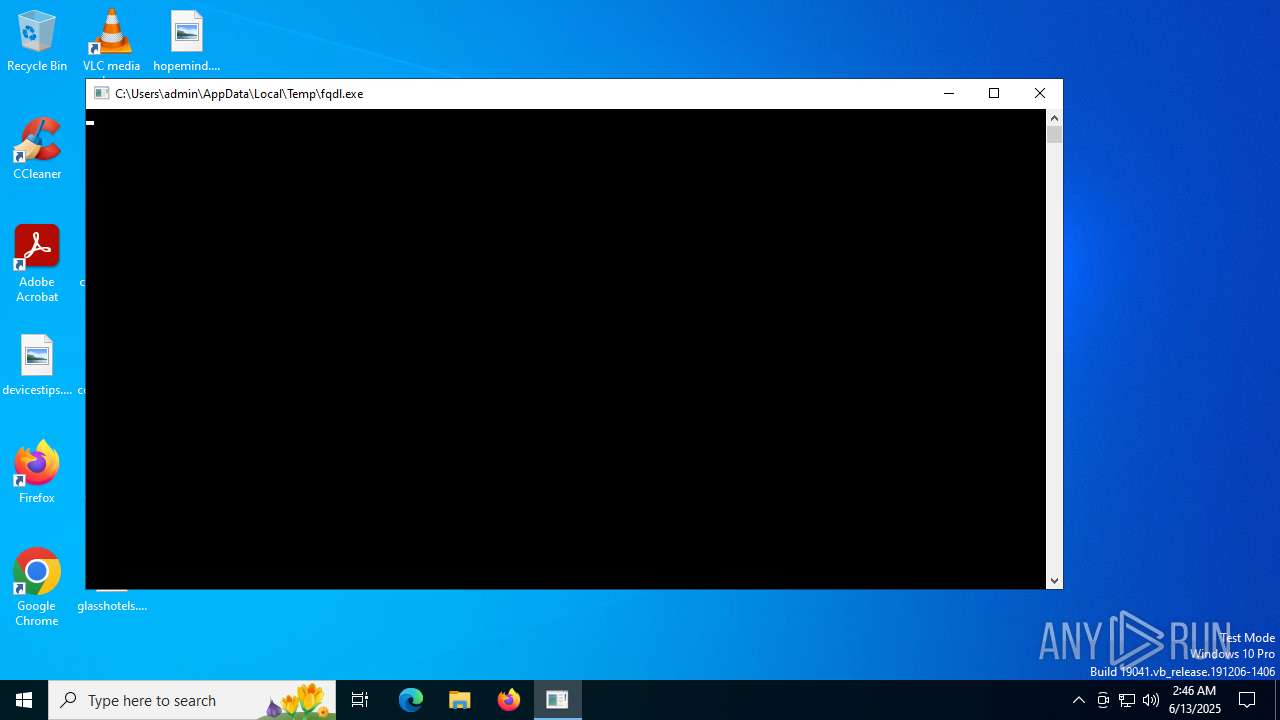
| File name: | fqdl.exe |
| Full analysis: | https://app.any.run/tasks/95d425ac-136a-4ac3-88c0-deb9dc390180 |
| Verdict: | Malicious activity |
| Analysis date: | June 13, 2025, 02:46:48 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (console) Intel 80386 Mono/.Net assembly, for MS Windows, 3 sections |
| MD5: | E3DAAF80AB14D57E0F468458225A5A65 |
| SHA1: | 5FBEB9B699F881D6EEA0DC39EDD89A2810E53E21 |
| SHA256: | 9095B3AB544E3430DBB4B11119E7CE8BACA45B38CA0DF742732C33EDA3AADBB4 |
| SSDEEP: | 48:Y3ELKj5VUu2LZa2XVJTf6NMDm3HWXSZzGAKGmbrHiBFgYbREm1m9t+nlYJKzmjFJ:X2cucE2rYzzYRriBJ2V87zzNt |
MALICIOUS
No malicious indicators.SUSPICIOUS
Executable content was dropped or overwritten
- fqdl.exe (PID: 2760)
- Clash for Windows.exe (PID: 3864)
Process drops legitimate windows executable
- fqdl.exe (PID: 2760)
Drops a system driver (possible attempt to evade defenses)
- fqdl.exe (PID: 2760)
Reads security settings of Internet Explorer
- fqdl.exe (PID: 2760)
Starts CMD.EXE for commands execution
- Clash for Windows.exe (PID: 3864)
Suspicious use of NETSH.EXE
- cmd.exe (PID: 6936)
- cmd.exe (PID: 1488)
Uses ROUTE.EXE to obtain the routing table information
- cmd.exe (PID: 5300)
Connects to unusual port
- clash-win64.exe (PID: 3580)
Application launched itself
- Clash for Windows.exe (PID: 1896)
INFO
Checks supported languages
- fqdl.exe (PID: 2760)
- Clash for Windows.exe (PID: 1896)
- Clash for Windows.exe (PID: 3876)
- Clash for Windows.exe (PID: 3864)
- clash-win64.exe (PID: 3580)
- Clash for Windows.exe (PID: 3756)
Reads the computer name
- fqdl.exe (PID: 2760)
- Clash for Windows.exe (PID: 3756)
- Clash for Windows.exe (PID: 3876)
- Clash for Windows.exe (PID: 3864)
- clash-win64.exe (PID: 3580)
- Clash for Windows.exe (PID: 1896)
Reads the machine GUID from the registry
- fqdl.exe (PID: 2760)
- Clash for Windows.exe (PID: 1896)
- clash-win64.exe (PID: 3580)
Disables trace logs
- fqdl.exe (PID: 2760)
- netsh.exe (PID: 3964)
- netsh.exe (PID: 2648)
Checks proxy server information
- fqdl.exe (PID: 2760)
- Clash for Windows.exe (PID: 1896)
Reads the software policy settings
- fqdl.exe (PID: 2760)
- Clash for Windows.exe (PID: 1896)
- clash-win64.exe (PID: 3580)
Create files in a temporary directory
- fqdl.exe (PID: 2760)
- Clash for Windows.exe (PID: 3864)
- Clash for Windows.exe (PID: 1896)
The sample compiled with english language support
- fqdl.exe (PID: 2760)
- Clash for Windows.exe (PID: 3864)
