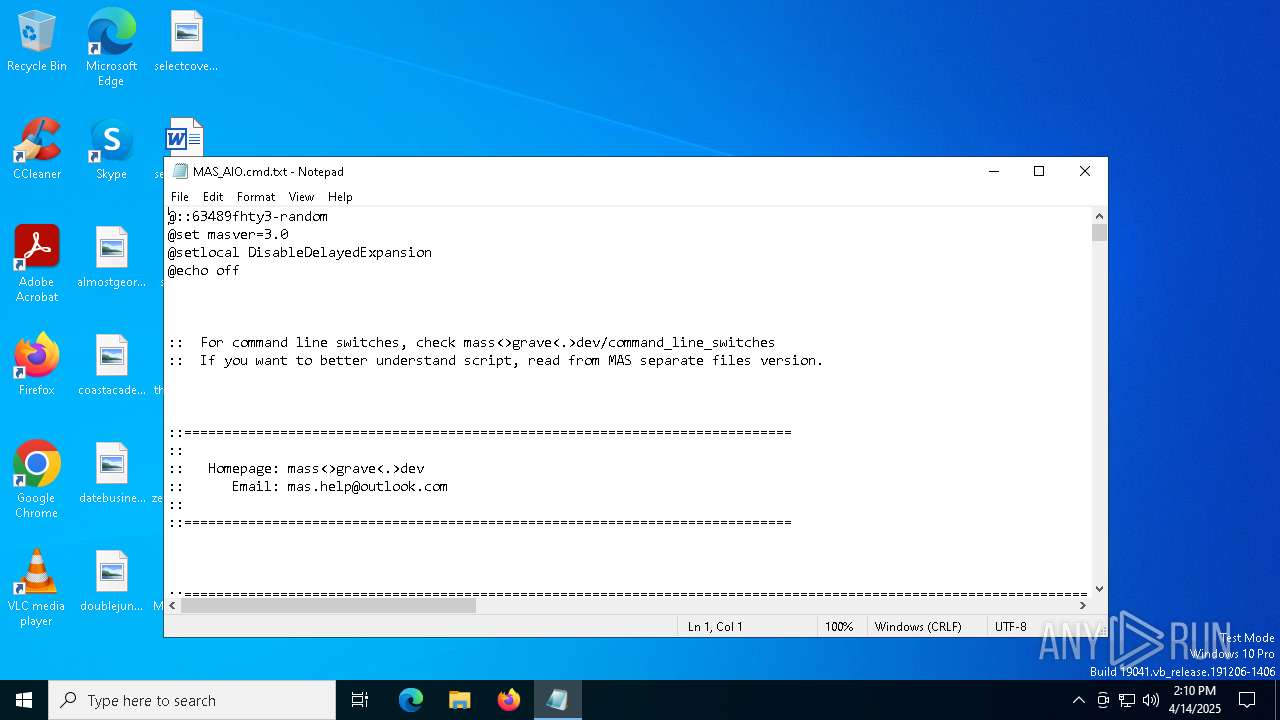
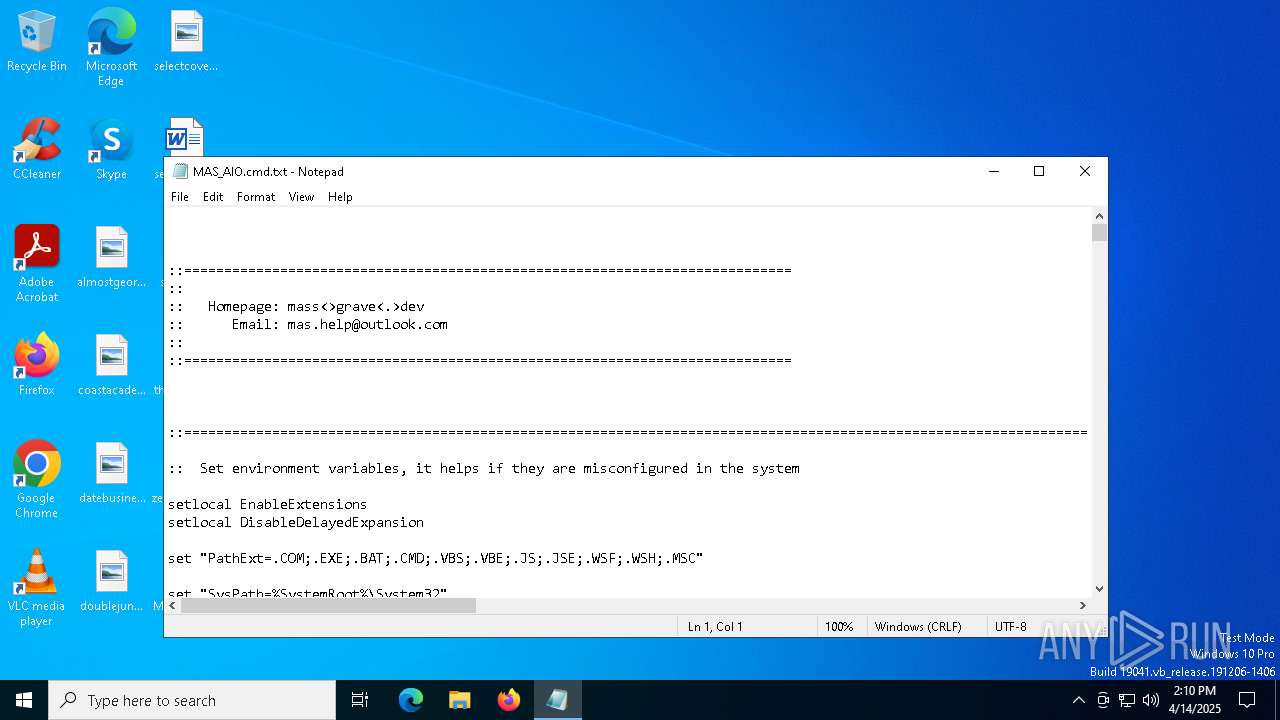
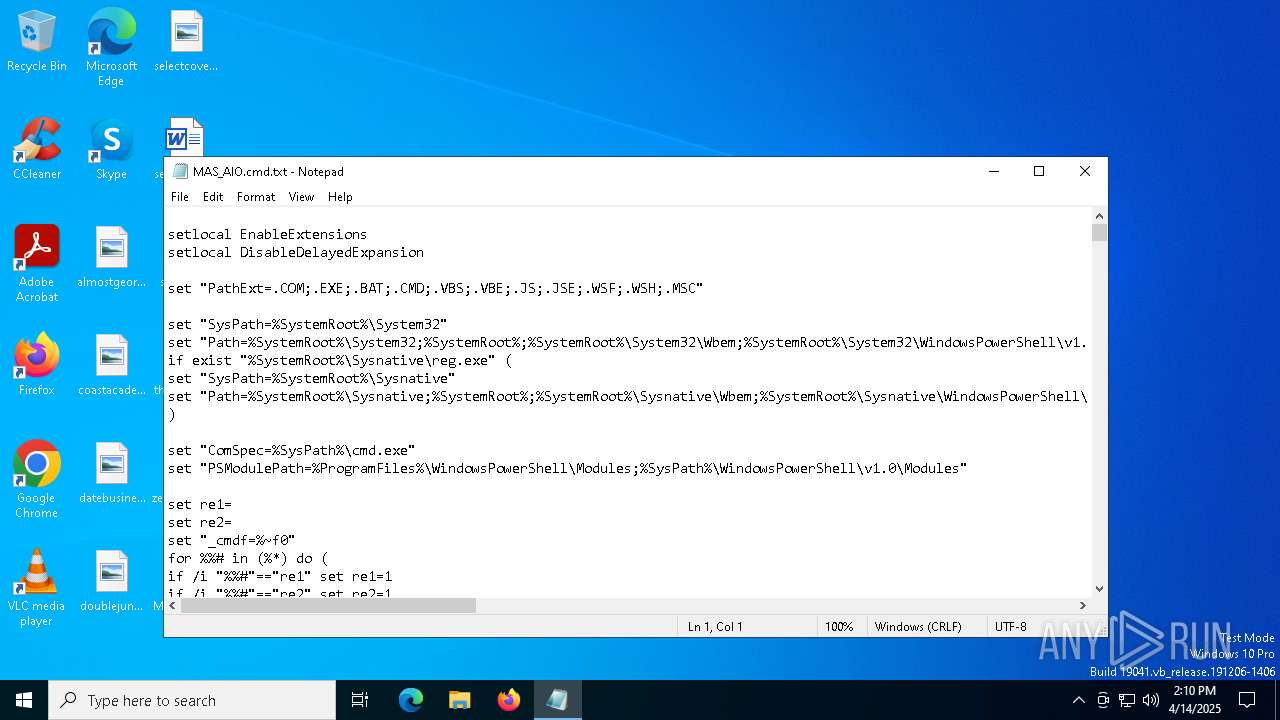
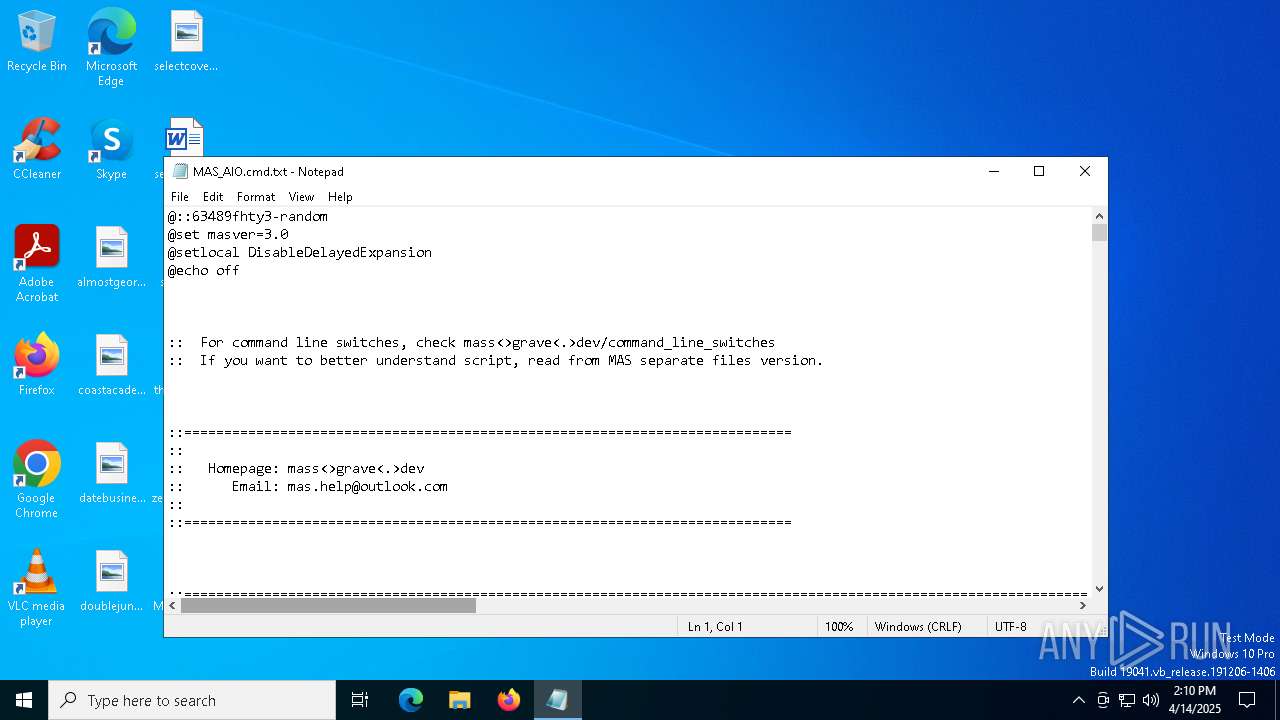
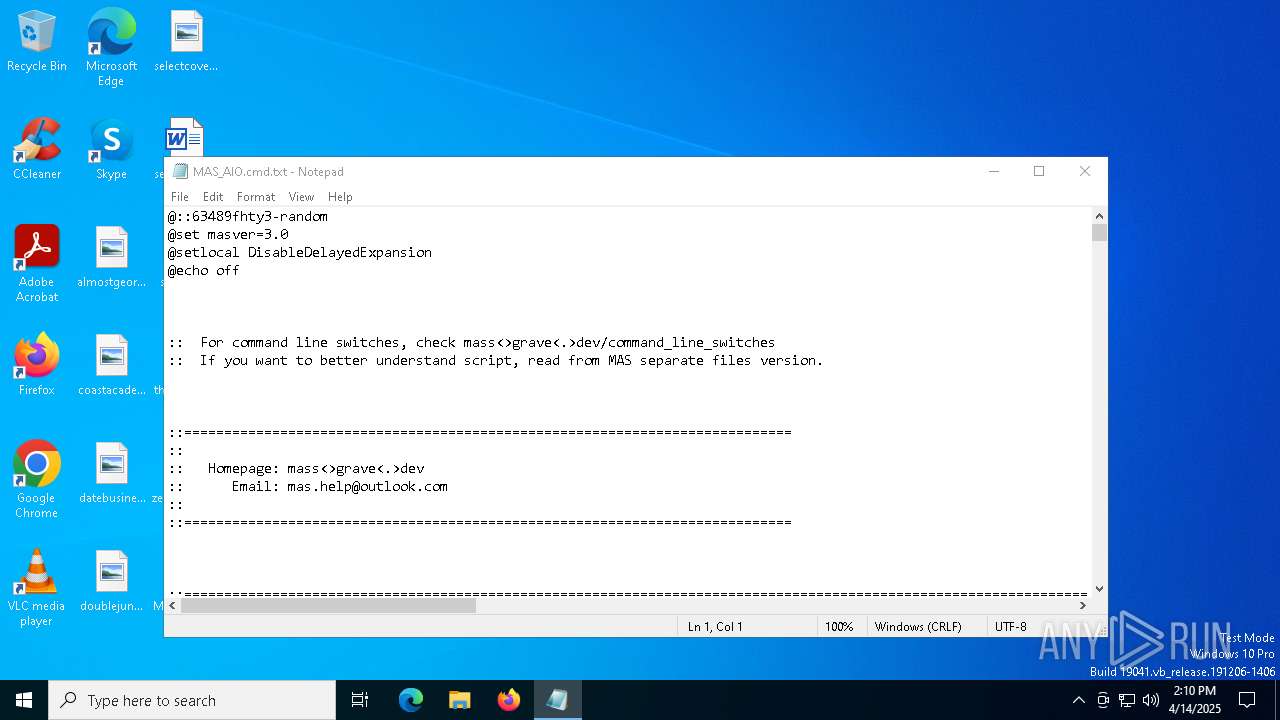
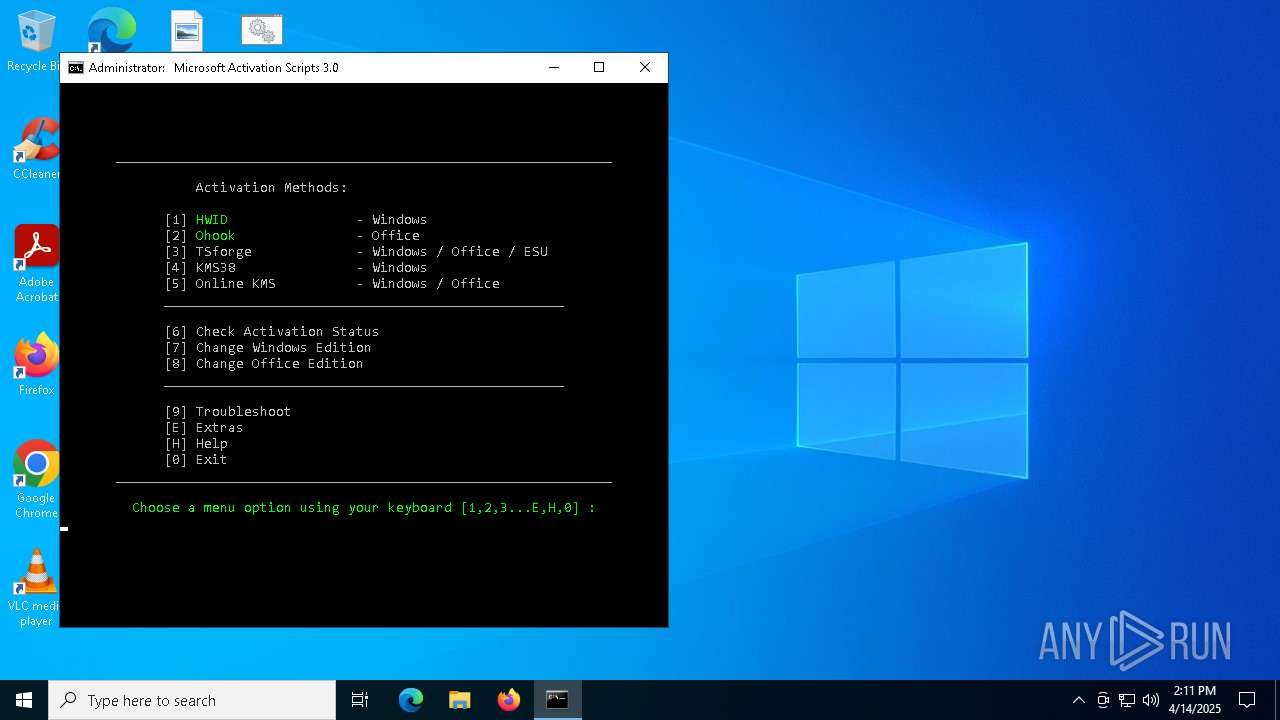
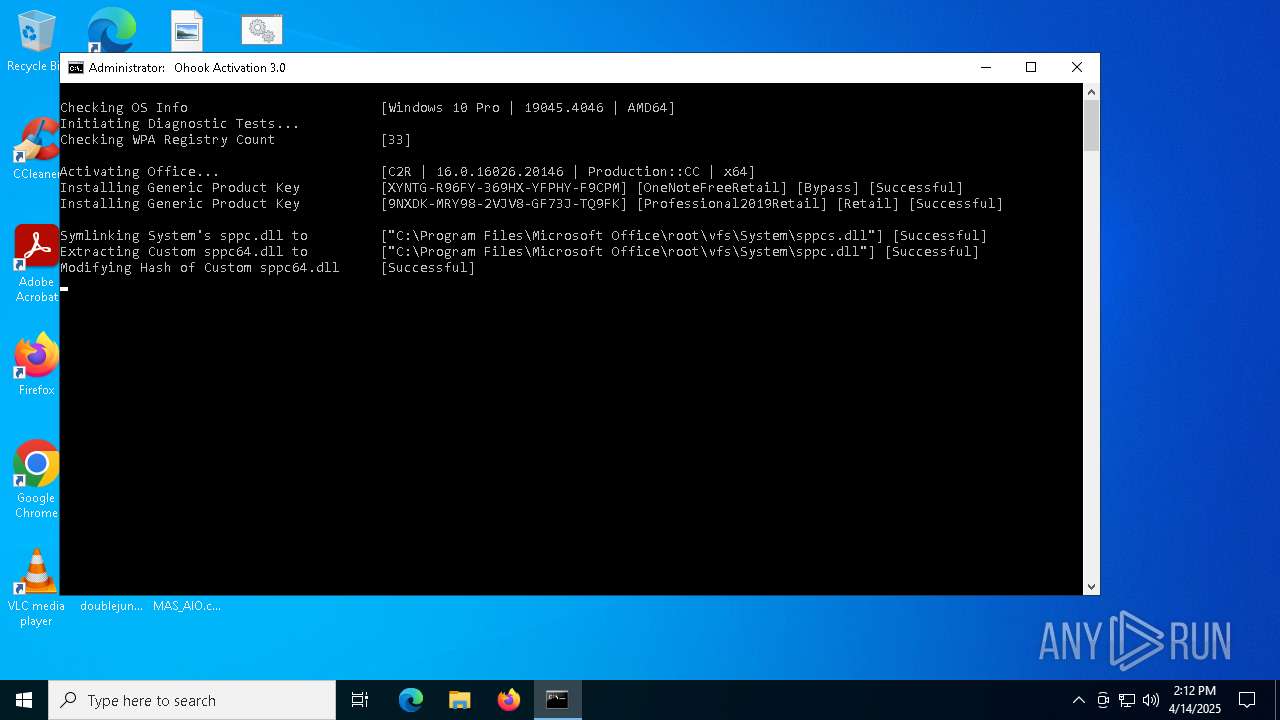
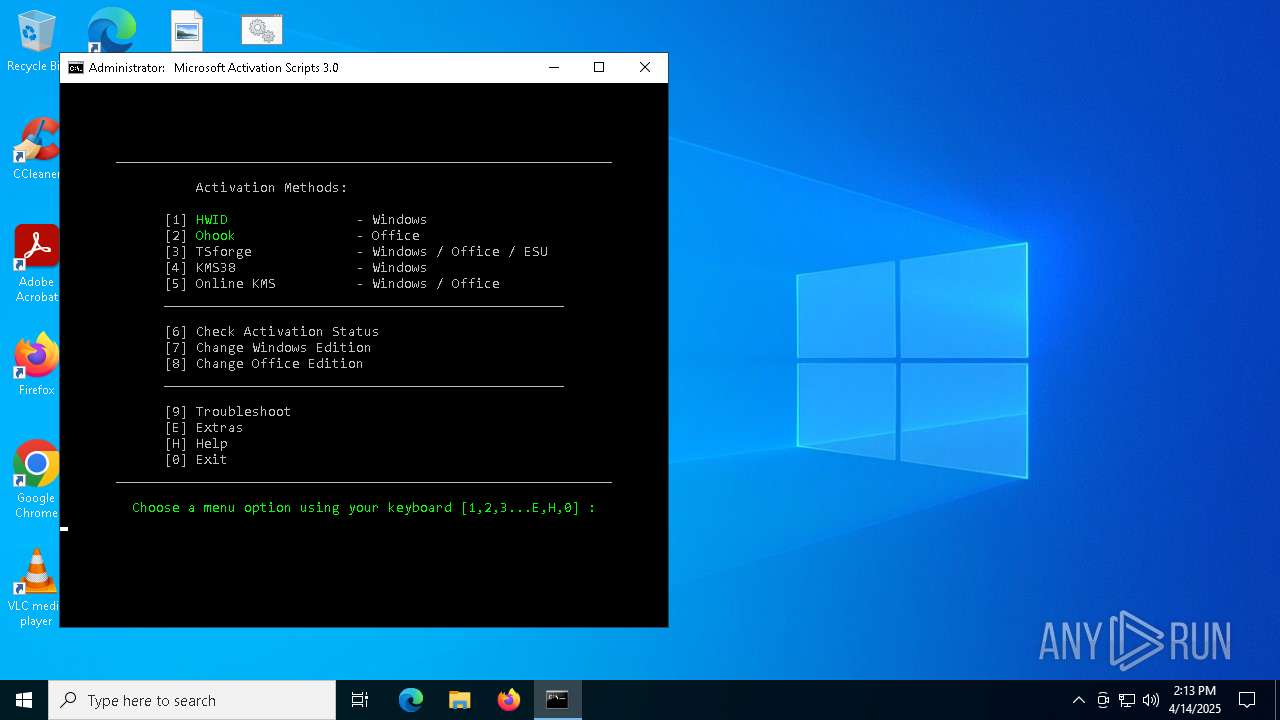
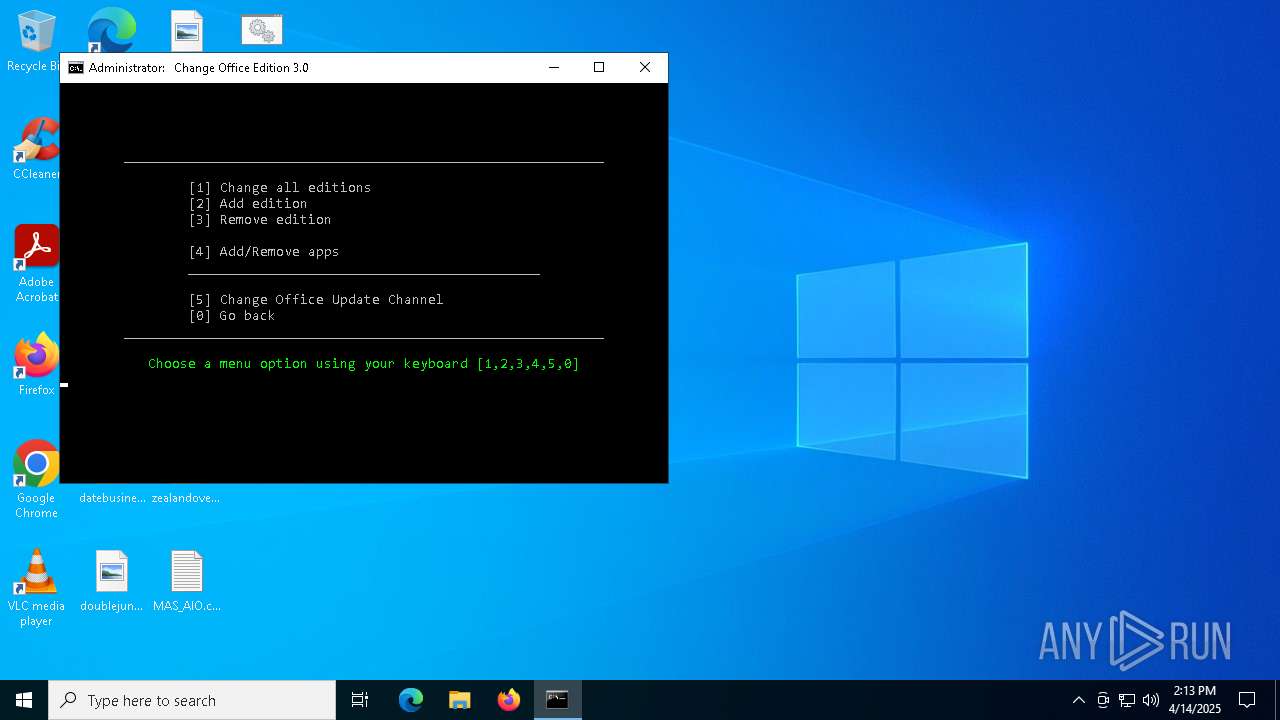
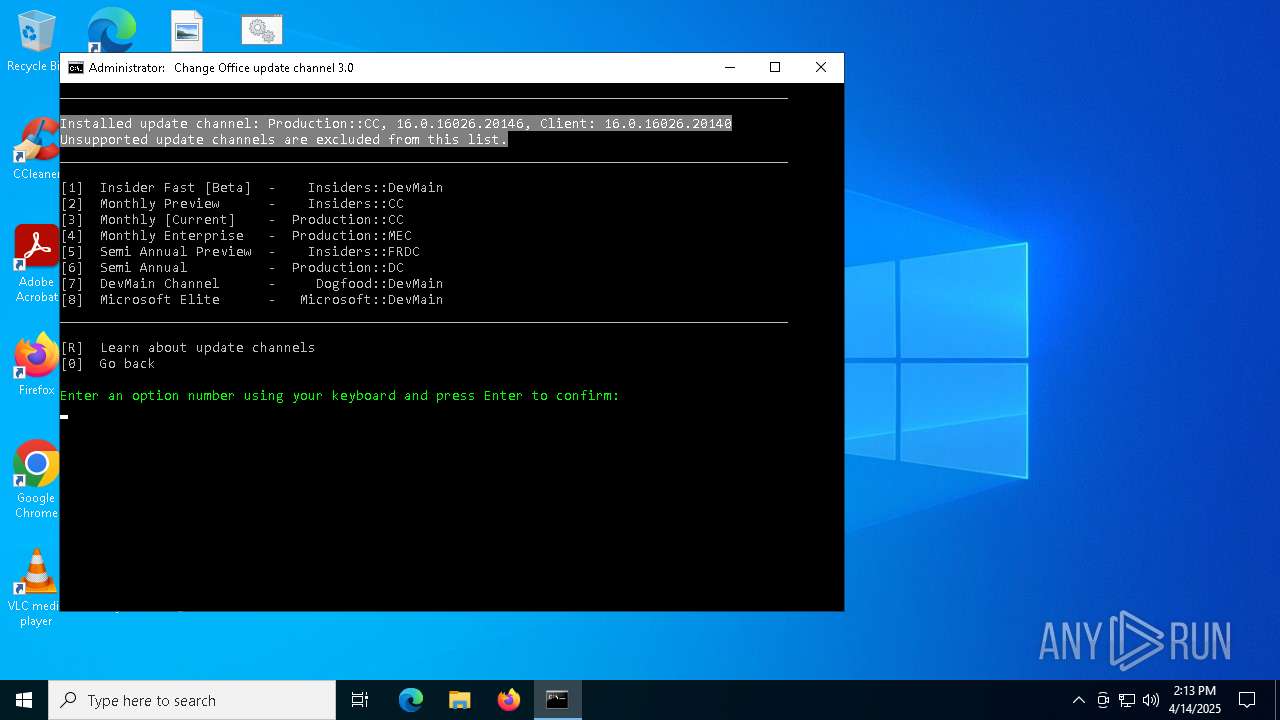
| File name: | MAS_AIO.cmd |
| Full analysis: | https://app.any.run/tasks/71c87a5e-eb3e-4555-86bf-73508128a2f2 |
| Verdict: | Malicious activity |
| Analysis date: | April 14, 2025, 14:09:56 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Indicators: | |
| MIME: | text/plain |
| File info: | ASCII text, with very long lines (348), with CRLF line terminators |
| MD5: | 792AA716B87B5B6591B43B6FC8C64CE4 |
| SHA1: | 0734B56937F4028C7A6AFC20AB4F3351DC9CD7B6 |
| SHA256: | 919F17B46BF62169E8811201F75EFDF1D5C1504321B78A7B0FB47C335ECBC1B0 |
| SSDEEP: | 6144:ToIjH+imAc5g+9YCMD0a9g7nc/4IsK0ykpBwuI:ToIjHOAWYCMDF0c/psK0ykpBm |
MALICIOUS
No malicious indicators.SUSPICIOUS
Windows service management via SC.EXE
- sc.exe (PID: 6620)
- sc.exe (PID: 7676)
- sc.exe (PID: 8148)
- sc.exe (PID: 4408)
- sc.exe (PID: 7440)
- sc.exe (PID: 7796)
- sc.exe (PID: 7760)
- sc.exe (PID: 7284)
- sc.exe (PID: 6300)
- sc.exe (PID: 7148)
- sc.exe (PID: 680)
- sc.exe (PID: 6240)
- sc.exe (PID: 5360)
- sc.exe (PID: 7972)
- sc.exe (PID: 5384)
- sc.exe (PID: 8028)
- sc.exe (PID: 4424)
- sc.exe (PID: 6640)
- sc.exe (PID: 4408)
- sc.exe (PID: 2772)
Starts SC.EXE for service management
- cmd.exe (PID: 456)
- cmd.exe (PID: 7548)
- cmd.exe (PID: 7516)
Using 'findstr.exe' to search for text patterns in files and output
- cmd.exe (PID: 456)
- cmd.exe (PID: 7548)
- cmd.exe (PID: 7880)
- cmd.exe (PID: 7516)
- cmd.exe (PID: 4208)
- cmd.exe (PID: 864)
- cmd.exe (PID: 6700)
- cmd.exe (PID: 7768)
Application launched itself
- cmd.exe (PID: 456)
- cmd.exe (PID: 4988)
- cmd.exe (PID: 7548)
- cmd.exe (PID: 7796)
- cmd.exe (PID: 7516)
- cmd.exe (PID: 8180)
- powershell.exe (PID: 6272)
- powershell.exe (PID: 5116)
Starts CMD.EXE for commands execution
- cmd.exe (PID: 456)
- cmd.exe (PID: 4988)
- powershell.exe (PID: 2852)
- cmd.exe (PID: 7548)
- cmd.exe (PID: 7796)
- cmd.exe (PID: 8180)
- cmd.exe (PID: 7516)
- powershell.exe (PID: 3300)
Executing commands from ".cmd" file
- cmd.exe (PID: 456)
- powershell.exe (PID: 2852)
- cmd.exe (PID: 7548)
- powershell.exe (PID: 3300)
- cmd.exe (PID: 7516)
Starts POWERSHELL.EXE for commands execution
- cmd.exe (PID: 2088)
- cmd.exe (PID: 456)
- cmd.exe (PID: 3676)
- cmd.exe (PID: 7548)
- cmd.exe (PID: 7956)
- cmd.exe (PID: 7516)
- cmd.exe (PID: 6044)
- powershell.exe (PID: 6272)
- cmd.exe (PID: 2984)
- cmd.exe (PID: 6044)
- cmd.exe (PID: 4880)
- cmd.exe (PID: 444)
- powershell.exe (PID: 5116)
