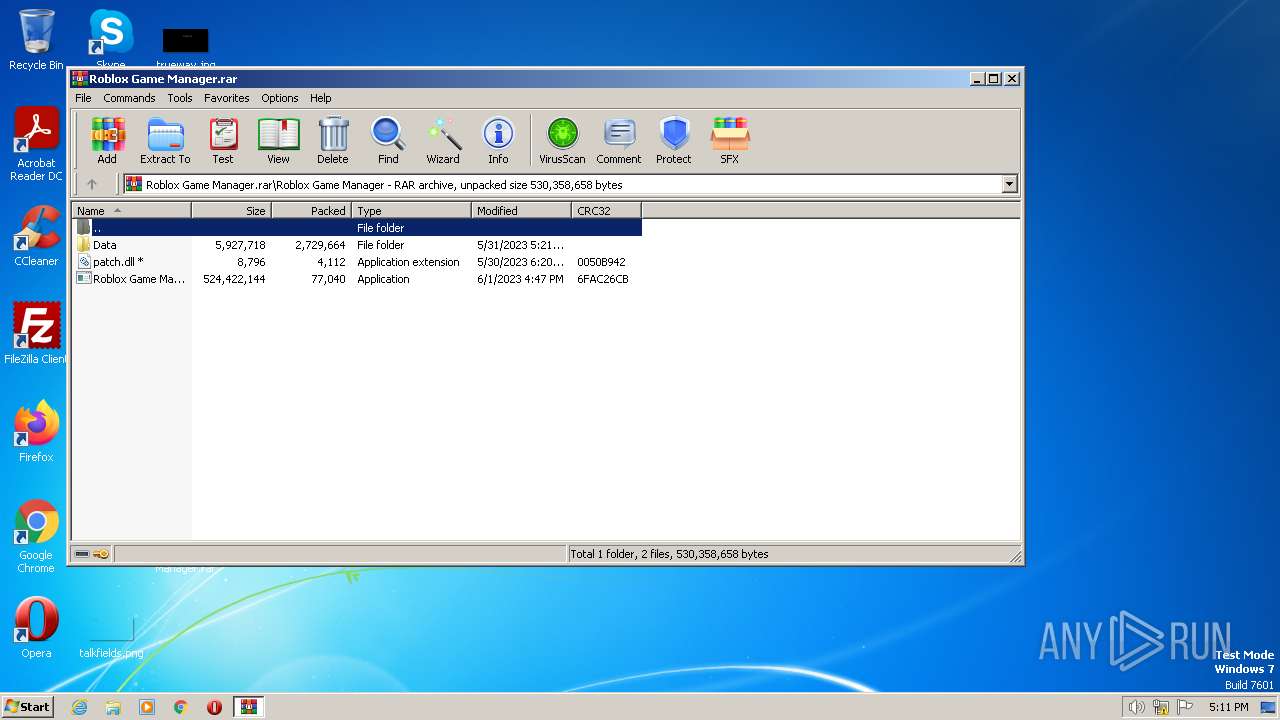
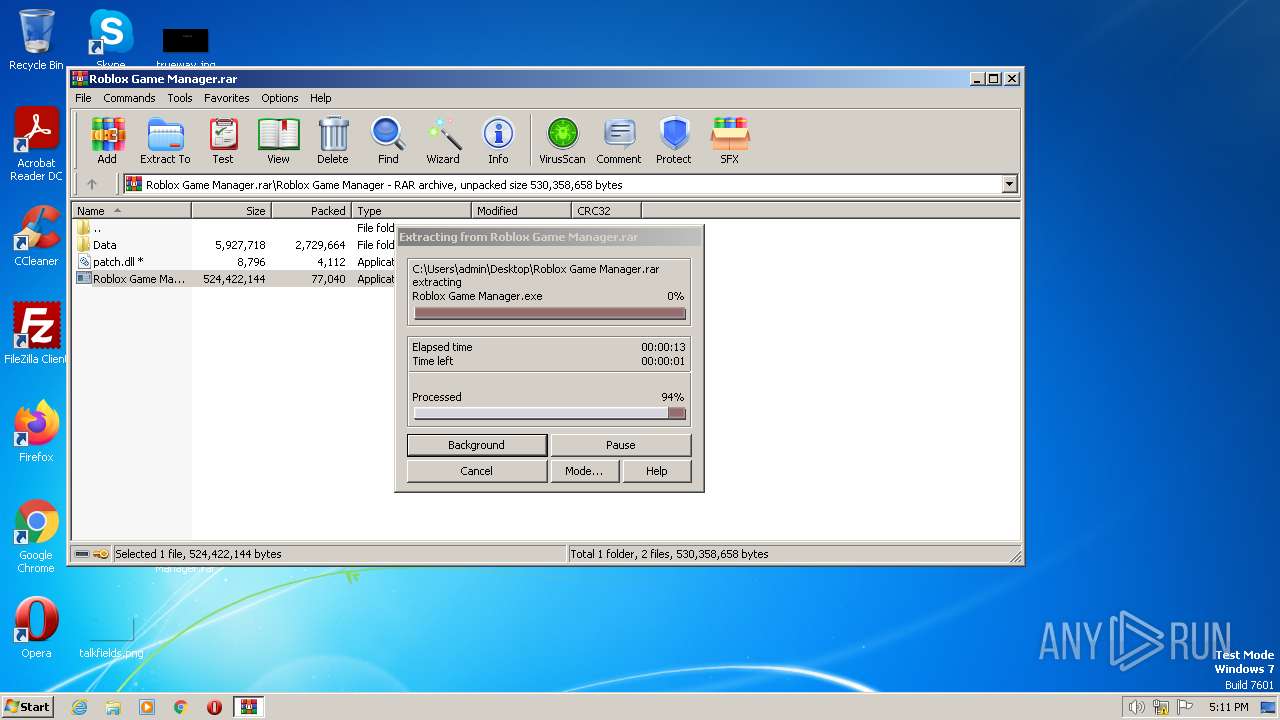
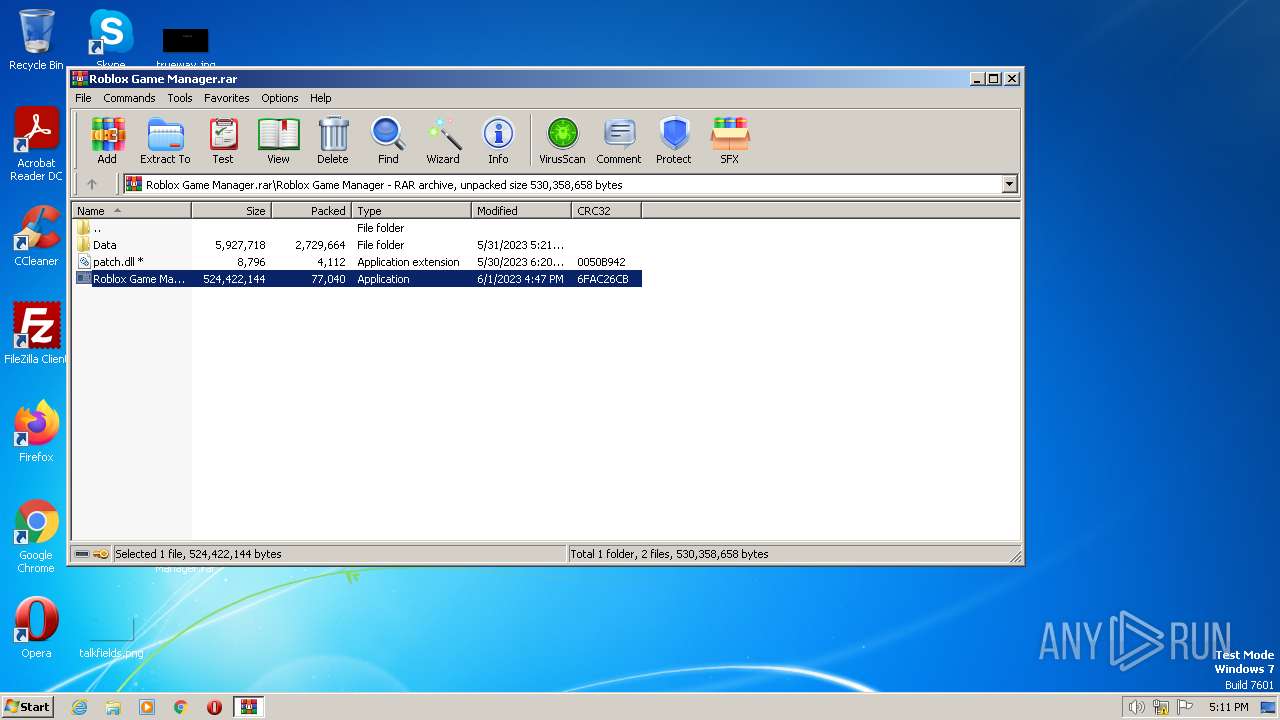
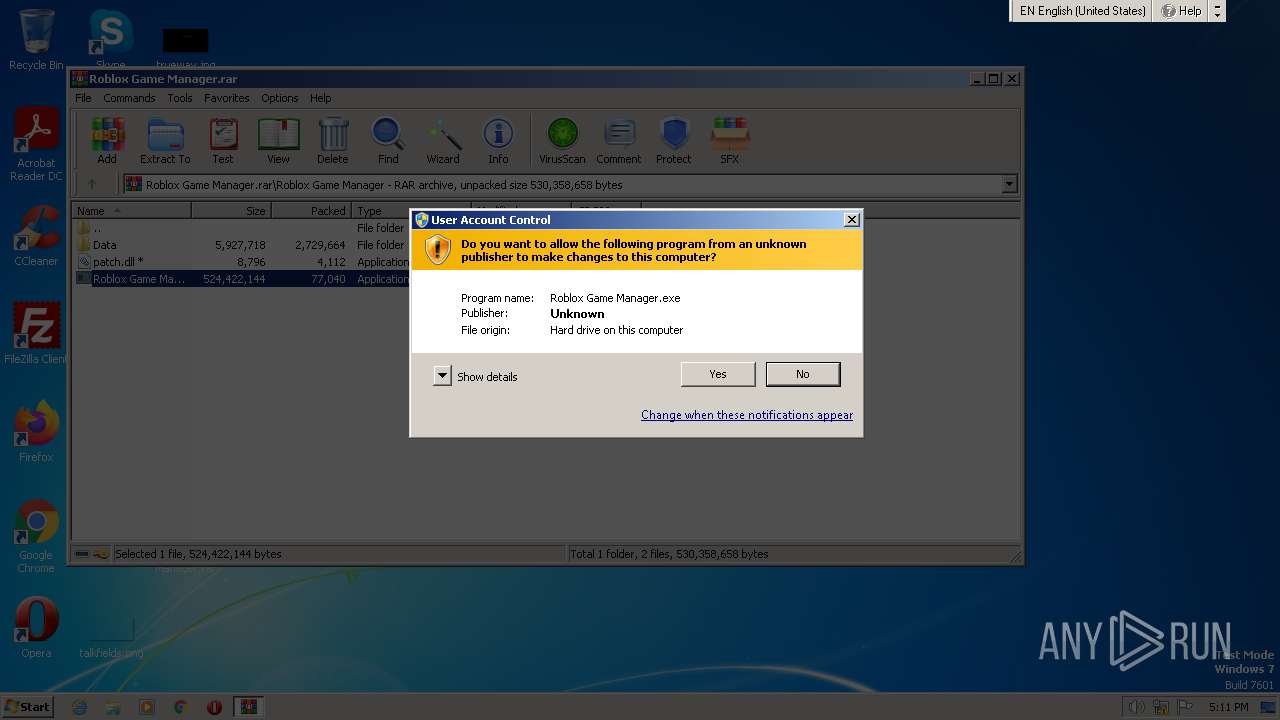
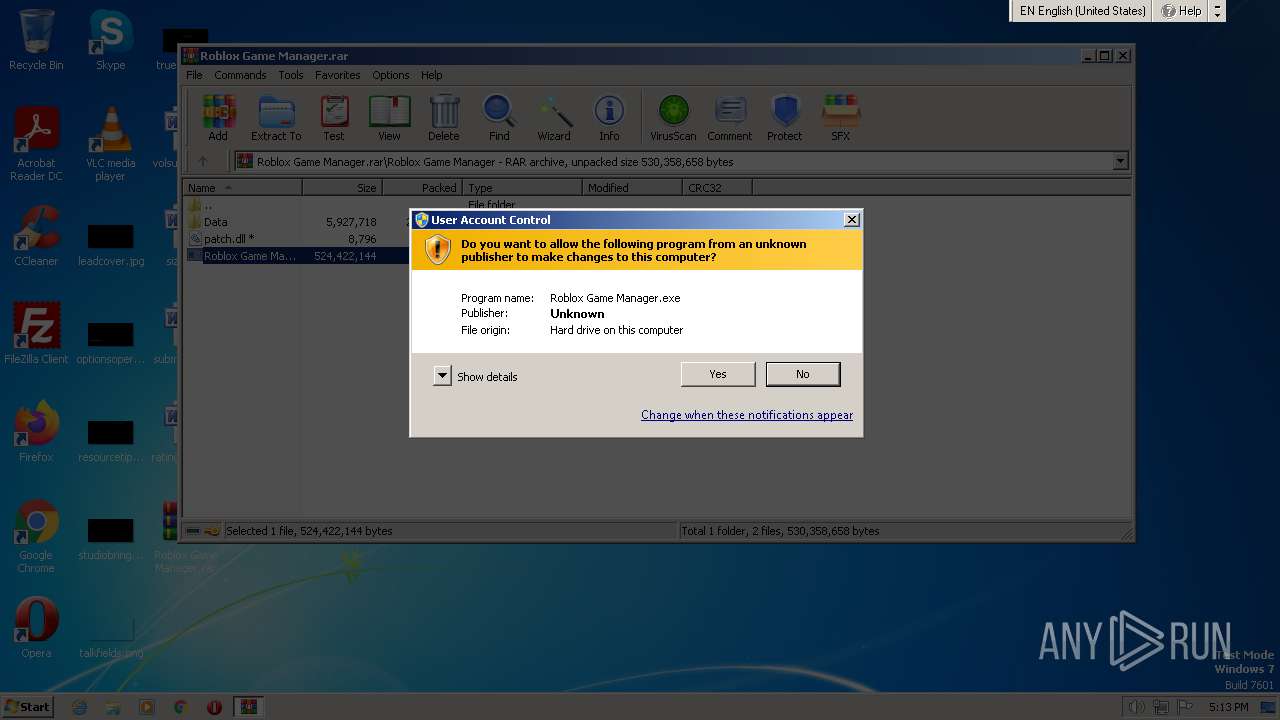
| File name: | Roblox Game Manager.rar |
| Full analysis: | https://app.any.run/tasks/f73c1b97-2bdc-4533-a995-10993290c2aa |
| Verdict: | Malicious activity |
| Threats: | A loader is malicious software that infiltrates devices to deliver malicious payloads. This malware is capable of infecting victims’ computers, analyzing their system information, and installing other types of threats, such as trojans or stealers. Criminals usually deliver loaders through phishing emails and links by relying on social engineering to trick users into downloading and running their executables. Loaders employ advanced evasion and persistence tactics to avoid detection. |
| Analysis date: | June 25, 2023, 16:10:39 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-rar |
| File info: | RAR archive data, v5 |
| MD5: | A7A070FEA3E75A91856AE28BA200EB45 |
| SHA1: | 18A93136443481CA0EEDE8EC625E21517B504C1B |
| SHA256: | 914349176C58586166FED229065945D849DE72E34CAE9E04585D6186D08F9D34 |
| SSDEEP: | 49152:0njnC2HQk9DL6KuEsJKJDoWC1T1o6o1FfBfpu9y3h7lsgmx4srNNVkWyg6tIksvp:cf9DGK8kbkC6o1lu43BmuwBkWQtIkm |
MALICIOUS
Adds path to the Windows Defender exclusion list
- cmd.exe (PID: 3096)
- cmd.exe (PID: 2044)
Application was dropped or rewritten from another process
- dclppAf.exe (PID: 1628)
- dclppAf.exe (PID: 752)
Unusual connection from system programs
- vbc.exe (PID: 2476)
- vbc.exe (PID: 796)
REDLINE detected by memory dumps
- vbc.exe (PID: 2476)
- vbc.exe (PID: 796)
REDLINE was detected
- vbc.exe (PID: 796)
Request from PowerShell which ran from CMD.EXE
- powershell.exe (PID: 3604)
Connects to the CnC server
- vbc.exe (PID: 796)
