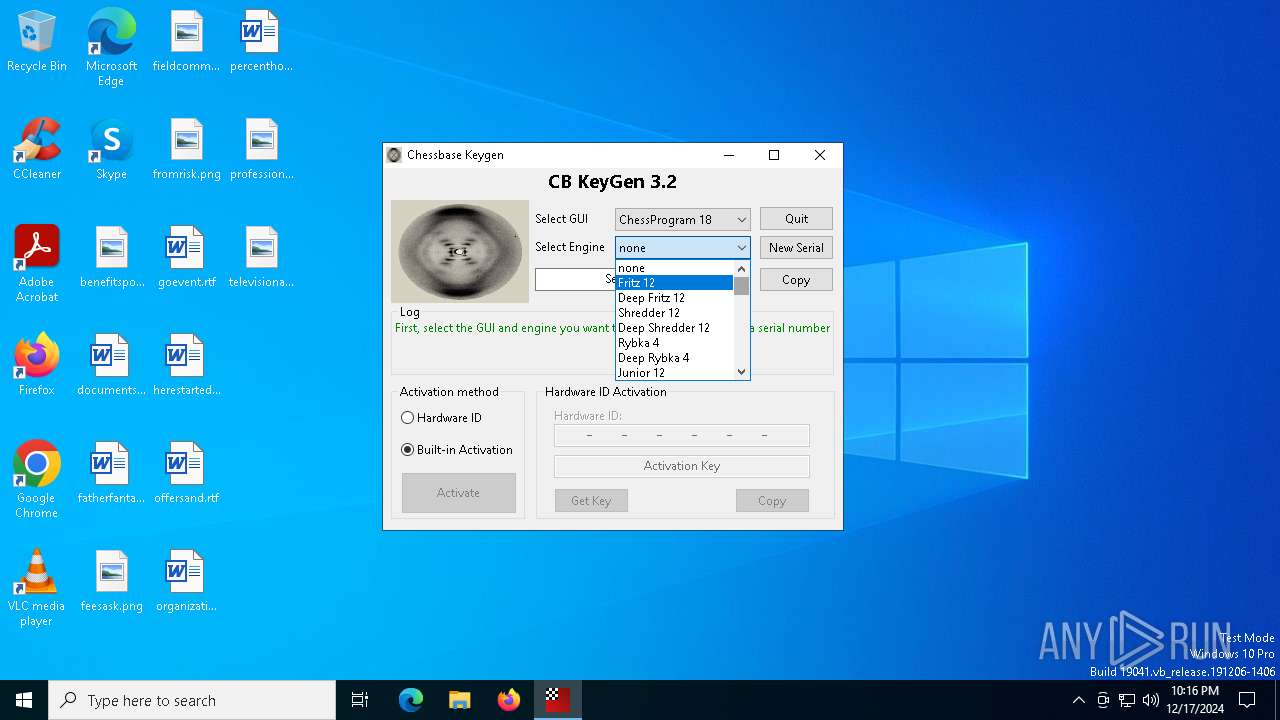
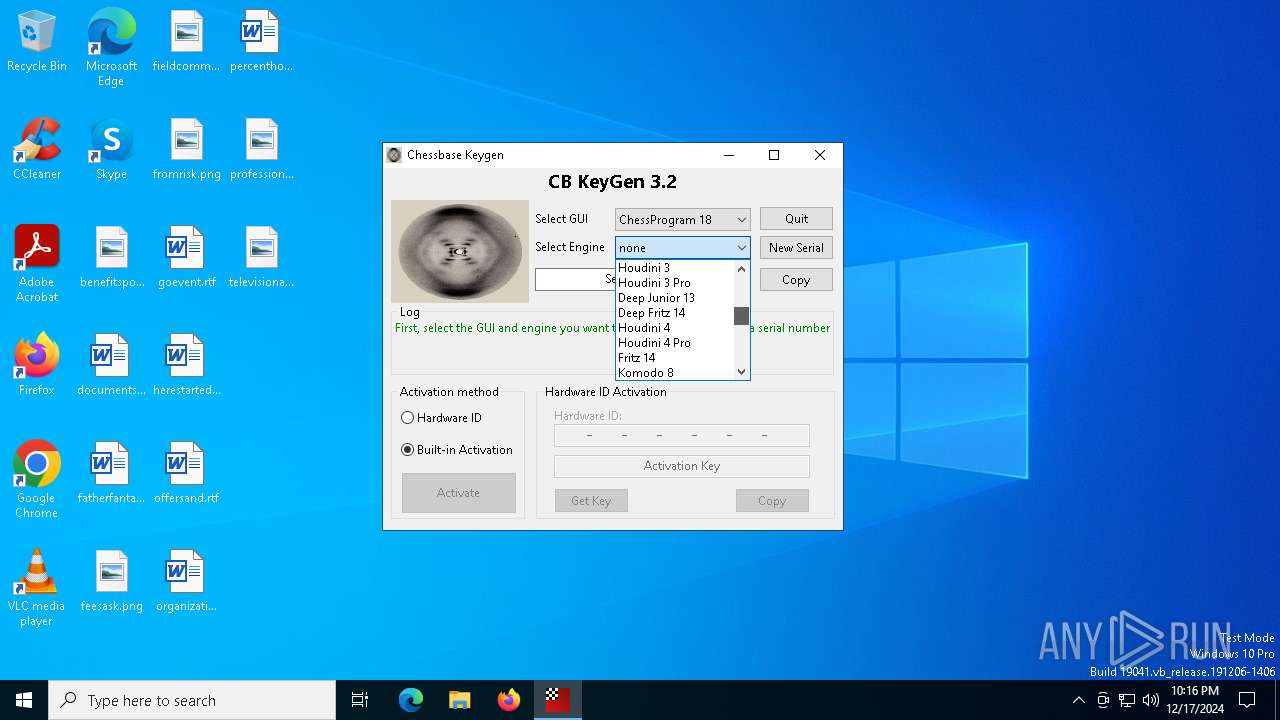
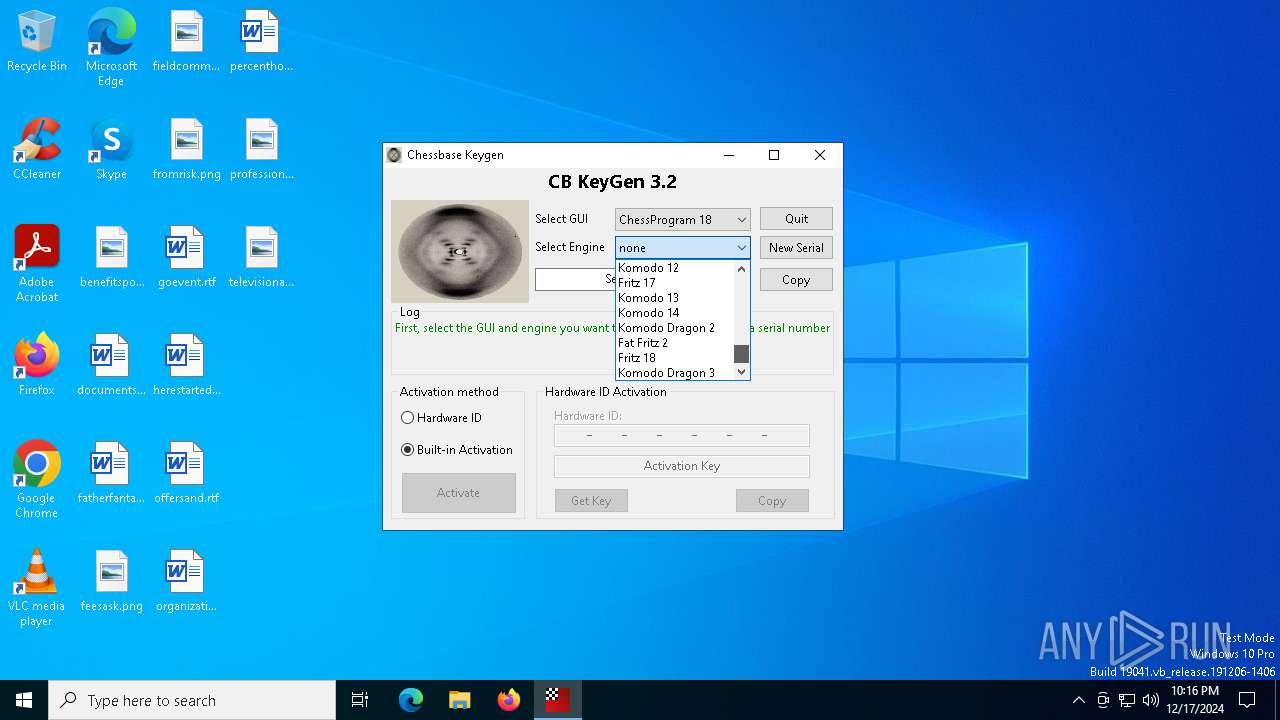
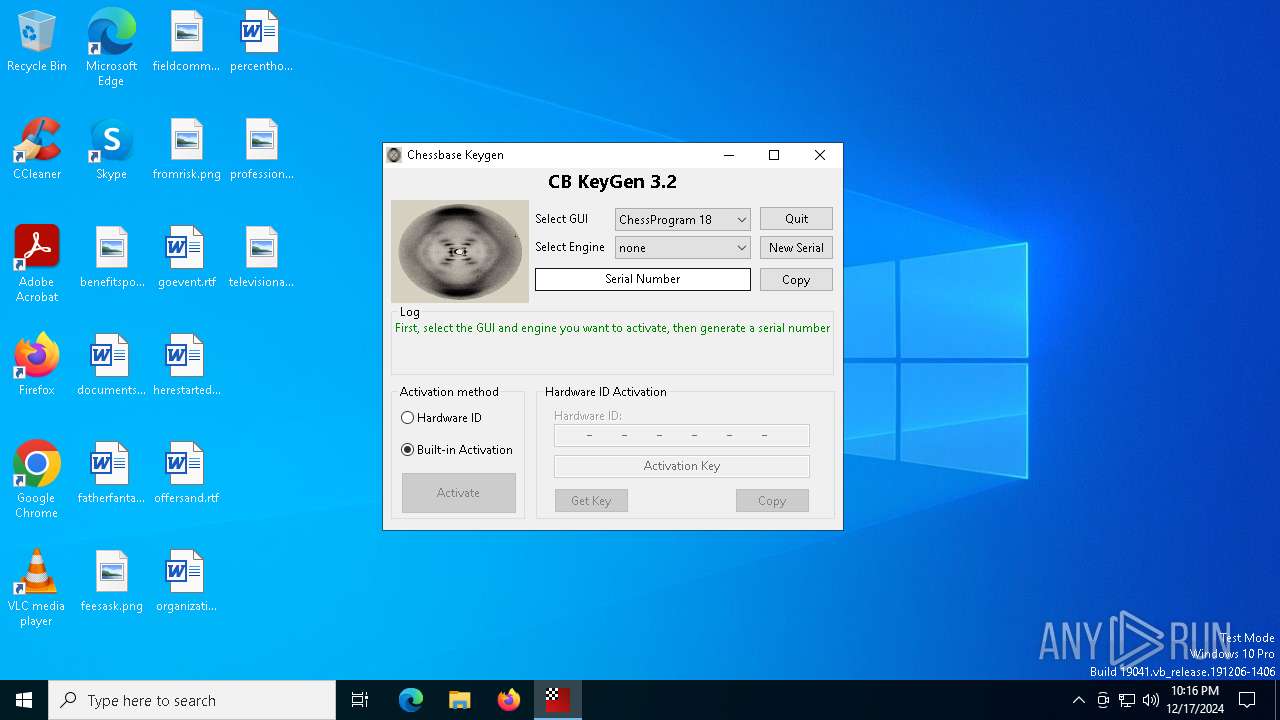
| File name: | CB-Keygen 3.2.exe |
| Full analysis: | https://app.any.run/tasks/fec5ea60-f1ab-43de-8c60-edba88c1f55b |
| Verdict: | Malicious activity |
| Analysis date: | December 17, 2024, 22:15:50 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, 6 sections |
| MD5: | 03EBA8A1A1ADB5337D8B43CCB6B554AF |
| SHA1: | 114A86DEB1F51D36FA1398A16DC974DD98938A8F |
| SHA256: | 916F8DFF7063ED6B1108E19E0F400F0969E7AE80F69F67C266E56F7055B92F2B |
| SSDEEP: | 98304:Oyi35bgowHn0dteCCfLuhhVI+xDCnVR7ToG4a9rIeJAVxqakhi3ZxH/+AA6LA409:qpa+RB/r9n0 |
MALICIOUS
Executing a file with an untrusted certificate
- ChessBaseAdminTool.exe (PID: 4944)
- ChessBaseAdminTool.exe (PID: 4716)
SUSPICIOUS
The process drops C-runtime libraries
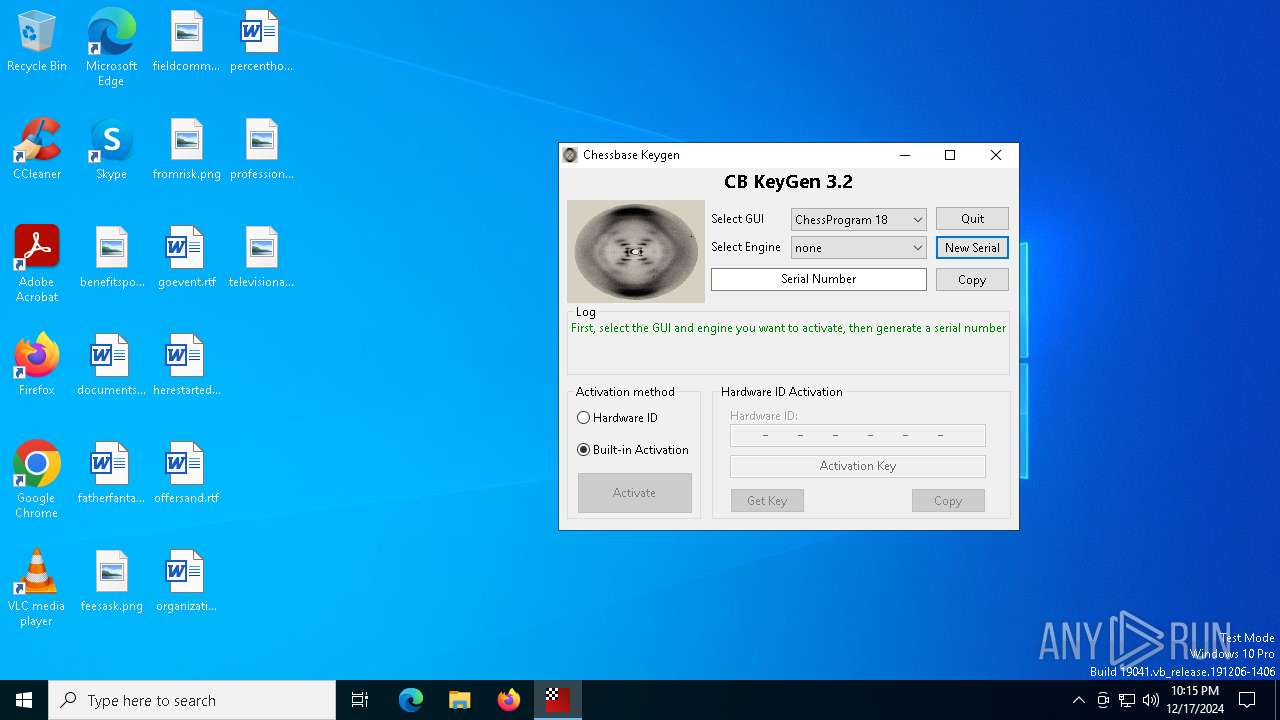
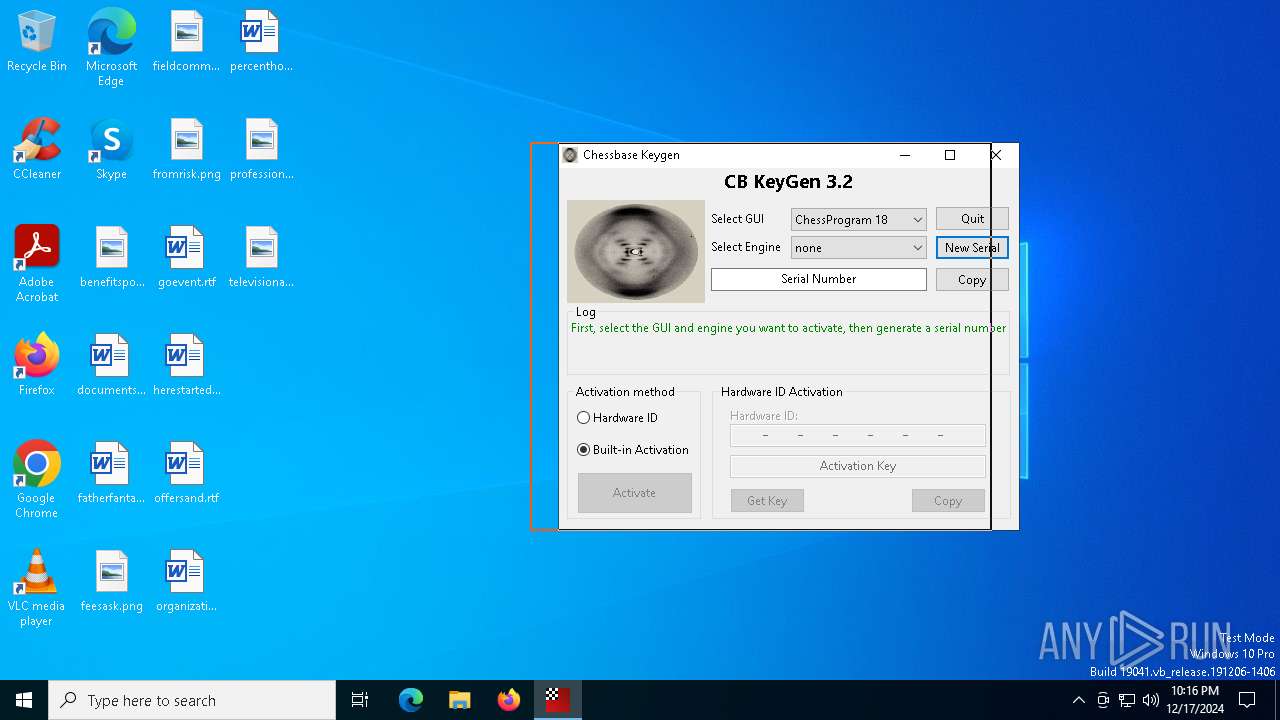
