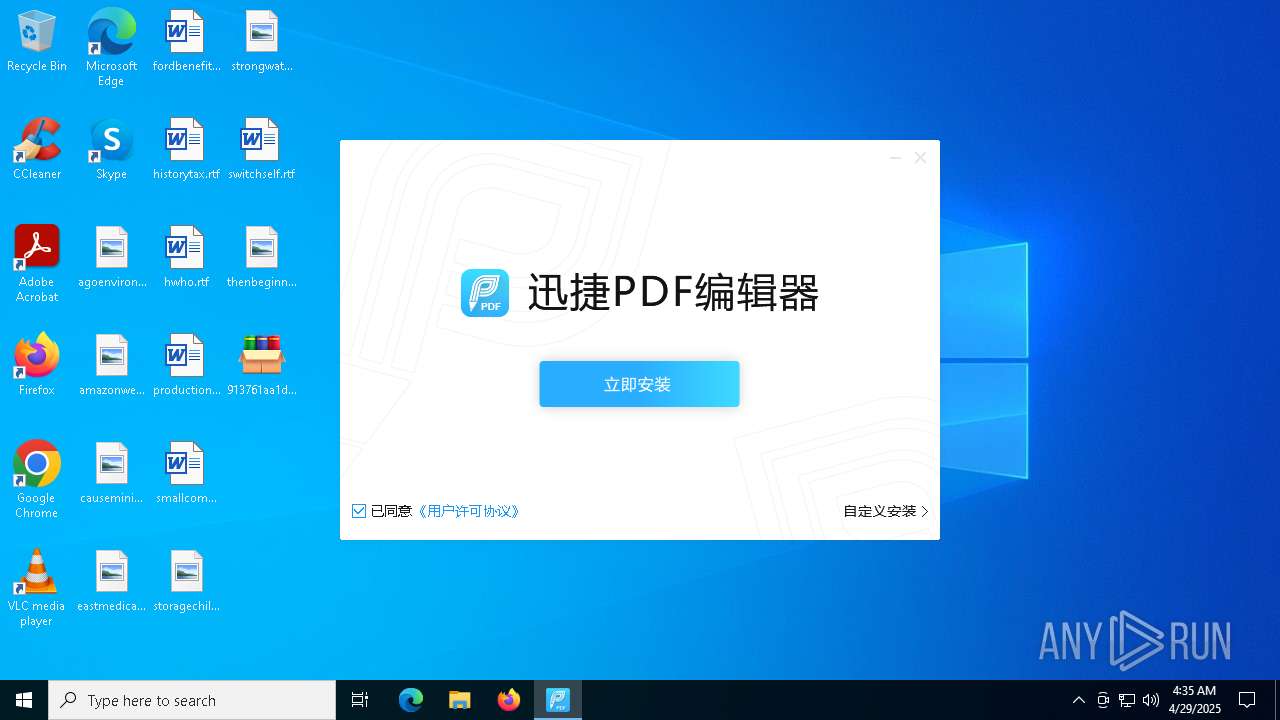
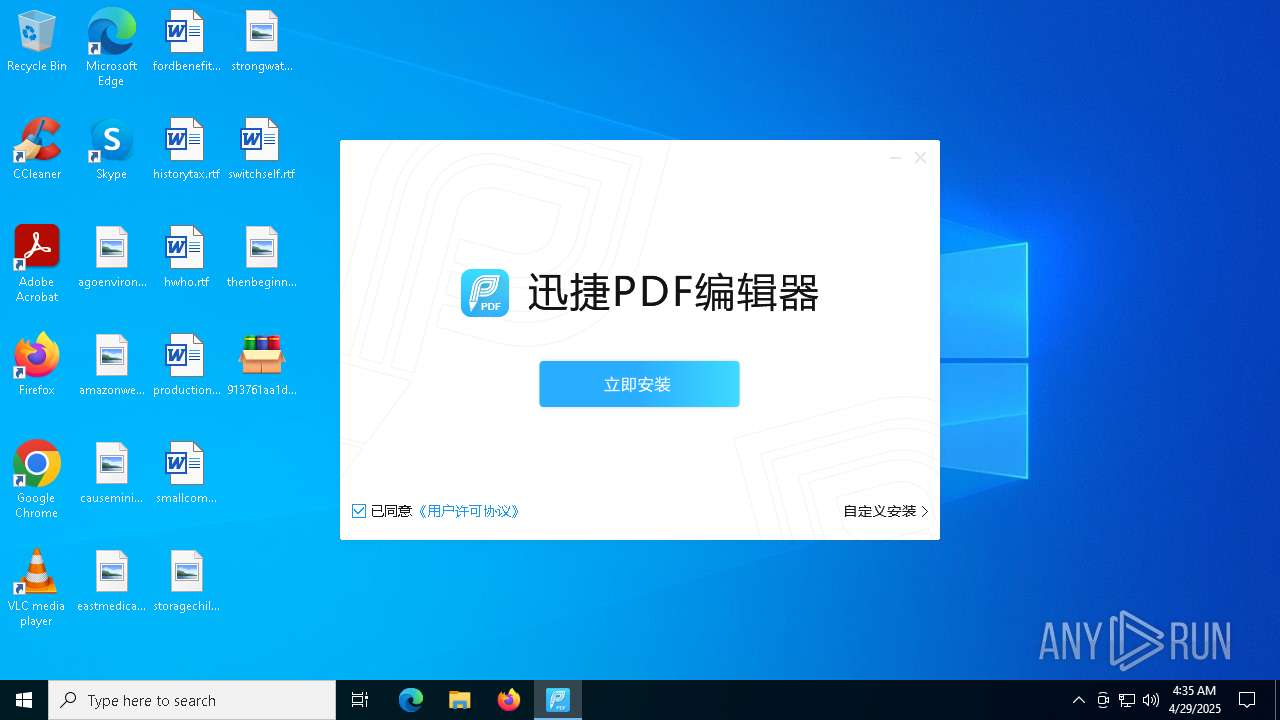
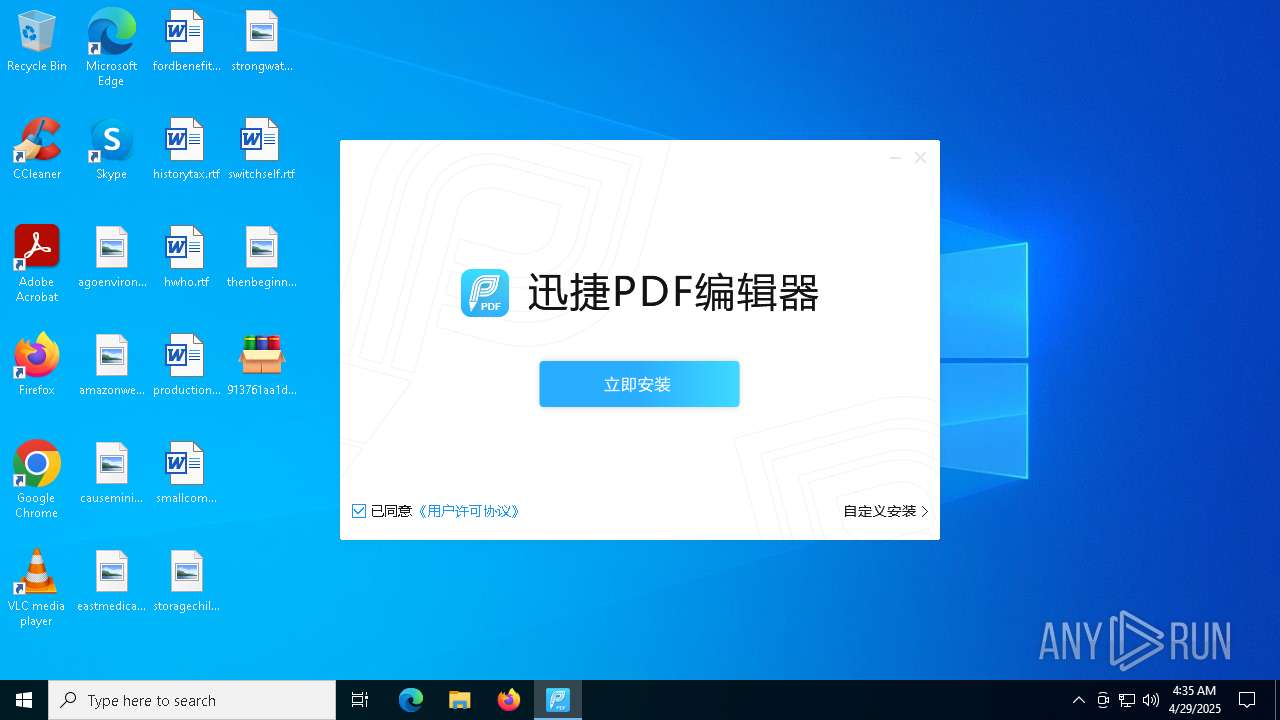
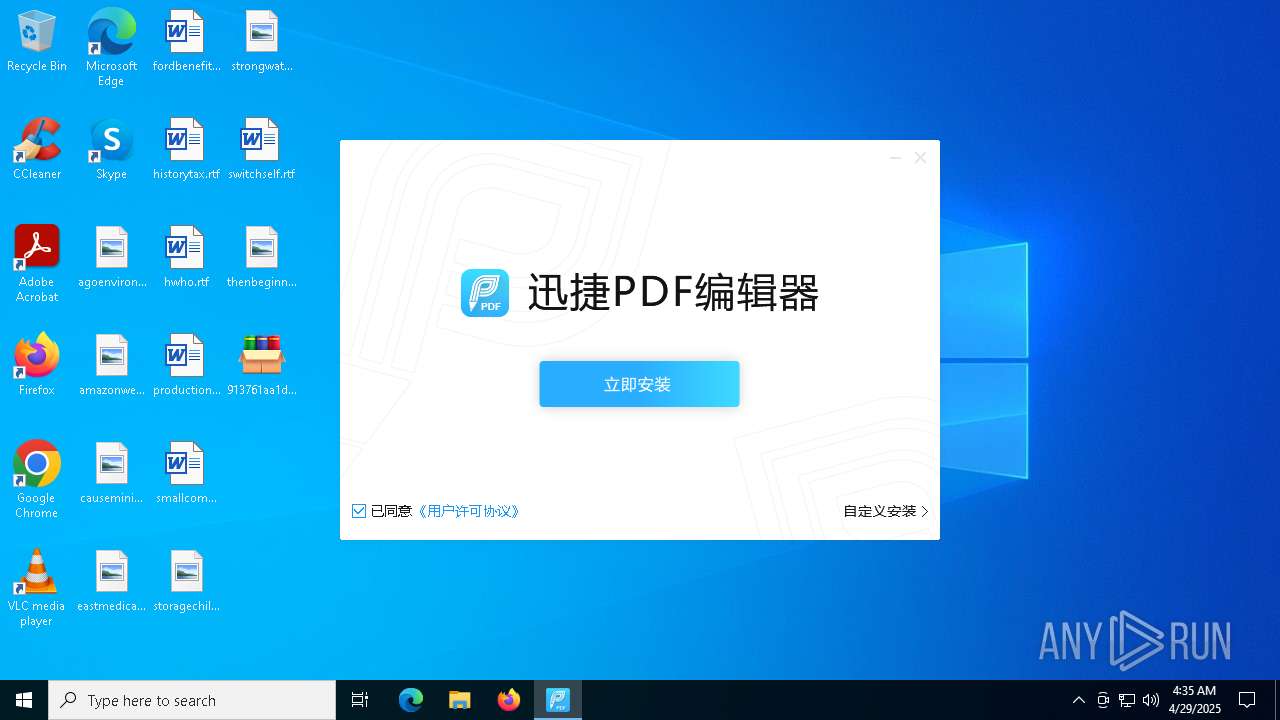
| File name: | 913761aa1d80264ac127390b251cdaeb914e7d70065e17276af15e51689c8d4f |
| Full analysis: | https://app.any.run/tasks/6fc3fff5-e859-462d-aa8e-80be1f86dbc5 |
| Verdict: | Malicious activity |
| Analysis date: | April 29, 2025, 04:34:14 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32+ executable (GUI) x86-64, for MS Windows, 7 sections |
| MD5: | 901051CE70DD7E1BF23B1BA9FD90E93B |
| SHA1: | 233CE83C51800CB1802374CB3312EA2FF4CDE45D |
| SHA256: | 913761AA1D80264AC127390B251CDAEB914E7D70065E17276AF15E51689C8D4F |
| SSDEEP: | 98304:RrL6kpKX8ALif0aZBdQcC7PW9+4ksPfO9KgxI3hIwctBCZTgYQUTxJnD6krSwJlm:Q |
MALICIOUS
METASPLOIT has been detected (YARA)
- cmd.exe (PID: 6192)
SUSPICIOUS
Executable content was dropped or overwritten
- 913761aa1d80264ac127390b251cdaeb914e7d70065e17276af15e51689c8d4f.exe (PID: 920)
Reads security settings of Internet Explorer
- 913761aa1d80264ac127390b251cdaeb914e7d70065e17276af15e51689c8d4f.exe (PID: 920)
Connects to unusual port