Probably obfuscated PowerShell command line is found
- cmd.exe (PID: 2088)
- cmd.exe (PID: 3676)
- cmd.exe (PID: 7956)
- cmd.exe (PID: 7516)
- cmd.exe (PID: 2984)
- cmd.exe (PID: 444)
Possibly malicious use of IEX has been detected
- cmd.exe (PID: 2088)
- cmd.exe (PID: 3676)
- cmd.exe (PID: 7956)
- cmd.exe (PID: 7516)
- cmd.exe (PID: 2984)
Gets content of a file (POWERSHELL)
- powershell.exe (PID: 516)
- powershell.exe (PID: 5384)
- powershell.exe (PID: 2392)
- powershell.exe (PID: 5452)
- powershell.exe (PID: 1512)
- powershell.exe (PID: 2776)
Uses base64 encoding (POWERSHELL)
- powershell.exe (PID: 516)
- powershell.exe (PID: 5384)
- powershell.exe (PID: 2392)
- powershell.exe (PID: 5452)
- powershell.exe (PID: 1512)
- powershell.exe (PID: 2776)
Uses sleep to delay execution (POWERSHELL)
- powershell.exe (PID: 516)
- powershell.exe (PID: 5384)
- powershell.exe (PID: 2392)
- powershell.exe (PID: 5452)
- powershell.exe (PID: 1512)
- powershell.exe (PID: 2776)
Checks a user's role membership (POWERSHELL)
- powershell.exe (PID: 5452)
The process creates files with name similar to system file names
- wermgr.exe (PID: 7204)
Get information on the list of running processes
- cmd.exe (PID: 7516)
- cmd.exe (PID: 7880)
Hides command output
- cmd.exe (PID: 7880)
- cmd.exe (PID: 2984)
- cmd.exe (PID: 4880)
- cmd.exe (PID: 7348)
- cmd.exe (PID: 3968)
- cmd.exe (PID: 6044)
- cmd.exe (PID: 7972)
- cmd.exe (PID: 7792)
- cmd.exe (PID: 7848)
- cmd.exe (PID: 7880)
- cmd.exe (PID: 4268)
- cmd.exe (PID: 3008)
- cmd.exe (PID: 6940)
- cmd.exe (PID: 4208)
- cmd.exe (PID: 3396)
- cmd.exe (PID: 1004)
- cmd.exe (PID: 7608)
- cmd.exe (PID: 2568)
- cmd.exe (PID: 6668)
- cmd.exe (PID: 7336)
- cmd.exe (PID: 7552)
- cmd.exe (PID: 1096)
- cmd.exe (PID: 4464)
- cmd.exe (PID: 7636)
- cmd.exe (PID: 6824)
- cmd.exe (PID: 444)
- cmd.exe (PID: 7876)
- cmd.exe (PID: 7892)
- cmd.exe (PID: 7864)
- cmd.exe (PID: 2420)
- cmd.exe (PID: 864)
- cmd.exe (PID: 1004)
- cmd.exe (PID: 6192)
- cmd.exe (PID: 6964)
- cmd.exe (PID: 5204)
- cmd.exe (PID: 7328)
- cmd.exe (PID: 456)
- cmd.exe (PID: 5548)
- cmd.exe (PID: 7228)
- cmd.exe (PID: 4024)
- cmd.exe (PID: 7740)
- cmd.exe (PID: 7896)
- cmd.exe (PID: 7708)
- cmd.exe (PID: 7100)
- cmd.exe (PID: 3028)
- cmd.exe (PID: 8116)
- cmd.exe (PID: 1088)
- cmd.exe (PID: 6752)
- cmd.exe (PID: 7592)
- cmd.exe (PID: 5556)
- cmd.exe (PID: 6032)
- cmd.exe (PID: 5352)
- cmd.exe (PID: 6700)
- cmd.exe (PID: 7768)
- cmd.exe (PID: 2420)
- cmd.exe (PID: 5260)
- cmd.exe (PID: 5384)
Uses WMIC.EXE to obtain computer system information
- cmd.exe (PID: 7376)
- cmd.exe (PID: 7516)
- cmd.exe (PID: 6392)
The process bypasses the loading of PowerShell profile settings
- powershell.exe (PID: 6272)
- powershell.exe (PID: 5116)
The process hides Powershell's copyright startup banner
- powershell.exe (PID: 6272)
- powershell.exe (PID: 5116)
