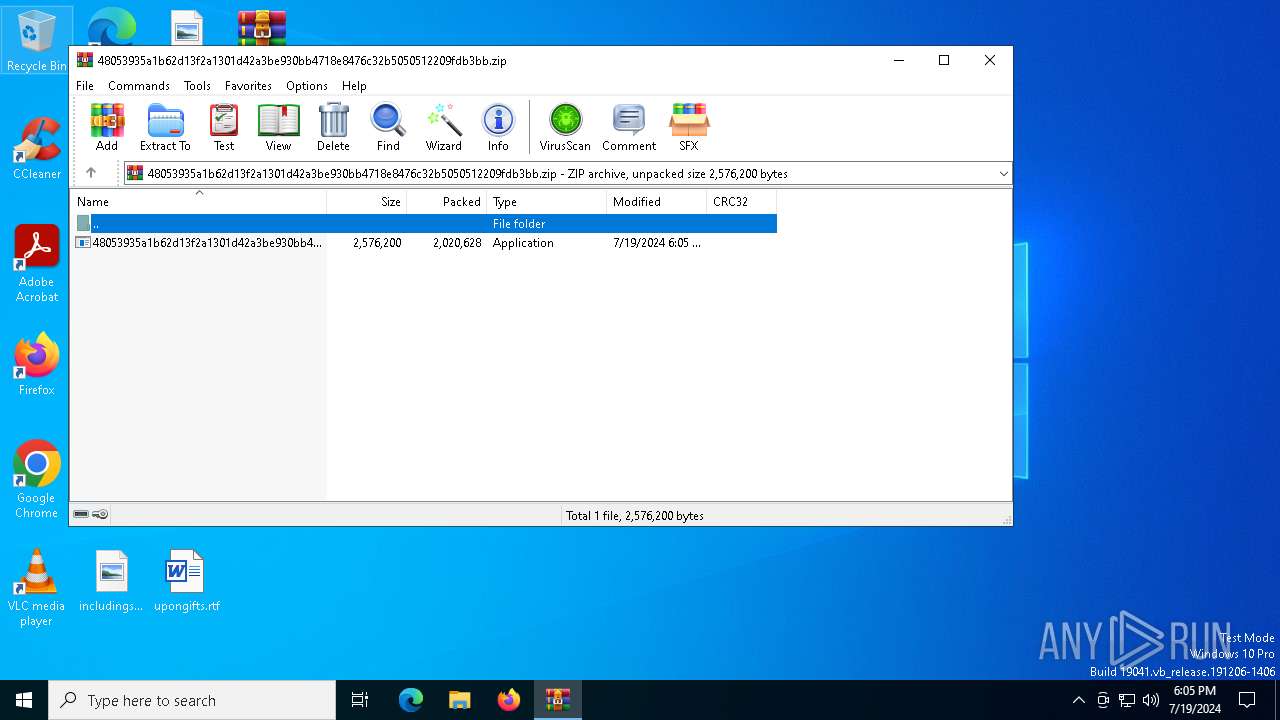
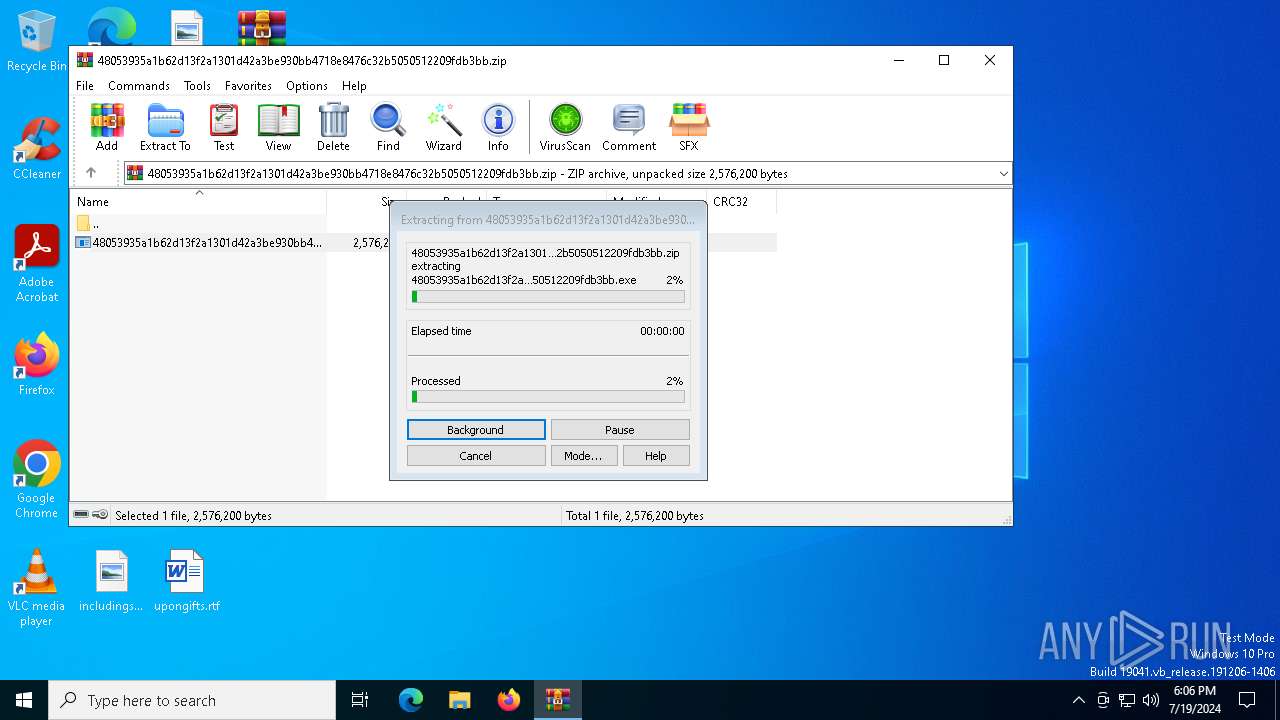
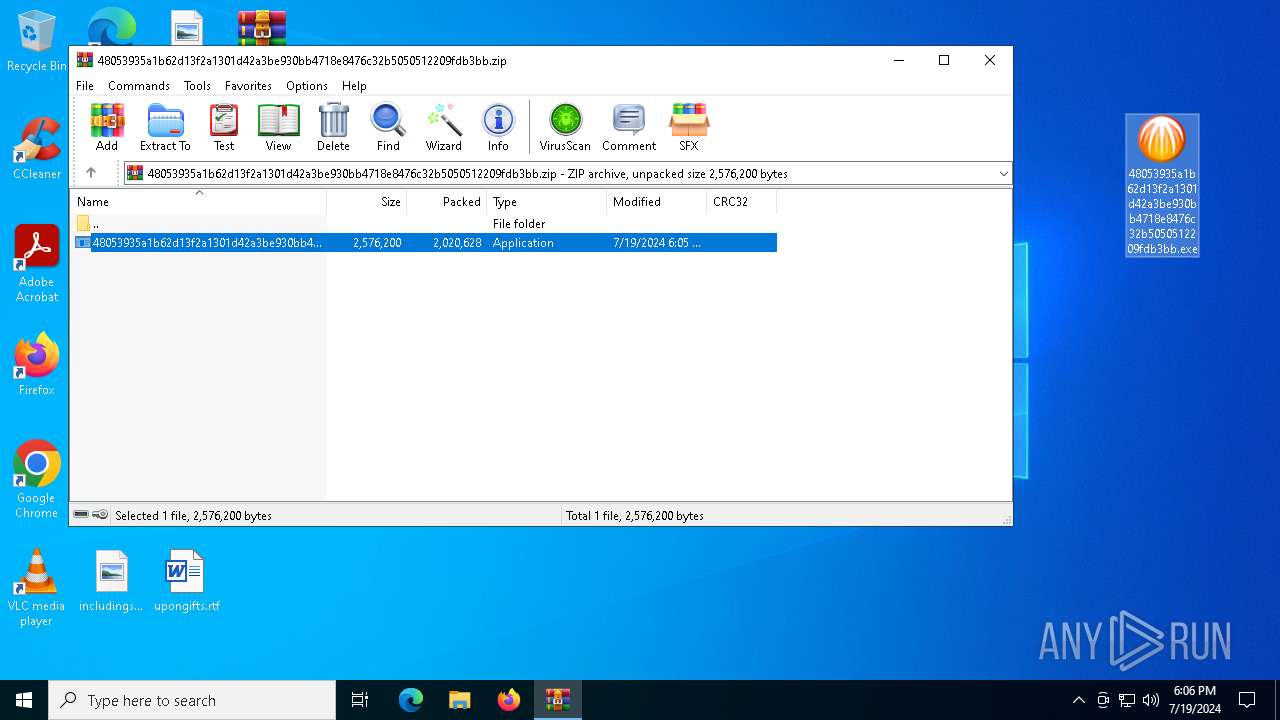
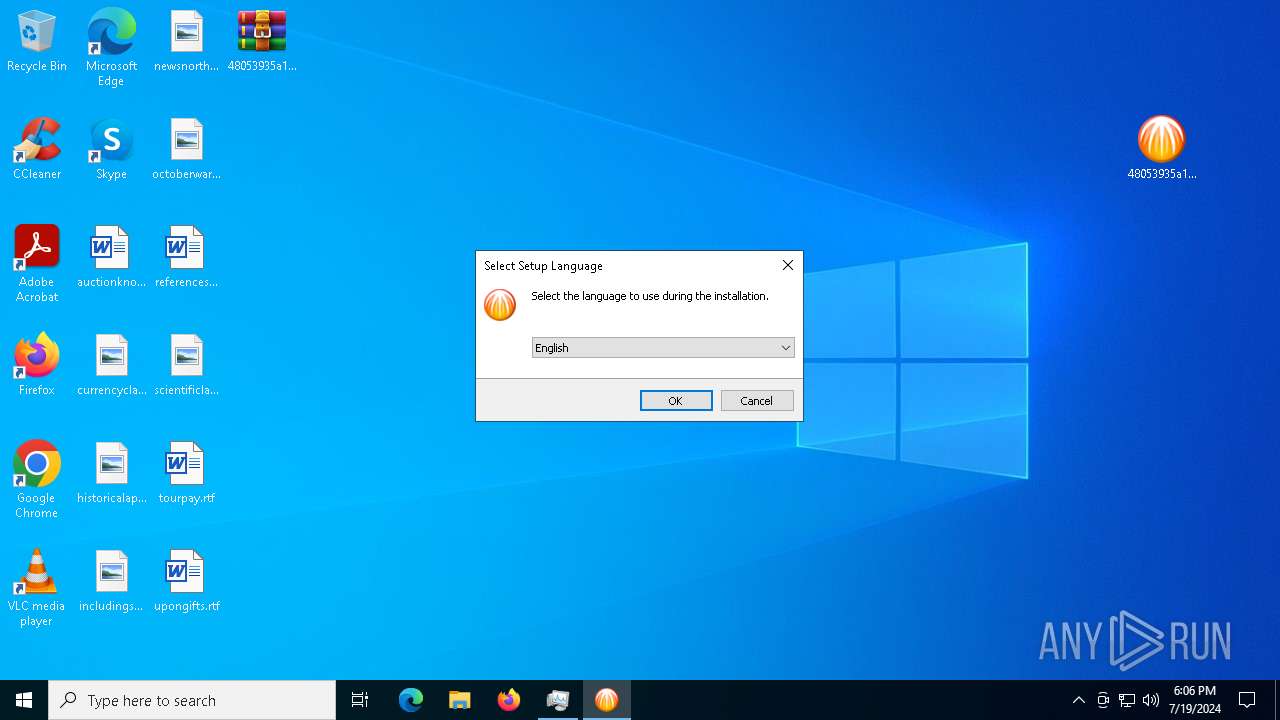
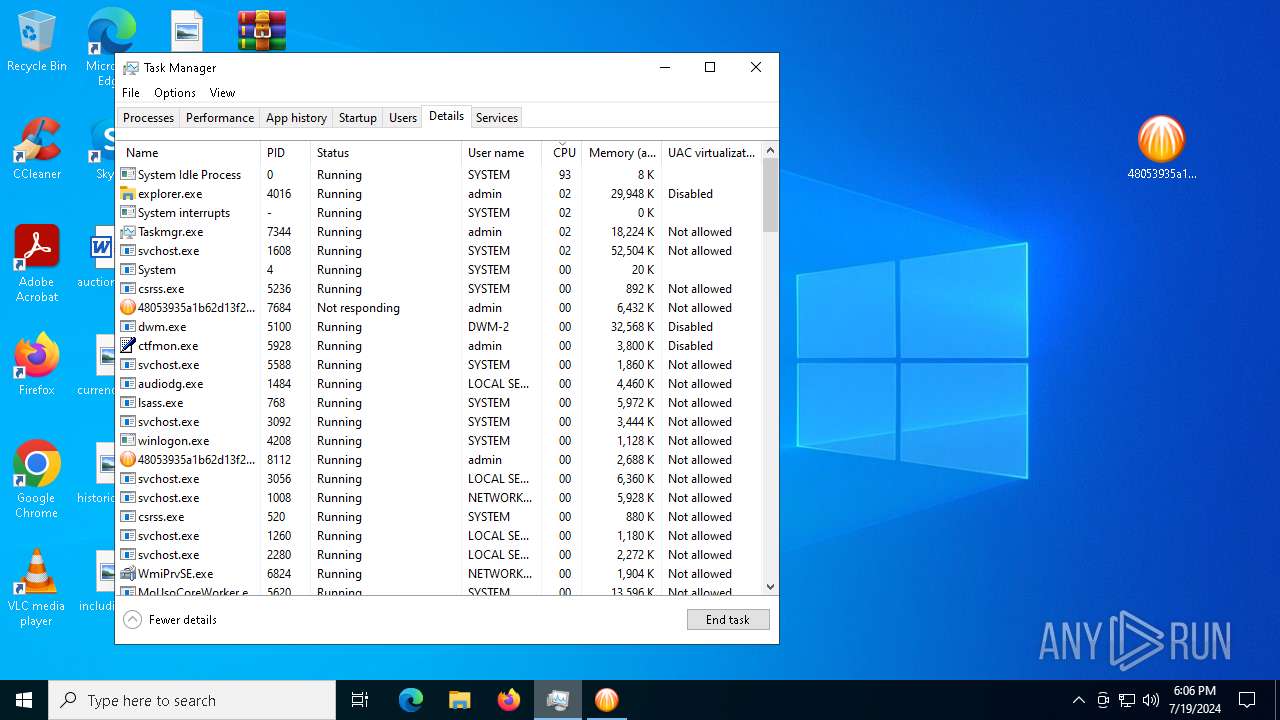
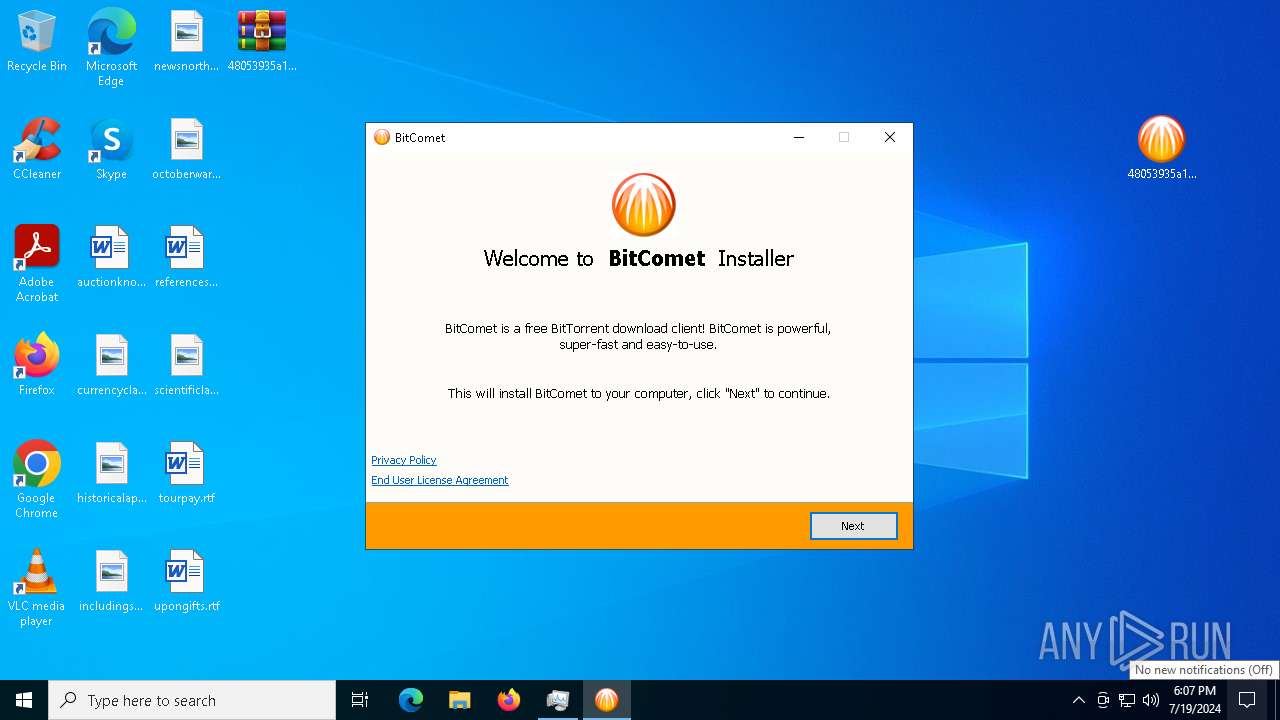
| File name: | 48053935a1b62d13f2a1301d42a3be930bb4718e8476c32b5050512209fdb3bb.zip |
| Full analysis: | https://app.any.run/tasks/04e2f615-9bcf-4ed8-99cc-8e99378c8a6a |
| Verdict: | Malicious activity |
| Analysis date: | July 19, 2024, 18:05:47 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
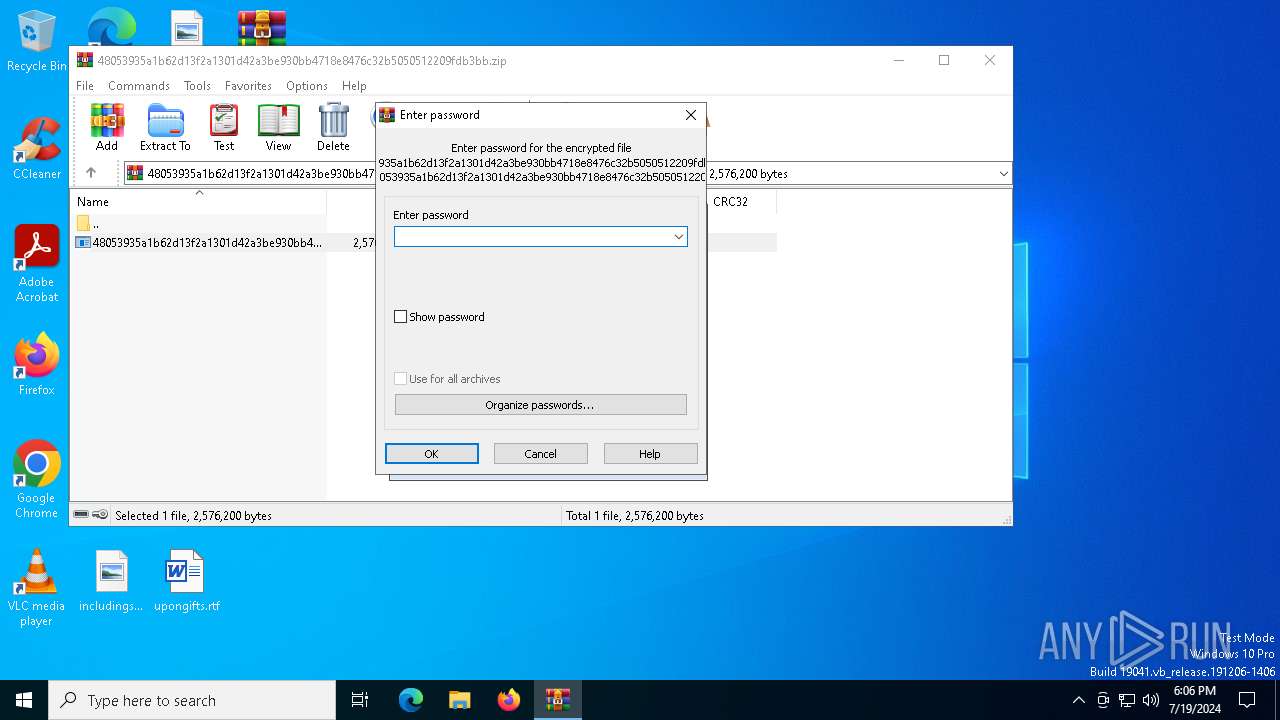
| File info: | Zip archive data, at least v5.1 to extract, compression method=AES Encrypted |
| MD5: | 90979AFF2B6FA2E3093EC593FB515DB7 |
| SHA1: | DB0ECED45590225814E02DDA68BD8EDA3C2DB1D0 |
| SHA256: | 8FE3BFF7178B430314F38BAE4D49C21A0C57A09D76141B6FB82C72272D2DC372 |
| SSDEEP: | 98304:P9JYrWN+tCEJ0kQuwS1czc4ZOSAoXa8khHo80/VkLaTR5evK0M9EkqeEUO7aeXM6:P7FVt+ |
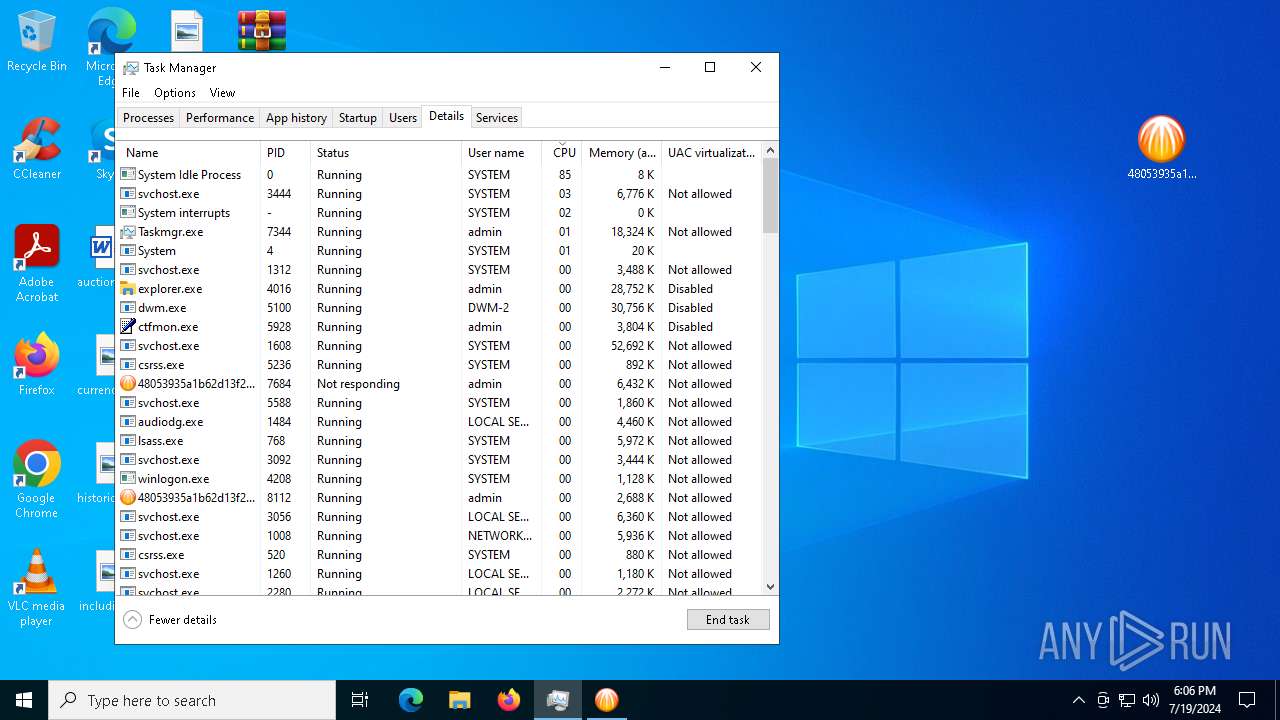
MALICIOUS
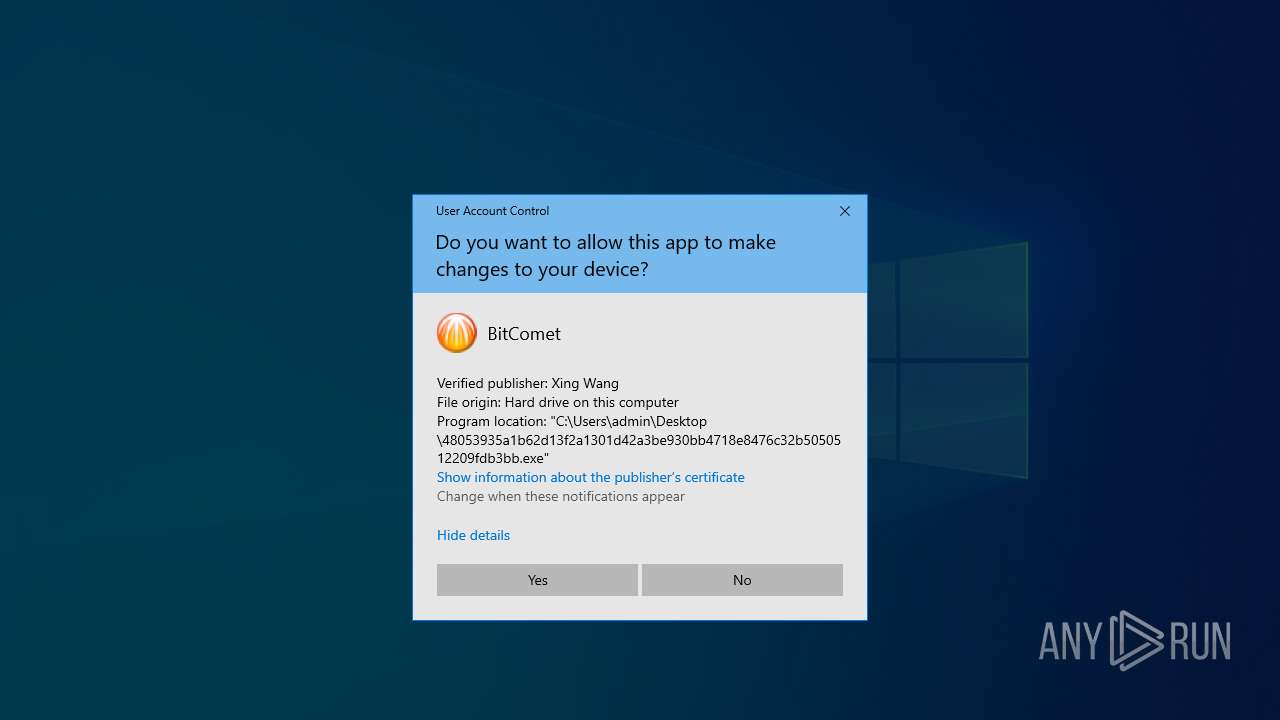
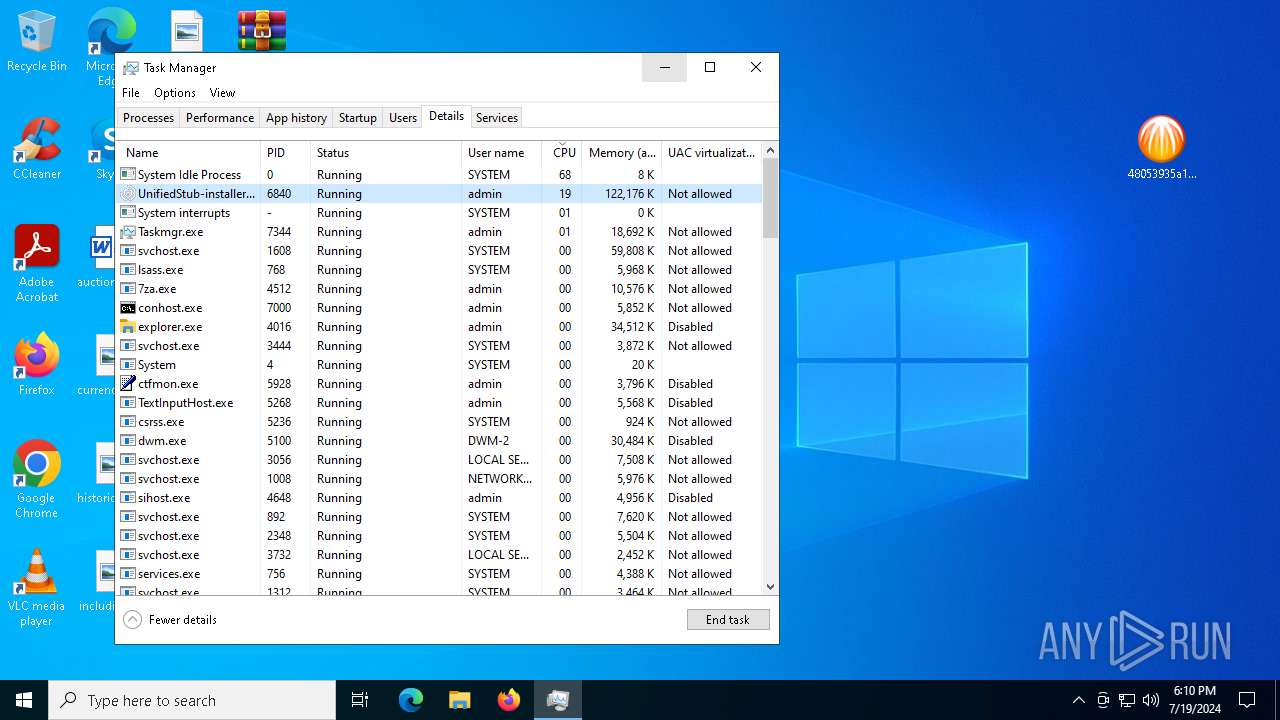
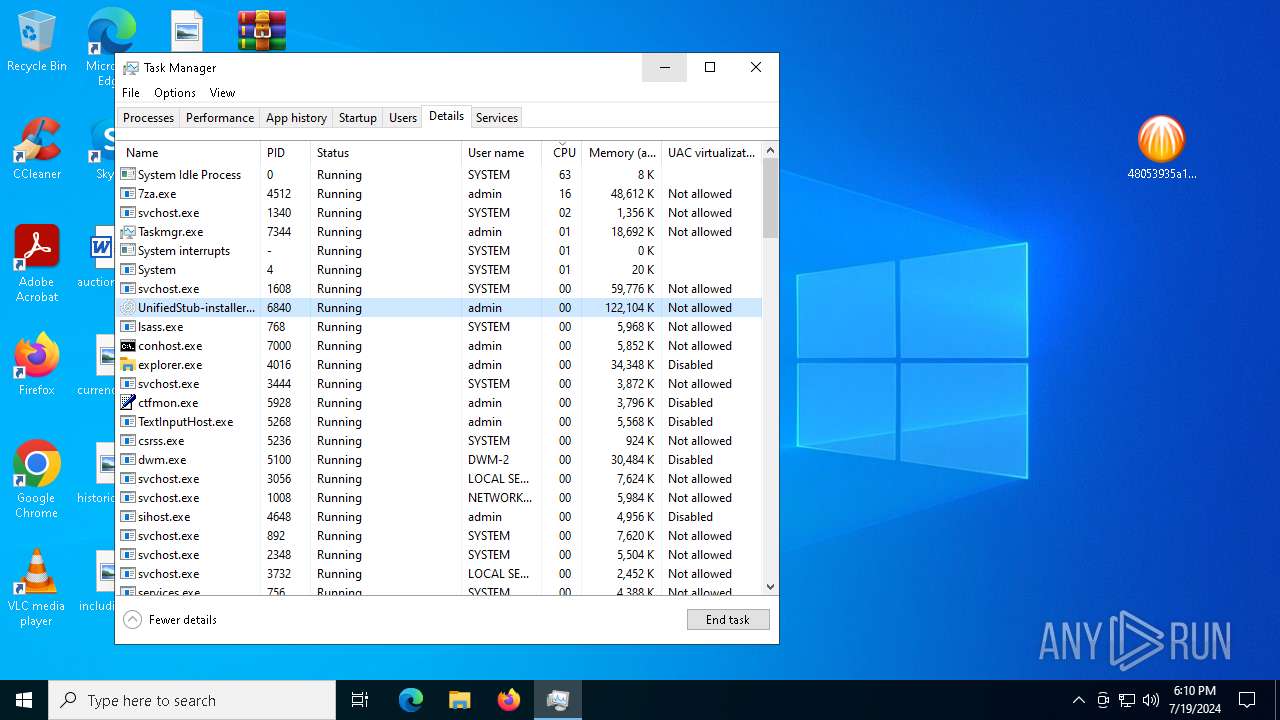
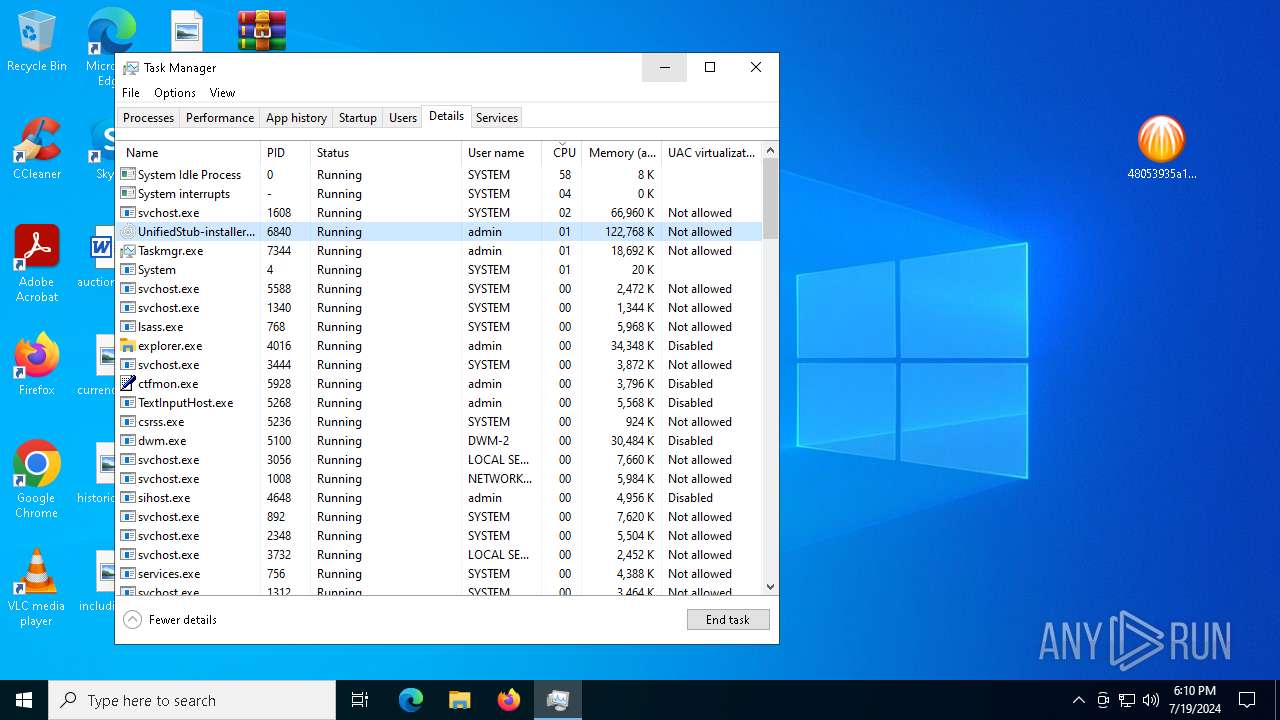
Drops the executable file immediately after the start
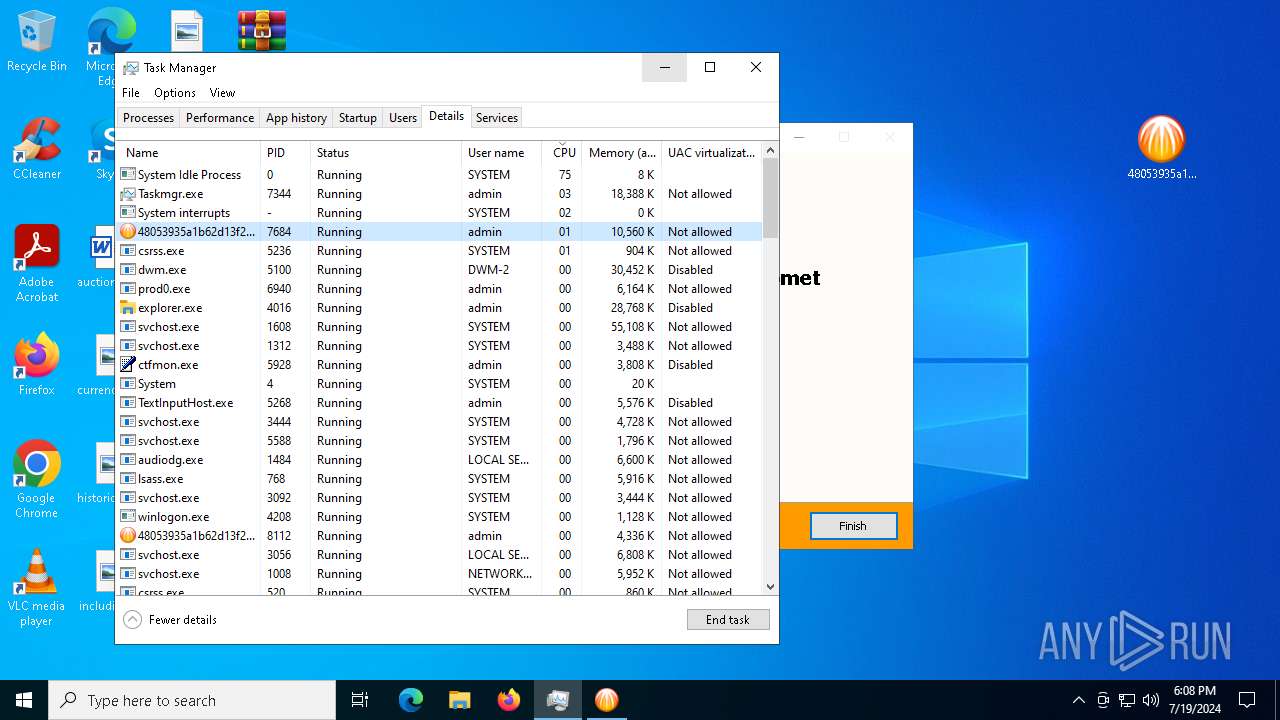
- WinRAR.exe (PID: 6800)
- 48053935a1b62d13f2a1301d42a3be930bb4718e8476c32b5050512209fdb3bb.exe (PID: 8112)
- 48053935a1b62d13f2a1301d42a3be930bb4718e8476c32b5050512209fdb3bb.tmp (PID: 7684)
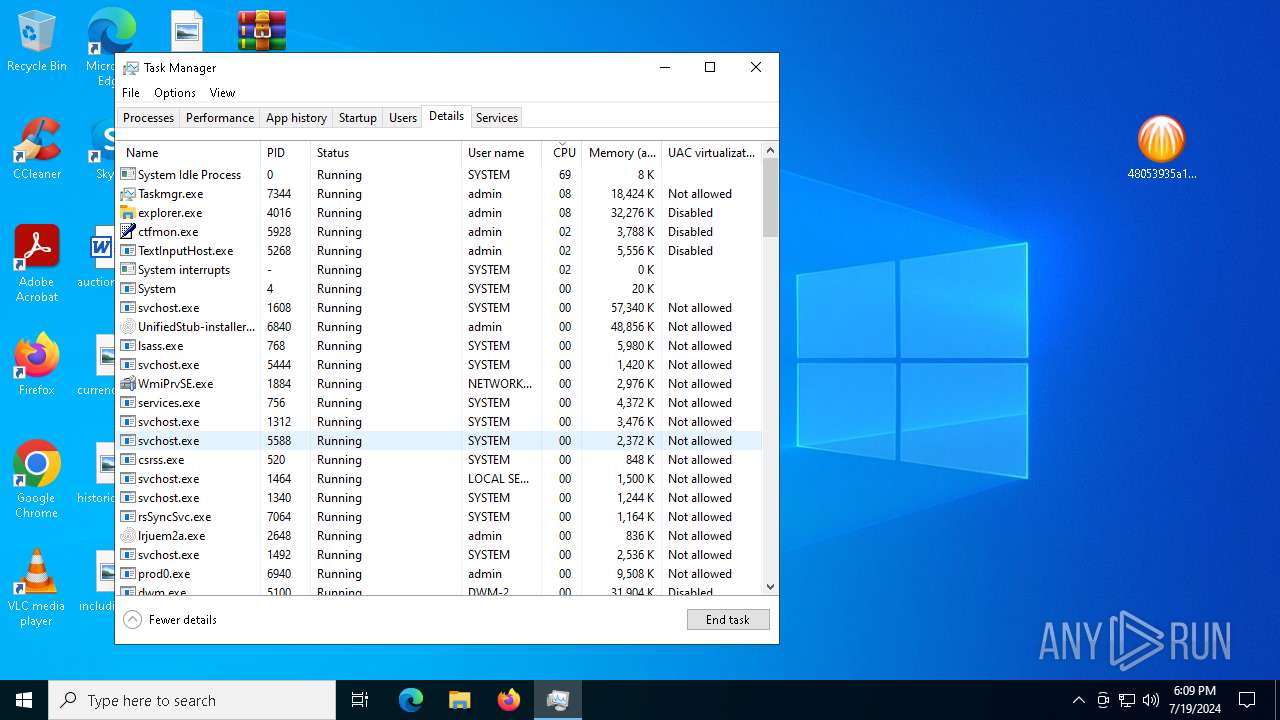
- prod0.exe (PID: 6940)
- lrjuem2a.exe (PID: 2648)
- 7za.exe (PID: 4796)
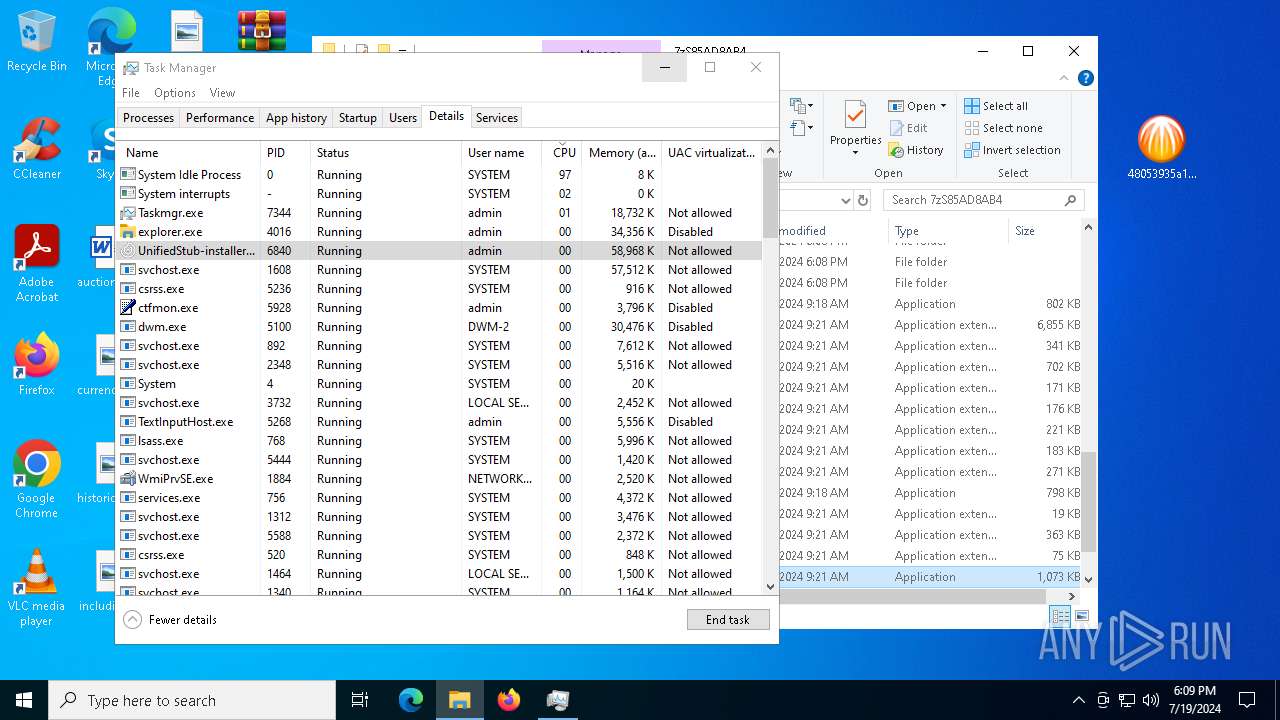
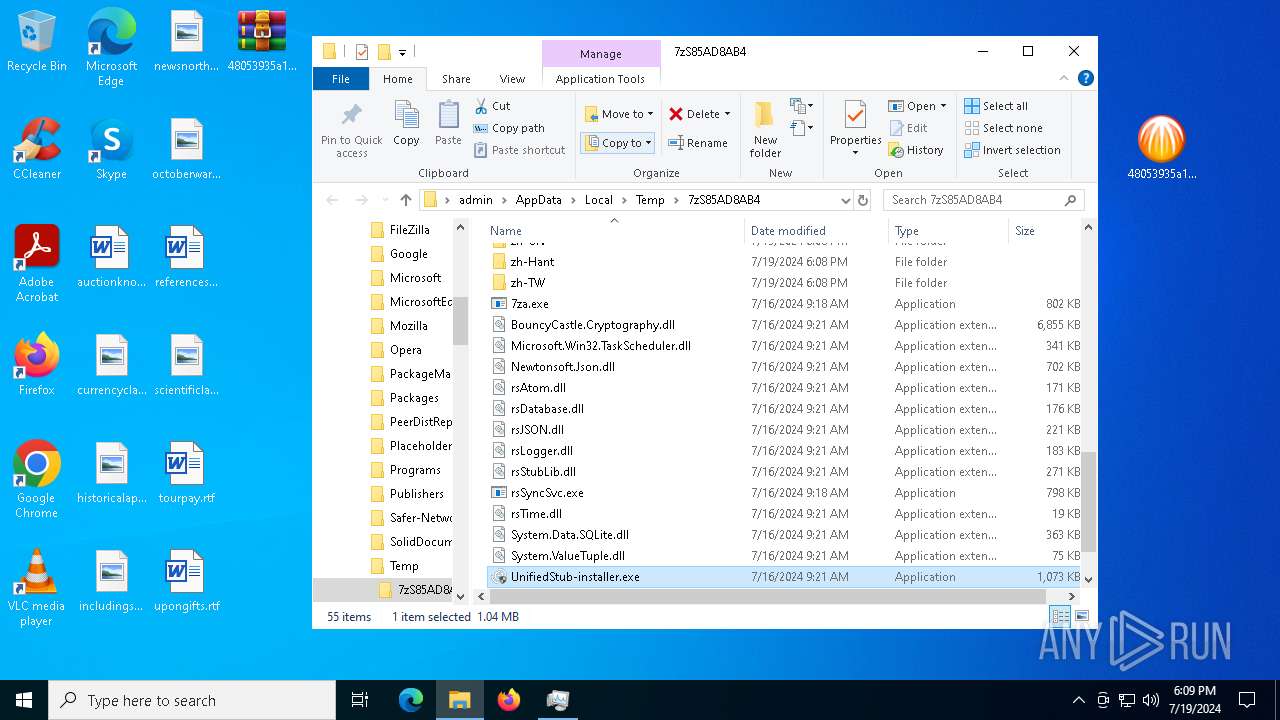
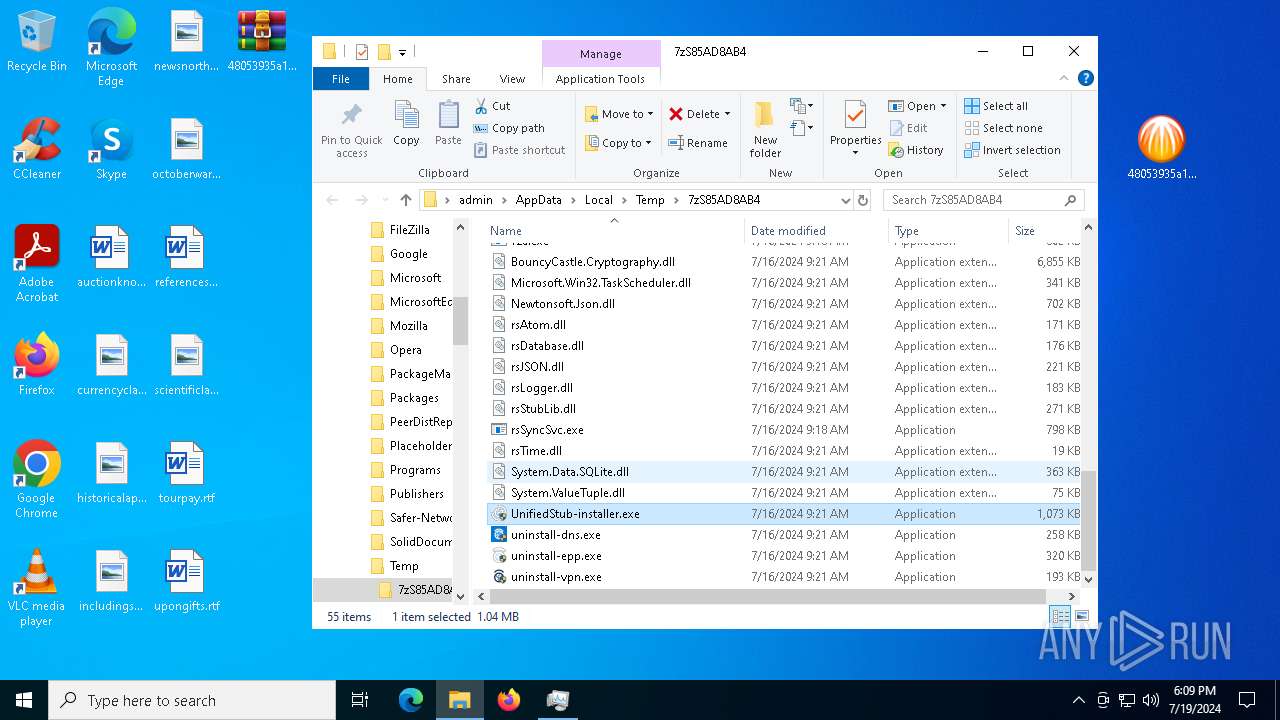
- UnifiedStub-installer.exe (PID: 6840)
- 7za.exe (PID: 4512)
Actions looks like stealing of personal data
- UnifiedStub-installer.exe (PID: 6840)
- rsEngineSvc.exe (PID: 3128)
Creates a writable file in the system directory
- UnifiedStub-installer.exe (PID: 6840)
- rsEDRSvc.exe (PID: 2276)
Changes the autorun value in the registry
- rundll32.exe (PID: 7936)
SUSPICIOUS
Executable content was dropped or overwritten
- 48053935a1b62d13f2a1301d42a3be930bb4718e8476c32b5050512209fdb3bb.exe (PID: 8112)
- 48053935a1b62d13f2a1301d42a3be930bb4718e8476c32b5050512209fdb3bb.tmp (PID: 7684)
- prod0.exe (PID: 6940)
- lrjuem2a.exe (PID: 2648)
- UnifiedStub-installer.exe (PID: 6840)