Steals credentials from Web Browsers
- vbc.exe (PID: 796)
Actions looks like stealing of personal data
- vbc.exe (PID: 796)
SUSPICIOUS
Executing commands from a ".bat" file
- Roblox Game Manager.exe (PID: 2460)
- Roblox Game Manager.exe (PID: 2272)
Reads the Internet Settings
- Roblox Game Manager.exe (PID: 2460)
- powershell.exe (PID: 3372)
- powershell.exe (PID: 3792)
- Roblox Game Manager.exe (PID: 2272)
- powershell.exe (PID: 1472)
- powershell.exe (PID: 3604)
Using PowerShell to operate with local accounts
- powershell.exe (PID: 3372)
- powershell.exe (PID: 1472)
Executable content was dropped or overwritten
- powershell.exe (PID: 3792)
Starts CMD.EXE for commands execution
- Roblox Game Manager.exe (PID: 2460)
- Roblox Game Manager.exe (PID: 2272)
Starts POWERSHELL.EXE for commands execution
- cmd.exe (PID: 3096)
- cmd.exe (PID: 2044)
Script adds exclusion path to Windows Defender
- cmd.exe (PID: 3096)
- cmd.exe (PID: 2044)
Download files or web resources using Curl/Wget
- cmd.exe (PID: 3096)
- cmd.exe (PID: 2044)
Possibly malicious use of IEX has been detected
- cmd.exe (PID: 3096)
- cmd.exe (PID: 2044)
The process executes VB scripts
- dclppAf.exe (PID: 1628)
- dclppAf.exe (PID: 752)
Connects to unusual port
- vbc.exe (PID: 2476)
- vbc.exe (PID: 796)
The Powershell connects to the Internet
- powershell.exe (PID: 3792)
- powershell.exe (PID: 3604)
Unusual connection from system programs
- powershell.exe (PID: 3792)
- powershell.exe (PID: 3604)
Connects to the server without a host name
- powershell.exe (PID: 3604)
Process requests binary or script from the Internet
- powershell.exe (PID: 3604)
Reads browser cookies
- vbc.exe (PID: 796)
Searches for installed software
- vbc.exe (PID: 796)
INFO
Reads the computer name
- Roblox Game Manager.exe (PID: 2460)
- dclppAf.exe (PID: 1628)
