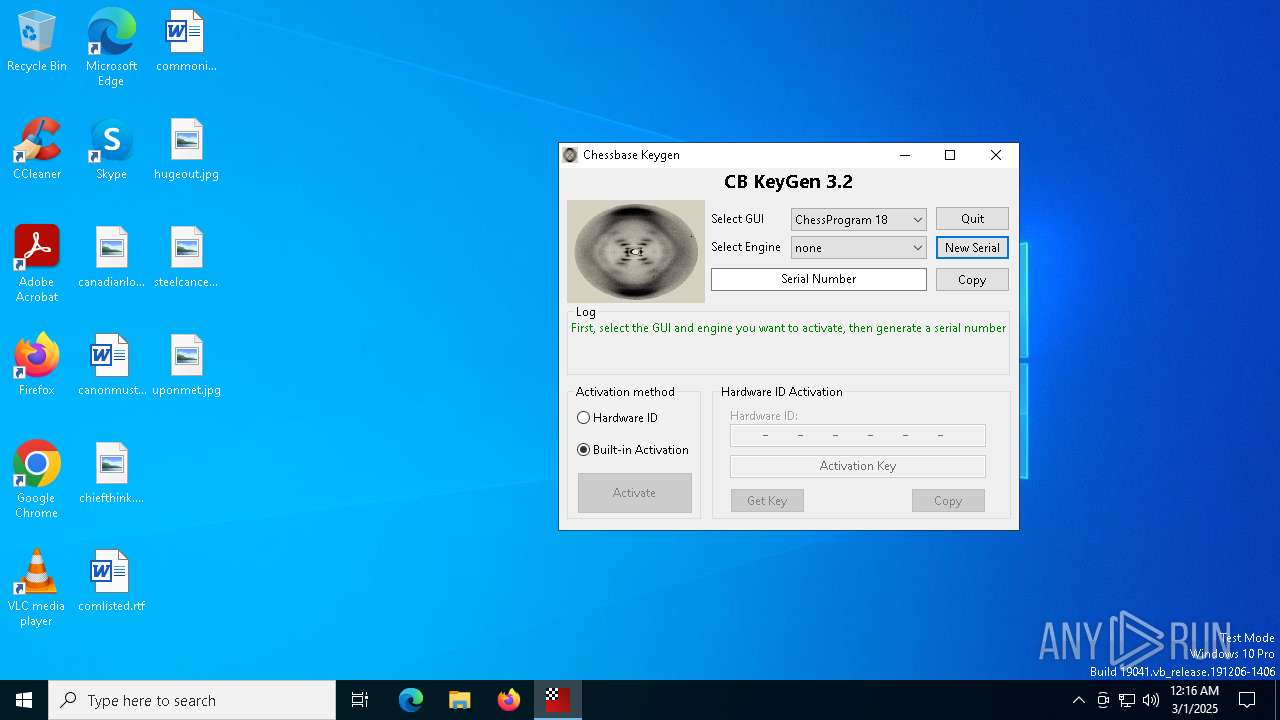
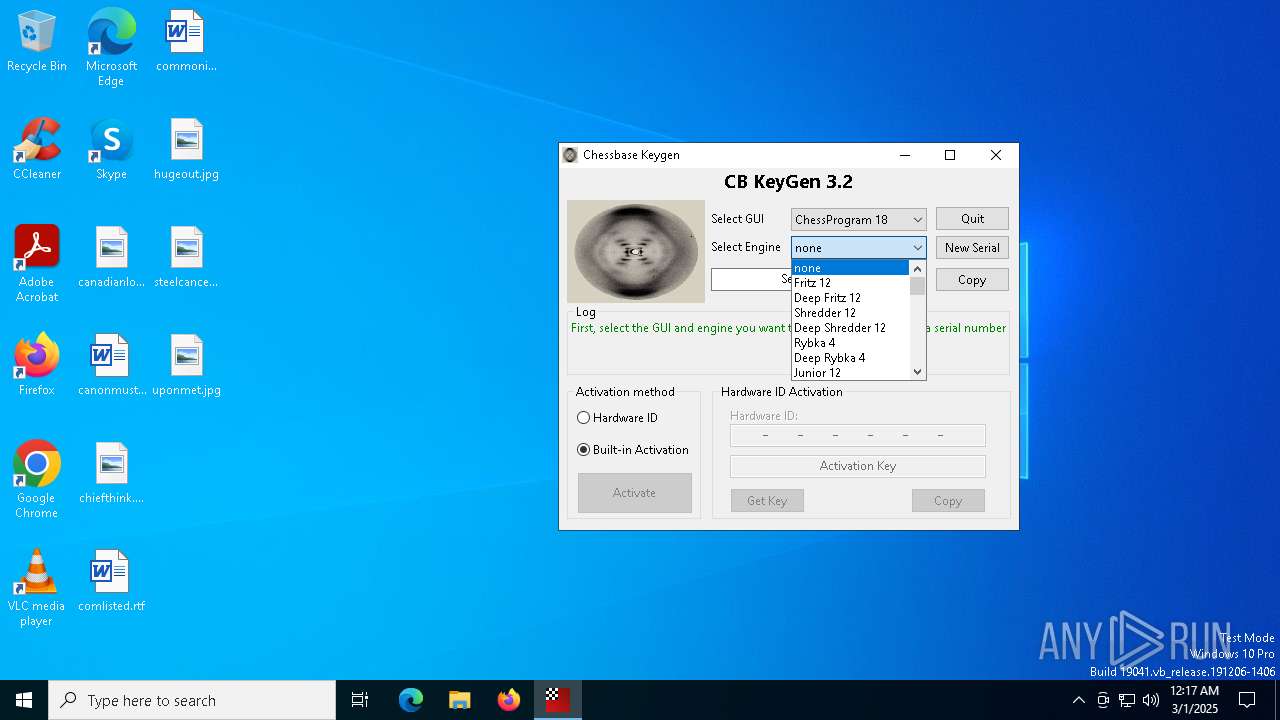
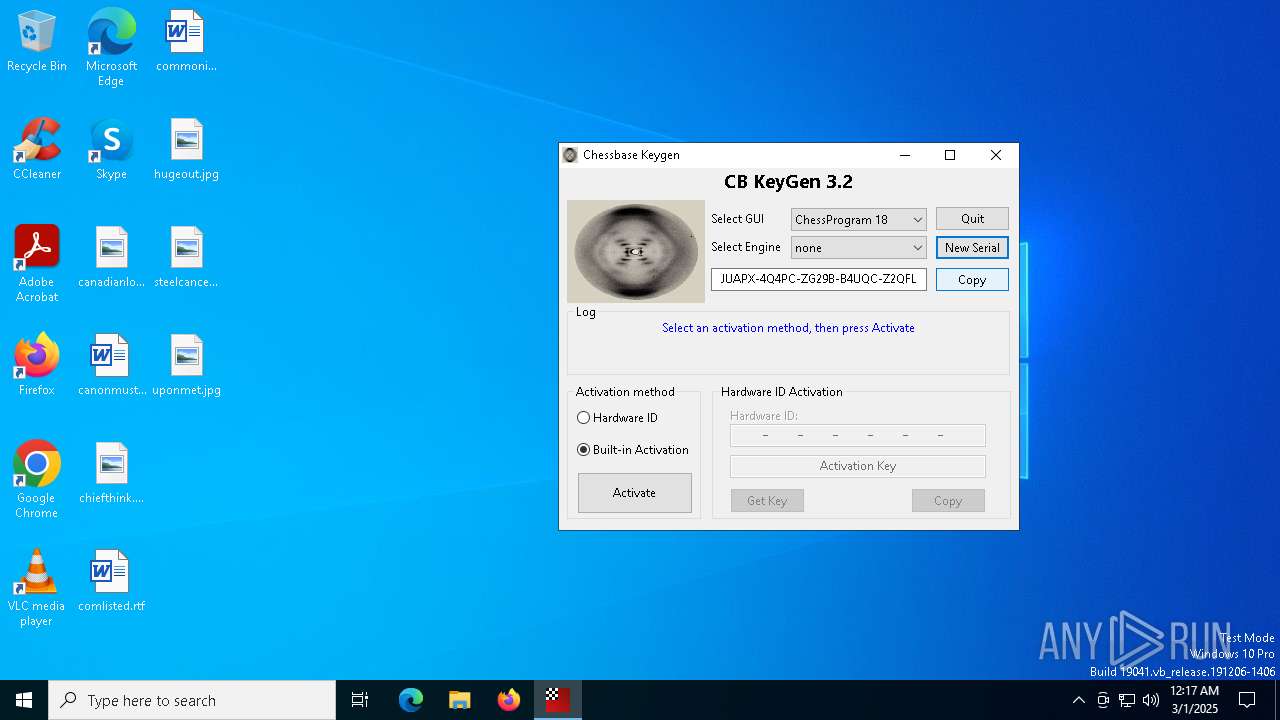
| File name: | CB-Keygen 3.2.exe |
| Full analysis: | https://app.any.run/tasks/b15ada62-57db-4772-bb7a-ccb3cc884d53 |
| Verdict: | Malicious activity |
| Analysis date: | March 01, 2025, 00:16:39 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, 6 sections |
| MD5: | 03EBA8A1A1ADB5337D8B43CCB6B554AF |
| SHA1: | 114A86DEB1F51D36FA1398A16DC974DD98938A8F |
| SHA256: | 916F8DFF7063ED6B1108E19E0F400F0969E7AE80F69F67C266E56F7055B92F2B |
| SSDEEP: | 98304:Oyi35bgowHn0dteCCfLuhhVI+xDCnVR7ToG4a9rIeJAVxqakhi3ZxH/+AA6LA409:qpa+RB/r9n0 |
MALICIOUS
Executing a file with an untrusted certificate
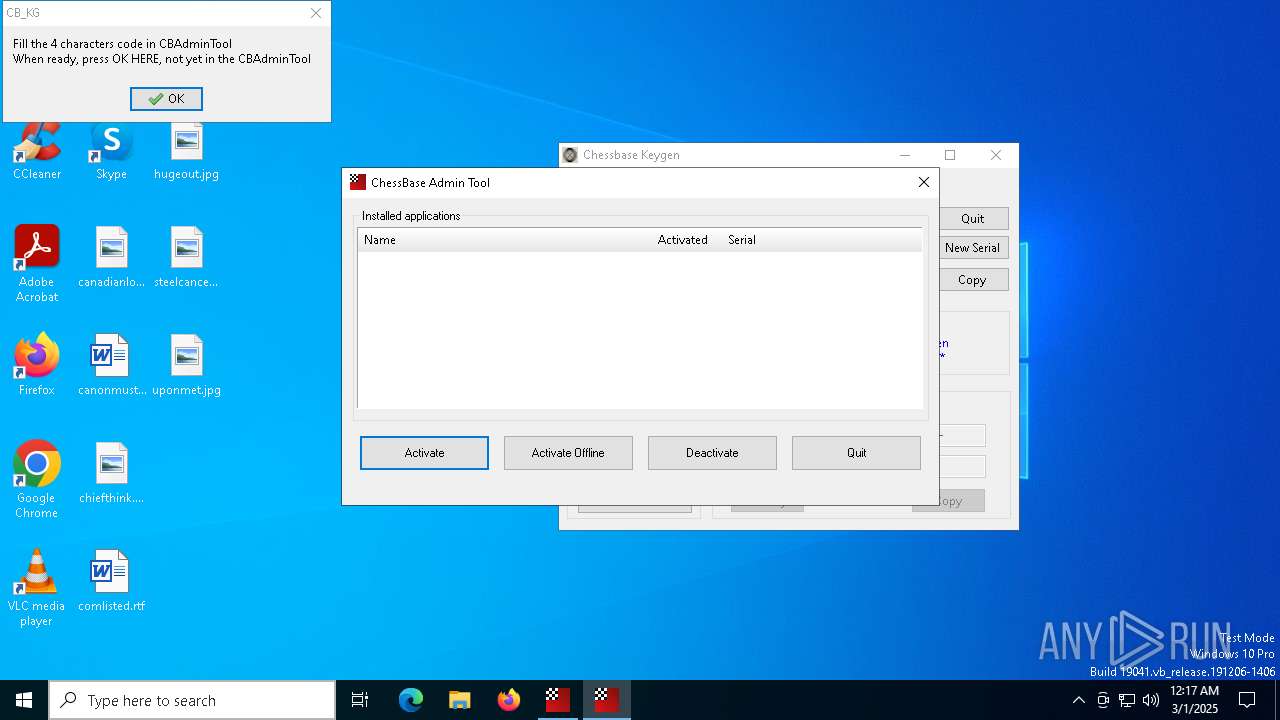
- ChessBaseAdminTool.exe (PID: 4180)
- ChessBaseAdminTool.exe (PID: 6228)
SUSPICIOUS
Executable content was dropped or overwritten
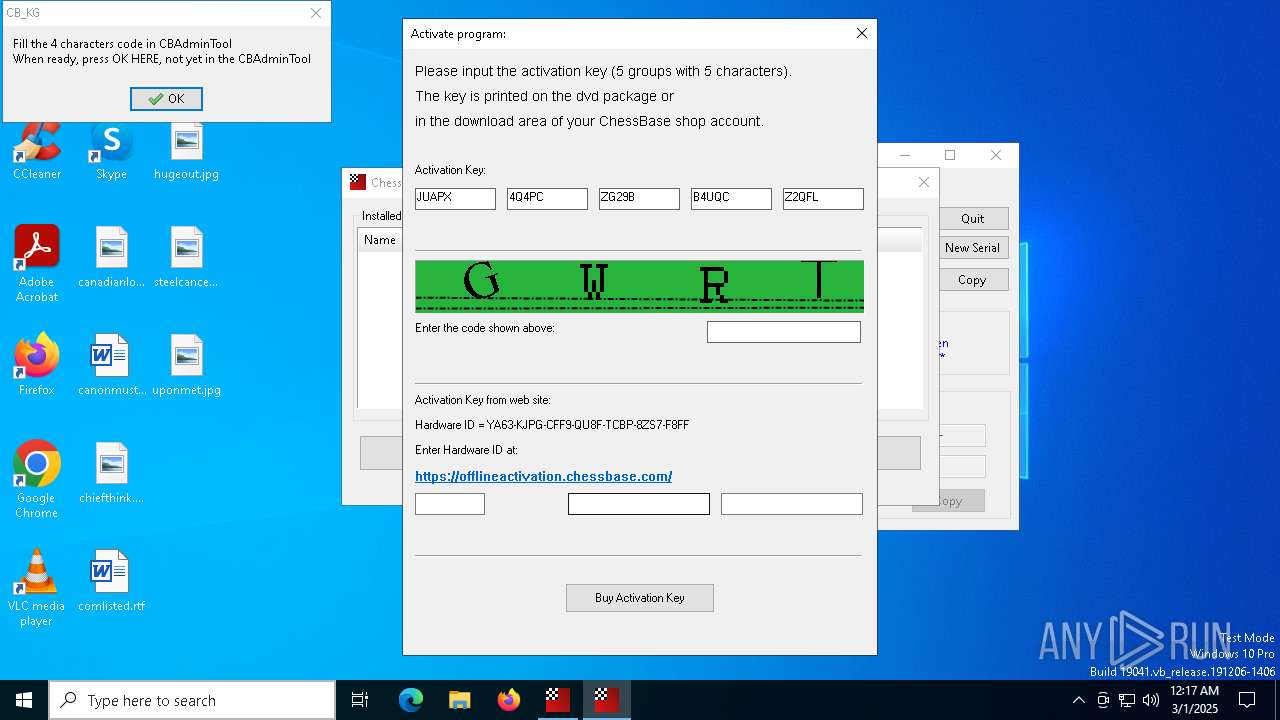
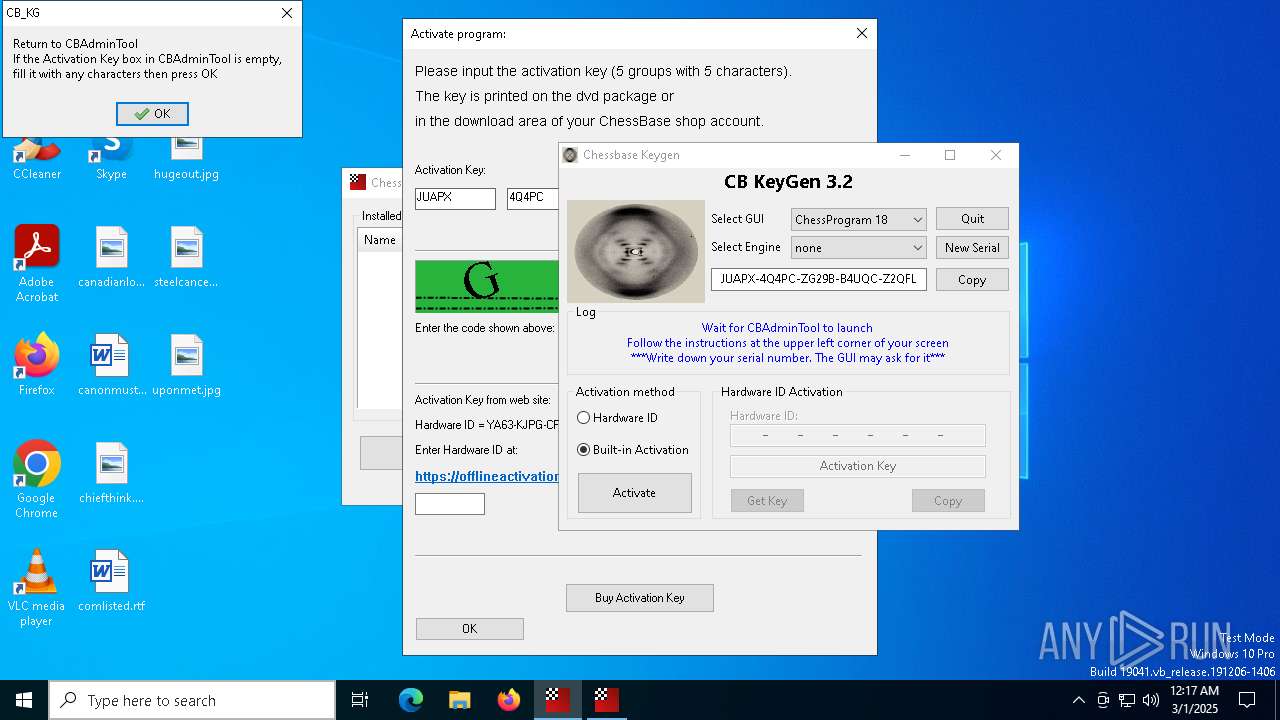
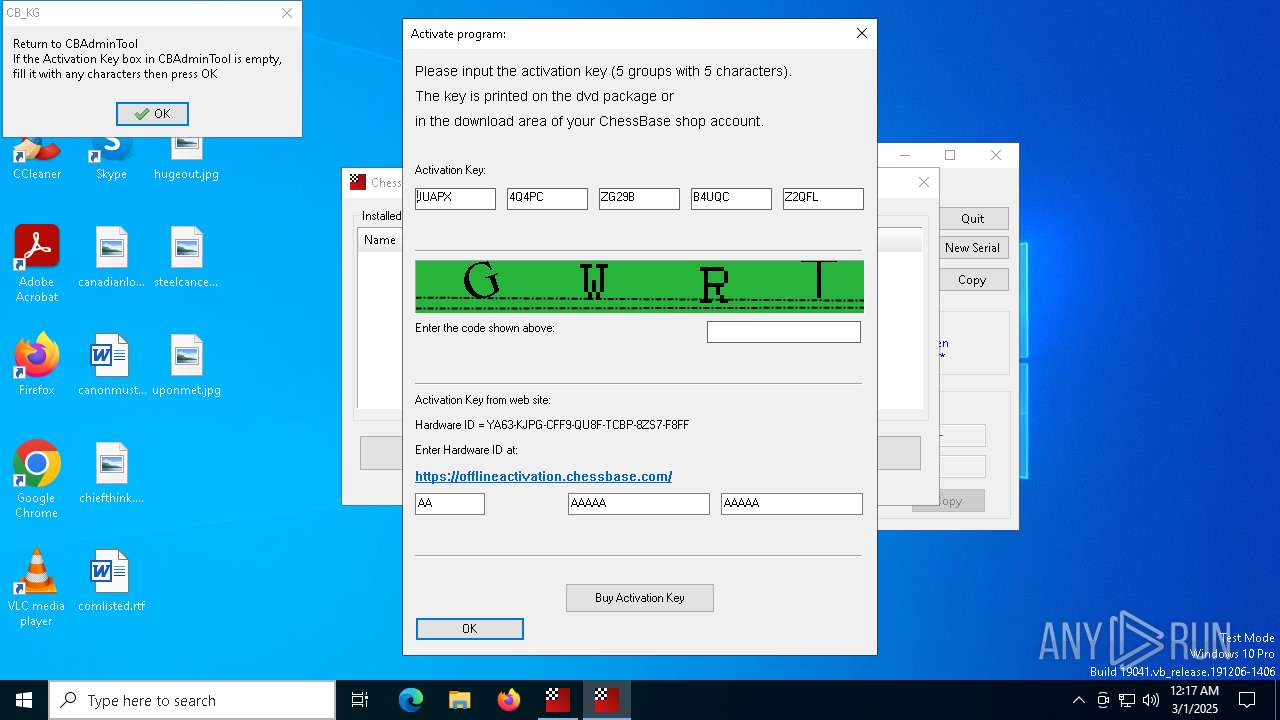