- cmd.exe (PID: 6192)
The process creates files with name similar to system file names
- 913761aa1d80264ac127390b251cdaeb914e7d70065e17276af15e51689c8d4f.exe (PID: 920)
Reads the date of Windows installation
- 913761aa1d80264ac127390b251cdaeb914e7d70065e17276af15e51689c8d4f.exe (PID: 920)
INFO
Checks supported languages
- 913761aa1d80264ac127390b251cdaeb914e7d70065e17276af15e51689c8d4f.exe (PID: 920)
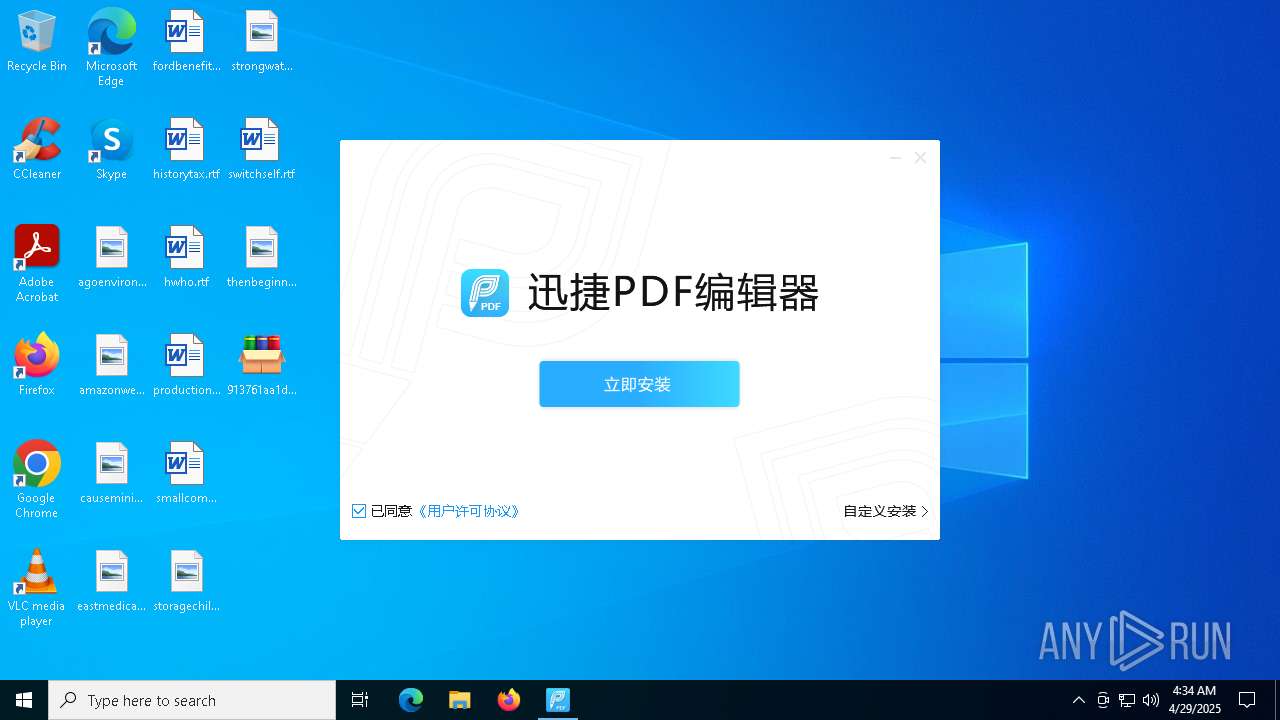
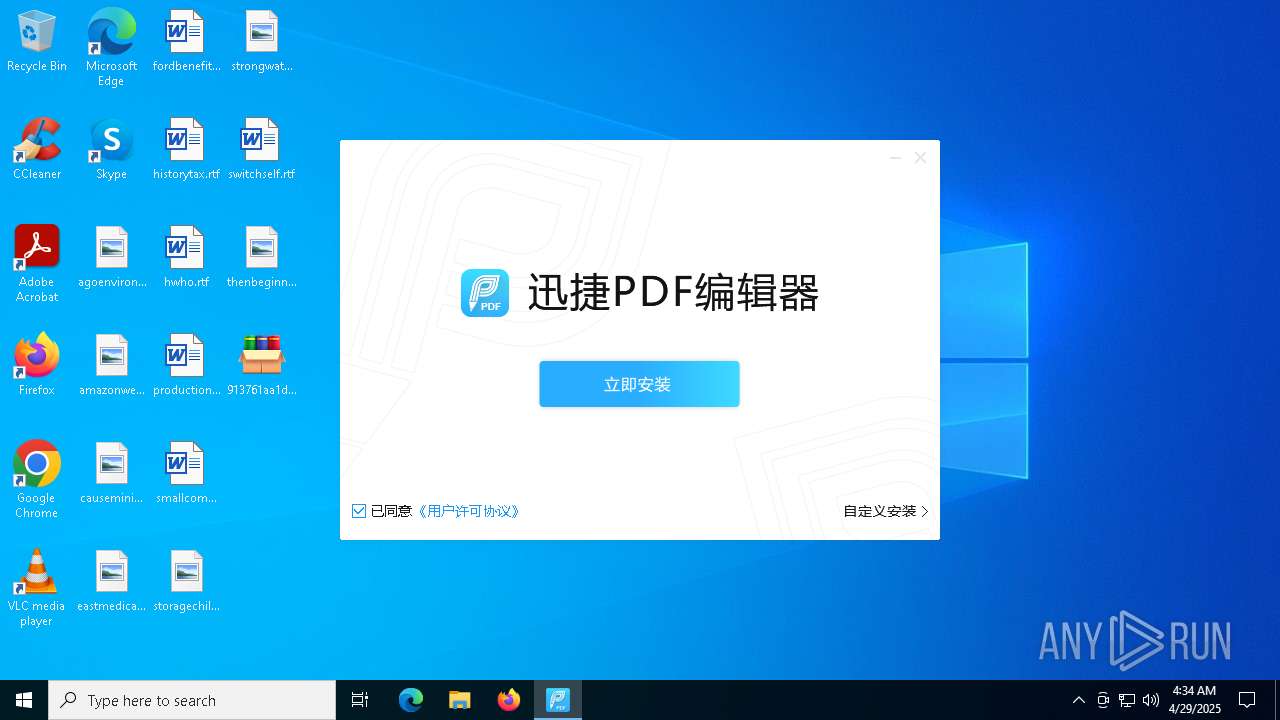
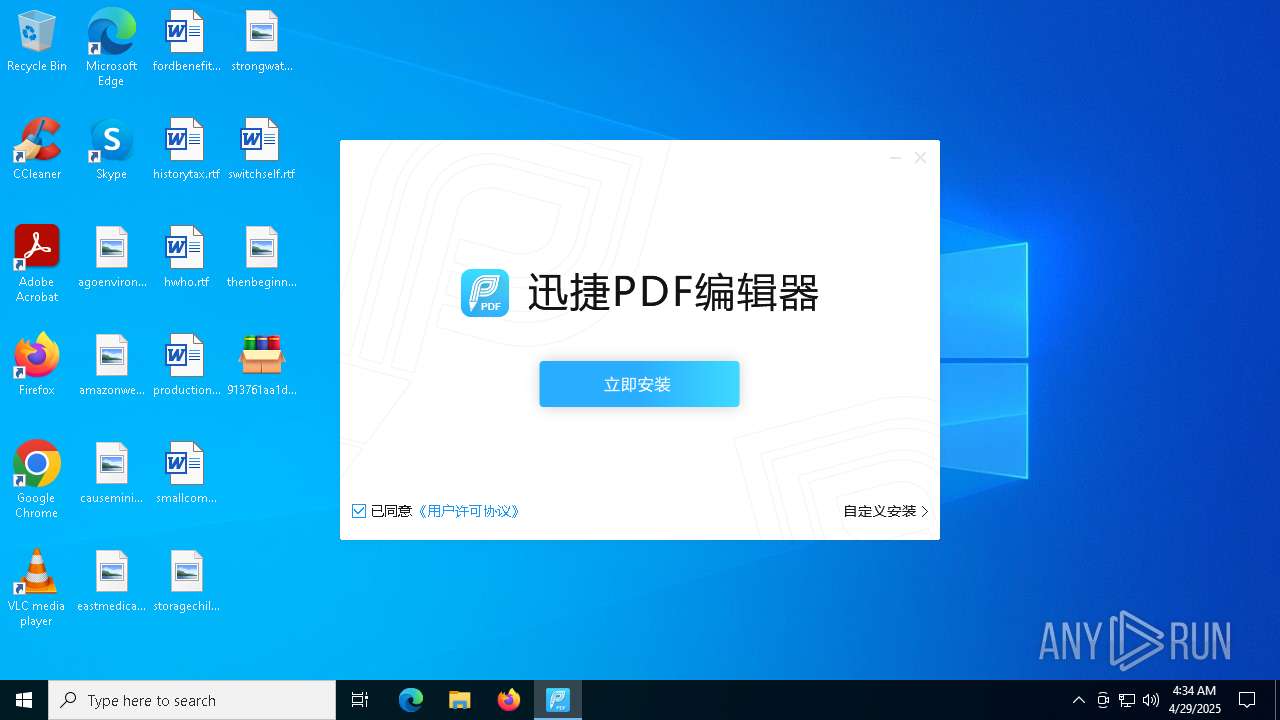
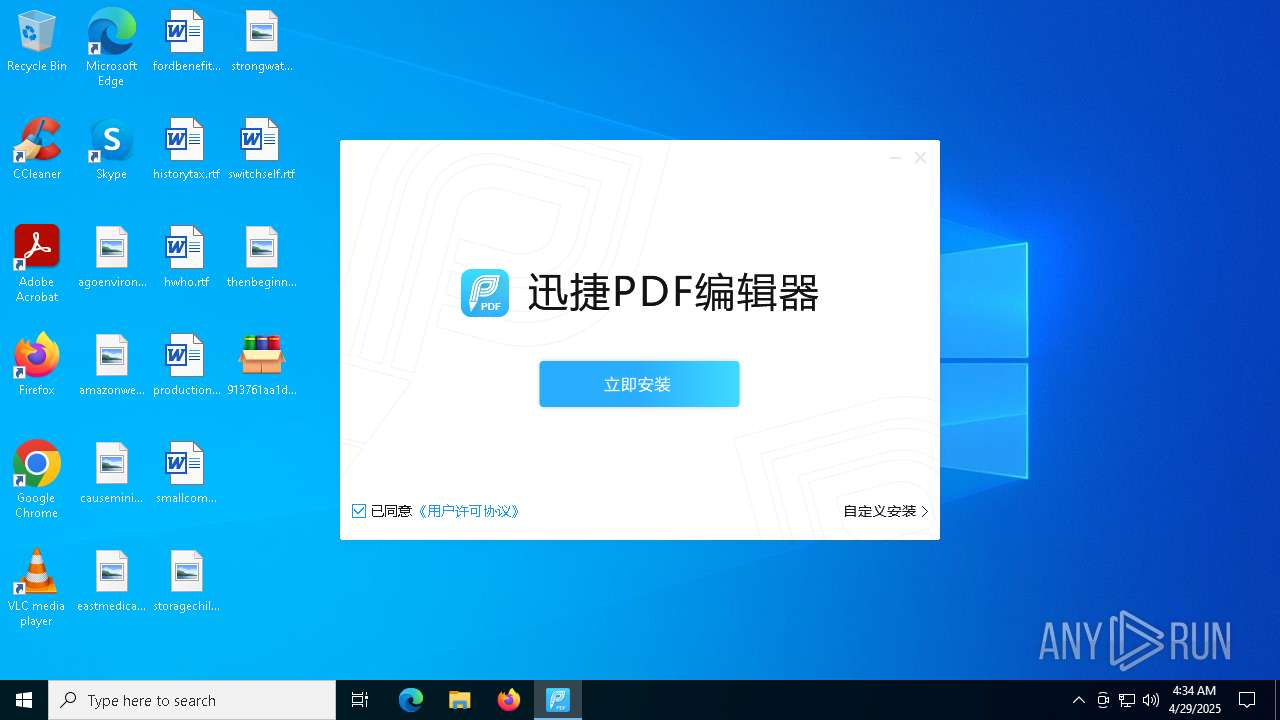
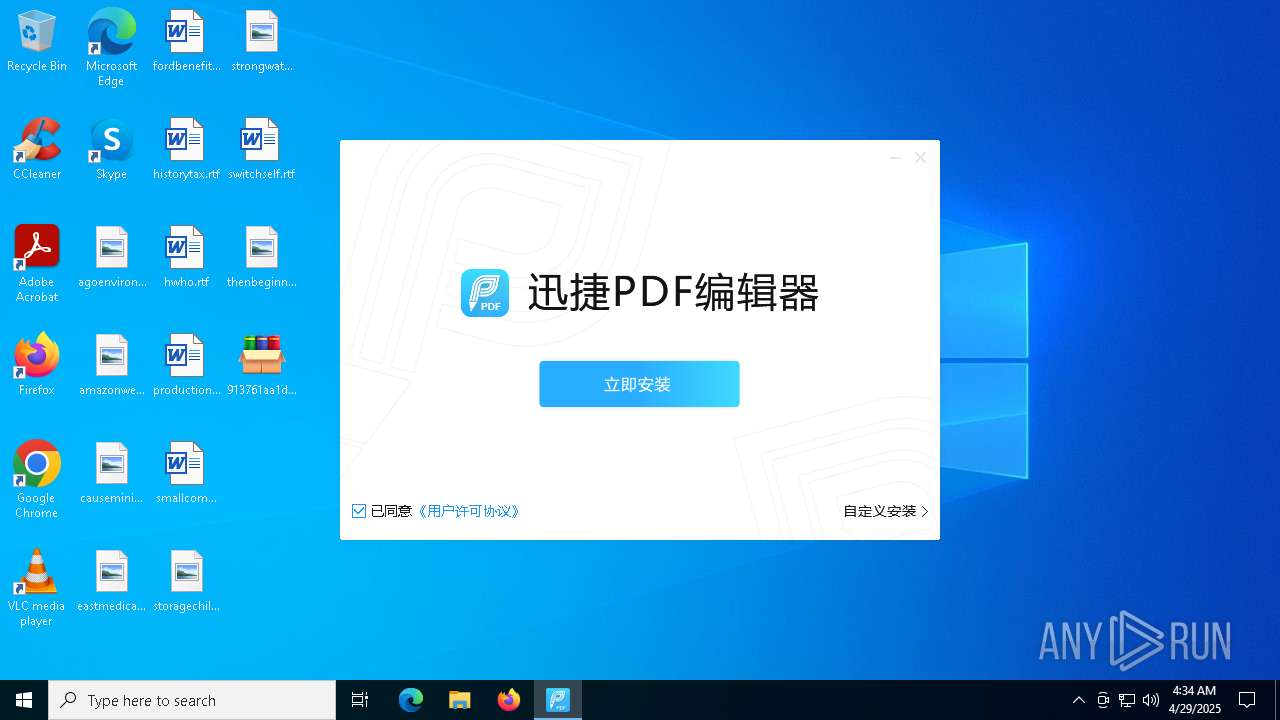
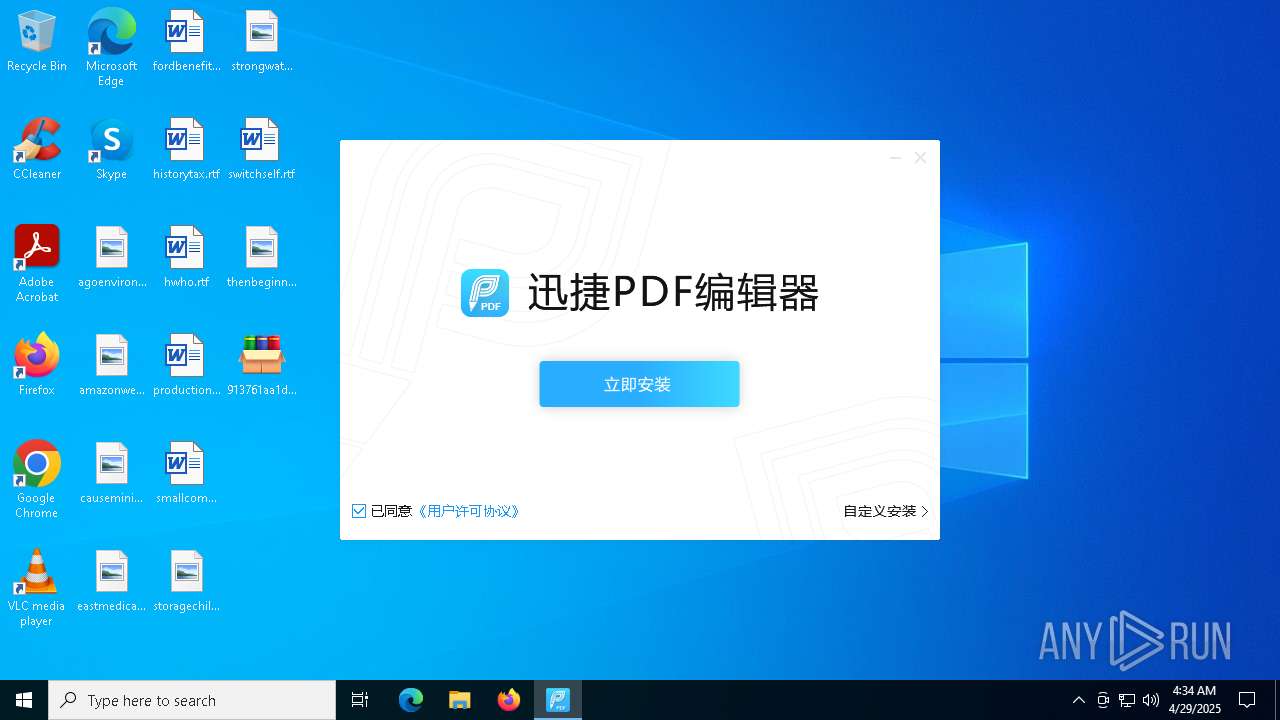
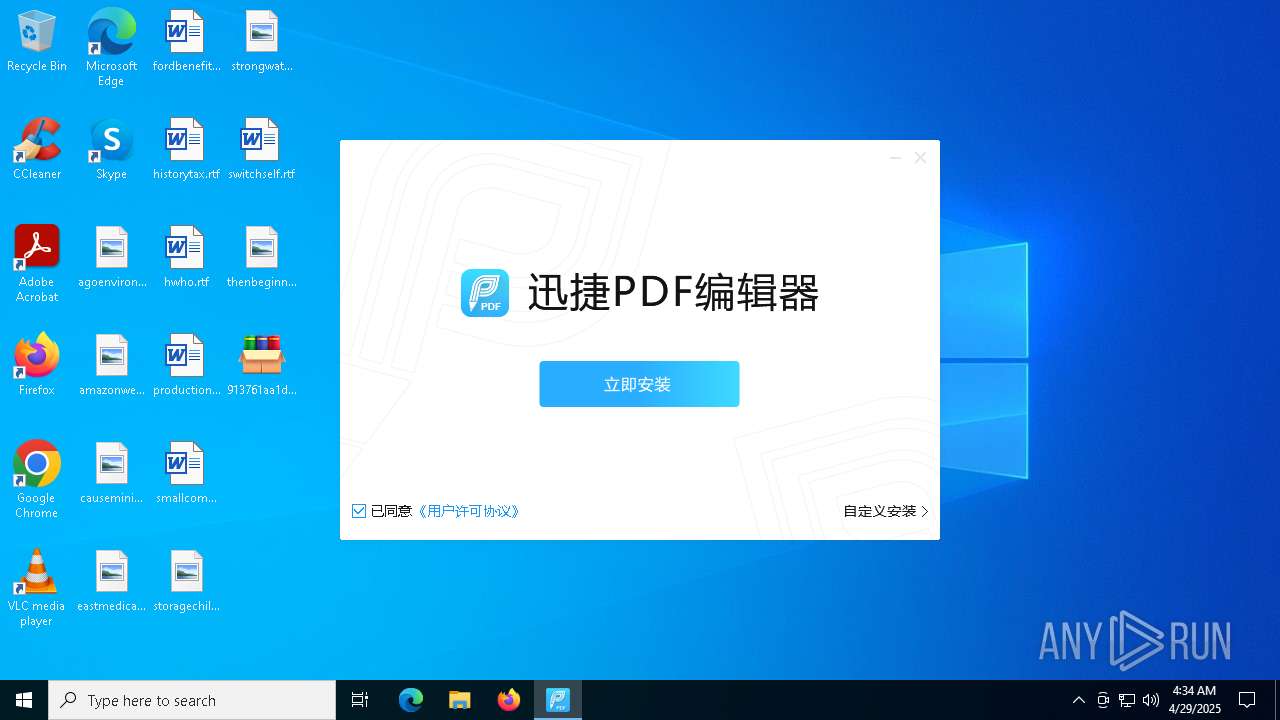
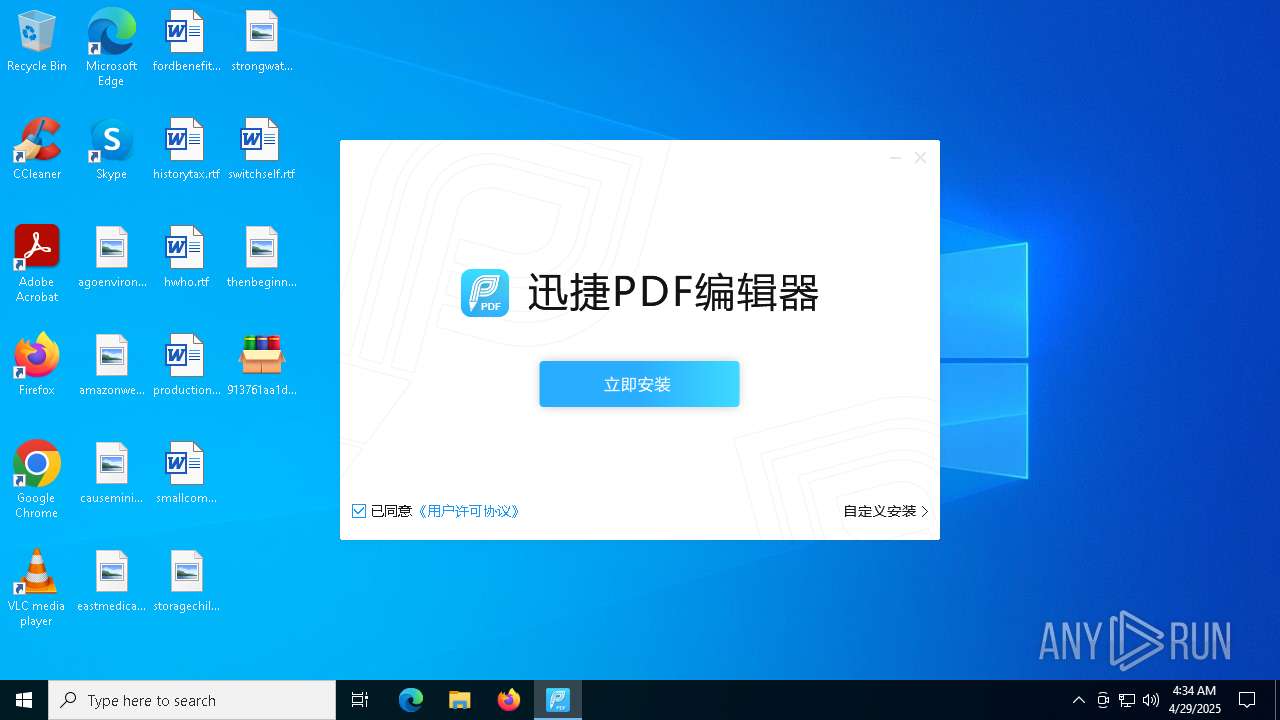
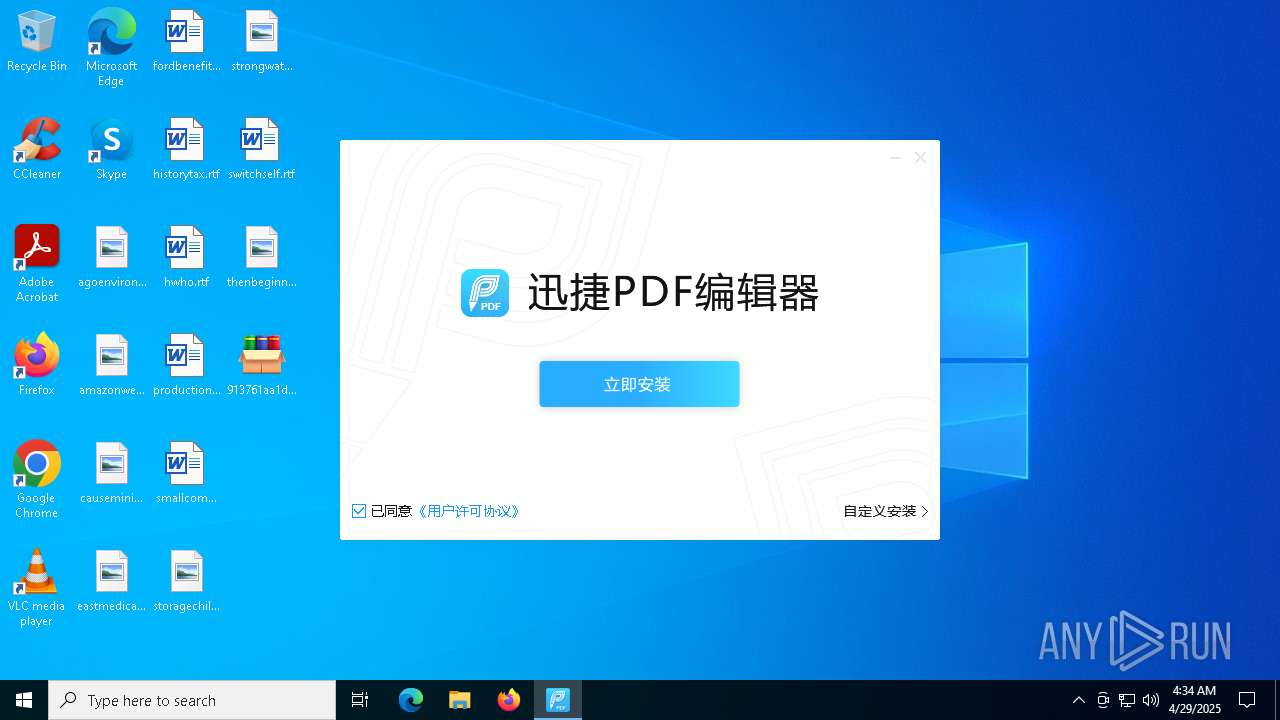
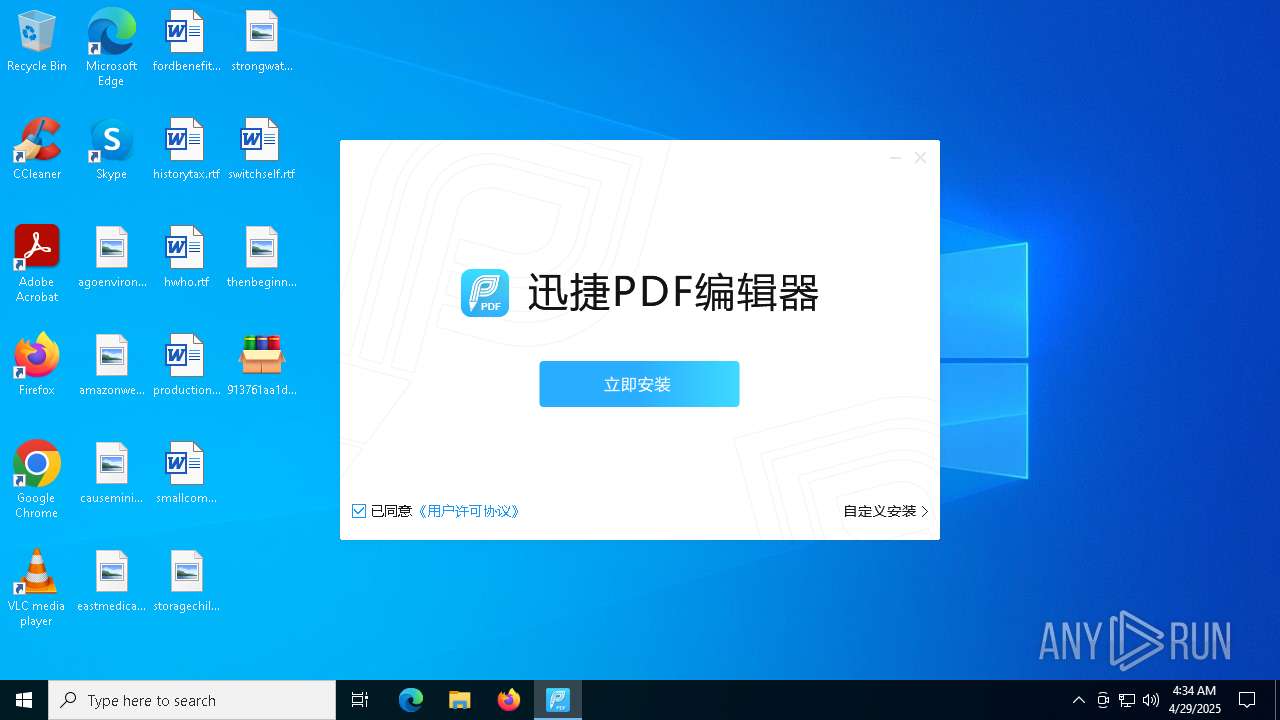
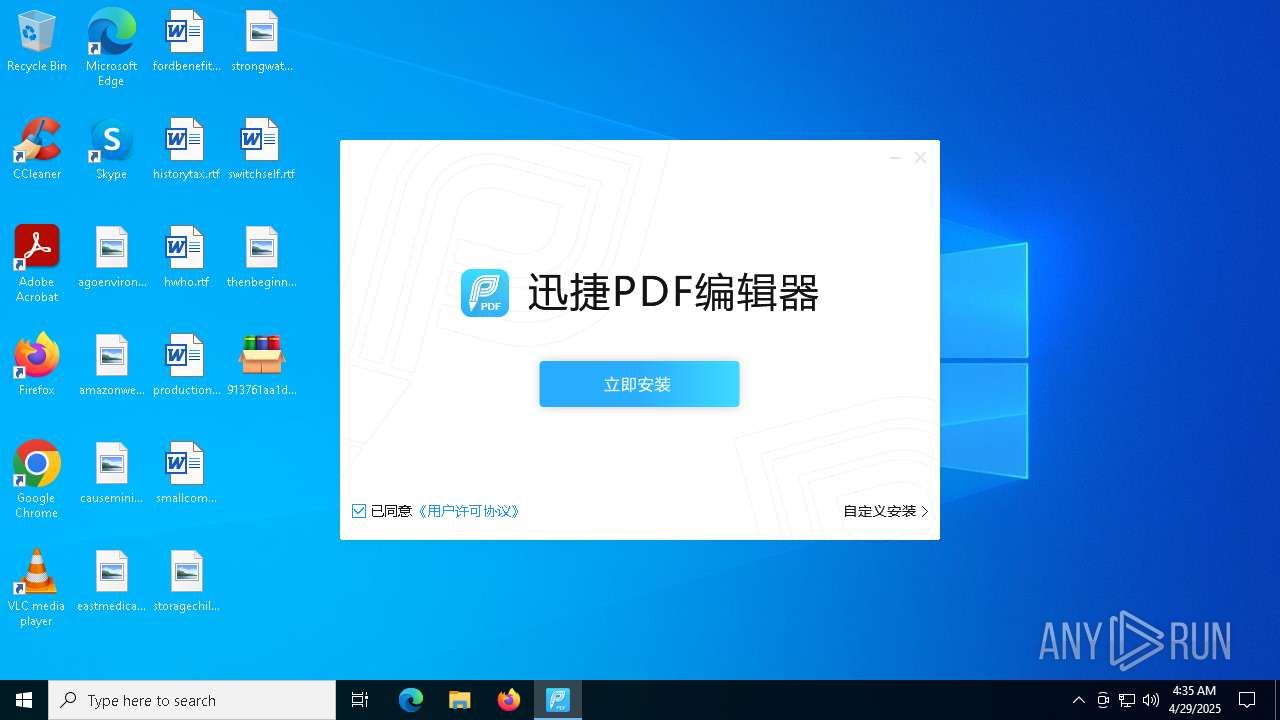
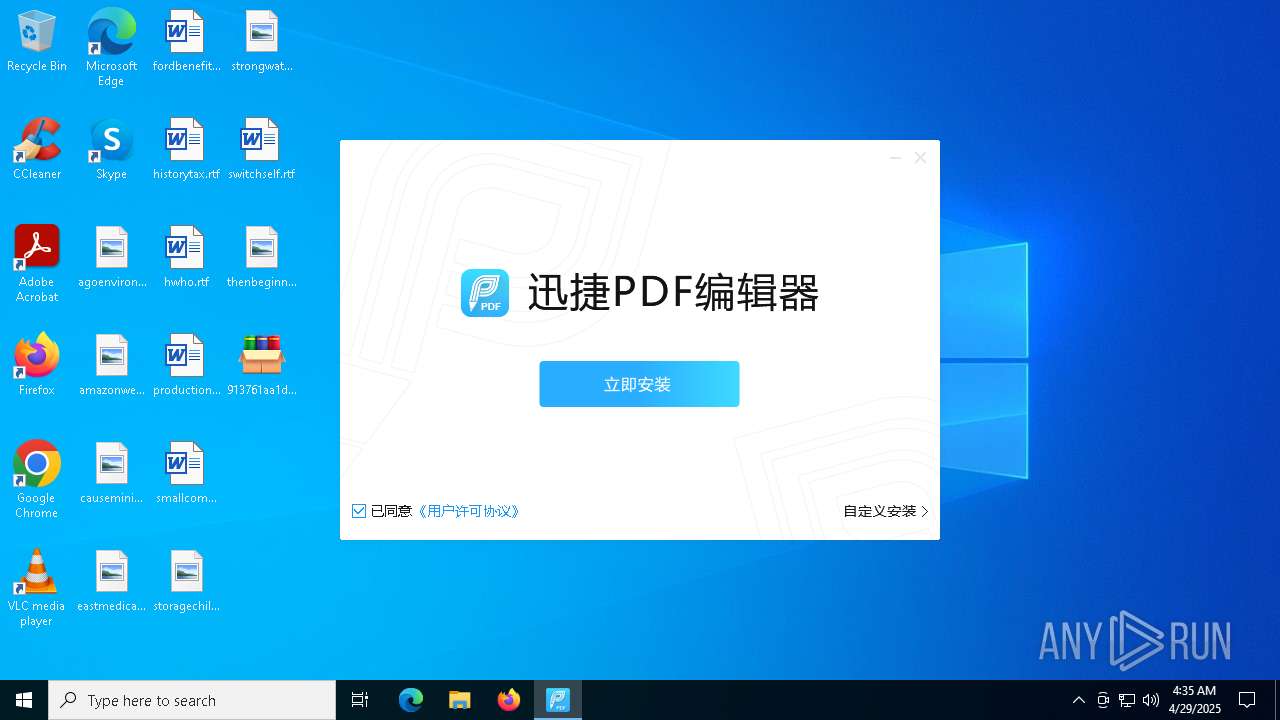
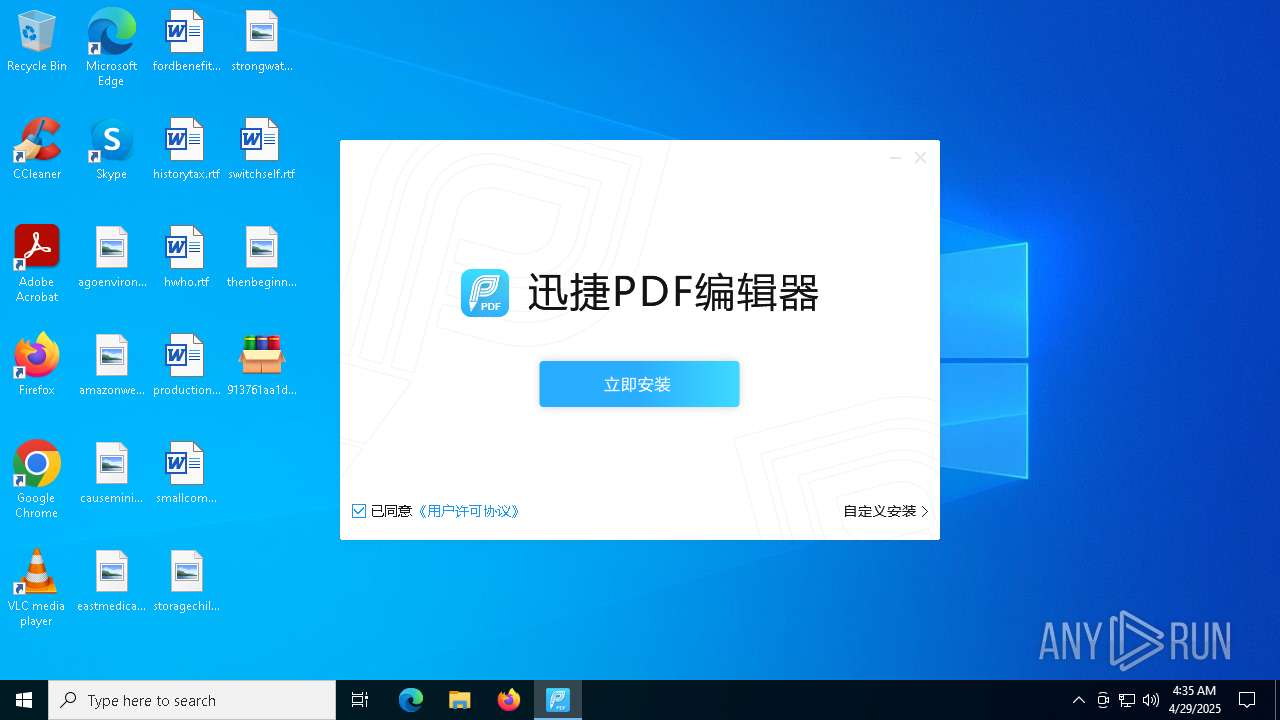
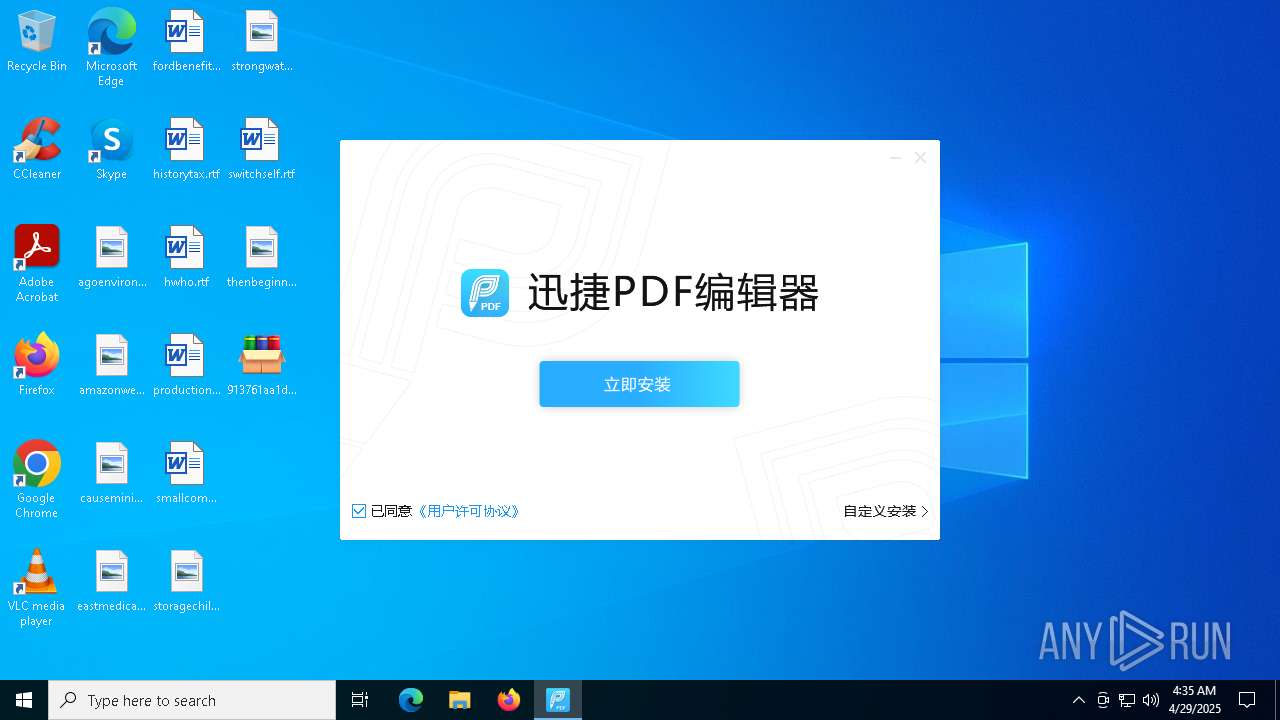
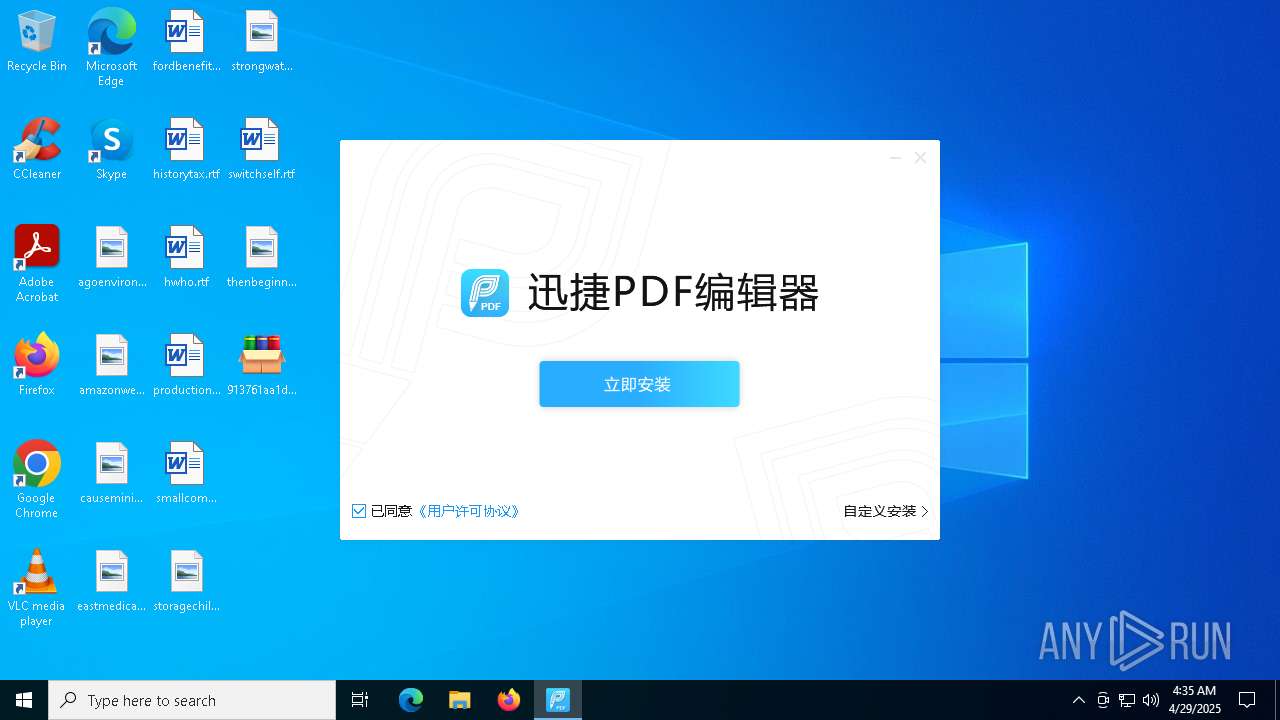
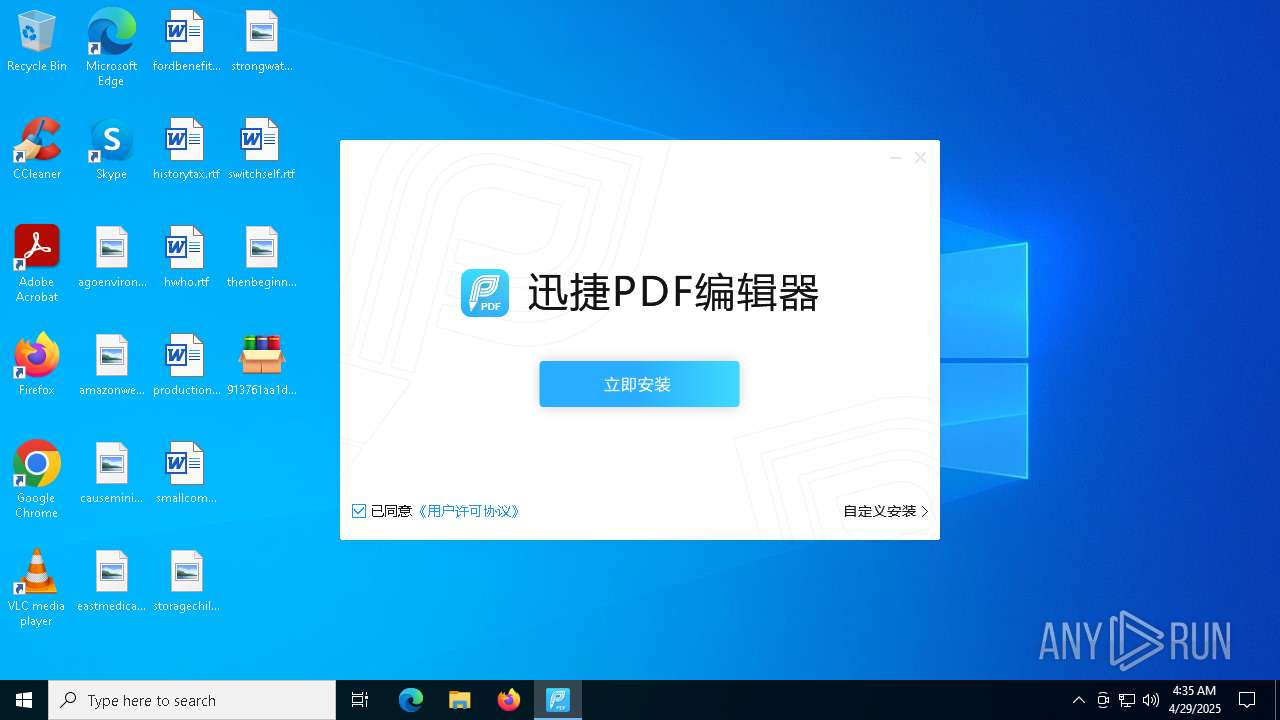
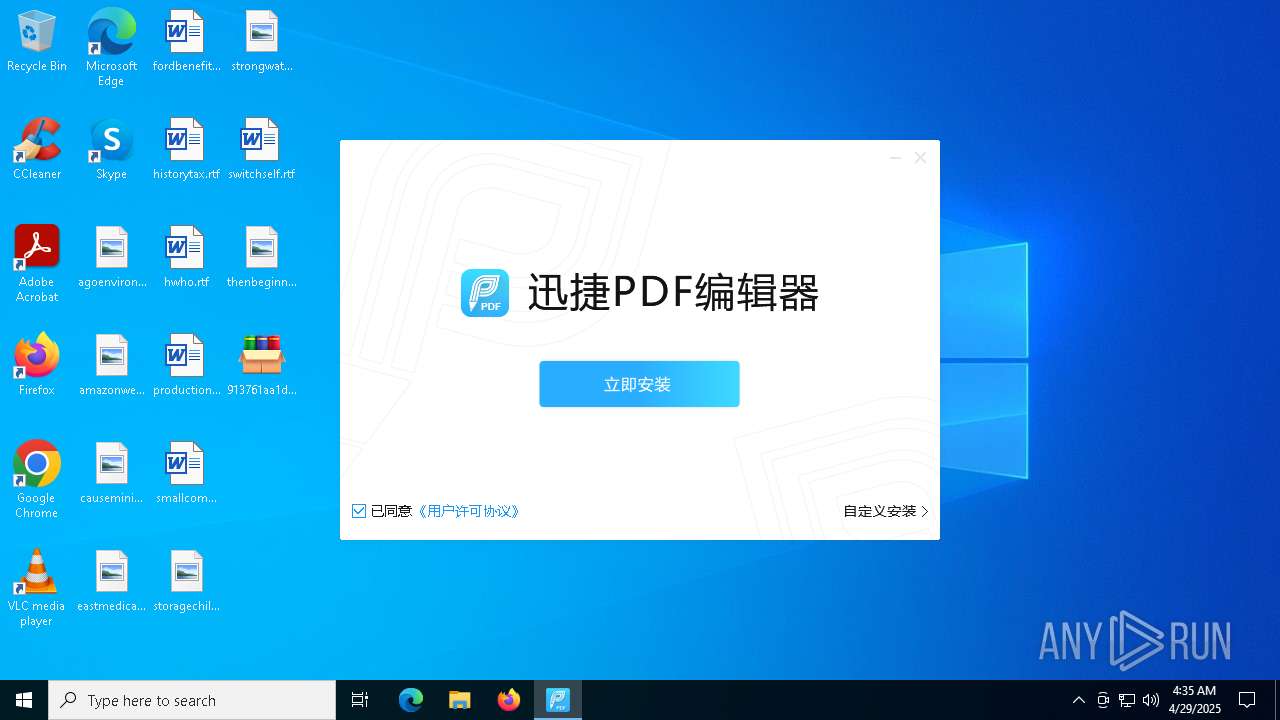
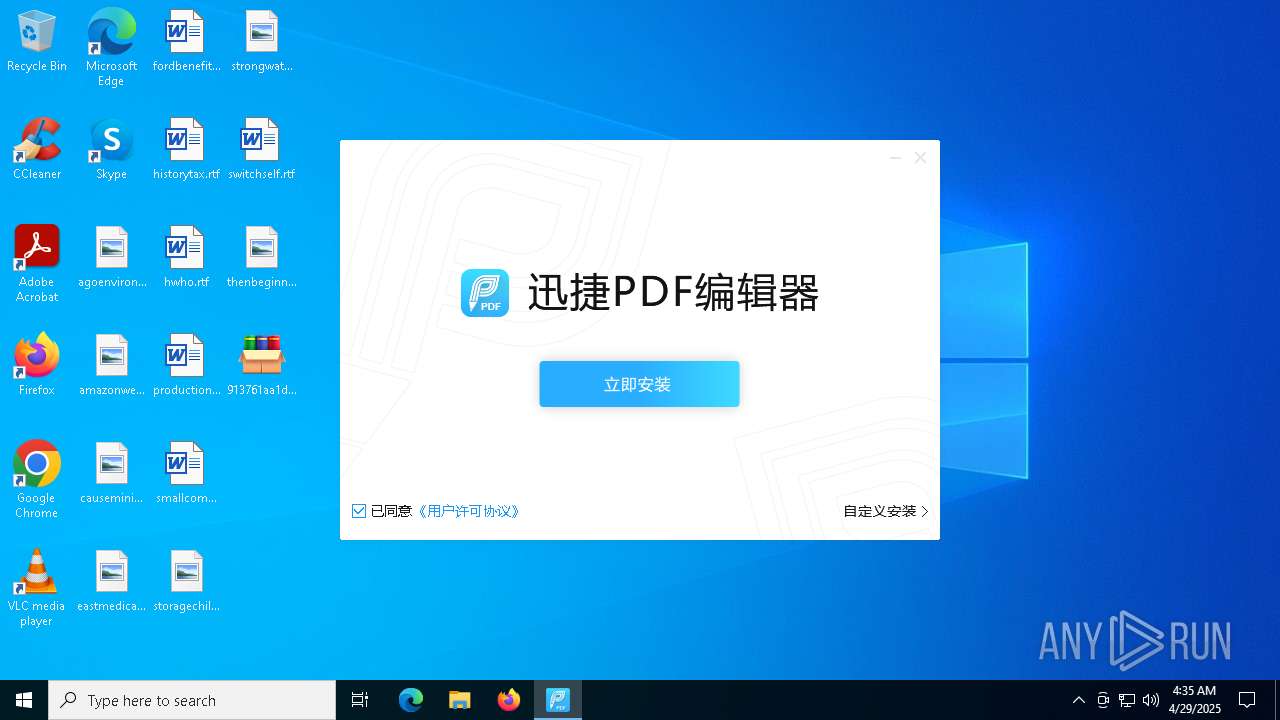
