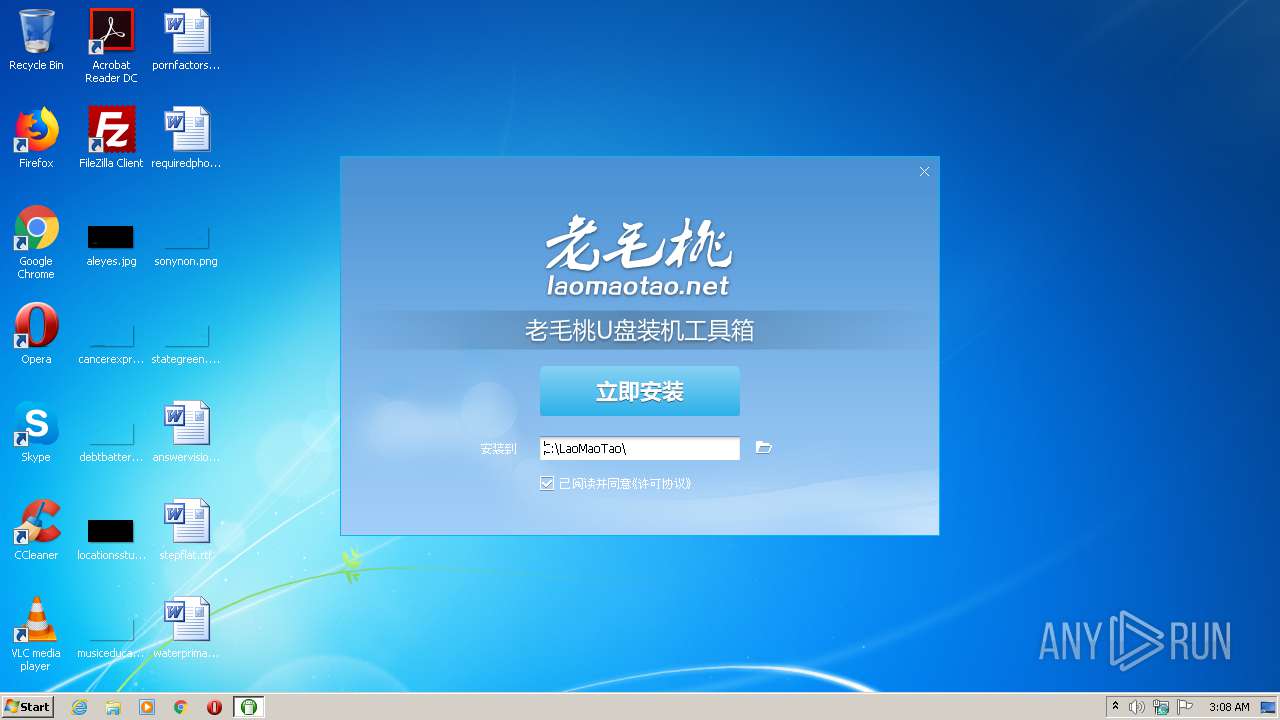
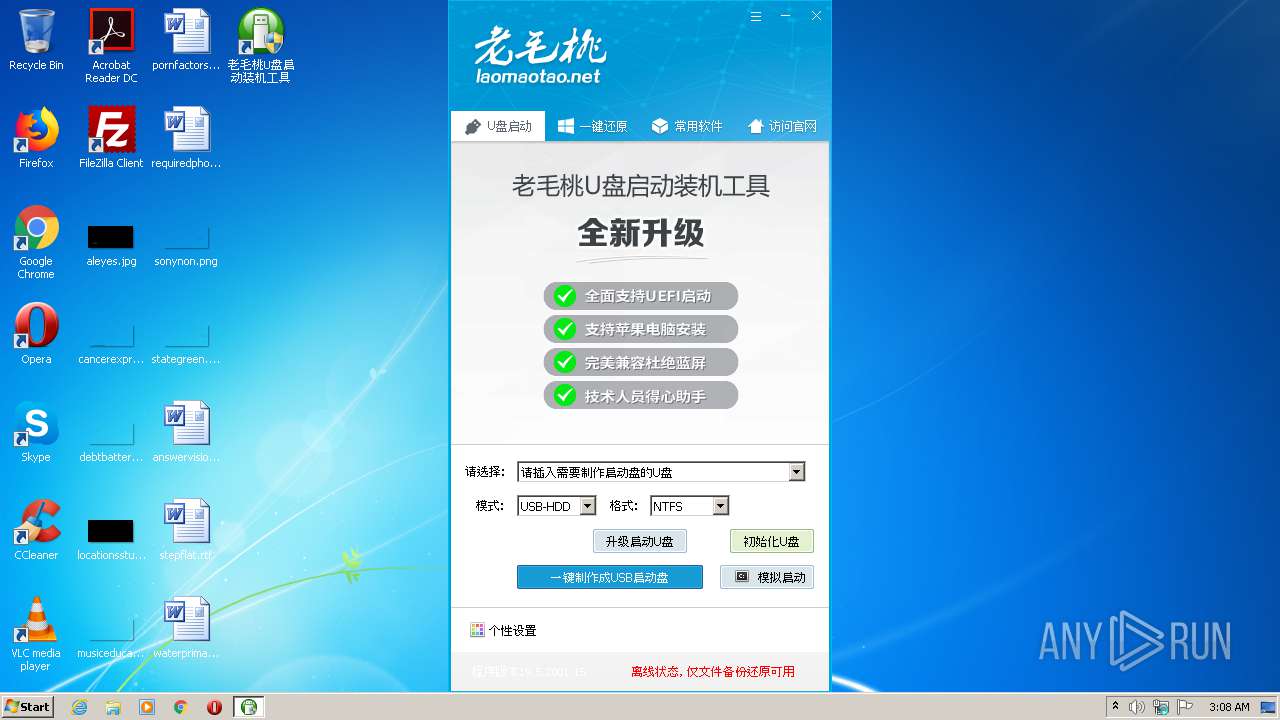
| File name: | LaoMaoTao(1).exe |
| Full analysis: | https://app.any.run/tasks/7d532237-5a0a-4864-9c58-6f70a5b2f2ed |
| Verdict: | Malicious activity |
| Analysis date: | June 12, 2020, 02:08:36 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, UPX compressed |
| MD5: | 99568E26F49F7272669DBC8C55C8565C |
| SHA1: | 2C89F4677AF7DE3DACBC2A5764D9EFC5356A80DA |
| SHA256: | 911BE0B2327E23EB8B76E748C2C50C04A790B5BB716C78733327E7002F0D1C20 |
| SSDEEP: | 49152:ujYgWFvRpCHLTAWz49r+qJQhJ4O85qJVJWvxR9wyCgMgixokQS3e2xZdp:ucgGyLz49+qNO3WvhwyPMgixokP |
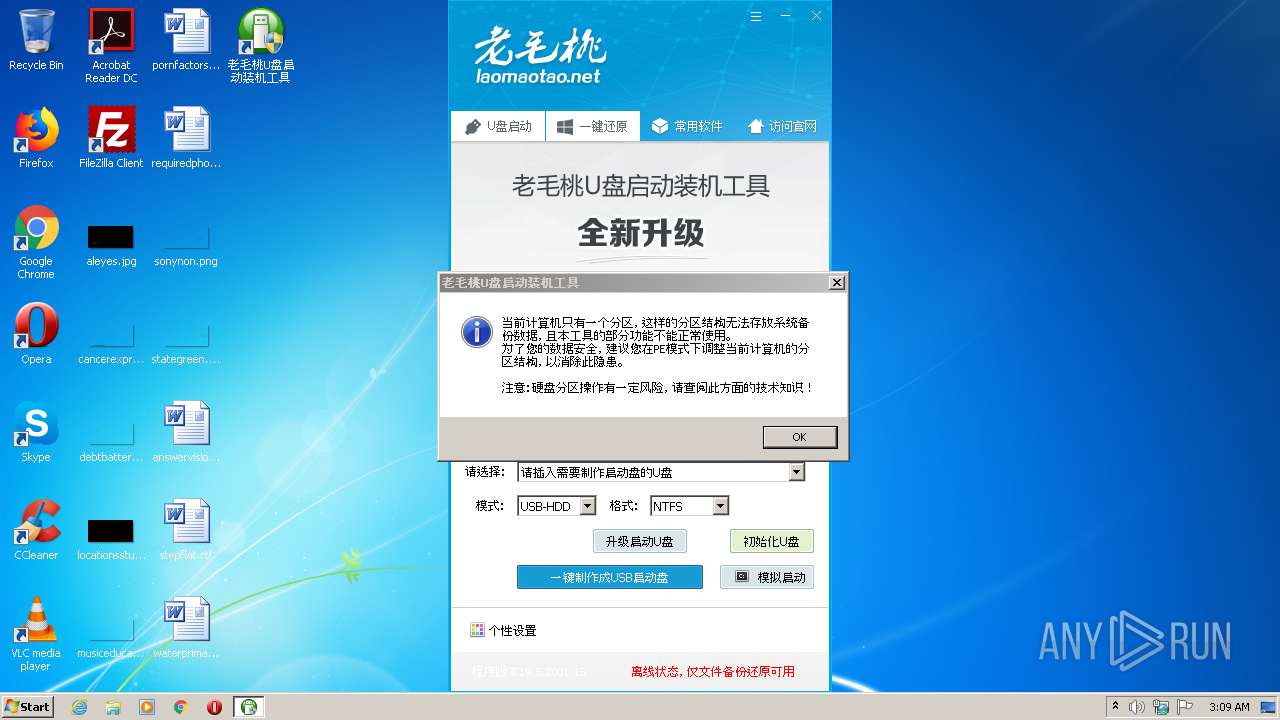
MALICIOUS
Loads dropped or rewritten executable
- LaoMaoTao.exe (PID: 2640)
- Dism.exe (PID: 1832)
- dismhost.exe (PID: 2900)
- Dism.exe (PID: 1736)
Application was dropped or rewritten from another process
- bcdedit.exe (PID: 2216)
- bcdedit.exe (PID: 1660)
- bcdedit.exe (PID: 760)
- dismhost.exe (PID: 2900)
SUSPICIOUS
Starts itself from another location
- LaoMaoTao(1).exe (PID: 2708)
Executable content was dropped or overwritten
- LaoMaoTao(1).exe (PID: 2708)
- Dism.exe (PID: 1832)
- LaoMaoTao.exe (PID: 2640)
Creates files in the program directory
- LaoMaoTao(1).exe (PID: 2708)
Low-level read access rights to disk partition
- bcdedit.exe (PID: 2216)
- bcdedit.exe (PID: 1660)
- LaoMaoTao.exe (PID: 2640)
- bcdedit.exe (PID: 760)
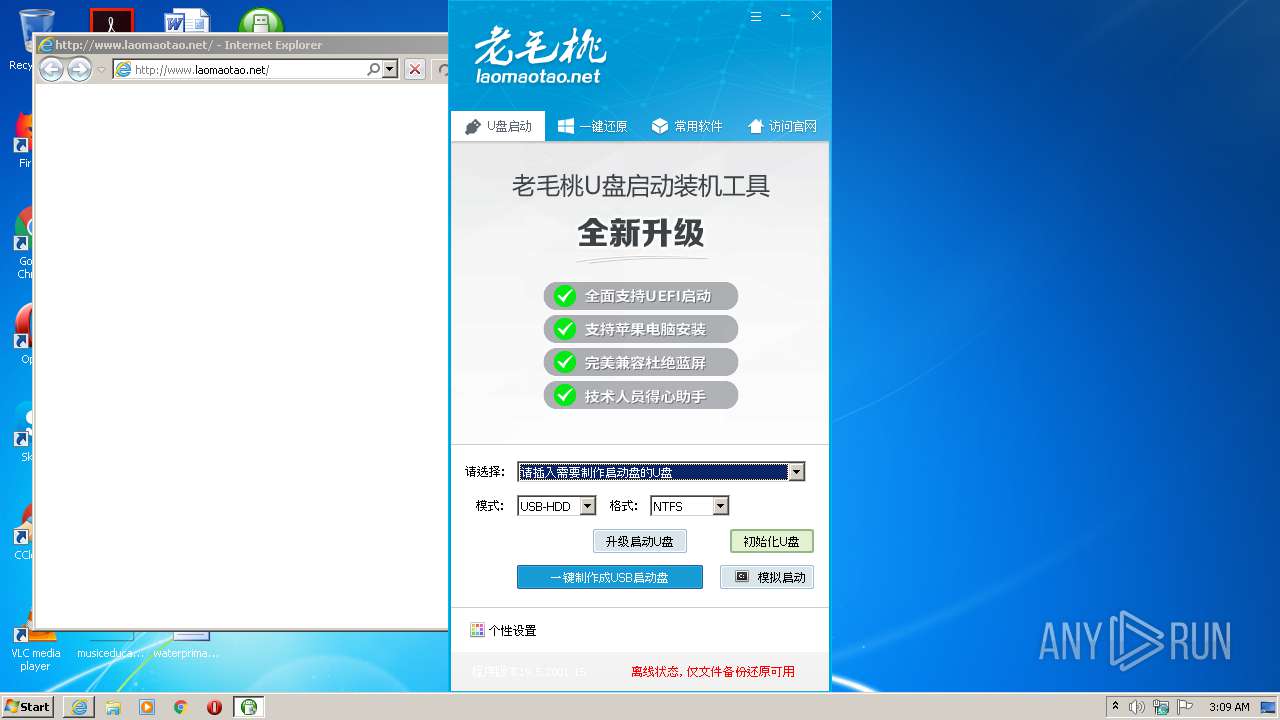
Starts Internet Explorer
- LaoMaoTao.exe (PID: 2640)
Creates a software uninstall entry
- LaoMaoTao.exe (PID: 2640)
INFO
Reads Internet Cache Settings
- iexplore.exe (PID: 2160)
- iexplore.exe (PID: 2180)
Changes internet zones settings
- iexplore.exe (PID: 2160)
Creates files in the user directory
- iexplore.exe (PID: 2180)
Reads settings of System Certificates
- iexplore.exe (PID: 2180)
Reads internet explorer settings
- iexplore.exe (PID: 2180)