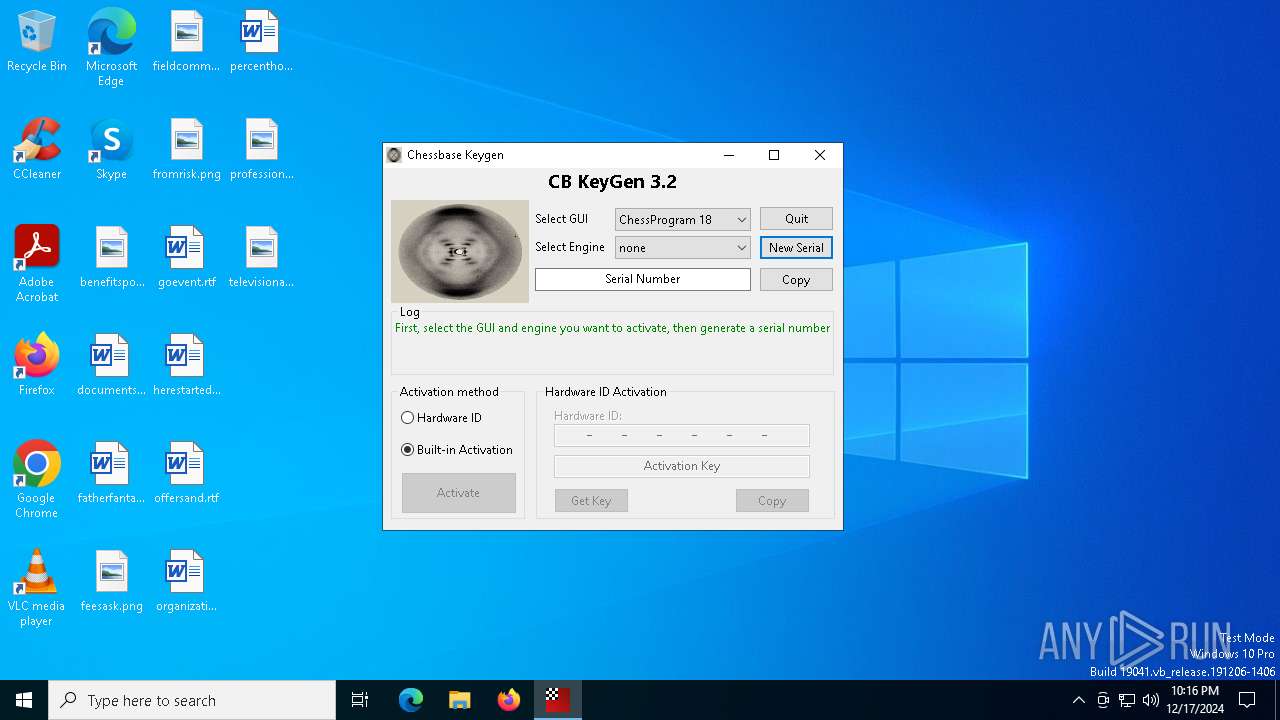
- CB-Keygen 3.2.exe (PID: 3952)
Executable content was dropped or overwritten
- CB-Keygen 3.2.exe (PID: 3952)
- CB_KG.exe (PID: 6284)
Reads security settings of Internet Explorer
- CB-Keygen 3.2.exe (PID: 3952)
- CB_KG.exe (PID: 6284)
Process drops legitimate windows executable
- CB-Keygen 3.2.exe (PID: 3952)
INFO
Reads the computer name
- CB-Keygen 3.2.exe (PID: 3952)
- CB_KG.exe (PID: 6284)
The sample compiled with german language support
- CB-Keygen 3.2.exe (PID: 3952)
- CB_KG.exe (PID: 6284)
The sample compiled with english language support
- CB-Keygen 3.2.exe (PID: 3952)
Process checks computer location settings
- CB-Keygen 3.2.exe (PID: 3952)
- CB_KG.exe (PID: 6284)
Checks supported languages
- CB-Keygen 3.2.exe (PID: 3952)
- CB_KG.exe (PID: 6284)
The process uses the downloaded file
- CB_KG.exe (PID: 6284)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win64 Executable (generic) (64.6) |
|---|---|---|
