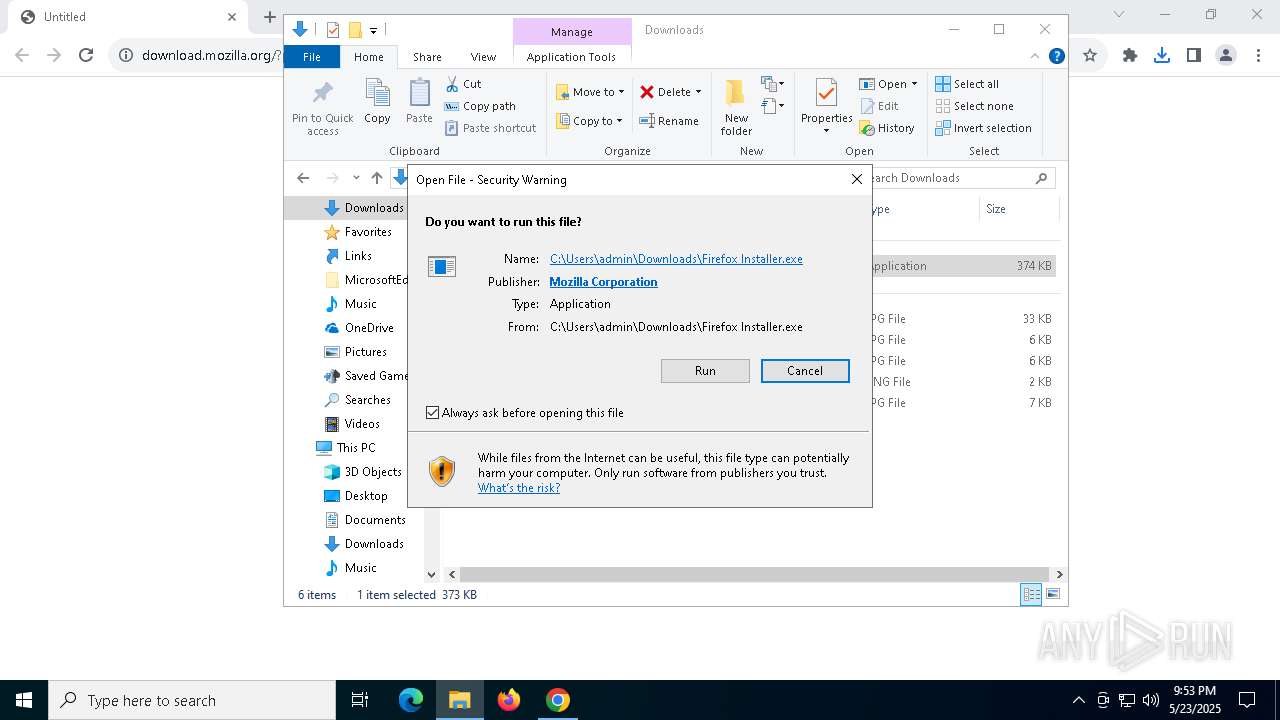
| URL: | https://download.mozilla.org/?product=firefox-stub&os=win64&lang=en-US&_gl=1*1o2ia5f*_ga*MTI1MzEwNjk5OS4xNzQ4MDM3MTI3*_ga_MQ7767QQQW*czE3NDgwMzcxMjckbzEkZzAkdDE3NDgwMzcxMjckajAkbDAkaDA. |
| Full analysis: | https://app.any.run/tasks/4fc36198-cd4c-4730-8a9e-8cd555765b7f |
| Verdict: | Malicious activity |
| Analysis date: | May 23, 2025, 21:52:56 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MD5: | E6DAC69167D5E2AA72C2368AE275B9F2 |
| SHA1: | 87BA21FB61828B1E732238205BF799AE8716A244 |
| SHA256: | 9128EB1863E5A164EFE0FED45D1DDBC652294BA3F1C00443288FF959BC68204A |
| SSDEEP: | 3:N8SElUJJiMMXbGYidrRNK2kD5sMSwfu5oGqHH6PdTqGdSaOwWvCGdSkkEZL:2SKciXXyYidFNK2kD5sgu5oLH2TSFjvN |
MALICIOUS
Registers / Runs the DLL via REGSVR32.EXE
- setup.exe (PID: 6184)
SUSPICIOUS
Executable content was dropped or overwritten
- Firefox Installer.exe (PID: 7704)
- setup-stub.exe (PID: 7908)
- setup-stub.exe (PID: 8024)
- download.exe (PID: 1040)
- setup.exe (PID: 6184)
- maintenanceservice_installer.exe (PID: 1616)
- maintenanceservice_tmp.exe (PID: 6540)
Application launched itself
- setup-stub.exe (PID: 8024)
The process creates files with name similar to system file names
- setup-stub.exe (PID: 7908)
- setup-stub.exe (PID: 8024)
- setup.exe (PID: 6184)
Malware-specific behavior (creating "System.dll" in Temp)
- setup-stub.exe (PID: 7908)
- setup-stub.exe (PID: 8024)
- setup.exe (PID: 6184)
- maintenanceservice_installer.exe (PID: 1616)
Reads security settings of Internet Explorer
- setup-stub.exe (PID: 8024)
- setup-stub.exe (PID: 7908)
- setup.exe (PID: 6184)
Reads Microsoft Outlook installation path
- setup-stub.exe (PID: 7908)
There is functionality for taking screenshot (YARA)
- setup-stub.exe (PID: 8024)
- setup-stub.exe (PID: 7908)
The process drops Mozilla's DLL files
- download.exe (PID: 1040)
- setup.exe (PID: 6184)
The process drops C-runtime libraries
- download.exe (PID: 1040)
- setup.exe (PID: 6184)
Process drops legitimate windows executable
- download.exe (PID: 1040)
- setup.exe (PID: 6184)
Reads Internet Explorer settings
- setup-stub.exe (PID: 7908)
Loads DLL from Mozilla Firefox
- regsvr32.exe (PID: 4272)
Searches for installed software
- setup.exe (PID: 6184)
Creates/Modifies COM task schedule object
- regsvr32.exe (PID: 4272)
Creates a software uninstall entry
- setup.exe (PID: 6184)
INFO
The sample compiled with english language support
- chrome.exe (PID: 4944)
- Firefox Installer.exe (PID: 7704)
- chrome.exe (PID: 2040)
- download.exe (PID: 1040)
- setup.exe (PID: 6184)
- maintenanceservice_installer.exe (PID: 1616)
- firefox.exe (PID: 7828)
Checks proxy server information
- explorer.exe (PID: 5492)
- setup-stub.exe (PID: 7908)
Executable content was dropped or overwritten
- chrome.exe (PID: 4944)
- chrome.exe (PID: 2040)
- firefox.exe (PID: 7828)
Checks supported languages
- Firefox Installer.exe (PID: 7704)
- setup-stub.exe (PID: 7908)
- setup-stub.exe (PID: 8024)
- download.exe (PID: 1040)
- setup.exe (PID: 6184)
Reads security settings of Internet Explorer
- explorer.exe (PID: 5492)