- 7za.exe (PID: 4796)
- 7za.exe (PID: 4512)
Reads the Windows owner or organization settings
- 48053935a1b62d13f2a1301d42a3be930bb4718e8476c32b5050512209fdb3bb.tmp (PID: 7684)
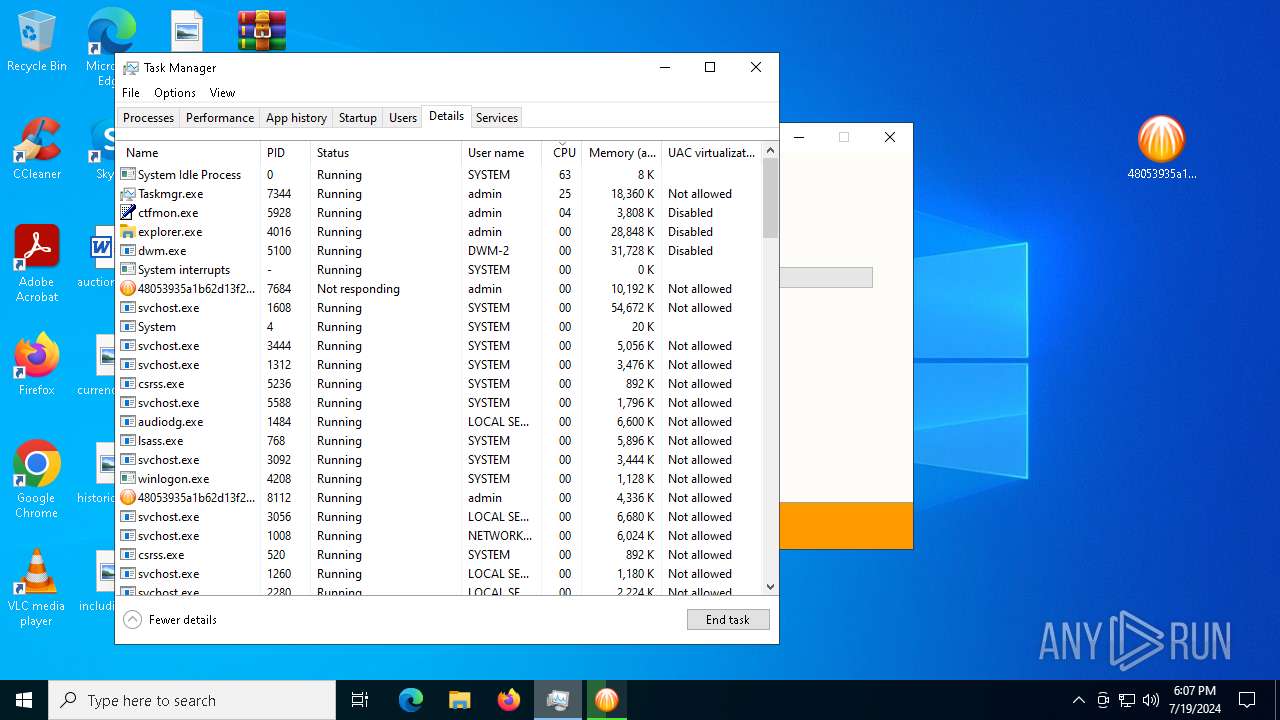
Application launched itself
- Taskmgr.exe (PID: 6932)
Reads the date of Windows installation
- 48053935a1b62d13f2a1301d42a3be930bb4718e8476c32b5050512209fdb3bb.tmp (PID: 7684)
- prod0.exe (PID: 6940)
- rsEDRSvc.exe (PID: 2276)
Reads security settings of Internet Explorer
- 48053935a1b62d13f2a1301d42a3be930bb4718e8476c32b5050512209fdb3bb.tmp (PID: 7684)
- prod0.exe (PID: 6940)
- UnifiedStub-installer.exe (PID: 6840)
- rsWSC.exe (PID: 3888)
- rsEngineSvc.exe (PID: 6276)
- rsEDRSvc.exe (PID: 3404)
Drops 7-zip archiver for unpacking
- lrjuem2a.exe (PID: 2648)
- 7za.exe (PID: 4512)
Process drops legitimate windows executable
- lrjuem2a.exe (PID: 2648)
- 7za.exe (PID: 4796)
- 7za.exe (PID: 4512)
- UnifiedStub-installer.exe (PID: 6840)
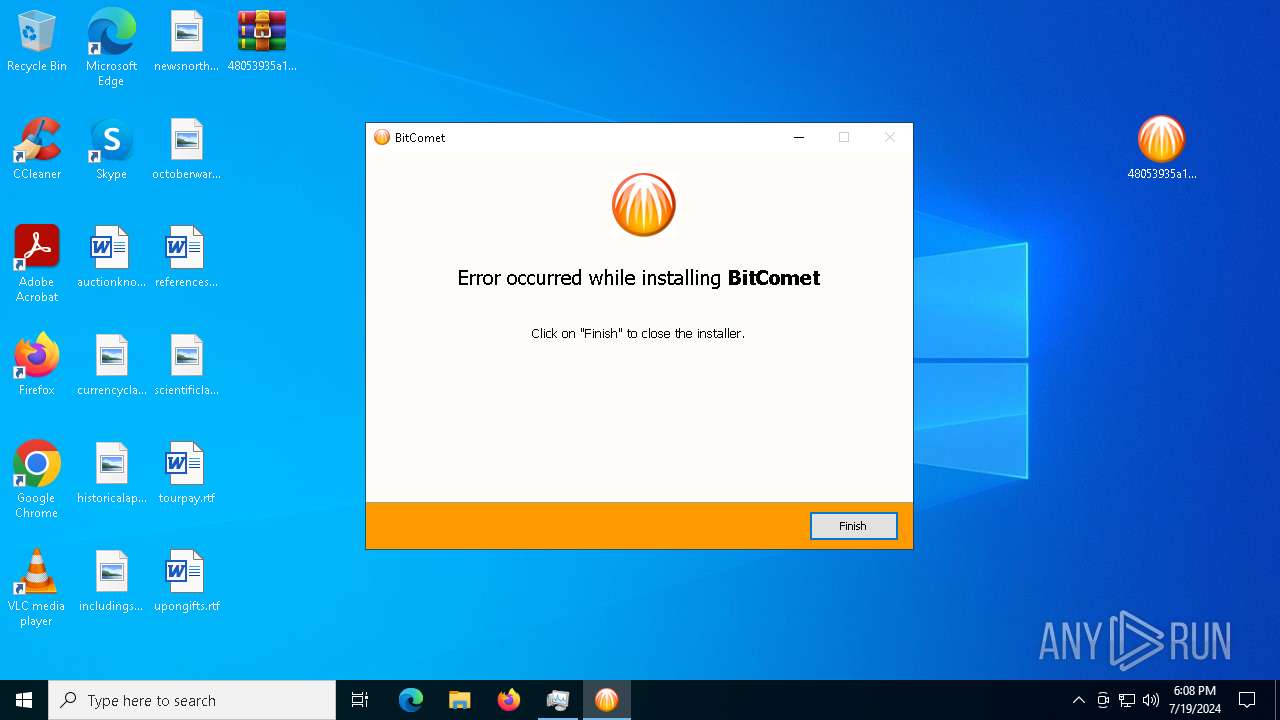
Executes application which crashes
- 48053935a1b62d13f2a1301d42a3be930bb4718e8476c32b5050512209fdb3bb.tmp (PID: 7684)
Creates a software uninstall entry
- UnifiedStub-installer.exe (PID: 6840)
Searches for installed software
- UnifiedStub-installer.exe (PID: 6840)
Executes as Windows Service
- rsSyncSvc.exe (PID: 7064)
- rsClientSvc.exe (PID: 6640)
- rsWSC.exe (PID: 2104)
- rsEngineSvc.exe (PID: 3128)
- rsEDRSvc.exe (PID: 2276)
The process creates files with name similar to system file names
- 7za.exe (PID: 4512)
The process drops C-runtime libraries
- 7za.exe (PID: 4512)
- UnifiedStub-installer.exe (PID: 6840)
Drops a system driver (possible attempt to evade defenses)
- 7za.exe (PID: 4512)
- UnifiedStub-installer.exe (PID: 6840)
Creates or modifies Windows services
- UnifiedStub-installer.exe (PID: 6840)
- rundll32.exe (PID: 7936)
Uses RUNDLL32.EXE to load library
- UnifiedStub-installer.exe (PID: 6840)
Uses WEVTUTIL.EXE to install publishers and event logs from the manifest
- UnifiedStub-installer.exe (PID: 6840)
Checks Windows Trust Settings
- rsWSC.exe (PID: 3888)
- rsEngineSvc.exe (PID: 6276)
- rsEDRSvc.exe (PID: 3404)
- rsEDRSvc.exe (PID: 2276)
- rsWSC.exe (PID: 2104)
Adds/modifies Windows certificates
- rsWSC.exe (PID: 3888)
- rsEngineSvc.exe (PID: 6276)
- rsEDRSvc.exe (PID: 2276)
Reads the BIOS version
- rsEDRSvc.exe (PID: 2276)