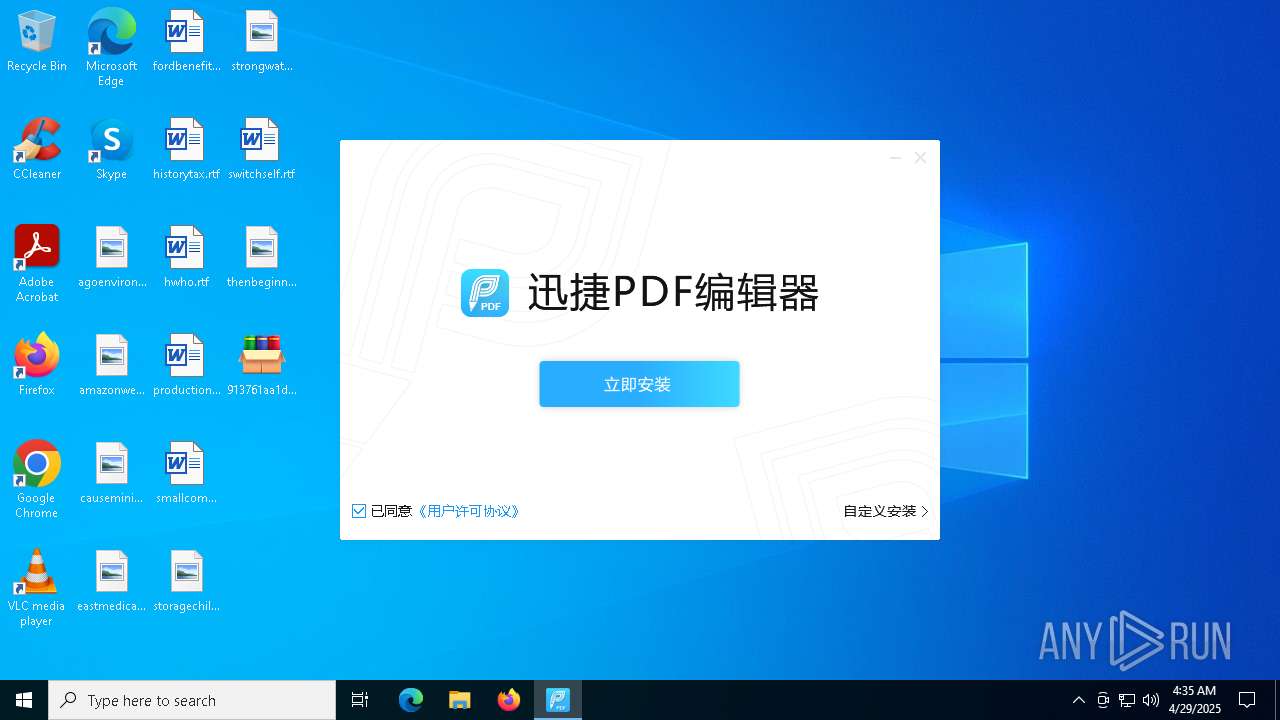
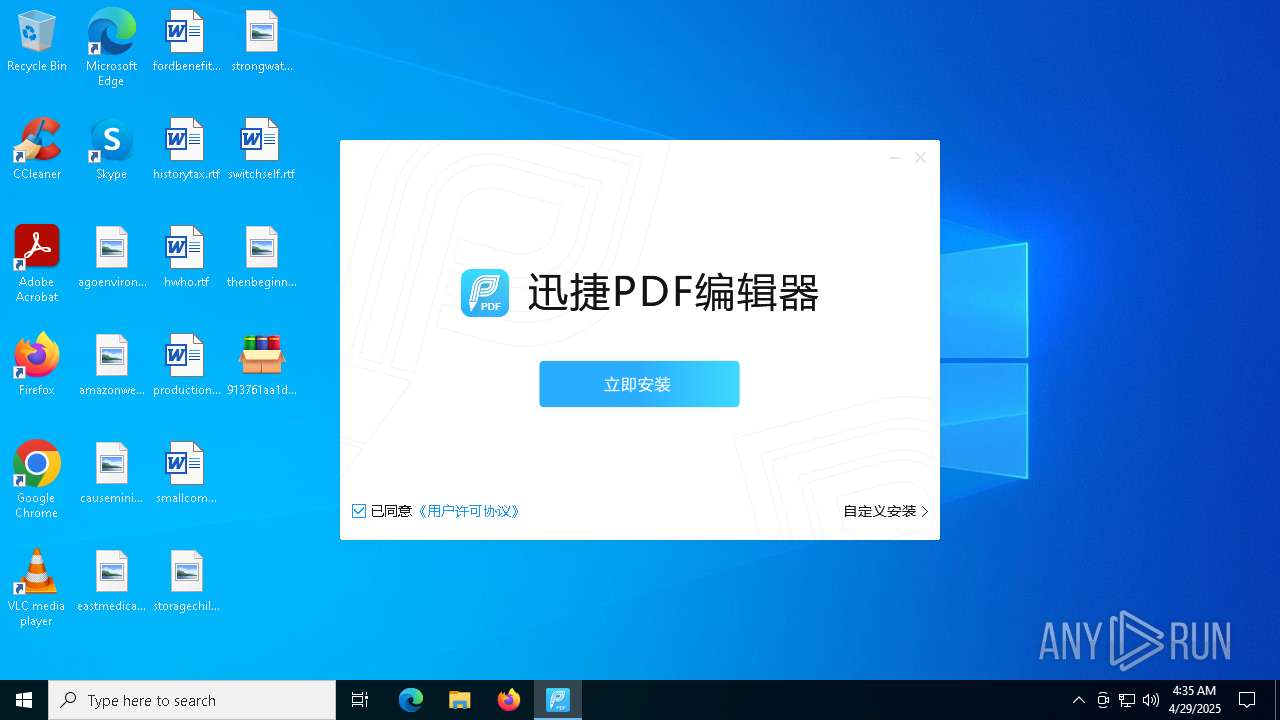
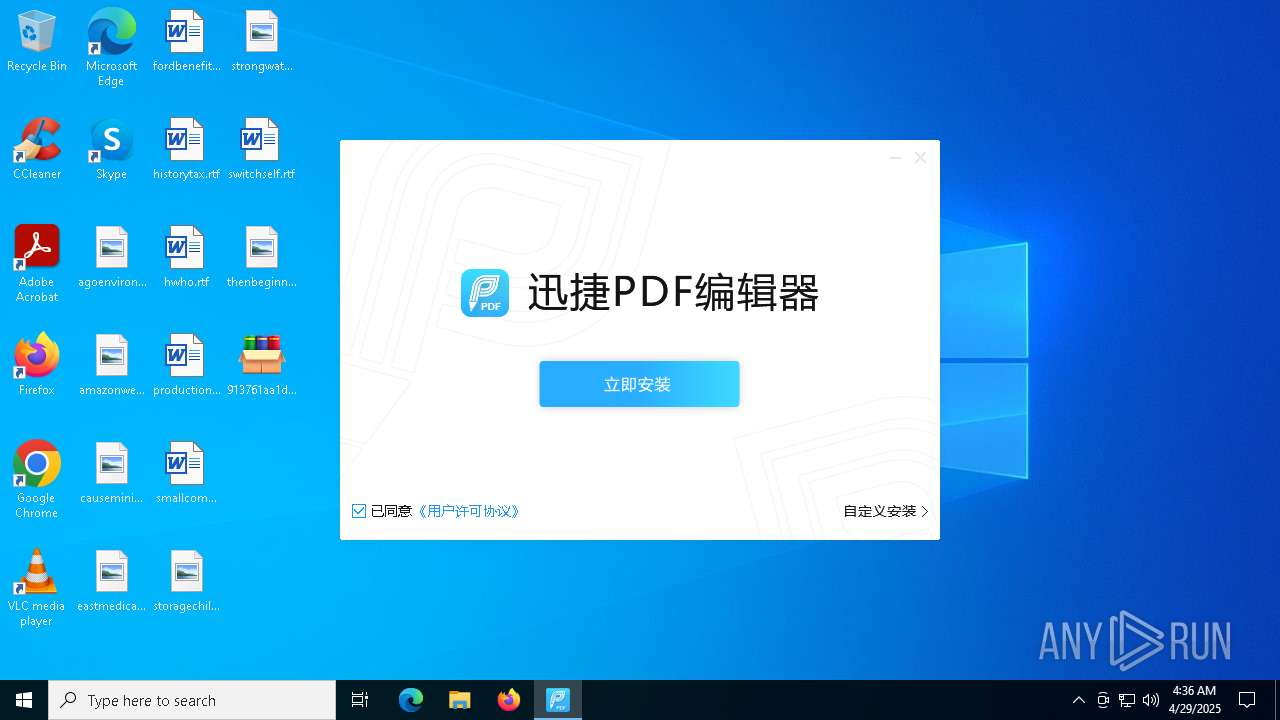
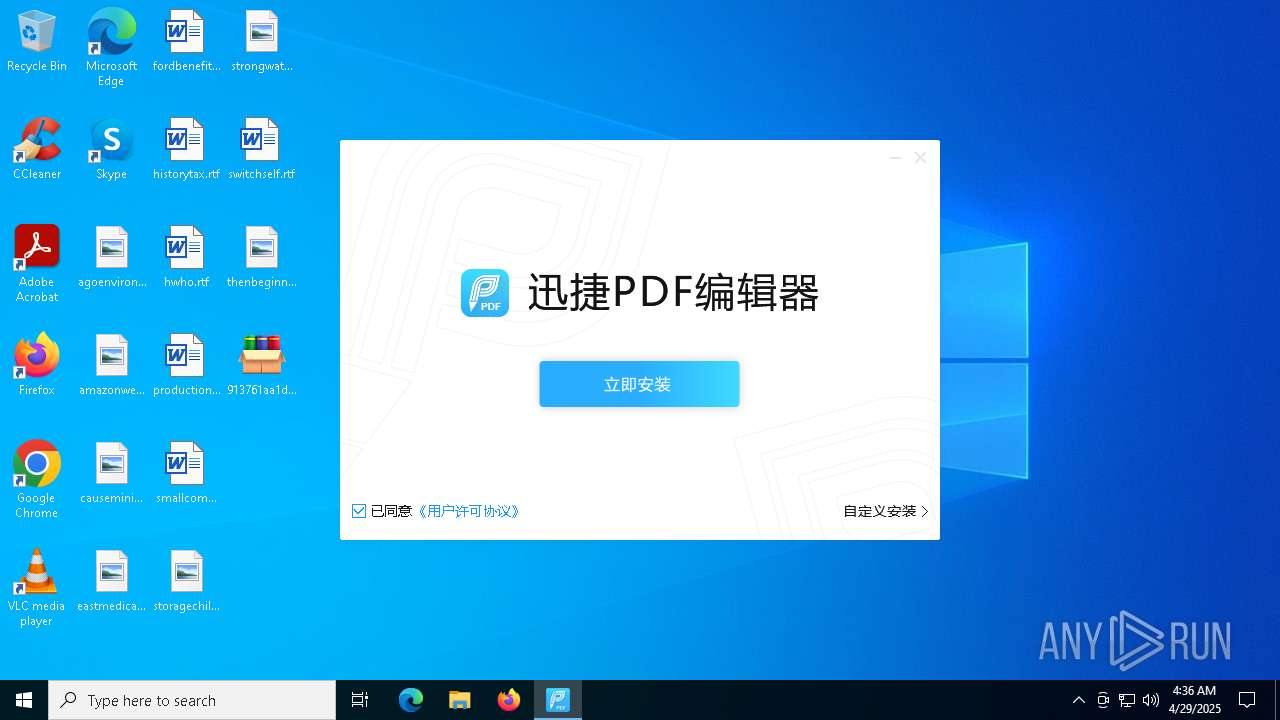
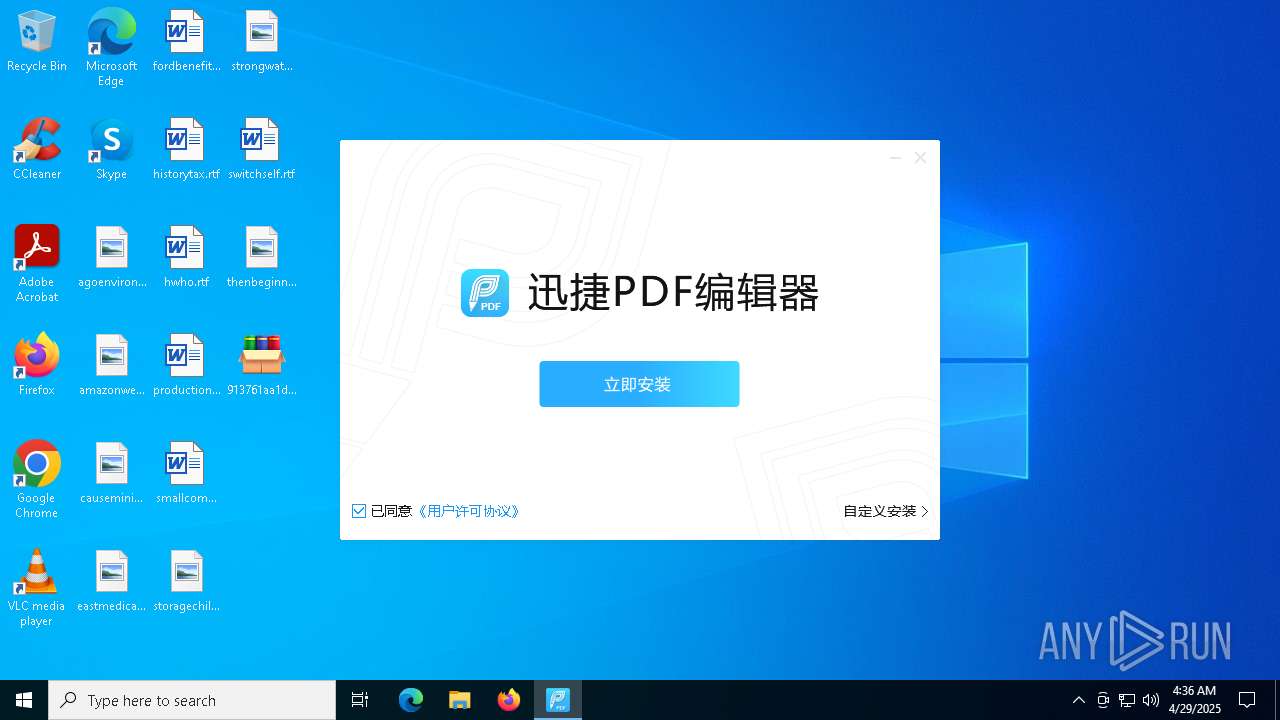
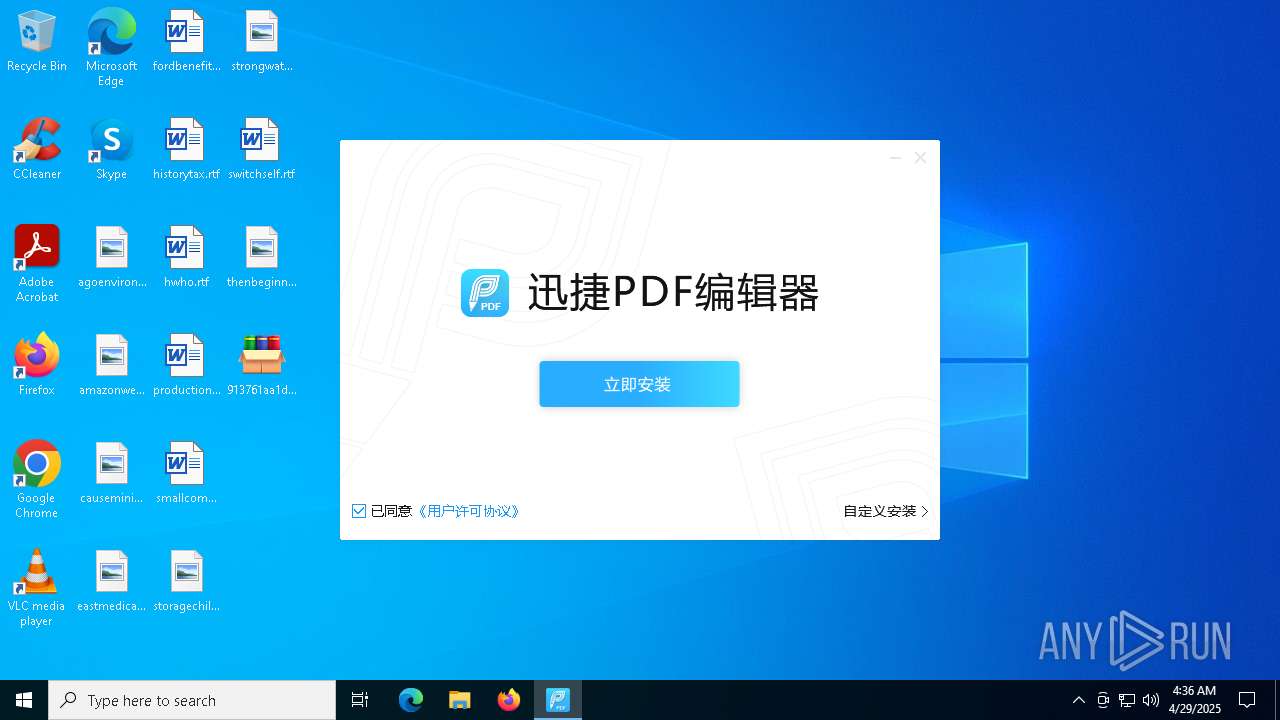
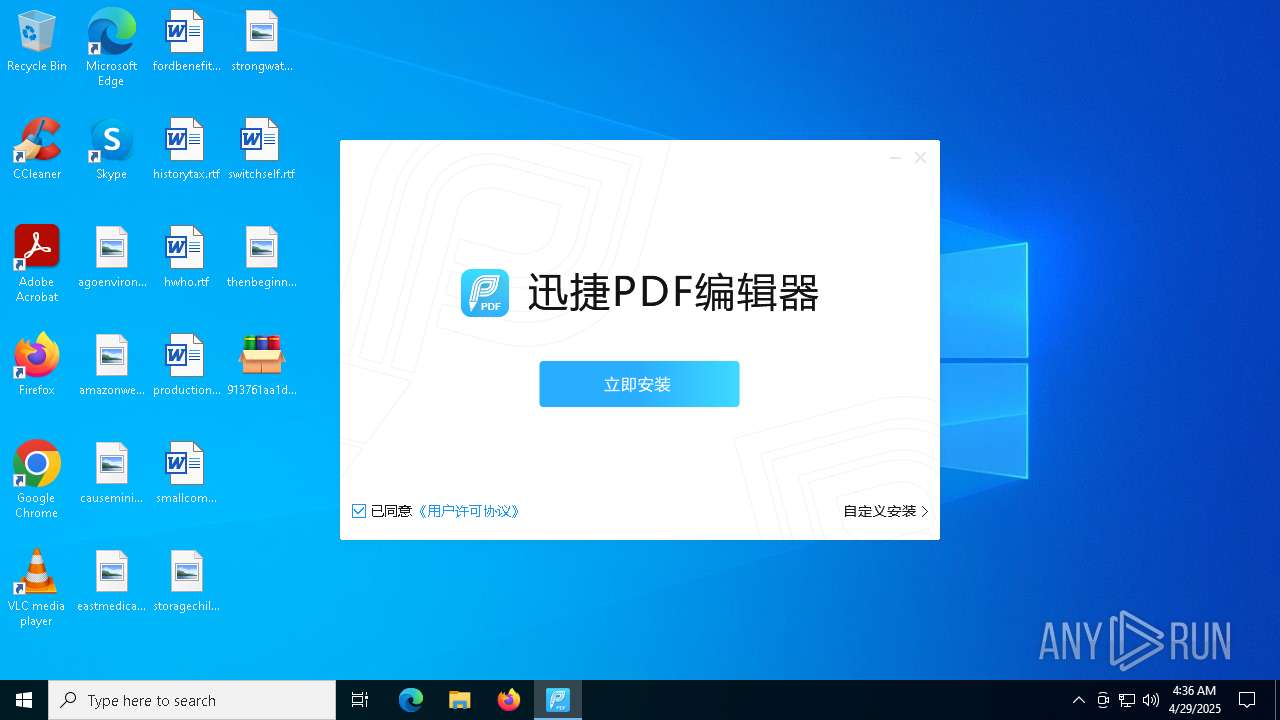
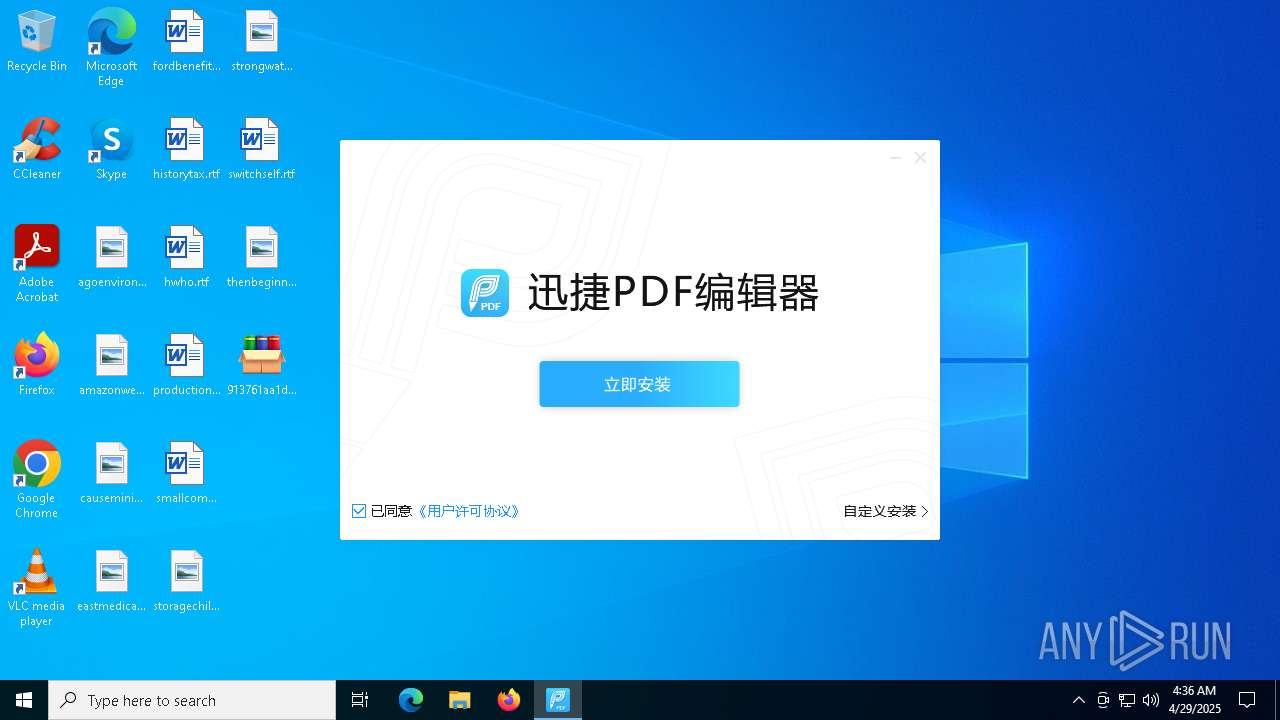
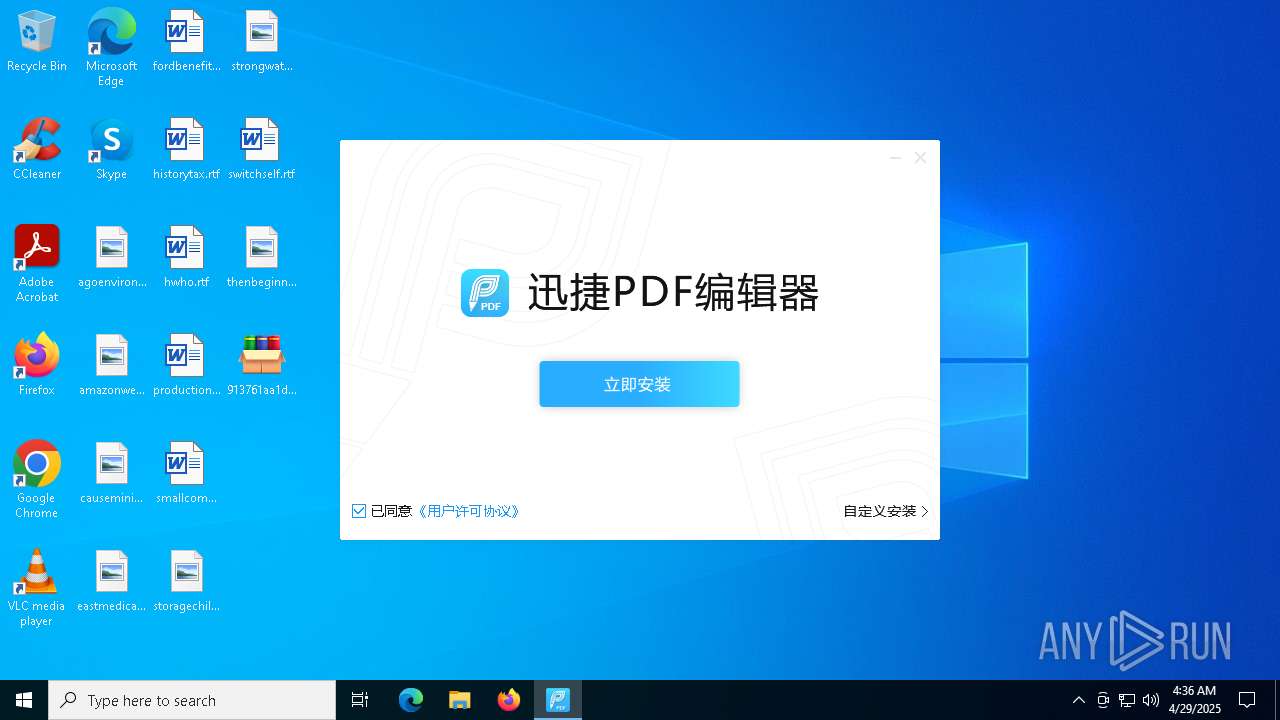
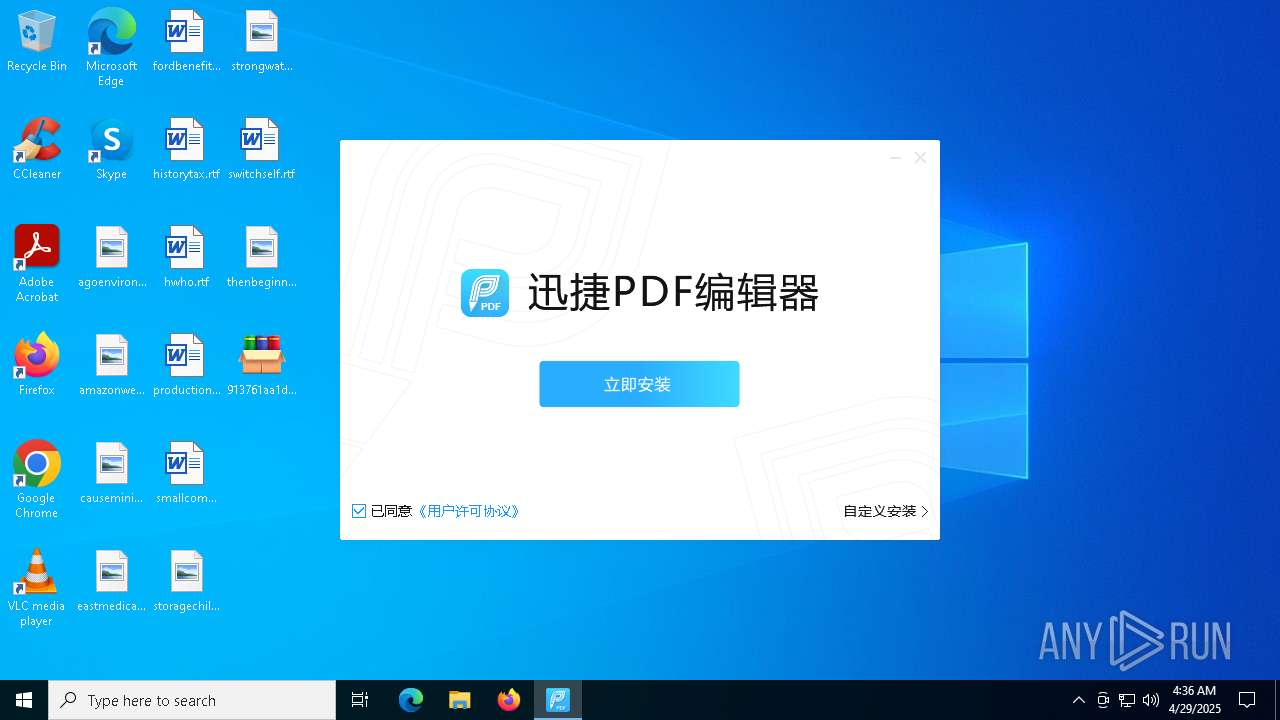
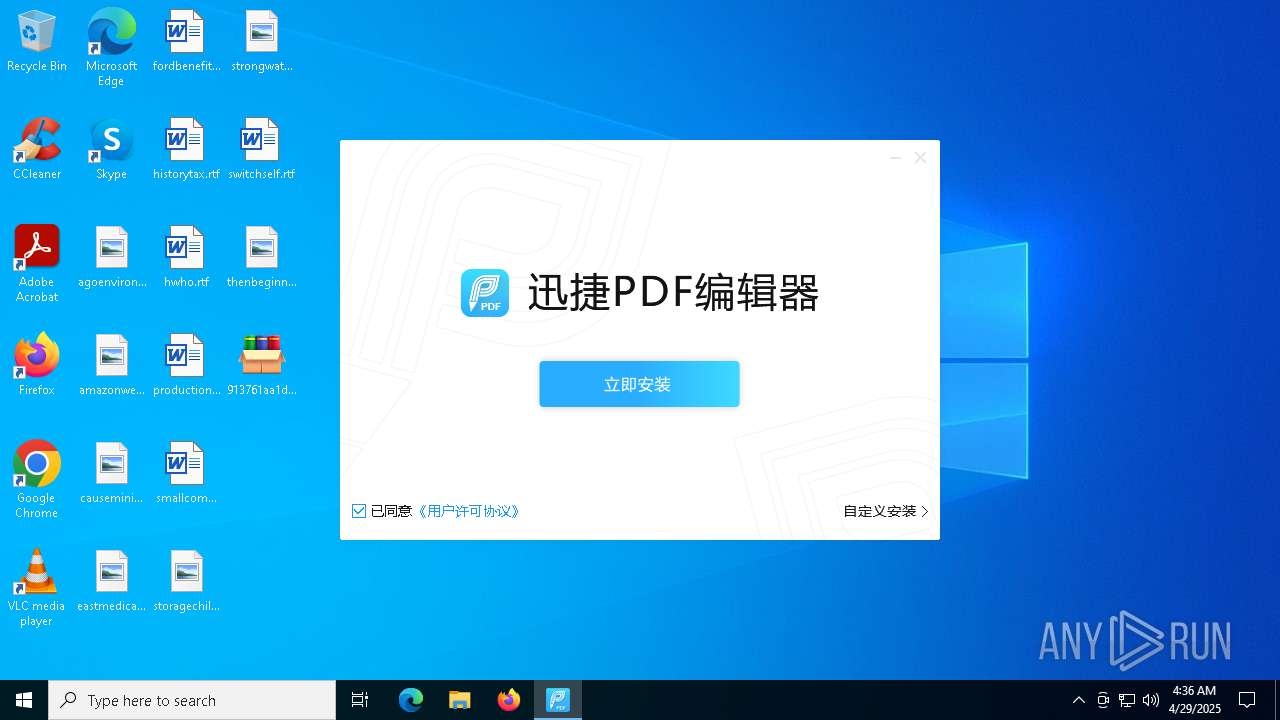
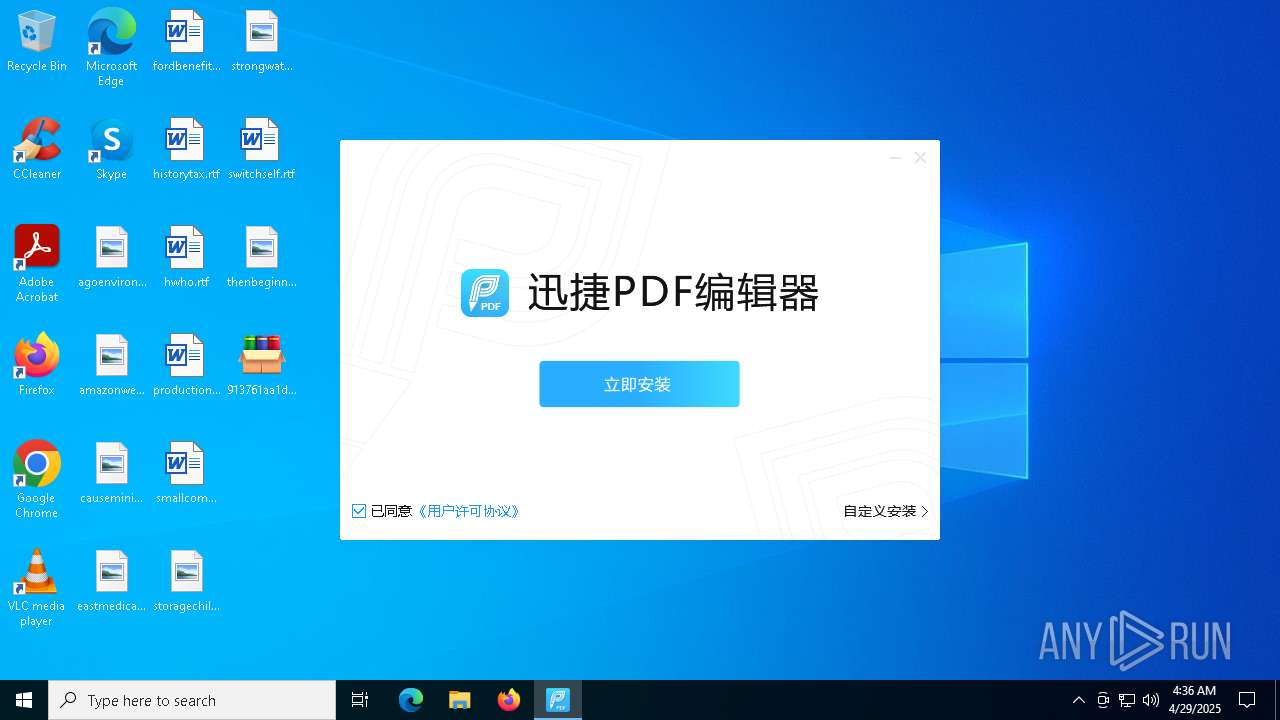
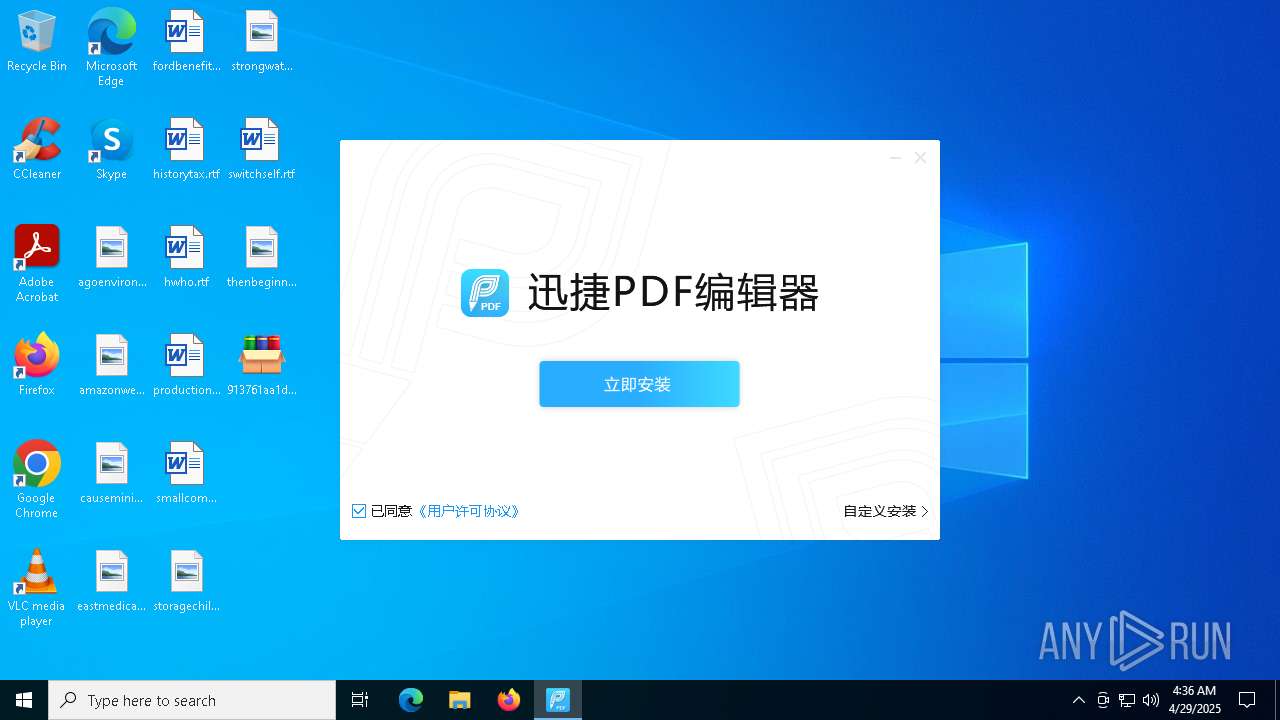
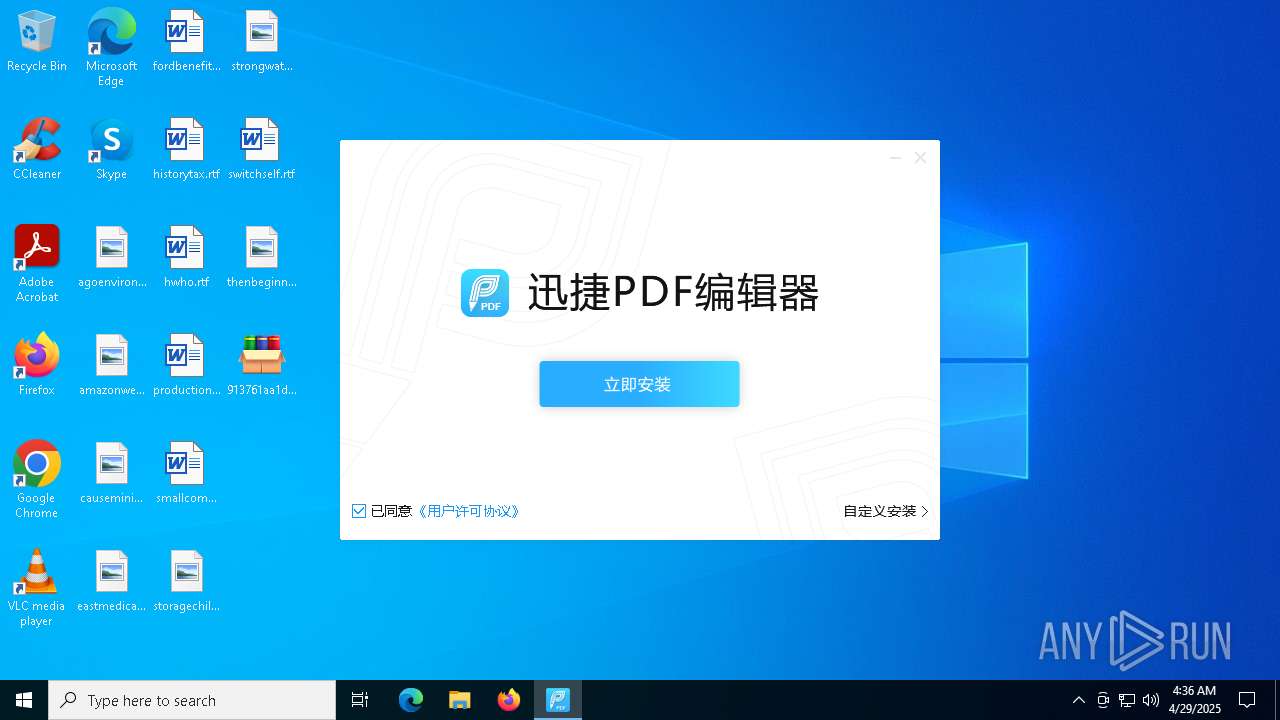
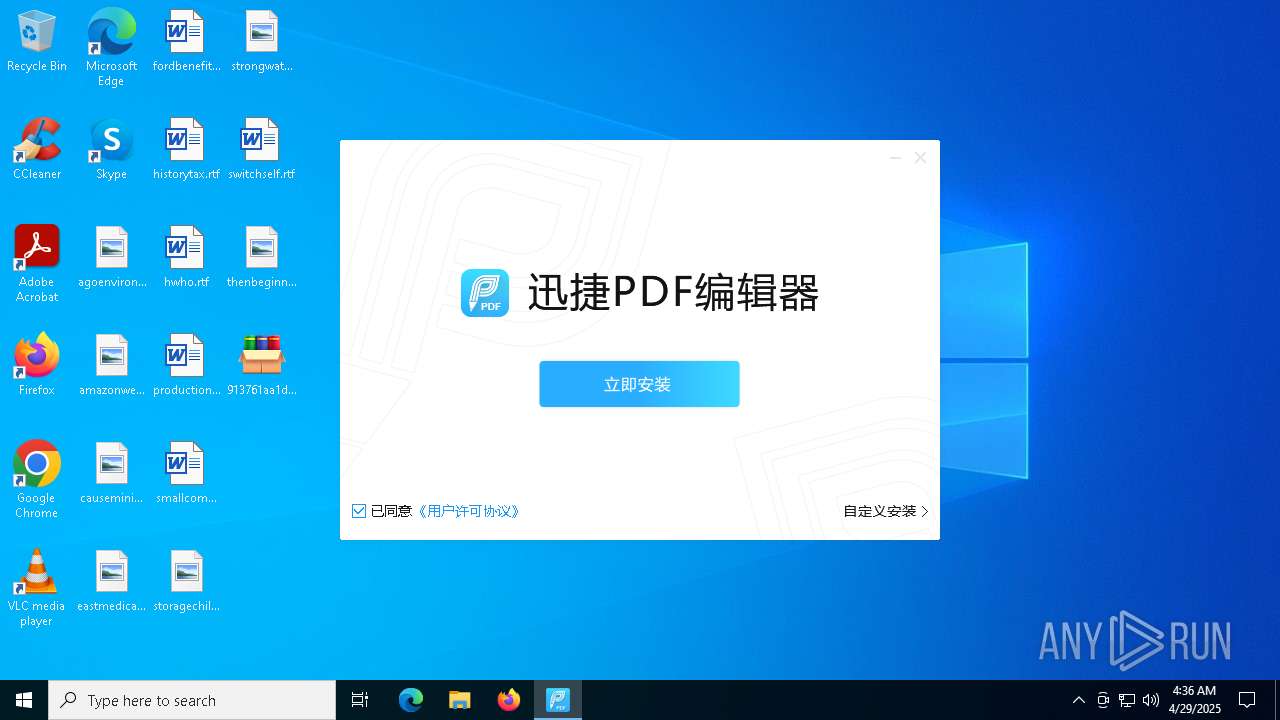
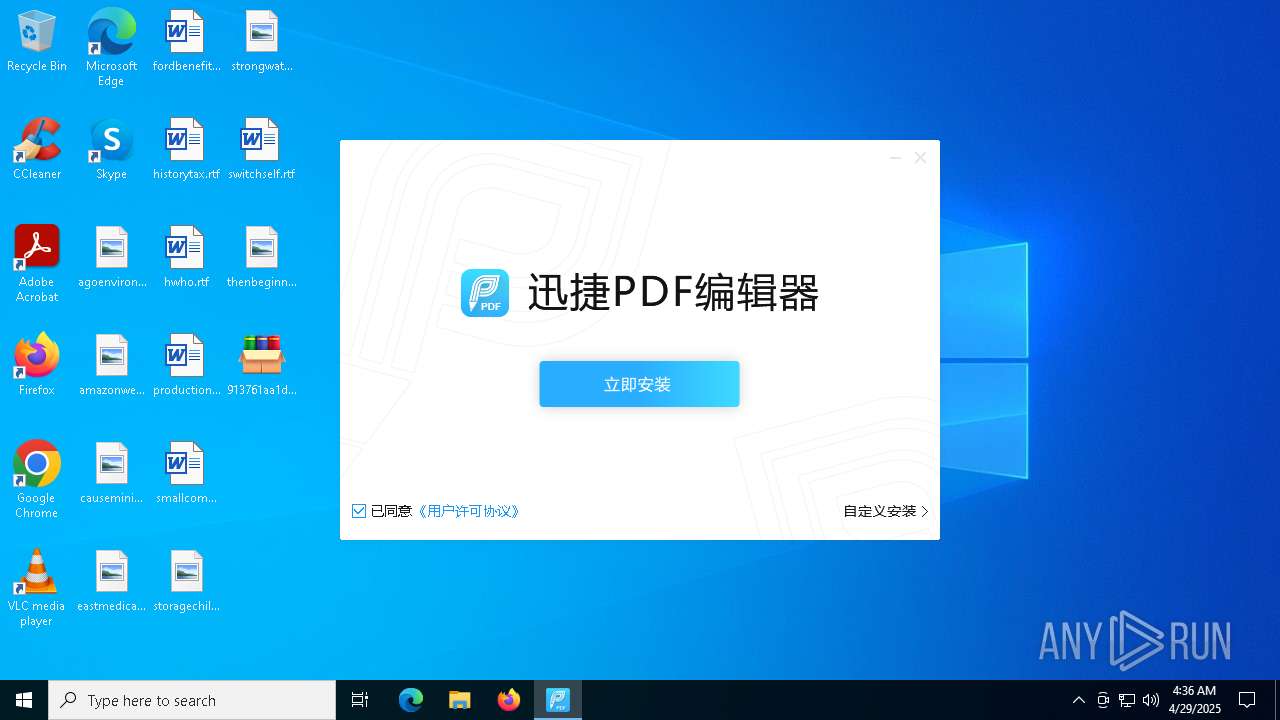
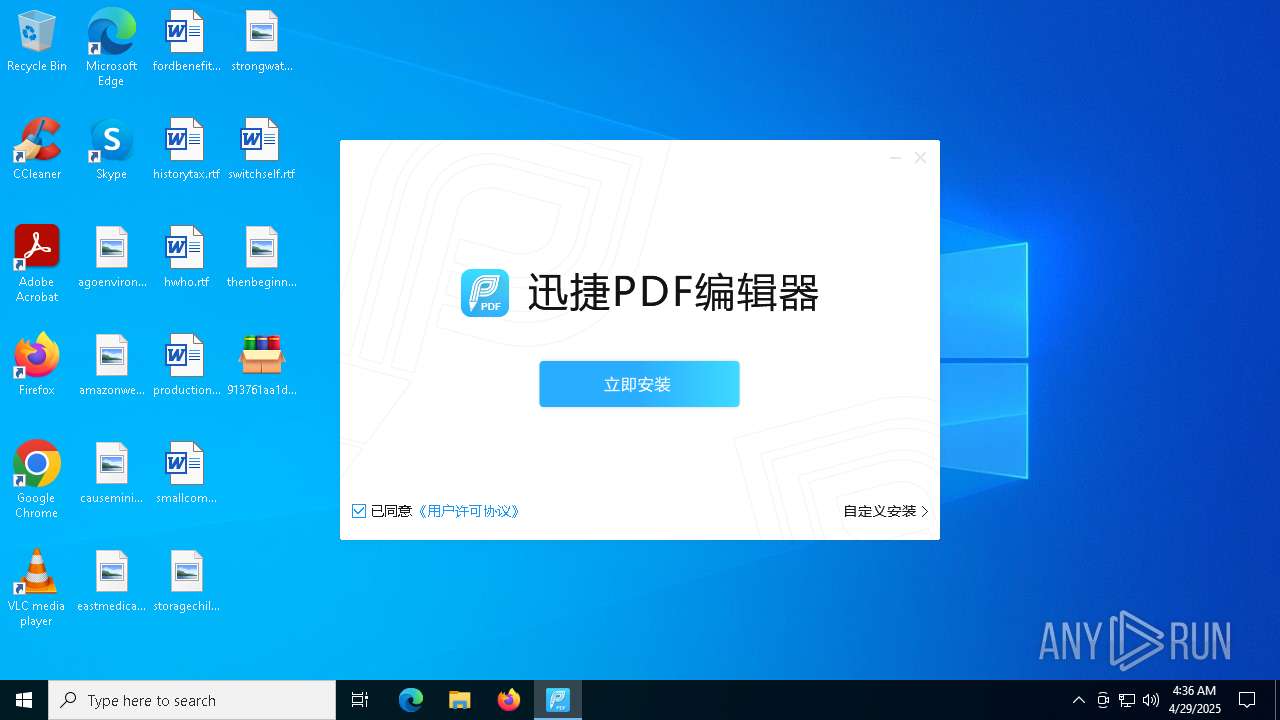
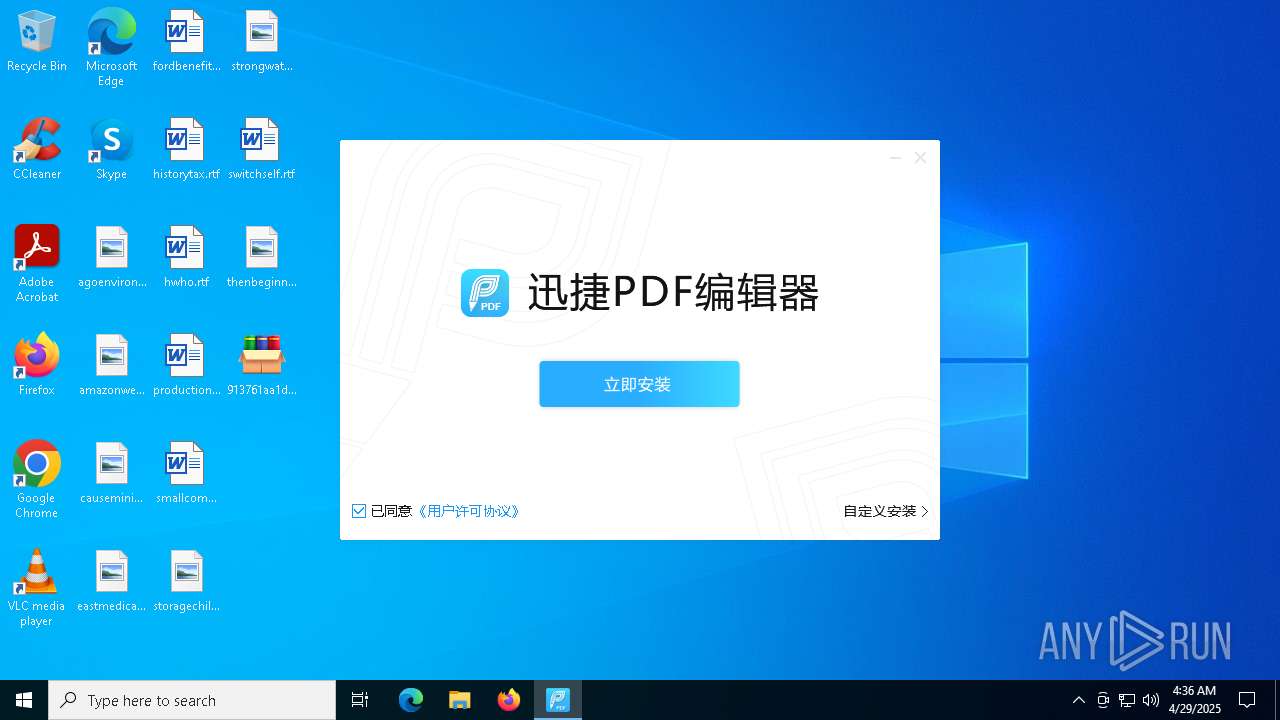
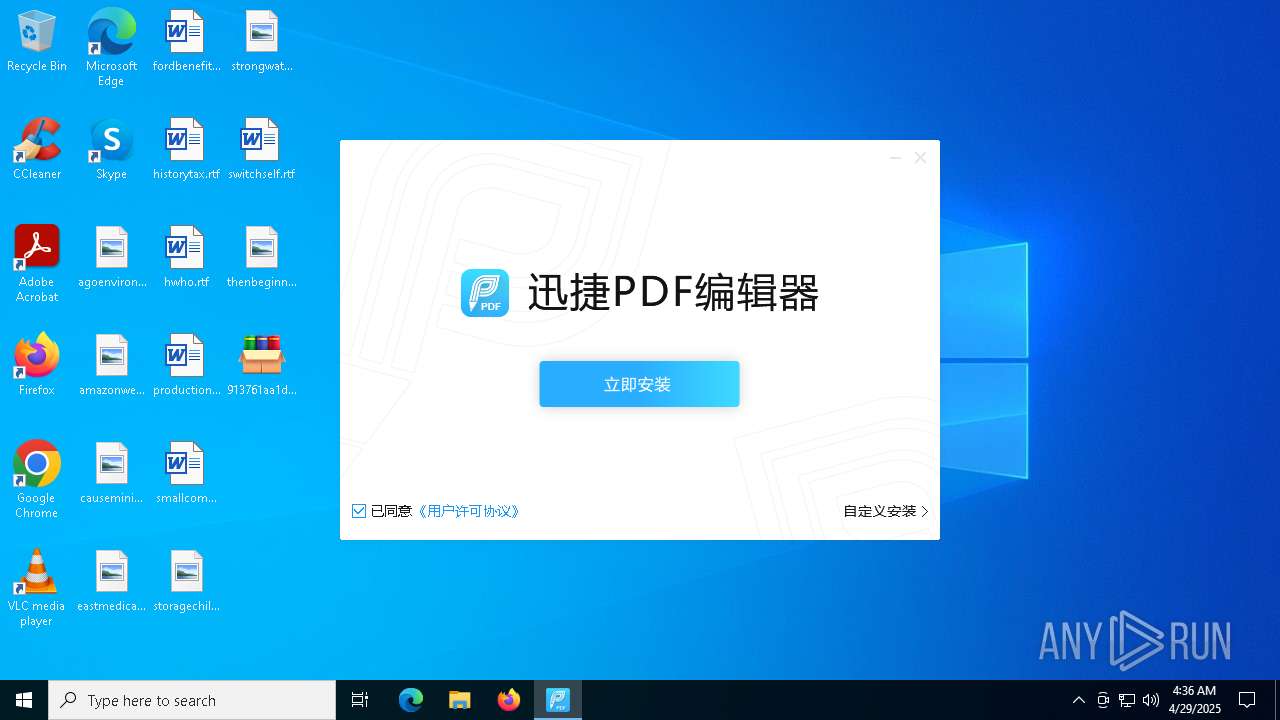
- 迅捷PDF编辑器cpc-Bing06_e0d006e67623143e56fb6ee105aafaff.exe (PID: 7152)
- cmd.exe (PID: 6192)
The sample compiled with chinese language support
- 913761aa1d80264ac127390b251cdaeb914e7d70065e17276af15e51689c8d4f.exe (PID: 920)
Reads the software policy settings
- slui.exe (PID: 5008)
Reads the computer name
- 913761aa1d80264ac127390b251cdaeb914e7d70065e17276af15e51689c8d4f.exe (PID: 920)