Dropped object may contain Bitcoin addresses
- LaoMaoTao.exe (PID: 2640)
Changes settings of System certificates
- iexplore.exe (PID: 2180)
Adds / modifies Windows certificates
- iexplore.exe (PID: 2180)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | UPX compressed Win32 Executable (61.1) |
|---|---|---|
| .dll | | | Win32 Dynamic Link Library (generic) (14.8) |
| .exe | | | Win32 Executable (generic) (10.1) |
| .exe | | | Win16/32 Executable Delphi generic (4.6) |
| .exe | | | Generic Win/DOS Executable (4.5) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2020:01:15 11:00:18+01:00 |
| PEType: | PE32 |
| LinkerVersion: | 2.25 |
| CodeSize: | 3096576 |
| InitializedDataSize: | 36864 |
| UninitializedDataSize: | 3624960 |
| EntryPoint: | 0x668610 |
| OSVersion: | 5 |
| ImageVersion: | - |
| SubsystemVersion: | 5 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 9.5.2001.15 |
| ProductVersionNumber: | 9.5.0.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | Chinese (Simplified) |
| CharacterSet: | Windows, Chinese (Simplified) |
| CompanyName: | www.laomaotao.net |
| FileDescription: | 老毛桃U盘启动装机工具 |
| FileVersion: | 9.5.2001.15 |
| LegalCopyright: | Copyright © 2010-2020 LaoMaoTao.Net |
| LegalTrademarks: | www.laomaotao.net |
| ProductName: | 老毛桃U盘启动装机工具 |
| ProductVersion: | 9.5 |
| Comments: | 老毛桃U盘启动装机工具 |
Summary
| Architecture: | IMAGE_FILE_MACHINE_I386 |
|---|---|
| Subsystem: | IMAGE_SUBSYSTEM_WINDOWS_GUI |
| Compilation Date: | 15-Jan-2020 10:00:18 |
DOS Header
| Magic number: | MZ |
|---|---|
| Bytes on last page of file: | 0x0050 |
| Pages in file: | 0x0002 |
| Relocations: | 0x0000 |
| Size of header: | 0x0004 |
| Min extra paragraphs: | 0x000F |
| Max extra paragraphs: | 0xFFFF |
| Initial SS value: | 0x0000 |
| Initial SP value: | 0x00B8 |
| Checksum: | 0x0000 |
| Initial IP value: | 0x0000 |
| Initial CS value: | 0x0000 |
| Overlay number: | 0x001A |