- CB-Keygen 3.2.exe (PID: 5072)
- CB_KG.exe (PID: 5740)
Reads security settings of Internet Explorer
- CB-Keygen 3.2.exe (PID: 5072)
- CB_KG.exe (PID: 5740)
Process drops legitimate windows executable
- CB-Keygen 3.2.exe (PID: 5072)
The process drops C-runtime libraries
- CB-Keygen 3.2.exe (PID: 5072)
There is functionality for taking screenshot (YARA)
- CB_KG.exe (PID: 5740)
- CB-Keygen 3.2.exe (PID: 5072)
INFO
Create files in a temporary directory
- CB-Keygen 3.2.exe (PID: 5072)
- CB_KG.exe (PID: 5740)
Reads the computer name
- CB-Keygen 3.2.exe (PID: 5072)
- ChessBaseAdminTool.exe (PID: 6228)
Process checks computer location settings
- CB-Keygen 3.2.exe (PID: 5072)
- CB_KG.exe (PID: 5740)
Checks supported languages
- CB-Keygen 3.2.exe (PID: 5072)
- CB_KG.exe (PID: 5740)
- ChessBaseAdminTool.exe (PID: 6228)
The sample compiled with english language support
- CB-Keygen 3.2.exe (PID: 5072)
Compiled with Borland Delphi (YARA)
- CB_KG.exe (PID: 5740)
The sample compiled with german language support
