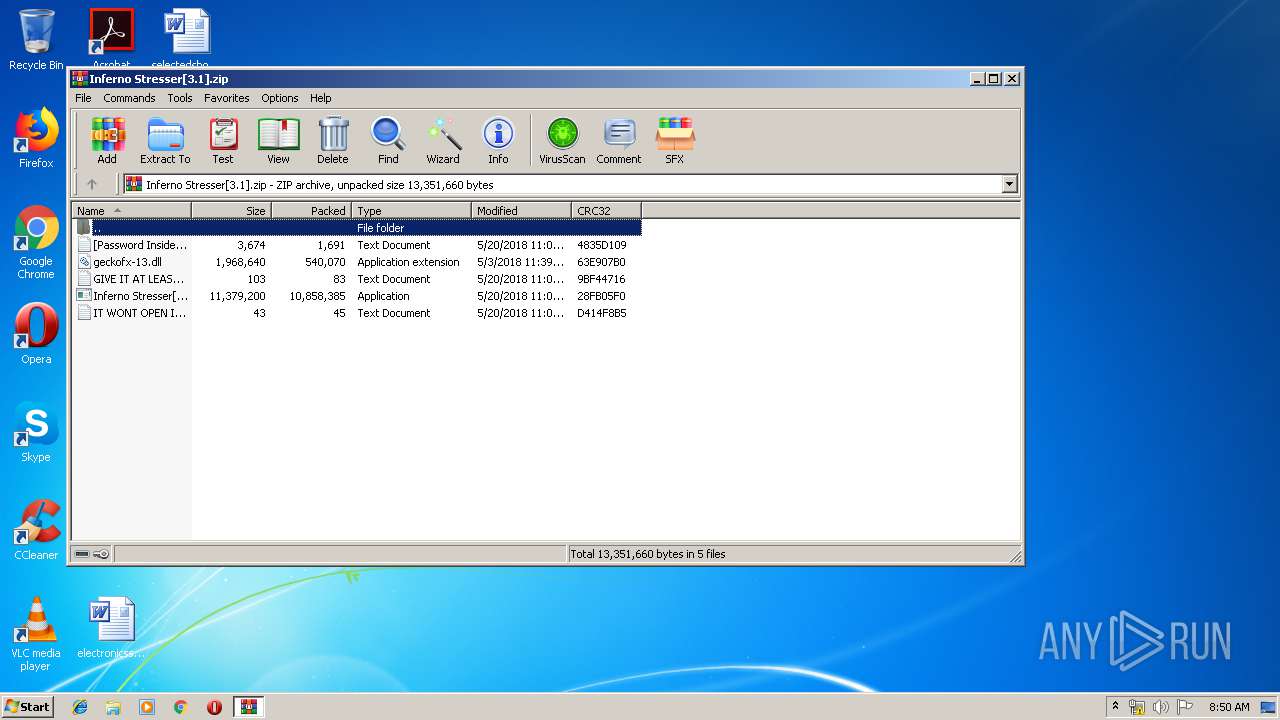
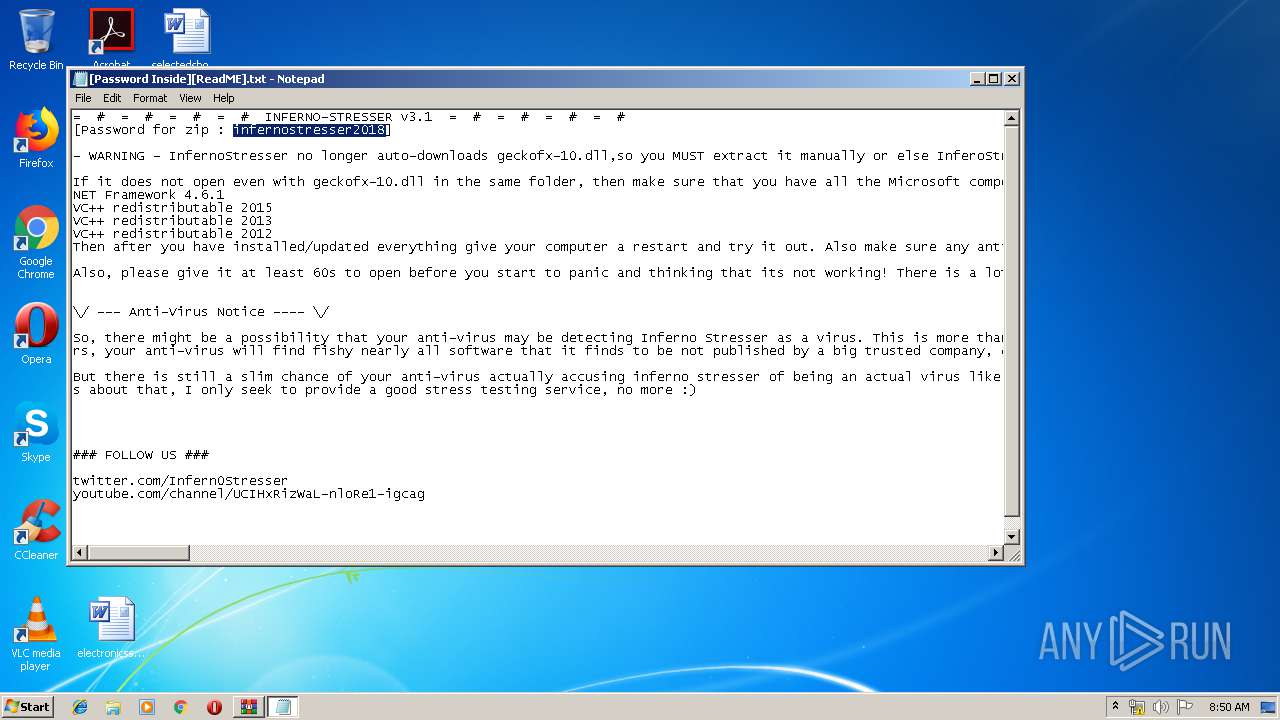
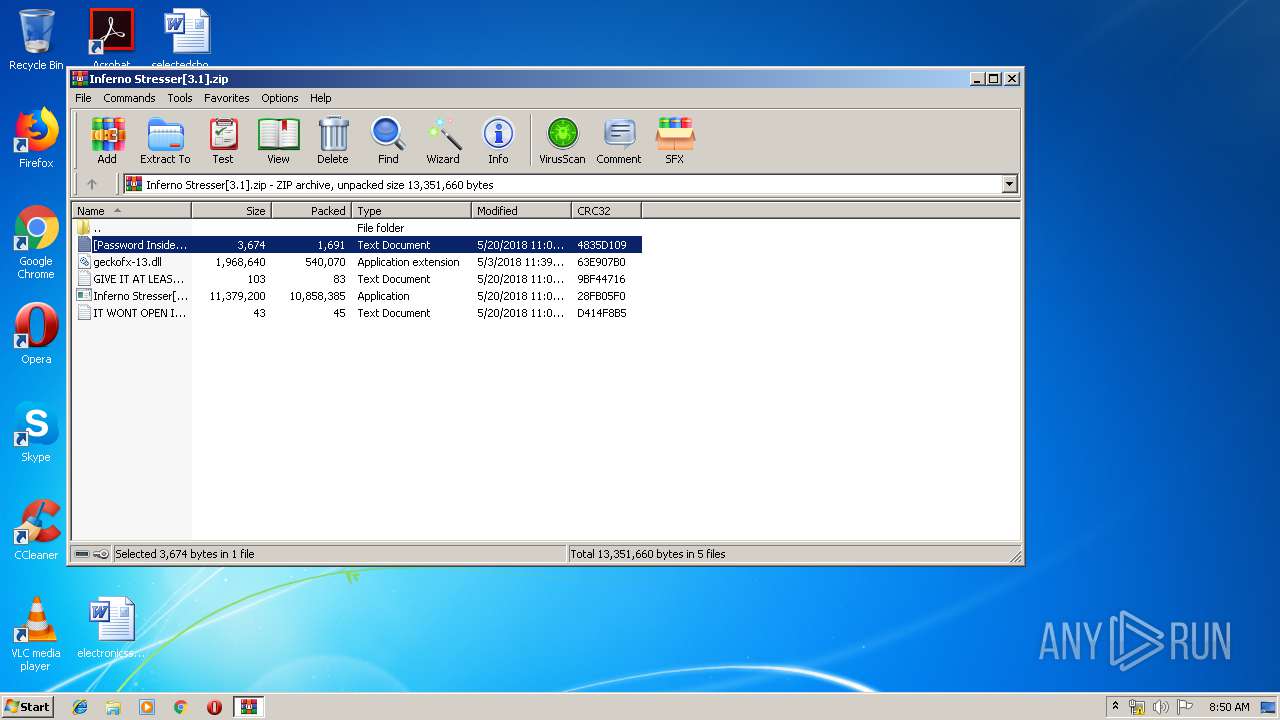
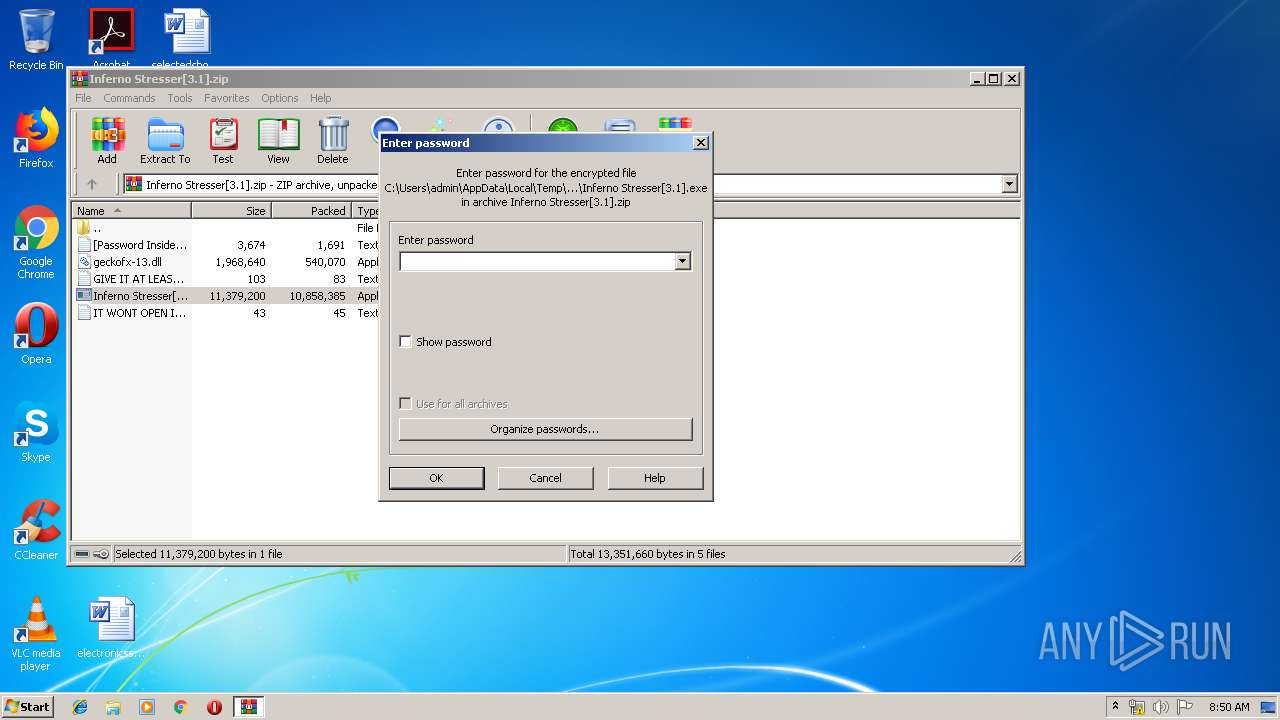
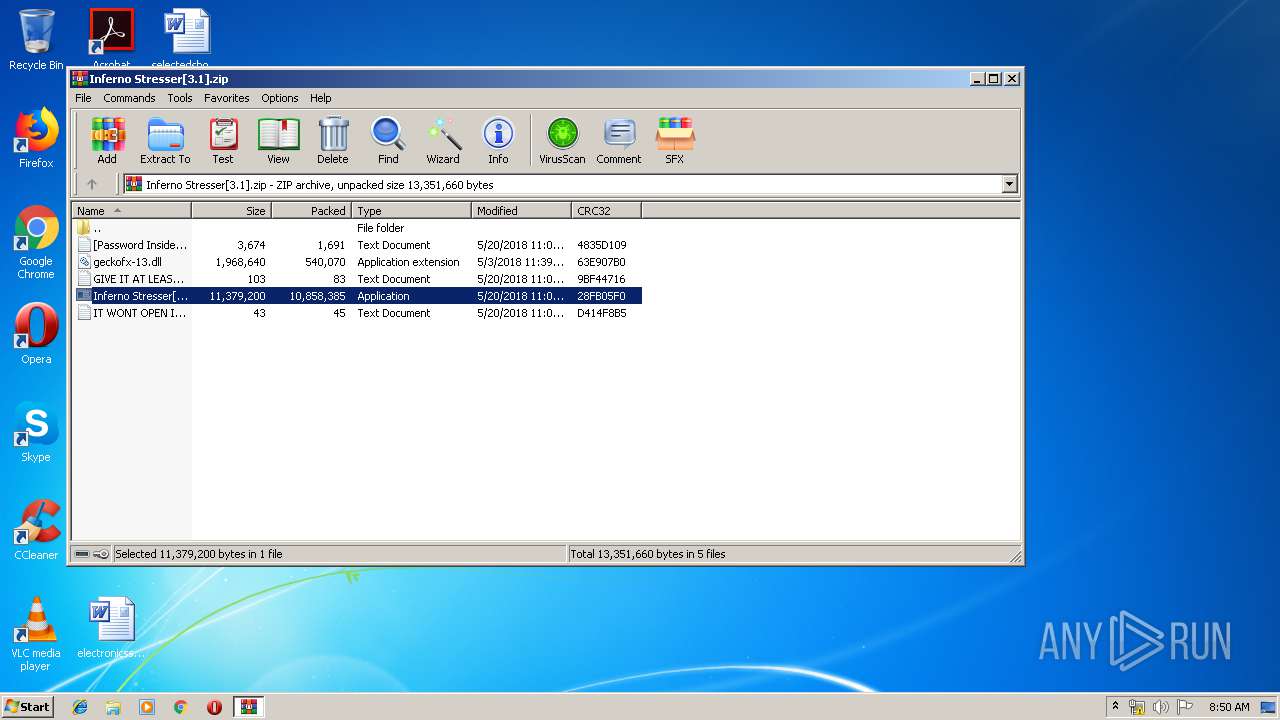
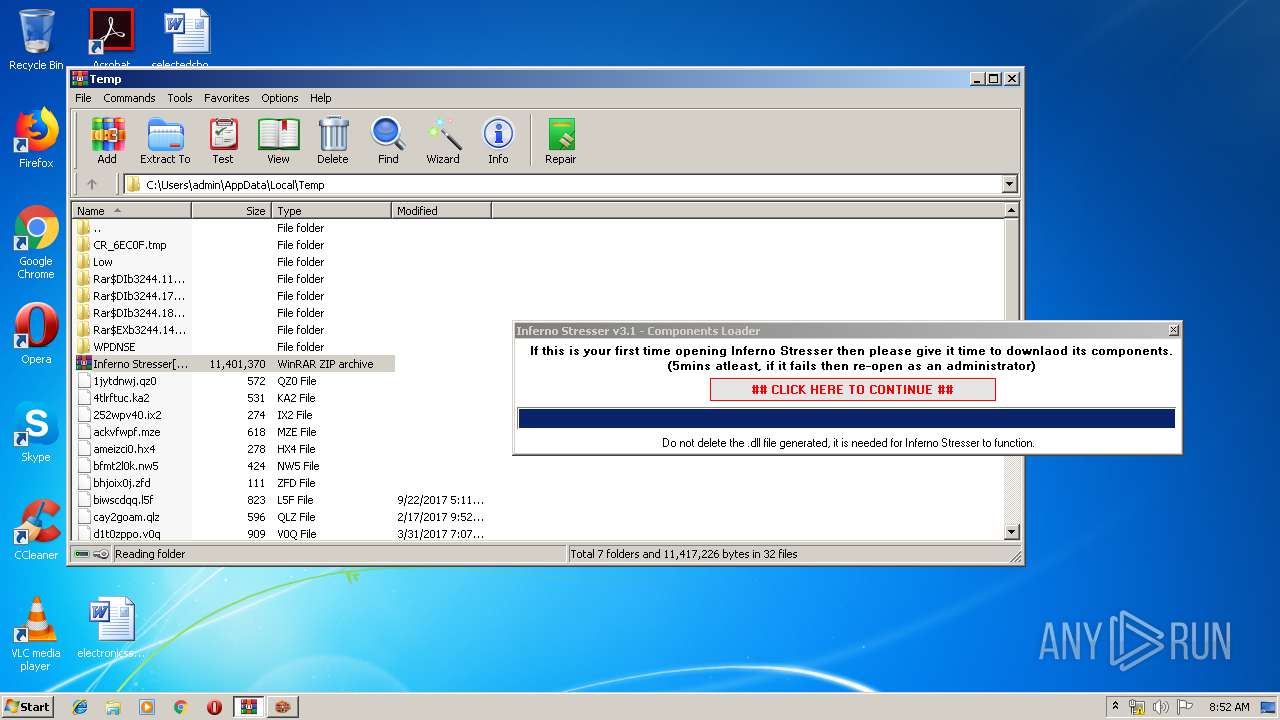
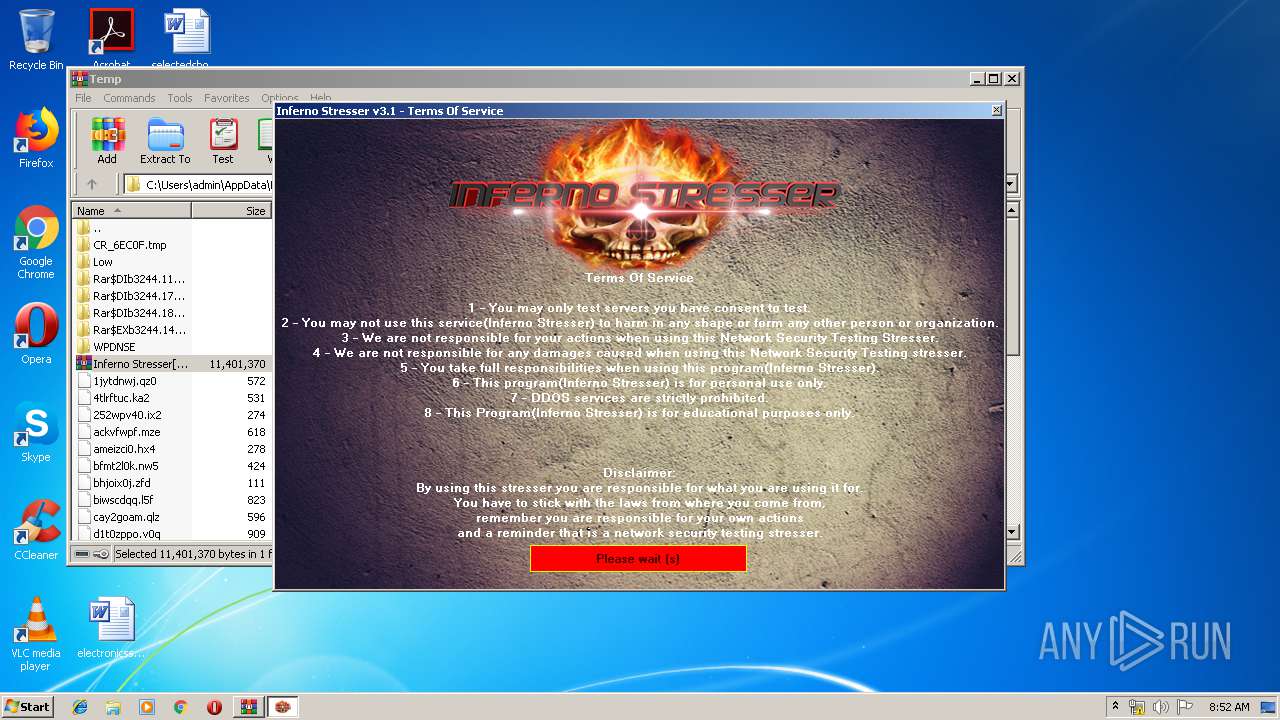
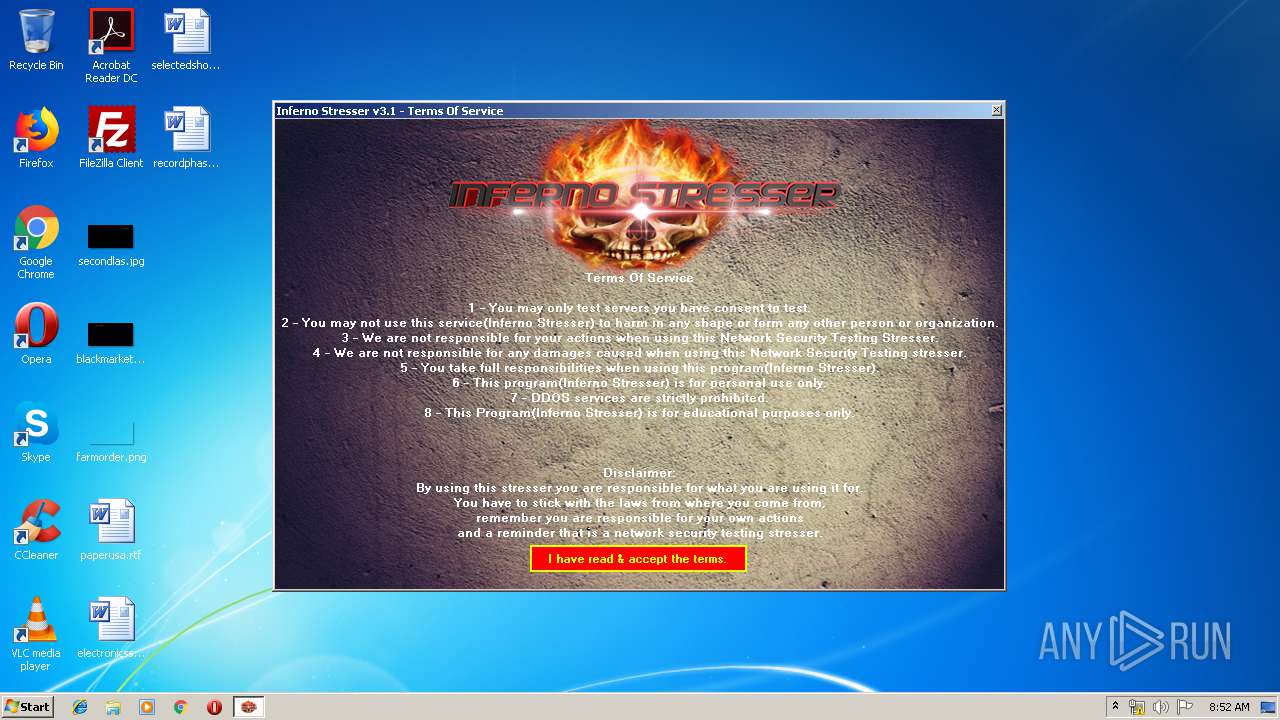
| File name: | Inferno Stresser[3.1].zip |
| Full analysis: | https://app.any.run/tasks/fca0bf63-837b-4f62-b7dc-8bb6667ee295 |
| Verdict: | Malicious activity |
| Analysis date: | May 15, 2019, 07:49:24 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract |
| MD5: | F3D7C89D4BE9EE88B267E9F15FF83E30 |
| SHA1: | 3957C08B6B79101A21DB8563D69C56B2689F79AD |
| SHA256: | 90E5ECD5BF7CCEC925A0001199F66AC456459F8E55237F0EE672CF223E6B1F1A |
| SSDEEP: | 196608:ceMVWiRvQ09RYNu5W3UEdcHXLZSo0hKAKdIzJOZOMxzwwerIRnCziaD0aB8GNKru:CVWS4SYc5W3zyLV0RKdgJKDzwwe8RuRD |
MALICIOUS
Loads dropped or rewritten executable
- Inferno Stresser[3.1].exe (PID: 2504)
- SearchProtocolHost.exe (PID: 3824)
Application was dropped or rewritten from another process
- Inferno Stresser[3.1].exe (PID: 2504)
SUSPICIOUS
Executable content was dropped or overwritten
- WinRAR.exe (PID: 3244)
- Inferno Stresser[3.1].exe (PID: 2504)
Reads Environment values
- Inferno Stresser[3.1].exe (PID: 2504)