Application launched itself
- chrome.exe (PID: 4944)
- firefox.exe (PID: 208)
- firefox.exe (PID: 7828)
- firefox.exe (PID: 7480)
- firefox.exe (PID: 5304)
Creates files or folders in the user directory
- explorer.exe (PID: 5492)
- setup-stub.exe (PID: 7908)
Reads the software policy settings
- explorer.exe (PID: 5492)
- slui.exe (PID: 7748)
- setup-stub.exe (PID: 7908)
Reads the computer name
- Firefox Installer.exe (PID: 7704)
- setup-stub.exe (PID: 7908)
- setup-stub.exe (PID: 8024)
- setup.exe (PID: 6184)
Create files in a temporary directory
- Firefox Installer.exe (PID: 7704)
- setup-stub.exe (PID: 7908)
- setup-stub.exe (PID: 8024)
- download.exe (PID: 1040)
- setup.exe (PID: 6184)
Creates files in the program directory
- setup-stub.exe (PID: 7908)
- setup.exe (PID: 6184)
Process checks whether UAC notifications are on
- setup-stub.exe (PID: 8024)
Process checks computer location settings
- setup-stub.exe (PID: 8024)
Reads the machine GUID from the registry
- setup-stub.exe (PID: 7908)
UPX packer has been detected
- Firefox Installer.exe (PID: 7704)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
184
Monitored processes
47
Malicious processes
5
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 208 | "C:\Program Files\Mozilla Firefox\firefox.exe" -reset-profile -migration -first-startup | C:\Program Files\Mozilla Firefox\firefox.exe | — | setup-stub.exe | |||||||||||
User: admin Company: Mozilla Corporation Integrity Level: MEDIUM Description: Firefox Exit code: 0 Version: 138.0.4 Modules
| |||||||||||||||
| 684 | "C:\Program Files\Mozilla Firefox\firefox.exe" -contentproc -isForBrowser -prefsHandle 4604:27089 -prefMapHandle 4608:273308 -jsInitHandle 4612:247720 -parentBuildID 20250517143237 -ipcHandle 4616 -initialChannelId {edaf36a8-82a6-4351-9252-bd45ea95bda7} -parentPid 7828 -crashReporter "\\.\pipe\gecko-crash-server-pipe.7828" -win32kLockedDown -appDir "C:\Program Files\Mozilla Firefox\browser" - 8 tab | C:\Program Files\Mozilla Firefox\firefox.exe | — | firefox.exe | |||||||||||
User: admin Company: Mozilla Corporation Integrity Level: LOW Description: Firefox Version: 138.0.4 Modules
| |||||||||||||||
| 1040 | "C:\Users\admin\AppData\Local\Temp\nsxA120.tmp\download.exe" /LaunchedFromStub /INI=C:\Users\admin\AppData\Local\Temp\nsxA120.tmp\config.ini | C:\Users\admin\AppData\Local\Temp\nsxA120.tmp\download.exe | setup-stub.exe | ||||||||||||
User: admin Company: Mozilla Integrity Level: HIGH Description: Firefox Exit code: 0 Version: 18.05 Modules
| |||||||||||||||
| 1132 | "C:\Program Files\Mozilla Firefox\default-browser-agent.exe" register-task 308046B0AF4A39CB | C:\Program Files\Mozilla Firefox\default-browser-agent.exe | — | setup.exe | |||||||||||
User: admin Company: Mozilla Foundation Integrity Level: HIGH Exit code: 0 Version: 138.0.4 Modules
| |||||||||||||||
