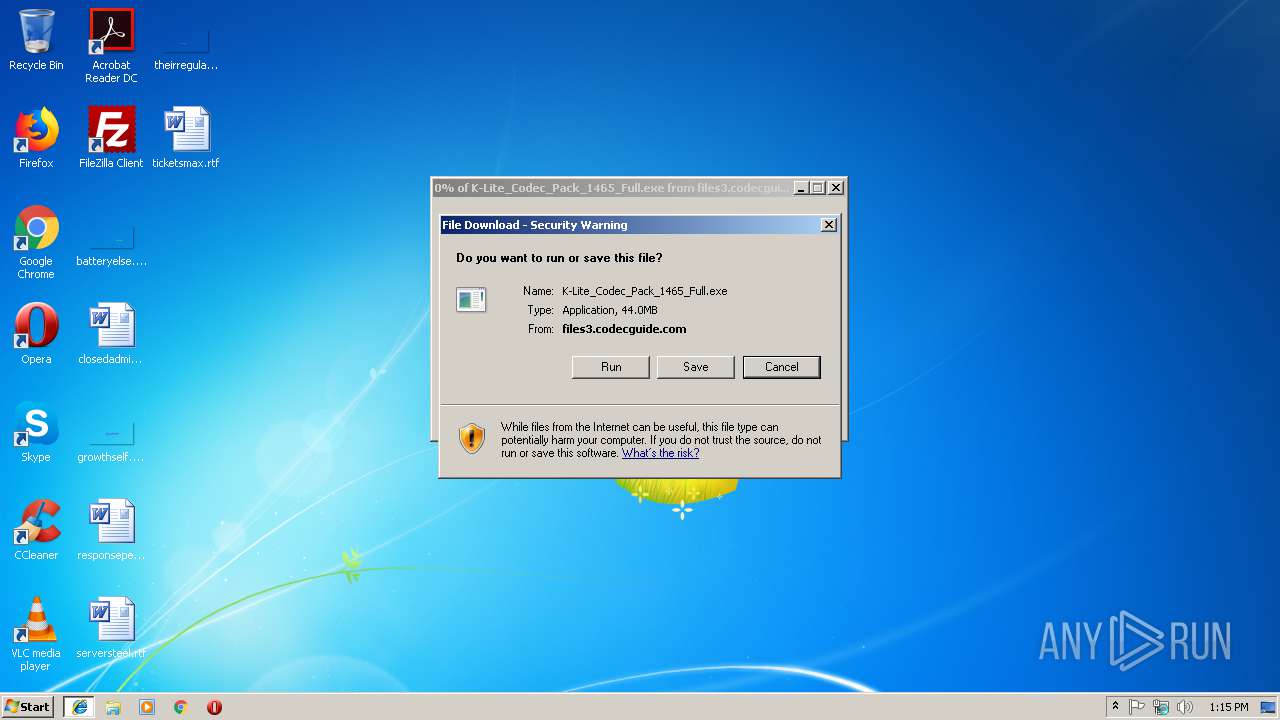
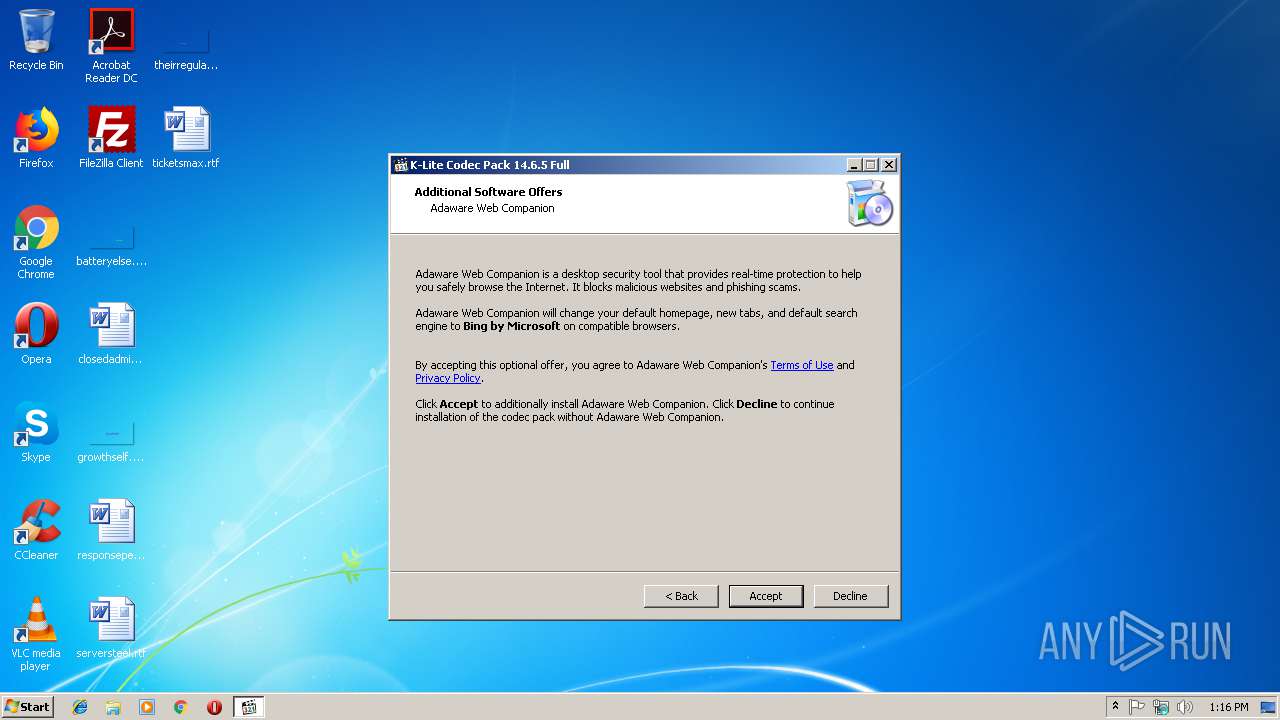
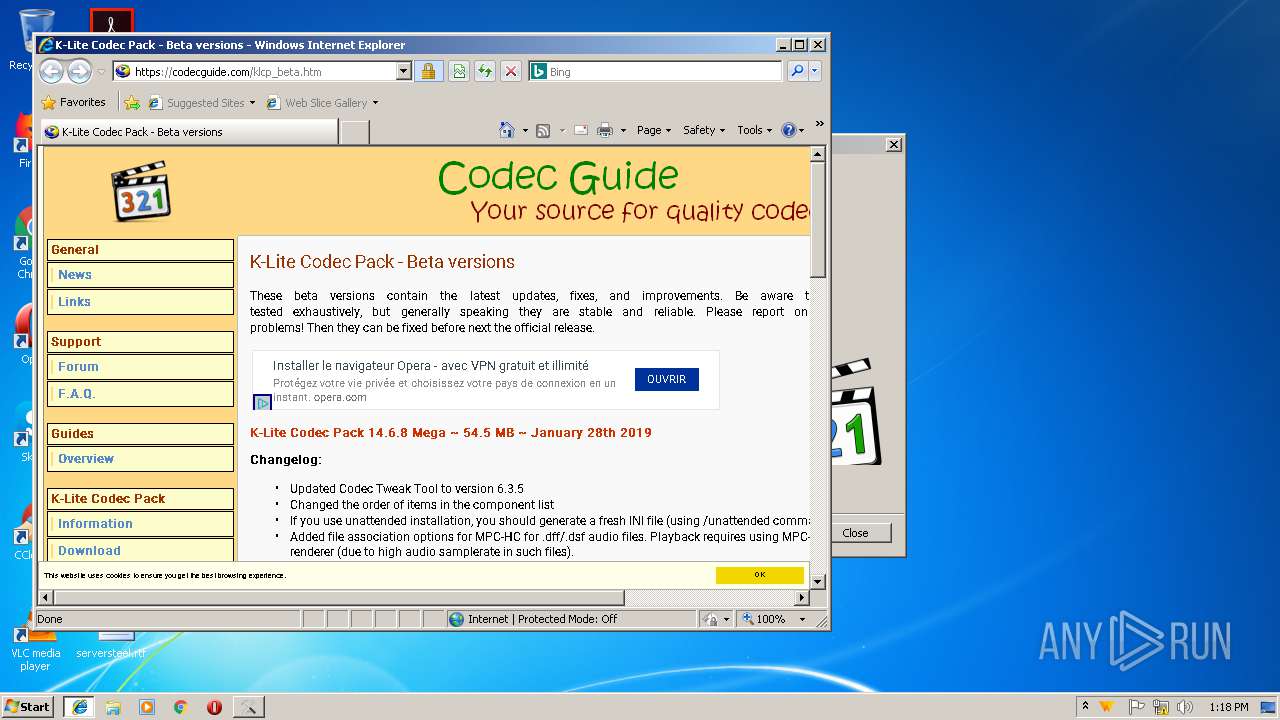
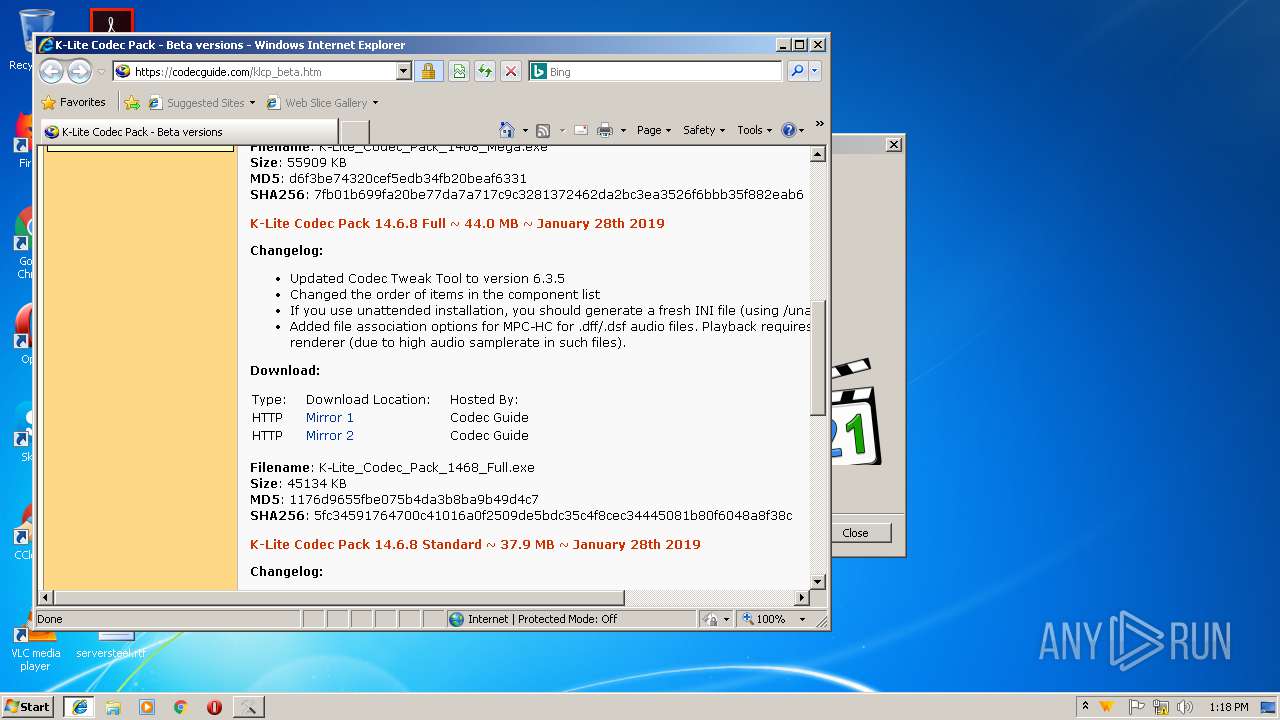
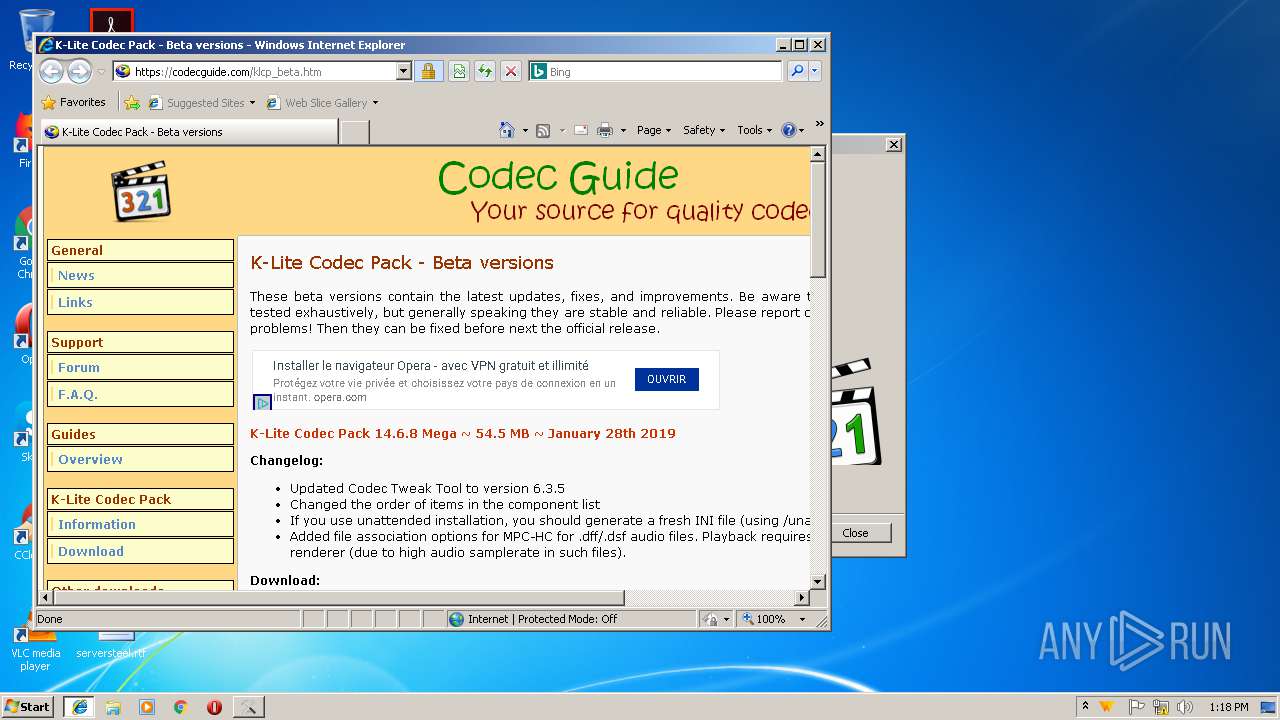
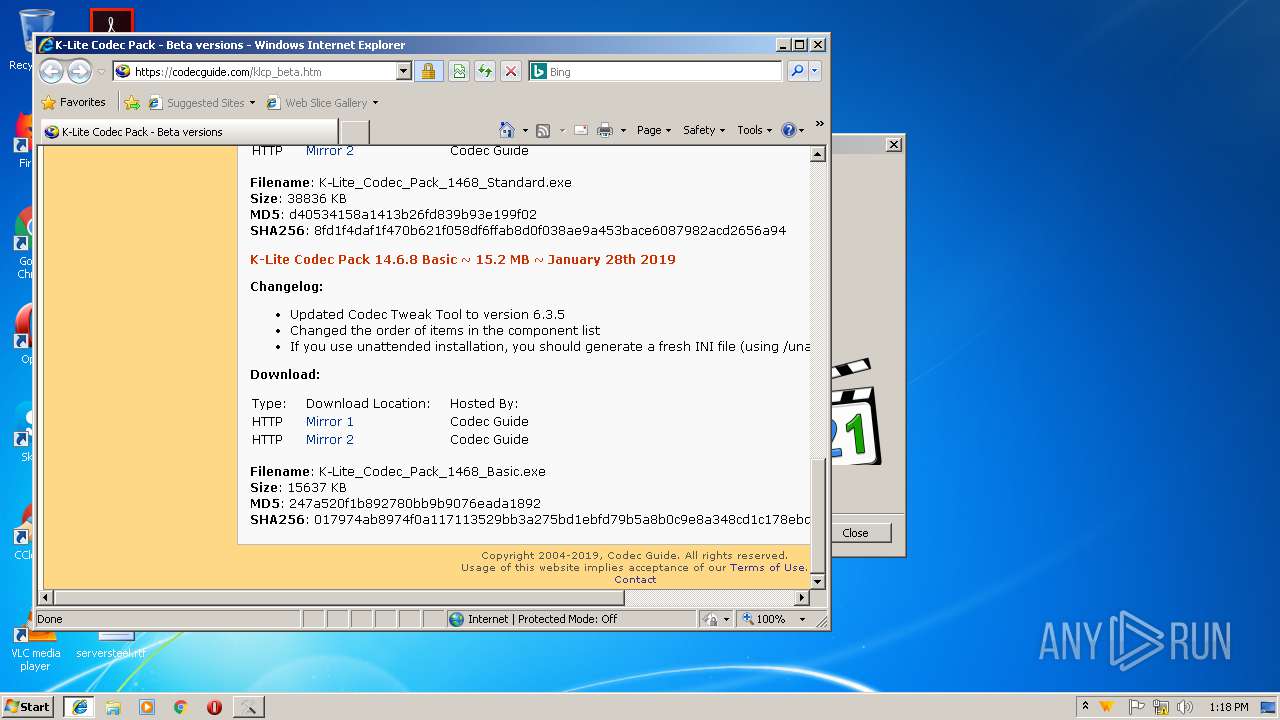
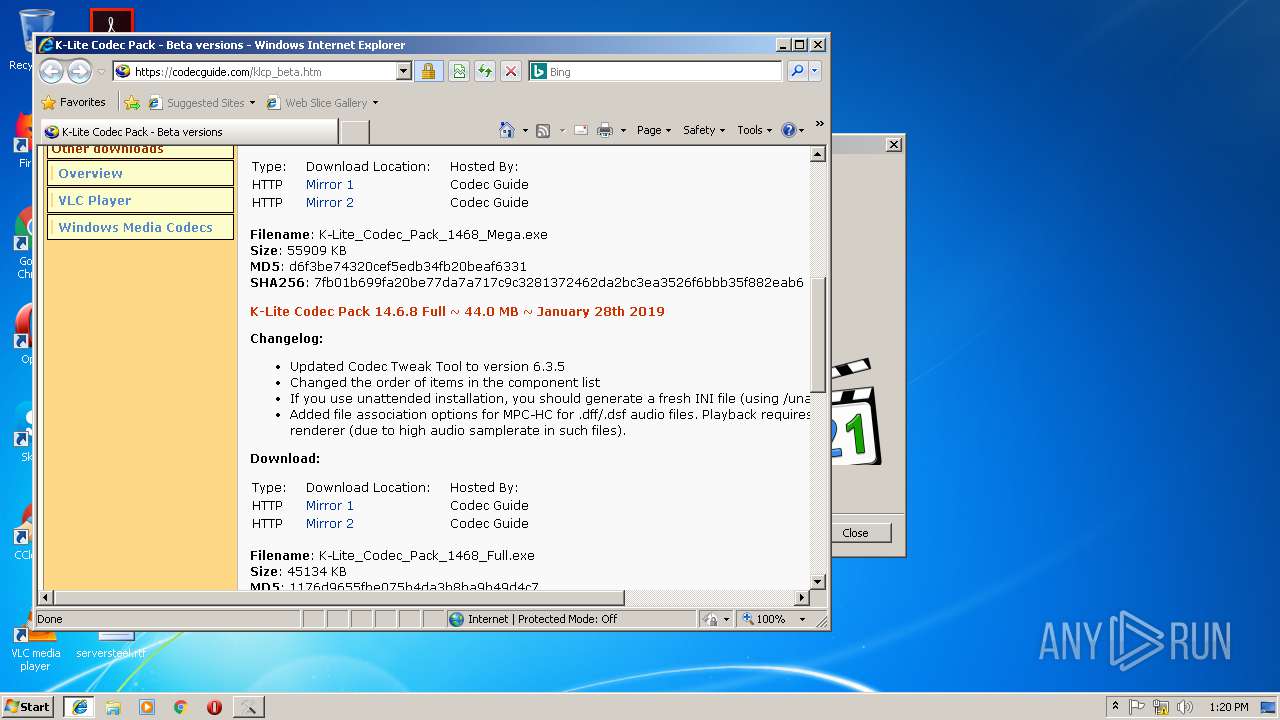
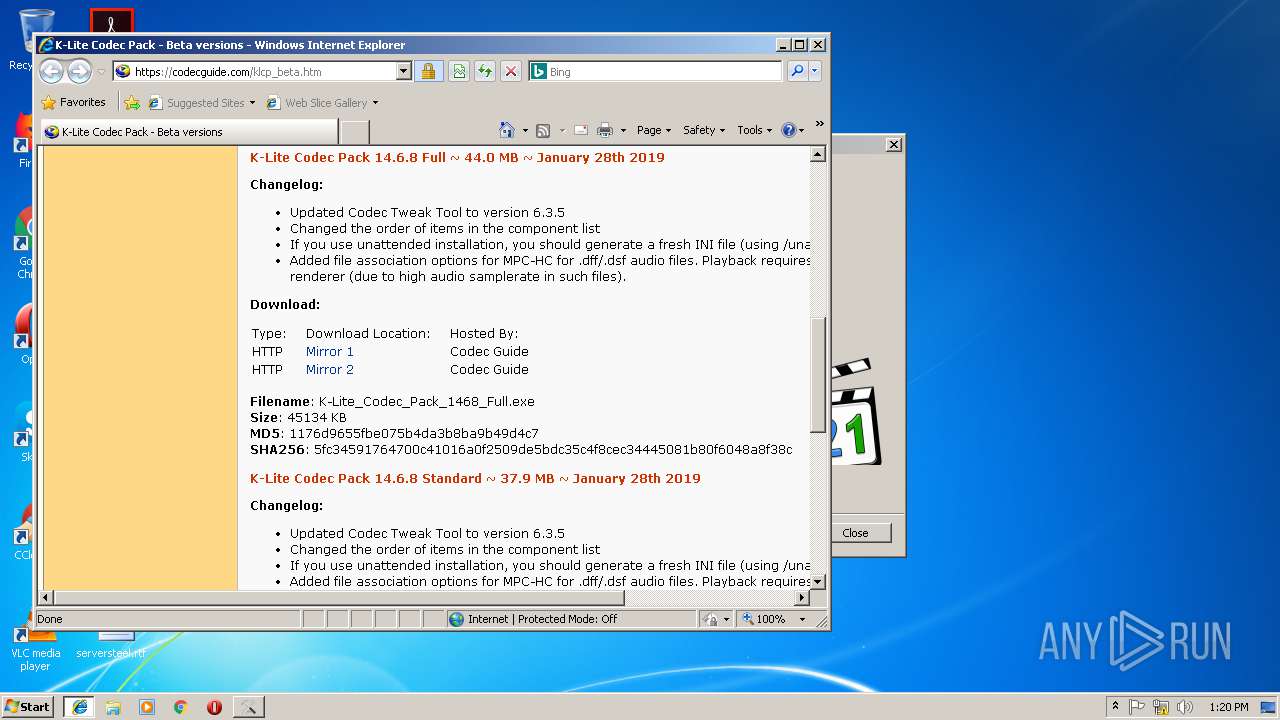
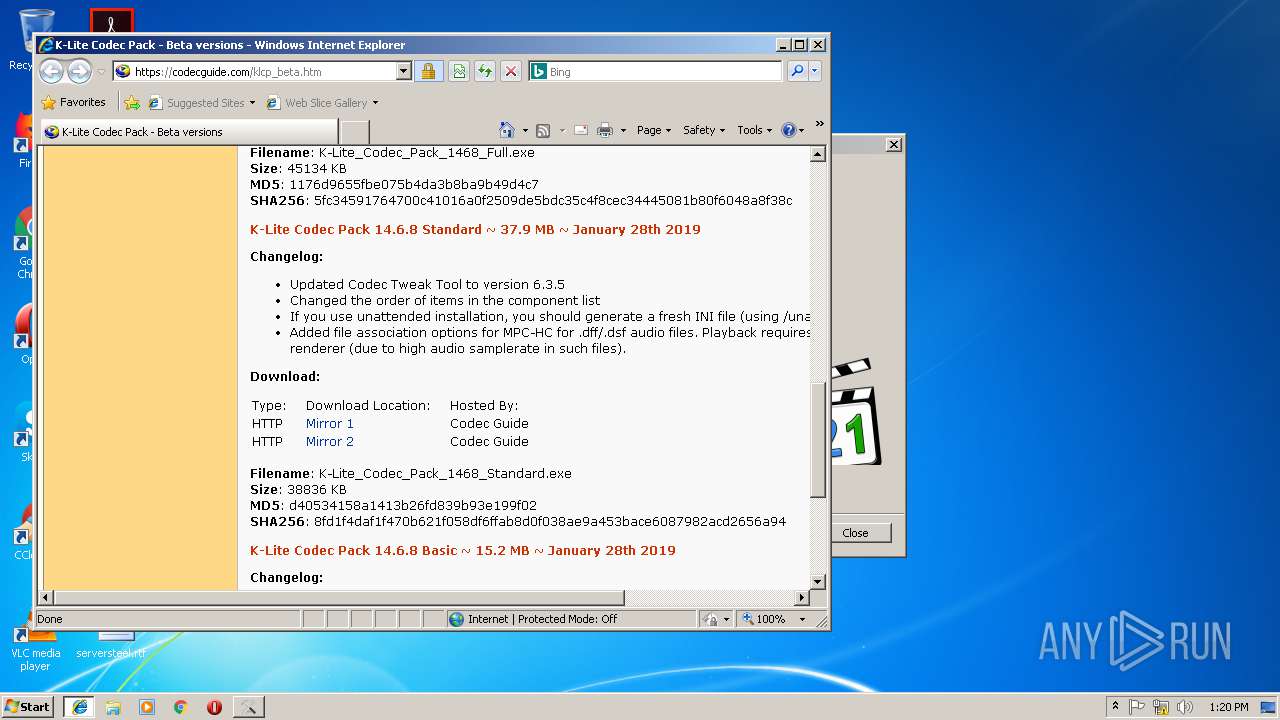
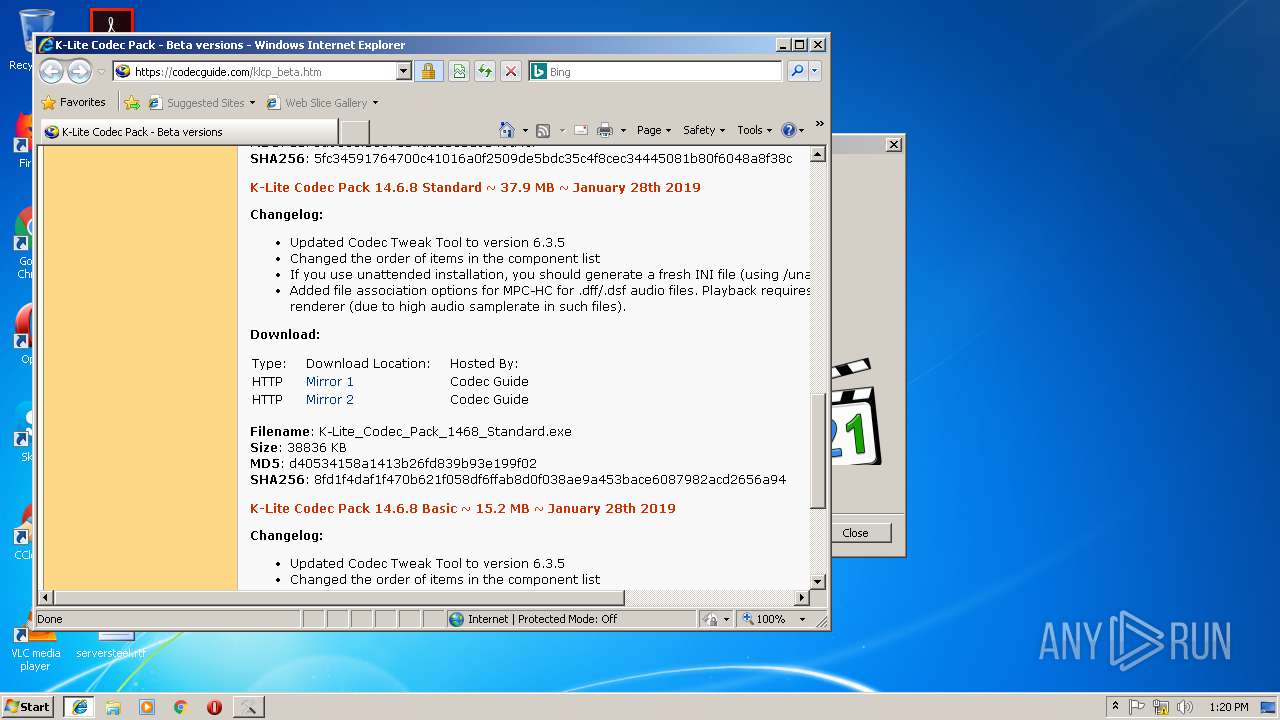
| URL: | http://files3.codecguide.com/K-Lite_Codec_Pack_1465_Full.exe |
| Full analysis: | https://app.any.run/tasks/2da81d23-fdb2-4621-8ebd-4a2843fb50ec |
| Verdict: | Malicious activity |
| Threats: | A loader is malicious software that infiltrates devices to deliver malicious payloads. This malware is capable of infecting victims’ computers, analyzing their system information, and installing other types of threats, such as trojans or stealers. Criminals usually deliver loaders through phishing emails and links by relying on social engineering to trick users into downloading and running their executables. Loaders employ advanced evasion and persistence tactics to avoid detection. |
| Analysis date: | January 29, 2019, 13:15:18 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MD5: | 13D6B78A4A57D4691E40D3C5456A5A6D |
| SHA1: | 1468B38BF525CE4EAA19ED4012B7C9A2518EA587 |
| SHA256: | 908B05A03A85891522EC440C1C10A9F203B922BFAD3CDABF95CC4B46D67398C0 |
| SSDEEP: | 3:N1KYvLdDLKKcBivOiIc6C:CYTZLTWi+C |
MALICIOUS
Downloads executable files from the Internet
- iexplore.exe (PID: 3156)
- K-Lite_Codec_Pack_1465_Full[1].tmp (PID: 2440)
Registers / Runs the DLL via REGSVR32.EXE
- K-Lite_Codec_Pack_1465_Full[1].tmp (PID: 2440)
Loads dropped or rewritten executable
- regsvr32.exe (PID: 2988)
- regsvr32.exe (PID: 2736)
- WebCompanionInstaller.exe (PID: 3120)
- WebCompanion.exe (PID: 2528)
- Lavasoft.WCAssistant.WinService.exe (PID: 3808)
- WebCompanion.exe (PID: 2740)
Uses Task Scheduler to run other applications
- K-Lite_Codec_Pack_1465_Full[1].tmp (PID: 2440)
Loads the Task Scheduler COM API
- schtasks.exe (PID: 2696)
Application was dropped or rewritten from another process
- CodecTweakTool.exe (PID: 3592)
- WcInstaller.exe (PID: 3496)
- WebCompanionInstaller.exe (PID: 3120)
- WebCompanion.exe (PID: 2528)