Creates files in the user directory
- Inferno Stresser[3.1].exe (PID: 2504)
Reads Internet Cache Settings
- Inferno Stresser[3.1].exe (PID: 2504)
Reads internet explorer settings
- Inferno Stresser[3.1].exe (PID: 2504)
INFO
No info indicators.
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | 0x0009 |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2018:05:20 11:00:16 |
| ZipCRC: | 0x28fb05f0 |
| ZipCompressedSize: | 10858385 |
| ZipUncompressedSize: | 11379200 |
| ZipFileName: | Inferno Stresser[3.1].exe |
Total processes
37
Monitored processes
6
Malicious processes
3
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
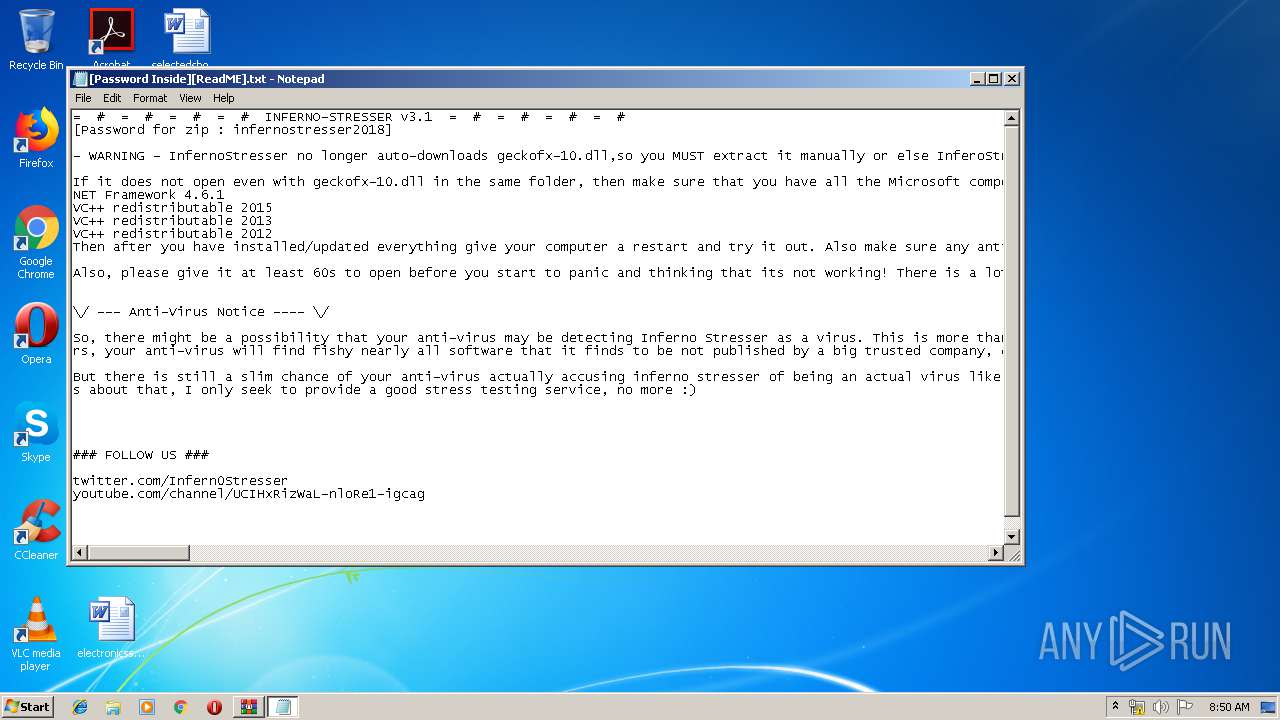
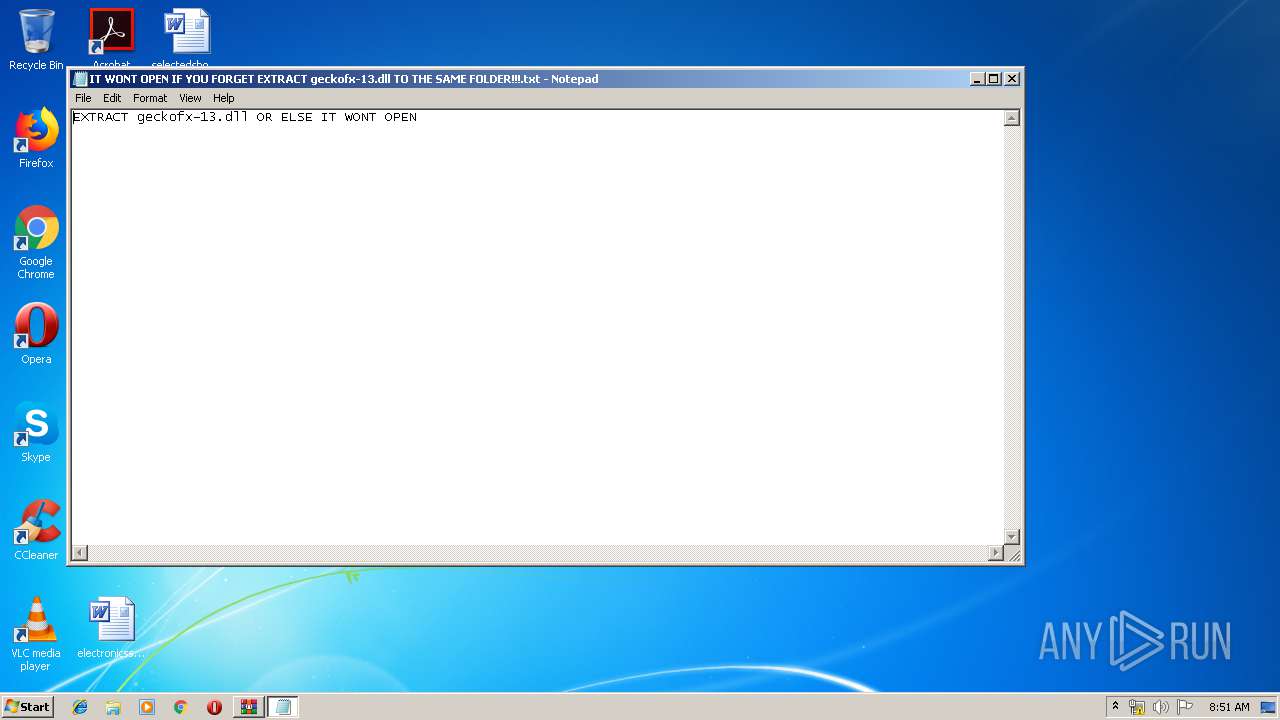
| 1860 | "C:\Windows\system32\NOTEPAD.EXE" C:\Users\admin\AppData\Local\Temp\Rar$DIb3244.18683\IT WONT OPEN IF YOU FORGET EXTRACT geckofx-13.dll TO THE SAME FOLDER!!!.txt | C:\Windows\system32\NOTEPAD.EXE | — | WinRAR.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Notepad Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2148 | "C:\Windows\system32\NOTEPAD.EXE" C:\Users\admin\AppData\Local\Temp\Rar$DIb3244.11892\[Password Inside][ReadME].txt | C:\Windows\system32\NOTEPAD.EXE | — | WinRAR.