- 迅捷PDF编辑器cpc-Bing06_e0d006e67623143e56fb6ee105aafaff.exe (PID: 7152)
Creates files or folders in the user directory
- 迅捷PDF编辑器cpc-Bing06_e0d006e67623143e56fb6ee105aafaff.exe (PID: 7152)
Process checks computer location settings
- 913761aa1d80264ac127390b251cdaeb914e7d70065e17276af15e51689c8d4f.exe (PID: 920)
Checks proxy server information
- slui.exe (PID: 5008)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win64 Executable (generic) (87.3) |
|---|---|---|
| .exe | | | Generic Win/DOS Executable (6.3) |
| .exe | | | DOS Executable Generic (6.3) |
EXIF
EXE
| MachineType: | AMD AMD64 |
|---|---|
| TimeStamp: | 2025:03:20 10:01:29+00:00 |
| ImageFileCharacteristics: | Executable, Large address aware |
| PEType: | PE32+ |
| LinkerVersion: | 14.42 |
| CodeSize: | 307200 |
| InitializedDataSize: | 208384 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x32690 |
| OSVersion: | 6 |
| ImageVersion: | - |
| SubsystemVersion: | 6 |
| Subsystem: | Windows GUI |
Total processes
127
Monitored processes
5
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 920 | "C:\Users\admin\Desktop\913761aa1d80264ac127390b251cdaeb914e7d70065e17276af15e51689c8d4f.exe" | C:\Users\admin\Desktop\913761aa1d80264ac127390b251cdaeb914e7d70065e17276af15e51689c8d4f.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 2088 | "C:\windows\temp\迅捷PDF编辑器cpc-Bing06_e0d006e67623143e56fb6ee105aafaff.exe" | C:\Windows\Temp\迅捷PDF编辑器cpc-Bing06_e0d006e67623143e56fb6ee105aafaff.exe | — | 913761aa1d80264ac127390b251cdaeb914e7d70065e17276af15e51689c8d4f.exe | |||||||||||
User: admin Company: 上海互盾信息科技有限公司 Integrity Level: MEDIUM Description: 迅捷PDF编辑器 Exit code: 3221226540 Version: 1.7.9 Modules
| |||||||||||||||
| 5008 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6192 | "C:\windows\temp\cmd.exe" | C:\Windows\Temp\cmd.exe | 913761aa1d80264ac127390b251cdaeb914e7d70065e17276af15e51689c8d4f.exe | ||||||||||||
User: admin Company: Apache Software Foundation Integrity Level: MEDIUM Description: ApacheBench command line utility Version: 2.2.14 Modules
| |||||||||||||||
| 7152 | "C:\windows\temp\迅捷PDF编辑器cpc-Bing06_e0d006e67623143e56fb6ee105aafaff.exe" | C:\Windows\Temp\迅捷PDF编辑器cpc-Bing06_e0d006e67623143e56fb6ee105aafaff.exe | 913761aa1d80264ac127390b251cdaeb914e7d70065e17276af15e51689c8d4f.exe | ||||||||||||