- vbc.exe (PID: 2476)
- wmpnscfg.exe (PID: 3028)
- dclppAf.exe (PID: 752)
- Roblox Game Manager.exe (PID: 2272)
- vbc.exe (PID: 796)
The process checks LSA protection
- Roblox Game Manager.exe (PID: 2460)
- dclppAf.exe (PID: 1628)
- vbc.exe (PID: 2476)
- wmpnscfg.exe (PID: 3028)
- Roblox Game Manager.exe (PID: 2272)
- vbc.exe (PID: 796)
- dclppAf.exe (PID: 752)
Checks supported languages
- Roblox Game Manager.exe (PID: 2460)
- dclppAf.exe (PID: 1628)
- wmpnscfg.exe (PID: 3028)
- Roblox Game Manager.exe (PID: 2272)
- vbc.exe (PID: 2476)
- dclppAf.exe (PID: 752)
- vbc.exe (PID: 796)
The executable file from the user directory is run by the Powershell process
- dclppAf.exe (PID: 1628)
- dclppAf.exe (PID: 752)
Reads the machine GUID from the registry
- dclppAf.exe (PID: 1628)
- vbc.exe (PID: 2476)
- wmpnscfg.exe (PID: 3028)
- vbc.exe (PID: 796)
- dclppAf.exe (PID: 752)
Manual execution by a user
- wmpnscfg.exe (PID: 3028)
Create files in a temporary directory
- Roblox Game Manager.exe (PID: 2272)
- Roblox Game Manager.exe (PID: 2460)
Reads product name
- vbc.exe (PID: 796)
Reads Environment values
- vbc.exe (PID: 796)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
RedLine
(PID) Process(2476) vbc.exe
C2 (1)94.142.138.105:15111
Botnetcryptx
Err_msg
Auth_valuea45302b7daf4f87798af144567e5d0ff
US (14)
net.tcp://
/
localhost
a45302b7daf4f87798af144567e5d0ff
Authorization
ns1
CCE9EzoxNB0LHykcOCZRHAoxOVA6MTAcCiEpWw==
HkYmUxQtN1A=
Gulfweed
(PID) Process(796) vbc.exe
C2 (1)94.142.138.105:15111
Botnetcryptx
Err_msg
Auth_valuea45302b7daf4f87798af144567e5d0ff
US (14)
net.tcp://
/
localhost
a45302b7daf4f87798af144567e5d0ff
Authorization
ns1
CCE9EzoxNB0LHykcOCZRHAoxOVA6MTAcCiEpWw==
HkYmUxQtN1A=
Gulfweed
TRiD
| .rar | | | RAR compressed archive (v5.0) (61.5) |
|---|---|---|
| .rar | | | RAR compressed archive (gen) (38.4) |