Process checks is Powershell's Script Block Logging on
- rsEDRSvc.exe (PID: 2276)
Creates files in the driver directory
- UnifiedStub-installer.exe (PID: 6840)
INFO
Executable content was dropped or overwritten
- WinRAR.exe (PID: 6800)
Reads the computer name
- 48053935a1b62d13f2a1301d42a3be930bb4718e8476c32b5050512209fdb3bb.tmp (PID: 7684)
- prod0.exe (PID: 6940)
- UnifiedStub-installer.exe (PID: 6840)
- rsSyncSvc.exe (PID: 7908)
- rsSyncSvc.exe (PID: 7064)
- 7za.exe (PID: 4796)
- 7za.exe (PID: 4512)
- rsWSC.exe (PID: 3888)
- rsClientSvc.exe (PID: 6640)
- rsEngineSvc.exe (PID: 6276)
- rsClientSvc.exe (PID: 6624)
- rsWSC.exe (PID: 2104)
- rsEngineSvc.exe (PID: 3128)
- rsEDRSvc.exe (PID: 3404)
- rsEDRSvc.exe (PID: 2276)
- rsHelper.exe (PID: 6668)
Manual execution by a user
- 48053935a1b62d13f2a1301d42a3be930bb4718e8476c32b5050512209fdb3bb.exe (PID: 8112)
- Taskmgr.exe (PID: 6932)
- Taskmgr.exe (PID: 8084)
Checks supported languages
- 48053935a1b62d13f2a1301d42a3be930bb4718e8476c32b5050512209fdb3bb.exe (PID: 8112)
- prod0.exe (PID: 6940)
- UnifiedStub-installer.exe (PID: 6840)
- lrjuem2a.exe (PID: 2648)
- rsSyncSvc.exe (PID: 7908)
- rsSyncSvc.exe (PID: 7064)
- 7za.exe (PID: 4796)
- 7za.exe (PID: 4512)
- rsWSC.exe (PID: 3888)
- rsEngineSvc.exe (PID: 6276)
- rsClientSvc.exe (PID: 6640)
- rsClientSvc.exe (PID: 6624)
- rsWSC.exe (PID: 2104)
- 48053935a1b62d13f2a1301d42a3be930bb4718e8476c32b5050512209fdb3bb.tmp (PID: 7684)
- rsEngineSvc.exe (PID: 3128)
- rsEDRSvc.exe (PID: 3404)
- rsEDRSvc.exe (PID: 2276)
- rsHelper.exe (PID: 6668)
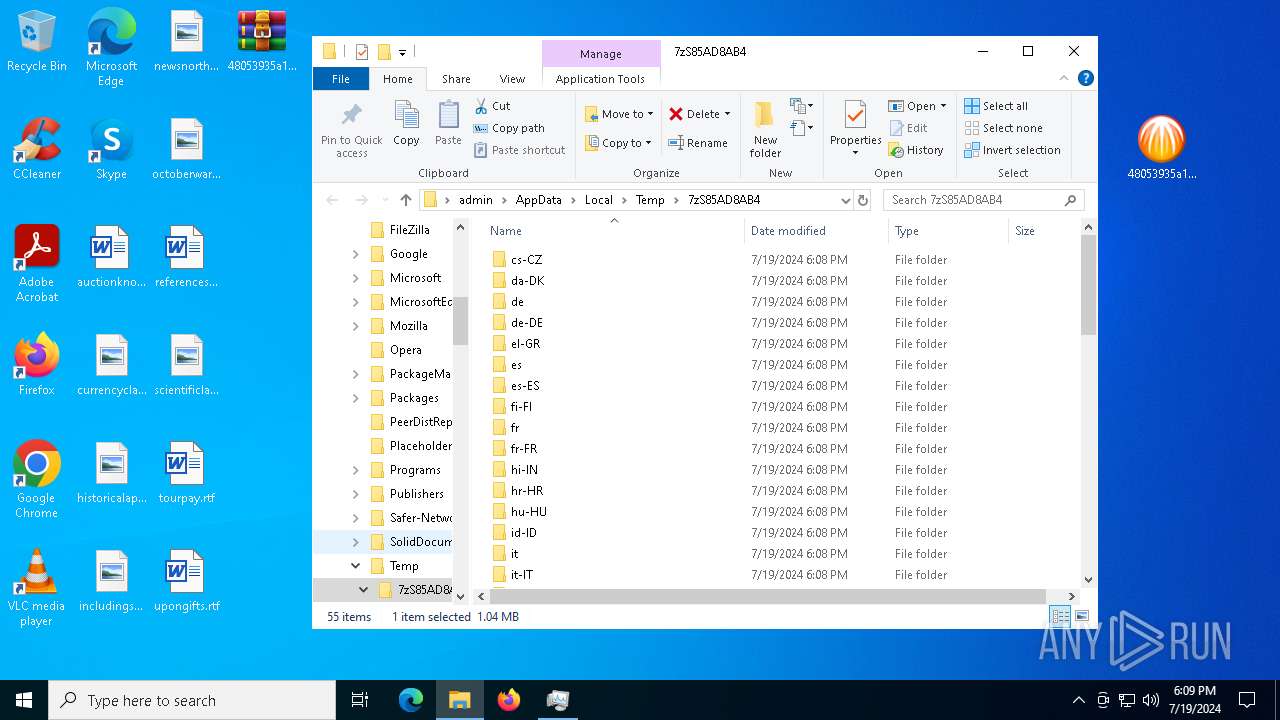
Create files in a temporary directory
- 48053935a1b62d13f2a1301d42a3be930bb4718e8476c32b5050512209fdb3bb.tmp (PID: 7684)
- 48053935a1b62d13f2a1301d42a3be930bb4718e8476c32b5050512209fdb3bb.exe (PID: 8112)
- prod0.exe (PID: 6940)
- lrjuem2a.exe (PID: 2648)
- UnifiedStub-installer.exe (PID: 6840)
Reads the software policy settings
- 48053935a1b62d13f2a1301d42a3be930bb4718e8476c32b5050512209fdb3bb.tmp (PID: 7684)
- prod0.exe (PID: 6940)
- UnifiedStub-installer.exe (PID: 6840)
- rsWSC.exe (PID: 3888)
- rsEngineSvc.exe (PID: 6276)
- rsEDRSvc.exe (PID: 3404)
- rsEDRSvc.exe (PID: 2276)
- rsEngineSvc.exe (PID: 3128)
- rsWSC.exe (PID: 2104)
Reads the machine GUID from the registry
- 48053935a1b62d13f2a1301d42a3be930bb4718e8476c32b5050512209fdb3bb.tmp (PID: 7684)
- prod0.exe (PID: 6940)