Uses REG/REGEDIT.EXE to modify registry
- cmd.exe (PID: 7516)
- cmd.exe (PID: 4208)
Uses WMIC.EXE to obtain Windows Installer data
- cmd.exe (PID: 6940)
- cmd.exe (PID: 3396)
- cmd.exe (PID: 6192)
- cmd.exe (PID: 7100)
Uses WMIC.EXE to obtain service application data
- cmd.exe (PID: 7516)
Writes data into a file (POWERSHELL)
- powershell.exe (PID: 2776)
Executable content was dropped or overwritten
- powershell.exe (PID: 2776)
Returns all items found within a container (POWERSHELL)
- powershell.exe (PID: 5428)
INFO
Reads security settings of Internet Explorer
- notepad.exe (PID: 7448)
- notepad.exe (PID: 8128)
- WMIC.exe (PID: 3968)
- WMIC.exe (PID: 8104)
- WMIC.exe (PID: 6252)
- WMIC.exe (PID: 4212)
- WMIC.exe (PID: 3976)
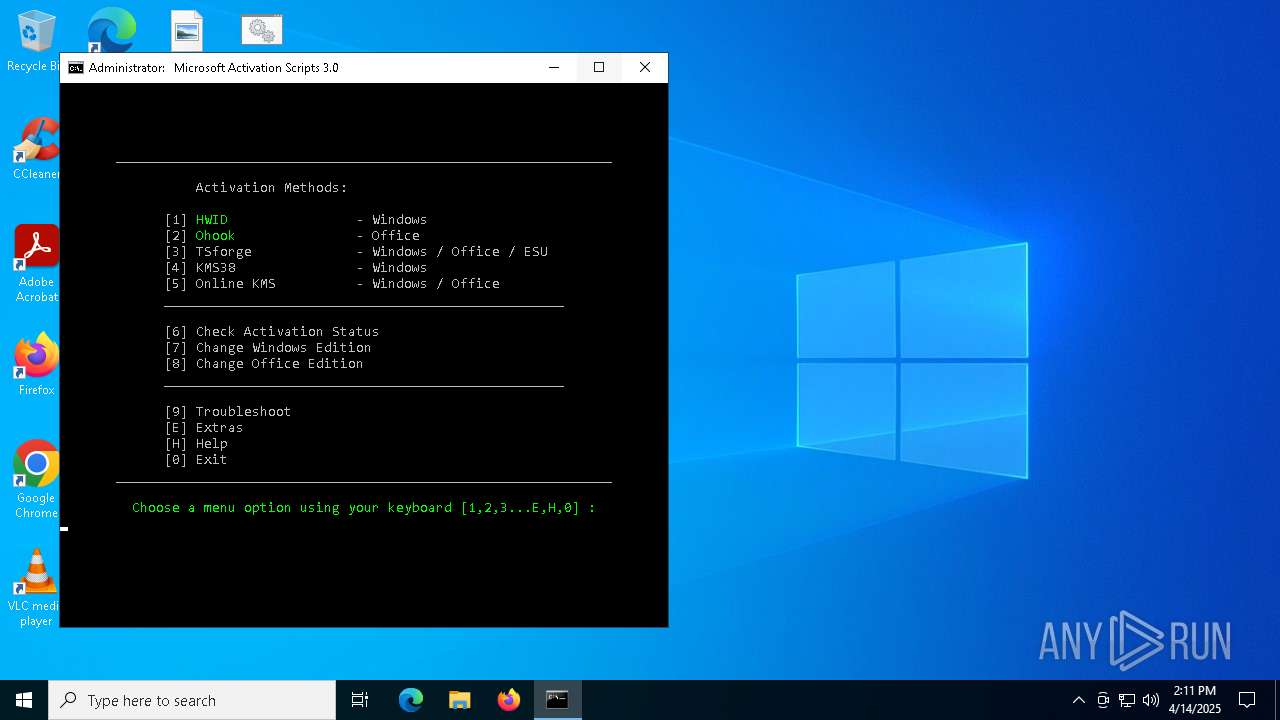
Manual execution by a user
- notepad.exe (PID: 8128)
- cmd.exe (PID: 456)
Checks operating system version
- cmd.exe (PID: 456)
- cmd.exe (PID: 7548)
- cmd.exe (PID: 7516)
Converts byte array into ASCII string (POWERSHELL)
- powershell.exe (PID: 516)
- powershell.exe (PID: 5384)
- powershell.exe (PID: 2392)
- powershell.exe (PID: 5452)
- powershell.exe (PID: 1512)
- powershell.exe (PID: 2776)
Creates a byte array (POWERSHELL)
- powershell.exe (PID: 516)
- powershell.exe (PID: 5384)
- powershell.exe (PID: 2392)
- powershell.exe (PID: 5452)
- powershell.exe (PID: 1512)
- powershell.exe (PID: 2776)
Checks whether the specified file exists (POWERSHELL)
- powershell.exe (PID: 516)
- powershell.exe (PID: 5384)
- powershell.exe (PID: 2392)
- powershell.exe (PID: 5452)
- powershell.exe (PID: 1512)
- powershell.exe (PID: 2776)
Gets a random number, or selects objects randomly from a collection (POWERSHELL)
- powershell.exe (PID: 516)
- powershell.exe (PID: 2392)
- powershell.exe (PID: 5452)
- powershell.exe (PID: 5384)
- powershell.exe (PID: 1512)
- powershell.exe (PID: 2776)
Checks supported languages
- mode.com (PID: 5392)
- mode.com (PID: 5512)
- mode.com (PID: 7668)
- mode.com (PID: 7744)
- mode.com (PID: 2568)
- mode.com (PID: 6852)
Starts MODE.COM to configure console settings
- mode.com (PID: 5392)
- mode.com (PID: 5512)
- mode.com (PID: 7744)
- mode.com (PID: 7668)
- mode.com (PID: 2568)
- mode.com (PID: 6852)
- mode.com (PID: 8128)
- mode.com (PID: 6676)
- mode.com (PID: 8184)
Reads the software policy settings
- slui.exe (PID: 7604)
- wermgr.exe (PID: 7204)
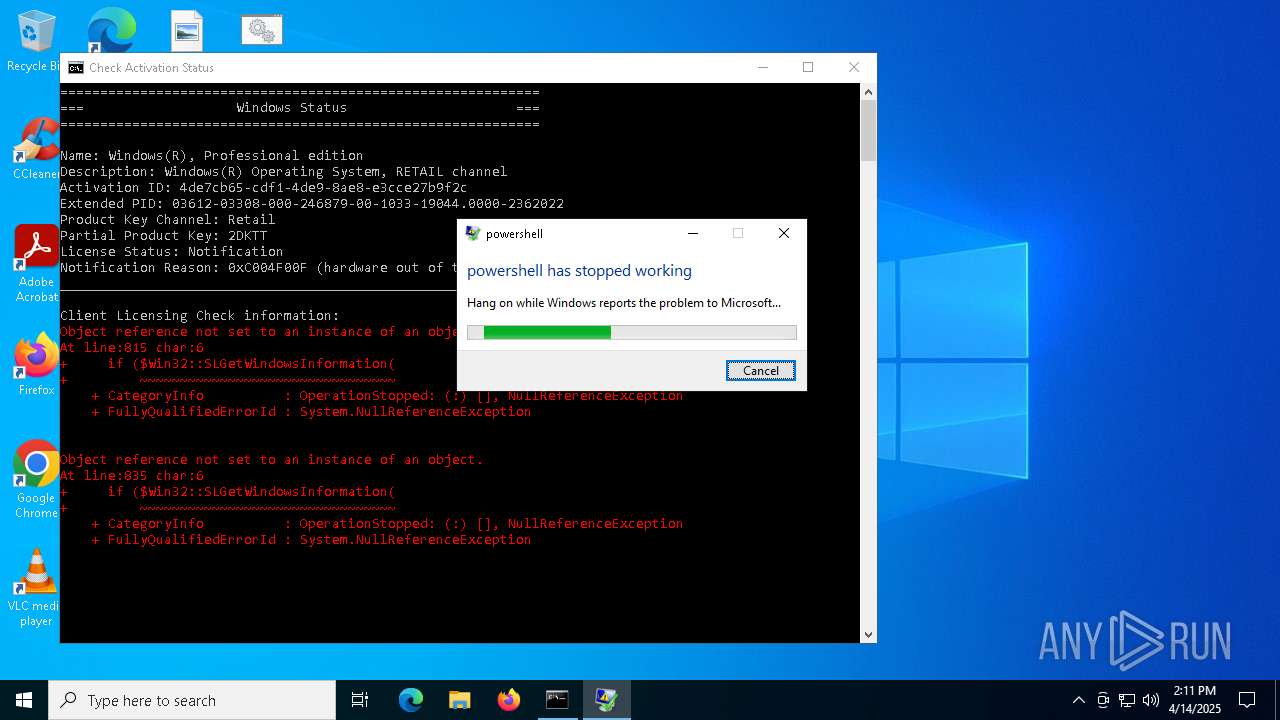
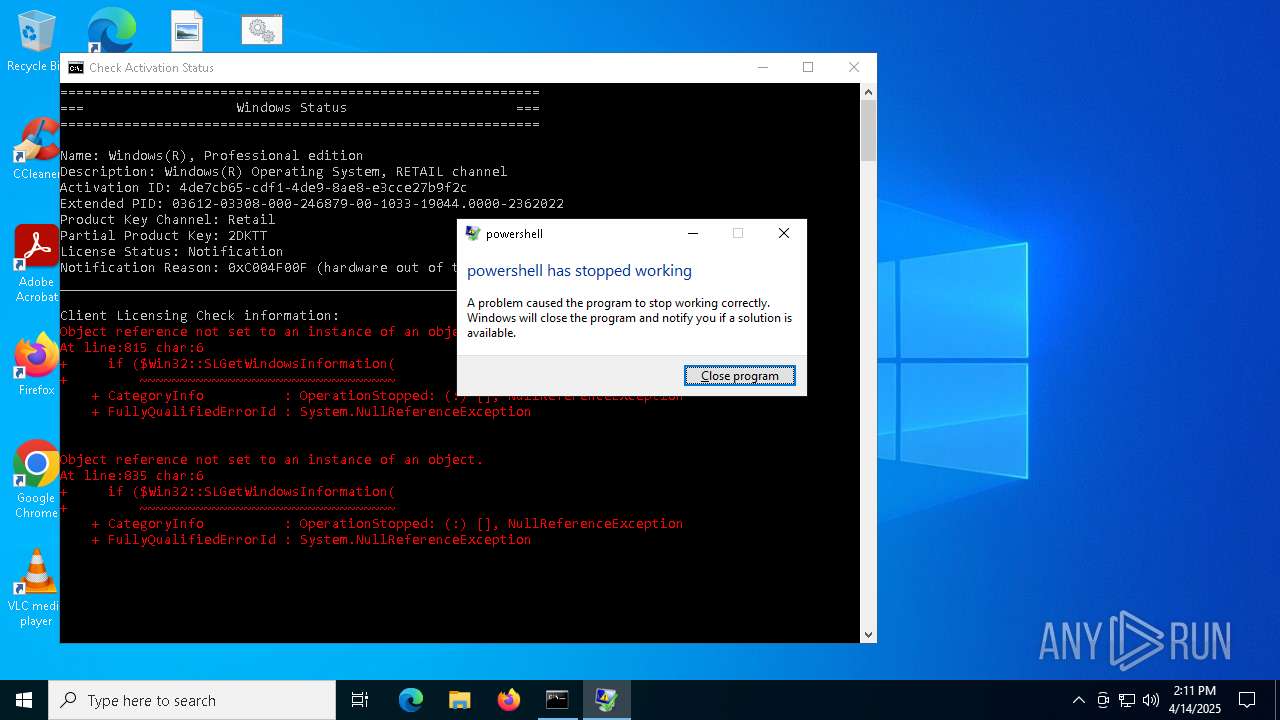
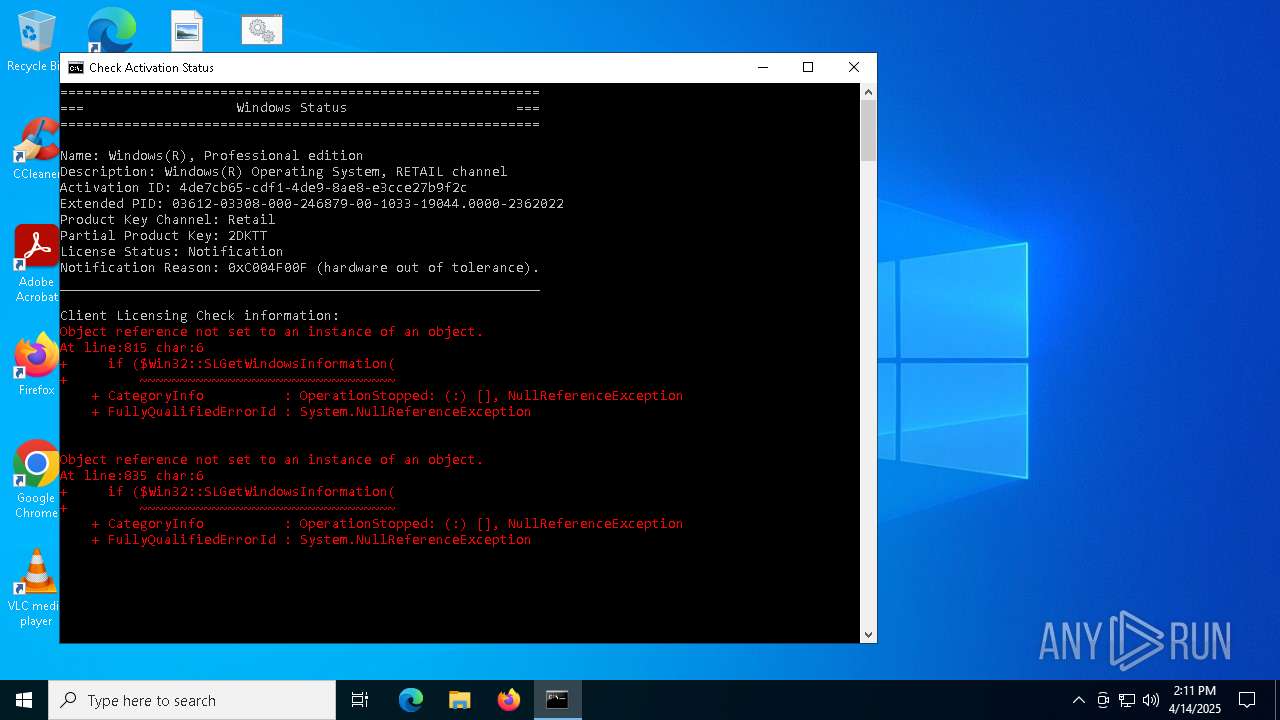
Script raised an exception (POWERSHELL)
- powershell.exe (PID: 5452)
Creates files in the program directory
- powershell.exe (PID: 5452)
Creates files or folders in the user directory
- wermgr.exe (PID: 7204)
Checks proxy server information
- wermgr.exe (PID: 7204)
Checks if a key exists in the options dictionary (POWERSHELL)
- powershell.exe (PID: 2108)
Reads Microsoft Office registry keys