- CB_KG.exe (PID: 5740)
Reads the machine GUID from the registry
- ChessBaseAdminTool.exe (PID: 6228)
Creates files in the program directory
- ChessBaseAdminTool.exe (PID: 6228)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win64 Executable (generic) (64.6) |
|---|---|---|
| .dll | | | Win32 Dynamic Link Library (generic) (15.4) |
| .exe | | | Win32 Executable (generic) (10.5) |
| .exe | | | Generic Win/DOS Executable (4.6) |
| .exe | | | DOS Executable Generic (4.6) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2022:03:03 13:15:57+00:00 |
| ImageFileCharacteristics: | Executable, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 14.3 |
| CodeSize: | 203776 |
| InitializedDataSize: | 261632 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x1f530 |
| OSVersion: | 5.1 |
| ImageVersion: | - |
| SubsystemVersion: | 5.1 |
| Subsystem: | Windows GUI |
Total processes
138
Monitored processes
5
Malicious processes
2
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 4180 | "C:\Users\admin\AppData\Local\Temp\RarSFX0\ChessBaseAdminTool.exe" /ActivationOffline "1678901504" | C:\Users\admin\AppData\Local\Temp\RarSFX0\ChessBaseAdminTool.exe | — | CB_KG.exe | |||||||||||
User: admin Company: ChessBase GmbH Integrity Level: MEDIUM Description: ChessBase Admin Tool Exit code: 3221226540 Version: 2, 0, 0, 3 Modules
| |||||||||||||||
| 5072 | "C:\Users\admin\AppData\Local\Temp\CB-Keygen 3.2.exe" | C:\Users\admin\AppData\Local\Temp\CB-Keygen 3.2.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Modules
| |||||||||||||||
| 5740 | "C:\Users\admin\AppData\Local\Temp\RarSFX0\CB_KG.exe" | C:\Users\admin\AppData\Local\Temp\RarSFX0\CB_KG.exe | CB-Keygen 3.2.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Modules
| |||||||||||||||
| 6048 | C:\WINDOWS\system32\SppExtComObj.exe -Embedding | C:\Windows\System32\SppExtComObj.Exe | — | svchost.exe | |||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: KMS Connection Broker Version: 10.0.19041.3996 (WinBuild.160101.0800) | |||||||||||||||