- UnifiedStub-installer.exe (PID: 6840)
- rsWSC.exe (PID: 3888)
- rsEngineSvc.exe (PID: 6276)
- rsWSC.exe (PID: 2104)
- rsEngineSvc.exe (PID: 3128)
- rsEDRSvc.exe (PID: 3404)
- rsEDRSvc.exe (PID: 2276)
- rsHelper.exe (PID: 6668)
Reads security settings of Internet Explorer
- Taskmgr.exe (PID: 6932)
- Taskmgr.exe (PID: 7344)
- runonce.exe (PID: 5300)
Process checks computer location settings
- 48053935a1b62d13f2a1301d42a3be930bb4718e8476c32b5050512209fdb3bb.tmp (PID: 7684)
- prod0.exe (PID: 6940)
Disables trace logs
- prod0.exe (PID: 6940)
- UnifiedStub-installer.exe (PID: 6840)
- rsEngineSvc.exe (PID: 3128)
- rsEDRSvc.exe (PID: 2276)
Checks proxy server information
- prod0.exe (PID: 6940)
- 48053935a1b62d13f2a1301d42a3be930bb4718e8476c32b5050512209fdb3bb.tmp (PID: 7684)
- UnifiedStub-installer.exe (PID: 6840)
- rsWSC.exe (PID: 3888)
- rsEngineSvc.exe (PID: 6276)
Reads Environment values
- prod0.exe (PID: 6940)
- UnifiedStub-installer.exe (PID: 6840)
- rsEDRSvc.exe (PID: 2276)
- rsEngineSvc.exe (PID: 3128)
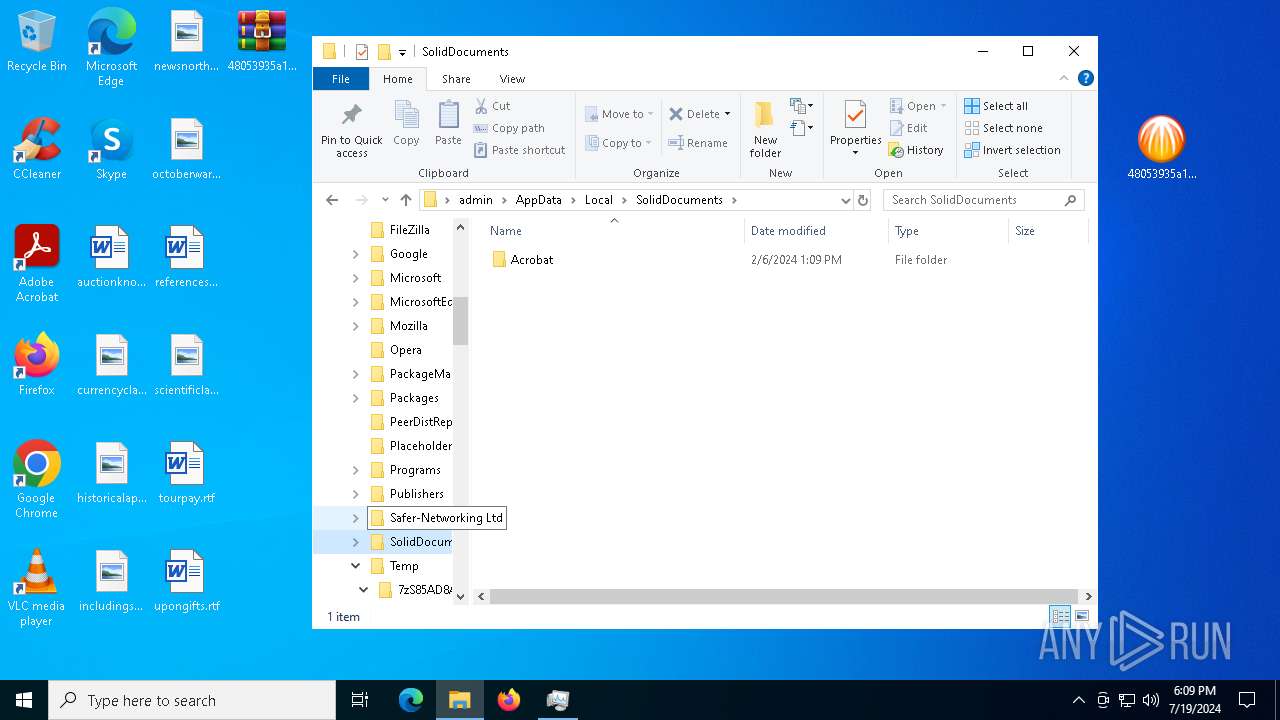
Creates files or folders in the user directory
- WerFault.exe (PID: 2276)
- WerFault.exe (PID: 2476)
- rsWSC.exe (PID: 3888)
- rsEngineSvc.exe (PID: 6276)
Creates files in the program directory
- UnifiedStub-installer.exe (PID: 6840)
- 7za.exe (PID: 4796)
- 7za.exe (PID: 4512)
- rsWSC.exe (PID: 3888)
- rsEngineSvc.exe (PID: 6276)
- rsEDRSvc.exe (PID: 3404)
- rsEngineSvc.exe (PID: 3128)
- rsEDRSvc.exe (PID: 2276)
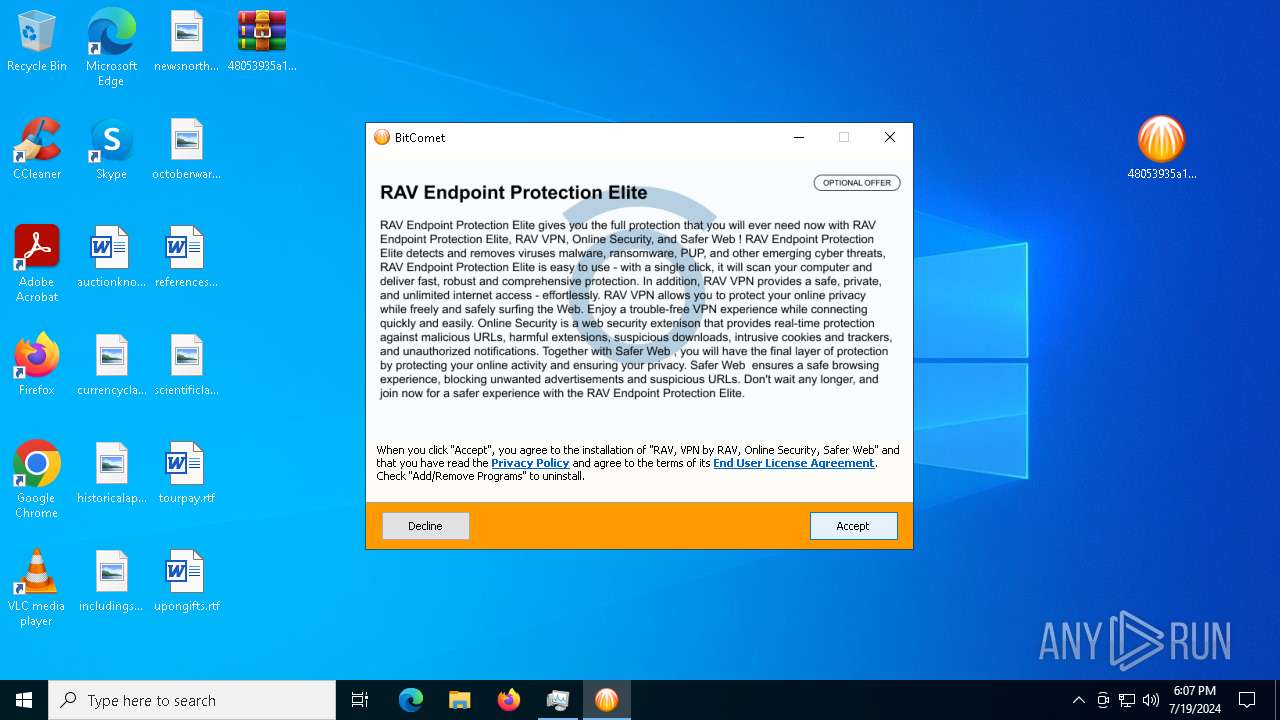
.NET Reactor protector has been detected
- UnifiedStub-installer.exe (PID: 6840)
Reads the time zone
- runonce.exe (PID: 5300)
- rsEDRSvc.exe (PID: 2276)
Reads product name
- rsEDRSvc.exe (PID: 2276)
Reads CPU info
- rsEDRSvc.exe (PID: 2276)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 51 |
|---|---|
| ZipBitFlag: | 0x0003 |
| ZipCompression: | Unknown (99) |
| ZipModifyDate: | 2024:07:19 18:05:12 |
| ZipCRC: | 0x000b524a |
| ZipCompressedSize: | 2020628 |
| ZipUncompressedSize: | 2576200 |
| ZipFileName: | 48053935a1b62d13f2a1301d42a3be930bb4718e8476c32b5050512209fdb3bb.exe |
Total processes
190
Monitored processes
40
Malicious processes
10
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2104 | "C:\Program Files\ReasonLabs\EPP\rsWSC.exe" | C:\Program Files\ReasonLabs\EPP\rsWSC.exe | — | services.exe | |||||||||||