Total processes
64
Monitored processes
18
Malicious processes
12
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 752 | "C:\Users\admin\AppData\Roaming\dclppAf.exe" | C:\Users\admin\AppData\Roaming\dclppAf.exe | — | powershell.exe | |||||||||||
User: admin Company: John Paul Chacha's Lab Integrity Level: HIGH Description: Setup Package for Chasys Draw IES Exit code: 0 Version: 5, 25, 1, 0 Modules
| |||||||||||||||
| 796 | "C:\Windows\Microsoft.NET\Framework\v4.0.30319\vbc.exe" | C:\Windows\Microsoft.NET\Framework\v4.0.30319\vbc.exe | dclppAf.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Visual Basic Command Line Compiler Exit code: 0 Version: 12.0.51209.34209 Modules
RedLine(PID) Process(796) vbc.exe C2 (1)94.142.138.105:15111 Botnetcryptx Err_msg Auth_valuea45302b7daf4f87798af144567e5d0ff US (14) net.tcp:// / localhost a45302b7daf4f87798af144567e5d0ff Authorization ns1 CCE9EzoxNB0LHykcOCZRHAoxOVA6MTAcCiEpWw== HkYmUxQtN1A= Gulfweed | |||||||||||||||
| 1472 | powershell -Command "Add-MpPreference -ExclusionPath "'C:\'" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows PowerShell Exit code: 1 Version: 10.0.14409.1005 (rs1_srvoob.161208-1155) Modules
| |||||||||||||||
| 1628 | "C:\Users\admin\AppData\Roaming\dclppAf.exe" | C:\Users\admin\AppData\Roaming\dclppAf.exe | — | powershell.exe | |||||||||||
User: admin Company: John Paul Chacha's Lab Integrity Level: HIGH Description: Setup Package for Chasys Draw IES Exit code: 0 Version: 5, 25, 1, 0 Modules
| |||||||||||||||
| 2044 | "C:\Windows\system32\cmd.exe" /c "C:\Users\admin\AppData\Local\Temp\73B7.tmp\73B8.tmp\73B9.bat "C:\Users\admin\AppData\Local\Temp\Rar$EXb3460.5444\Roblox Game Manager\Roblox Game Manager.exe"" | C:\Windows\System32\cmd.exe | — | Roblox Game Manager.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 2192 | powershell -command "Invoke-Expression -Command "C:\Users\admin\AppData\Roaming\dclppAf.exe" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows PowerShell Exit code: 0 Version: 10.0.14409.1005 (rs1_srvoob.161208-1155) Modules