User: admin Company: 上海互盾信息科技有限公司 Integrity Level: HIGH Description: 迅捷PDF编辑器 Version: 1.7.9 Modules
| |||||||||||||||
Total events
4 046
Read events
4 046
Write events
0
Delete events
0
Modification events
Executable files
2
Suspicious files
0
Text files
1
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 920 | 913761aa1d80264ac127390b251cdaeb914e7d70065e17276af15e51689c8d4f.exe | C:\Windows\Temp\迅捷PDF编辑器cpc-Bing06_e0d006e67623143e56fb6ee105aafaff.exe | executable | |
MD5:FB375264BC1423B10E283D597E81E3F7 | SHA256:54E9A129A158167E155888360ACE3027DF2981F918B97B1E375FB7C7DF9EB66A | |||
| 920 | 913761aa1d80264ac127390b251cdaeb914e7d70065e17276af15e51689c8d4f.exe | C:\Windows\Temp\cmd.exe | executable | |
MD5:260582453429EEF35B56E8721BB56916 | SHA256:28EF55B6842DED0B4448BA2D96FA20E8EF4C69E3195DCBB10C2071926FE6519E | |||
| 7152 | 迅捷PDF编辑器cpc-Bing06_e0d006e67623143e56fb6ee105aafaff.exe | C:\Users\admin\AppData\Local\HDLocal\PDFEditor.downloader\PDFEditor.downloader_HDSConfigure.ini | text | |
MD5:179C67479DEB57E4848C652DAA5DF63A | SHA256:6C9C6B3C726D9C4D52B379585027FAEF706D7D64FDD556072E56074B0ABD4377 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