User: SYSTEM Company: Reason Software Company Inc. Integrity Level: SYSTEM Description: rsWSC Version: 6.0.3.0 | |||||||||||||||
| 2276 | C:\WINDOWS\SysWOW64\WerFault.exe -u -p 7684 -s 1108 | C:\Windows\SysWOW64\WerFault.exe | — | 48053935a1b62d13f2a1301d42a3be930bb4718e8476c32b5050512209fdb3bb.tmp | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Problem Reporting Exit code: 0 Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2276 | "C:\Program Files\ReasonLabs\EDR\rsEDRSvc.exe" | C:\Program Files\ReasonLabs\EDR\rsEDRSvc.exe | services.exe | ||||||||||||
User: SYSTEM Company: Reason Cybersecurity Ltd. Integrity Level: SYSTEM Description: Reason EDR Service Version: 2.1.0 | |||||||||||||||
| 2476 | C:\WINDOWS\SysWOW64\WerFault.exe -u -p 7684 -s 1108 | C:\Windows\SysWOW64\WerFault.exe | — | 48053935a1b62d13f2a1301d42a3be930bb4718e8476c32b5050512209fdb3bb.tmp | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Problem Reporting Exit code: 0 Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2648 | "C:\Users\admin\AppData\Local\Temp\lrjuem2a.exe" /silent | C:\Users\admin\AppData\Local\Temp\lrjuem2a.exe | prod0.exe | ||||||||||||
User: admin Company: ReasonLabs Integrity Level: HIGH Description: ReasonLabs-setup-wizard.exe Version: 6.0.2 Modules
| |||||||||||||||
| 3128 | "C:\Program Files\ReasonLabs\EPP\rsEngineSvc.exe" | C:\Program Files\ReasonLabs\EPP\rsEngineSvc.exe | services.exe | ||||||||||||
User: SYSTEM Company: Reason Software Company Inc. Integrity Level: SYSTEM Description: rsEngineSvc Version: 3.2.0.0 | |||||||||||||||
| 3404 | "C:\Program Files\ReasonLabs\EDR\rsEDRSvc.exe" -i | C:\Program Files\ReasonLabs\EDR\rsEDRSvc.exe | — | UnifiedStub-installer.exe | |||||||||||
User: admin Company: Reason Cybersecurity Ltd. Integrity Level: HIGH Description: Reason EDR Service Exit code: 0 Version: 2.1.0 | |||||||||||||||
| 3412 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3776 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | wevtutil.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) | |||||||||||||||
| 3868 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | rsSyncSvc.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
27 681
Read events
27 539
Write events
109
Delete events
33
Modification events