| |||||||||||||||
| 2272 | "C:\Users\admin\AppData\Local\Temp\Rar$EXb3460.5444\Roblox Game Manager\Roblox Game Manager.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXb3460.5444\Roblox Game Manager\Roblox Game Manager.exe | WinRAR.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 2460 | "C:\Users\admin\AppData\Local\Temp\Rar$EXb3460.47446\Roblox Game Manager\Roblox Game Manager.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXb3460.47446\Roblox Game Manager\Roblox Game Manager.exe | WinRAR.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 2476 | "C:\Windows\Microsoft.NET\Framework\v4.0.30319\vbc.exe" | C:\Windows\Microsoft.NET\Framework\v4.0.30319\vbc.exe | dclppAf.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Visual Basic Command Line Compiler Exit code: 0 Version: 12.0.51209.34209 Modules
RedLine(PID) Process(2476) vbc.exe C2 (1)94.142.138.105:15111 Botnetcryptx Err_msg Auth_valuea45302b7daf4f87798af144567e5d0ff US (14) net.tcp:// / localhost a45302b7daf4f87798af144567e5d0ff Authorization ns1 CCE9EzoxNB0LHykcOCZRHAoxOVA6MTAcCiEpWw== HkYmUxQtN1A= Gulfweed | |||||||||||||||
| 2896 | "C:\Users\admin\AppData\Local\Temp\Rar$EXb3460.5444\Roblox Game Manager\Roblox Game Manager.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXb3460.5444\Roblox Game Manager\Roblox Game Manager.exe | — | WinRAR.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 3221226540 Modules
| |||||||||||||||
Total events
12 450
Read events
12 370
Write events
77
Delete events
3
Modification events