| 1228 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=gpu-process --disable-gpu-sandbox --use-gl=disabled --gpu-vendor-id=5140 --gpu-device-id=140 --gpu-sub-system-id=0 --gpu-revision=0 --gpu-driver-version=10.0.19041.3636 --no-appcompat-clear --gpu-preferences=WAAAAAAAAADoABAMAAAAAAAAAAAAAAAAAABgAAAAAAA4AAAAAAAAAAAAAABEAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAGAAAAAAAAAAYAAAAAAAAAAgAAAAAAAAACAAAAAAAAAAIAAAAAAAAAA== --mojo-platform-channel-handle=3212 --field-trial-handle=1916,i,17756022800059790523,1367485101159459411,262144 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction --variations-seed-version /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 122.0.6261.70 Modules
| |||||||||||||||
| 1616 | "C:\Program Files\Mozilla Firefox\maintenanceservice_installer.exe" | C:\Program Files\Mozilla Firefox\maintenanceservice_installer.exe | setup.exe | ||||||||||||
User: admin Company: Mozilla Corporation Integrity Level: HIGH Description: Mozilla Maintenance Service Installer Exit code: 0 Version: 138.0.4 Modules
| |||||||||||||||
| 2040 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=unzip.mojom.Unzipper --lang=en-US --service-sandbox-type=service --disable-quic --no-appcompat-clear --mojo-platform-channel-handle=4364 --field-trial-handle=1916,i,17756022800059790523,1367485101159459411,262144 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction --variations-seed-version /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | chrome.exe | ||||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 122.0.6261.70 Modules
| |||||||||||||||
| 2332 | "C:\Program Files\Mozilla Firefox\firefox.exe" -contentproc -isForBrowser -prefsHandle 4800:28581 -prefMapHandle 4804:273308 -jsInitHandle 4808:247720 -parentBuildID 20250517143237 -ipcHandle 4816 -initialChannelId {3fd8ea01-240a-4161-bdb0-ba4330a89746} -parentPid 7828 -crashReporter "\\.\pipe\gecko-crash-server-pipe.7828" -win32kLockedDown -appDir "C:\Program Files\Mozilla Firefox\browser" - 9 tab | C:\Program Files\Mozilla Firefox\firefox.exe | — | firefox.exe | |||||||||||
User: admin Company: Mozilla Corporation Integrity Level: LOW Description: Firefox Version: 138.0.4 Modules
| |||||||||||||||
| 2344 | "C:\Program Files\Mozilla Firefox\firefox.exe" -contentproc -isForBrowser -prefsHandle 3880:27089 -prefMapHandle 4008:273308 -jsInitHandle 4132:247720 -parentBuildID 20250517143237 -ipcHandle 4236 -initialChannelId {fc54217d-2324-4a5d-8615-aa539f6081db} -parentPid 7828 -crashReporter "\\.\pipe\gecko-crash-server-pipe.7828" -win32kLockedDown -appDir "C:\Program Files\Mozilla Firefox\browser" - 6 tab | C:\Program Files\Mozilla Firefox\firefox.exe | — | firefox.exe | |||||||||||
User: admin Company: Mozilla Corporation Integrity Level: LOW Description: Firefox Version: 138.0.4 Modules
| |||||||||||||||
| 2432 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=crashpad-handler "--user-data-dir=C:\Users\admin\AppData\Local\Google\Chrome\User Data" /prefetch:4 --monitor-self-annotation=ptype=crashpad-handler "--database=C:\Users\admin\AppData\Local\Google\Chrome\User Data\Crashpad" --url=https://clients2.google.com/cr/report --annotation=channel= --annotation=plat=Win64 --annotation=prod=Chrome --annotation=ver=122.0.6261.70 --initial-client-data=0x21c,0x220,0x224,0x1f8,0x228,0x7ffc89a9dc40,0x7ffc89a9dc4c,0x7ffc89a9dc58 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Version: 122.0.6261.70 Modules