| .dll | | | Win32 Dynamic Link Library (generic) (15.4) |
| .exe | | | Win32 Executable (generic) (10.5) |
| .exe | | | Generic Win/DOS Executable (4.6) |
| .exe | | | DOS Executable Generic (4.6) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2022:03:03 13:15:57+00:00 |
| ImageFileCharacteristics: | Executable, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 14.3 |
| CodeSize: | 203776 |
| InitializedDataSize: | 261632 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x1f530 |
| OSVersion: | 5.1 |
| ImageVersion: | - |
| SubsystemVersion: | 5.1 |
| Subsystem: | Windows GUI |
Total processes
132
Monitored processes
4
Malicious processes
2
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 3952 | "C:\Users\admin\AppData\Local\Temp\CB-Keygen 3.2.exe" | C:\Users\admin\AppData\Local\Temp\CB-Keygen 3.2.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Modules
| |||||||||||||||
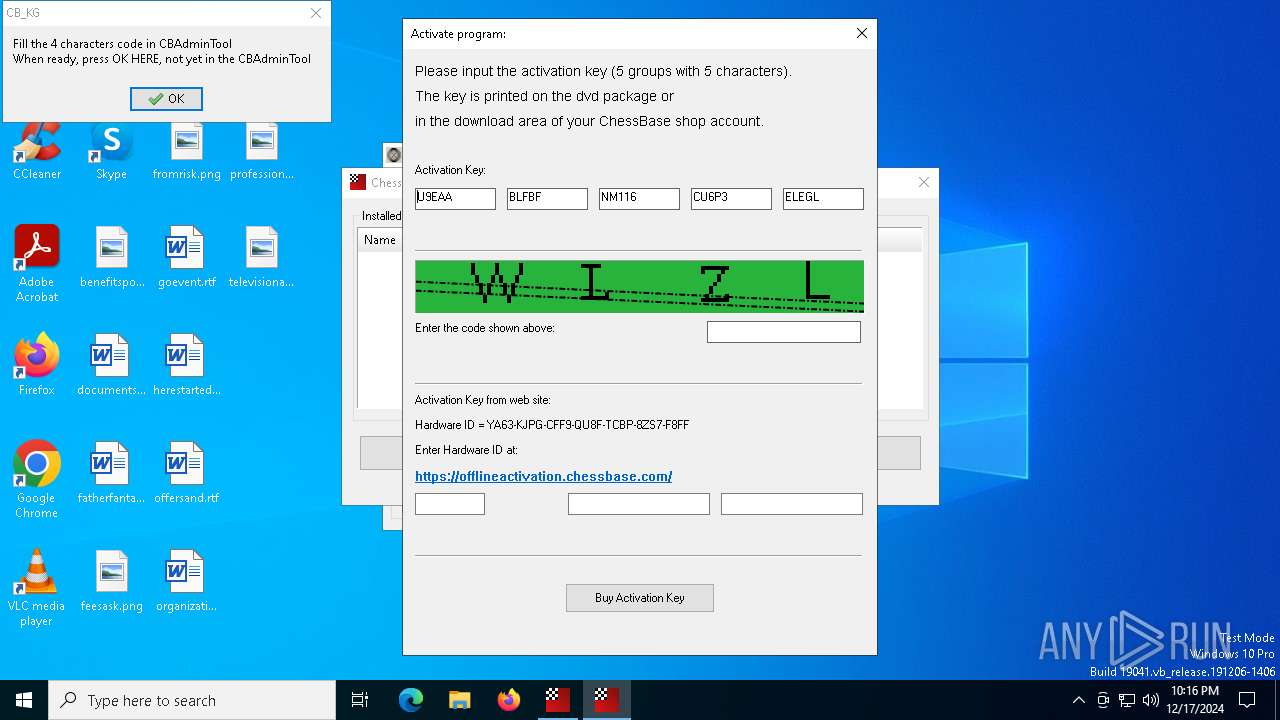