| (PID) Process: | (3460) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\16D\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3460) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface |
| Operation: | write | Name: | ShowPassword |
Value: 0 | |||
| (PID) Process: | (3460) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\virtio_ivshmem_master_build.zip | |||
| (PID) Process: | (3460) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\Win7-KB3191566-x86.zip | |||
| (PID) Process: | (3460) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\phacker.zip | |||
| (PID) Process: | (3460) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (3460) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (3460) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (3460) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (3460) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
Executable files
1
Suspicious files
13
Text files
1 368
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3460 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXb3460.47446\Roblox Game Manager\Data\ached\axinite\benjoinPartile\aboding.xml | xml | |
MD5:E62A04307D5E1AADE6D6F3F99CB6E2BD | SHA256:06B3B01858339D87039781BCE1324981768E0D617993A3F51B5EA33A4D404CB8 | |||
| 3460 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXb3460.47446\Roblox Game Manager\Data\ached\axinite\inialJomon\mahoesBummiePawns.xml | xml | |
MD5:77C878D245E5191E4F91FBD2437E13FC | SHA256:4C5C3260377C4004A3B431EAEBCB9A6764EA4CB18CD2BC0BAD6C8907541D8DFA | |||
| 3460 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXb3460.47446\Roblox Game Manager\Data\ached\axinite\bismerAfoot\refines.xml | xml | |
MD5:5A856C6B9B0AF741F9B6B4FED44C0EC5 | SHA256:740C54122F1DE664CAC6DCCFBE4DAC8FEFFFCFC07E9C61600AF29A6A0E6BF5AA | |||
| 3460 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXb3460.47446\Roblox Game Manager\Data\ached\axinite\benjoinPartile\fancied.xml | xml | |