| (PID) Process: | (6800) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (6800) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (6800) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\GoogleChromeEnterpriseBundle64.zip | |||
| (PID) Process: | (6800) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\48053935a1b62d13f2a1301d42a3be930bb4718e8476c32b5050512209fdb3bb.zip | |||
| (PID) Process: | (6800) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (6800) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (6800) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (6800) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (6800) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface |
| Operation: | write | Name: | ShowPassword |
Value: 0 | |||
| (PID) Process: | (6800) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\MainWin |
| Operation: | write | Name: | Placement |
Value: 2C0000000000000001000000FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF3D0000002D000000FD03000016020000 | |||
Executable files
507
Suspicious files
115
Text files
36
Unknown types
9
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6940 | prod0.exe | C:\Users\admin\AppData\Local\Temp\lrjuem2a.exe | executable | |
MD5:062179B7A046F091EB962CFE5033AF4E | SHA256:D3A5919C470CEB6A4CED211312C78548F0BDA633AB81790C19C1C6B57C3E92B9 | |||
| 2648 | lrjuem2a.exe | C:\Users\admin\AppData\Local\Temp\7zS85AD8AB4\BouncyCastle.Cryptography.dll | executable | |
MD5:22A8DB8233A2FCFC493852AE9ECEBB94 | SHA256:27504EDF2DADE4A83799C579179E72DAD089C6278895403D84206A1D027429EB | |||
| 7684 | 48053935a1b62d13f2a1301d42a3be930bb4718e8476c32b5050512209fdb3bb.tmp | C:\Users\admin\AppData\Local\Temp\is-1KONN.tmp\RAV_Cross.png | image | |
MD5:CD09F361286D1AD2622BA8A57B7613BD | SHA256:B92A31D4853D1B2C4E5B9D9624F40B439856D0C6A517E100978CBDE8D3C47DC8 | |||
| 7684 | 48053935a1b62d13f2a1301d42a3be930bb4718e8476c32b5050512209fdb3bb.tmp | C:\Users\admin\AppData\Local\Temp\is-1KONN.tmp\is-DIN1N.tmp | executable | |
MD5:1022CAF4E4E64D0189DC318EAC950C9E | SHA256:FF16FADDE46E59DBC4881858BD8EC8B63804F0FD959BBB086C2007D9F9DE073A | |||
| 7684 | 48053935a1b62d13f2a1301d42a3be930bb4718e8476c32b5050512209fdb3bb.tmp | C:\Users\admin\AppData\Local\Temp\is-1KONN.tmp\prod0.exe | executable | |
MD5:9EFB4669A19BFBDEB032BDC5F3F26382 | SHA256:68FA3EA087ED3C9089BB648C95F3A53078AC4C962F5BC7369B16DD2B0E450DF8 | |||
| 7684 | 48053935a1b62d13f2a1301d42a3be930bb4718e8476c32b5050512209fdb3bb.tmp | C:\Users\admin\AppData\Local\Temp\is-1KONN.tmp\error.png | image | |
