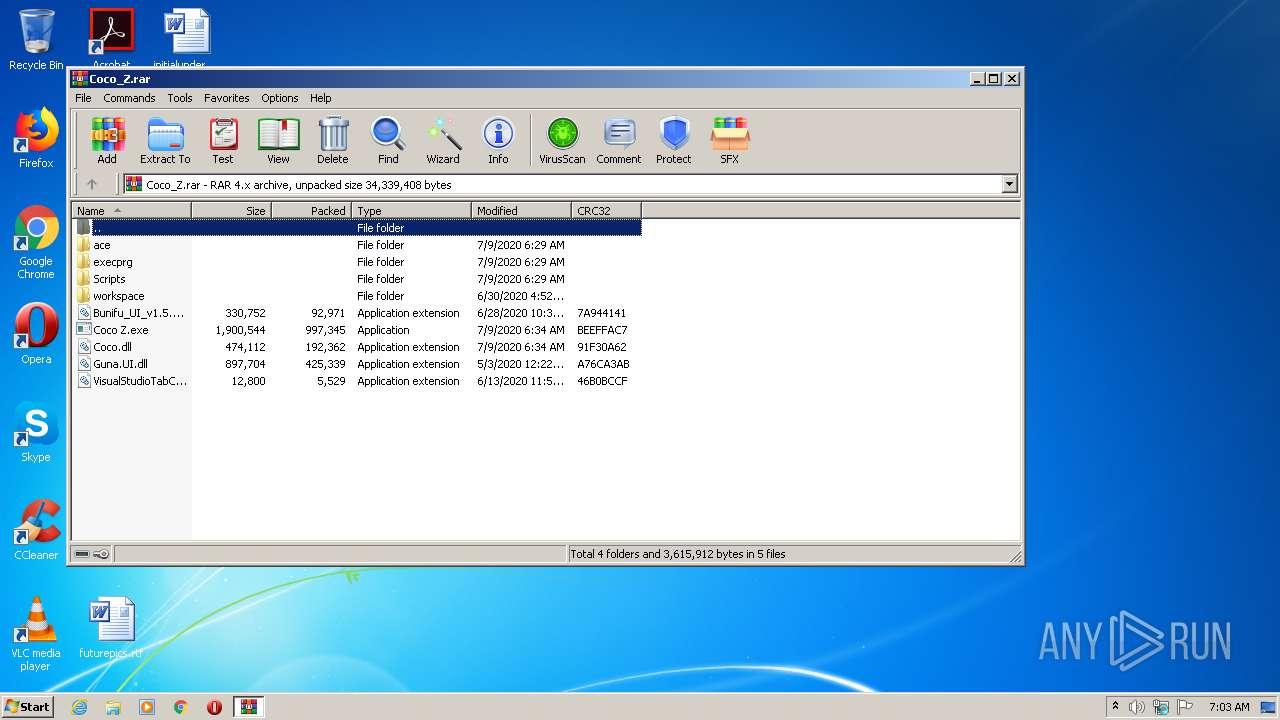
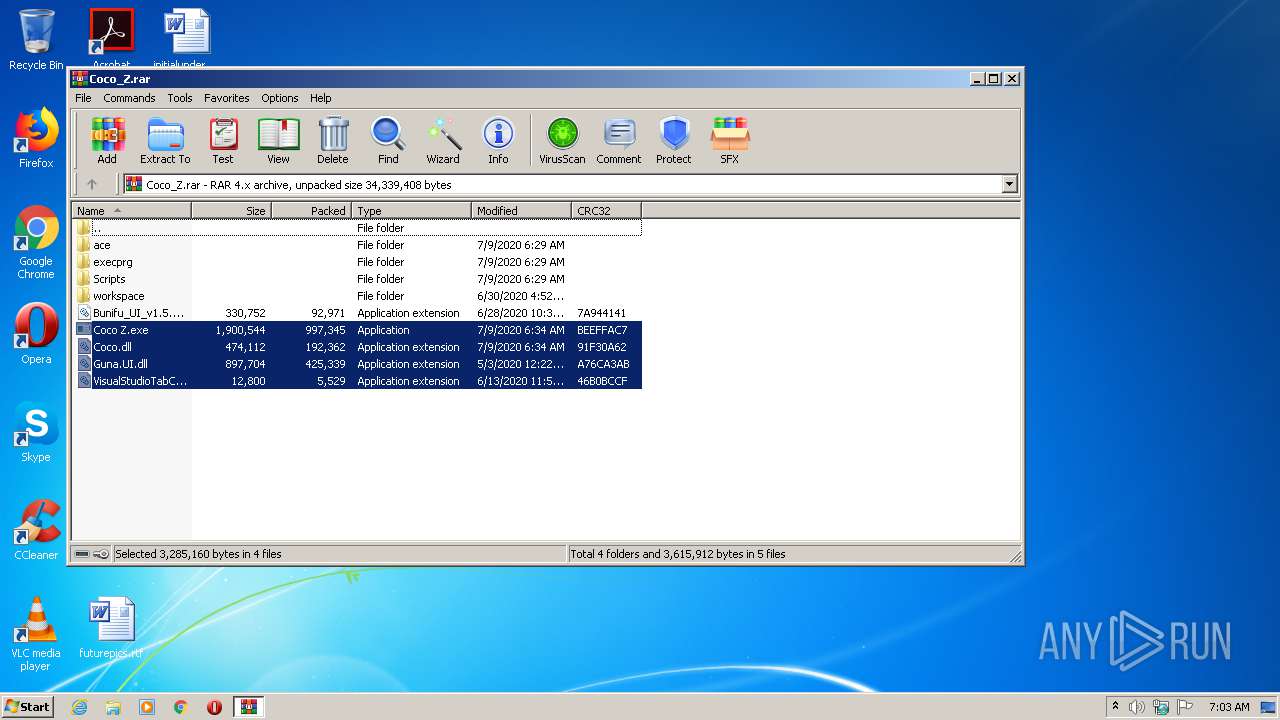
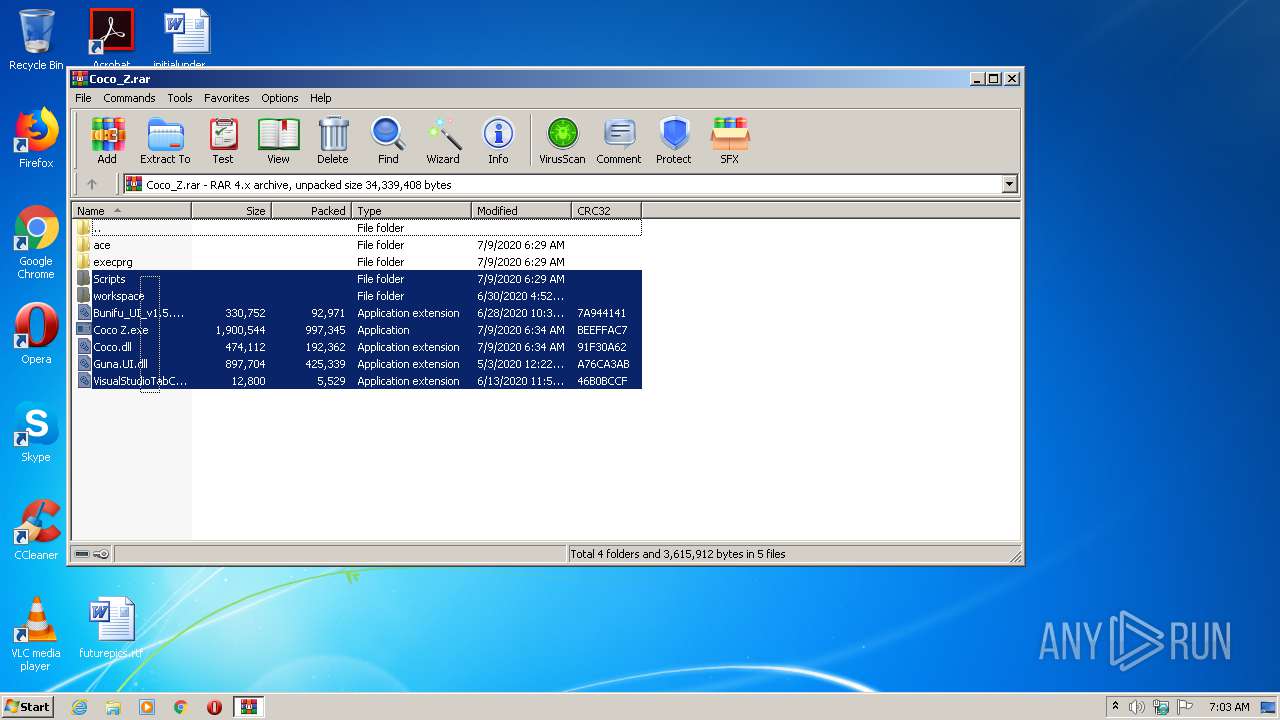
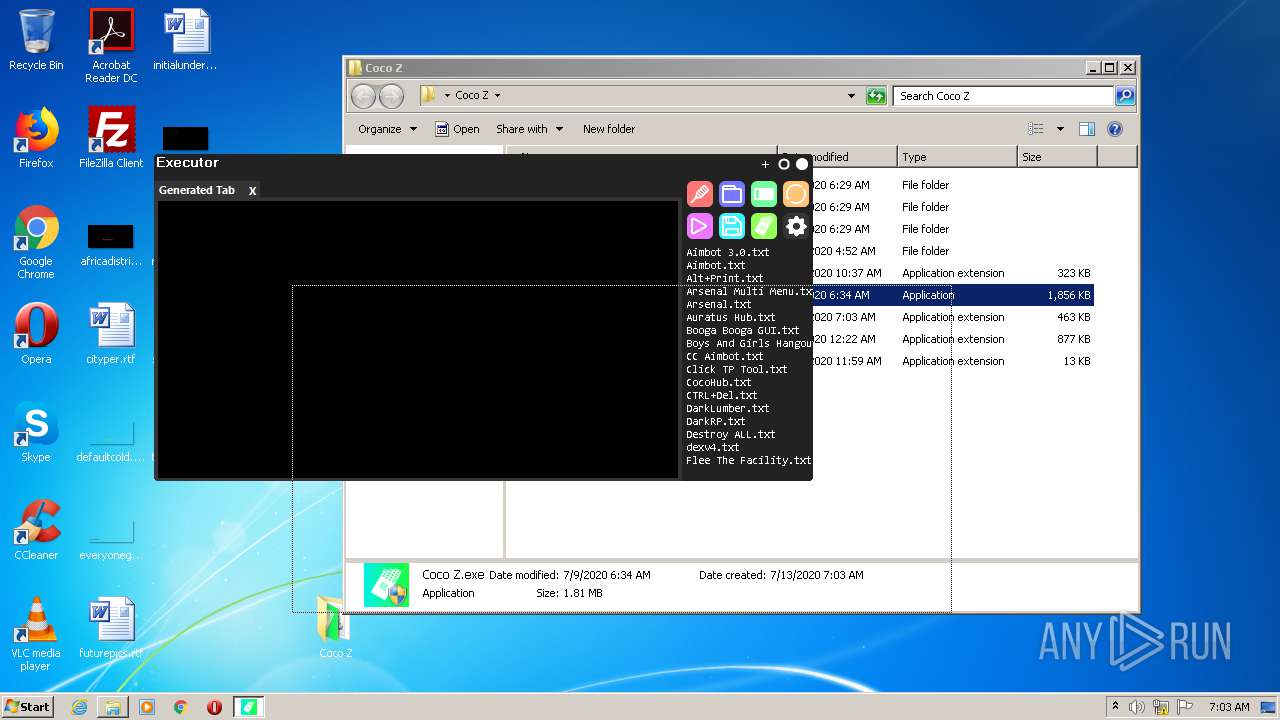
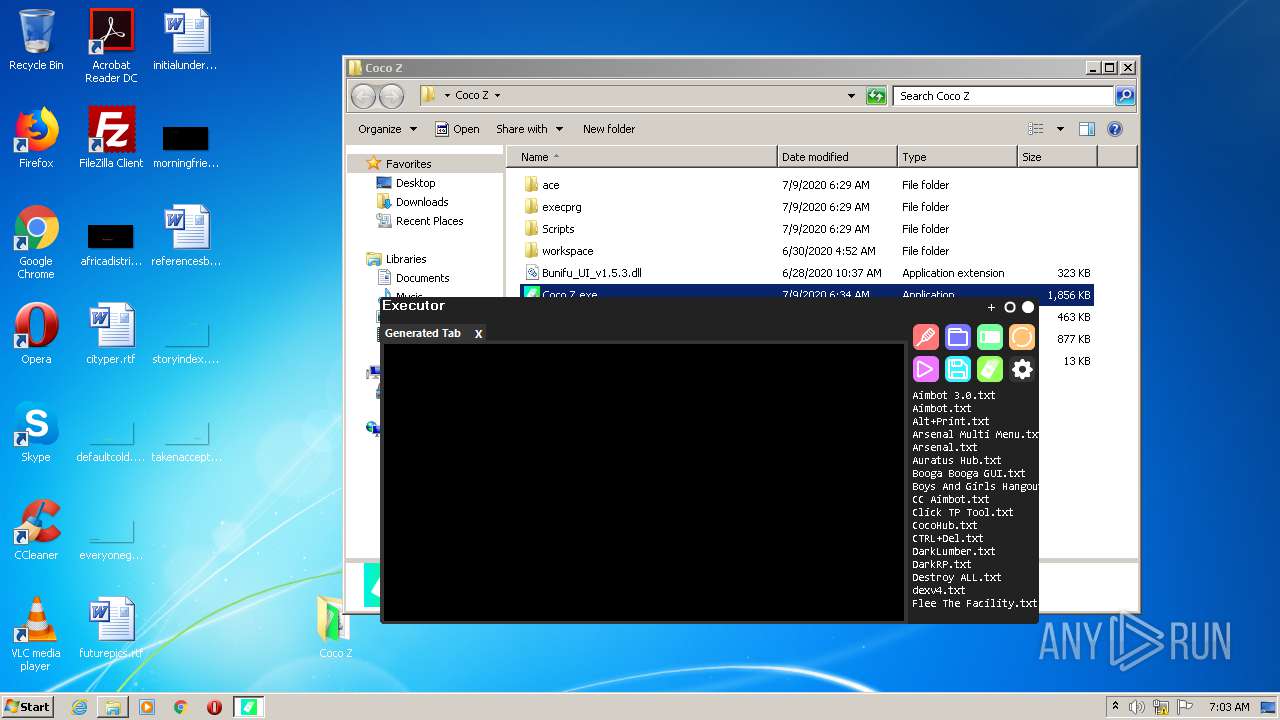
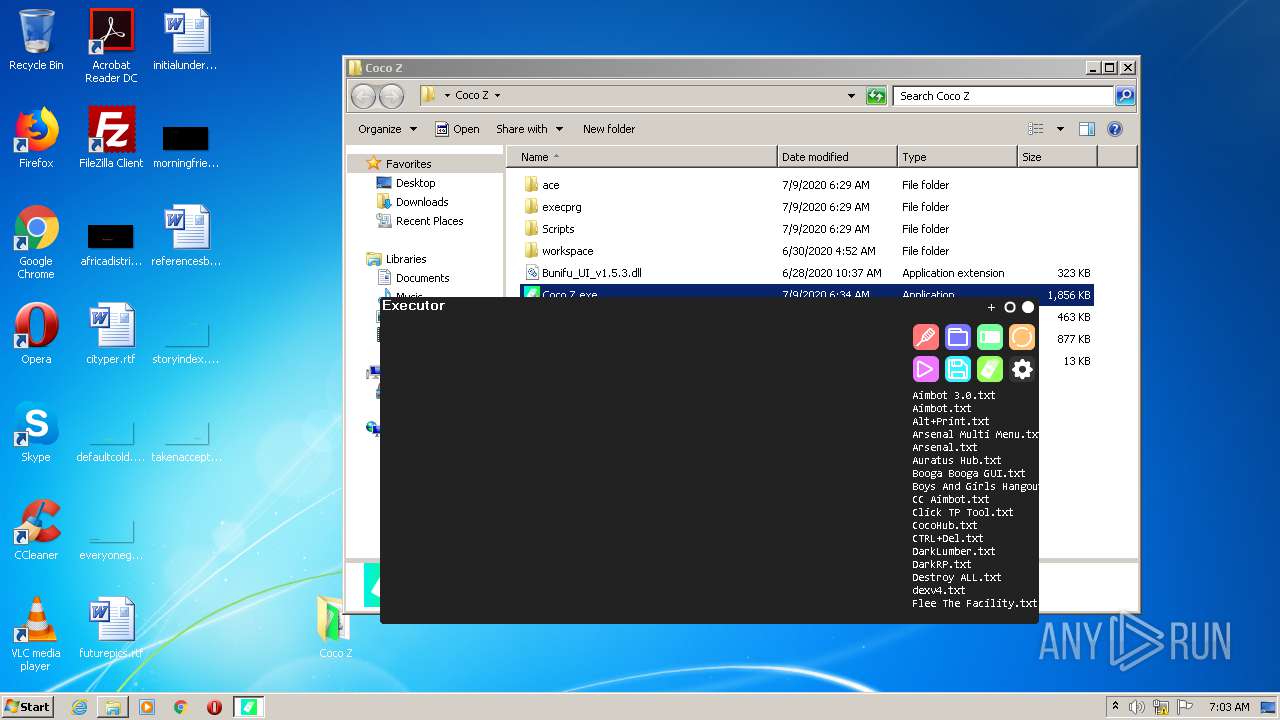
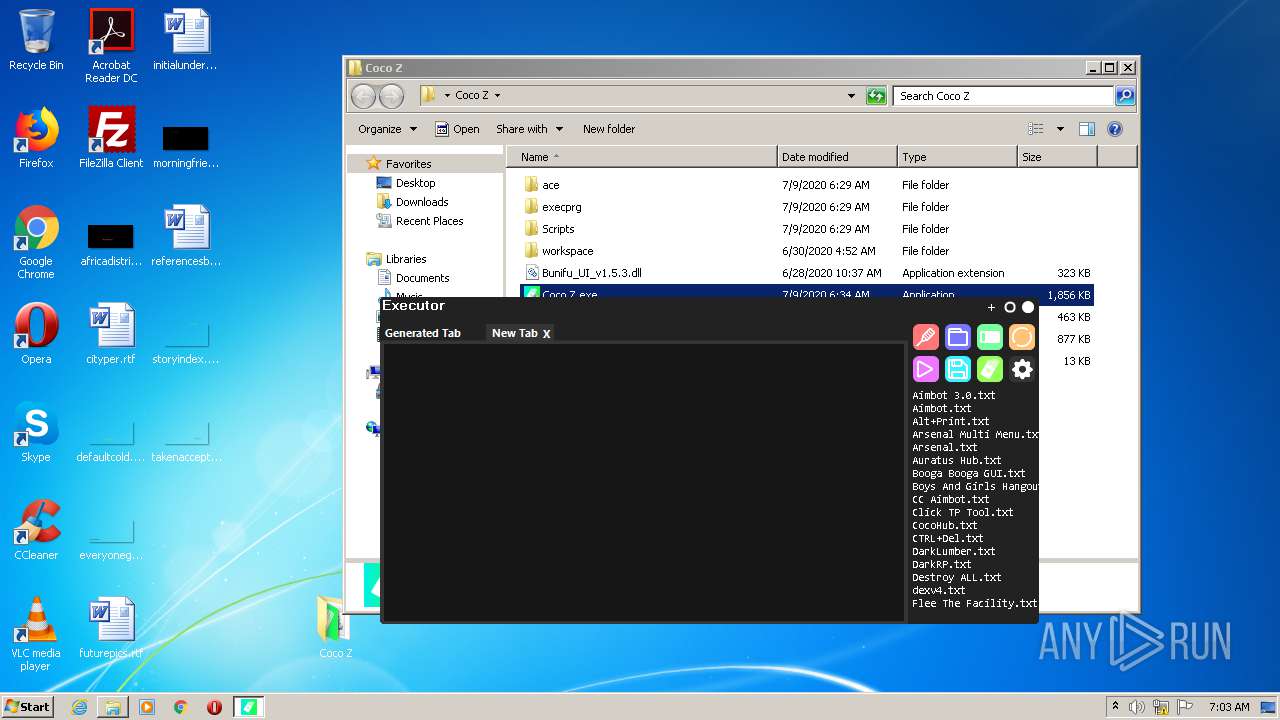
| File name: | Coco_Z.rar |
| Full analysis: | https://app.any.run/tasks/aa425cb7-5076-457a-a034-b096868bfcd3 |
| Verdict: | Malicious activity |
| Analysis date: | July 13, 2020, 06:02:40 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-rar |
| File info: | RAR archive data, v4, os: Win32 |
| MD5: | 75BAD7CFAD8351A50814F85EE1FF5C89 |
| SHA1: | 19B078F0B92C03D23C7A333C4864E096D5726F18 |
| SHA256: | 907AA542FB87581AD730E74AA75FD4605E4B425A2A9186C12E2C1A2225C90AB2 |
| SSDEEP: | 196608:pRYJ3aiHJsjXXhVN9IaKPpF6yr7SIZB2IFBYs8hrvDN:pRYJ3ai2jBVT1SF5XSIn2I7ah9 |
MALICIOUS
Loads dropped or rewritten executable
- SearchProtocolHost.exe (PID: 3464)
- Coco Z.exe (PID: 3264)
Application was dropped or rewritten from another process