| 4716 | "C:\Users\admin\AppData\Local\Temp\RarSFX0\ChessBaseAdminTool.exe" /ActivationOffline "1678901504" | C:\Users\admin\AppData\Local\Temp\RarSFX0\ChessBaseAdminTool.exe | CB_KG.exe | ||||||||||||
User: admin Company: ChessBase GmbH Integrity Level: HIGH Description: ChessBase Admin Tool Version: 2, 0, 0, 3 Modules
| |||||||||||||||
| 4944 | "C:\Users\admin\AppData\Local\Temp\RarSFX0\ChessBaseAdminTool.exe" /ActivationOffline "1678901504" | C:\Users\admin\AppData\Local\Temp\RarSFX0\ChessBaseAdminTool.exe | — | CB_KG.exe | |||||||||||
User: admin Company: ChessBase GmbH Integrity Level: MEDIUM Description: ChessBase Admin Tool Exit code: 3221226540 Version: 2, 0, 0, 3 Modules
| |||||||||||||||
| 6284 | "C:\Users\admin\AppData\Local\Temp\RarSFX0\CB_KG.exe" | C:\Users\admin\AppData\Local\Temp\RarSFX0\CB_KG.exe | CB-Keygen 3.2.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Modules
| |||||||||||||||
Total events
905
Read events
905
Write events
0
Delete events
0
Modification events
Executable files
6
Suspicious files
1