- Lavasoft.WCAssistant.WinService.exe (PID: 3808)
- Ad-Aware Web Companion.exe (PID: 1856)
- WebCompanion.exe (PID: 2740)
Changes internet zones settings
- WebCompanionInstaller.exe (PID: 3120)
Changes the autorun value in the registry
- WebCompanion.exe (PID: 2528)
SUSPICIOUS
Executable content was dropped or overwritten
- K-Lite_Codec_Pack_1465_Full[1].exe (PID: 2868)
- K-Lite_Codec_Pack_1465_Full[1].exe (PID: 3748)
- K-Lite_Codec_Pack_1465_Full[1].tmp (PID: 2440)
- WcInstaller.exe (PID: 3496)
- WebCompanionInstaller.exe (PID: 3120)
- csc.exe (PID: 960)
Searches for installed software
- K-Lite_Codec_Pack_1465_Full[1].tmp (PID: 2440)
Reads the Windows organization settings
- K-Lite_Codec_Pack_1465_Full[1].tmp (PID: 2440)
- CodecTweakTool.exe (PID: 3592)
Reads Windows owner or organization settings
- K-Lite_Codec_Pack_1465_Full[1].tmp (PID: 2440)
- CodecTweakTool.exe (PID: 3592)
Checks for external IP
- K-Lite_Codec_Pack_1465_Full[1].tmp (PID: 2440)
Creates files in the user directory
- K-Lite_Codec_Pack_1465_Full[1].tmp (PID: 2440)
- WebCompanionInstaller.exe (PID: 3120)
- WebCompanion.exe (PID: 2528)
Checks supported languages
- K-Lite_Codec_Pack_1465_Full[1].tmp (PID: 2440)
Creates COM task schedule object
- regsvr32.exe (PID: 2988)
- regsvr32.exe (PID: 2736)
Creates files in the program directory
- regsvr32.exe (PID: 2736)
- WebCompanionInstaller.exe (PID: 3120)
- WebCompanion.exe (PID: 2528)
- Lavasoft.WCAssistant.WinService.exe (PID: 3808)
- iexplore.exe (PID: 4004)
- WebCompanion.exe (PID: 2740)
Modifies the open verb of a shell class
- K-Lite_Codec_Pack_1465_Full[1].tmp (PID: 2440)
Starts SC.EXE for service management
- WebCompanionInstaller.exe (PID: 3120)
Uses NETSH.EXE for network configuration
- cmd.exe (PID: 3660)
- cmd.exe (PID: 2564)
Creates a software uninstall entry
- WebCompanionInstaller.exe (PID: 3120)
Starts CMD.EXE for commands execution
- WebCompanionInstaller.exe (PID: 3120)
- Lavasoft.WCAssistant.WinService.exe (PID: 3808)
Removes files from Windows directory
- Lavasoft.WCAssistant.WinService.exe (PID: 3808)
- WebCompanionInstaller.exe (PID: 3120)
Creates files in the Windows directory
- Lavasoft.WCAssistant.WinService.exe (PID: 3808)
- WebCompanionInstaller.exe (PID: 3120)