| OEM identifier: | 0x0000 |
| OEM information: | 0x0000 |
| Address of NE header: | 0x00000100 |
PE Headers
| Signature: | PE |
|---|---|
| Machine: | IMAGE_FILE_MACHINE_I386 |
| Number of sections: | 3 |
| Time date stamp: | 15-Jan-2020 10:00:18 |
| Pointer to Symbol Table: | 0x00000000 |
| Number of symbols: | 0 |
| Size of Optional Header: | 0x00E0 |
| Characteristics: |
|
Sections
Name | Virtual Address | Virtual Size | Raw Size | Charateristics | Entropy |
|---|---|---|---|---|---|
UPX0 | 0x00001000 | 0x00375000 | 0x00000000 | IMAGE_SCN_CNT_UNINITIALIZED_DATA, IMAGE_SCN_MEM_EXECUTE, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 0 |
UPX1 | 0x00376000 | 0x002F4000 | 0x002F3400 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_EXECUTE, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 7.99992 |
.rsrc | 0x0066A000 | 0x00009000 | 0x00008C00 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 5.37733 |
Imports
KERNEL32.DLL |
URLMON.DLL |
advapi32.dll |
comctl32.dll |
comdlg32.dll |
gdi32.dll |
gdiplus.dll |
msvcrt.dll |
ole32.dll |
oleacc.dll |
Total processes
54
Monitored processes
11
Malicious processes
8
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 760 | "C:\LaoMaoTao\Data\Bin\bcdedit.exe" /enum all | C:\LaoMaoTao\Data\Bin\bcdedit.exe | — | LaoMaoTao.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Boot Configuration Data Editor Exit code: 0 Version: 6.2.9200.16384 (win8_rtm.120725-1247) Modules
| |||||||||||||||
| 1660 | "C:\LaoMaoTao\Data\Bin\bcdedit.exe" /enum all /v | C:\LaoMaoTao\Data\Bin\bcdedit.exe | — | LaoMaoTao.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Boot Configuration Data Editor Exit code: 0 Version: 6.2.9200.16384 (win8_rtm.120725-1247) Modules
| |||||||||||||||