| 6228 | "C:\Users\admin\AppData\Local\Temp\RarSFX0\ChessBaseAdminTool.exe" /ActivationOffline "1678901504" | C:\Users\admin\AppData\Local\Temp\RarSFX0\ChessBaseAdminTool.exe | CB_KG.exe | ||||||||||||
User: admin Company: ChessBase GmbH Integrity Level: HIGH Description: ChessBase Admin Tool Exit code: 0 Version: 2, 0, 0, 3 Modules
| |||||||||||||||
Total events
884
Read events
884
Write events
0
Delete events
0
Modification events
Executable files
6
Suspicious files
1
Text files
9
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 5072 | CB-Keygen 3.2.exe | C:\Users\admin\AppData\Local\Temp\RarSFX0\mfc140.dll | executable | |
MD5:C594917D6C51B6696CAA3C707BC435BF | SHA256:6E668ACF6F4FC3FBED14C89CFA80AE38E49B09AC9035DF698C191A217C6D0BC0 | |||
| 5072 | CB-Keygen 3.2.exe | C:\Users\admin\AppData\Local\Temp\RarSFX0\SView3.dll | executable | |
MD5:A04D243A7324084053A91F5B73A433D1 | SHA256:5595FC73179F90D8ADFBC1FD82E57FEF9E6D17A0D992CC242C013FA8FB7F69D4 | |||