- Coco Z.exe (PID: 2668)
- Coco Z.exe (PID: 3264)
Changes settings of System certificates
- Coco Z.exe (PID: 3264)
SUSPICIOUS
Executable content was dropped or overwritten
- WinRAR.exe (PID: 2436)
- Coco Z.exe (PID: 3264)
Reads Internet Cache Settings
- Coco Z.exe (PID: 3264)
Reads internet explorer settings
- Coco Z.exe (PID: 3264)
Reads Environment values
- Coco Z.exe (PID: 3264)
Changes IE settings (feature browser emulation)
- Coco Z.exe (PID: 3264)
Adds / modifies Windows certificates
- Coco Z.exe (PID: 3264)
INFO
Dropped object may contain Bitcoin addresses
- WinRAR.exe (PID: 2436)
Manual execution by user
- Coco Z.exe (PID: 2668)
- Coco Z.exe (PID: 3264)
Reads settings of System Certificates
- Coco Z.exe (PID: 3264)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .rar | | | RAR compressed archive (v-4.x) (58.3) |
|---|---|---|
| .rar | | | RAR compressed archive (gen) (41.6) |
EXIF
ZIP
| CompressedSize: | 93017 |
|---|---|
| UncompressedSize: | 330752 |
| OperatingSystem: | Win32 |