The sample compiled with chinese language support
- fqdl.exe (PID: 2760)
Process checks computer location settings
- fqdl.exe (PID: 2760)
- Clash for Windows.exe (PID: 3864)
- Clash for Windows.exe (PID: 1896)
Reads Environment values
- Clash for Windows.exe (PID: 3864)
Creates files or folders in the user directory
- Clash for Windows.exe (PID: 3876)
- Clash for Windows.exe (PID: 3864)
- Clash for Windows.exe (PID: 1896)
Reads product name
- Clash for Windows.exe (PID: 3864)
Prints a route via ROUTE.EXE
- ROUTE.EXE (PID: 6504)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Generic CIL Executable (.NET, Mono, etc.) (82.9) |
|---|---|---|
| .dll | | | Win32 Dynamic Link Library (generic) (7.4) |
| .exe | | | Win32 Executable (generic) (5.1) |
| .exe | | | Generic Win/DOS Executable (2.2) |
| .exe | | | DOS Executable Generic (2.2) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2078:10:02 02:55:04+00:00 |
| ImageFileCharacteristics: | Executable, Large address aware |
| PEType: | PE32 |
| LinkerVersion: | 48 |
| CodeSize: | 3072 |
| InitializedDataSize: | 2048 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x2a16 |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 6 |
| Subsystem: | Windows command line |
| FileVersionNumber: | 1.0.0.0 |
| ProductVersionNumber: | 1.0.0.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | Neutral |
| CharacterSet: | Unicode |
| Comments: | - |
| CompanyName: | - |
| FileDescription: | fqdl |
| FileVersion: | 1.0.0.0 |
| InternalName: | fqdl.exe |
| LegalCopyright: | Copyright © 2025 |
| LegalTrademarks: | - |
| OriginalFileName: | fqdl.exe |
| ProductName: | fqdl |
| ProductVersion: | 1.0.0.0 |
| AssemblyVersion: | 1.0.0.0 |
Total processes
154
Monitored processes
18
Malicious processes
4
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1488 | C:\WINDOWS\system32\cmd.exe /d /s /c "netsh interface show interface" | C:\Windows\System32\cmd.exe | — | Clash for Windows.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1564 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1812 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
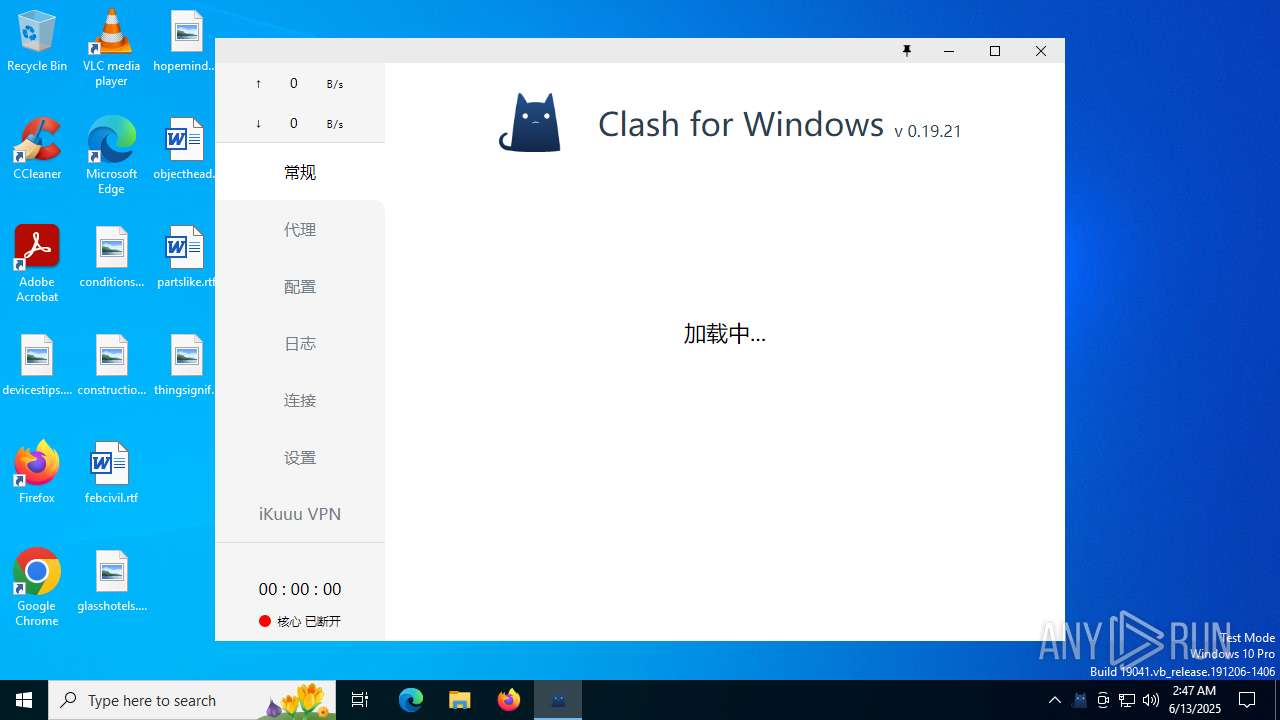
| 1896 | "C:\Users\admin\AppData\Local\Temp\Clash.for.Windows-0.19.21-ikuuu\Clash for Windows.exe" | C:\Users\admin\AppData\Local\Temp\Clash.for.Windows-0.19.21-ikuuu\Clash for Windows.exe | — | fqdl.exe | |||||||||||
User: admin Company: Fndroid Integrity Level: MEDIUM Description: Clash for Windows Version: 0.19.21 Modules