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Notepad Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2504 | "C:\Users\admin\AppData\Local\Temp\Rar$EXb3244.14712\Inferno Stresser[3.1].exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXb3244.14712\Inferno Stresser[3.1].exe | WinRAR.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Description: Inferno-Stresser Exit code: 0 Version: 3.0.0.0 Modules
| |||||||||||||||
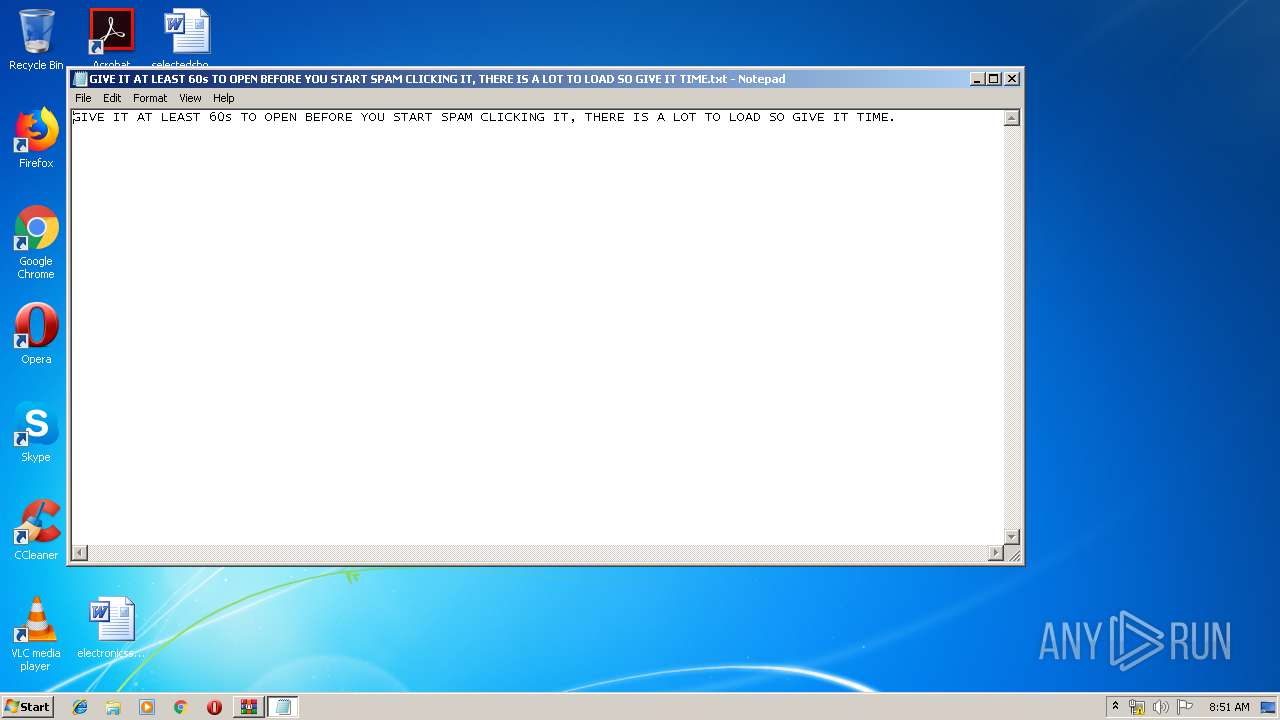
| 3128 | "C:\Windows\system32\NOTEPAD.EXE" C:\Users\admin\AppData\Local\Temp\Rar$DIb3244.17667\GIVE IT AT LEAST 60s TO OPEN BEFORE YOU START SPAM CLICKING IT, THERE IS A LOT TO LOAD SO GIVE IT TIME.txt | C:\Windows\system32\NOTEPAD.EXE | — | WinRAR.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Notepad Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3244 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\Inferno Stresser[3.1].zip" | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.60.0 Modules
| |||||||||||||||
| 3824 | "C:\Windows\system32\SearchProtocolHost.exe" Global\UsGthrFltPipeMssGthrPipe6_ Global\UsGthrCtrlFltPipeMssGthrPipe6 1 -2147483646 "Software\Microsoft\Windows Search" "Mozilla/4.0 (compatible; MSIE 6.0; Windows NT; MS Search 4.0 Robot)" "C:\ProgramData\Microsoft\Search\Data\Temp\usgthrsvc" "DownLevelDaemon" | C:\Windows\system32\SearchProtocolHost.exe | — | SearchIndexer.