| 1736 | C:\Windows\system32\Dism.exe /English /? | C:\Windows\system32\Dism.exe | LaoMaoTao.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Dism Image Servicing Utility Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1832 | C:\Windows\system32\Dism.exe /English /online /Export-Driver /? | C:\Windows\system32\Dism.exe | LaoMaoTao.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Dism Image Servicing Utility Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2160 | "C:\Program Files\Internet Explorer\iexplore.exe" http://www.laomaotao.net/ | C:\Program Files\Internet Explorer\iexplore.exe | LaoMaoTao.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 2180 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:2160 CREDAT:275457 /prefetch:2 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 2216 | "C:\LaoMaoTao\Data\Bin\bcdedit.exe" /enum all | C:\LaoMaoTao\Data\Bin\bcdedit.exe | — | LaoMaoTao.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Boot Configuration Data Editor Exit code: 0 Version: 6.2.9200.16384 (win8_rtm.120725-1247) Modules
| |||||||||||||||
| 2236 | "C:\Users\admin\AppData\Local\Temp\LaoMaoTao(1).exe" | C:\Users\admin\AppData\Local\Temp\LaoMaoTao(1).exe | — | explorer.exe | |||||||||||
User: admin Company: www.laomaotao.net Integrity Level: MEDIUM Description: 老毛桃U盘启动装机工具 Exit code: 3221226540 Version: 9.5.2001.15 Modules
| |||||||||||||||
| 2640 | "C:\LaoMaoTao\LaoMaoTao.exe" C:\Users\admin\AppData\Local\Temp\LaoMaoTao(1).exe | C:\LaoMaoTao\LaoMaoTao.exe | LaoMaoTao(1).exe | ||||||||||||
User: admin Company: www.laomaotao.net Integrity Level: HIGH Description: 老毛桃U盘启动装机工具 Exit code: 0 Version: 9.5.2001.15 Modules
| |||||||||||||||
| 2708 | "C:\Users\admin\AppData\Local\Temp\LaoMaoTao(1).exe" | C:\Users\admin\AppData\Local\Temp\LaoMaoTao(1).exe | explorer.exe | ||||||||||||
User: admin Company: www.laomaotao.net Integrity Level: HIGH Description: 老毛桃U盘启动装机工具 Exit code: 0 Version: 9.5.2001.15 Modules
| |||||||||||||||
Total events
1 715
Read events
455
Write events
1 260
Delete events
0
Modification events