- WebCompanion.exe (PID: 2528)
Changes the started page of IE
- WebCompanion.exe (PID: 2528)
Starts Internet Explorer
- CodecTweakTool.exe (PID: 3592)
Reads Internet Cache Settings
- CodecTweakTool.exe (PID: 3592)
INFO
Changes internet zones settings
- iexplore.exe (PID: 2980)
- iexplore.exe (PID: 4048)
Reads Internet Cache Settings
- iexplore.exe (PID: 3156)
- iexplore.exe (PID: 2980)
- iexplore.exe (PID: 4004)
- iexplore.exe (PID: 4048)
Application was dropped or rewritten from another process
- K-Lite_Codec_Pack_1465_Full[1].tmp (PID: 2440)
- K-Lite_Codec_Pack_1465_Full[1].tmp (PID: 2232)
Loads dropped or rewritten executable
- K-Lite_Codec_Pack_1465_Full[1].tmp (PID: 2440)
Creates a software uninstall entry
- K-Lite_Codec_Pack_1465_Full[1].tmp (PID: 2440)
Creates files in the program directory
- K-Lite_Codec_Pack_1465_Full[1].tmp (PID: 2440)
Dropped object may contain Bitcoin addresses
- K-Lite_Codec_Pack_1465_Full[1].tmp (PID: 2440)
- WebCompanionInstaller.exe (PID: 3120)
- WebCompanion.exe (PID: 2528)
Reads internet explorer settings
- iexplore.exe (PID: 4004)
Creates files in the user directory
- iexplore.exe (PID: 4004)
Changes settings of System certificates
- iexplore.exe (PID: 4004)
Adds / modifies Windows certificates
- iexplore.exe (PID: 4004)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
78
Monitored processes
29
Malicious processes
11
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 960 | "C:\Windows\Microsoft.NET\Framework\v2.0.50727\csc.exe" /noconfig /fullpaths @"C:\Users\admin\AppData\Local\Temp\gg4zssqd.cmdline" | C:\Windows\Microsoft.NET\Framework\v2.0.50727\csc.exe | WebCompanion.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Visual C# Command Line Compiler Exit code: 0 Version: 8.0.50727.4927 (NetFXspW7.050727-4900) Modules
| |||||||||||||||
| 1856 | "C:\Program Files\Lavasoft\Web Companion\Application\Ad-Aware Web Companion.exe" {0633EE93-D776-472f-A0FF-E1416B8B2E3A} | C:\Program Files\Lavasoft\Web Companion\Application\Ad-Aware Web Companion.exe | — | WebCompanion.exe | |||||||||||
User: admin Company: Integrity Level: HIGH Description: Ad-Aware Web Companion.exe Exit code: 0 Version: 4.5.1957.3838 Modules
| |||||||||||||||