Text files
6
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3952 | CB-Keygen 3.2.exe | C:\Users\admin\AppData\Local\Temp\RarSFX0\msvcp140.dll | executable | |
MD5:C092885EA11BD80D35CB55C7D488F1E2 | SHA256:885A0A146A83B0D5A19B88C4EB6372B648CFAED817BD31D8CD3FB91313DEA13D | |||
| 3952 | CB-Keygen 3.2.exe | C:\Users\admin\AppData\Local\Temp\RarSFX0\Messages\English\Frame.strings | text | |
MD5:DFF64D178593FB1EEC98072664F04268 | SHA256:C304DF5ED37EE370E0920BED1A6E5DFB64C643E15CA684302EEBDEDADA05E117 | |||
| 3952 | CB-Keygen 3.2.exe | C:\Users\admin\AppData\Local\Temp\RarSFX0\Messages\Deutsch\Frame.strings | text | |
MD5:FCDC77C0E15E65E130F9816F6BC81157 | SHA256:240134ECA02DB1493C6195364833F2F0564E9AAD10F13B3A33AACC4F6B160338 | |||
| 3952 | CB-Keygen 3.2.exe | C:\Users\admin\AppData\Local\Temp\RarSFX0\mfc140.dll | executable | |
MD5:C594917D6C51B6696CAA3C707BC435BF | SHA256:6E668ACF6F4FC3FBED14C89CFA80AE38E49B09AC9035DF698C191A217C6D0BC0 | |||