MD5:53852EA8C50BE1BD473E69674B2EA282 | SHA256:FC0C301D9CA63F69EEB6F30E79E6EB227A355031EB54D6891503A9DE1D5491AD | |||
| 3460 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXb3460.47446\Roblox Game Manager\Data\ached\axinite\bismerAfoot\viraWebbedBossies.xml | xml | |
MD5:A0F40B5AC4872A26943F67F1132816FD | SHA256:A4887D317901BBA07453C509546E71B9D2BA466B68CB9EA076123ACB982D26BF | |||
| 3460 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXb3460.47446\Roblox Game Manager\Data\ached\axinite\inialJomon\splurt.xml | xml | |
MD5:75638DD2021C3C65F87C92022ED2C8C6 | SHA256:332C06B8C7DB769EC022DF4B0A5F81891AD438DC0F0B6EE859DF2F7ECA927876 | |||
| 3460 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXb3460.47446\Roblox Game Manager\Data\ached\axinite\benjoinPartile\pimpleJicaraJumpily.xml | xml | |
MD5:053447672F350A4196E75503383BE104 | SHA256:9505973060B88E2EF0D6C55132E89C1742187CC6B4B944EC76203137C1C17AB7 | |||
| 3460 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXb3460.47446\Roblox Game Manager\Data\ached\axinite\bismerAfoot\ikonsStorage.xml | xml | |
MD5:EBA101F727D30A725F464878E2278926 | SHA256:19519B252B584B4992732F26D258605C0D9D63F883420D1AB4BEE188FD6D762B | |||
| 3460 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXb3460.47446\Roblox Game Manager\Data\ached\axinite\ovoidalParers.xml | xml | |
MD5:81A92A3DF3826262EE836ADC5B3EDBFE | SHA256:7AA2B8FFEEE3FCAC748430FAF88C3B8B801E78F67F76050D72162CD0513955BF | |||
| 3460 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXb3460.47446\Roblox Game Manager\Data\ached\axinite\inialJomon\limplyMorfond.xml | xml | |
MD5:EC331637A472239F7D472F13C9E835BD | SHA256:D1FB81152A2909862D1CF6C19E68765E3545096D12E35A47E25BF527A90E9519 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