| 2232 | "C:\Users\admin\AppData\Local\Temp\is-28GHC.tmp\K-Lite_Codec_Pack_1465_Full[1].tmp" /SL5="$501A4,45567768,259072,C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\0UU90R59\K-Lite_Codec_Pack_1465_Full[1].exe" | C:\Users\admin\AppData\Local\Temp\is-28GHC.tmp\K-Lite_Codec_Pack_1465_Full[1].tmp | — | K-Lite_Codec_Pack_1465_Full[1].exe | |||||||||||
User: admin Integrity Level: MEDIUM Description: Setup/Uninstall Exit code: 0 Version: 51.1052.0.0 Modules
| |||||||||||||||
| 2280 | netsh http add urlacl url=http://+:9007/ user=Everyone | C:\Windows\system32\netsh.exe | — | cmd.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Network Command Shell Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2440 | "C:\Users\admin\AppData\Local\Temp\is-790QL.tmp\K-Lite_Codec_Pack_1465_Full[1].tmp" /SL5="$50130,45567768,259072,C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\0UU90R59\K-Lite_Codec_Pack_1465_Full[1].exe" /SPAWNWND=$4015A /NOTIFYWND=$501A4 | C:\Users\admin\AppData\Local\Temp\is-790QL.tmp\K-Lite_Codec_Pack_1465_Full[1].tmp | K-Lite_Codec_Pack_1465_Full[1].exe | ||||||||||||
User: admin Integrity Level: HIGH Description: Setup/Uninstall Exit code: 0 Version: 51.1052.0.0 Modules
| |||||||||||||||
| 2528 | "C:\Program Files\Lavasoft\Web Companion\Application\WebCompanion.exe" --silent --install --geo= | C:\Program Files\Lavasoft\Web Companion\Application\WebCompanion.exe | WebCompanionInstaller.exe | ||||||||||||
User: admin Company: Lavasoft Integrity Level: HIGH Description: Web Companion Exit code: 0 Version: 4.5.1957.3838 Modules
| |||||||||||||||
| 2560 | "sc.exe" description "WCAssistantService" "Ad-Aware Web Companion Internet security service" | C:\Windows\system32\sc.exe | — | WebCompanionInstaller.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: A tool to aid in developing services for WindowsNT Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2564 | "C:\Windows\System32\cmd.exe" /C netsh http add urlacl url=http://+:9007/ user=Everyone | C:\Windows\System32\cmd.exe | — | WebCompanionInstaller.