
- sc.exe (PID: 5600)
- sc.exe (PID: 1764)
- sc.exe (PID: 5164)
- sc.exe (PID: 2644)
- sc.exe (PID: 6268)
- sc.exe (PID: 4380)
- sc.exe (PID: 5384)
- sc.exe (PID: 5452)
- sc.exe (PID: 5344)
- sc.exe (PID: 3332)
- sc.exe (PID: 1312)
- sc.exe (PID: 5244)
- sc.exe (PID: 3032)
- sc.exe (PID: 2096)
- sc.exe (PID: 6744)
- sc.exe (PID: 5608)
- sc.exe (PID: 6248)
- sc.exe (PID: 5172)
- sc.exe (PID: 5452)
- sc.exe (PID: 2656)
Application launched itself
- cmd.exe (PID: 4112)
- cmd.exe (PID: 6712)
- cmd.exe (PID: 1764)
- cmd.exe (PID: 3008)
- cmd.exe (PID: 7084)
- cmd.exe (PID: 4560)
- powershell.exe (PID: 2288)
- powershell.exe (PID: 5360)
- ClipUp.exe (PID: 6044)
- powershell.exe (PID: 4696)
- powershell.exe (PID: 1388)
- powershell.exe (PID: 5952)
- powershell.exe (PID: 4284)
Starts CMD.EXE for commands execution
- cmd.exe (PID: 4112)
- cmd.exe (PID: 6712)
- cmd.exe (PID: 3008)
- cmd.exe (PID: 1764)
- powershell.exe (PID: 1096)
- cmd.exe (PID: 4560)
- cmd.exe (PID: 7084)
- powershell.exe (PID: 2564)
Probably obfuscated PowerShell command line is found
- cmd.exe (PID: 5512)
- cmd.exe (PID: 968)
- cmd.exe (PID: 2644)
- cmd.exe (PID: 7084)
- cmd.exe (PID: 2148)
Uses sleep to delay execution (POWERSHELL)
- powershell.exe (PID: 960)
- powershell.exe (PID: 2644)
- powershell.exe (PID: 5344)
- powershell.exe (PID: 6740)
- powershell.exe (PID: 6392)
Using 'findstr.exe' to search for text patterns in files and output
- cmd.exe (PID: 6712)
- cmd.exe (PID: 3008)
- cmd.exe (PID: 7084)
Possibly malicious use of IEX has been detected
- cmd.exe (PID: 5512)
- cmd.exe (PID: 968)
- cmd.exe (PID: 2644)
- cmd.exe (PID: 7084)
- cmd.exe (PID: 2148)
Executing commands from ".cmd" file
- cmd.exe (PID: 6712)
- cmd.exe (PID: 3008)
- powershell.exe (PID: 1096)
- cmd.exe (PID: 7084)
- powershell.exe (PID: 2564)
Executing commands from a ".bat" file
- cmd.exe (PID: 6712)
- powershell.exe (PID: 2564)
- cmd.exe (PID: 3008)
- powershell.exe (PID: 1096)
- cmd.exe (PID: 7084)
Starts POWERSHELL.EXE for commands execution
- cmd.exe (PID: 6712)
- cmd.exe (PID: 968)
- cmd.exe (PID: 3008)
- cmd.exe (PID: 2644)
- cmd.exe (PID: 7084)
- cmd.exe (PID: 5512)
- cmd.exe (PID: 6620)
- cmd.exe (PID: 6708)
- powershell.exe (PID: 2288)
- cmd.exe (PID: 2148)
- cmd.exe (PID: 1196)
- cmd.exe (PID: 6252)
- powershell.exe (PID: 5360)
- cmd.exe (PID: 2104)
- powershell.exe (PID: 4696)
- powershell.exe (PID: 1388)
- powershell.exe (PID: 5952)
- powershell.exe (PID: 4284)
Uses base64 encoding (POWERSHELL)
- powershell.exe (PID: 960)
- powershell.exe (PID: 2644)
- powershell.exe (PID: 5344)
- powershell.exe (PID: 6740)
- powershell.exe (PID: 1348)
- powershell.exe (PID: 6392)
Gets content of a file (POWERSHELL)
- powershell.exe (PID: 2644)
- powershell.exe (PID: 5344)
- powershell.exe (PID: 960)
- powershell.exe (PID: 6740)
- powershell.exe (PID: 6392)
Uses REG/REGEDIT.EXE to modify registry
- cmd.exe (PID: 7084)
Hides command output
- cmd.exe (PID: 5736)
- cmd.exe (PID: 6044)
- cmd.exe (PID: 2980)
- cmd.exe (PID: 2148)
- cmd.exe (PID: 4728)
- cmd.exe (PID: 6036)
- cmd.exe (PID: 728)
- cmd.exe (PID: 1196)
- cmd.exe (PID: 6620)
- cmd.exe (PID: 6080)
- cmd.exe (PID: 6620)
- cmd.exe (PID: 2148)
- cmd.exe (PID: 5776)
Uses WMIC.EXE to obtain operating system information
- cmd.exe (PID: 6044)
Uses WMIC.EXE to obtain computer system information
- cmd.exe (PID: 6676)
- cmd.exe (PID: 7084)
The process bypasses the loading of PowerShell profile settings
- powershell.exe (PID: 2288)
- powershell.exe (PID: 5360)
- powershell.exe (PID: 4696)
- powershell.exe (PID: 1388)
- powershell.exe (PID: 5952)
- powershell.exe (PID: 4284)
The process hides Powershell's copyright startup banner
- powershell.exe (PID: 2288)
- powershell.exe (PID: 5360)
- powershell.exe (PID: 4696)
- powershell.exe (PID: 5952)
- powershell.exe (PID: 1388)
- powershell.exe (PID: 4284)
Uses WMIC.EXE to obtain Windows Installer data
- cmd.exe (PID: 7084)
- cmd.exe (PID: 6036)
- cmd.exe (PID: 6620)
- cmd.exe (PID: 6620)
Uses WMIC.EXE to obtain service application data
- cmd.exe (PID: 7084)
Process uses IPCONFIG to clear DNS cache
- cmd.exe (PID: 7084)
Gets or sets the security protocol (POWERSHELL)
- powershell.exe (PID: 4560)
- powershell.exe (PID: 4016)
- powershell.exe (PID: 2772)
Executes application which crashes
- powershell.exe (PID: 5680)
The process creates files with name similar to system file names
- WerFault.exe (PID: 2344)
INFO
Manual execution by a user
- cmd.exe (PID: 6712)
Checks operating system version
- cmd.exe (PID: 6712)
- cmd.exe (PID: 3008)
- cmd.exe (PID: 7084)
Converts byte array into ASCII string (POWERSHELL)
- powershell.exe (PID: 960)
- powershell.exe (PID: 2644)
- powershell.exe (PID: 5344)
- powershell.exe (PID: 6740)
- powershell.exe (PID: 6392)
Reads security settings of Internet Explorer
- notepad.exe (PID: 5280)