| ModifyDate: | 2020:06:28 10:37:22 |
| PackingMethod: | Normal |
| ArchivedFileName: | Bunifu_UI_v1.5.3.dll |
Total processes
41
Monitored processes
4
Malicious processes
3
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2436 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\Coco_Z.rar" | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.60.0 Modules
| |||||||||||||||
| 2668 | "C:\Users\admin\Desktop\Coco Z\Coco Z.exe" | C:\Users\admin\Desktop\Coco Z\Coco Z.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Description: Coco Z (1st Generation) Exit code: 3221226540 Version: 1.0.0.0 Modules
| |||||||||||||||
| 3264 | "C:\Users\admin\Desktop\Coco Z\Coco Z.exe" | C:\Users\admin\Desktop\Coco Z\Coco Z.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: HIGH Description: Coco Z (1st Generation) Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
| 3464 | "C:\Windows\system32\SearchProtocolHost.exe" Global\UsGthrFltPipeMssGthrPipe3_ Global\UsGthrCtrlFltPipeMssGthrPipe3 1 -2147483646 "Software\Microsoft\Windows Search" "Mozilla/4.0 (compatible; MSIE 6.0; Windows NT; MS Search 4.0 Robot)" "C:\ProgramData\Microsoft\Search\Data\Temp\usgthrsvc" "DownLevelDaemon" | C:\Windows\System32\SearchProtocolHost.exe | — | SearchIndexer.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft Windows Search Protocol Host Exit code: 0 Version: 7.00.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
2 126
Read events
894
Write events
1 232
Delete events
0
Modification events
| (PID) Process: | (2436) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (2436) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (2436) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\12F\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (2436) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\12F\52C64B7E |
| Operation: | write | Name: | @C:\Windows\system32\NetworkExplorer.dll,-1 |
Value: Network | |||
| (PID) Process: | (2436) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\Coco_Z.rar | |||