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 2696 | "C:\Windows\system32\schtasks.exe" /Create /TN "klcp_update" /XML "C:\Users\admin\AppData\Local\Temp\is-B0VQM.tmp\klcp_update_task.xml" /F | C:\Windows\system32\schtasks.exe | — | K-Lite_Codec_Pack_1465_Full[1].tmp | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Manages scheduled tasks Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2736 | "C:\Windows\system32\regsvr32.exe" /s "C:\Program Files\K-Lite Codec Pack\Icaros\32-bit\IcarosPropertyHandler.dll" | C:\Windows\system32\regsvr32.exe | — | K-Lite_Codec_Pack_1465_Full[1].tmp | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft(C) Register Server Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
5 938
Read events
3 633
Write events
2 274
Delete events
31
Modification events
| (PID) Process: | (2980) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
| (PID) Process: | (2980) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
| (PID) Process: | (2980) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 1 | |||
| (PID) Process: | (2980) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\Zones |
| Operation: | write | Name: | SecuritySafe |
Value: 1 | |||
| (PID) Process: | (2980) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings |
| Operation: | write | Name: | ProxyEnable |
Value: 0 | |||
| (PID) Process: | (2980) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\Connections |
| Operation: | write | Name: | SavedLegacySettings |
Value: 4600000069000000010000000000000000000000000000000000000000000000C0E333BBEAB1D301000000000000000000000000020000001700000000000000FE800000000000007D6CB050D9C573F70B000000000000006D00330032005C004D00530049004D004700330032002E0064006C000100000004AA400014AA4000040000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000002000000C0A8016400000000000000000000000000000000000000000800000000000000805D3F00983740000008000002000000000000600000002060040000B8A94000020000008802000060040000B8A9400004000000F8010000B284000088B64000B84B400043003A000000000000000000000000000000000000000000 | |||
| (PID) Process: | (2980) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Recovery\Active |
| Operation: | write | Name: | {F539F5D5-23C7-11E9-91D7-5254004A04AF} |
Value: 0 | |||
| (PID) Process: | (2980) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Ext\Stats\{2670000A-7350-4F3C-8081-5663EE0C6C49}\iexplore |
| Operation: | write | Name: | Type |