MD5:84655B67373CBF75DF620481A2A2C092 | SHA256:DE17422973741F1F199B5654095D759D92A737E51BBD6A0AAE1A1D695E3C334E | |||
| 7684 | 48053935a1b62d13f2a1301d42a3be930bb4718e8476c32b5050512209fdb3bb.tmp | C:\Users\admin\AppData\Local\Temp\is-1KONN.tmp\is-NPHGG.tmp | executable | |
MD5:9EFB4669A19BFBDEB032BDC5F3F26382 | SHA256:68FA3EA087ED3C9089BB648C95F3A53078AC4C962F5BC7369B16DD2B0E450DF8 | |||
| 2648 | lrjuem2a.exe | C:\Users\admin\AppData\Local\Temp\7zS85AD8AB4\7za.exe | executable | |
MD5:8F57948E69C82BF98704F129C5460576 | SHA256:F00836A63BE7EBF14E1B8C40100C59777FE3432506B330927EA1F1B7FD47EE44 | |||
| 7684 | 48053935a1b62d13f2a1301d42a3be930bb4718e8476c32b5050512209fdb3bb.tmp | C:\Users\admin\AppData\Local\Temp\is-1KONN.tmp\_isetup\_setup64.tmp | executable | |
MD5:E4211D6D009757C078A9FAC7FF4F03D4 | SHA256:388A796580234EFC95F3B1C70AD4CB44BFDDC7BA0F9203BF4902B9929B136F95 | |||
| 8112 | 48053935a1b62d13f2a1301d42a3be930bb4718e8476c32b5050512209fdb3bb.exe | C:\Users\admin\AppData\Local\Temp\is-R415F.tmp\48053935a1b62d13f2a1301d42a3be930bb4718e8476c32b5050512209fdb3bb.tmp | executable | |
MD5:DD40149397C65DB7E46877143552AAC5 | SHA256:F4E460EDDF3D8408AE887AC53FE96906A3B534D99A5FD9C3FE7777948293D1F7 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
24
TCP/UDP connections
77
DNS requests
32
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3888 | rsWSC.exe | GET | 200 | 172.64.149.23:80 | http://ocsp.sectigo.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQRz3ETyLz2DaZTxGOH%2BA%2BjK7MkGAQUJGWTmAgB6E7U1kzqZFXhwPr7z7MCEAeSK29bdU5YKBXAnjHx1BY%3D | unknown | — | — | whitelisted |
3888 | rsWSC.exe | GET | 200 | 172.64.149.23:80 | http://ocsp.usertrust.com/MFIwUDBOMEwwSjAJBgUrDgMCGgUABBTNMNJMNDqCqx8FcBWK16EHdimS6QQUU3m%2FWqorSs9UgOHYm8Cd8rIDZssCEQCeArDpSs6yEJyh6YNr4MLb | unknown | — | — | whitelisted |
6276 | rsEngineSvc.exe | GET | 200 | 204.79.197.203:80 | http://oneocsp.microsoft.com/ocsp/MFQwUjBQME4wTDAJBgUrDgMCGgUABBTDHsfuqfubd3pihvq4mgQVWgHWNwQUyH7SaoUqG8oZmAQHJ89QEE9oqKICEzMAAAAHh6M0o3uljhwAAAAAAAc%3D | unknown | — | — | whitelisted |
6276 | rsEngineSvc.exe | GET | 200 | 204.79.197.203:80 | http://oneocsp.microsoft.com/ocsp/MFQwUjBQME4wTDAJBgUrDgMCGgUABBTOQYLFSE5GO%2FpaRVfYu7d9gZEbQAQU2UEpsA8PY2zvadf1zSmepEhqMOYCEzMAAAAHN4xbodlbjNQAAAAAAAc%3D | unknown | — | — | whitelisted |