| 3952 | CB-Keygen 3.2.exe | C:\Users\admin\AppData\Local\Temp\RarSFX0\SView3.dll | executable | |
MD5:A04D243A7324084053A91F5B73A433D1 | SHA256:5595FC73179F90D8ADFBC1FD82E57FEF9E6D17A0D992CC242C013FA8FB7F69D4 | |||
| 3952 | CB-Keygen 3.2.exe | C:\Users\admin\AppData\Local\Temp\RarSFX0\vcruntime140.dll | executable | |
MD5:31CE620CB32AC950D31E019E67EFC638 | SHA256:1E0F8F7F13502F5CEE17232E9BEBCA7B44DD6EC29F1842BB61033044C65B2BBF | |||
| 4716 | ChessBaseAdminTool.exe | C:\Users\admin\AppData\Roaming\Microsoft\Crypto\RSA\S-1-5-21-1693682860-607145093-2874071422-1001\0f5007522459c86e95ffcc62f32308f1_bb926e54-e3ca-40fd-ae90-2764341e7792 | binary | |
MD5:97FC4004BAAC3B09E238DCB4C60DF019 | SHA256:FB5C4AF6D3E161CF6E9E6C3FCD3C8909A6A81A5281574D651B2050AABEB9438E | |||
| 6284 | CB_KG.exe | C:\Users\admin\AppData\Local\Temp\RarSFX0\ChessBaseAdminTool.exe | executable | |
MD5:154484EC3DF68A50ADAEEB122F33A2EB | SHA256:598B343954E8424FA9B69154046541F2D07185CE0C260C6CD713E1E4ED6ADCF9 | |||