| |||||||||||||||
| 2648 | netsh interface show interface | C:\Windows\System32\netsh.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Network Command Shell Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2760 | "C:\Users\admin\AppData\Local\Temp\fqdl.exe" | C:\Users\admin\AppData\Local\Temp\fqdl.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Description: fqdl Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
| 2864 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2976 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3580 | clash-win64.exe -d C:\Users\admin\AppData\Local\Temp\Clash.for.Windows-0.19.21-ikuuu\data | C:\Users\admin\AppData\Local\Temp\Clash.for.Windows-0.19.21-ikuuu\resources\static\files\win\x64\clash-win64.exe | Clash for Windows.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Modules
| |||||||||||||||
| 3756 | "C:\Users\admin\AppData\Local\Temp\Clash.for.Windows-0.19.21-ikuuu\Clash for Windows.exe" --type=gpu-process --user-data-dir="C:\Users\admin\AppData\Roaming\clash_win" --gpu-preferences=UAAAAAAAAADgAAAYAAAAAAAAAAAAAAAAAABgAAAAAAAwAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAEgAAAAAAAAASAAAAAAAAAAYAAAAAgAAABAAAAAAAAAAGAAAAAAAAAAQAAAAAAAAAAAAAAAOAAAAEAAAAAAAAAABAAAADgAAAAgAAAAAAAAACAAAAAAAAAA= --use-gl=angle --use-angle=swiftshader-webgl --mojo-platform-channel-handle=1592 --field-trial-handle=1736,i,5218533864549030537,8823376388024340098,131072 --disable-features=OutOfBlinkCors,SpareRendererForSitePerProcess,WinRetrieveSuggestionsOnlyOnDemand /prefetch:2 | C:\Users\admin\AppData\Local\Temp\Clash.for.Windows-0.19.21-ikuuu\Clash for Windows.exe | — | Clash for Windows.exe | |||||||||||
User: admin Company: Fndroid Integrity Level: LOW Description: Clash for Windows Version: 0.19.21 Modules
| |||||||||||||||
Total events
12 050
Read events
12 017
Write events
15
Delete events
18
Modification events
| (PID) Process: | (2760) fqdl.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\fqdl_RASAPI32 |
| Operation: | write | Name: | EnableFileTracing |
Value: 0 | |||
| (PID) Process: | (2760) fqdl.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\fqdl_RASAPI32 |
| Operation: | write | Name: | EnableAutoFileTracing |
Value: 0 | |||
| (PID) Process: | (2760) fqdl.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\fqdl_RASAPI32 |
| Operation: | write | Name: | EnableConsoleTracing |
Value: 0 | |||
| (PID) Process: | (2760) fqdl.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\fqdl_RASAPI32 |
