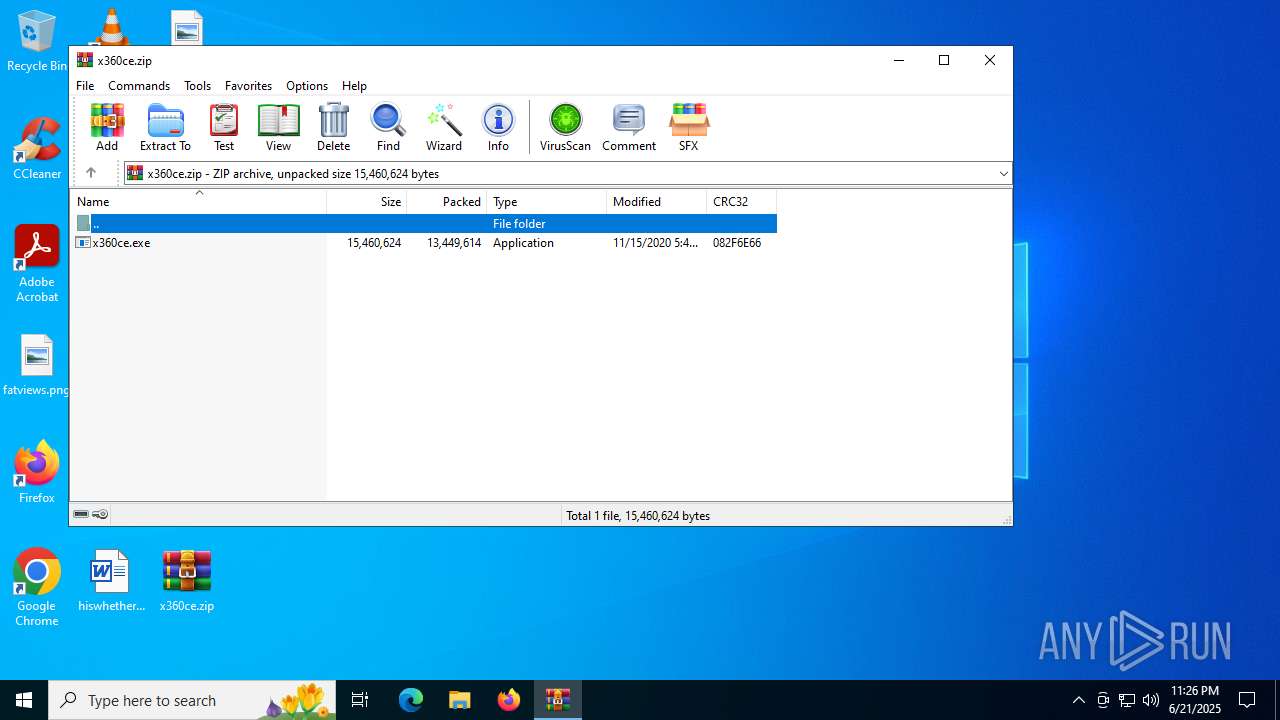
| File name: | x360ce.zip |
| Full analysis: | https://app.any.run/tasks/c7c590f2-d6f1-4d4d-b145-e9a55b1b7b4a |
| Verdict: | Malicious activity |
| Analysis date: | June 21, 2025, 23:26:01 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract, compression method=deflate |
| MD5: | 425B3E1E66C3CE08449F229C716BEEDF |
| SHA1: | 0AAAA0795D232E41443AD1B298DE82F55F75D704 |
| SHA256: | 908BABF5E35F2C31922744E1BF78990F9C1EDBC5F7C1CE950812E920E60DA1E9 |
| SSDEEP: | 393216:npWZYcR4z9GHzAklmHqaps9I4RO1PT/+nRr10:pWZqzszUHi9APTWnt10 |
MALICIOUS
Generic archive extractor
- WinRAR.exe (PID: 6124)
SUSPICIOUS
Searches for installed software
- x360ce.exe (PID: 4800)
Executable content was dropped or overwritten
- x360ce.exe (PID: 4800)
INFO
Manual execution by a user
- x360ce.exe (PID: 4800)
Checks supported languages
- x360ce.exe (PID: 4800)
Reads the computer name
- x360ce.exe (PID: 4800)
Reads the machine GUID from the registry
- x360ce.exe (PID: 4800)
Creates files in the program directory
- x360ce.exe (PID: 4800)
Reads the software policy settings
- slui.exe (PID: 3288)
Checks proxy server information
- slui.exe (PID: 3288)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 6124)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2020:11:15 17:46:06 |
| ZipCRC: | 0x082f6e66 |
| ZipCompressedSize: | 13449614 |
| ZipUncompressedSize: | 15460624 |
| ZipFileName: | x360ce.exe |
Total processes
136
Monitored processes
3
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 3288 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4800 | "C:\Users\admin\Desktop\x360ce.exe" | C:\Users\admin\Desktop\x360ce.exe | explorer.exe | ||||||||||||
User: admin Company: Jocys.com Integrity Level: MEDIUM Description: Jocys.com X360 Controller Emulator Version: 4.17.15.0 Modules
| |||||||||||||||
| 6124 | "C:\Program Files\WinRAR\WinRAR.exe" C:\Users\admin\Desktop\x360ce.zip | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Version: 5.91.0 Modules
| |||||||||||||||
Total events
15 870
Read events
15 854
Write events
16
Delete events
0
Modification events
| (PID) Process: | (6124) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (6124) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (6124) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (6124) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\x360ce.zip | |||
| (PID) Process: | (6124) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (6124) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (6124) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (6124) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (4800) x360ce.exe | Key: | HKEY_CURRENT_USER\System\CurrentControlSet\Control\MediaProperties\PrivateProperties\DirectInput\VID_0627&PID_0001\Calibration\0 |
| Operation: | write | Name: | GUID |
Value: A0DA6622F74EF0118001444553540000 | |||
| (PID) Process: | (4800) x360ce.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\DirectInput\X360CE.EXE5FB168DB00EBE910 |
| Operation: | write | Name: | Name |
Value: X360CE.EXE | |||
Executable files
2
Suspicious files
0
Text files
12
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 4800 | x360ce.exe | C:\ProgramData\X360CE\Settings\x360ce.UserSettings.xml | text | |
MD5:9D099E80ECF73BE1610855B3A84EC8B5 | SHA256:A30B3506B24AD894638E6995FD7E0D257F4A5378B7F8105298D56C996EAD9493 | |||
| 4800 | x360ce.exe | C:\ProgramData\X360CE\Settings\x360ce.Options.xml | text | |
MD5:0345954272C3992AA160F10A89DAF02C | SHA256:758CFD9446A8850B43C974344C1B464B77D2A825D2771D65FBDDEB040B0EBA14 | |||
| 4800 | x360ce.exe | C:\ProgramData\X360CE\Settings\x360ce.UserGames.xml | text | |
MD5:12C2B4CDF79C0EA01511289EB1231FDB | SHA256:6E447FC5871E1530E248BFF98599DEDAF243410E8F3892D8D4B5B5E16BE14AAA | |||