| (PID) Process: | (2436) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (2436) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (2436) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (2436) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (3464) SearchProtocolHost.exe | Key: | HKEY_USERS\.DEFAULT\Software\Classes\Local Settings\MuiCache\12F\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
Executable files
8
Suspicious files
4
Text files
828
Unknown types
2
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2436 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2436.3147\Coco.dll | executable | |
MD5:— | SHA256:— | |||
| 2436 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2436.3147\ace\ext-prompt.js | text | |
MD5:— | SHA256:— | |||
| 2436 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2436.3147\ace\ext-modelist.js | text | |
MD5:— | SHA256:— | |||
| 2436 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2436.3147\ace\ace.js | text | |
MD5:A17EA4028CCE563F3972D6CE555FDCE6 | SHA256:0E82BF4C24525CF4AED5A3A7885B198FAAFF5908CE279E6EC1704C443B4BD1E1 | |||
| 2436 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2436.3147\Bunifu_UI_v1.5.3.dll | executable | |
MD5:E0EF2817EE5A7C8CD1EB837195768BD2 | SHA256:76E1D3EC95FDEF74ABAF90392DD6F4AA5E344922ABF11E572707287D467F2930 | |||
| 2436 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2436.3147\Coco Z.exe | executable | |
MD5:— | SHA256:— | |||
| 2436 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2436.3147\ace\editor.html | html | |
MD5:— | SHA256:— | |||
| 2436 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2436.3147\ace\ext-emmet.js | text | |
MD5:— | SHA256:— | |||
| 2436 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2436.3147\VisualStudioTabControl.dll | executable | |
MD5:— | SHA256:— | |||
| 2436 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2436.3147\ace\ext-keybinding_menu.js | text | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
2
TCP/UDP connections
4
DNS requests
4
