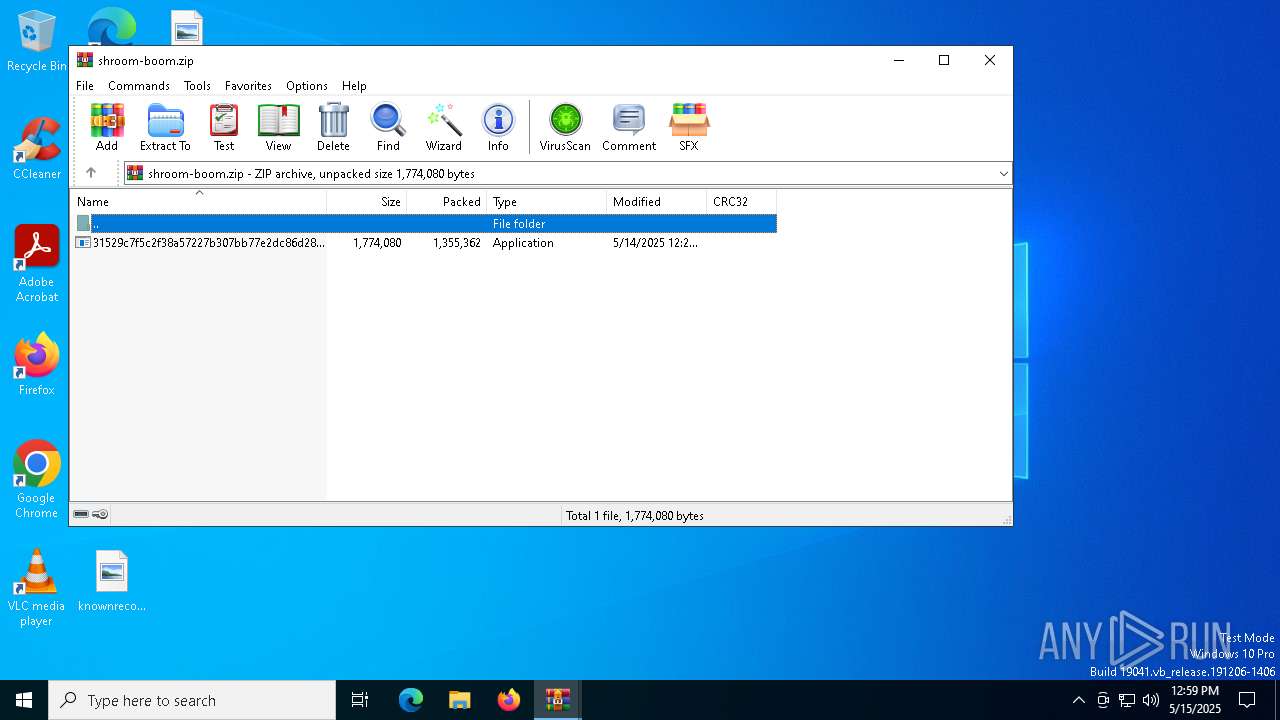
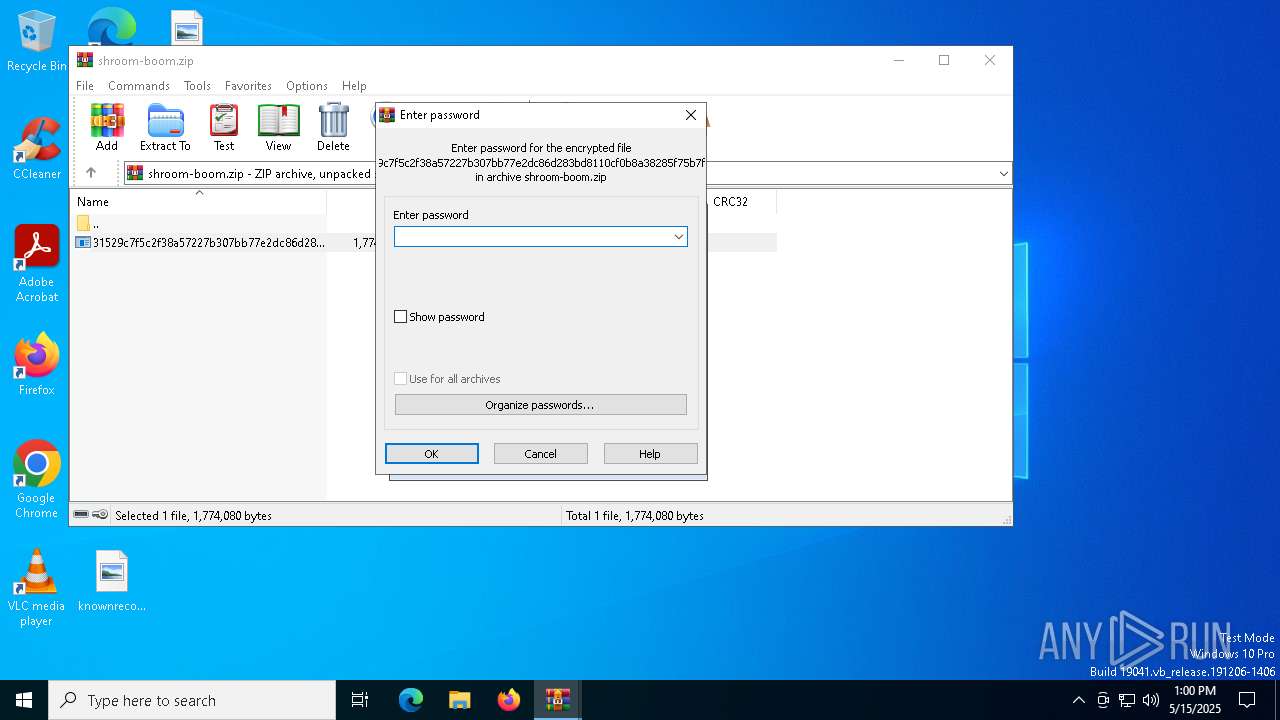
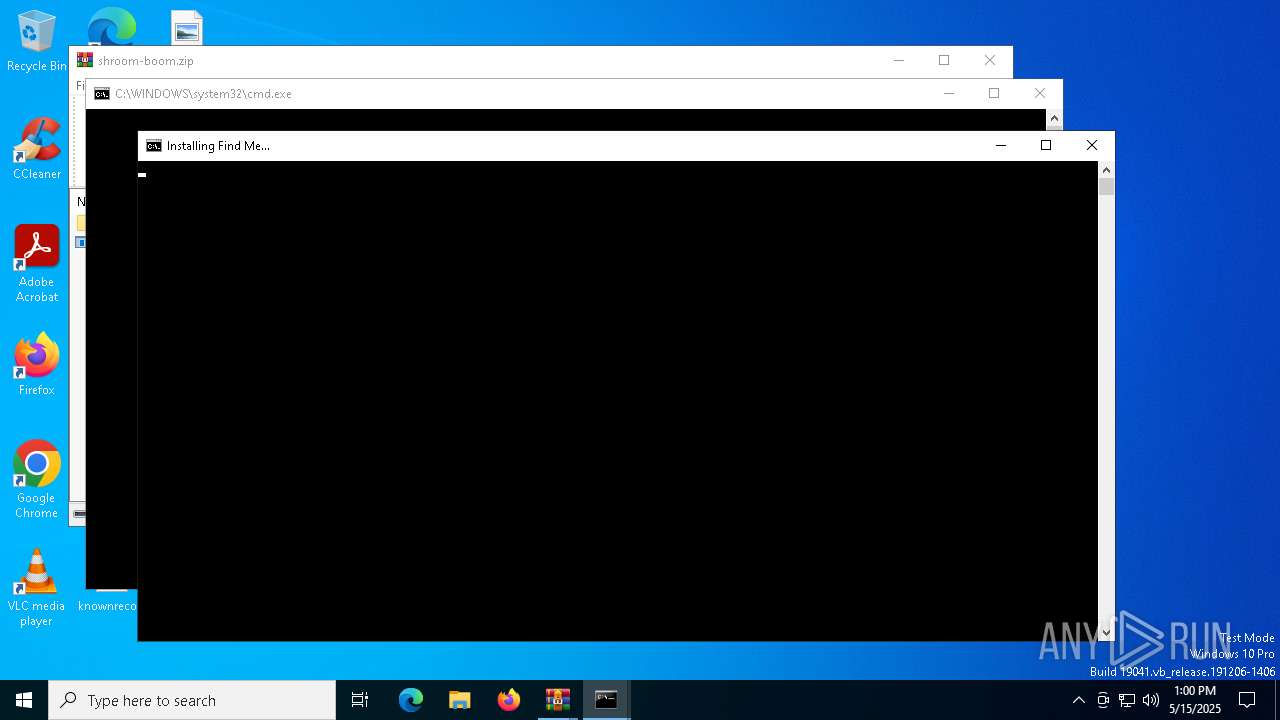
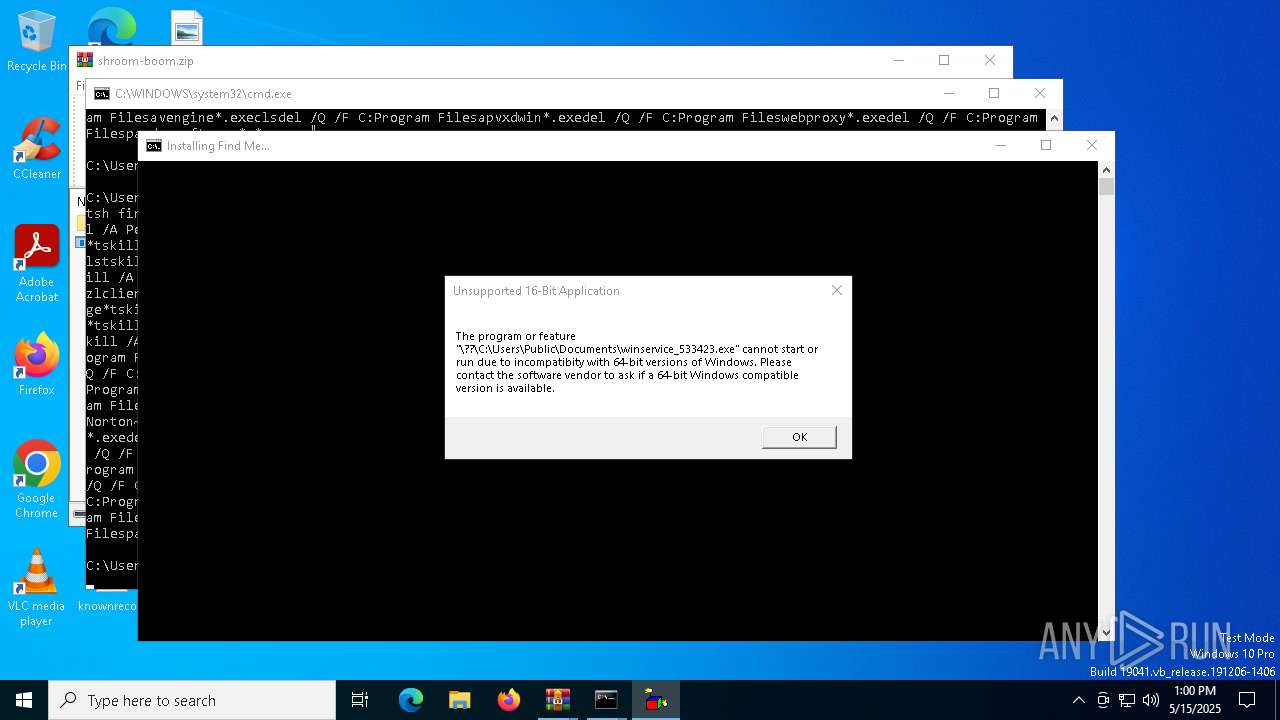
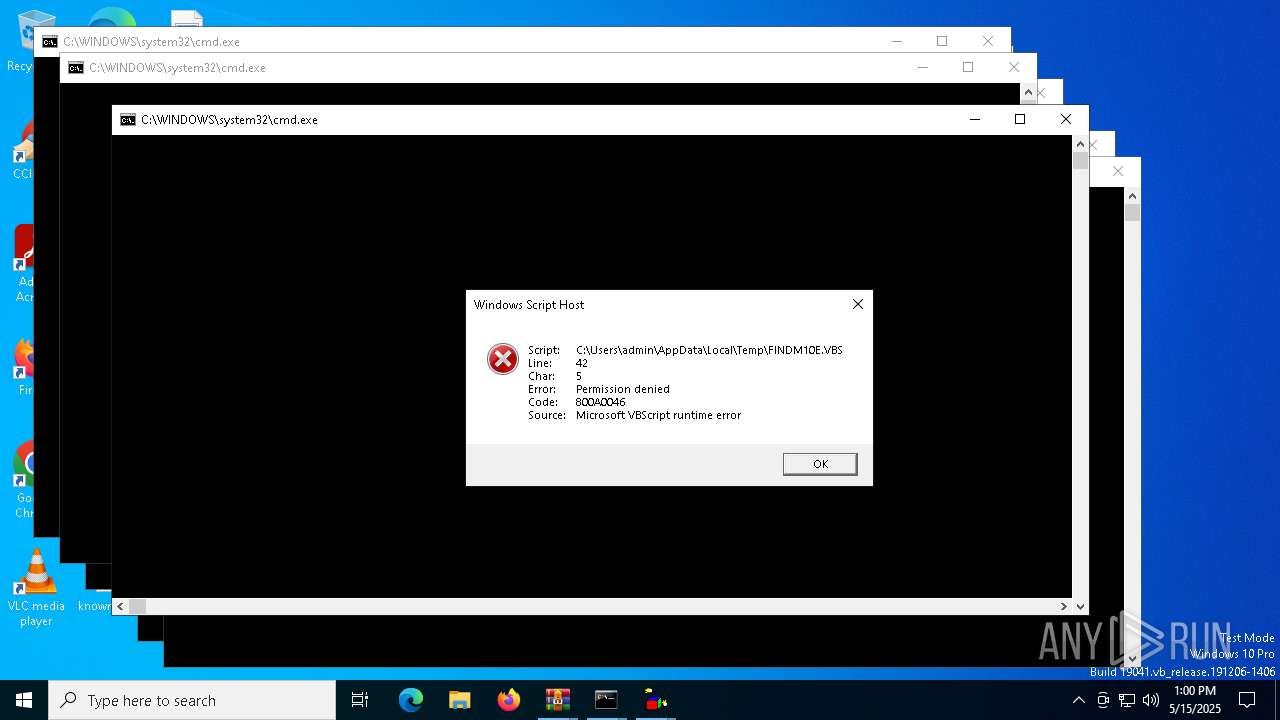
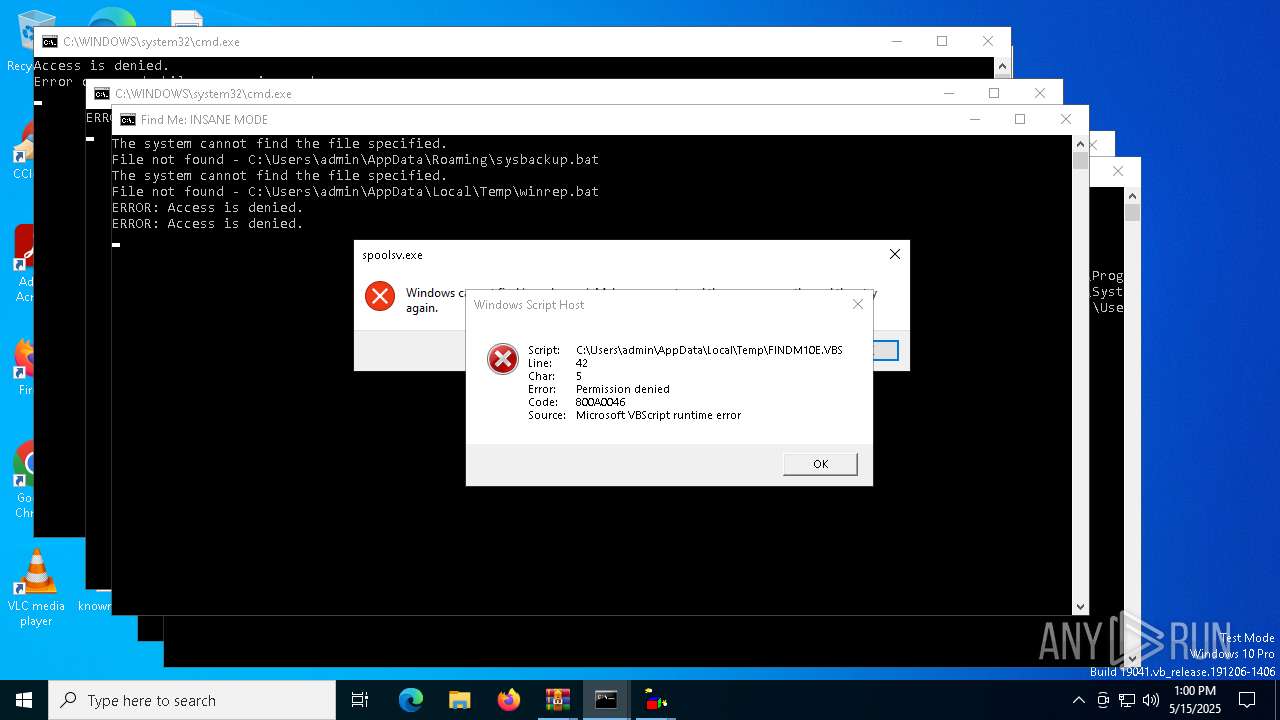
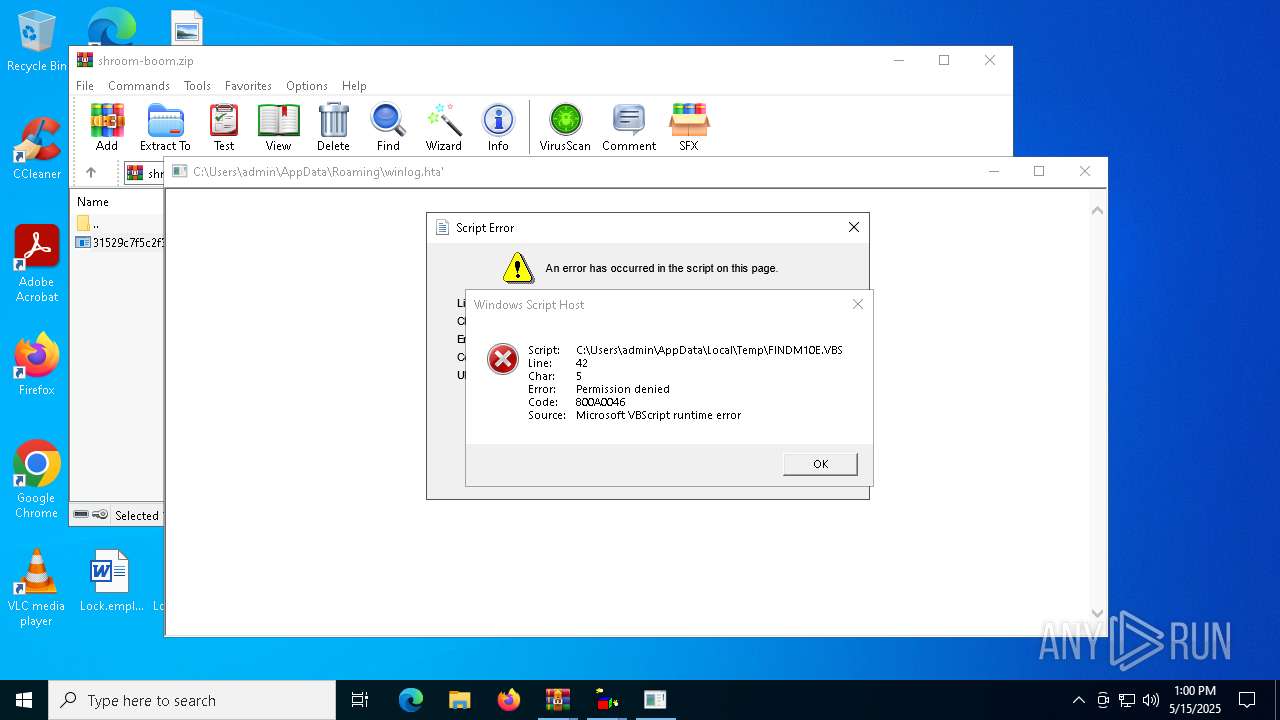
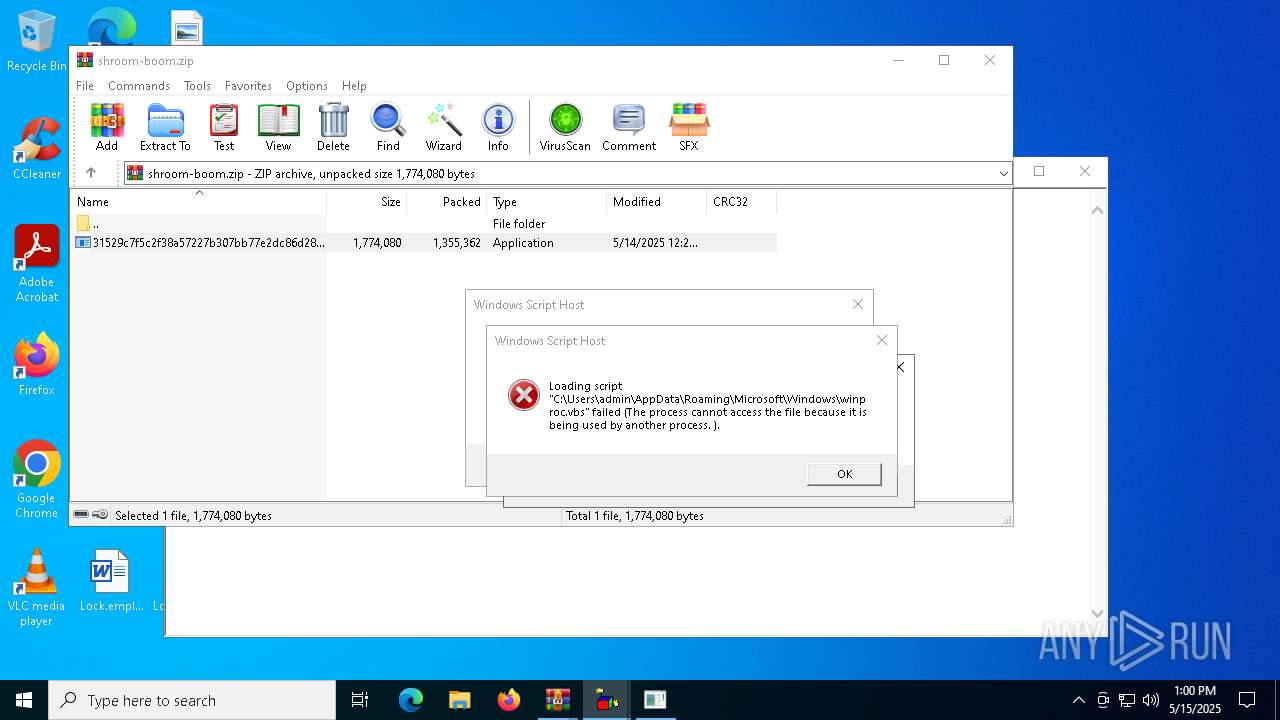
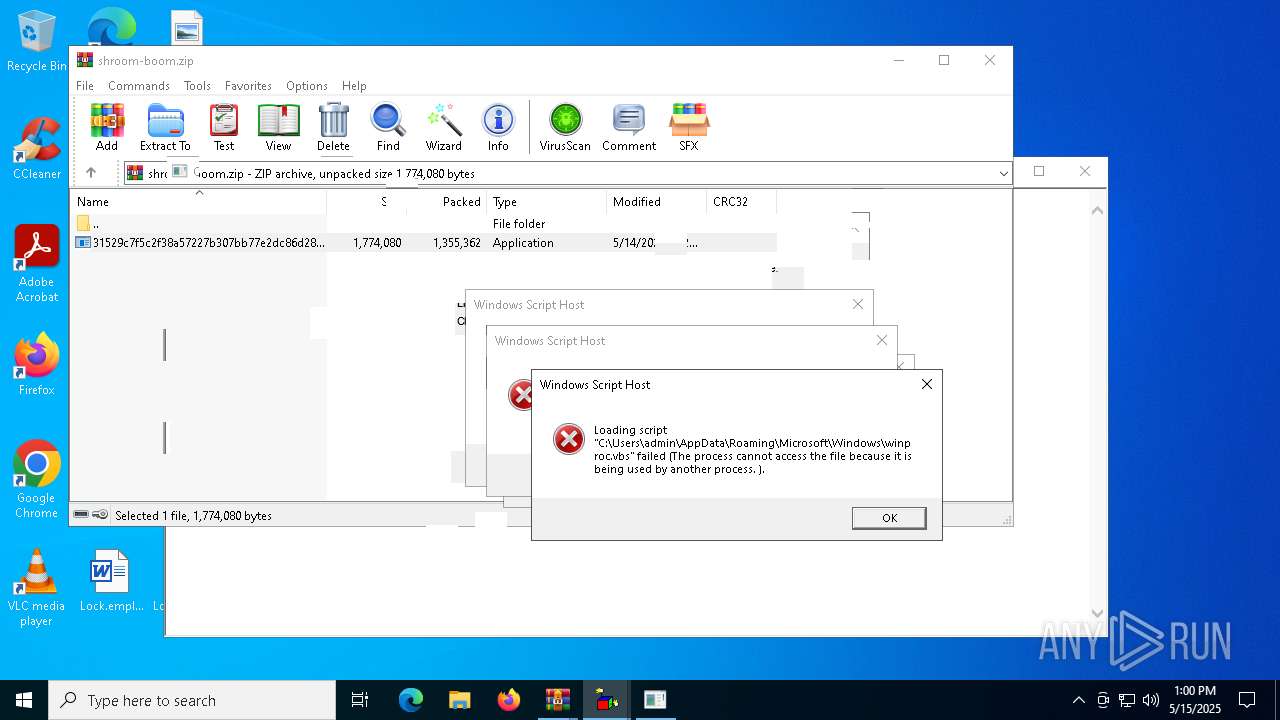
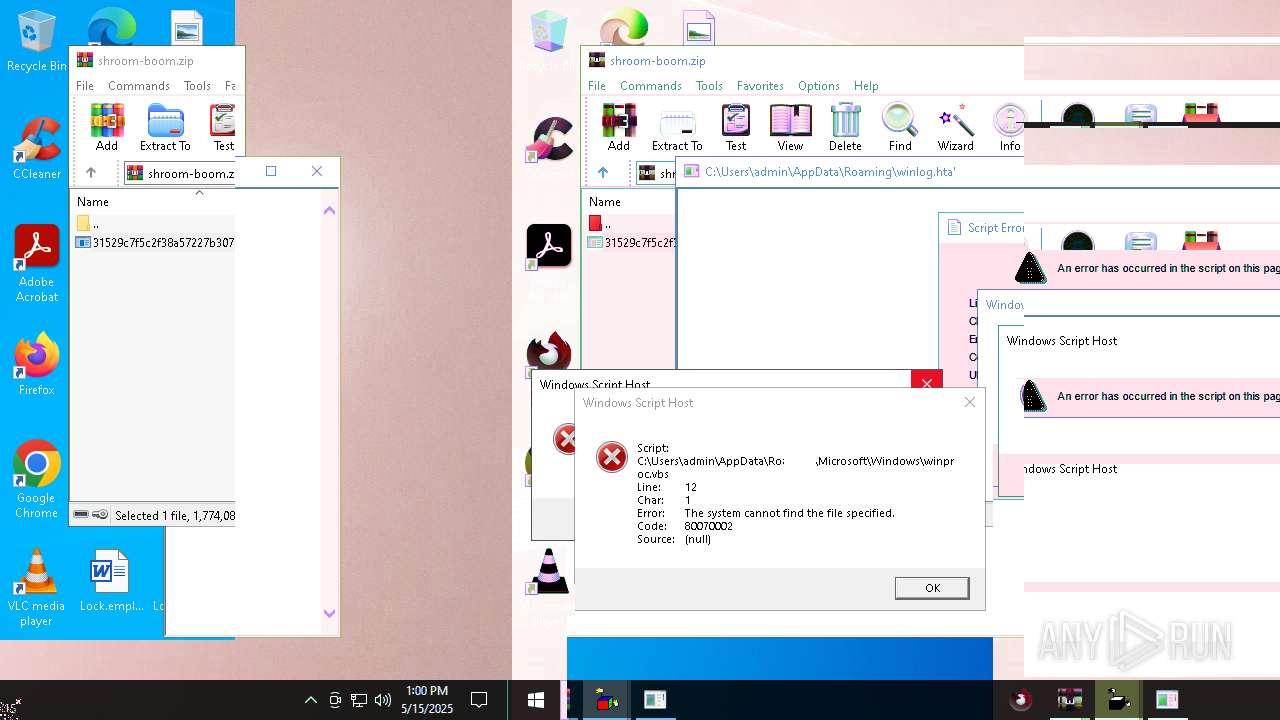
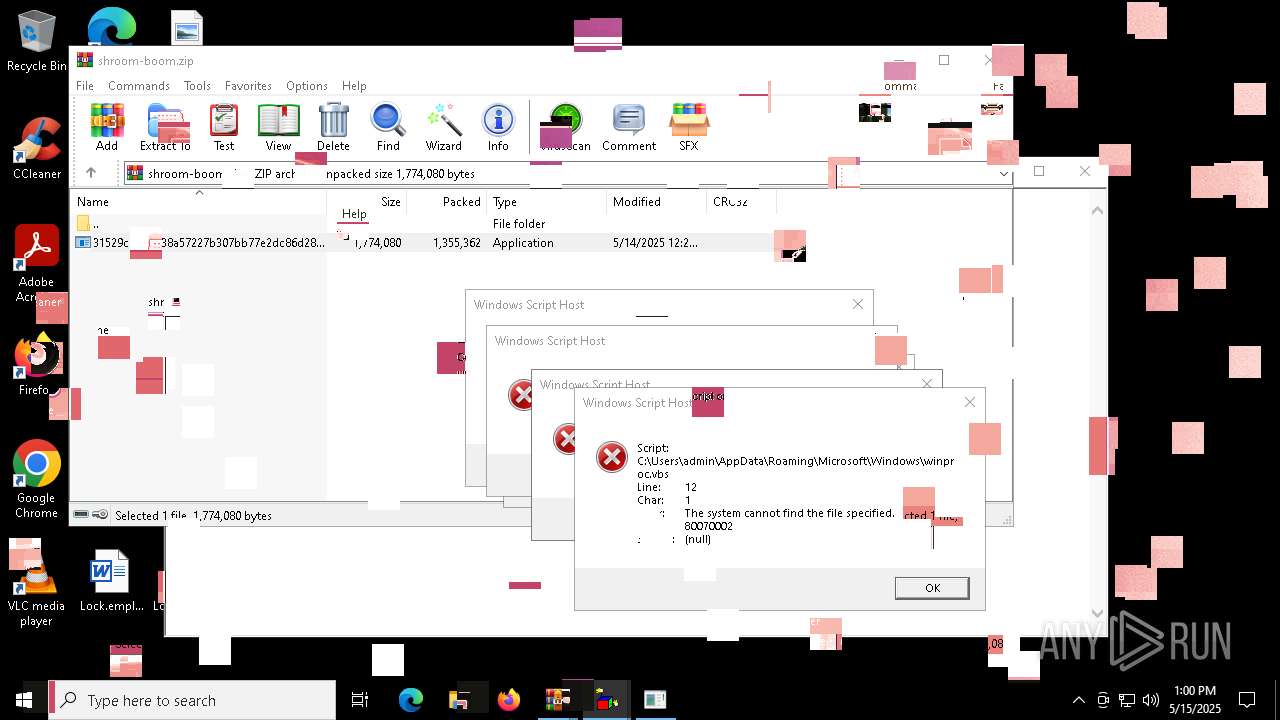
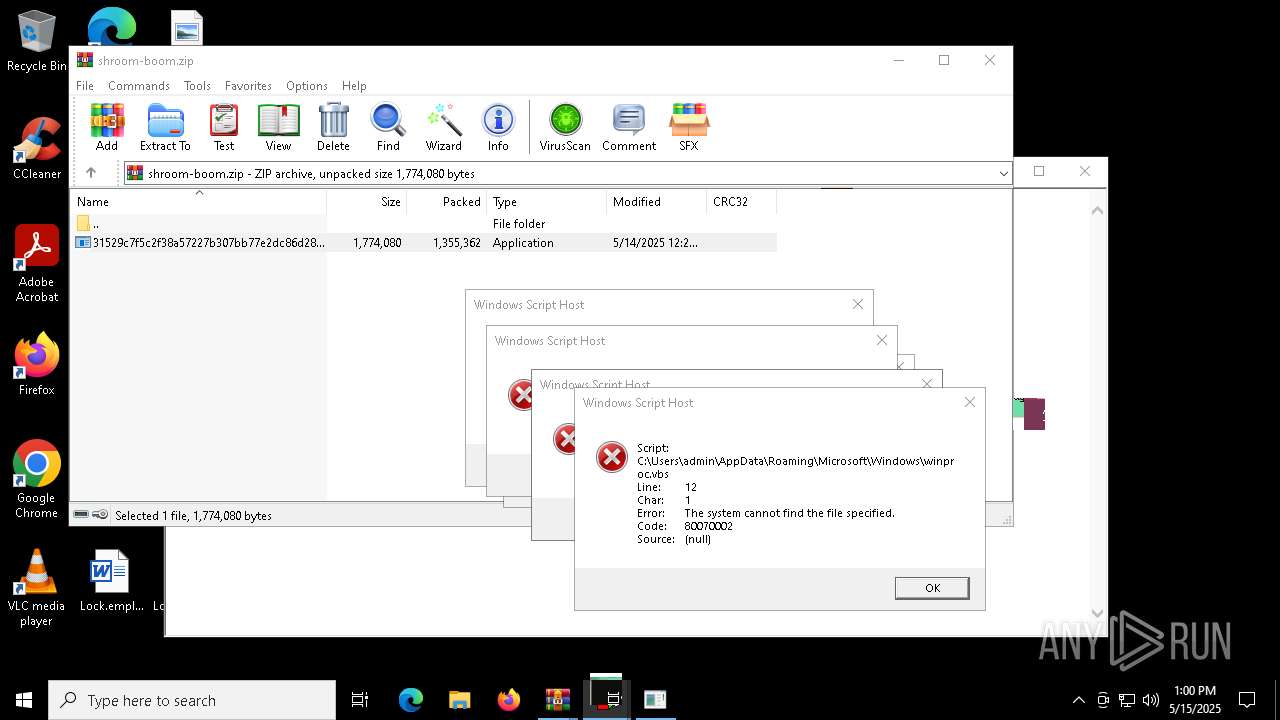
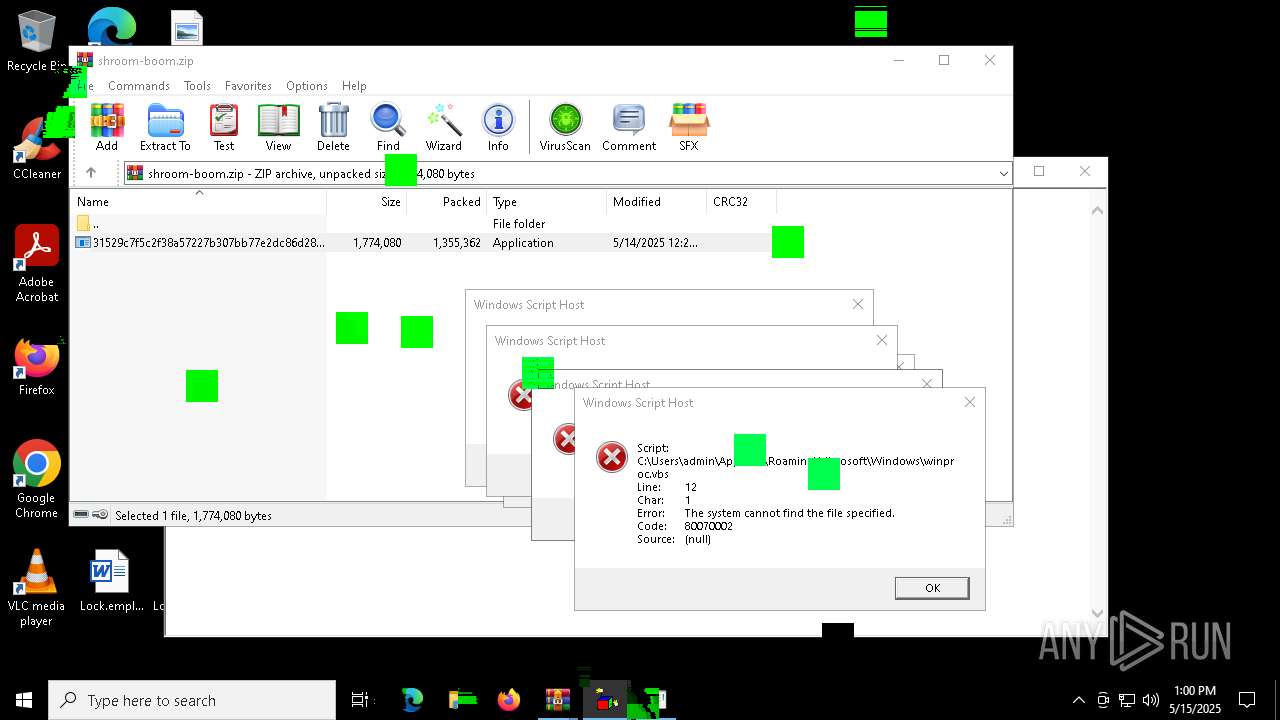
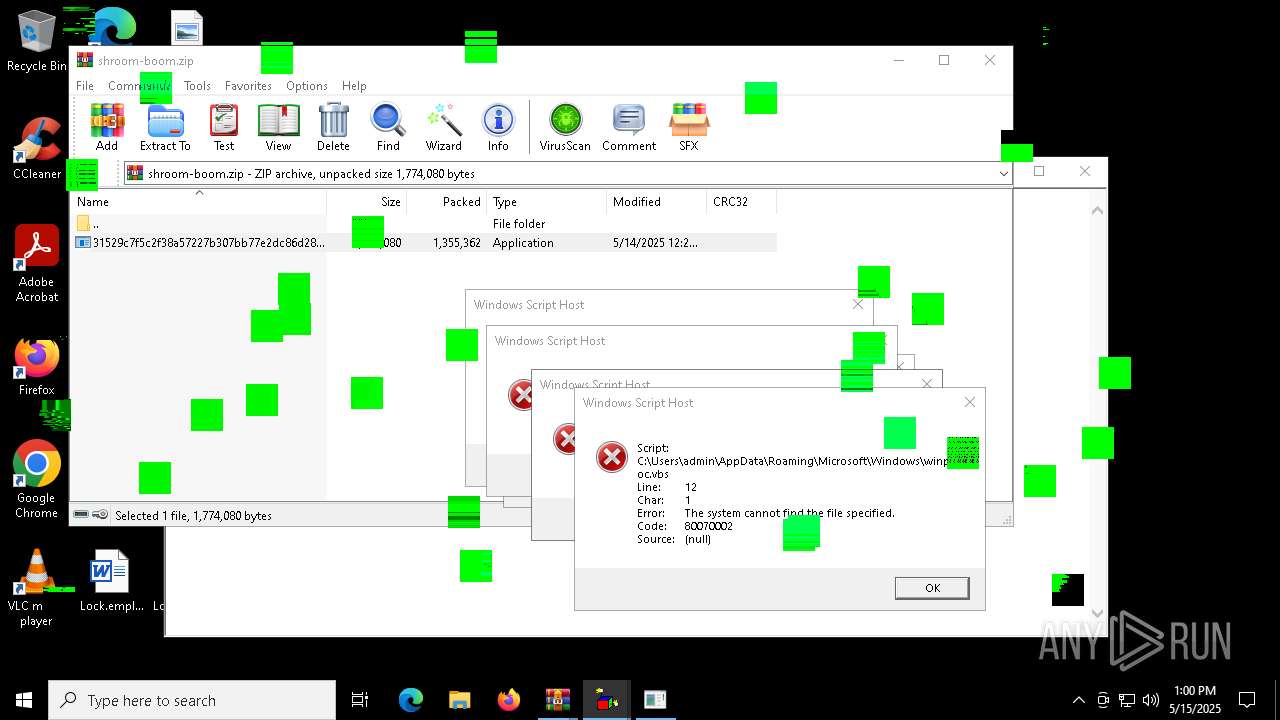
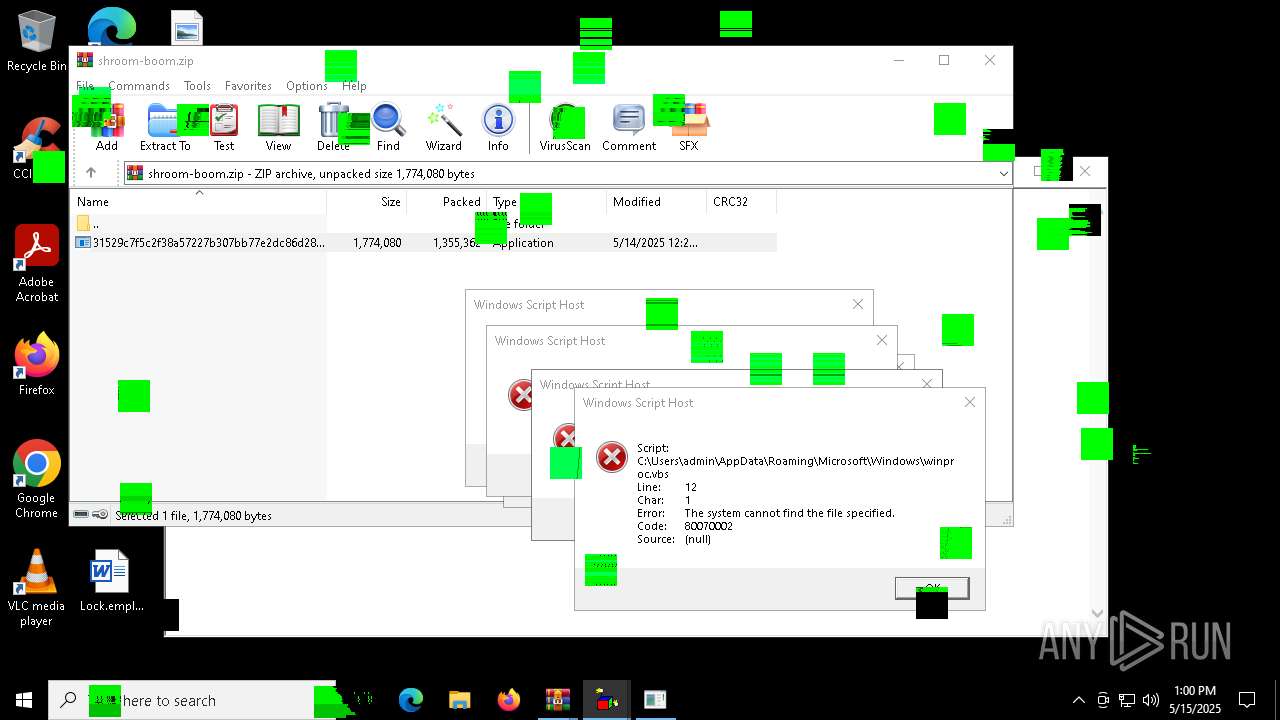
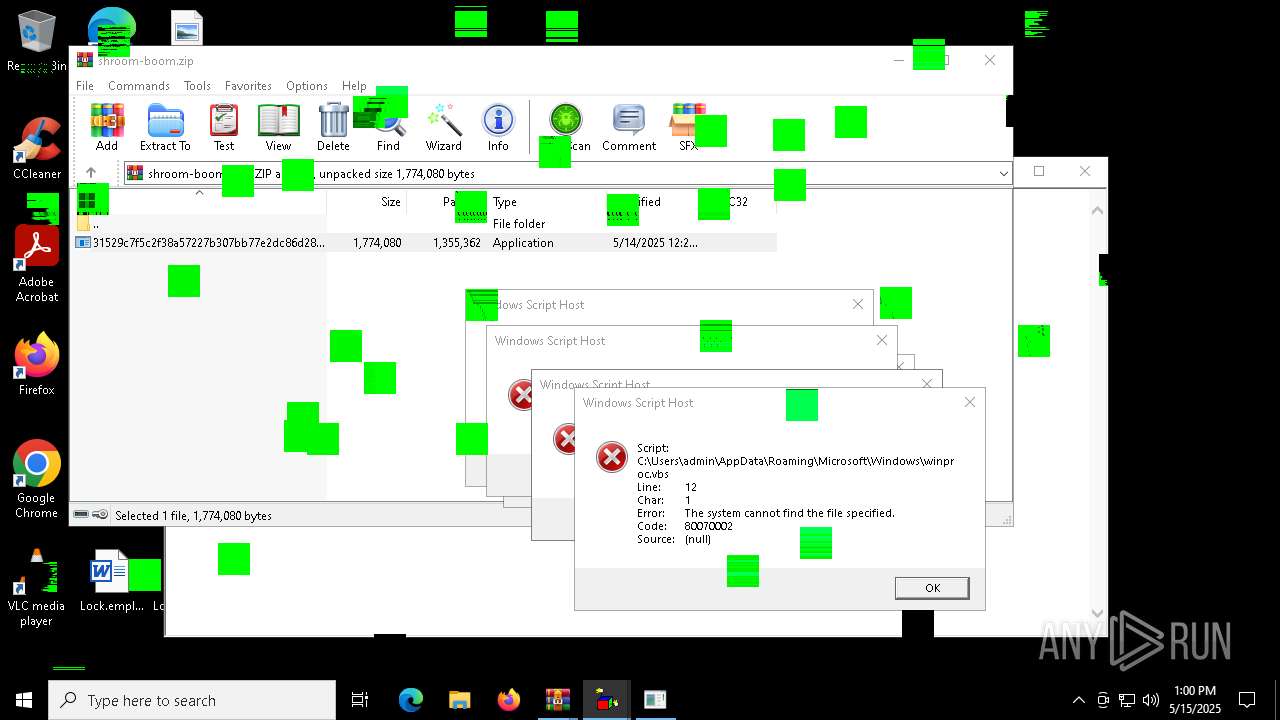
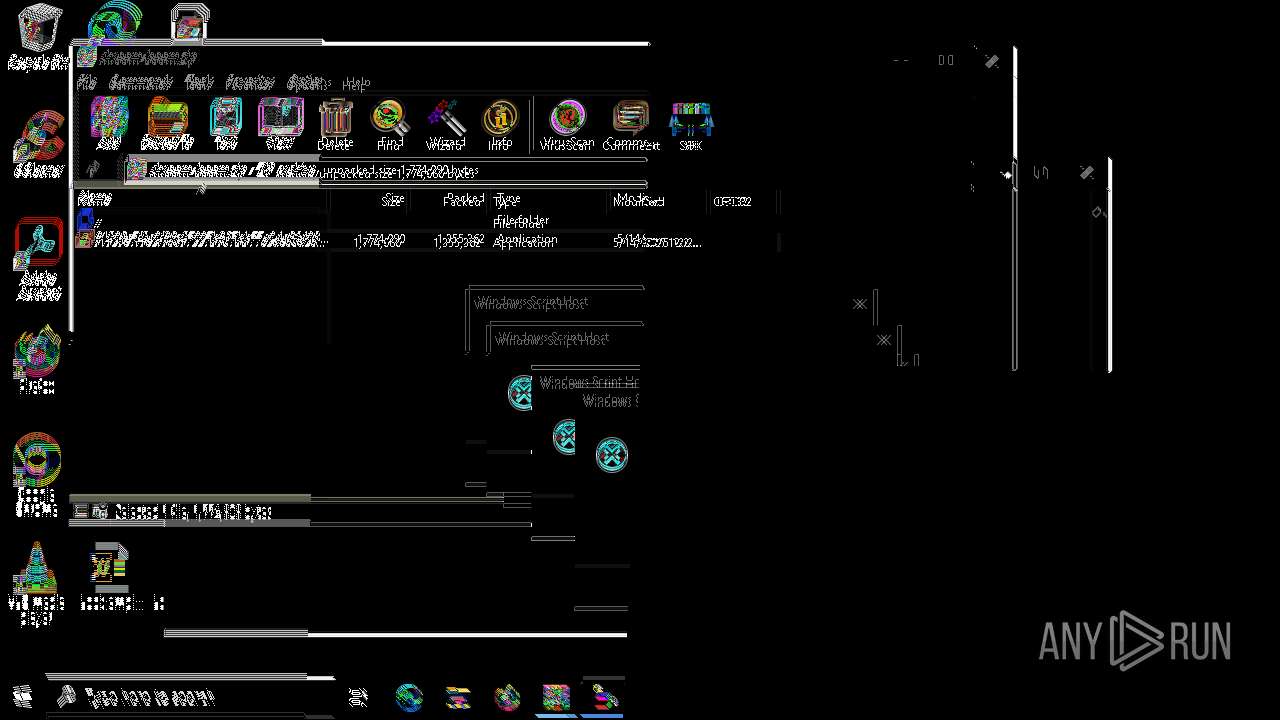
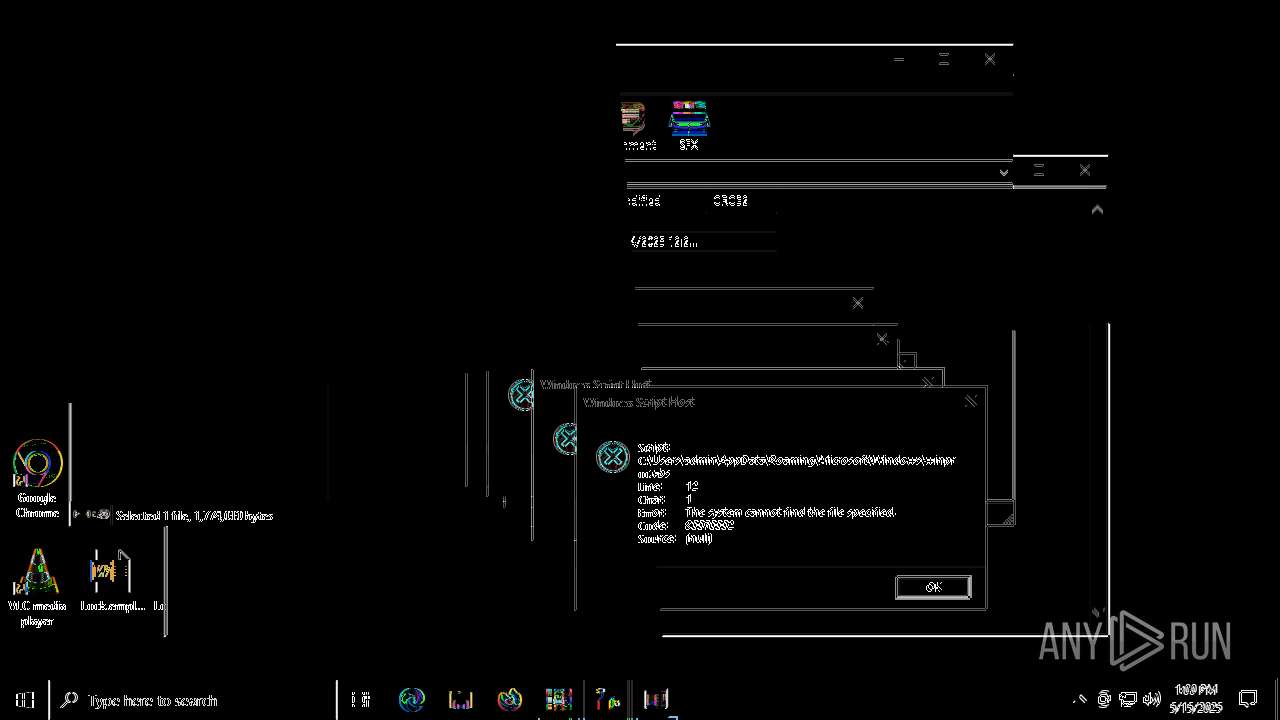
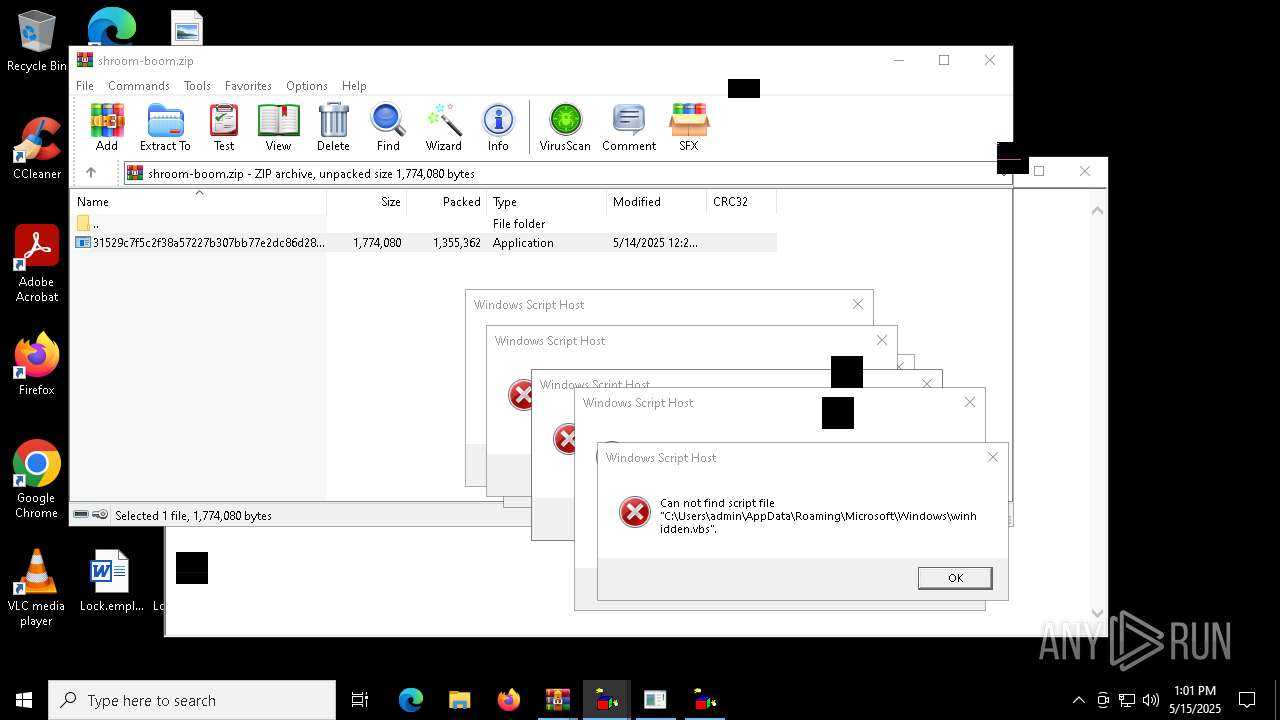
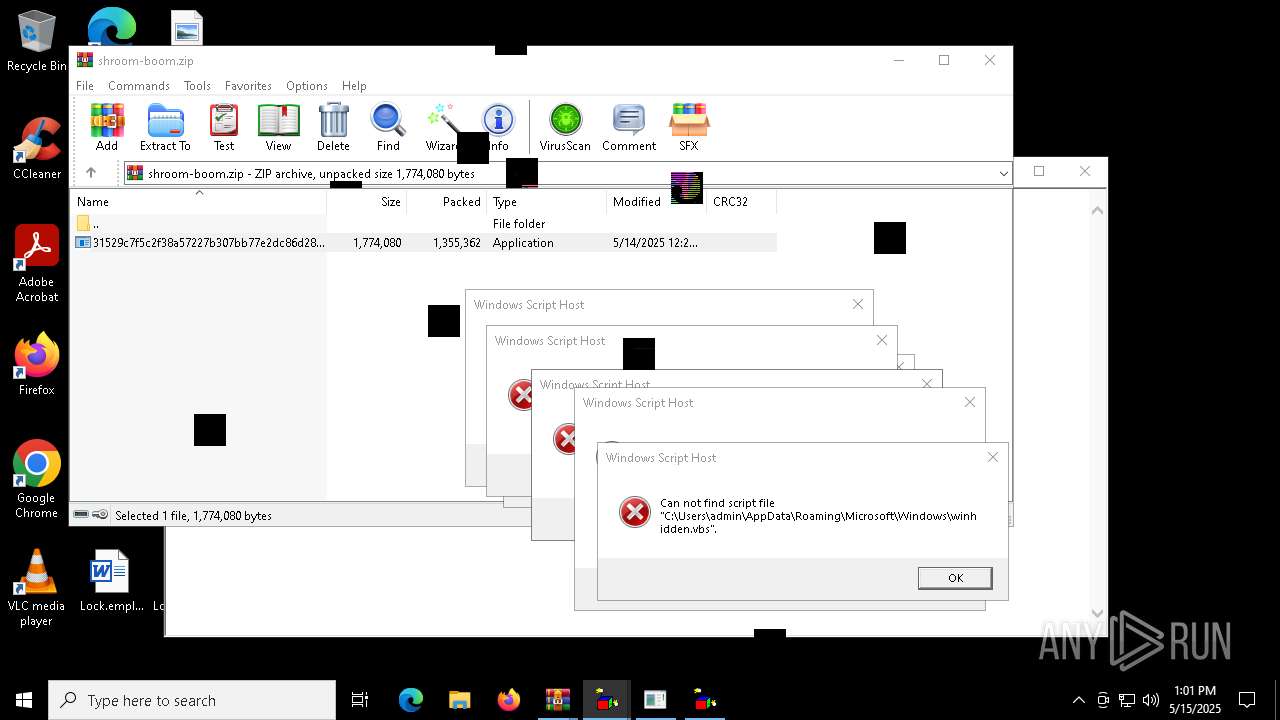
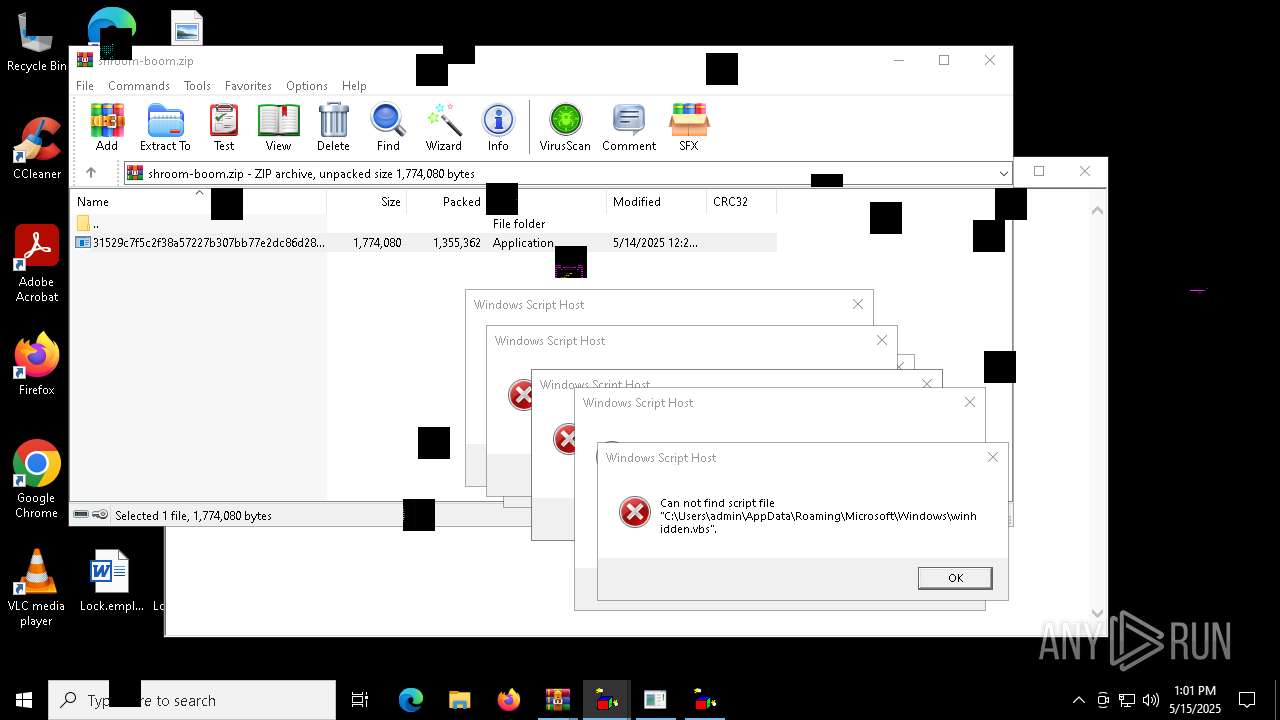
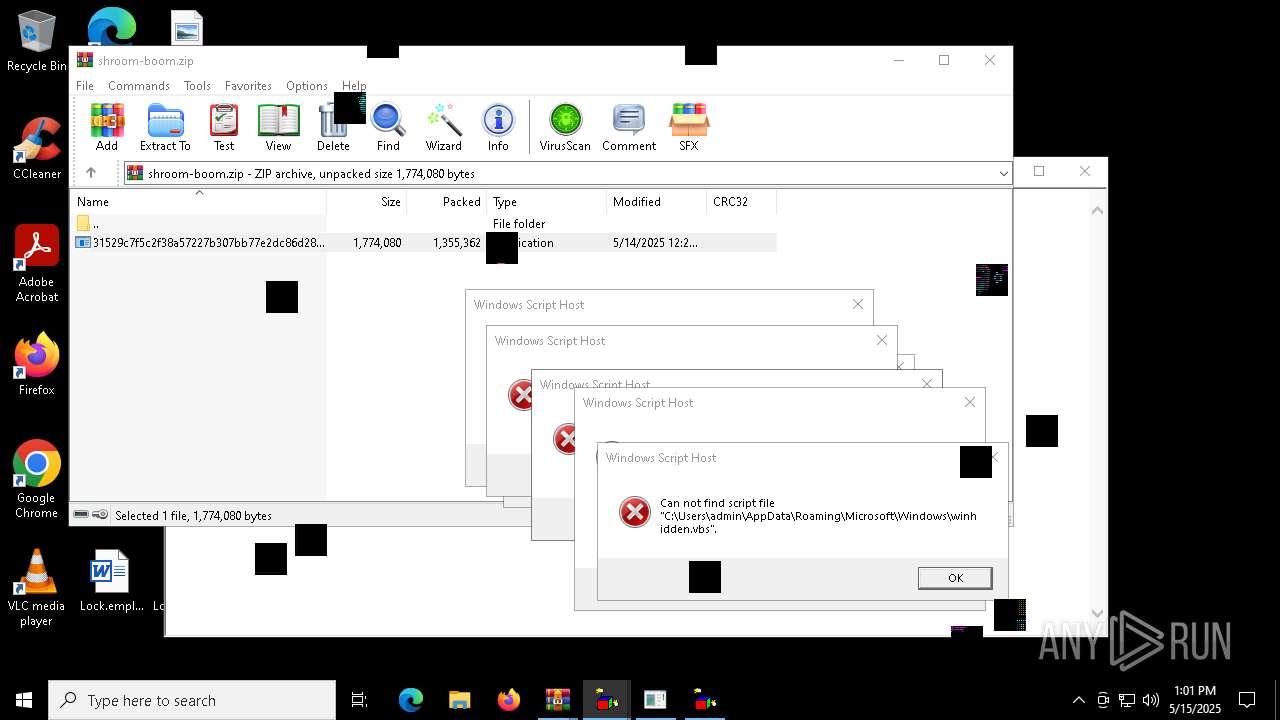
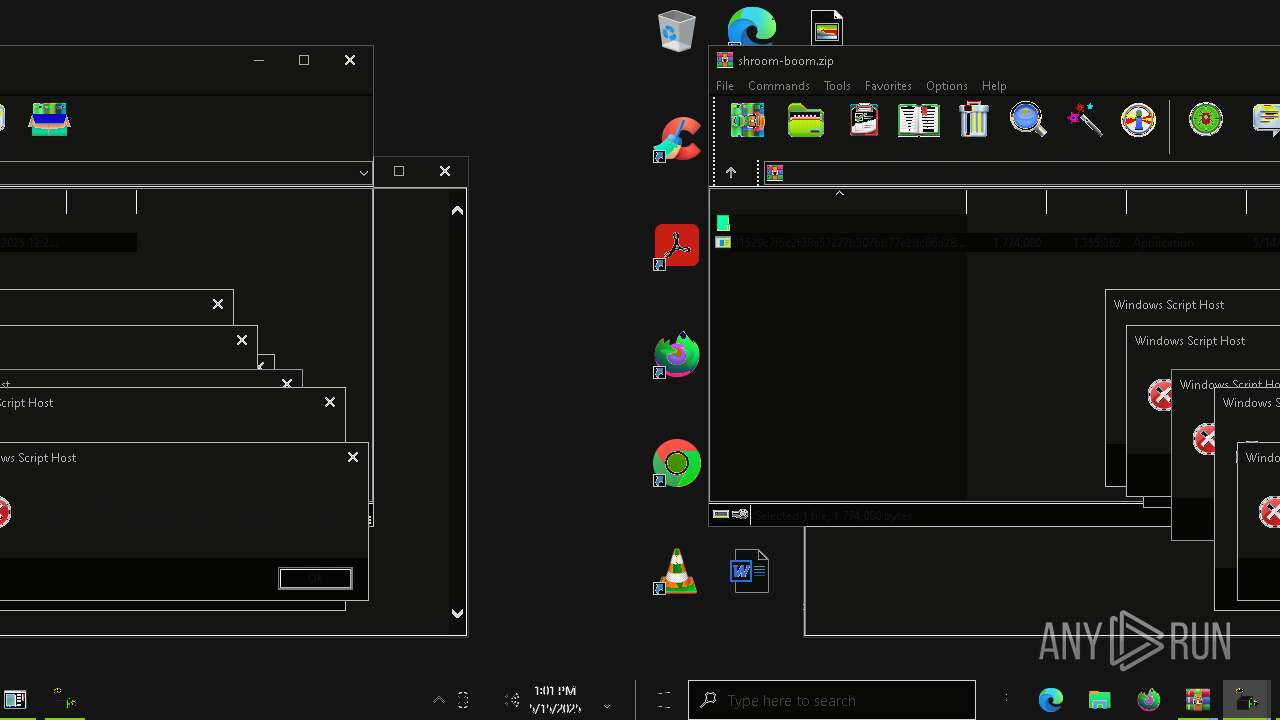
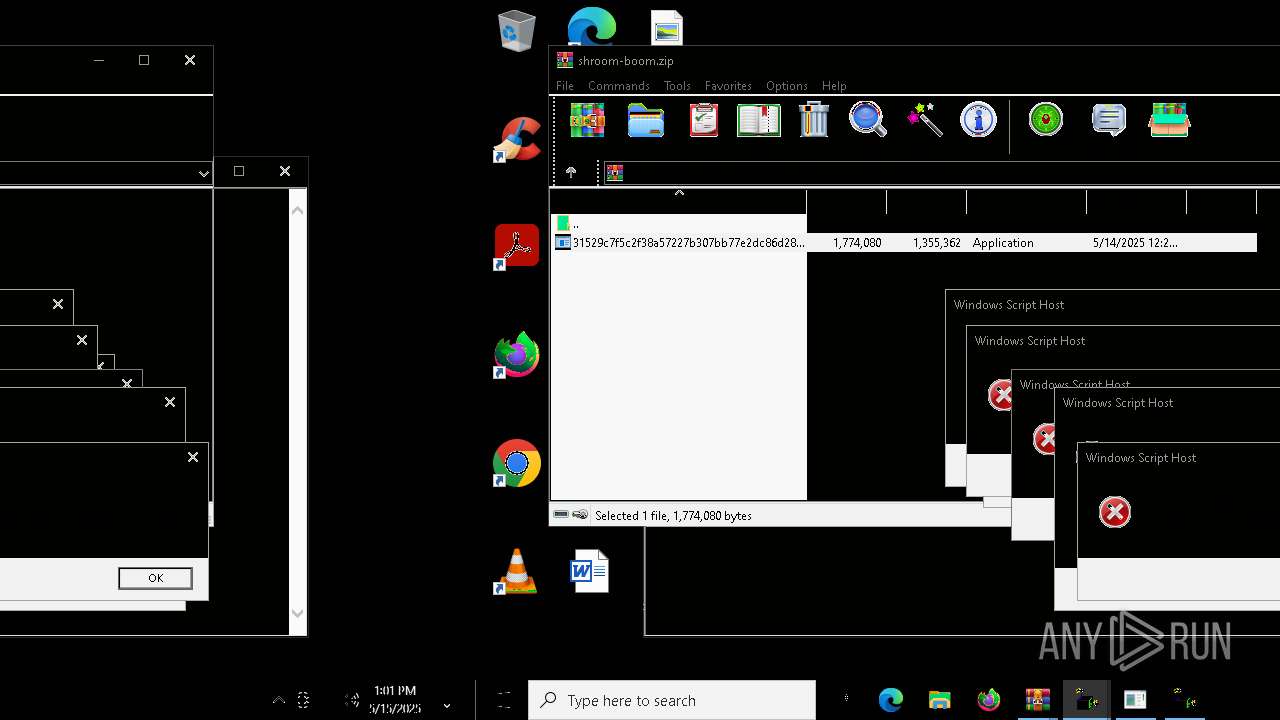
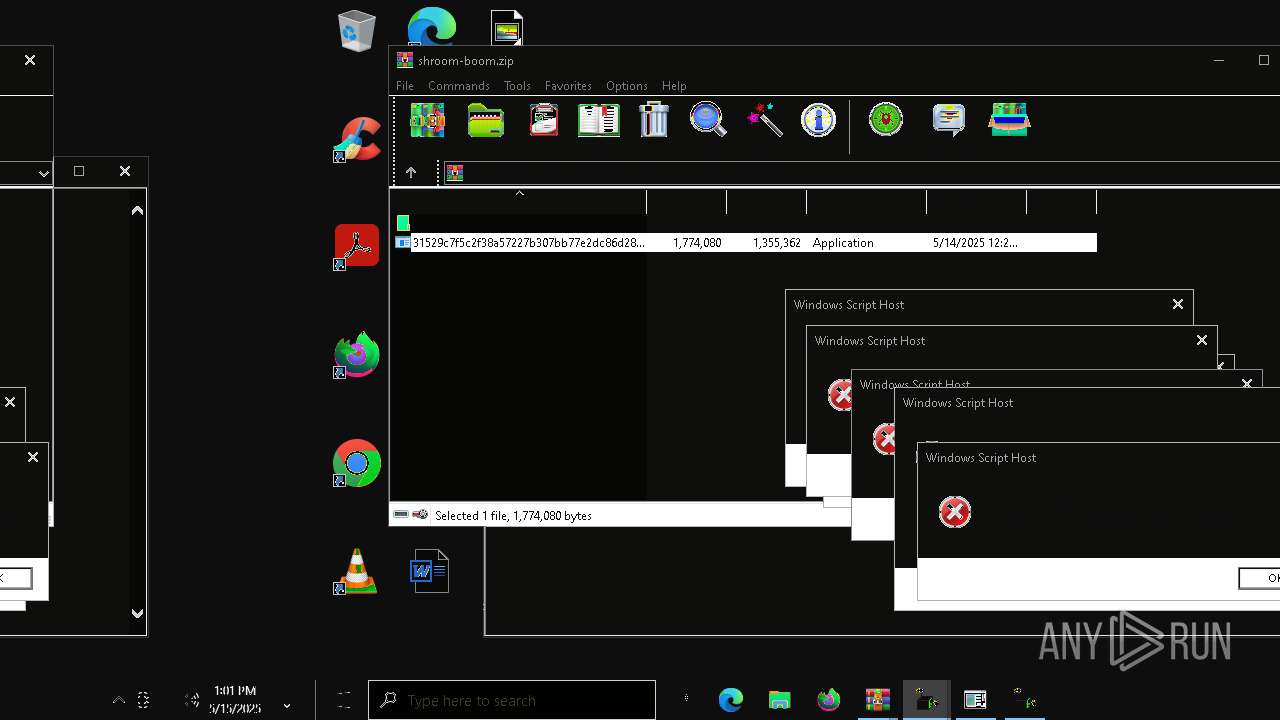
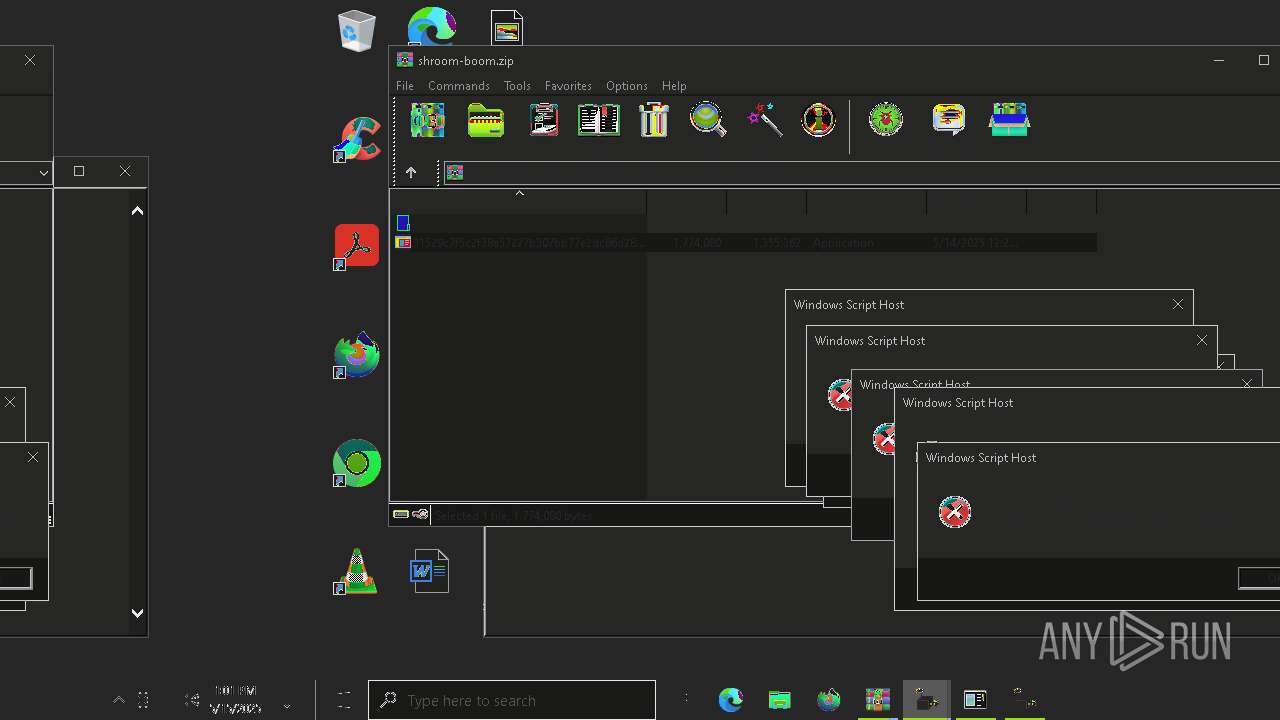
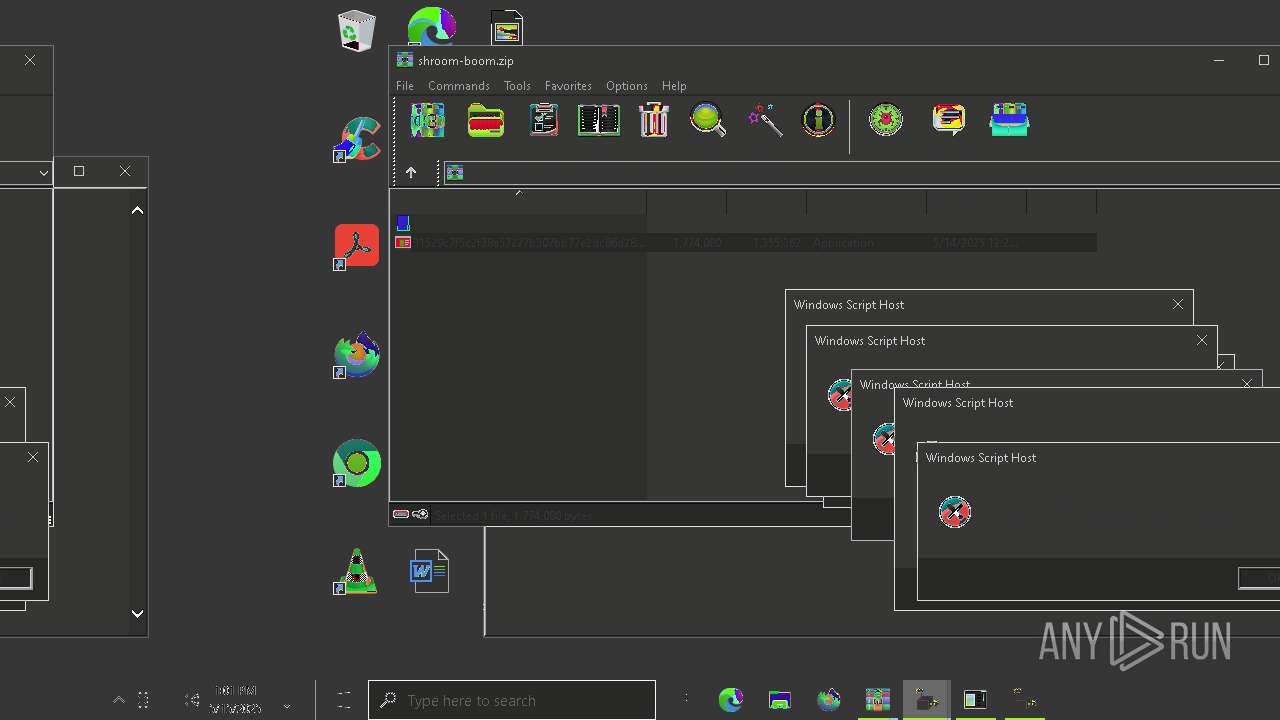
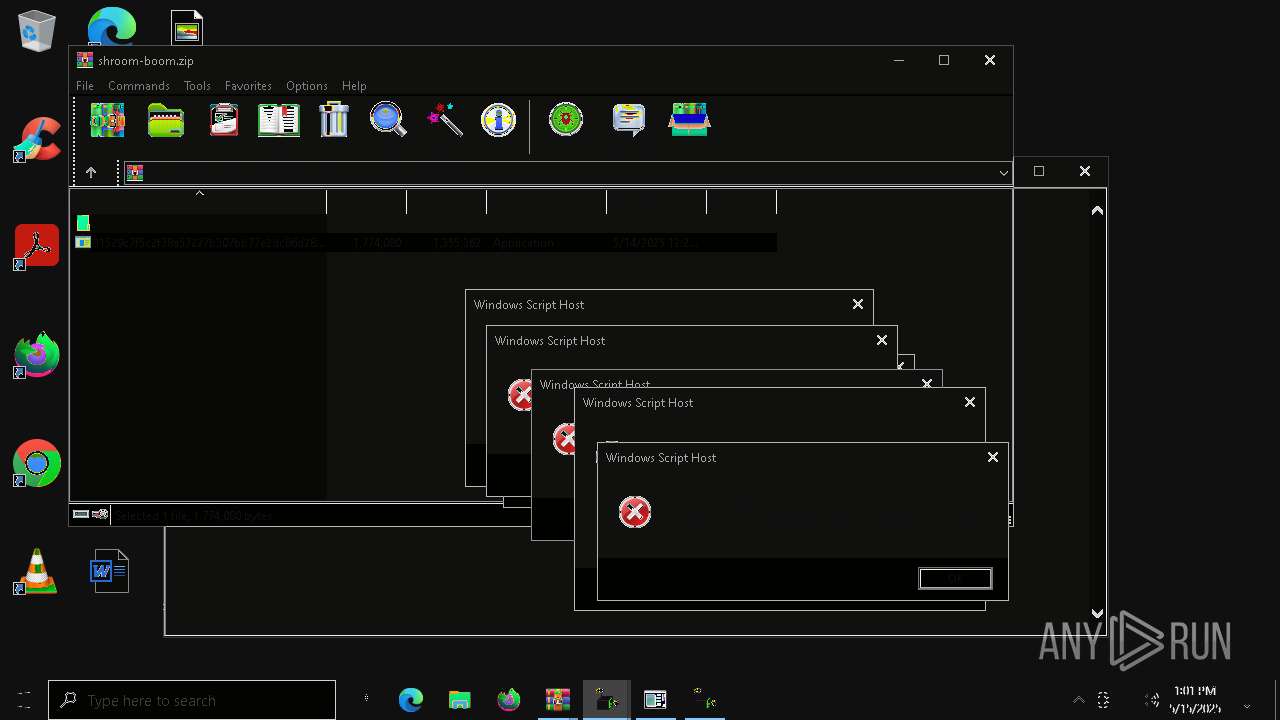
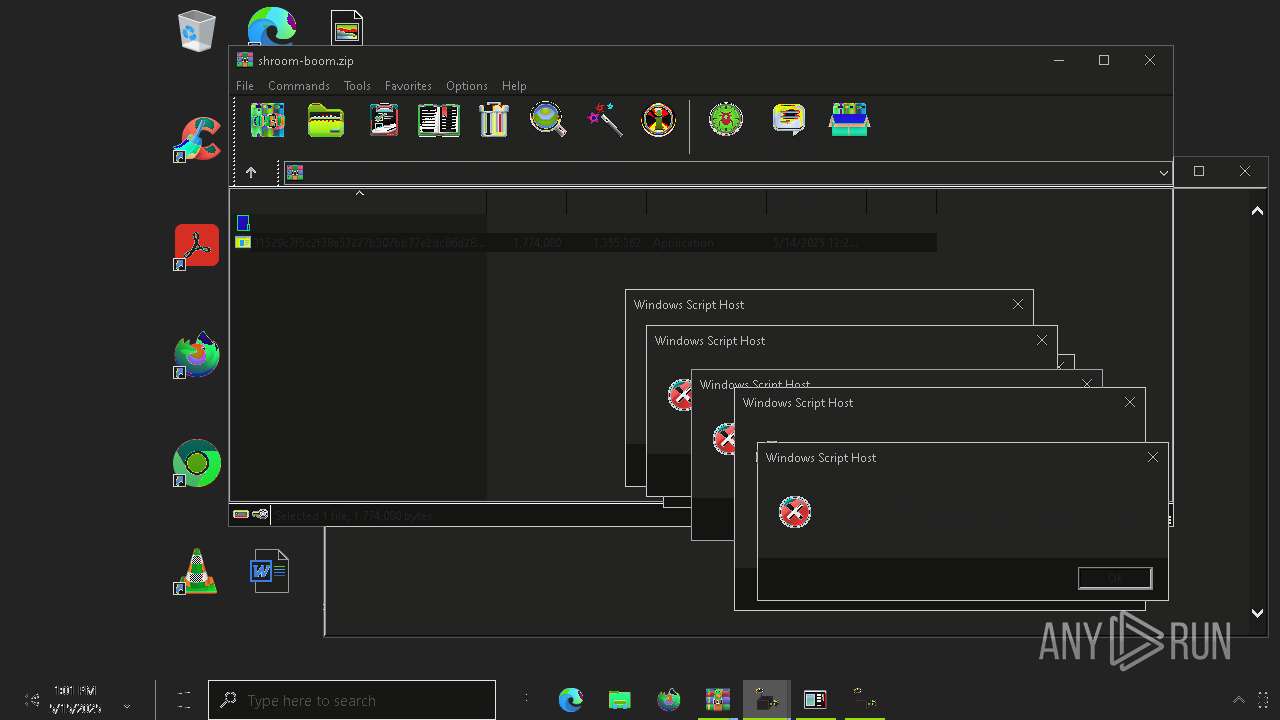
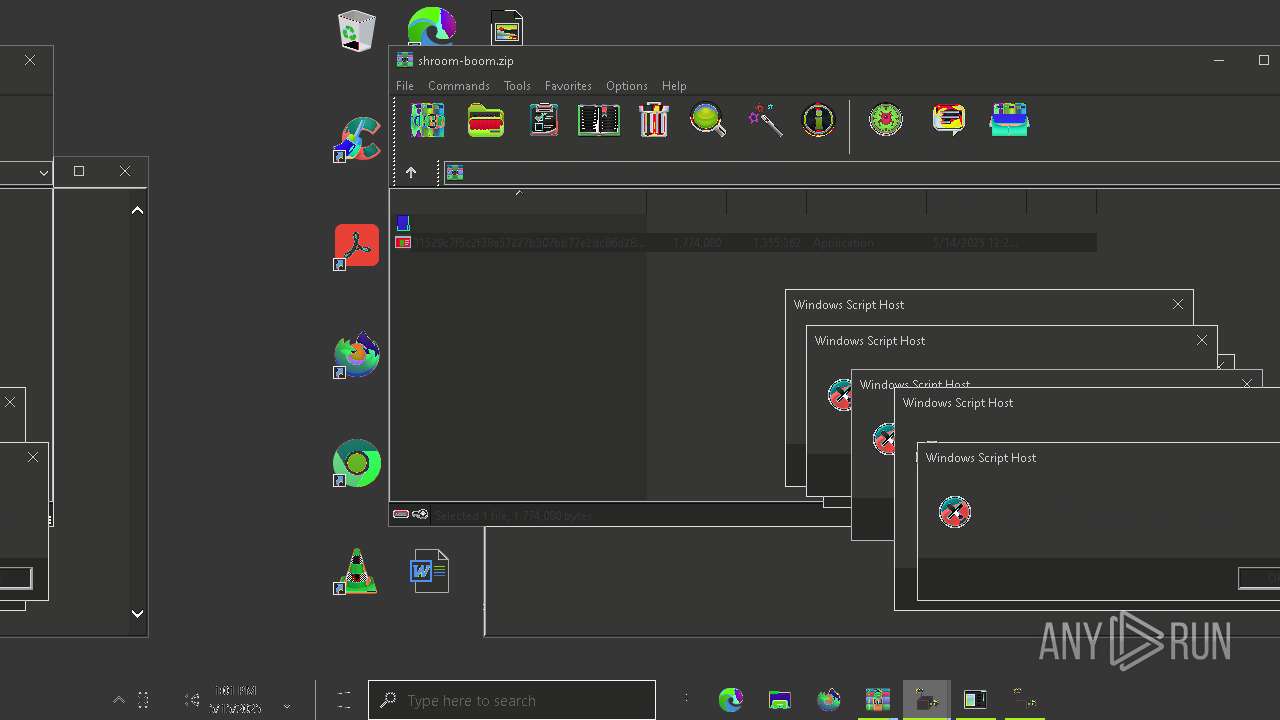
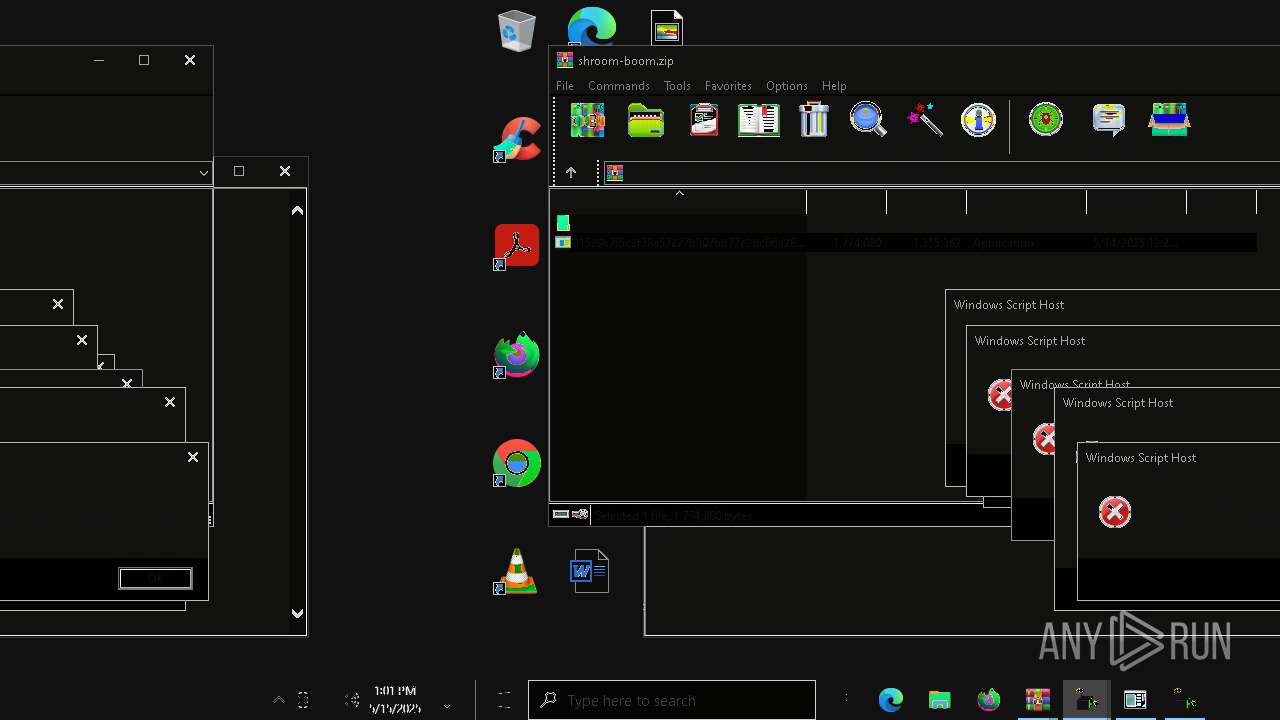
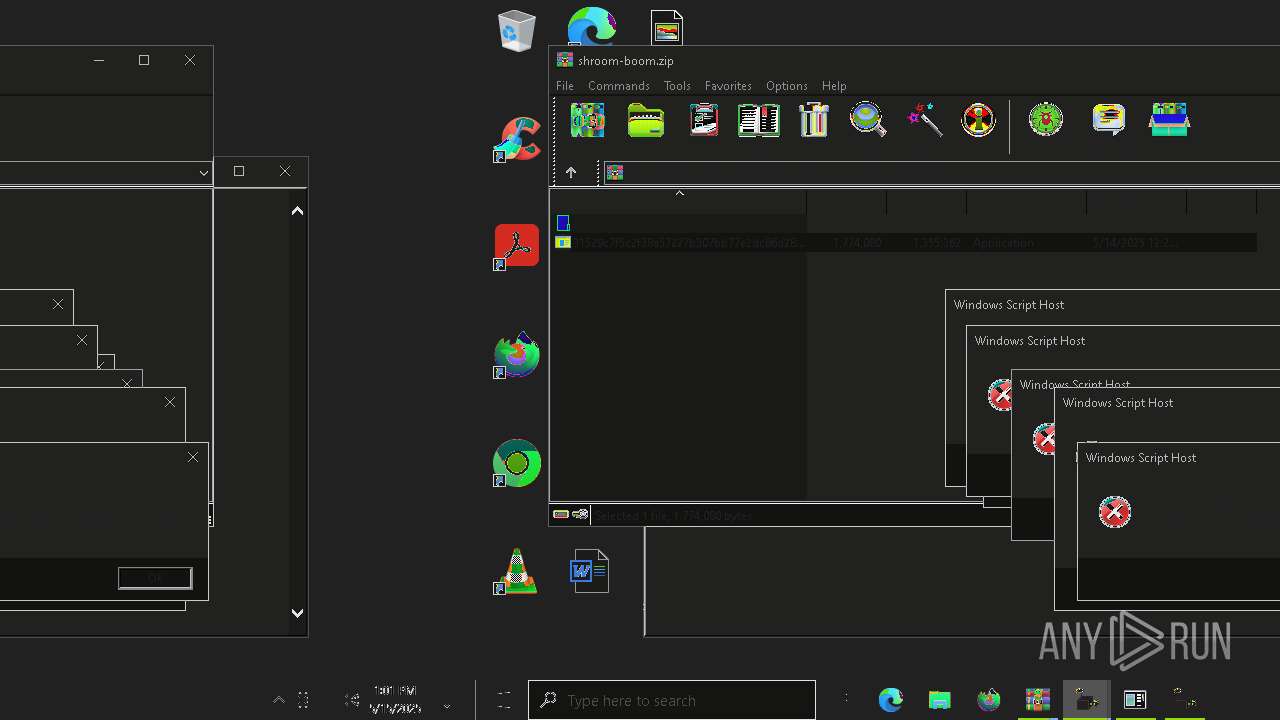
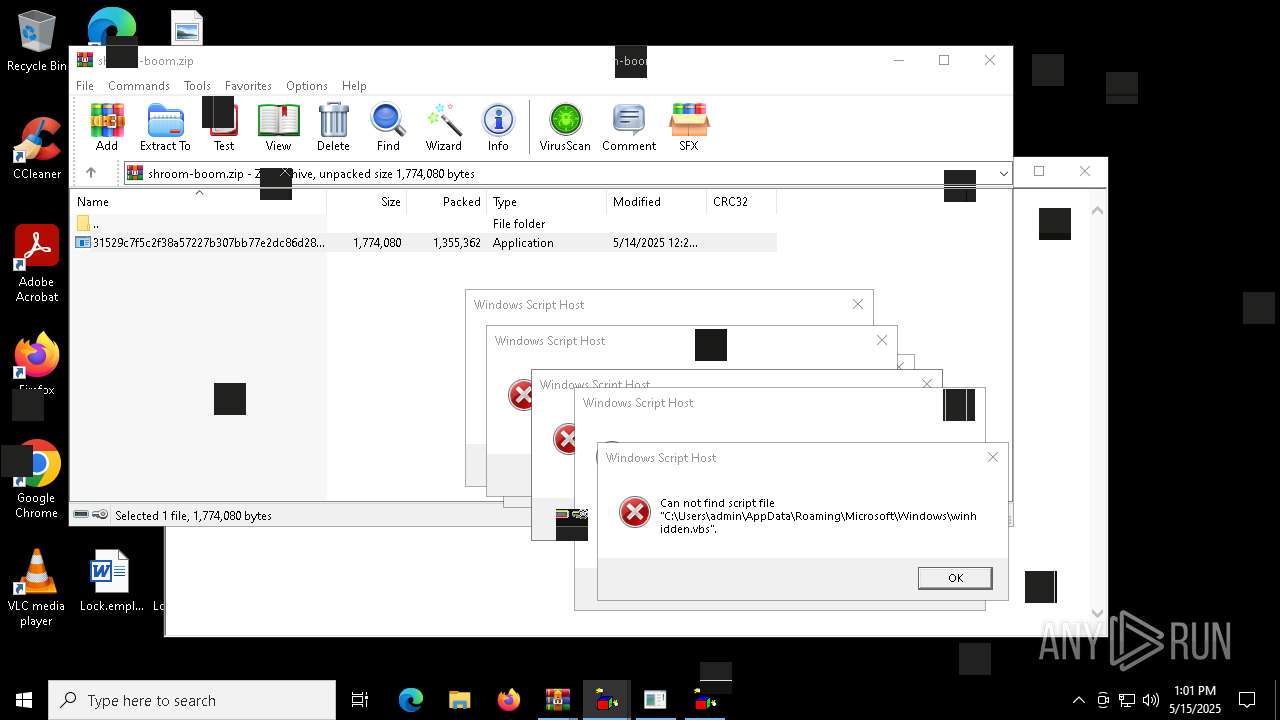
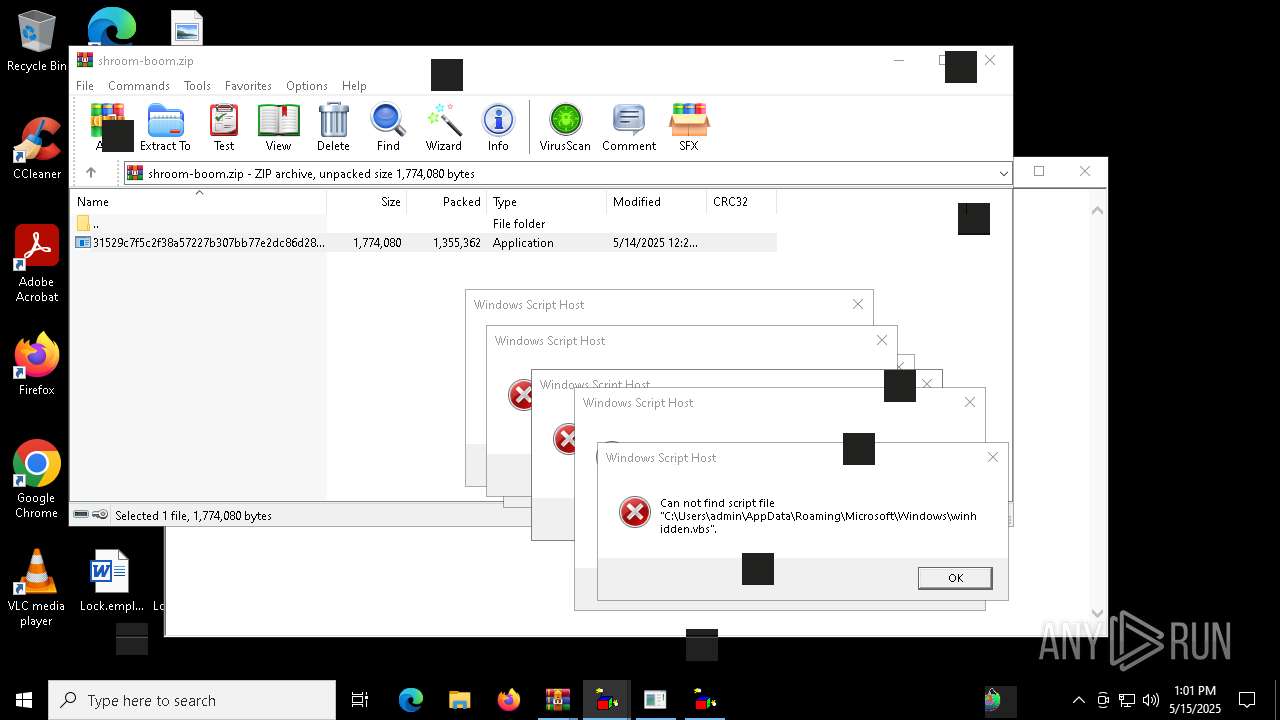
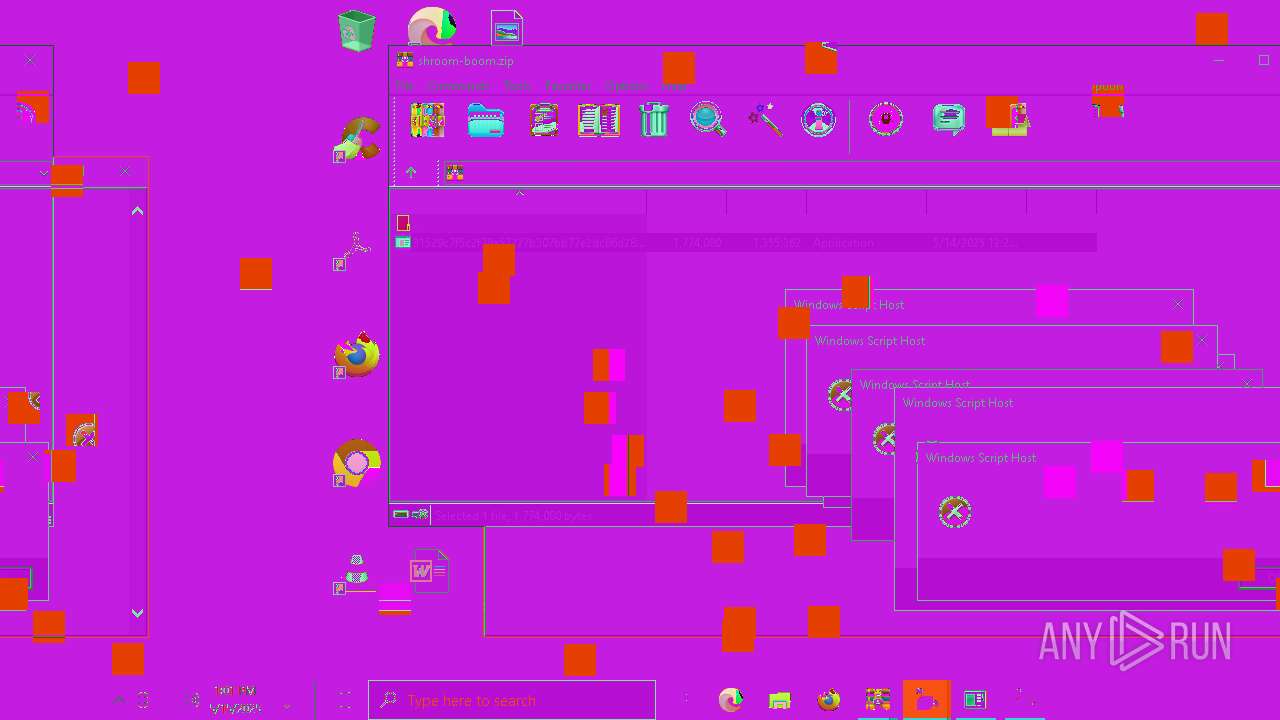
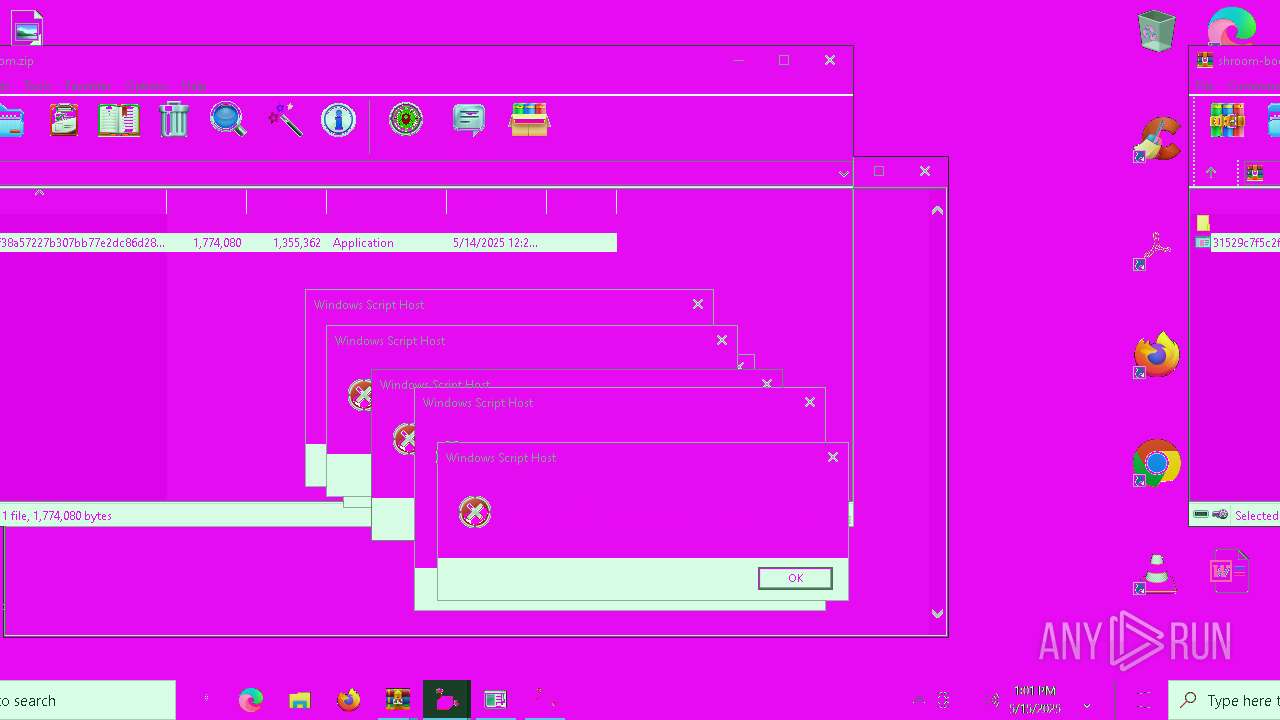
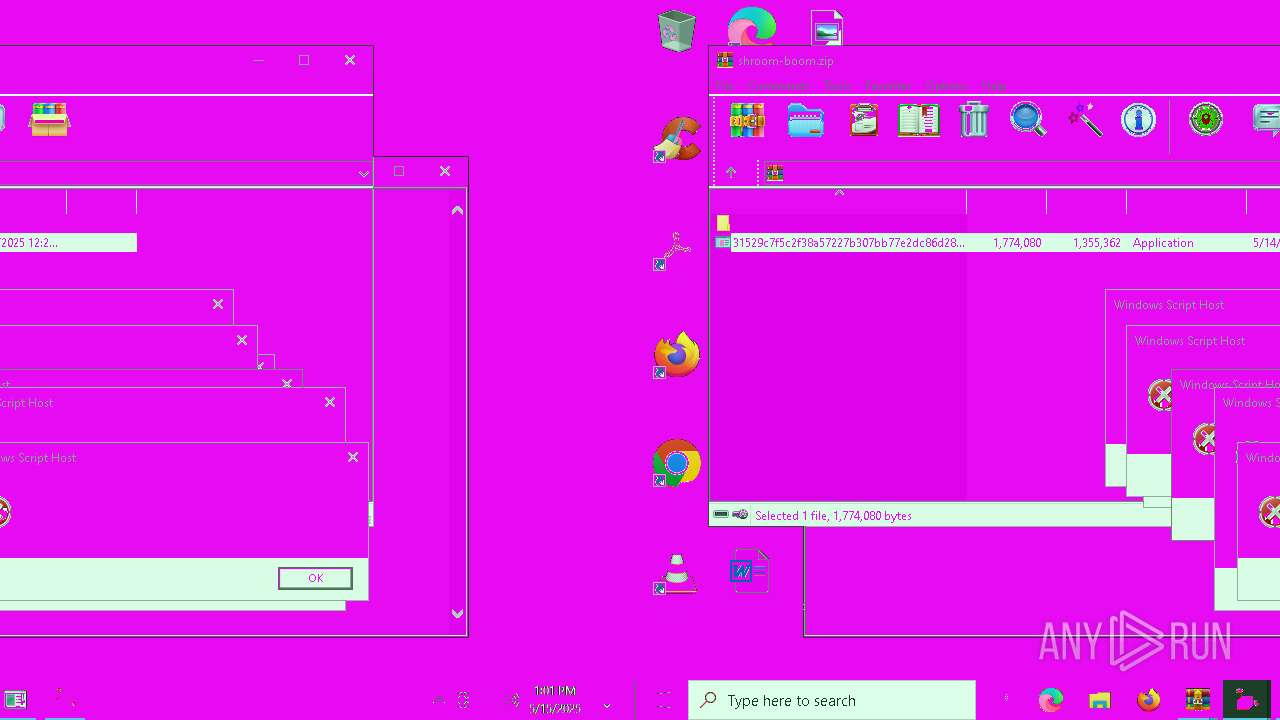
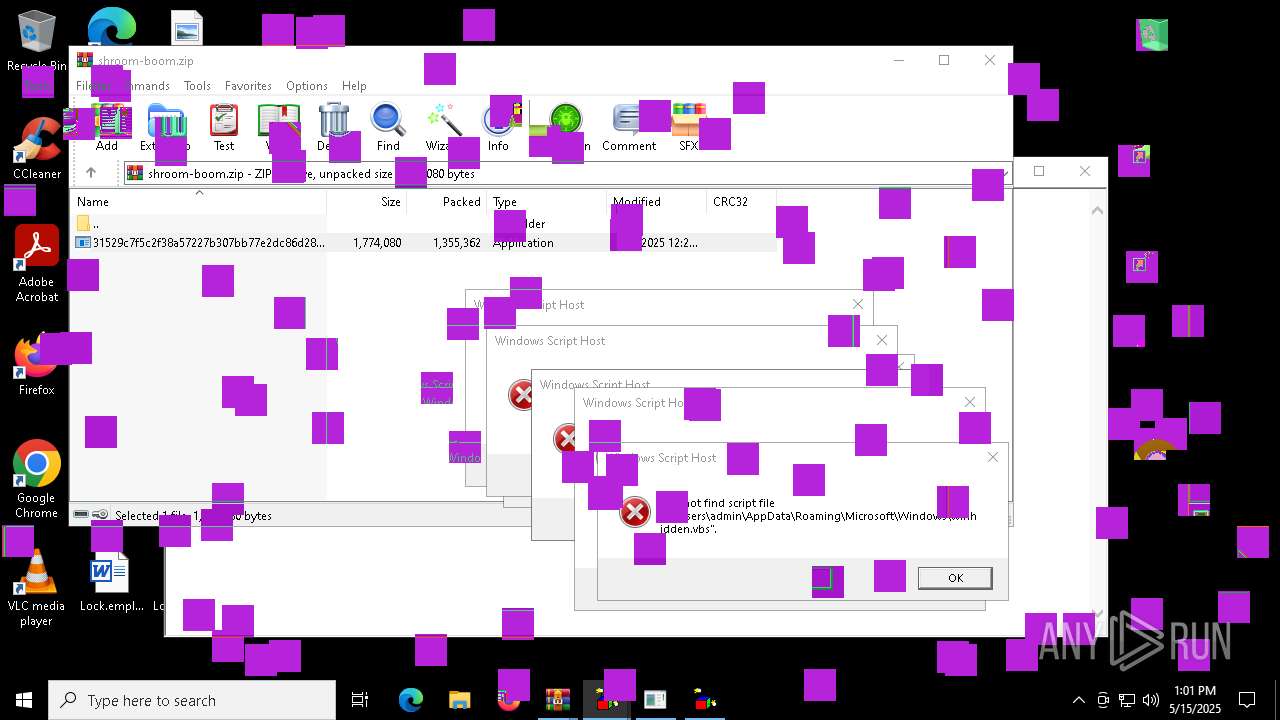
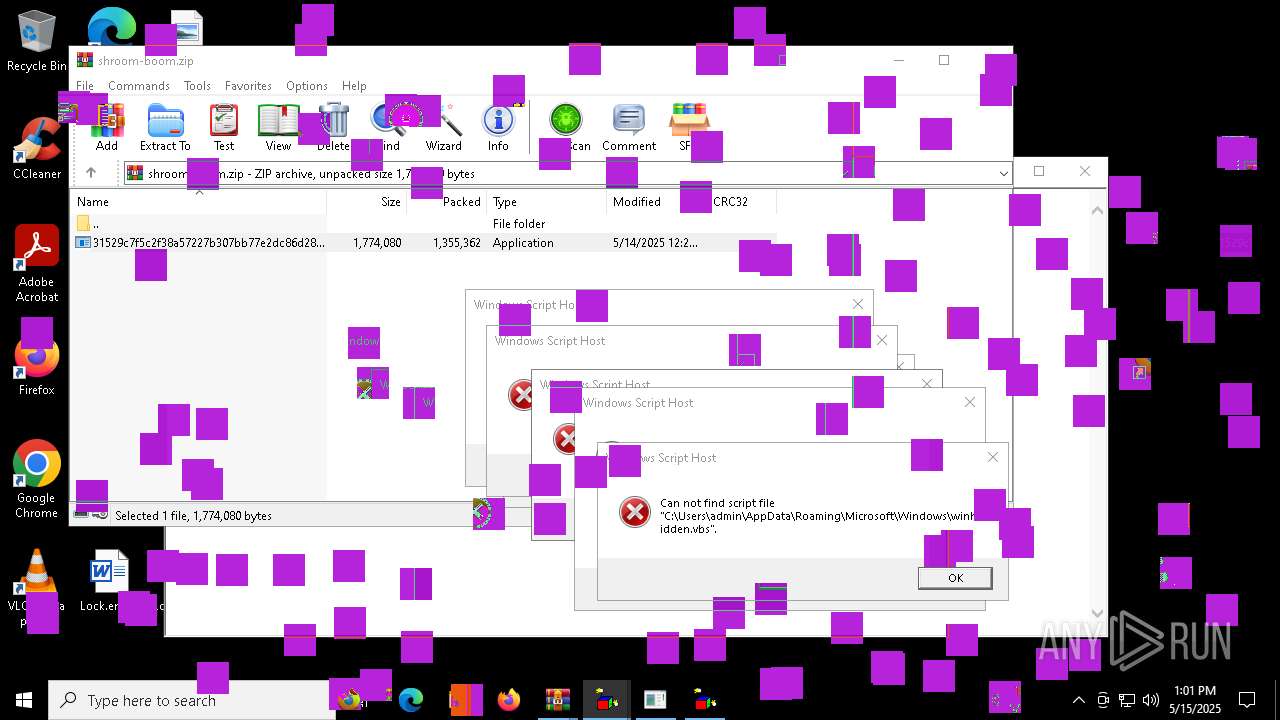
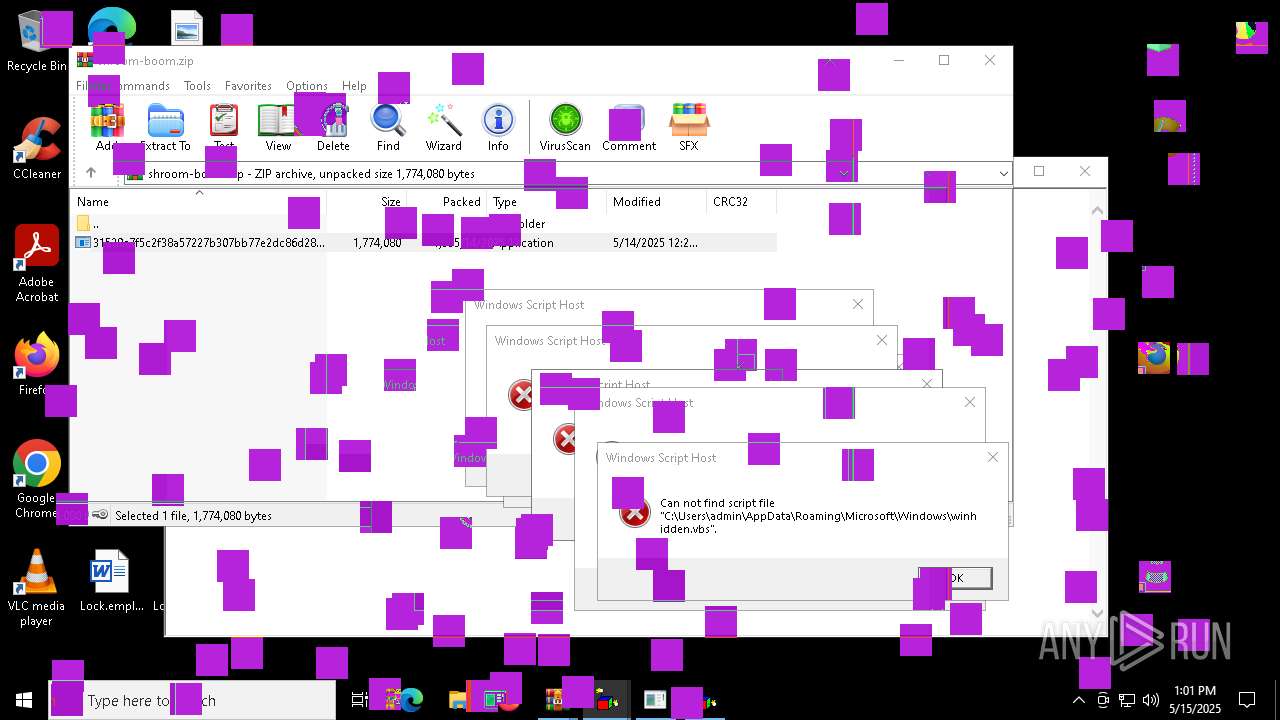
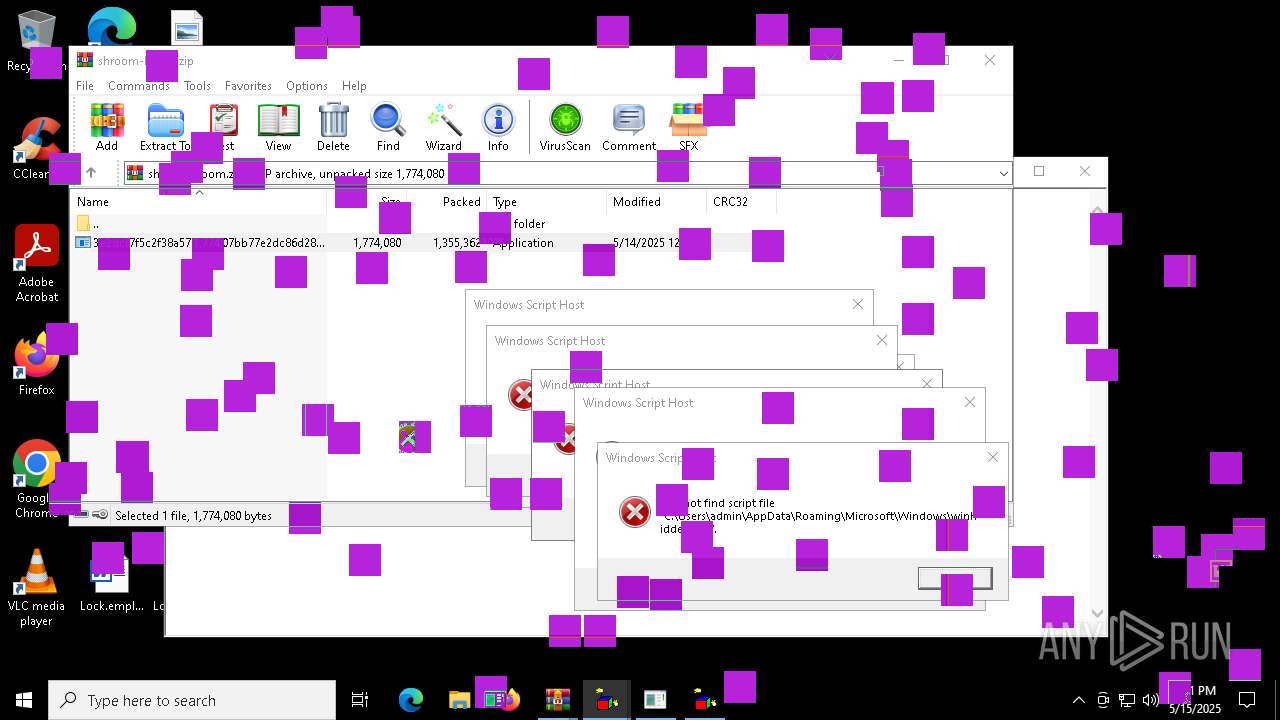
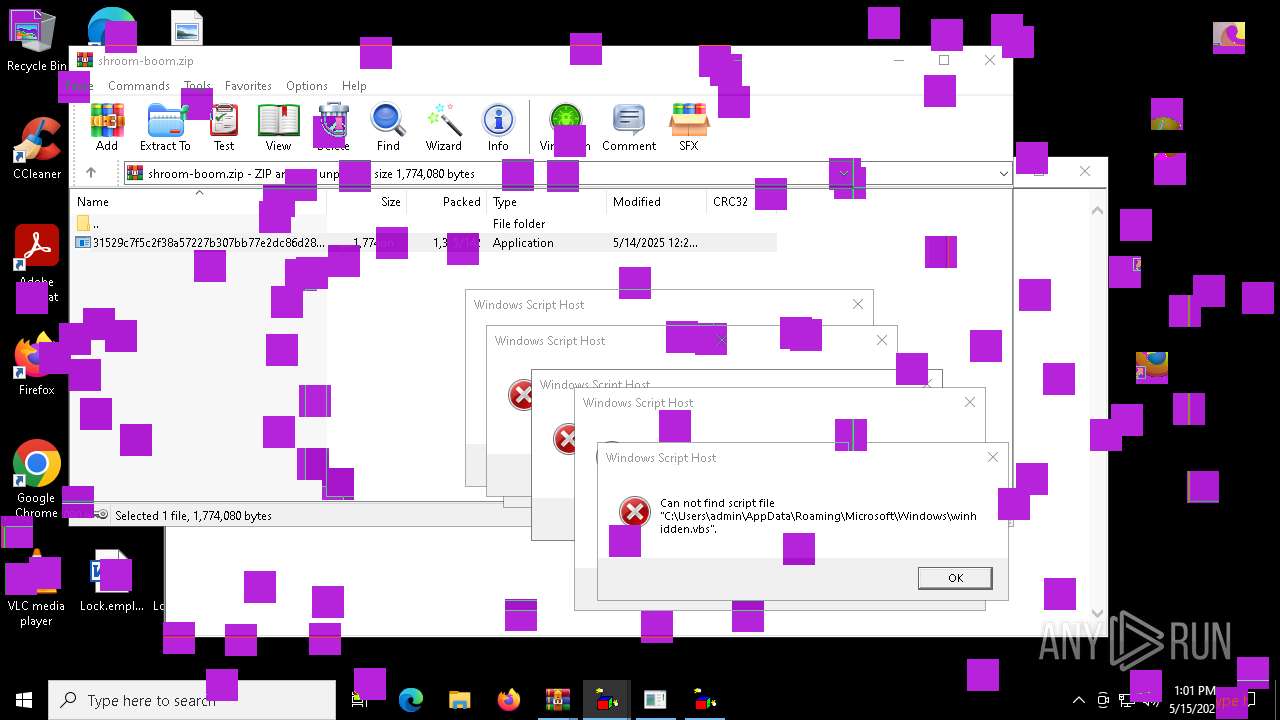
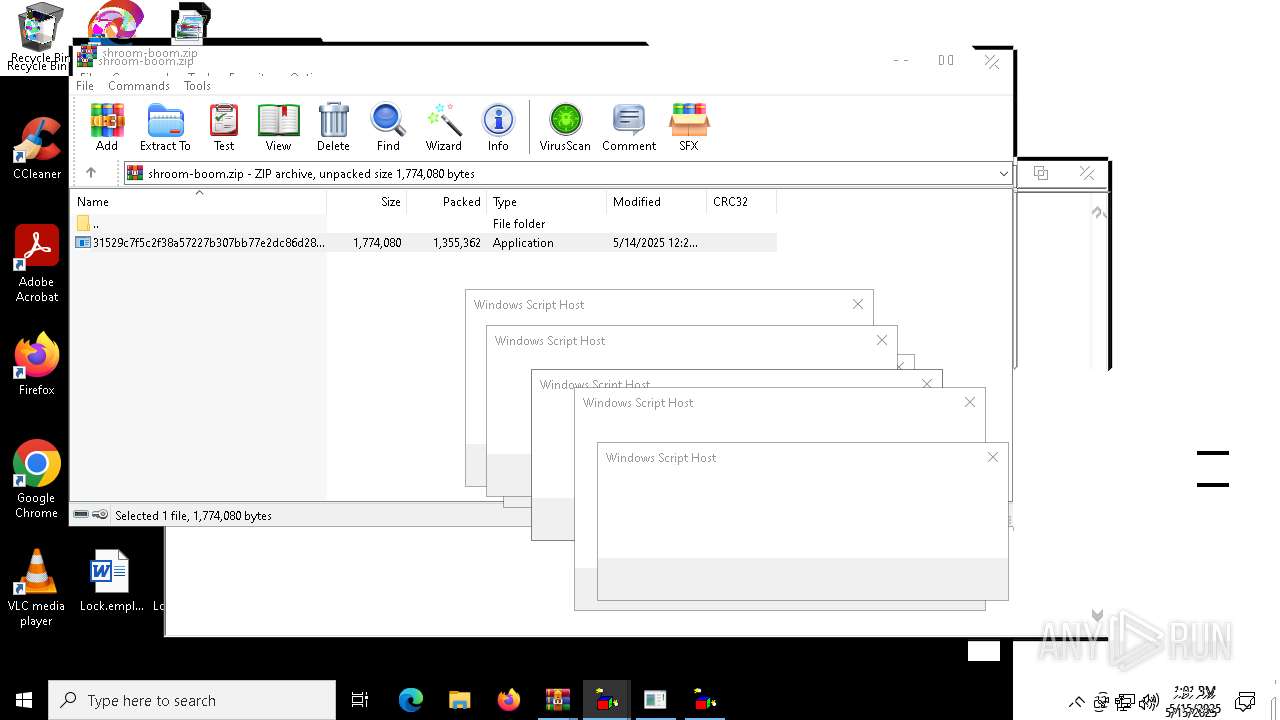
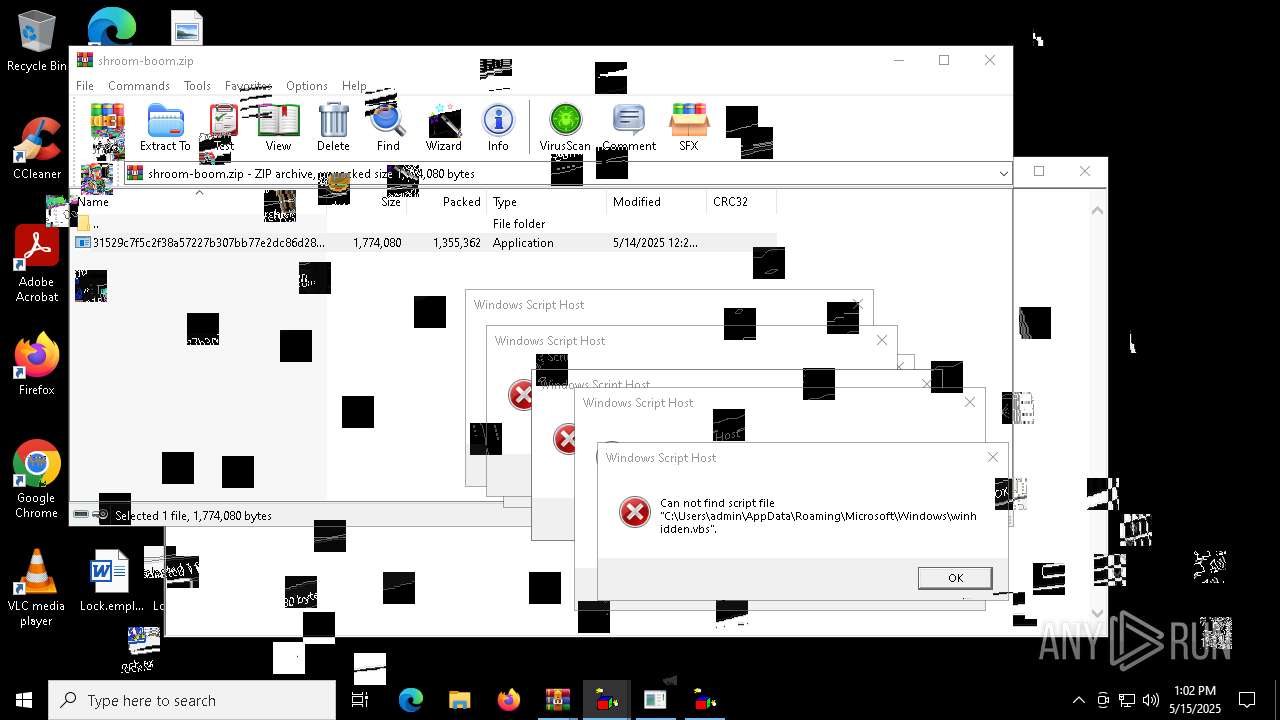
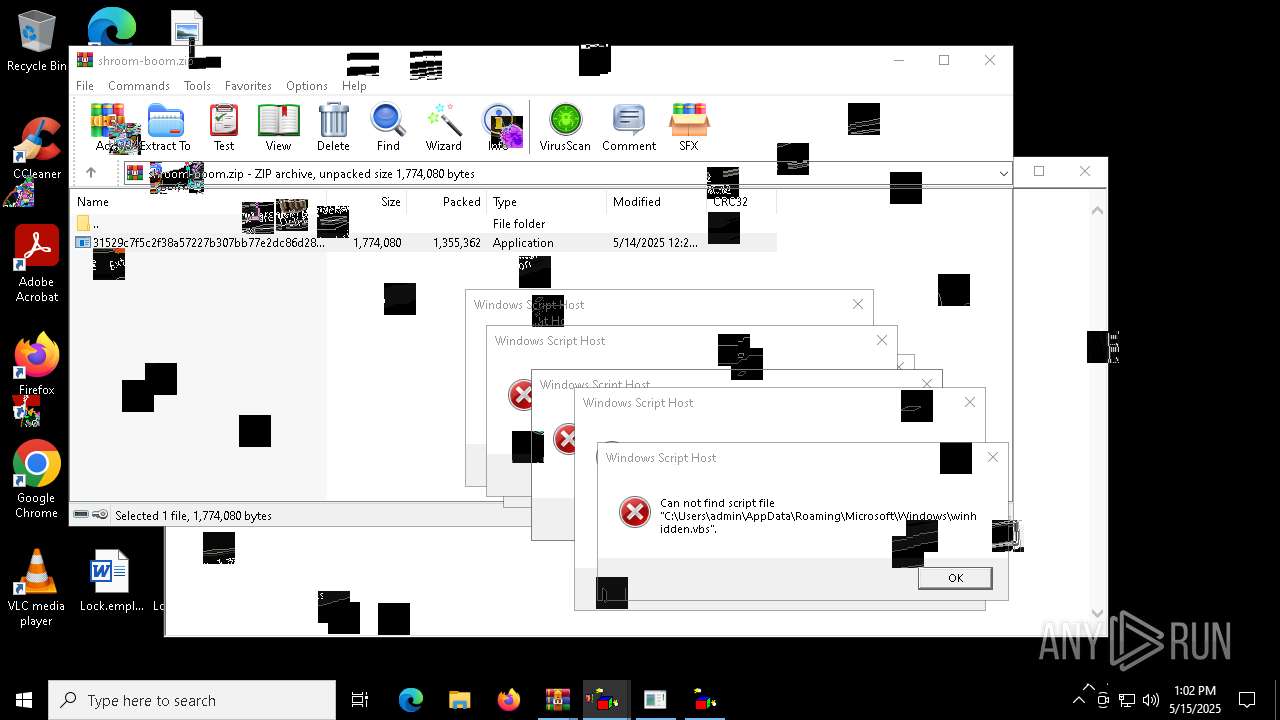
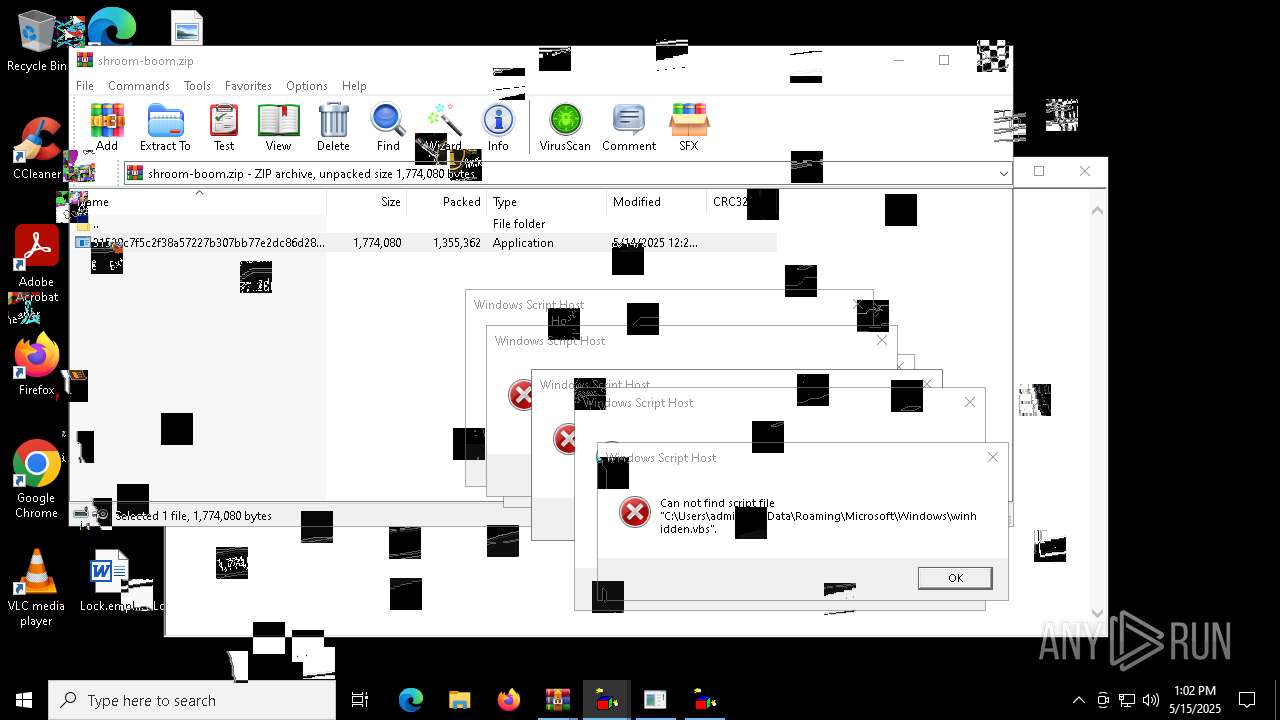
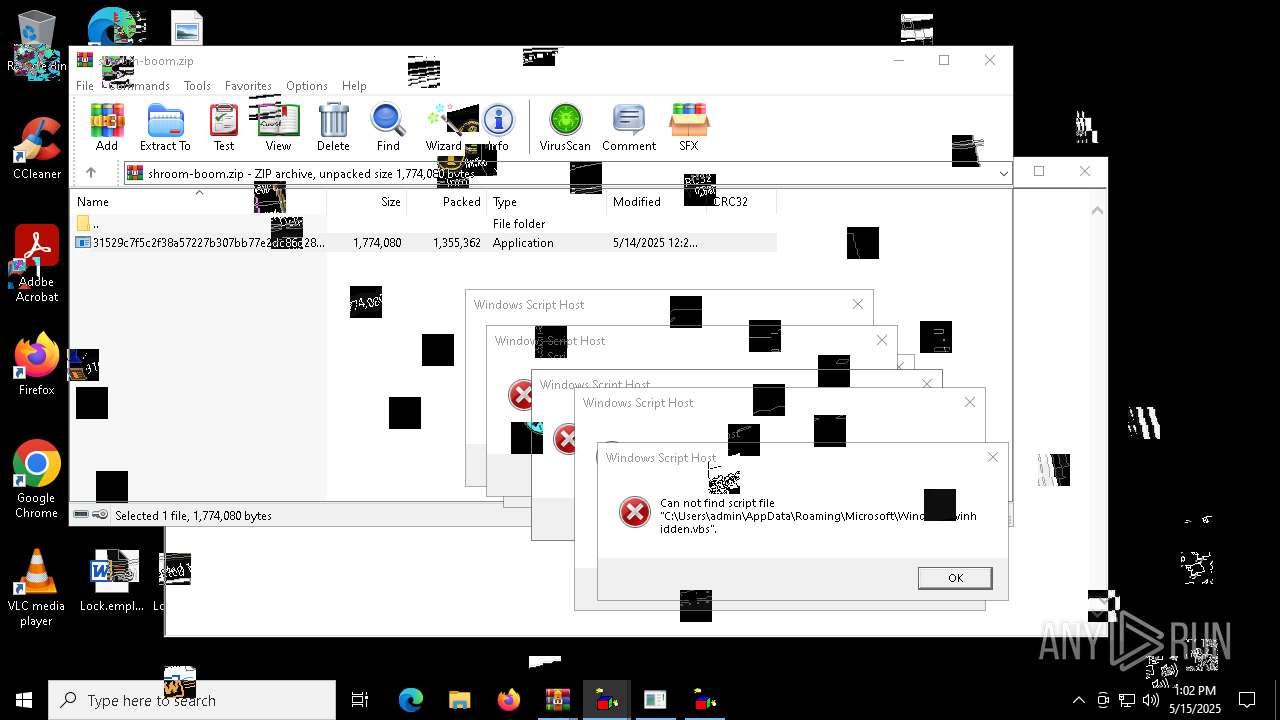
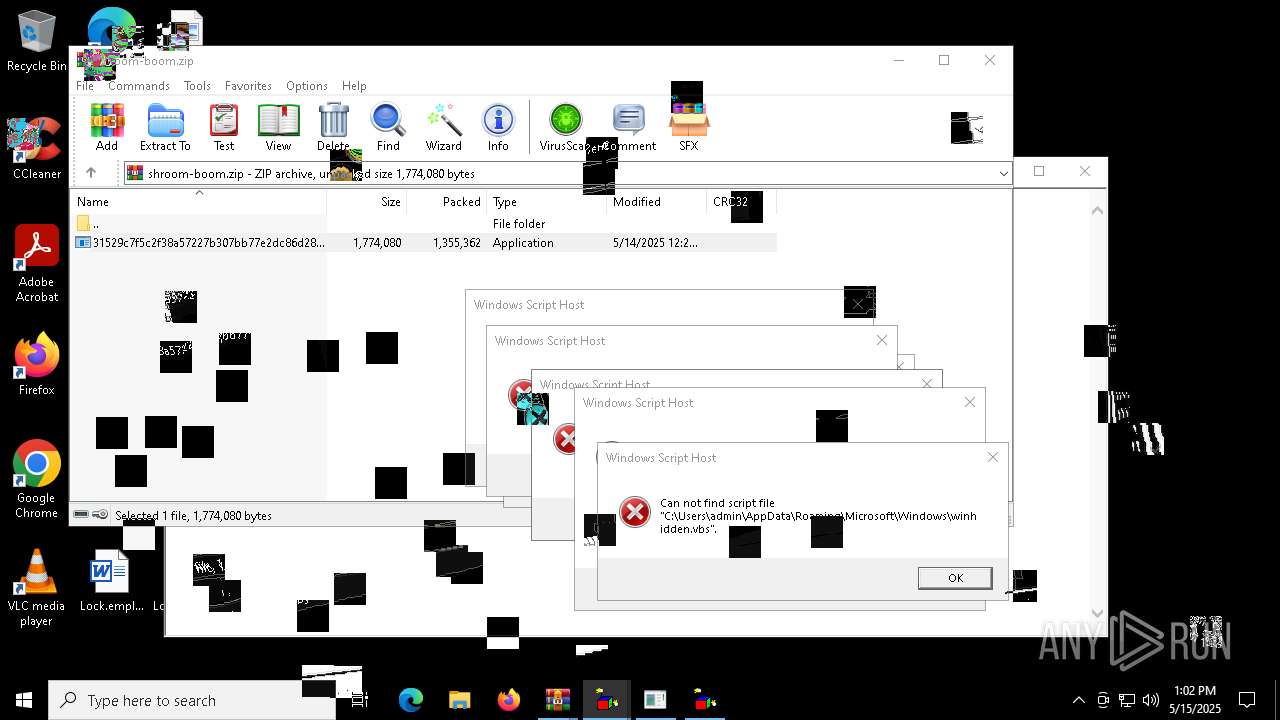
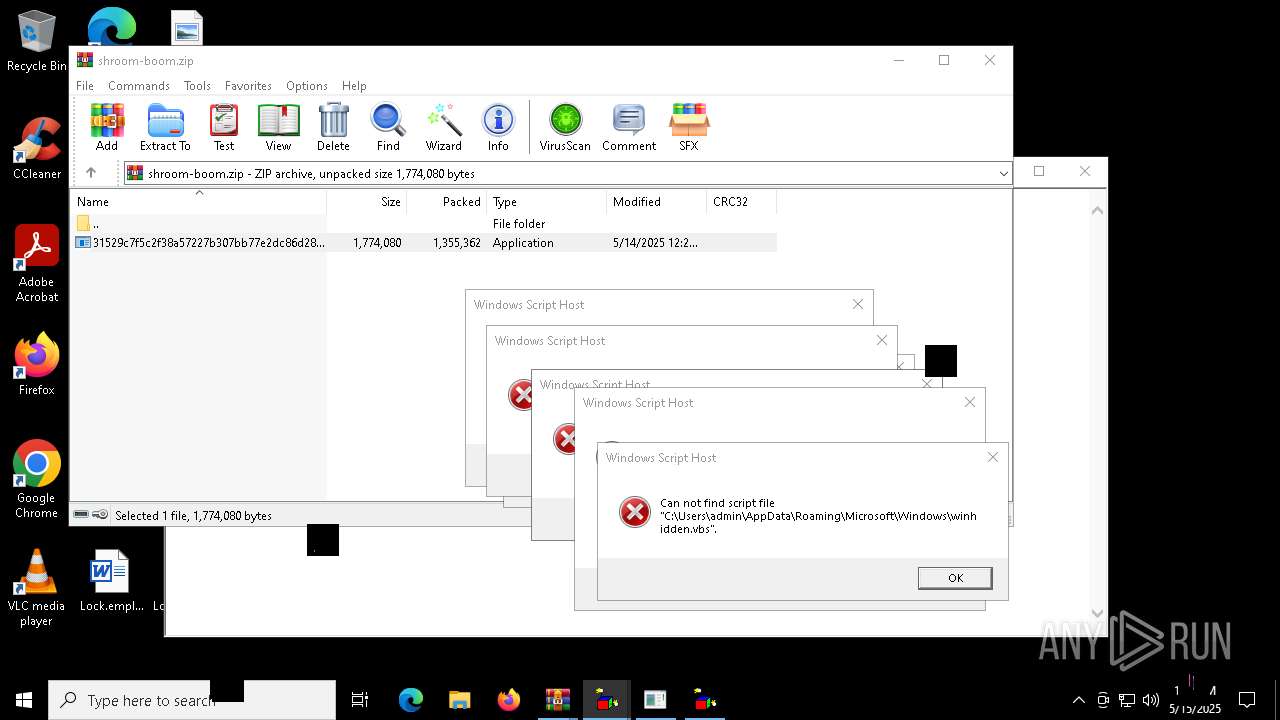
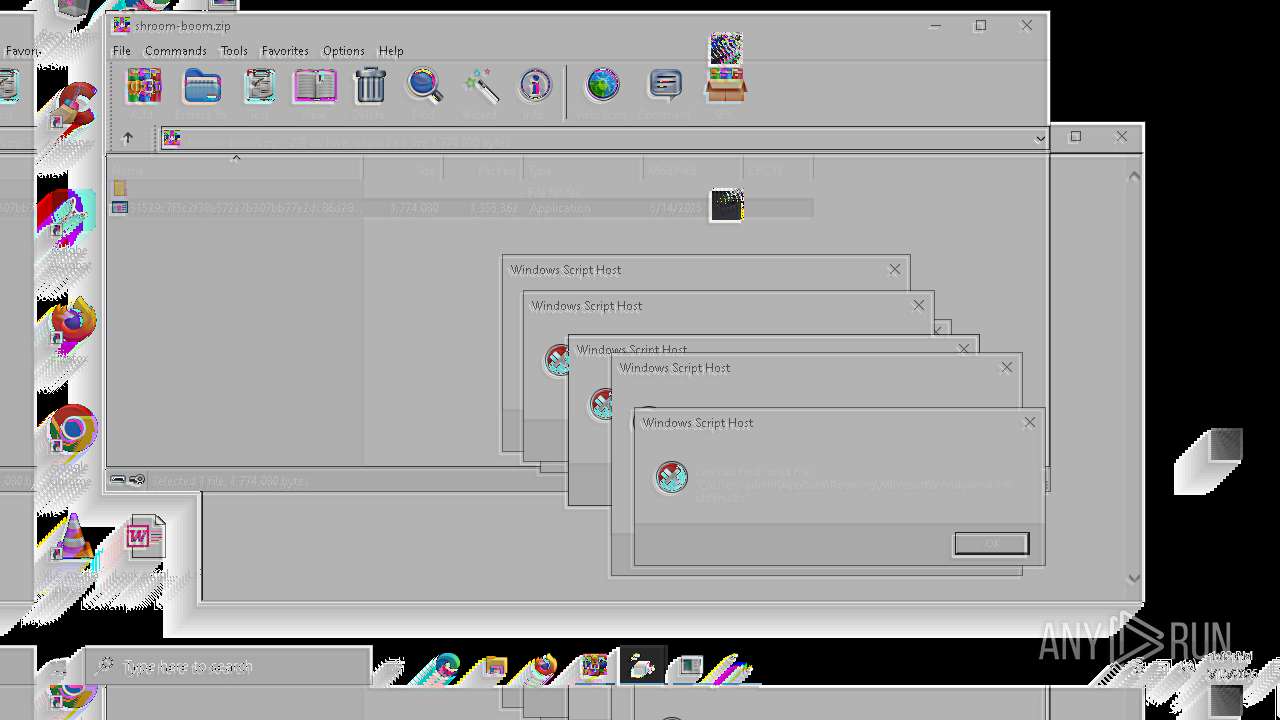
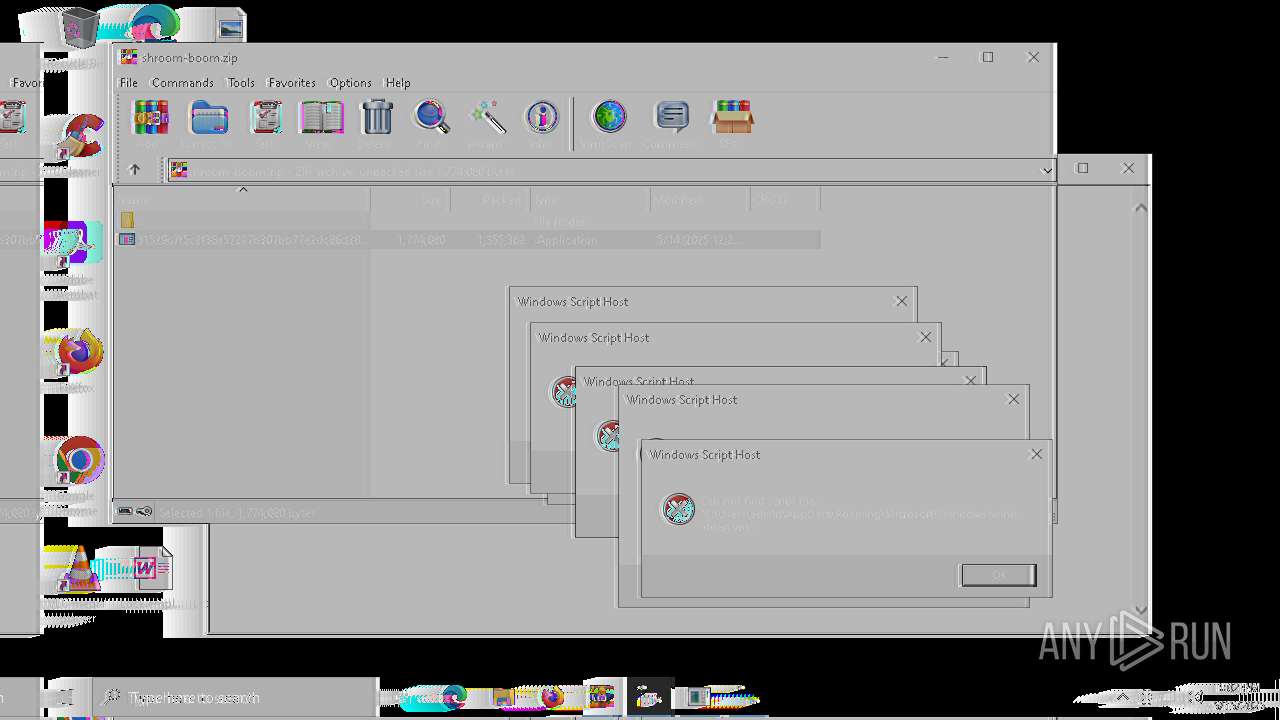
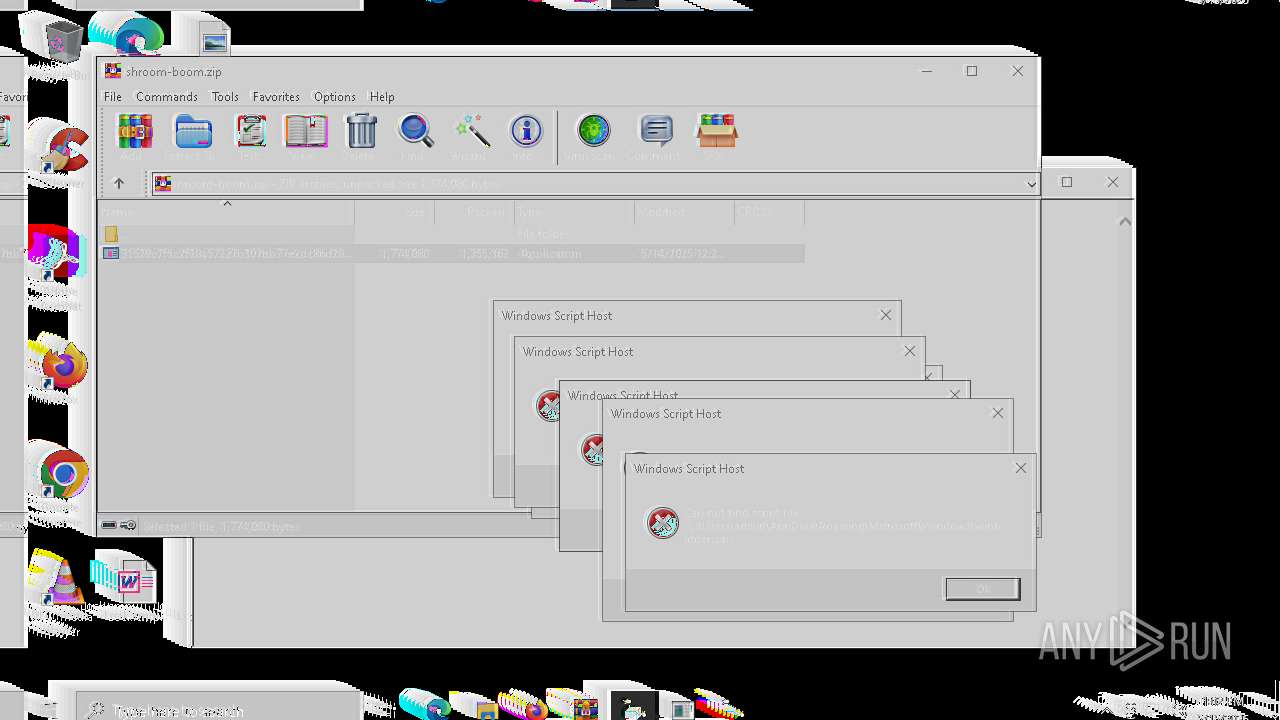
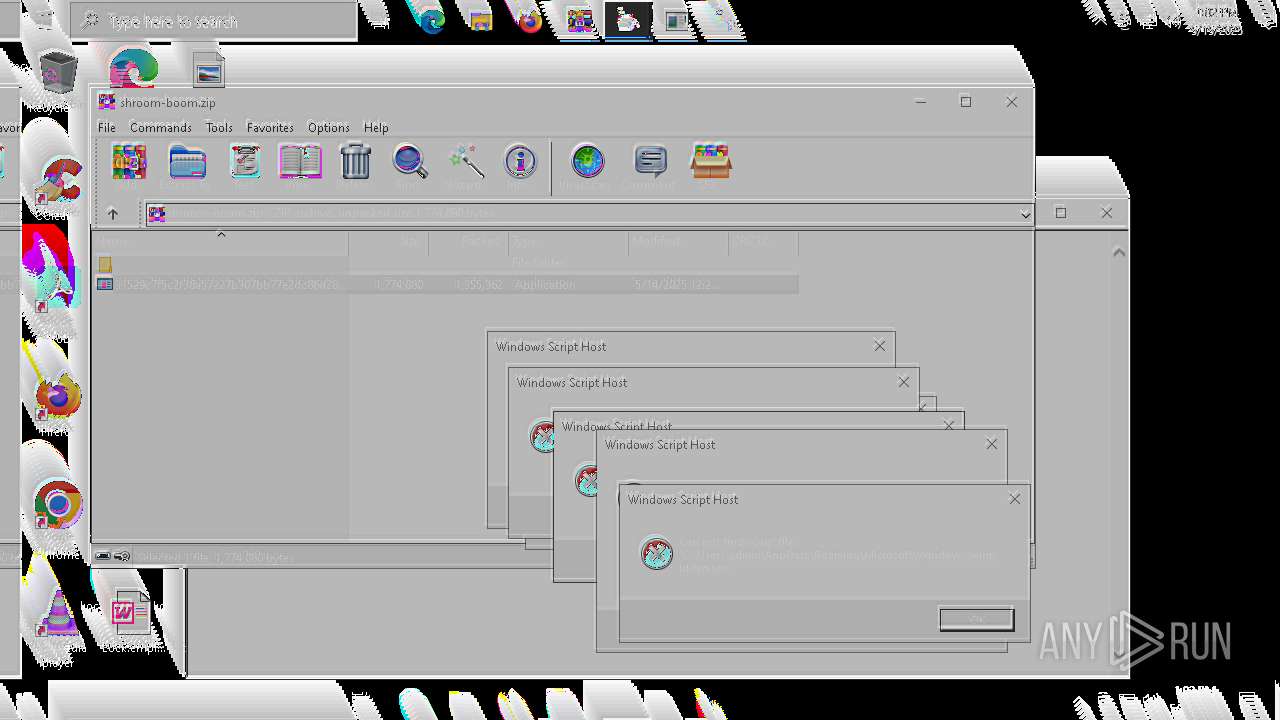
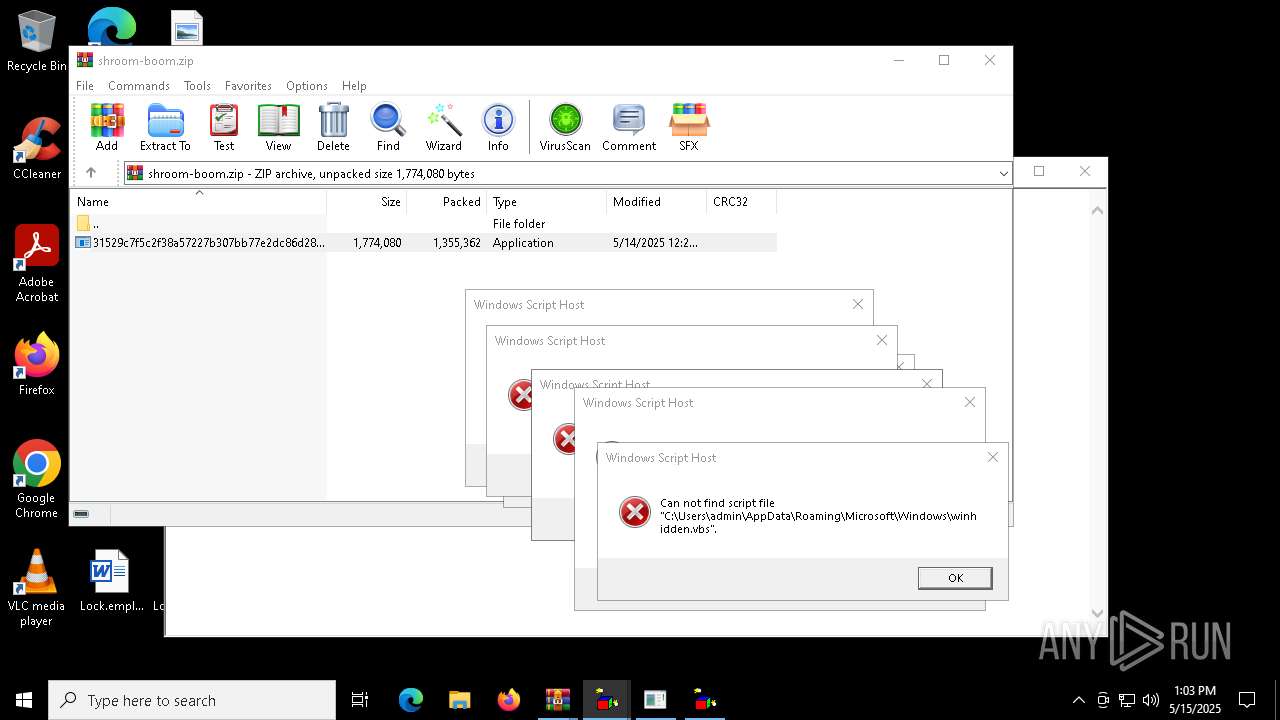
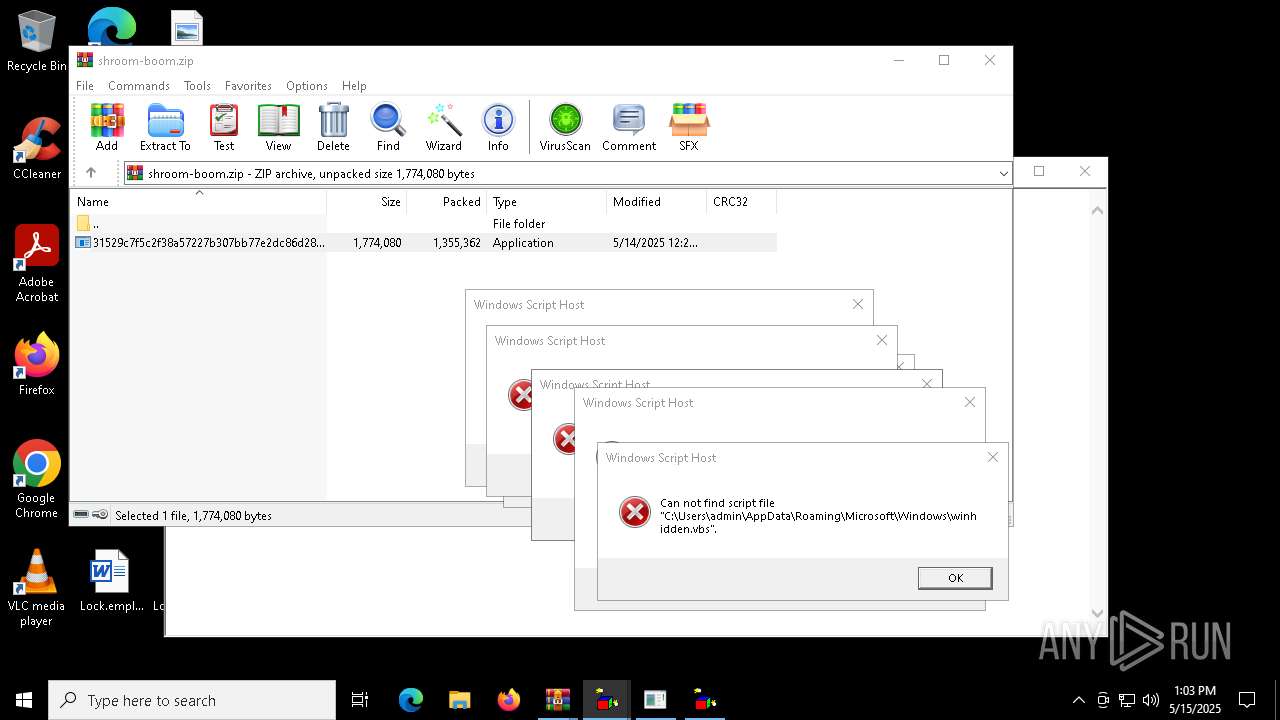
| File name: | shroom-boom.zip.zip |
| Full analysis: | https://app.any.run/tasks/c9314ac1-c41c-47b3-8ce9-78e5b8f9be70 |
| Verdict: | Malicious activity |
| Analysis date: | May 15, 2025, 12:59:38 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
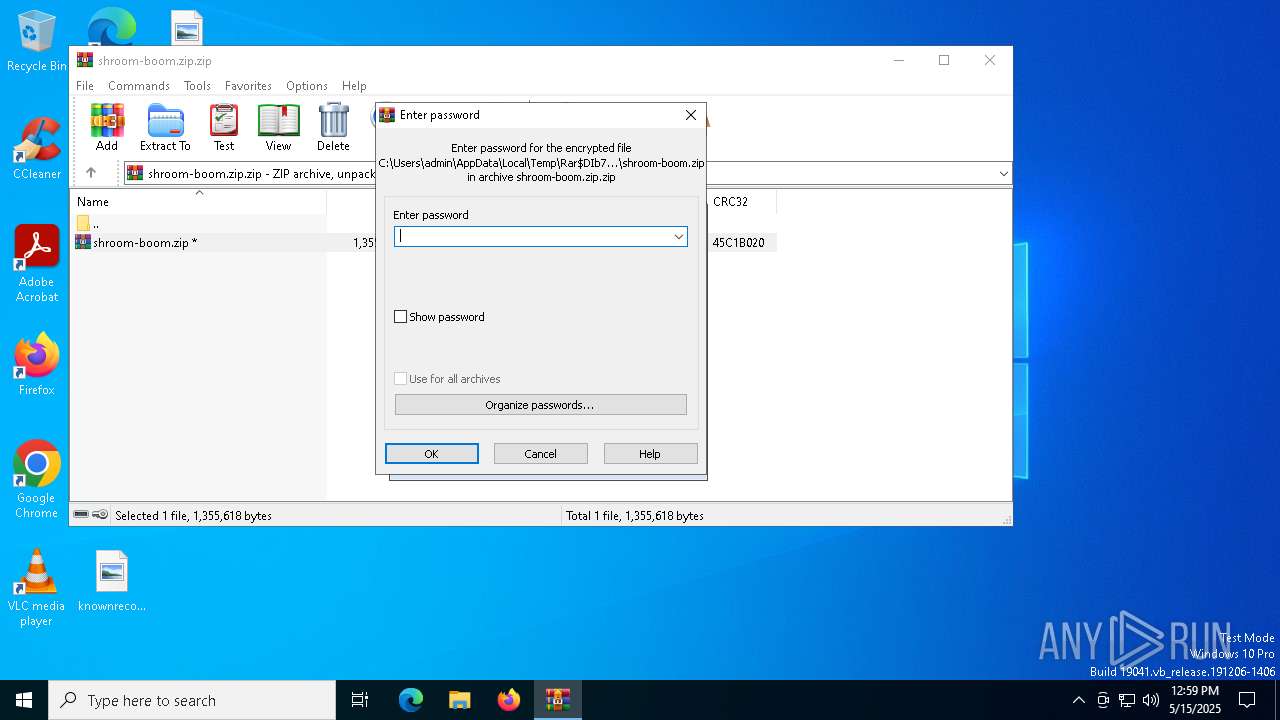
| File info: | Zip archive data, at least v5.1 to extract, compression method=AES Encrypted |
| MD5: | EABF4A99EFA55377D8BD3D274F79DD12 |
| SHA1: | AC79B3649D0D4B01C23C1EB5AFCCD9C04D7A4992 |
| SHA256: | 90C5B09C663DF2AABC361E0EE6CBC75EA618D4519BEB27040FB3CF0255FE9910 |
| SSDEEP: | 49152:YA+dvUrsBwndD1hNKS9KkUSwCMRzkTwP9UKfF37hJfI6Sr1lk+x62gfsFoK7icTk:bEvUrfndDH4MMBH9Bd3YVrs6t7FucTkb |
MALICIOUS
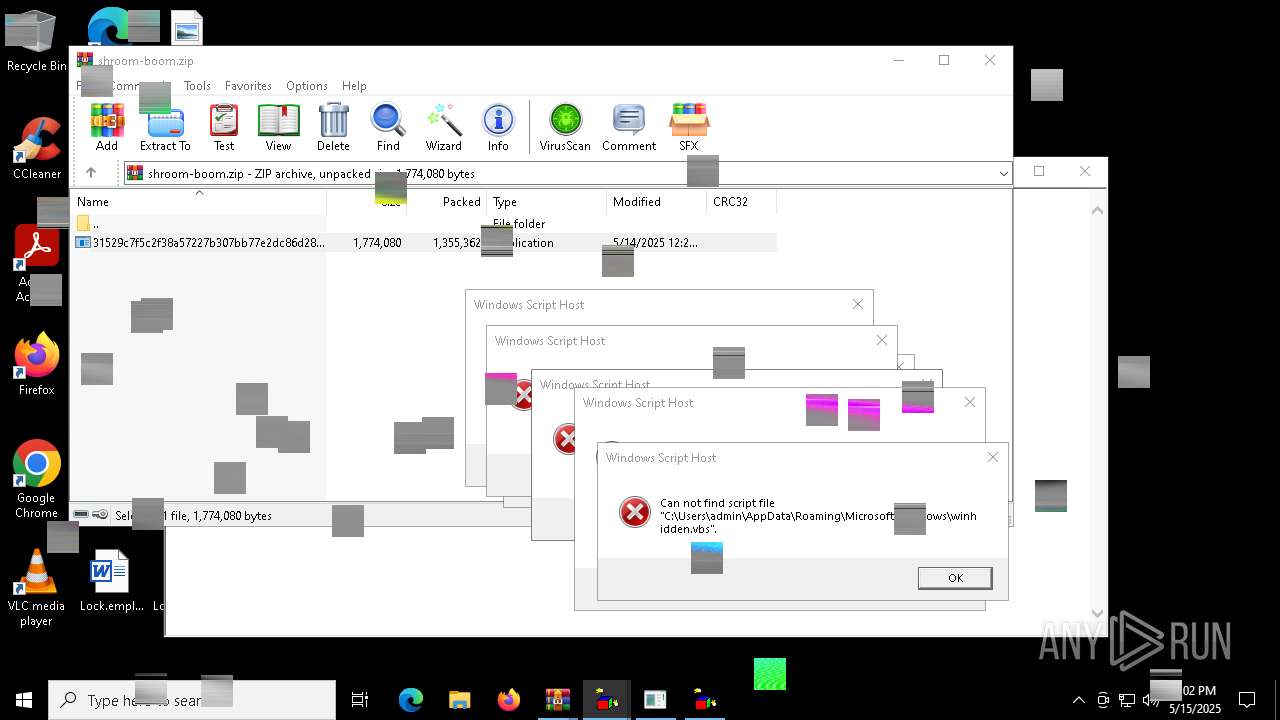
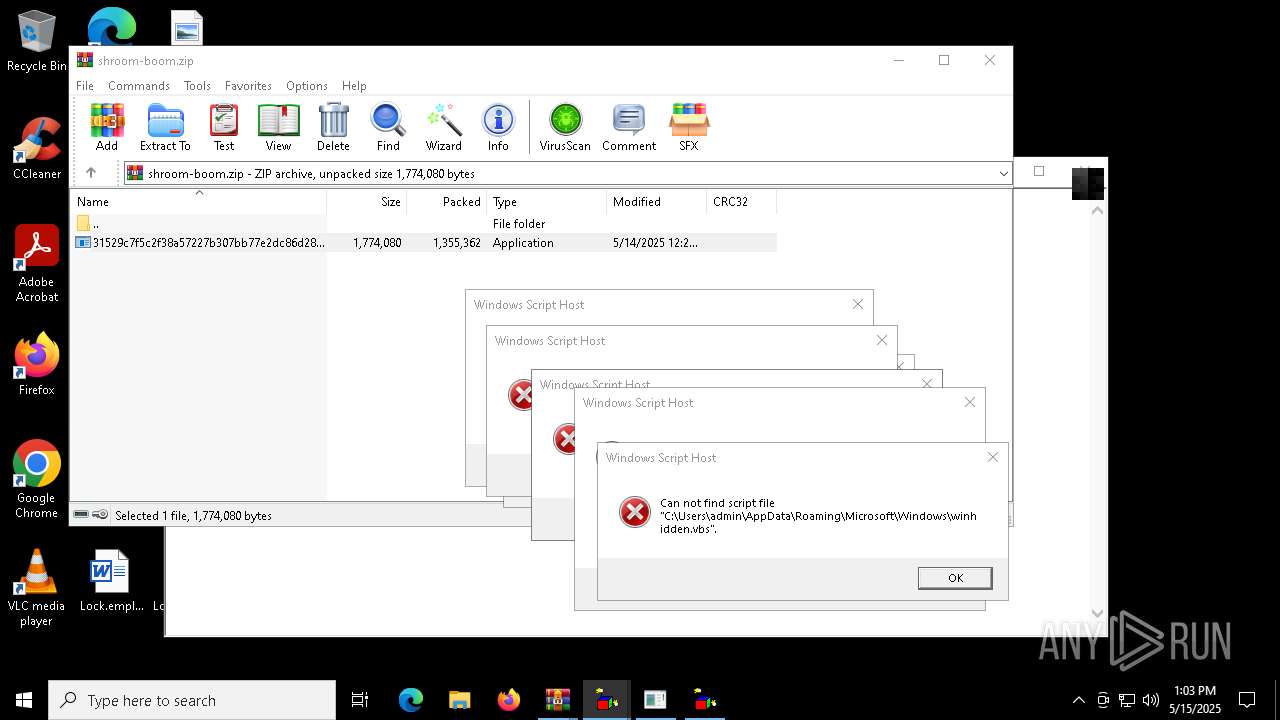
Gets %appdata% folder path (SCRIPT)
- wscript.exe (PID: 8152)
- wscript.exe (PID: 2108)
Accesses environment variables (SCRIPT)
- wscript.exe (PID: 8152)
- wscript.exe (PID: 2108)
Reads the value of a key from the registry (SCRIPT)
- wscript.exe (PID: 7264)
Modifies registry startup key (SCRIPT)
- wscript.exe (PID: 7264)
- wscript.exe (PID: 8180)
Creates a new registry key or changes the value of an existing one (SCRIPT)
- wscript.exe (PID: 7264)
- wscript.exe (PID: 8180)
Copies file to a new location (SCRIPT)
- wscript.exe (PID: 7264)
- wscript.exe (PID: 2108)
- wscript.exe (PID: 8180)
Starts NET.EXE for service management
- cmd.exe (PID: 7740)
- net.exe (PID: 8080)
Changes the autorun value in the registry
- reg.exe (PID: 8420)
Uses Task Scheduler to run other applications
- cmd.exe (PID: 7212)
SUSPICIOUS
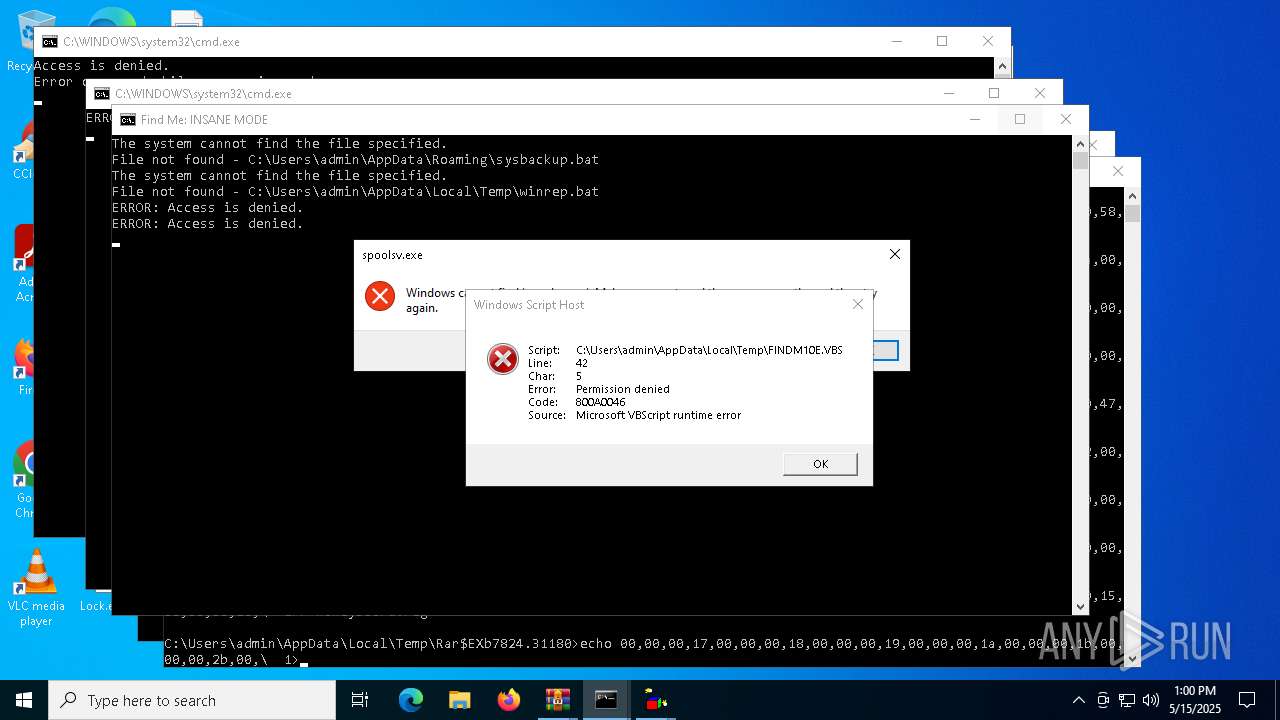
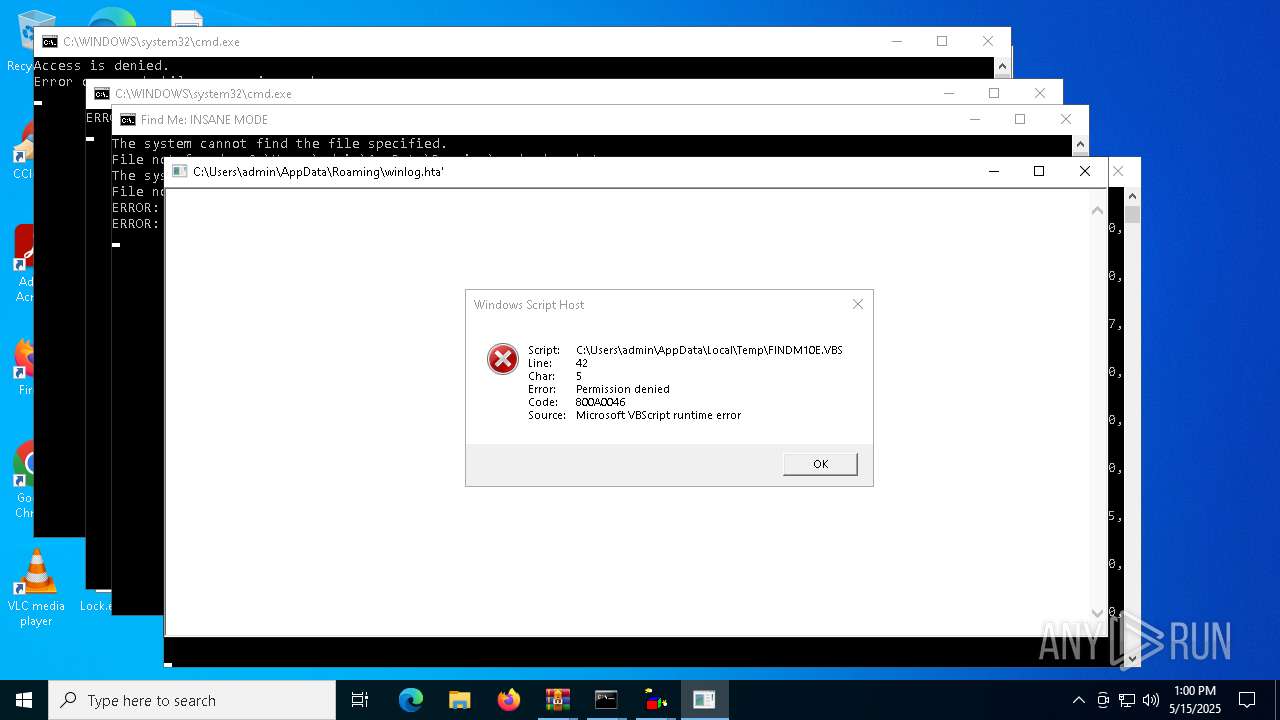
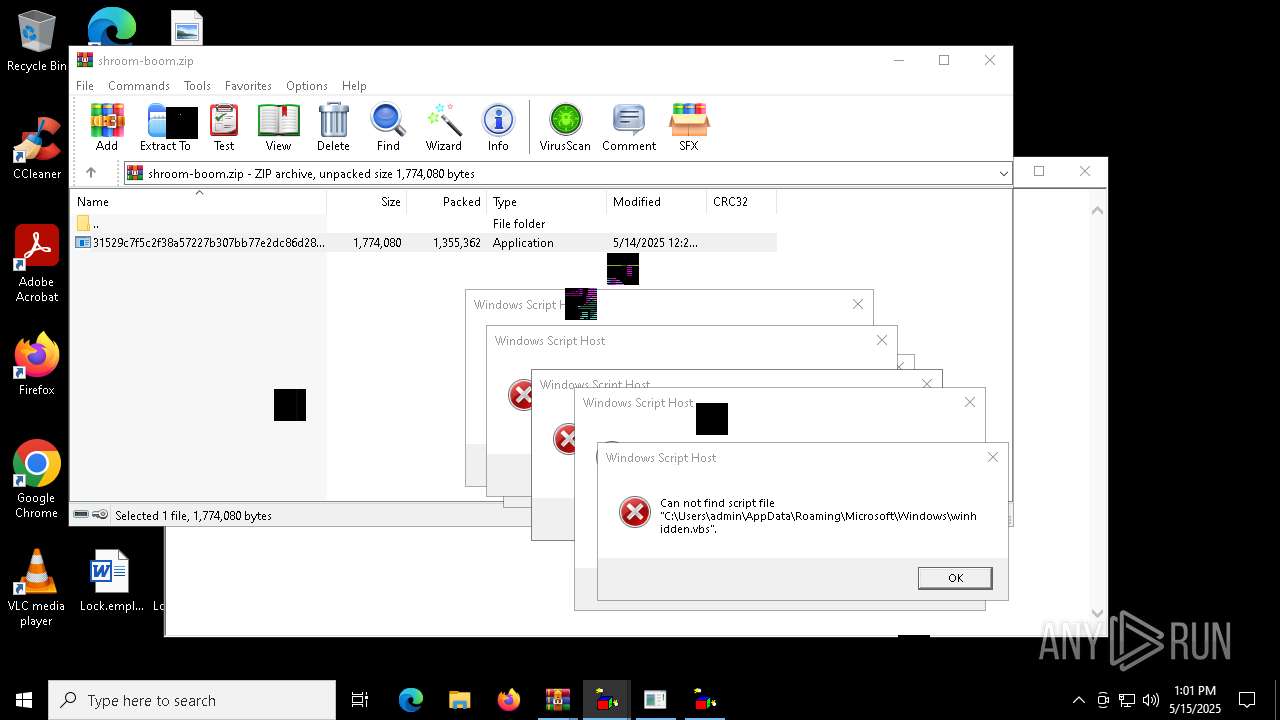
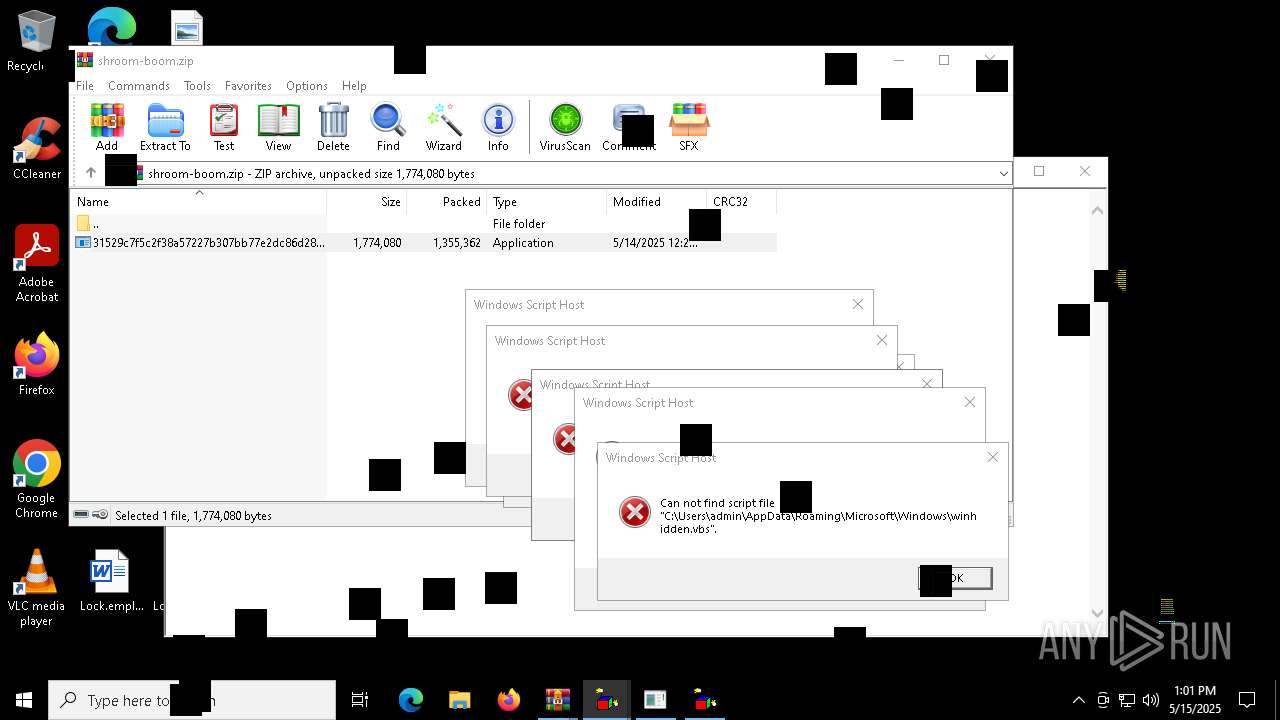
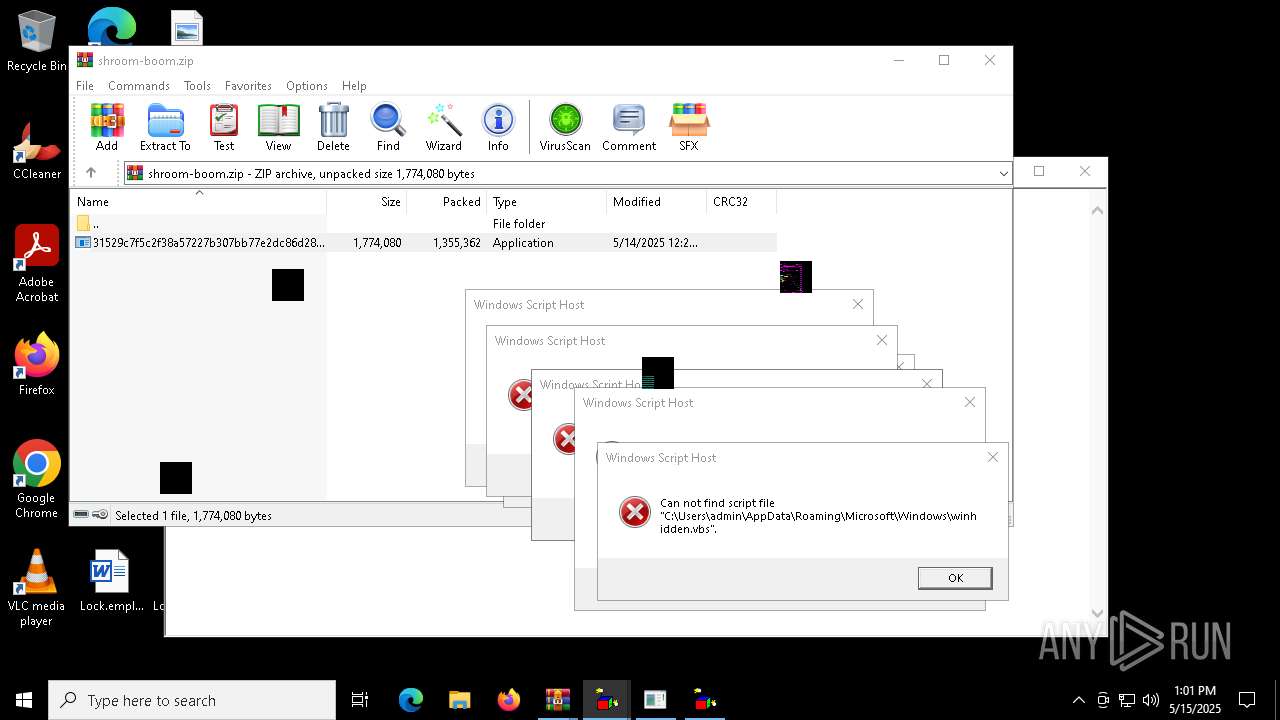
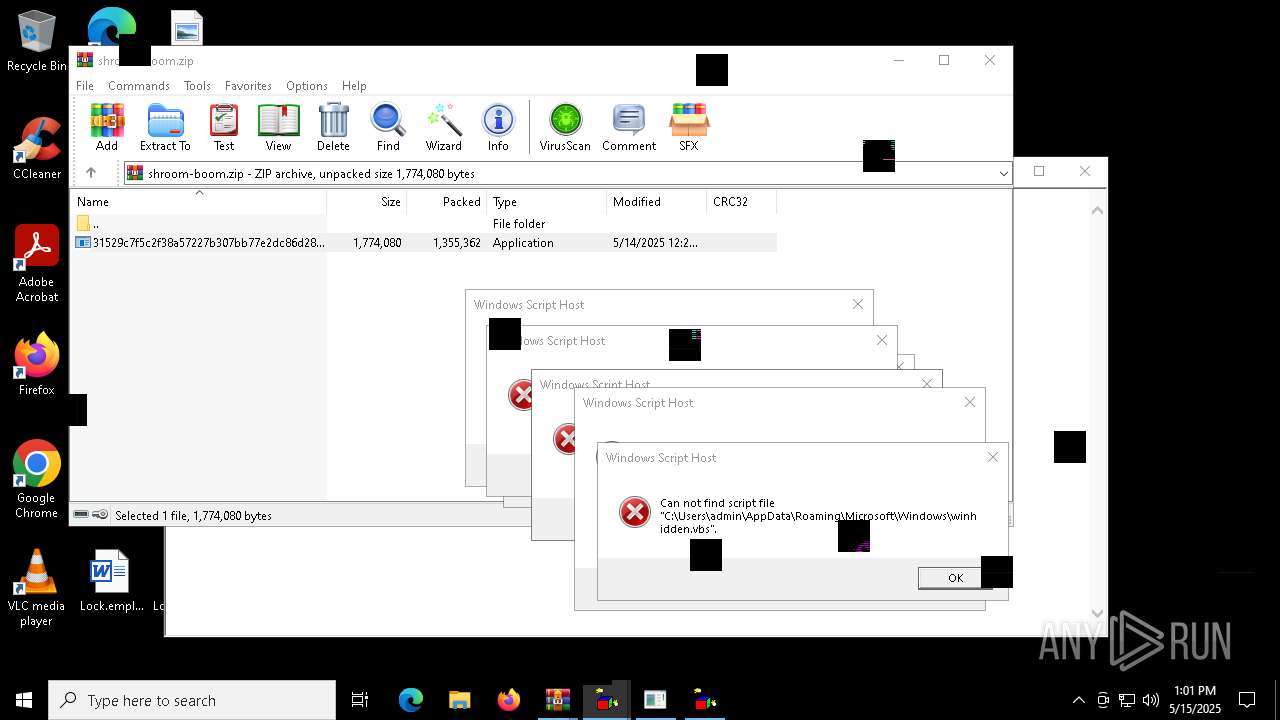
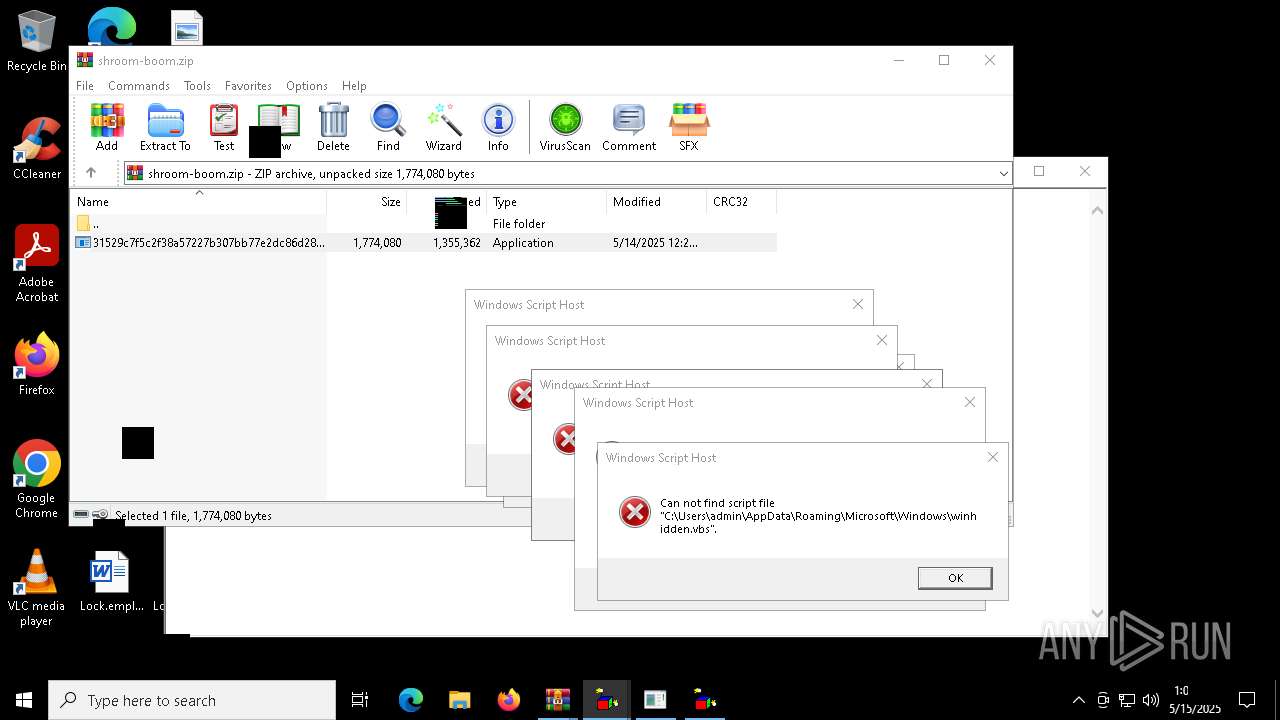
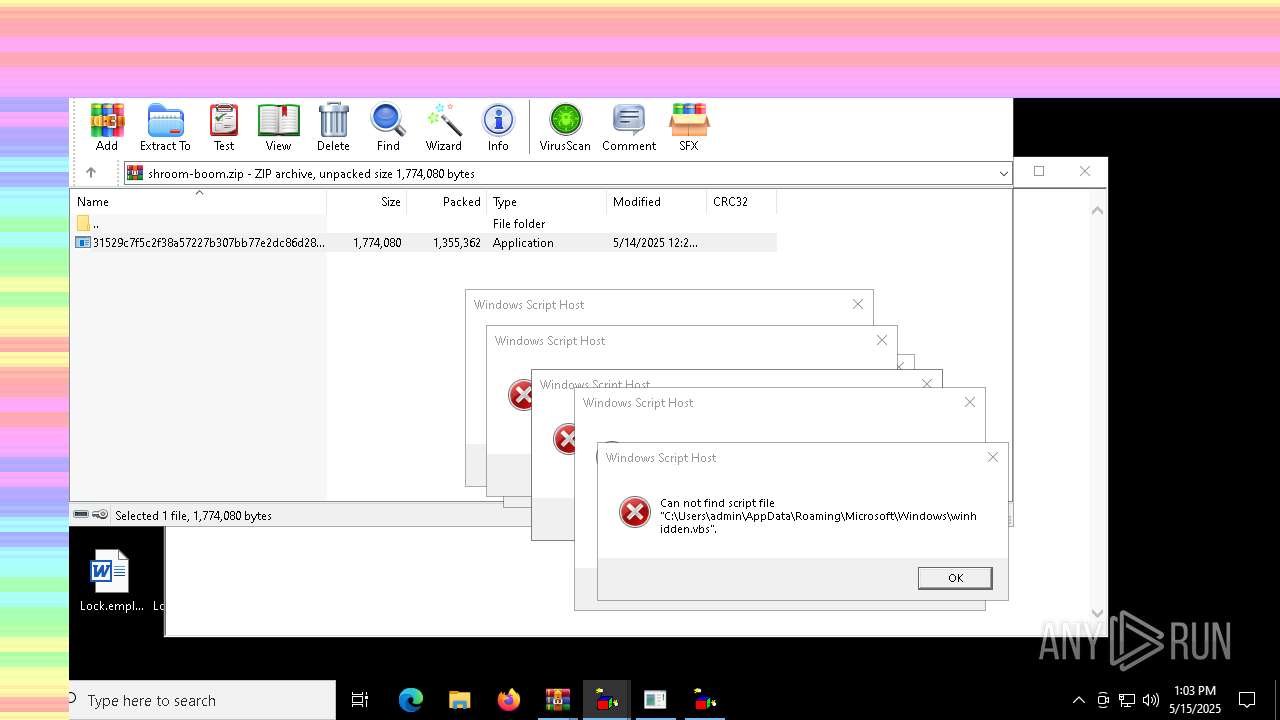
The process executes VB scripts
- 31529c7f5c2f38a57227b307bb77e2dc86d283bd8110cf0b8a38285f75b7f872.exe (PID: 8036)
- cmd.exe (PID: 4980)
- cmd.exe (PID: 8944)
- cmd.exe (PID: 8904)
- cmd.exe (PID: 8568)
- cmd.exe (PID: 5048)
- cmd.exe (PID: 8512)
- cmd.exe (PID: 7208)
- cmd.exe (PID: 8296)
- cmd.exe (PID: 8644)
- cmd.exe (PID: 8712)
The process executes JS scripts
- 31529c7f5c2f38a57227b307bb77e2dc86d283bd8110cf0b8a38285f75b7f872.exe (PID: 8036)
Reads security settings of Internet Explorer
- WinRAR.exe (PID: 7824)
- WinRAR.exe (PID: 7268)
- 31529c7f5c2f38a57227b307bb77e2dc86d283bd8110cf0b8a38285f75b7f872.exe (PID: 8036)
- ORNYAE.EXE (PID: 5548)
Application launched itself
- WinRAR.exe (PID: 7268)
- cmd.exe (PID: 736)
- cmd.exe (PID: 7588)
Checks whether a specific file exists (SCRIPT)
- wscript.exe (PID: 8152)
- wscript.exe (PID: 2108)
Creates FileSystem object to access computer's file system (SCRIPT)
- wscript.exe (PID: 8152)
- wscript.exe (PID: 7264)
- wscript.exe (PID: 2108)
- wscript.exe (PID: 8180)
Gets full path of the running script (SCRIPT)
- wscript.exe (PID: 8180)
- wscript.exe (PID: 7264)
- wscript.exe (PID: 2108)
Uses ATTRIB.EXE to modify file attributes
- cmd.exe (PID: 7212)
- cmd.exe (PID: 2692)
- cmd.exe (PID: 5640)
- cmd.exe (PID: 1052)
- cmd.exe (PID: 4980)
- cmd.exe (PID: 7588)
- cmd.exe (PID: 8944)
- cmd.exe (PID: 8904)
- cmd.exe (PID: 5048)
- cmd.exe (PID: 8568)
- cmd.exe (PID: 8296)
- cmd.exe (PID: 8512)
- cmd.exe (PID: 8644)
- cmd.exe (PID: 8436)
- cmd.exe (PID: 8712)
- cmd.exe (PID: 8612)
- cmd.exe (PID: 4932)
- cmd.exe (PID: 7208)
Runs shell command (SCRIPT)
- wscript.exe (PID: 7264)
- wscript.exe (PID: 8180)
- wscript.exe (PID: 8152)
- wscript.exe (PID: 2108)
- wscript.exe (PID: 8536)
- wscript.exe (PID: 9176)
- wscript.exe (PID: 9120)
Starts CMD.EXE for commands execution
- wscript.exe (PID: 7264)
- mshta.exe (PID: 5256)
- wscript.exe (PID: 8180)
- 31529c7f5c2f38a57227b307bb77e2dc86d283bd8110cf0b8a38285f75b7f872.exe (PID: 8036)
- wscript.exe (PID: 8152)
- wscript.exe (PID: 2108)
- mshta.exe (PID: 7816)
- cmd.exe (PID: 736)
- wscript.exe (PID: 8536)
- cmd.exe (PID: 7588)
- wscript.exe (PID: 9176)
- wscript.exe (PID: 9120)
- wscript.exe (PID: 7376)
- wscript.exe (PID: 8952)
- wscript.exe (PID: 9172)
- wscript.exe (PID: 6392)
Likely accesses (executes) a file from the Public directory
- cmd.exe (PID: 5640)
- attrib.exe (PID: 7816)
- cmd.exe (PID: 728)
Kill processes via PowerShell
- powershell.exe (PID: 7672)
- powershell.exe (PID: 7676)
- powershell.exe (PID: 7768)
- powershell.exe (PID: 5384)
- powershell.exe (PID: 7752)
Starts POWERSHELL.EXE for commands execution
- wscript.exe (PID: 8180)
Write to the desktop.ini file (may be used to cloak folders)
- ORNYAE.EXE (PID: 5548)
Executable content was dropped or overwritten
- 31529c7f5c2f38a57227b307bb77e2dc86d283bd8110cf0b8a38285f75b7f872.exe (PID: 8036)
- ORNYAE.EXE (PID: 5548)
Gets a collection of all available drive names (SCRIPT)
- wscript.exe (PID: 2108)
Gets the drive type (SCRIPT)
- wscript.exe (PID: 2108)
Uses WMI to retrieve WMI-managed resources (SCRIPT)
- wscript.exe (PID: 2108)
Executing commands from a ".bat" file
- 31529c7f5c2f38a57227b307bb77e2dc86d283bd8110cf0b8a38285f75b7f872.exe (PID: 8036)
- wscript.exe (PID: 8536)
- wscript.exe (PID: 9176)
- wscript.exe (PID: 9120)
- wscript.exe (PID: 7376)
- wscript.exe (PID: 8952)
- wscript.exe (PID: 9172)
- wscript.exe (PID: 6392)
Accesses ComputerSystem(Win32_ComputerSystem) via WMI (SCRIPT)
- wscript.exe (PID: 2108)
Executes WMI query (SCRIPT)
- wscript.exe (PID: 2108)
Accesses computer name via WMI (SCRIPT)
- wscript.exe (PID: 2108)
Accesses current user name via WMI (SCRIPT)
- wscript.exe (PID: 8180)
Uses REG/REGEDIT.EXE to modify registry
- cmd.exe (PID: 5984)
- cmd.exe (PID: 6300)
- cmd.exe (PID: 8332)
- cmd.exe (PID: 1052)
- cmd.exe (PID: 7588)
Uses TASKKILL.EXE to kill process
- cmd.exe (PID: 1052)
Uses NETSH.EXE to change the status of the firewall
- cmd.exe (PID: 7740)
Uses WMIC.EXE to create a new process
- cmd.exe (PID: 8244)
Uses WMIC.EXE to obtain local storage devices information
- cmd.exe (PID: 9048)
There is functionality for taking screenshot (YARA)
- MONOXIDEX86.HARMLESS.EXE (PID: 5552)
- ORNYAE.EXE (PID: 5548)
The process executes via Task Scheduler
- wscript.exe (PID: 9992)
INFO
Process checks computer location settings
- 31529c7f5c2f38a57227b307bb77e2dc86d283bd8110cf0b8a38285f75b7f872.exe (PID: 8036)
Create files in a temporary directory
- 31529c7f5c2f38a57227b307bb77e2dc86d283bd8110cf0b8a38285f75b7f872.exe (PID: 8036)
Reads the computer name
- 31529c7f5c2f38a57227b307bb77e2dc86d283bd8110cf0b8a38285f75b7f872.exe (PID: 8036)
- ORNYAE.EXE (PID: 5548)
Checks supported languages
- 31529c7f5c2f38a57227b307bb77e2dc86d283bd8110cf0b8a38285f75b7f872.exe (PID: 8036)
- ORNYAE.EXE (PID: 5548)
- MONOXIDEX86.HARMLESS.EXE (PID: 5552)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 7824)
Reads Internet Explorer settings
- mshta.exe (PID: 5256)
- mshta.exe (PID: 5680)
- mshta.exe (PID: 7816)
- mshta.exe (PID: 7084)
The sample compiled with english language support
- 31529c7f5c2f38a57227b307bb77e2dc86d283bd8110cf0b8a38285f75b7f872.exe (PID: 8036)
- ORNYAE.EXE (PID: 5548)
Reads mouse settings
- ORNYAE.EXE (PID: 5548)
Reads the machine GUID from the registry
- ORNYAE.EXE (PID: 5548)
Checks proxy server information
- mshta.exe (PID: 5680)
Reads security settings of Internet Explorer
- WMIC.exe (PID: 8552)
- WMIC.exe (PID: 9068)
Creates files or folders in the user directory
- ORNYAE.EXE (PID: 5548)
The process uses AutoIt
- ORNYAE.EXE (PID: 5548)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 51 |
|---|---|
| ZipBitFlag: | 0x0009 |
| ZipCompression: | Unknown (99) |
| ZipModifyDate: | 2025:05:15 12:59:04 |
| ZipCRC: | 0x45c1b020 |
| ZipCompressedSize: | 1356061 |
| ZipUncompressedSize: | 1355618 |
| ZipFileName: | shroom-boom.zip |
Total processes
525
Monitored processes
396
Malicious processes
22
Suspicious processes
4
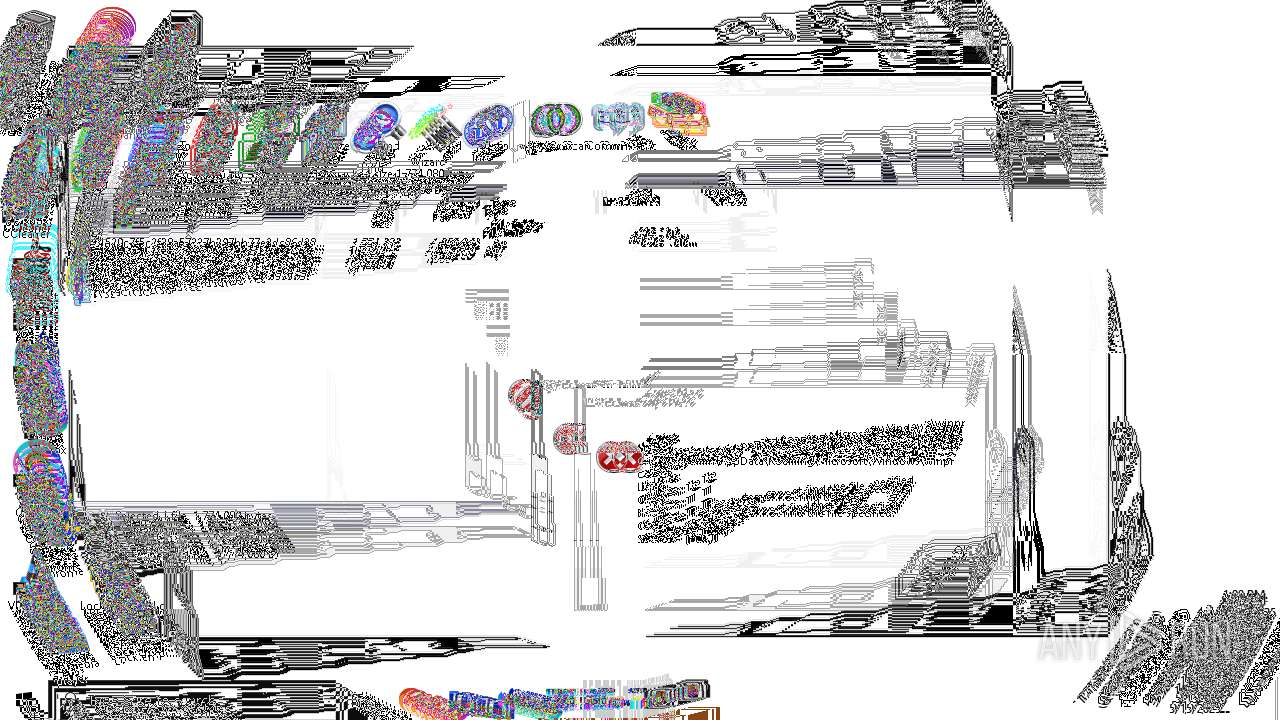
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 680 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 684 | "C:\Windows\System32\cmd.exe" /c copy C:\Users\admin\AppData\Roaming\sysproc.js C:\Users\admin\AppData\Roaming\winupdate.hta | C:\Windows\SysWOW64\cmd.exe | — | wscript.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 1 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 728 | "C:\Windows\System32\cmd.exe" /c copy C:\Users\admin\AppData\Roaming\sys32.hta \\DESKTOP-JGLLJLD\C$\Users\Public\sys32.hta | C:\Windows\SysWOW64\cmd.exe | — | wscript.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 736 | C:\WINDOWS\system32\cmd.exe /c ""C:\Users\admin\AppData\Local\Temp\S409-L4.BAT" " | C:\Windows\SysWOW64\cmd.exe | — | 31529c7f5c2f38a57227b307bb77e2dc86d283bd8110cf0b8a38285f75b7f872.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 1 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 896 | wscript "C:\Users\admin\AppData\Roaming\Microsoft\Windows\winproc.vbs" | C:\Windows\SysWOW64\wscript.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft ® Windows Based Script Host Version: 5.812.10240.16384 Modules
| |||||||||||||||
| 976 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1012 | "C:\Windows\System32\cmd.exe" /c copy C:\Users\admin\AppData\Roaming\sysproc.js C:\Users\admin\AppData\Roaming\winupdate.hta | C:\Windows\SysWOW64\cmd.exe | — | wscript.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 1 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1040 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1052 | C:\WINDOWS\system32\cmd.exe /c ""C:\Users\admin\AppData\Local\Temp\WIN32.BAT" " | C:\Windows\SysWOW64\cmd.exe | — | 31529c7f5c2f38a57227b307bb77e2dc86d283bd8110cf0b8a38285f75b7f872.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 1 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1132 | C:\WINDOWS\system32\cmd.exe /c ""C:\Users\admin\AppData\Local\Temp\S409-M1.BAT" " | C:\Windows\SysWOW64\cmd.exe | — | 31529c7f5c2f38a57227b307bb77e2dc86d283bd8110cf0b8a38285f75b7f872.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 1 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
61 275
Read events
61 052
Write events
223
Delete events
0
Modification events
| (PID) Process: | (7268) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (7268) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (7268) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (7268) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\shroom-boom.zip.zip | |||
| (PID) Process: | (7268) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (7268) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (7268) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (7268) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (7268) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface |
| Operation: | write | Name: | ShowPassword |
Value: 0 | |||
| (PID) Process: | (7824) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
Executable files
4
Suspicious files
83
Text files
45
Unknown types
1
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 8036 | 31529c7f5c2f38a57227b307bb77e2dc86d283bd8110cf0b8a38285f75b7f872.exe | C:\Users\admin\AppData\Local\Temp\HV23UR2.BAT | text | |
MD5:56D31575090E9C578213B2A5297B537E | SHA256:15938AAA257893055D2D5EA2B738FAF5E56640477108CE861471C3B3BA5770C0 | |||
| 7824 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXb7824.31180\31529c7f5c2f38a57227b307bb77e2dc86d283bd8110cf0b8a38285f75b7f872.exe | executable | |
MD5:86DC4A2BA727DF70A0C289846852CEA3 | SHA256:31529C7F5C2F38A57227B307BB77E2DC86D283BD8110CF0B8A38285F75B7F872 | |||
| 8036 | 31529c7f5c2f38a57227b307bb77e2dc86d283bd8110cf0b8a38285f75b7f872.exe | C:\Users\admin\AppData\Local\Temp\FINDME.HTA | html | |
MD5:1C5F01BC9E5017F6817B36FBF51FD4A2 | SHA256:06F073BC04C7FF783CD3ACFDAF6D7C835155FEE970EC8A98584B517D260E52E6 | |||
| 8036 | 31529c7f5c2f38a57227b307bb77e2dc86d283bd8110cf0b8a38285f75b7f872.exe | C:\Users\admin\AppData\Local\Temp\INSTALL.BAT | text | |
MD5:33B1DBCF0001EF830215EC58FB52F59B | SHA256:D2EFF3E7090B113664305AB77CD7C2883E302FE8F806D8C3E0BBF935298FE3D1 | |||
| 8036 | 31529c7f5c2f38a57227b307bb77e2dc86d283bd8110cf0b8a38285f75b7f872.exe | C:\Users\admin\AppData\Local\Temp\KVJ012A.BAT | text | |
MD5:06BA6D36BE44C91A2344B0F27BAEC1E8 | SHA256:E56B217717985D8AE33CEE12F9F76A439A85EC04F07A16254B02CD8A263E31E0 | |||
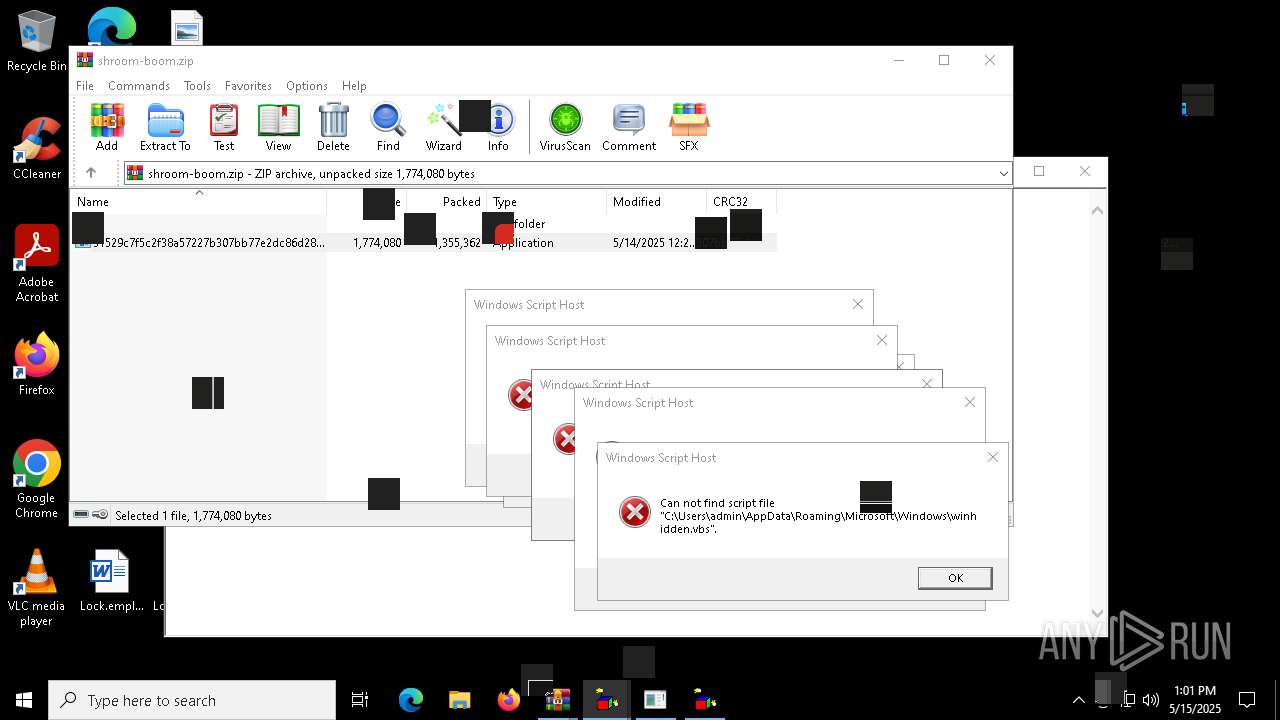
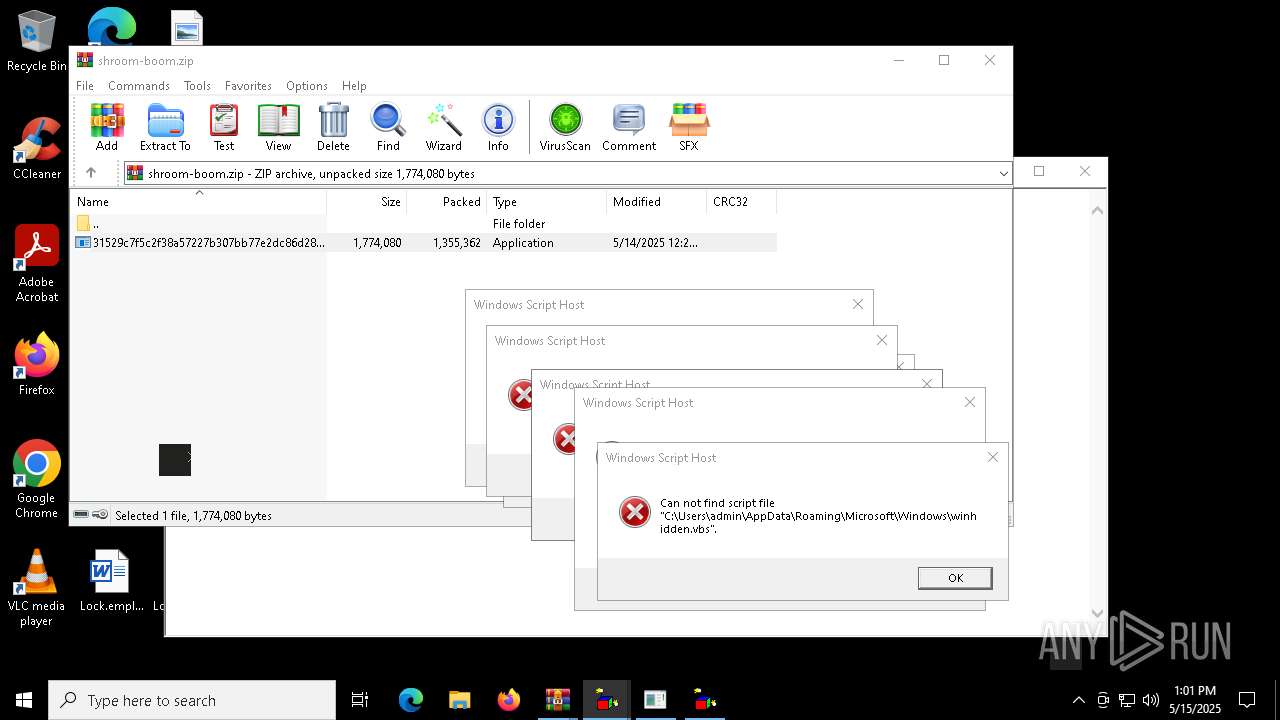
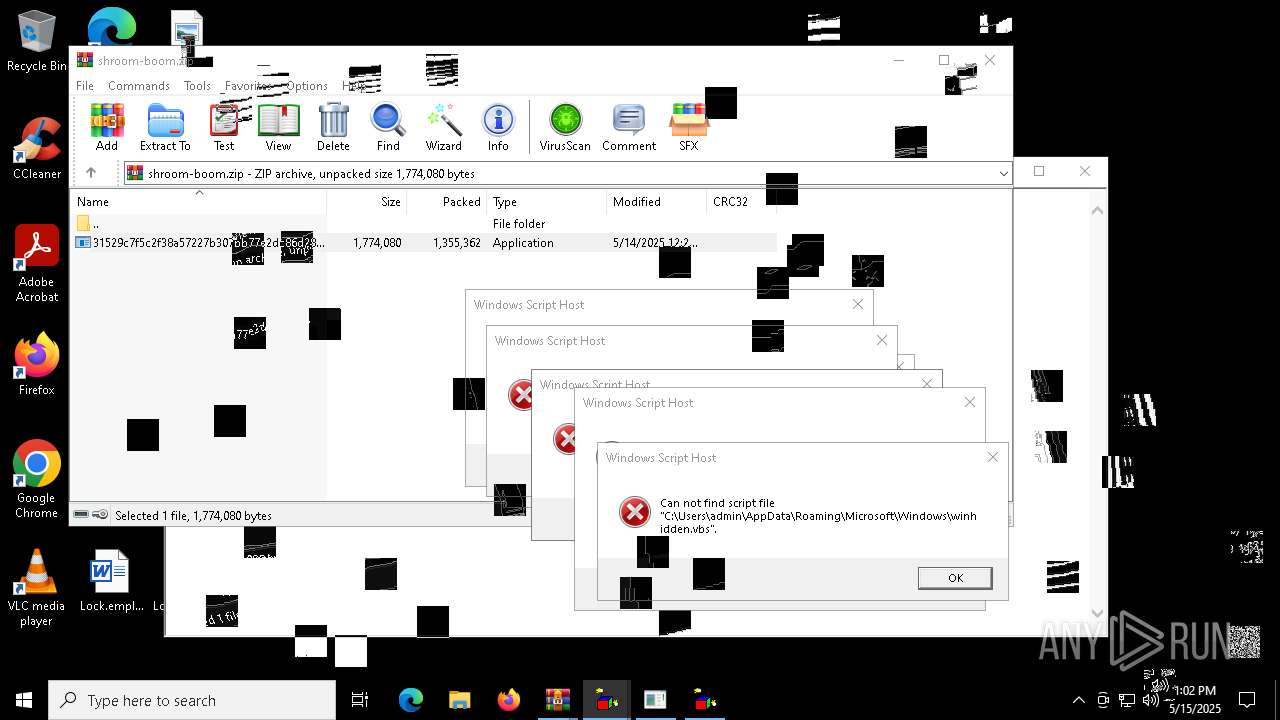
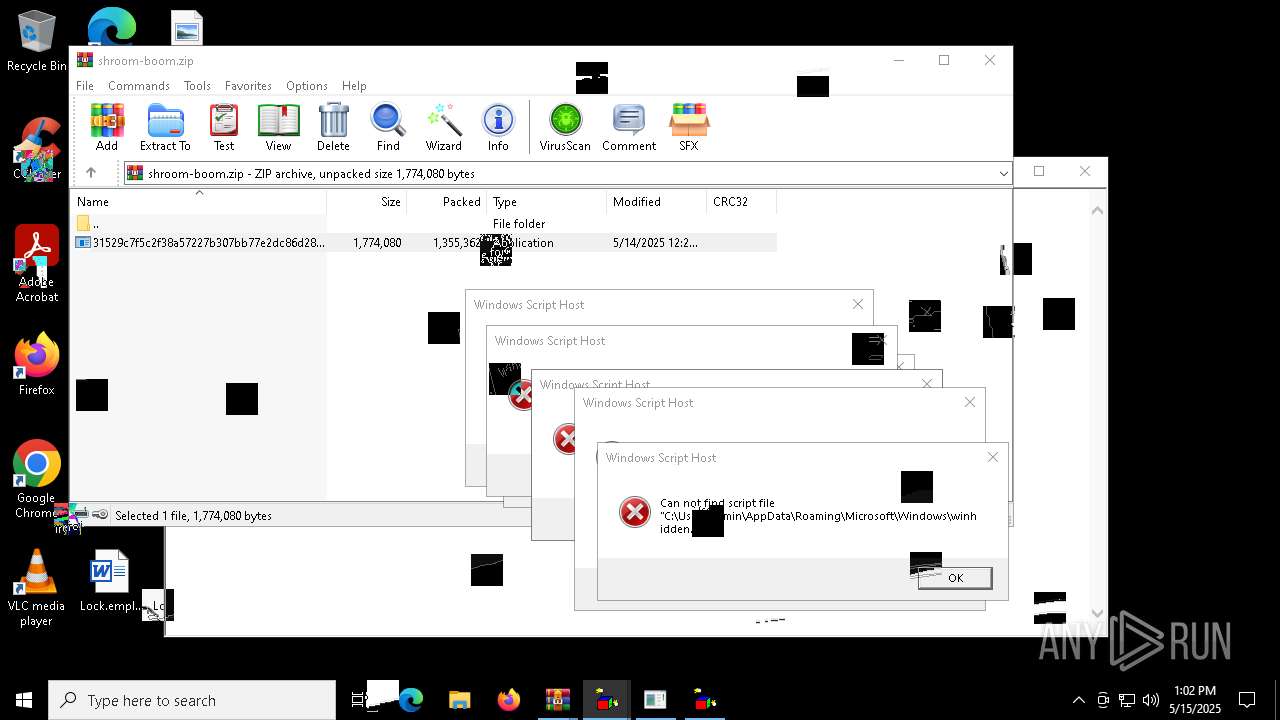
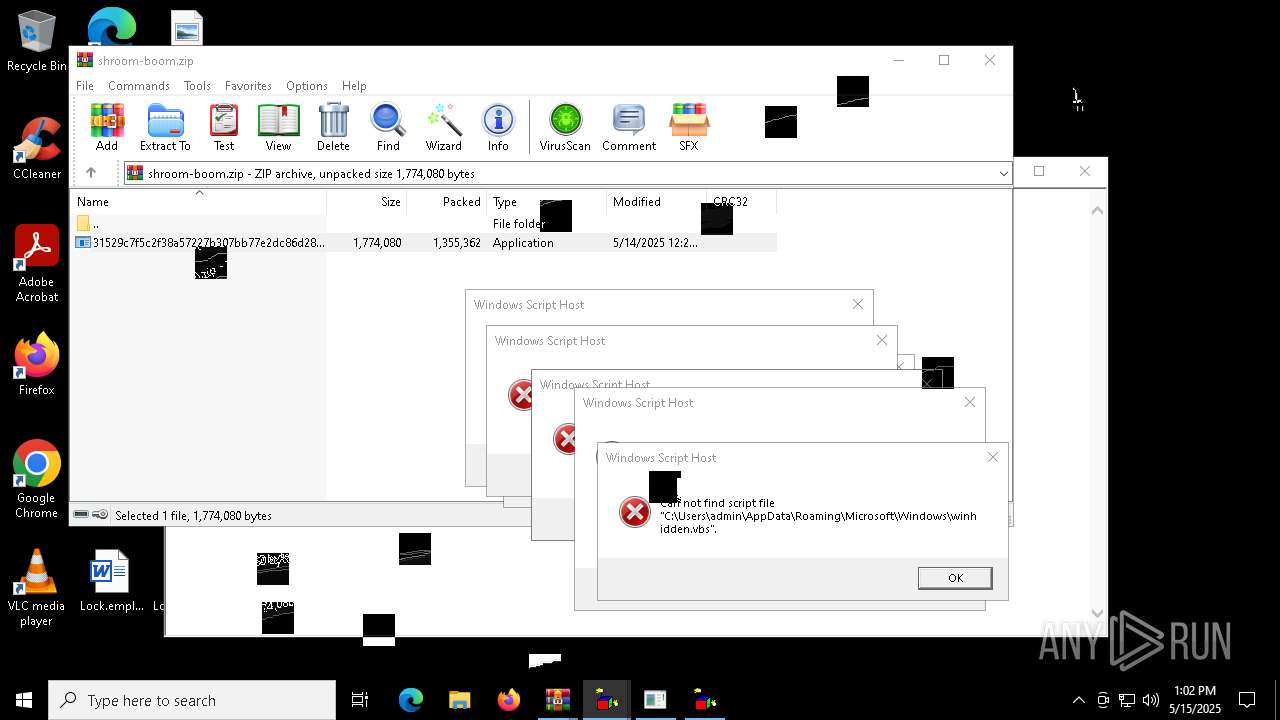
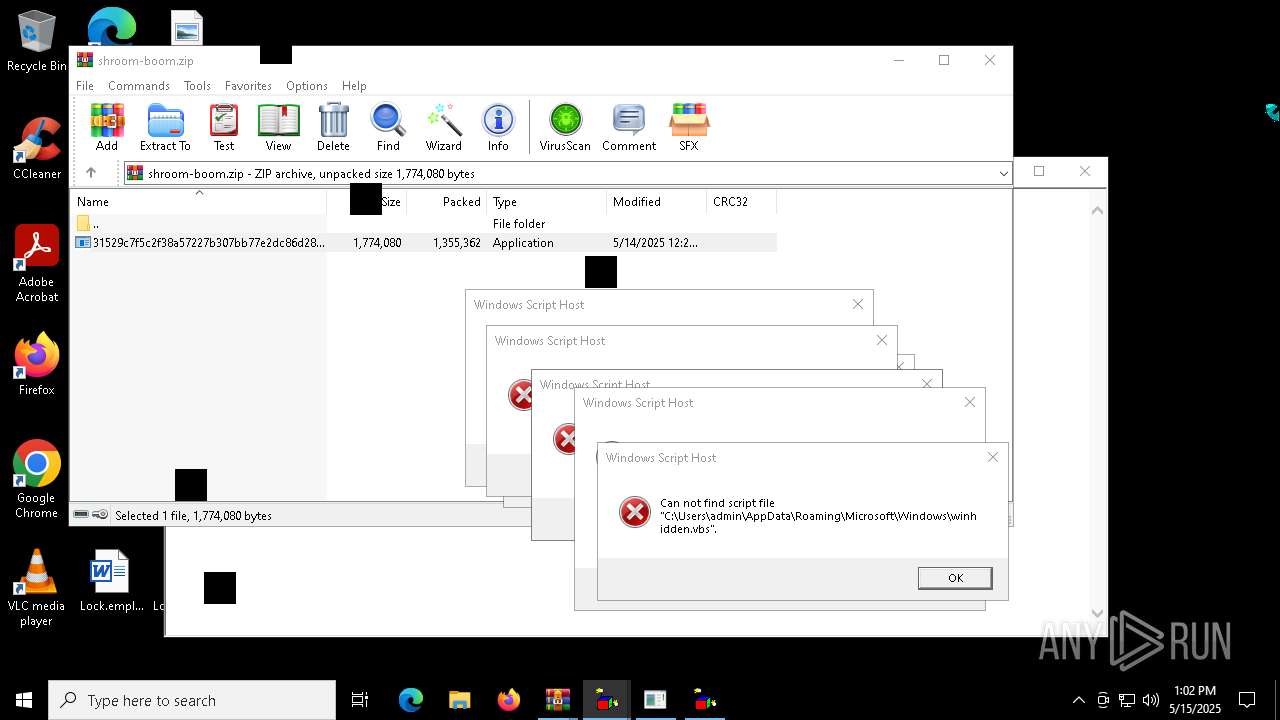
| 8036 | 31529c7f5c2f38a57227b307bb77e2dc86d283bd8110cf0b8a38285f75b7f872.exe | C:\Users\admin\AppData\Local\Temp\LOL.VBS | text | |
MD5:8BB7D55904F0592B12912CD17A6226A2 | SHA256:B363FBB1413DA760FDA389FBC481025B725DD281712542C32014BC6273EDDAC8 | |||
| 8180 | wscript.exe | C:\Windows\Temp\svchost_533423.exe | text | |