| 4800 | x360ce.exe | C:\ProgramData\X360CE\Settings\x360ce.UserMacros.xml | text | |
MD5:8737567F5B4A25C6F1FD0F37803C5E1F | SHA256:6BEB7E262E173440ED8B59EEB1B376D8B6D4DFF15CE01E4979221202ADE75A9D | |||
| 4800 | x360ce.exe | C:\ProgramData\X360CE\Settings\x360ce.Programs.xml | text | |
MD5:FF3EE9530247EFA888D7A24611B1BDCD | SHA256:57C26E543061F382AA15F2621C0891BD7428424CA49D6155B0257CE2AE83277C | |||
| 4800 | x360ce.exe | C:\ProgramData\X360CE\Settings\x360ce.UserDevices.xml | text | |
MD5:C59E2E26ABA4EB3B1C699838DD452276 | SHA256:613E34FD780F73E981004D0B3AF9D6F39C86438B3B665DFFC230A9F852A206FC | |||
| 4800 | x360ce.exe | C:\ProgramData\X360CE\Settings\x360ce.PadSettings.xml | text | |
MD5:518B7E8043729212AEF492310F8CF421 | SHA256:9AA4B9AC4E8A18BB2C9ECE24E007171B19999CBAC70A6567D171811599010732 | |||
| 4800 | x360ce.exe | C:\ProgramData\X360CE\Settings\x360ce.Summaries.xml | text | |
MD5:86EF143234C7C15066AE67732A42A257 | SHA256:352789A74CB6D9187BFEDED112F8A780E9A5F59D0BD713F896A9AF736C4CCA92 | |||
| 4800 | x360ce.exe | C:\ProgramData\X360CE\Settings\x360ce.Presets.xml | text | |
MD5:E22EF49BE69AF14AAA588938A80FFB3C | SHA256:D874CCA7E90E93FBD217C3924E5F01FE7DD5B92D83456C0B86284AB1693B923F | |||
| 4800 | x360ce.exe | C:\ProgramData\X360CE\Settings\x360ce.XInputMask.xml | text | |
MD5:2736469BA90BDF85E8C04C778114A656 | SHA256:FBB85DD2F408CD3D442D2511A41B0032524E31BA5F3166589E860A698BF5D2A0 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
31
TCP/UDP connections
42
DNS requests
19
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5944 | MoUsoCoreWorker.exe | GET | 200 | 23.53.40.178:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
1268 | svchost.exe | GET | 200 | 23.53.40.178:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
472 | RUXIMICS.exe | GET | 200 | 23.53.40.178:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
5944 | MoUsoCoreWorker.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
472 | RUXIMICS.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
1268 | svchost.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
— | — | POST | 200 | 20.190.159.23:443 | https://login.live.com/RST2.srf | unknown | xml | 1.24 Kb | whitelisted |
— | — | POST | 400 | 20.190.159.23:443 | https://login.live.com/ppsecure/deviceaddcredential.srf | unknown | text | 203 b | whitelisted |
— | — | POST | 200 | 40.126.31.129:443 | https://login.live.com/RST2.srf | unknown | xml | 11.1 Kb | whitelisted |
— | — | POST | 200 | 40.126.31.128:443 | https://login.live.com/ppsecure/deviceaddcredential.srf | unknown | text | 16.7 Kb | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
5944 | MoUsoCoreWorker.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
1268 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
472 | RUXIMICS.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
5944 | MoUsoCoreWorker.exe | 23.53.40.178:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
1268 | svchost.exe | 23.53.40.178:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
472 | RUXIMICS.exe | 23.53.40.178:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
5944 | MoUsoCoreWorker.exe | 23.35.229.160:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
1268 | svchost.exe | 23.35.229.160:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
nexusrules.officeapps.live.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
activation-v2.sls.microsoft.com |
| whitelisted |
Threats
Process | Message |
|---|---|
x360ce.exe | x360ce.exe Information: 0 : |
x360ce.exe | InitializeServices
|
x360ce.exe | x360ce.exe Information: 0 : |
x360ce.exe | InitializeCloudClient
|
x360ce.exe | Stopping remote server... |
x360ce.exe | already stopped.
|