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3264 | Coco Z.exe | GET | 200 | 172.217.22.3:80 | http://ocsp.pki.goog/gts1o1core/MFIwUDBOMEwwSjAJBgUrDgMCGgUABBRCRjDCJxnb3nDwj%2Fxz5aZfZjgXvAQUmNH4bhDrz5vsYJ8YkBug630J%2FSsCEQDRWV%2BNyD7WkwIAAAAAbwew | US | der | 472 b | whitelisted |
3264 | Coco Z.exe | GET | 200 | 172.217.22.3:80 | http://ocsp.pki.goog/gsr2/ME4wTDBKMEgwRjAJBgUrDgMCGgUABBTgXIsxbvr2lBkPpoIEVRE6gHlCnAQUm%2BIHV2ccHsBqBt5ZtJot39wZhi4CDQHjtJqhjYqpgSVpULg%3D | US | der | 468 b | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3264 | Coco Z.exe | 162.159.129.233:443 | cdn.discordapp.com | Cloudflare Inc | — | shared |
3264 | Coco Z.exe | 104.28.13.51:443 | pastebinp.com | Cloudflare Inc | US | unknown |
3264 | Coco Z.exe | 216.58.206.10:443 | fonts.googleapis.com | Google Inc. | US | whitelisted |
3264 | Coco Z.exe | 172.217.22.3:80 | ocsp.pki.goog | Google Inc. | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
pastebinp.com |
| unknown |
cdn.discordapp.com |
| shared |
fonts.googleapis.com |
| whitelisted |
ocsp.pki.goog |
| whitelisted |