| (PID) Process: | (2708) LaoMaoTao(1).exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
| (PID) Process: | (2708) LaoMaoTao(1).exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 1 | |||
| (PID) Process: | (2640) LaoMaoTao.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\LaoMaoTao |
| Operation: | write | Name: | DisplayIcon |
Value: C:\LaoMaoTao\LaoMaoTao.exe | |||
| (PID) Process: | (2640) LaoMaoTao.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\LaoMaoTao |
| Operation: | write | Name: | DisplayName |
Value: 老毛桃U盘启动装机工具 | |||
| (PID) Process: | (2640) LaoMaoTao.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\LaoMaoTao |
| Operation: | write | Name: | DisplayVersion |
Value: 9.5.2001.15 | |||
| (PID) Process: | (2640) LaoMaoTao.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\LaoMaoTao |
| Operation: | write | Name: | InstallLocation |
Value: C:\LaoMaoTao\ | |||
| (PID) Process: | (2640) LaoMaoTao.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\LaoMaoTao |
| Operation: | write | Name: | UninstallString |
Value: "C:\LaoMaoTao\LaoMaoTao.exe" /uninst | |||
| (PID) Process: | (2640) LaoMaoTao.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\LaoMaoTao |
| Operation: | write | Name: | URLInfoAbout |
Value: http://www.laomaotao.net/ | |||
| (PID) Process: | (2160) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateLowDateTime |
Value: 2279339442 | |||
| (PID) Process: | (2160) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateHighDateTime |
Value: 30818398 | |||
Executable files
47
Suspicious files
15
Text files
52
Unknown types
9
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2640 | LaoMaoTao.exe | C:\Users\admin\AppData\Local\Temp\A426.tmp | — | |
MD5:— | SHA256:— | |||
| 2640 | LaoMaoTao.exe | C:\LaoMaoTao\Data\Hash | text | |
MD5:— | SHA256:— | |||
| 2708 | LaoMaoTao(1).exe | C:\LaoMaoTao\LaoMaoTao.exe | executable | |