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft Windows Search Protocol Host Exit code: 0 Version: 7.00.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
1 217
Read events
1 134
Write events
83
Delete events
0
Modification events
| (PID) Process: | (3244) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (3244) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (3244) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\62\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3244) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\Inferno Stresser[3.1].zip | |||
| (PID) Process: | (3244) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (3244) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (3244) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (3244) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (3244) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\62\52C64B7E |
| Operation: | write | Name: | @C:\Windows\system32\notepad.exe,-469 |
Value: Text Document | |||
| (PID) Process: | (2148) NOTEPAD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Notepad |
| Operation: | write | Name: | iWindowPosX |
Value: 66 | |||
Executable files
39
Suspicious files
7
Text files
61
Unknown types
1
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3244 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DIb3244.11892\[Password Inside][ReadME].txt | text | |
MD5:— | SHA256:— | |||
| 3244 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXb3244.14712\IT WONT OPEN IF YOU FORGET EXTRACT geckofx-13.dll TO THE SAME FOLDER!!!.txt | text | |
MD5:— | SHA256:— | |||
| 3244 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXb3244.14712\geckofx-13.dll | executable | |
MD5:— | SHA256:— | |||
| 3244 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DIb3244.17667\GIVE IT AT LEAST 60s TO OPEN BEFORE YOU START SPAM CLICKING IT, THERE IS A LOT TO LOAD SO GIVE IT TIME.txt | text | |
MD5:— | SHA256:— | |||
| 3244 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DIb3244.18683\IT WONT OPEN IF YOU FORGET EXTRACT geckofx-13.dll TO THE SAME FOLDER!!!.txt | text | |
MD5:— | SHA256:— | |||
| 3244 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXb3244.14712\[Password Inside][ReadME].txt | text | |
MD5:— | SHA256:— | |||
| 3244 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXb3244.14712\Inferno Stresser[3.1].exe | executable | |
MD5:— | SHA256:— | |||
| 3244 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXb3244.14712\GIVE IT AT LEAST 60s TO OPEN BEFORE YOU START SPAM CLICKING IT, THERE IS A LOT TO LOAD SO GIVE IT TIME.txt | text | |