- reg.exe (PID: 7340)
- reg.exe (PID: 8164)
Returns hidden items found within a container (POWERSHELL)
- conhost.exe (PID: 4896)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .bib/bibtex/txt | | | BibTeX references (100) |
|---|
Total processes
599
Monitored processes
467
Malicious processes
6
Suspicious processes
8
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 208 | find /i "True" | C:\Windows\System32\find.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Find String (grep) Utility Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
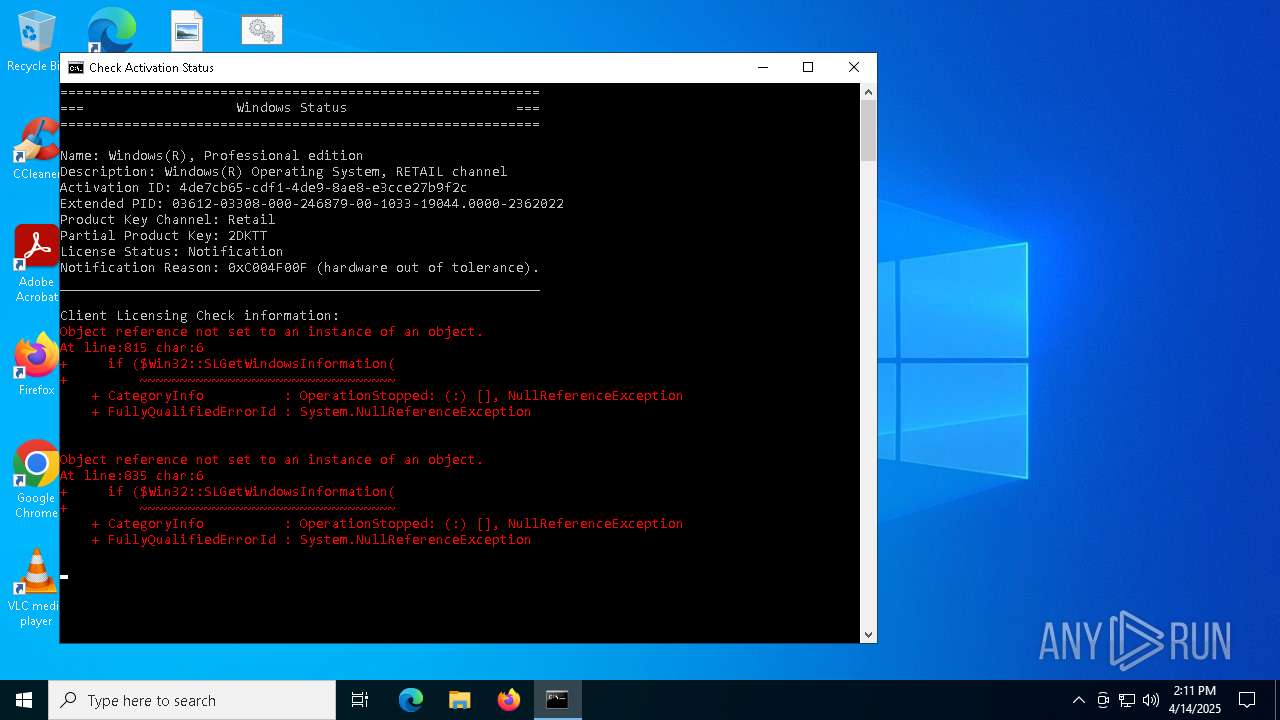
| 444 | powershell.exe "$netServ = (New-Object Security.Principal.SecurityIdentifier('S-1-5-20')).Translate([Security.Principal.NTAccount]).Value; $aclString = Get-Acl 'Registry::HKU\S-1-5-20\Software\Microsoft\Windows NT\CurrentVersion\SoftwareProtectionPlatform\Policies' | Format-List | Out-String; if (-not ($aclString.Contains($netServ + ' Allow FullControl') -or $aclString.Contains('NT SERVICE\sppsvc Allow FullControl')) -or ($aclString.Contains('Deny'))) {Exit 3}" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows PowerShell Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 444 | C:\WINDOWS\System32\cmd.exe /c powershell.exe "$p = 'HKLM:\SOFTWARE\Microsoft\Windows NT\CurrentVersion\ProfileList'; Get-ChildItem $p | ForEach-Object { $pi = (Get-ItemProperty """"$p\$($_.PSChildName)"""").ProfileImagePath; if ($pi -like '*\Users\*' -and (Test-Path """"$pi\NTUSER.DAT"""") -and -not ($_.PSChildName -match '\.bakf7f81a39-5f63-5b42-9efd-1f13b5431005#39;)) { Split-Path $_.PSPath -Leaf } }" 2>nul | C:\Windows\System32\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 456 | C:\WINDOWS\system32\cmd.exe /c ""C:\Users\admin\Desktop\MAS_AIO.cmd" " | C:\Windows\System32\cmd.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 456 | C:\WINDOWS\System32\cmd.exe /S /D /c" echo " OneNoteFreeRetail Professional2019Retail " " | C:\Windows\System32\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 456 | C:\WINDOWS\System32\cmd.exe /c "reg query HKLM\SOFTWARE\Microsoft\Office\ClickToRun\Configuration /v ClientFolder" 2>nul | C:\Windows\System32\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 516 | powershell.exe "$f=[io.file]::ReadAllText('C:\Users\admin\Desktop\MAS_AIO.cmd') -split ':PStest:\s*';iex ($f[1])" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 516 | reg query HKLM\SOFTWARE\Microsoft\Office\ClickToRun\Configuration /v AudienceId | C:\Windows\System32\reg.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Registry Console Tool Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 540 | reg query HKU\S-1-5-21-1693682860-607145093-2874071422-500\Software | C:\Windows\System32\reg.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Registry Console Tool Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 680 | sc start Winmgmt | C:\Windows\System32\sc.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Service Control Manager Configuration Tool Exit code: 1056 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