Value: 4 | |||
| (PID) Process: | (2980) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Ext\Stats\{2670000A-7350-4F3C-8081-5663EE0C6C49}\iexplore |
| Operation: | write | Name: | Count |
Value: 3 | |||
| (PID) Process: | (2980) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Ext\Stats\{2670000A-7350-4F3C-8081-5663EE0C6C49}\iexplore |
| Operation: | write | Name: | Time |
Value: E307010002001D000D000F002200B902 | |||
Executable files
153
Suspicious files
22
Text files
333
Unknown types
20
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2980 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\R9ZEWH8D\favicon[1].ico | — | |
MD5:— | SHA256:— | |||
| 2980 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\Internet Explorer\Services\search_{0633EE93-D776-472f-A0FF-E1416B8B2E3A}.ico | — | |
MD5:— | SHA256:— | |||
| 2980 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\~DFE1651DC4D1D96302.TMP | — | |
MD5:— | SHA256:— | |||
| 3156 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\OCDM6JB6\K-Lite_Codec_Pack_1465_Full[1].exe | — | |
MD5:— | SHA256:— | |||
| 2980 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\0UU90R59\K-Lite_Codec_Pack_1465_Full[1].exe | — | |
MD5:— | SHA256:— | |||
| 2980 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\~DFB13CC8F9DC2C97DA.TMP | — | |
MD5:— | SHA256:— | |||
| 2980 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Internet Explorer\Recovery\Active\RecoveryStore.{F539F5D5-23C7-11E9-91D7-5254004A04AF}.dat | — | |
MD5:— | SHA256:— | |||
| 2440 | K-Lite_Codec_Pack_1465_Full[1].tmp | C:\Program Files\K-Lite Codec Pack\is-96BGI.tmp | — | |
MD5:— | SHA256:— | |||
| 2440 | K-Lite_Codec_Pack_1465_Full[1].tmp | C:\Program Files\K-Lite Codec Pack\Info\is-KQ3J8.tmp | — | |
MD5:— | SHA256:— | |||
| 2440 | K-Lite_Codec_Pack_1465_Full[1].tmp | C:\Program Files\K-Lite Codec Pack\Tools\is-TMOAU.tmp | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
48
TCP/UDP connections
40
DNS requests
27
Threats
4
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2440 | K-Lite_Codec_Pack_1465_Full[1].tmp | GET | 200 | 104.24.119.99:80 | http://data.codecguide.com/config/offer_wc.ini | US | text | 370 b | malicious |