MD5:— | SHA256:— | |||
| 2708 | LaoMaoTao(1).exe | C:\ProgramData\Microsoft\Windows\Start Menu\Programs\老毛桃U盘启动装机工具.lnk | lnk | |
MD5:— | SHA256:— | |||
| 2708 | LaoMaoTao(1).exe | C:\Users\Public\Desktop\老毛桃U盘启动装机工具.lnk | lnk | |
MD5:— | SHA256:— | |||
| 2640 | LaoMaoTao.exe | C:\LaoMaoTao\Data\Bin\download\minizip.dll | executable | |
MD5:7FD4F79ACA0B09FD3A60841A47CA96E7 | SHA256:FC10C877E2BCFAB35758446A72A8DB704D8E8455470D65A6DE5492C10C8D6786 | |||
| 2640 | LaoMaoTao.exe | C:\LaoMaoTao\Data\Bin\download\id.dat | text | |
MD5:627C002647DD2F1B1CD0FE4C349A5E8A | SHA256:50056A44AC332C4E47FDDFF079E1E0988DE2835B0AA1CDE31587CEFA1B0A45AA | |||
| 2640 | LaoMaoTao.exe | C:\LaoMaoTao\Data\Bin\7za.dll | executable | |
MD5:93AA6A76E2F245C85C76FB4C993BC9CB | SHA256:0C19B611525E2B4FB5F04581B61F4119821A10EABDF73151F22BE18DB2C805B8 | |||
| 2640 | LaoMaoTao.exe | C:\LaoMaoTao\Data\Bin\download\atl71.dll | executable | |
MD5:79CB6457C81ADA9EB7F2087CE799AAA7 | SHA256:A68E1297FAE2BCF854B47FFA444F490353028DE1FA2CA713B6CF6CC5AA22B88A | |||
| 2640 | LaoMaoTao.exe | C:\LaoMaoTao\Data\Bin\bcdedit.exe | executable | |
MD5:C4D5B7B0CC017C7F5B906252A3F42C11 | SHA256:1D5A0320882BE0882BAD0D9A01B265533E359739E5552FBD94D2C49AA62940B3 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
9
TCP/UDP connections
26
DNS requests
14
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2180 | iexplore.exe | GET | 200 | 104.18.20.226:80 | http://ocsp2.globalsign.com/gsorganizationvalsha2g2/ME0wSzBJMEcwRTAJBgUrDgMCGgUABBQMnk2cPe3vhNiR6XLHz4QGvBl7BwQUlt5h8b0cFilTHMDMfTuDAEDmGnwCDEoqB3LuF7k61ZFD5g%3D%3D | US | der | 1.54 Kb | whitelisted |
2180 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTBL0V27RVZ7LBduom%2FnYB45SPUEwQU5Z1ZMIJHWMys%2BghUNoZ7OrUETfACEA8sEMlbBsCTf7jUSfg%2BhWk%3D | US | der | 1.47 Kb | whitelisted |