6276 | rsEngineSvc.exe | GET | 200 | 204.79.197.203:80 | http://oneocsp.microsoft.com/ocsp/MFQwUjBQME4wTDAJBgUrDgMCGgUABBRBq81UG1MnDOVNKqff0SSEz6JuZwQU6IPEM9fcnwycdpoKptTfh6ZeWO4CEzMAATXj8%2BWM%2BdRgn3UAAAABNeM%3D | unknown | — | — | whitelisted |
2276 | rsEDRSvc.exe | GET | 200 | 204.79.197.203:80 | http://oneocsp.microsoft.com/ocsp/MFQwUjBQME4wTDAJBgUrDgMCGgUABBTDHsfuqfubd3pihvq4mgQVWgHWNwQUyH7SaoUqG8oZmAQHJ89QEE9oqKICEzMAAAAHh6M0o3uljhwAAAAAAAc%3D | unknown | — | — | whitelisted |
2276 | rsEDRSvc.exe | GET | 200 | 204.79.197.203:80 | http://oneocsp.microsoft.com/ocsp/MFQwUjBQME4wTDAJBgUrDgMCGgUABBTOQYLFSE5GO%2FpaRVfYu7d9gZEbQAQU2UEpsA8PY2zvadf1zSmepEhqMOYCEzMAAAAHN4xbodlbjNQAAAAAAAc%3D | unknown | — | — | whitelisted |
2276 | rsEDRSvc.exe | GET | 200 | 204.79.197.203:80 | http://oneocsp.microsoft.com/ocsp/MFQwUjBQME4wTDAJBgUrDgMCGgUABBRBq81UG1MnDOVNKqff0SSEz6JuZwQU6IPEM9fcnwycdpoKptTfh6ZeWO4CEzMAATXj8%2BWM%2BdRgn3UAAAABNeM%3D | unknown | — | — | whitelisted |
2276 | rsEDRSvc.exe | GET | 200 | 88.221.169.152:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20Identity%20Verification%20Root%20Certificate%20Authority%202020.crl | unknown | — | — | whitelisted |
2276 | rsEDRSvc.exe | GET | 200 | 88.221.169.152:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20Public%20RSA%20Timestamping%20CA%202020.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4716 | svchost.exe | 40.126.31.67:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5620 | MoUsoCoreWorker.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
7856 | svchost.exe | 4.208.221.206:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | US | unknown |
4032 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
2760 | svchost.exe | 40.113.110.67:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
7320 | slui.exe | 20.83.72.98:443 | activation-v2.sls.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
4716 | svchost.exe | 20.190.159.64:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
3444 | svchost.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
login.live.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
activation-v2.sls.microsoft.com |
| whitelisted |
arc.msn.com |
| whitelisted |
www.bing.com |
| whitelisted |
fd.api.iris.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
d11iilsblp9z11.cloudfront.net |
| whitelisted |