- WMIC.exe (PID: 1324)
- WMIC.exe (PID: 6264)
- WMIC.exe (PID: 6112)
- WMIC.exe (PID: 684)
- WMIC.exe (PID: 5608)
- WMIC.exe (PID: 4336)
- WMIC.exe (PID: 4172)
- WMIC.exe (PID: 3300)
- WMIC.exe (PID: 6136)
- WMIC.exe (PID: 2192)
- WMIC.exe (PID: 2980)
- WMIC.exe (PID: 2992)
Checks whether the specified file exists (POWERSHELL)
- powershell.exe (PID: 960)
- powershell.exe (PID: 2644)
- powershell.exe (PID: 5344)
- powershell.exe (PID: 6740)
- powershell.exe (PID: 6392)
Gets a random number, or selects objects randomly from a collection (POWERSHELL)
- powershell.exe (PID: 960)
- powershell.exe (PID: 2644)
- powershell.exe (PID: 5344)
- powershell.exe (PID: 6740)
- powershell.exe (PID: 6392)
Creates a byte array (POWERSHELL)
- powershell.exe (PID: 960)
- powershell.exe (PID: 2644)
- powershell.exe (PID: 5344)
- powershell.exe (PID: 6740)
- powershell.exe (PID: 6392)
Checks supported languages
- mode.com (PID: 3332)
- mode.com (PID: 7144)
Starts MODE.COM to configure console settings
- mode.com (PID: 7144)
- mode.com (PID: 3332)
Reads the software policy settings
- slui.exe (PID: 1600)
Checks if a key exists in the options dictionary (POWERSHELL)
- powershell.exe (PID: 684)
Creates files in the program directory
- cmd.exe (PID: 7084)
Create files in a temporary directory
- ClipUp.exe (PID: 5232)
Checks proxy server information
- powershell.exe (PID: 2772)
- powershell.exe (PID: 4016)
Disables trace logs
- powershell.exe (PID: 2772)
- powershell.exe (PID: 4560)
- powershell.exe (PID: 4016)
Remote server returned an error (POWERSHELL)
- powershell.exe (PID: 2772)
- powershell.exe (PID: 4016)
- powershell.exe (PID: 4560)
Creates files or folders in the user directory
- WerFault.exe (PID: 2344)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .bib/bibtex/txt | | | BibTeX references (100) |
|---|
Total processes
479
Monitored processes
335
Malicious processes
5
Suspicious processes
9
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 232 | "C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe" -Version 5.1 -s -NoLogo -NoProfile | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows PowerShell Exit code: 4294967295 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 300 | reg query HKLM\SYSTEM\CurrentControlSet\Services\wuauserv /v ObjectName | C:\Windows\System32\reg.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Registry Console Tool Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 536 | reg query "HKU\S-1-5-20\Software\Microsoft\Windows NT\CurrentVersion" | C:\Windows\System32\reg.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Registry Console Tool Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 616 | find /i "0x1" | C:\Windows\System32\find.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Find String (grep) Utility Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 632 | find /i "RUNNING" | C:\Windows\System32\find.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Find String (grep) Utility Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 684 | wmic path SoftwareLicensingProduct where (ApplicationID='55c92734-d682-4d71-983e-d6ec3f16059f' AND LicenseDependsOn is NULL AND PartialProductKey IS NOT NULL) get LicenseFamily /VALUE | C:\Windows\System32\wbem\WMIC.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: WMI Commandline Utility Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 684 | powershell.exe "(Get-ScheduledTask -TaskName 'SvcRestartTask' -TaskPath '\Microsoft\Windows\SoftwareProtectionPlatform\').State" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows PowerShell Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 704 | "C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe" -Version 5.1 -s -NoLogo -NoProfile | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows PowerShell Exit code: 4294967295 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 720 | reg query HKLM\SYSTEM\CurrentControlSet\Services\wlidsvc /v Type | C:\Windows\System32\reg.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Registry Console Tool Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 728 | reg query HKLM\SYSTEM\CurrentControlSet\Services\wlidsvc /v ErrorControl | C:\Windows\System32\reg.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Registry Console Tool Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
180 956
Read events
180 878
Write events
66
Delete events
12
Modification events
| (PID) Process: | (5280) notepad.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\BagMRU |
| Operation: | write | Name: | NodeSlots |
Value: 02020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202 | |||
| (PID) Process: | (5280) notepad.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\BagMRU |
| Operation: | write | Name: | MRUListEx |