140 862
Read events
140 786
Write events
63
Delete events
13
Modification events
| (PID) Process: | (8128) notepad.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\BagMRU |
| Operation: | write | Name: | NodeSlots |
Value: 02020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202 | |||
| (PID) Process: | (8128) notepad.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\BagMRU |
| Operation: | write | Name: | MRUListEx |
Value: 04000000030000000E00000000000000100000000F0000000C0000000D0000000B000000050000000A000000090000000800000001000000070000000600000002000000FFFFFFFF | |||
| (PID) Process: | (8128) notepad.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\BagMRU\4 |
| Operation: | write | Name: | MRUListEx |
Value: 010000000000000004000000050000000200000003000000FFFFFFFF | |||
| (PID) Process: | (8128) notepad.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\Bags\34\Shell |
| Operation: | write | Name: | SniffedFolderType |
Value: Generic | |||
| (PID) Process: | (8128) notepad.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer |
| Operation: | write | Name: | GlobalAssocChangedCounter |
Value: 114 | |||
| (PID) Process: | (8128) notepad.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\ComDlg32\OpenSavePidlMRU\cmd |
| Operation: | write | Name: | 0 |
Value: 14001F50E04FD020EA3A6910A2D808002B30309D14002E803ACCBFB42CDB4C42B0297FE99A87C64162003200000000000000000080004D41535F41494F2E636D6400480009000400EFBE00000000000000002E00000000000000000000000000000000000000000000000000000000004D00410053005F00410049004F002E0063006D00640000001A000000 | |||
| (PID) Process: | (8128) notepad.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\ComDlg32\OpenSavePidlMRU\cmd |
| Operation: | write | Name: | MRUListEx |
Value: 00000000FFFFFFFF | |||
| (PID) Process: | (8128) notepad.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\ComDlg32\OpenSavePidlMRU\* |
| Operation: | write | Name: | 8 |
Value: 14001F50E04FD020EA3A6910A2D808002B30309D14002E803ACCBFB42CDB4C42B0297FE99A87C64162003200000000000000000080004D41535F41494F2E636D6400480009000400EFBE00000000000000002E00000000000000000000000000000000000000000000000000000000004D00410053005F00410049004F002E0063006D00640000001A000000 | |||
| (PID) Process: | (8128) notepad.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\ComDlg32\OpenSavePidlMRU\* |
| Operation: | write | Name: | MRUListEx |
Value: 080000000700000006000000050000000400000003000000020000000100000000000000FFFFFFFF | |||
| (PID) Process: | (8128) notepad.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\Modules\NavPane |