3156 | iexplore.exe | GET | 200 | 51.15.9.231:80 | http://files3.codecguide.com/K-Lite_Codec_Pack_1465_Full.exe | NL | executable | 44.0 Mb | suspicious |
2440 | K-Lite_Codec_Pack_1465_Full[1].tmp | GET | 200 | 104.17.114.51:80 | http://webcompanion.com/nano_download.php?partner=KL150601 | US | executable | 347 Kb | malicious |
2440 | K-Lite_Codec_Pack_1465_Full[1].tmp | GET | 200 | 216.239.32.21:80 | http://ipinfo.io/json | US | text | 172 b | shared |
3120 | WebCompanionInstaller.exe | POST | 200 | 72.55.154.81:80 | http://wc-update-service.lavasoft.com/update.asmx | CA | xml | 1.43 Kb | whitelisted |
3120 | WebCompanionInstaller.exe | GET | 200 | 104.17.60.19:80 | http://wcdownloadercdn.lavasoft.com/4.5.1957.3838/WebCompanion-4.5.1957.3838-prod.zip | US | compressed | 8.99 Mb | whitelisted |
2440 | K-Lite_Codec_Pack_1465_Full[1].tmp | POST | 200 | 172.217.23.142:80 | http://www.google-analytics.com/collect | US | image | 35 b | whitelisted |
3120 | WebCompanionInstaller.exe | POST | 200 | 72.55.154.82:80 | http://wc-tracking.lavasoft.com/Install.asmx | CA | xml | 294 b | whitelisted |
3120 | WebCompanionInstaller.exe | POST | 200 | 72.55.154.82:80 | http://wc-tracking.lavasoft.com/Install.asmx | CA | xml | 294 b | whitelisted |
3120 | WebCompanionInstaller.exe | POST | 200 | 72.55.154.82:80 | http://wc-tracking.lavasoft.com/Install.asmx | CA | xml | 294 b | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2980 | iexplore.exe | 204.79.197.200:80 | www.bing.com | Microsoft Corporation | US | whitelisted |
3156 | iexplore.exe | 51.15.9.231:80 | files3.codecguide.com | Online S.a.s. | NL | suspicious |
2440 | K-Lite_Codec_Pack_1465_Full[1].tmp | 216.239.32.21:80 | ipinfo.io | Google Inc. | US | whitelisted |
2440 | K-Lite_Codec_Pack_1465_Full[1].tmp | 104.24.119.99:80 | data.codecguide.com | Cloudflare Inc | US | shared |
2440 | K-Lite_Codec_Pack_1465_Full[1].tmp | 172.217.23.142:80 | www.google-analytics.com | Google Inc. | US | whitelisted |
2440 | K-Lite_Codec_Pack_1465_Full[1].tmp | 104.17.114.51:80 | webcompanion.com | Cloudflare Inc | US | shared |
3120 | WebCompanionInstaller.exe | 72.55.154.82:80 | wc-tracking.lavasoft.com | iWeb Technologies Inc. | CA | unknown |