2180 | iexplore.exe | GET | 200 | 104.18.20.226:80 | http://ocsp2.globalsign.com/gsorganizationvalsha2g2/ME0wSzBJMEcwRTAJBgUrDgMCGgUABBQMnk2cPe3vhNiR6XLHz4QGvBl7BwQUlt5h8b0cFilTHMDMfTuDAEDmGnwCDEoqB3LuF7k61ZFD5g%3D%3D | US | der | 1.54 Kb | whitelisted |
2180 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSXi0cW5bD2WLrmnasWibg2OuPDpgQUVXRPsnJP9WC6UNHX5lFcmgGHGtcCEATftd5w0Cg8q9Yez6AYC2I%3D | US | der | 471 b | whitelisted |
2180 | iexplore.exe | GET | 301 | 125.77.154.35:80 | http://www.laomaotao.net/ | CN | html | 168 b | malicious |
2180 | iexplore.exe | GET | 200 | 104.18.20.226:80 | http://ocsp2.globalsign.com/gsorganizationvalsha2g2/ME0wSzBJMEcwRTAJBgUrDgMCGgUABBQMnk2cPe3vhNiR6XLHz4QGvBl7BwQUlt5h8b0cFilTHMDMfTuDAEDmGnwCDHJYeDZun1boHUGISA%3D%3D | US | der | 1.54 Kb | whitelisted |
2180 | iexplore.exe | GET | 200 | 104.18.20.226:80 | http://ocsp.globalsign.com/rootr1/MEwwSjBIMEYwRDAJBgUrDgMCGgUABBS3V7W2nAf4FiMTjpDJKg6%2BMgGqMQQUYHtmGkUNl8qJUC99BM00qP%2F8%2FUsCCwQAAAAAAURO8EJH | US | der | 1.49 Kb | whitelisted |
2180 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ5rEWLwbJFq%2FmAU80sm7E%3D | US | der | 471 b | whitelisted |
2160 | iexplore.exe | GET | 200 | 13.107.21.200:80 | http://www.bing.com/favicon.ico | US | image | 237 b | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2180 | iexplore.exe | 125.77.154.35:80 | www.laomaotao.net | No.31,Jin-rong Street | CN | malicious |
2180 | iexplore.exe | 125.77.154.35:443 | www.laomaotao.net | No.31,Jin-rong Street | CN | malicious |
— | — | 13.107.21.200:80 | www.bing.com | Microsoft Corporation | US | whitelisted |
2180 | iexplore.exe | 93.184.220.29:80 | ocsp.digicert.com | MCI Communications Services, Inc. d/b/a Verizon Business | US | whitelisted |
2180 | iexplore.exe | 101.89.124.234:443 | s4.cnzz.com | China Telecom (Group) | CN | unknown |
2180 | iexplore.exe | 203.119.129.115:443 | z3.cnzz.com | — | CN | malicious |
2180 | iexplore.exe | 103.235.46.191:443 | hm.baidu.com | Beijing Baidu Netcom Science and Technology Co., Ltd. | HK | suspicious |