| Operation: | write | Name: | ExpandedState |
Value: 12000000160014001F80CB859F6720028040B29B5540CC05AAB60000010000004D0000001C00000031535053A66A63283D95D211B5D600C04FD918D0000000002D00000031535053357EC777E31B5043A48C7563D727776D1100000002000000000B000000FFFF00000000000000000000160014001F60983FFBB4EAC18D42A78AD1F5659CBA930000010000004D0000001C00000031535053A66A63283D95D211B5D600C04FD918D0000000002D00000031535053357EC777E31B5043A48C7563D727776D1100000002000000000B000000FFFF00000000000000000000160014001F7840F05F6481501B109F0800AA002F954E0000010000004D0000001C00000031535053A66A63283D95D211B5D600C04FD918D0000000002D00000031535053357EC777E31B5043A48C7563D727776D1100000002000000000B000000000000000000000000000000160014001F706806EE260AA0D7449371BEB064C986830000010000004D0000001C00000031535053A66A63283D95D211B5D600C04FD918D0000000002D00000031535053357EC777E31B5043A48C7563D727776D1100000002000000000B000000FFFF00000000000000000000160014001F580D1A2CF021BE504388B07367FC96EF3C0000010000004D0000001C00000031535053A66A63283D95D211B5D600C04FD918D0000000002D00000031535053357EC777E31B5043A48C7563D727776D1100000002000000000B000000000000000000000000000000160014001F5425481E03947BC34DB131E946B44C8DD50000010000004D0000001C00000031535053A66A63283D95D211B5D600C04FD918D0000000002D00000031535053357EC777E31B5043A48C7563D727776D1100000002000000000B000000000000000000000000000000160014001F50E04FD020EA3A6910A2D808002B30309D0000010000004D0000001C00000031535053A66A63283D95D211B5D600C04FD918D0000000002D00000031535053357EC777E31B5043A48C7563D727776D1100000002000000000B000000FFFF000000000000000000003C003A001F44471A0359723FA74489C55595FE6B30EE260001002600EFBE1000000034E9025AA9B7D80155EC262BAAB7D8018F3827B5B0B7D80114000000010000004D0000001C00000031535053A66A63283D95D211B5D600C04FD918D0000000002D00000031535053357EC777E31B5043A48C7563D727776D1100000002000000000B000000FFFF000000000000000000003C003A001F42665C8D01334507439B53224DE2ED1FE6260001002600EFBE11000000A1C1E0E0AF27D301F77F6305B0B7D8019F22F307B0B7D80114000000010000004D0000001C00000031535053A66A63283D95D211B5D600C04FD918D0000000002D00000031535053357EC777E31B5043A48C7563D727776D1100000002000000000B000000000000000000000000000000940092003200000080004658D1892000474F4F474C457E312E5A49500000760009000400EFBE4658D1894658D1892E000000F55D05000000090000000000000000000000000000001F47700047006F006F0067006C0065004300680072006F006D00650045006E0074006500720070007200690073006500420075006E0064006C006500360034002E007A006900700000001C000000010000004D0000001C00000031535053A66A63283D95D211B5D600C04FD918D0000000002D00000031535053357EC777E31B5043A48C7563D727776D1100000002000000000B0000000000000000000000000000005C005A00320099030000F2588C582000657874312E7A69700000420009000400EFBEF2588C58F2588C582E000000A70D00000000160000000000000000000000000000003A91F90065007800740031002E007A0069007000000018000000010000004D0000001C00000031535053A66