MD5:— | SHA256:— | |||
| 2504 | Inferno Stresser[3.1].exe | C:\Users\admin\AppData\Roaming\xul.zip | compressed | |
MD5:— | SHA256:— | |||
| 2504 | Inferno Stresser[3.1].exe | C:\Users\admin\AppData\Roaming\xulrunner\freebl3.chk | binary | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
28
TCP/UDP connections
22
DNS requests
13
Threats
1
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2504 | Inferno Stresser[3.1].exe | GET | 200 | 172.104.29.90:80 | http://www.supercounters.com/css/print.css | US | text | 671 b | malicious |
2504 | Inferno Stresser[3.1].exe | GET | 404 | 104.31.65.8:80 | http://inferno-stress.com/account/sys_cpanel/images/bottombody.jpg | US | html | 959 b | suspicious |
2504 | Inferno Stresser[3.1].exe | GET | 200 | 172.104.29.90:80 | http://www.supercounters.com/online/1029205 | US | binary | 4.33 Kb | malicious |
2504 | Inferno Stresser[3.1].exe | GET | 200 | 172.217.21.194:80 | http://pagead2.googlesyndication.com/pagead/js/r20190513/r20190131/show_ads_impl.js | US | text | 75.8 Kb | whitelisted |
2504 | Inferno Stresser[3.1].exe | GET | 200 | 172.104.29.90:80 | http://www.supercounters.com/js/jquery-1.6.1.min.js | US | html | 89.2 Kb | malicious |