23
TCP/UDP connections
43
DNS requests
13
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3768 | SIHClient.exe | GET | 200 | 2.16.164.120:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut_2010-06-23.crl | unknown | — | — | whitelisted |
3768 | SIHClient.exe | GET | 200 | 2.16.164.120:80 | http://crl.microsoft.com/pki/crl/products/MicTimStaPCA_2010-07-01.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 4.245.163.56:443 | https://slscr.update.microsoft.com/sls/ping | unknown | — | — | unknown |
3768 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Signing%20CA%202.1.crl | unknown | — | — | whitelisted |
3768 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Signing%20CA%202.2.crl | unknown | — | — | whitelisted |
3768 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20Update%20Signing%20CA%202.1.crl | unknown | — | — | whitelisted |
3768 | SIHClient.exe | GET | 200 | 2.16.164.120:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
— | — | GET | 304 | 4.245.163.56:443 | https://slscr.update.microsoft.com/SLS/%7B522D76A4-93E1-47F8-B8CE-07C937AD1A1E%7D/x64/10.0.19045.4046/0?CH=686&L=en-US&P=&PT=0x30&WUA=10.0.19041.3996&MK=DELL&MD=DELL | unknown | — | — | unknown |
— | — | GET | 200 | 20.3.187.198:443 | https://fe3cr.delivery.mp.microsoft.com/clientwebservice/ping | unknown | — | — | unknown |
3768 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20Update%20Signing%20CA%202.2.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
— | — | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
6192 | cmd.exe | 192.168.46.128:5566 | — | — | — | unknown |
3216 | svchost.exe | 172.211.123.249:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
3768 | SIHClient.exe | 4.245.163.56:443 | slscr.update.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
3768 | SIHClient.exe | 2.16.164.120:80 | crl.microsoft.com | Akamai International B.V. | NL | whitelisted |
3768 | SIHClient.exe | 95.101.149.131:80 | www.microsoft.com | Akamai International B.V. | NL | whitelisted |
3768 | SIHClient.exe | 40.69.42.241:443 | fe3cr.delivery.mp.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
activation-v2.sls.microsoft.com |
| whitelisted |
nexusrules.officeapps.live.com |
| whitelisted |
login.live.com |
| whitelisted |