A63283D95D211B5D600C04FD918D0000000002D00000031535053357EC777E31B5043A48C7563D727776D1100000002000000000B00000000000000000000000000000050004E00310000000000F258CE5810006578743100003A0009000400EFBEF258CE58F258CE582E000000DE0200000000170000000000000000000000000000001CB7E9006500780074003100000014000000010000004D0000001C00000031535053A66A63283D95D211B5D600C04FD918D0000000002D00000031535053357EC777E31B5043A48C7563D727776D1100000002000000000B000000FFFF000000000000000000006E006C0032001EEC0500F258826620005052454645527E312E5A49500000500009000400EFBEF2588266F25882662E00000028D4000000001900000000000000000000000000000005A1250050007200650066006500720065006E006300650073002E007A006900700000001C000000010000004D0000001C00000031535053A66A63283D95D211B5D600C04FD918D0000000002D00000031535053357EC777E31B5043A48C7563D727776D1100000002000000000B0000000000000000000000000000005800560032007E0D0000F258866620006578742E7A697000400009000400EFBEF2588666F25886662E0000002AD4000000001E0000000000000000000000000000005498DF006500780074002E007A0069007000000016000000010000004D0000001C00000031535053A66A63283D95D211B5D600C04FD918D0000000002D00000031535053357EC777E31B5043A48C7563D727776D1100000002000000000B00000000000000000000000000000062006000310000000000F2588D6610005052454645527E310000480009000400EFBEF2588D66F2588F662E0000002E2F0100000017000000000000000000000000000000CF57130150007200650066006500720065006E00630065007300000018000000010000004D0000001C00000031535053A66A63283D95D211B5D600C04FD918D0000000002D00000031535053357EC777E31B5043A48C7563D727776D1100000002000000000B0000000000000000000000000000004C004A00310000000000F2589066100065787400380009000400EFBEF2589066F25890662E000000E88D0100000007000000000000000000000000000000DE8B4100650078007400000012000000010000004D0000001C00000031535053A66A63283D95D211B5D600C04FD918D0000000002D00000031535053357EC777E31B5043A48C7563D727776D1100000002000000000B000000000000000000000000000000780076003200C1862C03F258957920004F4D4E495F327E312E5A495000005A0009000400EFBEF258E578F25895792E0000007C600500000039000000000000000000000000000000DE6FED006F006D006E0069005F00320033005F00310030005F0032003000320034005F002E007A006900700000001C000000010000004D0000001C00000031535053A66A63283D95D211B5D600C04FD918D0000000002D00000031535053357EC777E31B5043A48C7563D727776D1100000002000000000B00000000000000000000000000000070006E0032007E0D0000F2587B7920004348524F4D497E312E5A49500000520009000400EFBEF2587B79F2587B792E000000C260050000001800000000000000000000000000000028F586006300680072006F006D00690075006D005F006500780074002E007A006900700000001C000000010000004D0000001C00000031535053A66A63283D95D211B5D600C04FD918D0000000002D00000031535053357EC777E31B5043A48C7563D727776D1100000002000000000B000000000000000000000000000000 | |||
Executable files
2
Suspicious files
3
Text files
58
Unknown types
2