| 3952 | CB-Keygen 3.2.exe | C:\Users\admin\AppData\Local\Temp\RarSFX0\Messages\Frame.inc | text | |
MD5:9710429DFF75D90E6F6073B2B851B266 | SHA256:0F0FEE1920A1E76090CB405A08B3112C256BCC2F461A302AE56AE9B4A8DC05C0 | |||
| 3952 | CB-Keygen 3.2.exe | C:\Users\admin\AppData\Local\Temp\RarSFX0\Messages\English\Countries.strings | text | |
MD5:90B850C19BDFDA9A852A786878B31CB0 | SHA256:C52A78C82F7EEDD0CE5BE7BC678837496632C9DFD53A965E29F90D4367C8D211 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
8
TCP/UDP connections
33
DNS requests
17
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 184.24.77.37:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
— | — | GET | 200 | 2.19.217.218:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
1176 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
5432 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
6228 | SIHClient.exe | GET | 200 | 2.19.217.218:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
6228 | SIHClient.exe | GET | 200 | 2.19.217.218:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
5432 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 192.168.100.255:137 | — | — | — | whitelisted |
3508 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4712 | MoUsoCoreWorker.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5064 | SearchApp.exe | 23.212.110.160:443 | www.bing.com | Akamai International B.V. | CZ | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
— | — | 184.24.77.37:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
— | — | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
— | — | 2.19.217.218:80 | www.microsoft.com | Akamai International B.V. | NL | whitelisted |
1176 | svchost.exe | 20.190.160.20:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
www.bing.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
login.live.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
arc.msn.com |
| whitelisted |
fd.api.iris.microsoft.com |
| whitelisted |