| Operation: | write | Name: | FileTracingMask |
Value: | |||
| (PID) Process: | (2760) fqdl.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\fqdl_RASAPI32 |
| Operation: | write | Name: | ConsoleTracingMask |
Value: | |||
| (PID) Process: | (2760) fqdl.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\fqdl_RASAPI32 |
| Operation: | write | Name: | MaxFileSize |
Value: 1048576 | |||
| (PID) Process: | (2760) fqdl.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\fqdl_RASAPI32 |
| Operation: | write | Name: | FileDirectory |
Value: %windir%\tracing | |||
| (PID) Process: | (2760) fqdl.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\fqdl_RASMANCS |
| Operation: | write | Name: | EnableFileTracing |
Value: 0 | |||
| (PID) Process: | (2760) fqdl.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\fqdl_RASMANCS |
| Operation: | write | Name: | EnableAutoFileTracing |
Value: 0 | |||
| (PID) Process: | (2760) fqdl.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\fqdl_RASMANCS |
| Operation: | write | Name: | EnableConsoleTracing |
Value: 0 | |||
Executable files
22
Suspicious files
40
Text files
63
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2760 | fqdl.exe | C:\Users\admin\AppData\Local\Temp\1.zip | — | |
MD5:— | SHA256:— | |||
| 2760 | fqdl.exe | C:\Users\admin\AppData\Local\Temp\Clash.for.Windows-0.19.21-ikuuu\Clash for Windows.exe | — | |
MD5:— | SHA256:— | |||
| 2760 | fqdl.exe | C:\Users\admin\AppData\Local\Temp\Clash.for.Windows-0.19.21-ikuuu\data\profiles\1665194423995.yml | text | |
MD5:4C4EEDD6B2759D039CFE59560C7788BB | SHA256:D847B6DF6DEB4040ABCB2F1EDDBE5790C3CD4A8B0568EB381FEAA9C37DAC773E | |||
| 2760 | fqdl.exe | C:\Users\admin\AppData\Local\Temp\Clash.for.Windows-0.19.21-ikuuu\chrome_100_percent.pak | binary | |
MD5:237CA1BE894F5E09FD1CCB934229C33B | SHA256:F14362449E2A7C940C095EDA9C41AAD5F1E0B1A1B21D1DC911558291C0C36DD2 | |||
| 2760 | fqdl.exe | C:\Users\admin\AppData\Local\Temp\Clash.for.Windows-0.19.21-ikuuu\chrome_200_percent.pak | binary | |
MD5:7059AF03603F93898F66981FEB737064 | SHA256:04D699CFC36565FA9C06206BA1C0C51474612C8FE481C6FD1807197DC70661E6 | |||
| 2760 | fqdl.exe | C:\Users\admin\AppData\Local\Temp\Clash.for.Windows-0.19.21-ikuuu\d3dcompiler_47.dll | executable | |
MD5:7641E39B7DA4077084D2AFE7C31032E0 | SHA256:44422E6936DC72B7AC5ED16BB8BCAE164B7554513E52EFB66A3E942CEC328A47 | |||
| 2760 | fqdl.exe | C:\Users\admin\AppData\Local\Temp\Clash.for.Windows-0.19.21-ikuuu\data\cfw-settings.yaml | text | |