| 5072 | CB-Keygen 3.2.exe | C:\Users\admin\AppData\Local\Temp\RarSFX0\Messages\Countries.inc | text | |
MD5:200710201C95F4E8A612299B132289DA | SHA256:A1FF5302B95A293433F77DB64B40F04A2BD6706521CF0A8702991D88378B015C | |||
| 5072 | CB-Keygen 3.2.exe | C:\Users\admin\AppData\Local\Temp\RarSFX0\vcruntime140.dll | executable | |
MD5:31CE620CB32AC950D31E019E67EFC638 | SHA256:1E0F8F7F13502F5CEE17232E9BEBCA7B44DD6EC29F1842BB61033044C65B2BBF | |||
| 5072 | CB-Keygen 3.2.exe | C:\Users\admin\AppData\Local\Temp\RarSFX0\Messages\Deutsch\Countries.strings | text | |
MD5:E831412DB1A96BBA8BEFA223EF2849D6 | SHA256:637829E1E9198E5ED1C6B6B2AB2D8E8FF7E9B0BD02005272FD56E6C48C093555 | |||
| 5072 | CB-Keygen 3.2.exe | C:\Users\admin\AppData\Local\Temp\RarSFX0\Messages\English\Frame.strings | text | |
MD5:DFF64D178593FB1EEC98072664F04268 | SHA256:C304DF5ED37EE370E0920BED1A6E5DFB64C643E15CA684302EEBDEDADA05E117 | |||
| 5072 | CB-Keygen 3.2.exe | C:\Users\admin\AppData\Local\Temp\RarSFX0\CB_KG.exe | executable | |