Value: 04000000030000000E00000000000000100000000F0000000C0000000D0000000B000000050000000A000000090000000800000001000000070000000600000002000000FFFFFFFF | |||
| (PID) Process: | (5280) notepad.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\BagMRU\4 |
| Operation: | write | Name: | MRUListEx |
Value: 040000000000000005000000020000000100000003000000FFFFFFFF | |||
| (PID) Process: | (5280) notepad.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\Bags\119\Shell |
| Operation: | write | Name: | SniffedFolderType |
Value: Documents | |||
| (PID) Process: | (5280) notepad.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer |
| Operation: | write | Name: | GlobalAssocChangedCounter |
Value: 114 | |||
| (PID) Process: | (5280) notepad.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\OneDrive\Accounts |
| Operation: | write | Name: | LastUpdate |
Value: 06B0FF6700000000 | |||
| (PID) Process: | (5280) notepad.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\ComDlg32\OpenSavePidlMRU\bat |
| Operation: | delete value | Name: | MRUList |
Value: | |||
| (PID) Process: | (5280) notepad.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\ComDlg32\OpenSavePidlMRU\bat |
| Operation: | write | Name: | 0 |
Value: 14001F50E04FD020EA3A6910A2D808002B30309D14002E80922B16D365937A46956B92703ACA08AF6E003200000000000000000080004D41535F41494F2E636D642E62617400500009000400EFBE00000000000000002E00000000000000000000000000000000000000000000000000000000004D00410053005F00410049004F002E0063006D0064002E0062006100740000001E000000 | |||
| (PID) Process: | (5280) notepad.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\ComDlg32\OpenSavePidlMRU\bat |
| Operation: | write | Name: | MRUListEx |
Value: 00000000FFFFFFFF | |||
| (PID) Process: | (5280) notepad.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\ComDlg32\OpenSavePidlMRU\* |
| Operation: | write | Name: | 8 |
Value: 14001F50E04FD020EA3A6910A2D808002B30309D14002E80922B16D365937A46956B92703ACA08AF6E003200000000000000000080004D41535F41494F2E636D642E62617400500009000400EFBE00000000000000002E00000000000000000000000000000000000000000000000000000000004D00410053005F00410049004F002E0063006D0064002E0062006100740000001E000000 | |||
Executable files
0
Suspicious files
4
Text files
79
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2644 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_eoqrx0md.hwv.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 6740 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_s5h5lepp.2n4.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 2564 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_x0qlxtrm.p4s.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 6740 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_jwzqptxr.xef.psm1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 1096 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_qiho1cxz.xis.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 7148 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_makajk2z.5hr.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 2644 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_vw1mcly5.13i.psm1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 2192 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_yhvkhuxv.n1n.psm1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 960 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_3oot0jrg.n3j.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 5984 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_y4xcnzaq.0k3.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
4
TCP/UDP connections
27
DNS requests
22
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2104 | svchost.exe | GET | 200 | 23.48.23.160:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
6544 | svchost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
6808 | SIHClient.exe | GET | 200 | 2.23.246.101:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
6808 | SIHClient.exe | GET | 200 | 2.23.246.101:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 51.124.78.146:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
2104 | svchost.exe | 23.48.23.160:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
3216 | svchost.exe | 172.211.123.250:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
6544 | svchost.exe | 40.126.32.138:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
6544 | svchost.exe | 2.17.190.73:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
2104 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
6808 | SIHClient.exe | 172.202.163.200:443 | slscr.update.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | GB | whitelisted |
6808 | SIHClient.exe | 2.23.246.101:80 | www.microsoft.com | Ooredoo Q.S.C. | QA | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
crl.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
activated.win |
| unknown |