2504 | Inferno Stresser[3.1].exe | GET | 200 | 172.104.29.90:80 | http://www.supercounters.com/js/g.js | US | text | 2.70 Kb | malicious |
2504 | Inferno Stresser[3.1].exe | GET | 200 | 23.210.248.44:80 | http://s7.addthis.com/js/300/addthis_widget.js | NL | text | 109 Kb | whitelisted |
2504 | Inferno Stresser[3.1].exe | GET | 200 | 172.217.21.194:80 | http://pagead2.googlesyndication.com/pagead/show_ads.js | US | text | 23.2 Kb | whitelisted |
2504 | Inferno Stresser[3.1].exe | GET | 404 | 104.31.65.8:80 | http://inferno-stress.com/account/ | US | html | 956 b | suspicious |
2504 | Inferno Stresser[3.1].exe | GET | 200 | 172.104.29.90:80 | http://www.supercounters.com/js/stats.js | US | html | 7.26 Kb | malicious |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2504 | Inferno Stresser[3.1].exe | 172.217.21.194:80 | pagead2.googlesyndication.com | Google Inc. | US | whitelisted |
2504 | Inferno Stresser[3.1].exe | 23.210.248.44:80 | s7.addthis.com | Akamai International B.V. | NL | whitelisted |
2504 | Inferno Stresser[3.1].exe | 13.35.250.7:443 | ftp.mozilla.org | — | US | suspicious |
2504 | Inferno Stresser[3.1].exe | 172.217.23.130:443 | googleads.g.doubleclick.net | Google Inc. | US | whitelisted |
2504 | Inferno Stresser[3.1].exe | 172.217.16.206:443 | apis.google.com | Google Inc. | US | whitelisted |