1
TCP/UDP connections
9
DNS requests
0
Threats
39
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3604 | powershell.exe | GET | 200 | 89.23.96.203:80 | http://89.23.96.203/dashboard/1/trashcr.exe | RU | executable | 271 Kb | malicious |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
1076 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
2400 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
3792 | powershell.exe | 89.23.96.203:80 | — | LLC Smart Ape | RU | malicious |
2476 | vbc.exe | 94.142.138.105:15111 | — | Network Management Ltd | RU | malicious |
3604 | powershell.exe | 89.23.96.203:80 | — | LLC Smart Ape | RU | malicious |
796 | vbc.exe | 94.142.138.105:15111 | — | Network Management Ltd | RU | malicious |
DNS requests
Threats
PID | Process | Class | Message |
|---|---|---|---|
3792 | powershell.exe | Potentially Bad Traffic | ET INFO Executable Download from dotted-quad Host |
3792 | powershell.exe | Not Suspicious Traffic | ET INFO Windows Powershell User-Agent Usage |
3792 | powershell.exe | Misc activity | ET INFO Request for EXE via Powershell |
3792 | powershell.exe | Potential Corporate Privacy Violation | ET POLICY PE EXE or DLL Windows file download HTTP |
3792 | powershell.exe | Potentially Bad Traffic | ET HUNTING SUSPICIOUS Dotted Quad Host MZ Response |
3604 | powershell.exe | Potentially Bad Traffic | ET INFO Executable Download from dotted-quad Host |
3604 | powershell.exe | Not Suspicious Traffic | ET INFO Windows Powershell User-Agent Usage |
3604 | powershell.exe | Misc activity | ET INFO Request for EXE via Powershell |
3604 | powershell.exe | Potential Corporate Privacy Violation | ET POLICY PE EXE or DLL Windows file download HTTP |
3604 | powershell.exe | Potentially Bad Traffic | ET HUNTING SUSPICIOUS Dotted Quad Host MZ Response |