| |||||||||||||||
Total events
45 254
Read events
45 034
Write events
176
Delete events
44
Modification events
| (PID) Process: | (4944) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome\BLBeacon |
| Operation: | write | Name: | failed_count |
Value: 0 | |||
| (PID) Process: | (4944) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 2 | |||
| (PID) Process: | (5492) explorer.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\SessionInfo\5\ApplicationViewManagement\W32:00000000000502DA |
| Operation: | write | Name: | VirtualDesktop |
Value: 1000000030304456BFA0DB55E4278845B426357D5B5F97B3 | |||
| (PID) Process: | (5492) explorer.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\FeatureUsage\AppBadgeUpdated |
| Operation: | write | Name: | Chrome |
Value: 6 | |||
| (PID) Process: | (4944) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 1 | |||
| (PID) Process: | (4944) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome\StabilityMetrics |
| Operation: | write | Name: | user_experience_metrics.stability.exited_cleanly |
Value: 0 | |||
| (PID) Process: | (4944) chrome.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Google\Update\ClientStateMedium\{8A69D345-D564-463C-AFF1-A69D9E530F96} |
| Operation: | write | Name: | usagestats |
Value: 0 | |||
| (PID) Process: | (7636) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Shell Extensions\Cached |
| Operation: | write | Name: | {2781761E-28E0-4109-99FE-B9D127C57AFE} {56FFCC30-D398-11D0-B2AE-00A0C908FA49} 0xFFFF |
Value: 01000000000000005E6CC8112DCCDB01 | |||
| (PID) Process: | (5492) explorer.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\OneDrive\Accounts |
| Operation: | write | Name: | LastUpdate |
Value: 6CEE306800000000 | |||
| (PID) Process: | (5492) explorer.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\BagMRU |
| Operation: | write | Name: | NodeSlots |
Value: 02020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202 | |||
Executable files
102
Suspicious files
584
Text files
1 209
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 4944 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\commerce_subscription_db\LOG.old~RF10c16d.TMP | — | |
MD5:— | SHA256:— | |||
| 4944 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\commerce_subscription_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 4944 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\discounts_db\LOG.old~RF10c16d.TMP | — | |
MD5:— | SHA256:— | |||
| 4944 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\chrome_cart_db\LOG.old~RF10c16d.TMP | — | |
MD5:— | SHA256:— | |||
| 4944 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\discounts_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 4944 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\chrome_cart_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 4944 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\coupon_db\LOG.old~RF10c17d.TMP | — | |
MD5:— | SHA256:— | |||