2180 | iexplore.exe | 104.18.20.226:80 | ocsp.globalsign.com | Cloudflare Inc | US | shared |
2180 | iexplore.exe | 152.199.19.161:443 | iecvlist.microsoft.com | MCI Communications Services, Inc. d/b/a Verizon Business | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
www.laomaotao.net |
| malicious |
api.bing.com |
| whitelisted |
www.bing.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
hm.baidu.com |
| whitelisted |
ocsp.globalsign.com |
| whitelisted |
ocsp2.globalsign.com |
| whitelisted |
s4.cnzz.com |
| whitelisted |
z3.cnzz.com |
| whitelisted |
c.cnzz.com |
| whitelisted |
Threats
Process | Message |
|---|---|
Dism.exe | PID=1736 Attempting to initialize the logger from the Image Session. - CDISMProviderStore::Final_OnConnect |
Dism.exe | PID=1736 Initializing a provider store for the LOCAL session type. - CDISMProviderStore::Final_OnConnect |
Dism.exe | PID=1736 Loading Provider from location C:\Windows\System32\Dism\LogProvider.dll - CDISMProviderStore::Internal_GetProvider |
Dism.exe | PID=1736 Provider has not previously been encountered. Attempting to initialize the provider. - CDISMProviderStore::Internal_GetProvider |
Dism.exe | PID=1736 Instantiating the Provider Store. - CDISMImageSession::get_ProviderStore |
Dism.exe | PID=1736 Getting Provider OSServices - CDISMProviderStore::GetProvider |
Dism.exe | PID=1736 The requested provider was not found in the Provider Store. - CDISMProviderStore::Internal_GetProvider(hr:0x80004005) |
Dism.exe | PID=1736 Getting Provider OSServices - CDISMProviderStore::GetProvider |
Dism.exe | PID=1736 Failed to get an OSServices provider. Must be running in local store. Falling back to checking alongside the log provider for wdscore.dll. - CDISMLogger::FindWdsCore(hr:0x80004005) |
Dism.exe | PID=1736 Encountered a loaded provider DISMLogger. - CDISMProviderStore::Internal_DisconnectProvider |