MD5:B279F8C018C019F309370D32431EAD30 | SHA256:AE38A5ADA646D985E103A512D6676A794903A91E633EC0EEBF8CD97996DADE45 | |||
| 2760 | fqdl.exe | C:\Users\admin\AppData\Local\Temp\Clash.for.Windows-0.19.21-ikuuu\data\profiles\1665196564006.yml | text | |
MD5:D8EBAD139E4C4AA0FBA3EFE269413EFB | SHA256:F3DEF133A3EDE49A490804BEB9287497FA7188075F82349DD7EDD40374234FFF | |||
| 2760 | fqdl.exe | C:\Users\admin\AppData\Local\Temp\Clash.for.Windows-0.19.21-ikuuu\data\config.yaml | text | |
MD5:FAA602C964BEAA6D94F1A1C98E118C3F | SHA256:EEEFFE36A7454E8BEB38E2D896D2A389D7A57951AF5C8E4354B6C8E57B92DAD2 | |||
| 2760 | fqdl.exe | C:\Users\admin\AppData\Local\Temp\Clash.for.Windows-0.19.21-ikuuu\data\Country.mmdb | binary | |
MD5:601AA80A0A9C4EEAD525B5E5E19BB2E7 | SHA256:5725EDA4F16F731AE444AF0BE0BC7E5ECA8BAA196523D2151FAE47B65671D646 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
5
TCP/UDP connections
128
DNS requests
187
Threats
1
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2764 | svchost.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
1268 | svchost.exe | GET | 200 | 2.16.168.124:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
1268 | svchost.exe | GET | 200 | 23.219.150.101:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
3788 | SIHClient.exe | GET | 200 | 23.219.150.101:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
3788 | SIHClient.exe | GET | 200 | 23.219.150.101:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
5944 | MoUsoCoreWorker.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4156 | RUXIMICS.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
1268 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
2760 | fqdl.exe | 140.82.121.4:443 | github.com | GITHUB | US | whitelisted |
2760 | fqdl.exe | 185.199.108.133:443 | objects.githubusercontent.com | FASTLY | US | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
2336 | svchost.exe | 172.211.123.250:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
2764 | svchost.exe | 20.190.159.130:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
2764 | svchost.exe | 2.23.77.188:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
github.com |
| whitelisted |
objects.githubusercontent.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
sub.xeton.dev |
| unknown |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2200 | svchost.exe | Not Suspicious Traffic | INFO [ANY.RUN] Cloudflare Network Error Logging (NEL) |