2504 | Inferno Stresser[3.1].exe | 172.217.18.174:80 | www.google-analytics.com | Google Inc. | US | whitelisted |
2504 | Inferno Stresser[3.1].exe | 172.217.22.100:443 | www.google.com | Google Inc. | US | whitelisted |
2504 | Inferno Stresser[3.1].exe | 66.102.1.157:443 | stats.g.doubleclick.net | Google Inc. | US | whitelisted |
2504 | Inferno Stresser[3.1].exe | 216.58.207.67:443 | www.google.be | Google Inc. | US | whitelisted |
2504 | Inferno Stresser[3.1].exe | 172.217.21.194:443 | pagead2.googlesyndication.com | Google Inc. | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
ftp.mozilla.org |
| whitelisted |
swaggy-freddy.in |
| unknown |
inferno-stress.com |
| suspicious |
www.supercounters.com |
| malicious |
pagead2.googlesyndication.com |
| whitelisted |
s7.addthis.com |
| whitelisted |
googleads.g.doubleclick.net |
| whitelisted |
connect.facebook.net |
| whitelisted |
apis.google.com |
| whitelisted |
www.google-analytics.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2504 | Inferno Stresser[3.1].exe | Misc activity | SUSPICIOUS [PTsecurity] Cmd.Powershell.Download HTTP UserAgent (Win7) |
Process | Message |
|---|---|
Inferno Stresser[3.1].exe | %s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s |