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 516 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_m3p3ttjy.vf0.psm1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 516 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_kkc5buvg.1xh.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 516 | powershell.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\PowerShell\StartupProfileData-NonInteractive | binary | |
MD5:B5EE2DC354D8F3717A57798D4F51F3C9 | SHA256:E4580C642A162A3D5D6CE6F4AA280114CA3B769341DFA7C0798C92259EF0B978 | |||
| 2852 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_yai2ozw0.ack.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 6576 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_35qjaldi.ldj.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 5384 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_0iqgnn4j.mps.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 2852 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_soclaz5i.j4e.psm1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 7204 | wermgr.exe | C:\ProgramData\Microsoft\Windows\WER\ReportArchive\Critical_powershell.exe_4ae1596ba4d7c5a536b79cd636c5f37d83e3f8bd_00000000_956d2ba3-f0b5-4db9-98fe-363e392124de\Report.wer | — | |
MD5:— | SHA256:— | |||
| 6576 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_5svdo5dx.ue3.psm1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 8128 | notepad.exe | C:\Users\admin\Desktop\MAS_AIO.cmd | text | |
MD5:792AA716B87B5B6591B43B6FC8C64CE4 | SHA256:919F17B46BF62169E8811201F75EFDF1D5C1504321B78A7B0FB47C335ECBC1B0 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
6
TCP/UDP connections
24
DNS requests
21
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
6544 | svchost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
8160 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
5496 | MoUsoCoreWorker.exe | GET | 200 | 23.48.23.177:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
8160 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
7204 | wermgr.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
7204 | wermgr.exe | GET | 200 | 23.48.23.140:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
— | — | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5496 | MoUsoCoreWorker.exe | 23.48.23.177:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
3216 | svchost.exe | 172.211.123.250:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
6544 | svchost.exe | 20.190.160.128:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
6544 | svchost.exe | 2.17.190.73:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
2104 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
8160 | SIHClient.exe | 52.149.20.212:443 | slscr.update.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
8160 | SIHClient.exe | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
activated.win |
| unknown |