| 4944 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\coupon_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 4944 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\PersistentOriginTrials\LOG.old~RF10c17d.TMP | — | |
MD5:— | SHA256:— | |||
| 4944 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\PersistentOriginTrials\LOG.old | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
63
TCP/UDP connections
96
DNS requests
182
Threats
30
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5496 | MoUsoCoreWorker.exe | GET | 200 | 23.216.77.31:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
2104 | svchost.exe | GET | 200 | 23.216.77.31:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 23.216.77.31:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
5496 | MoUsoCoreWorker.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
2104 | svchost.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
5416 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
5416 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
5492 | explorer.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBT3xL4LQLXDRDM9P665TW442vrsUQQUReuir%2FSSy4IxLVGLp6chnfNtyA8CEAEkCvseOAuKFvFLcZ3008A%3D | unknown | — | — | whitelisted |
5492 | explorer.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTfIs%2BLjDtGwQ09XEB1Yeq%2BtX%2BBgQQU7NfjgtJxXWRM3y5nP%2Be6mK4cD08CEAitQLJg0pxMn17Nqb2Trtk%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5496 | MoUsoCoreWorker.exe | 23.216.77.31:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
2104 | svchost.exe | 23.216.77.31:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
— | — | 23.216.77.31:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
5496 | MoUsoCoreWorker.exe | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
2104 | svchost.exe | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
— | — | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
5496 | MoUsoCoreWorker.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
download.mozilla.org |
| whitelisted |
accounts.google.com |
| whitelisted |
download-installer.cdn.mozilla.net |
| whitelisted |
client.wns.windows.com |
| whitelisted |
sb-ssl.google.com |
| whitelisted |
www.google.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
7828 | firefox.exe | Generic Protocol Command Decode | SURICATA QUIC failed decrypt |
7828 | firefox.exe | Generic Protocol Command Decode | SURICATA QUIC failed decrypt |
7828 | firefox.exe | Generic Protocol Command Decode | SURICATA QUIC failed decrypt |
7828 | firefox.exe | Generic Protocol Command Decode | SURICATA QUIC failed decrypt |
7828 | firefox.exe | Generic Protocol Command Decode | SURICATA QUIC failed decrypt |
7828 | firefox.exe | Generic Protocol Command Decode | SURICATA QUIC failed decrypt |
7828 | firefox.exe | Generic Protocol Command Decode | SURICATA QUIC failed decrypt |
7828 | firefox.exe | Generic Protocol Command Decode | SURICATA QUIC failed decrypt |
7828 | firefox.exe | Generic Protocol Command Decode | SURICATA QUIC failed decrypt |
7828 | firefox.exe | Generic Protocol Command Decode | SURICATA QUIC failed decrypt |