MD5:9E07A919C6CD1FE569318D726A1B467E | SHA256:3FC56148604DF4639299CAC494F9B29316D55F87AB03CB43C25A9B2E184F9857 | |||
| 5072 | CB-Keygen 3.2.exe | C:\Users\admin\AppData\Local\Temp\RarSFX0\Messages\Deutsch\Frame.strings | text | |
MD5:FCDC77C0E15E65E130F9816F6BC81157 | SHA256:240134ECA02DB1493C6195364833F2F0564E9AAD10F13B3A33AACC4F6B160338 | |||
| 6228 | ChessBaseAdminTool.exe | C:\Users\admin\AppData\Roaming\Microsoft\Crypto\RSA\S-1-5-21-1693682860-607145093-2874071422-1001\0f5007522459c86e95ffcc62f32308f1_bb926e54-e3ca-40fd-ae90-2764341e7792 | binary | |
MD5:17011E7DB4379E83CD44DF33F3CD7982 | SHA256:FE346C744FE79A7CC60B7F2F91A756A4B05590F31434898283A752B9DD6DB0DC | |||
| 6228 | ChessBaseAdminTool.exe | C:\ProgramData\ChessBase\100-18.cbinfo | text | |
MD5:70E27E7E9C8590742CEC1546E4FE10F8 | SHA256:3212B335CB814E826E49A07E4FA3AE0C0F72AA03A3107EA23AAAC7B67460929F | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
2
TCP/UDP connections
23
DNS requests
13
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5344 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
5344 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2104 | svchost.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
— | — | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
2112 | svchost.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
6544 | svchost.exe | 20.190.159.75:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
3216 | svchost.exe | 40.113.103.199:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
3008 | backgroundTaskHost.exe | 104.126.37.131:443 | www.bing.com | Akamai International B.V. | DE | whitelisted |
2040 | backgroundTaskHost.exe | 20.199.58.43:443 | arc.msn.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
5376 | backgroundTaskHost.exe | 20.199.58.43:443 | arc.msn.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
login.live.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
www.bing.com |
| whitelisted |
arc.msn.com |
| whitelisted |
fd.api.iris.microsoft.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |