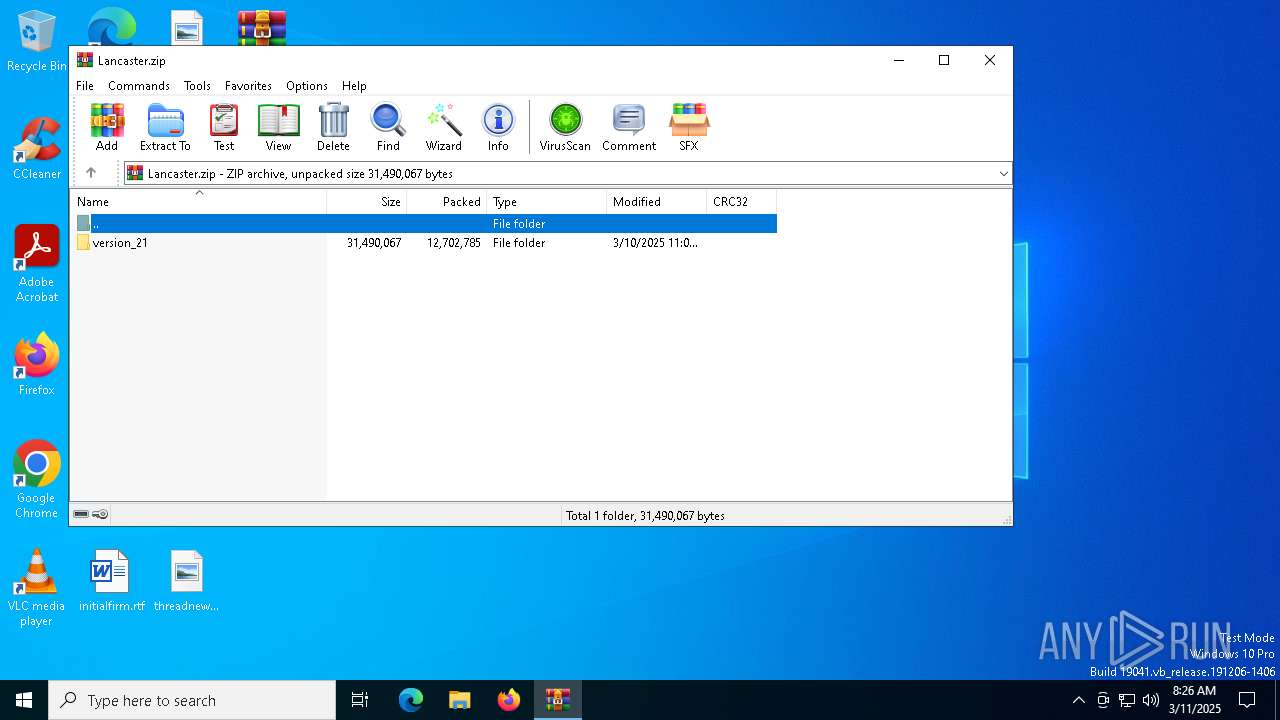
| File name: | Lancaster.zip |
| Full analysis: | https://app.any.run/tasks/c5fcab92-14a2-42d1-8458-267a006387f6 |
| Verdict: | Malicious activity |
| Analysis date: | March 11, 2025, 08:26:10 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v1.0 to extract, compression method=store |
| MD5: | 62DE72A8B5D947542B6C0A8F7273F074 |
| SHA1: | BC977DED3CEC56E689BB201CDB1550A39F68B2FA |
| SHA256: | 90A6D6B7AF9D74BB3B344F138EE56D572D60430B235D2609FF188BBCAEF836CB |
| SSDEEP: | 98304:z7e8YCPDFcSbFE6K+mALol9hhRLPEi1zj7kNxaCF1LxGeWZVOUzUChBZ8FDcZ7s8:ZkaPJ7mTGYgJegd4UaaA/ |
MALICIOUS
GENERIC has been found (auto)
- WinRAR.exe (PID: 6872)
SUSPICIOUS
Reads security settings of Internet Explorer
- WinRAR.exe (PID: 6872)
Executing commands from a ".bat" file
- WinRAR.exe (PID: 6872)
Starts CMD.EXE for commands execution
- WinRAR.exe (PID: 6872)
INFO
The sample compiled with english language support
- WinRAR.exe (PID: 6872)
Reads the computer name
- MpCmdRun.exe (PID: 2268)
Checks supported languages
- MpCmdRun.exe (PID: 2268)
Create files in a temporary directory
- MpCmdRun.exe (PID: 2268)
Checks proxy server information
- slui.exe (PID: 660)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 6872)
Reads the software policy settings
- slui.exe (PID: 660)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 10 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | None |
| ZipModifyDate: | 2025:03:10 19:02:46 |
| ZipCRC: | 0x00000000 |
| ZipCompressedSize: | - |
| ZipUncompressedSize: | - |
| ZipFileName: | version_21/ |
Total processes
127
Monitored processes
5
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 660 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 960 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2096 | C:\WINDOWS\system32\cmd.exe /c ""C:\Users\admin\AppData\Local\Temp\Rar$VR6872.46150\Rar$Scan67786.bat" " | C:\Windows\System32\cmd.exe | — | WinRAR.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2268 | "C:\Program Files\Windows Defender\MpCmdRun.exe" -Scan -ScanType 3 -File "C:\Users\admin\AppData\Local\Temp\Rar$VR6872.46150" | C:\Program Files\Windows Defender\MpCmdRun.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Malware Protection Command Line Utility Exit code: 2 Version: 4.18.1909.6 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6872 | "C:\Program Files\WinRAR\WinRAR.exe" C:\Users\admin\Desktop\Lancaster.zip | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Version: 5.91.0 Modules
| |||||||||||||||
Total events
4 930
Read events
4 920
Write events
10
Delete events
0
Modification events
| (PID) Process: | (6872) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (6872) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (6872) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (6872) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\Lancaster.zip | |||
| (PID) Process: | (6872) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (6872) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (6872) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (6872) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (6872) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList |
| Operation: | write | Name: | ArcSort |
Value: 32 | |||
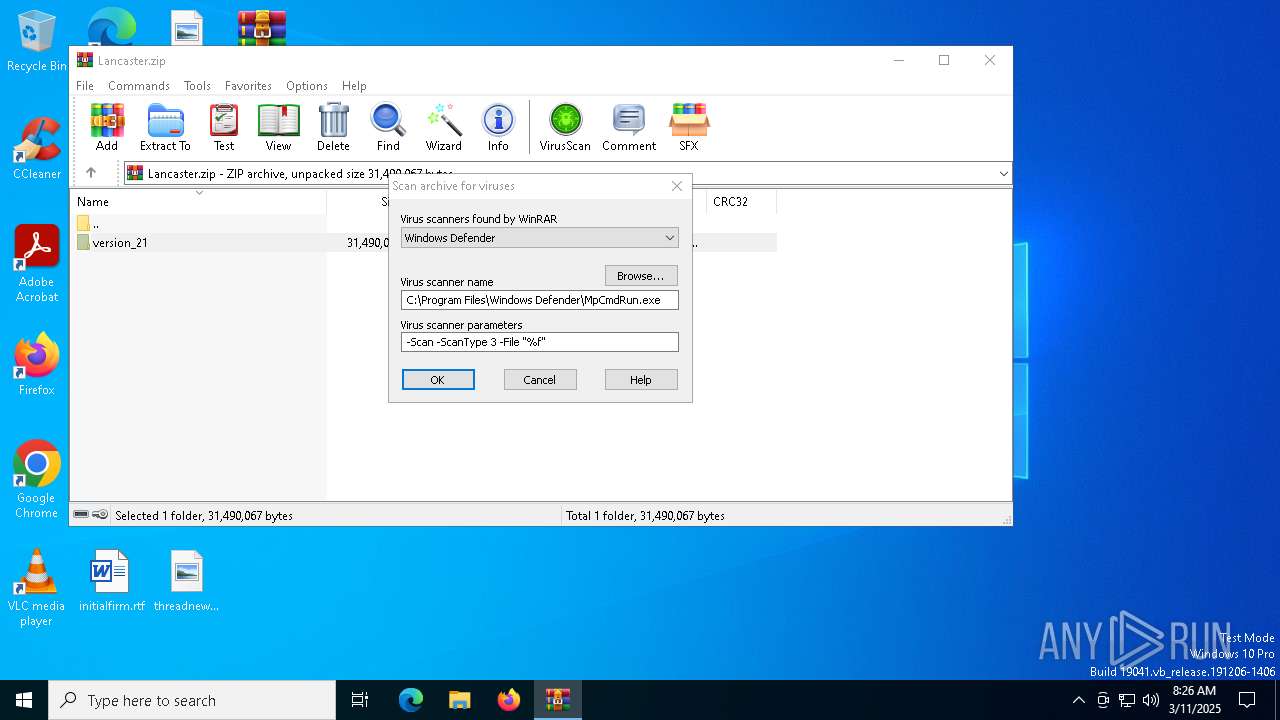
| (PID) Process: | (6872) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\VirusScan |
| Operation: | write | Name: | DefScanner |
Value: Windows Defender | |||
Executable files
3
Suspicious files
3
Text files
1
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6872 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$VR6872.46150\Lancaster.zip\version_21\cc32290mt.dll | executable | |
MD5:CAA0894A9B84FEC58881E06F93247B90 | SHA256:4E8DF175D47501EF372B599141DA743A3AA1CBB51F6055C7E1888244FC849FF4 | |||
| 6872 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$VR6872.46150\Lancaster.zip\version_21\protolanguage.php | binary | |
MD5:A2F83841FDA7B729B98BDA66C8627F3C | SHA256:1D8768C931E0C7AB9B1FD7A9269AA021204F93EE29259E7EA84742E5D6411DB4 | |||
| 6872 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$VR6872.46150\Lancaster.zip\version_21\legatee.vhd | binary | |
MD5:010E4EC745ADB44AACAB4ED624A99771 | SHA256:157CE0AFE946F4DA14880498629B239DE9E4FA817FF348DC26EA77B72069A68D | |||
| 6872 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$VR6872.46150\Lancaster.zip\version_21\borlndmm.dll | executable | |
MD5:2455C75C25687F2E363F0DBEF000DAF3 | SHA256:C36C66CFFEF5471D58CD81D61C9D799303FB44ABC784FC75FBCC2B5C6C44AA3A | |||
| 6872 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$VR6872.46150\Lancaster.zip\version_21\zkwindow.exe | executable | |
MD5:950F3BEBB7563EE8354B21EF9CBEA4A2 | SHA256:8F4F53BC02348A549F3437444AACEC43EAE5F90875EA3C5EC96600BA1CB4A061 | |||
| 2268 | MpCmdRun.exe | C:\Users\admin\AppData\Local\Temp\MpCmdRun.log | binary | |
MD5:F5BB4635C869D7CD187952B2F529D580 | SHA256:01EE99426892C9A51687676188BB2FA644612AC76DD863A5EA8B2D1473E98ECF | |||
| 6872 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$VR6872.46150\Rar$Scan67786.bat | text | |
MD5:20C75FDD64EE19A52F87D95DB792208E | SHA256:DA8B05EEAFA3A523F9DDB1A4A38C337267DE7847DFEA9B5BC202861FF49FCB3E | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
2
TCP/UDP connections
18
DNS requests
4
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | POST | 500 | 40.91.76.224:443 | https://activation-v2.sls.microsoft.com/SLActivateProduct/SLActivateProduct.asmx?configextension=Retail | unknown | xml | 512 b | whitelisted |
— | — | POST | 500 | 40.91.76.224:443 | https://activation-v2.sls.microsoft.com/SLActivateProduct/SLActivateProduct.asmx?configextension=Retail | unknown | xml | 512 b | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2104 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 192.168.100.255:138 | — | — | — | whitelisted |
— | — | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
2104 | svchost.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
616 | slui.exe | 20.83.72.98:443 | activation-v2.sls.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
660 | slui.exe | 20.83.72.98:443 | activation-v2.sls.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
activation-v2.sls.microsoft.com |
| whitelisted |