3120 | WebCompanionInstaller.exe | 72.55.154.81:80 | wc-tracking.lavasoft.com | iWeb Technologies Inc. | CA | unknown |
3120 | WebCompanionInstaller.exe | 104.17.60.19:80 | wcdownloadercdn.lavasoft.com | Cloudflare Inc | US | shared |
2528 | WebCompanion.exe | 104.17.114.51:80 | webcompanion.com | Cloudflare Inc | US | shared |
DNS requests
Domain | IP | Reputation |
|---|---|---|
www.bing.com |
| whitelisted |
files3.codecguide.com |
| suspicious |
ipinfo.io |
| shared |
data.codecguide.com |
| malicious |
www.google-analytics.com |
| whitelisted |
webcompanion.com |
| malicious |
wc-tracking.lavasoft.com |
| whitelisted |
wc-update-service.lavasoft.com |
| whitelisted |
wcdownloadercdn.lavasoft.com |
| whitelisted |
rt.webcompanion.com |
| malicious |
Threats
PID | Process | Class | Message |
|---|---|---|---|
3156 | iexplore.exe | Potential Corporate Privacy Violation | ET POLICY PE EXE or DLL Windows file download HTTP |
2440 | K-Lite_Codec_Pack_1465_Full[1].tmp | Potential Corporate Privacy Violation | ET POLICY Possible External IP Lookup ipinfo.io |
2440 | K-Lite_Codec_Pack_1465_Full[1].tmp | Potential Corporate Privacy Violation | ET POLICY PE EXE or DLL Windows file download HTTP |
2440 | K-Lite_Codec_Pack_1465_Full[1].tmp | Misc activity | ET INFO EXE - Served Attached HTTP |
Process | Message |
|---|---|
WebCompanionInstaller.exe | Detecting windows culture
|
WebCompanionInstaller.exe | 1/29/2019 1:17:19 PM :-> Starting installer 4.5.1957.3838 with: .\WebCompanionInstaller.exe --partner=KL150601 --version=4.5.1957.3838 --prod --silent --partner=KL150601 --homepage=1 --search=1, Run as admin: True
|
WebCompanionInstaller.exe | Preparing for installing Web Companion
|
WebCompanionInstaller.exe | 1/29/2019 1:17:20 PM :-> Generating Machine and Install Id ...
|
WebCompanionInstaller.exe | 1/29/2019 1:17:20 PM :-> Machine Id and Install Id has been generated
|
WebCompanionInstaller.exe | 1/29/2019 1:17:20 PM :-> Checking prerequisites ...
|
WebCompanionInstaller.exe | 1/29/2019 1:17:20 PM :-> Antivirus not detected
|
WebCompanionInstaller.exe | 1/29/2019 1:17:20 PM :-> vm_check False
|
WebCompanionInstaller.exe | 1/29/2019 1:17:21 PM :-> reg_check :False
|
WebCompanionInstaller.exe | 1/29/2019 1:17:21 PM :-> Installed .Net framework is V40
|