MD5:8EF7859CB44262053840E18037C862BD | SHA256:D4E84178FA198E903C717FAC251159A053BEDB307685E29C047621A22813BD9F | |||
| 8036 | 31529c7f5c2f38a57227b307bb77e2dc86d283bd8110cf0b8a38285f75b7f872.exe | C:\Users\admin\AppData\Local\Temp\KABOOMER.HTA | html | |
MD5:7D45B0D9EFCB4445975F2A914A7D6248 | SHA256:68BB9347CA9B337CCA3F4FBD949F93ABD2F3B73915F0E5F7EEB5D3F62209BCF0 | |||
| 8036 | 31529c7f5c2f38a57227b307bb77e2dc86d283bd8110cf0b8a38285f75b7f872.exe | C:\Users\admin\AppData\Local\Temp\INSTALLE10R.VBS | text | |
MD5:7CC3B626518CF48DBFC1AFCC85D95F21 | SHA256:5D3DB0D7702BC6B8CA3F8A644DD354203544E03E50E2745DD4540E95654C6296 | |||
| 7212 | cmd.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\winhide.bat | text | |
MD5:33B1DBCF0001EF830215EC58FB52F59B | SHA256:D2EFF3E7090B113664305AB77CD7C2883E302FE8F806D8C3E0BBF935298FE3D1 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
5
TCP/UDP connections
21
DNS requests
17
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5496 | MoUsoCoreWorker.exe | GET | 200 | 23.48.23.167:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
5496 | MoUsoCoreWorker.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
6544 | svchost.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
7996 | SIHClient.exe | GET | 200 | 23.219.150.101:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
7996 | SIHClient.exe | GET | 200 | 23.219.150.101:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5496 | MoUsoCoreWorker.exe | 23.48.23.167:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
5496 | MoUsoCoreWorker.exe | 23.35.229.160:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
3216 | svchost.exe | 172.211.123.248:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
6544 | svchost.exe | 20.190.160.3:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
6544 | svchost.exe | 2.23.77.188:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
2104 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
7996 | SIHClient.exe | 172.202.163.200:443 | slscr.update.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | GB | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
activation-v2.sls.microsoft.com |
| whitelisted |