| File name: | GUI Turbo Assembler v5.0.msi |
| Full analysis: | https://app.any.run/tasks/b1ff1e3e-9d3a-449f-b1fa-c329dafb7a11 |
| Verdict: | Malicious activity |
| Analysis date: | October 26, 2023, 07:55:02 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-msi |
| File info: | Composite Document File V2 Document, Little Endian, Os: Windows, Version 10.0, MSI Installer, Create Time/Date: Mon Jun 21 08:00:00 1999, Name of Creating Application: Windows Installer, Security: 1, Code page: 1252, Template: ;1033, Number of Pages: 200, Revision Number: {2B855D75-8C6B-447F-843E-D65315C767D3}, Title: GUI Turbo Assembler, Author: Lakhya Jyoti Nath, Keywords: tasm,tlink,td,guitasm,gui, Comments: An essential 32-64bit localized IDE for Assembly Language with TASM, TLINK and TD, Number of Words: 2, Last Saved Time/Date: Wed Oct 18 23:13:10 2023, Last Printed: Wed Oct 18 23:13:10 2023 |
| MD5: | 709E77A4DBBC7192D73EF47C722348AB |
| SHA1: | D8C96690F3D9CDBB131B162575E4967EBB5555F9 |
| SHA256: | 8FCC26490CE579D25C8A30ABDF01655E7963F4CF191A8528CABDA597557FA727 |
| SSDEEP: | 98304:kB0el1eIIeaSlSfRK8MZMT9ameTZY7A3vYBLUAYrbyjSTwKA9u2xFT8K2+E8kDxl:a2HJajTeBM2 |
MALICIOUS
Application was dropped or rewritten from another process
- GUI Turbo Assembler.exe (PID: 4072)
- GUI Turbo Assembler.exe (PID: 3580)
- AL.exe (PID: 3508)
Loads dropped or rewritten executable
- GUI Turbo Assembler.exe (PID: 3580)
Drops the executable file immediately after the start
- msiexec.exe (PID: 568)
SUSPICIOUS
Process drops legitimate windows executable
- msiexec.exe (PID: 1824)
- msiexec.exe (PID: 568)
Executes as Windows Service
- VSSVC.exe (PID: 3016)
Reads the Internet Settings
- GUI Turbo Assembler.exe (PID: 3580)
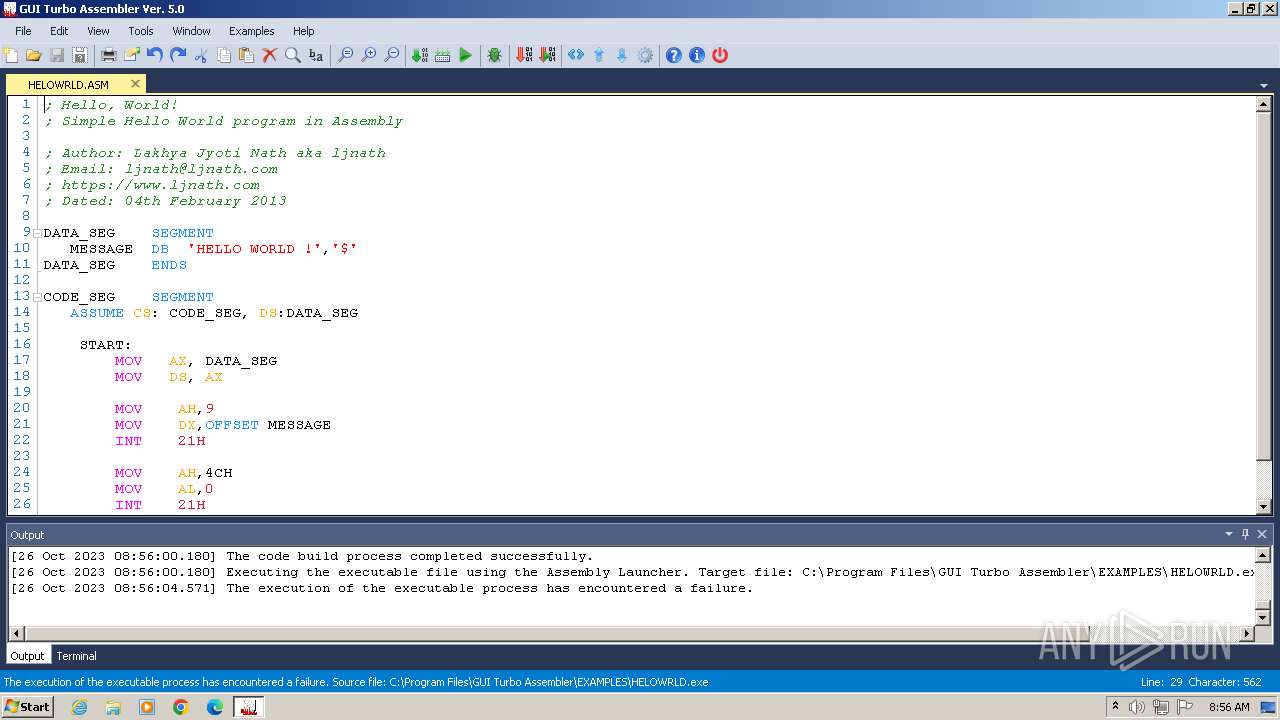
Starts CMD.EXE for commands execution
- GUI Turbo Assembler.exe (PID: 3580)
- AL.exe (PID: 3508)
Reads settings of System Certificates
- GUI Turbo Assembler.exe (PID: 3580)
Changes default file association
- msiexec.exe (PID: 568)
The process drops C-runtime libraries
- msiexec.exe (PID: 568)
INFO
Reads the computer name
- msiexec.exe (PID: 568)
- msiexec.exe (PID: 3792)
- msiexec.exe (PID: 2512)
- GUI Turbo Assembler.exe (PID: 3580)
Checks supported languages
- msiexec.exe (PID: 568)
- msiexec.exe (PID: 3792)
- msiexec.exe (PID: 2512)
- GUI Turbo Assembler.exe (PID: 3580)
- AL.exe (PID: 3508)
Create files in a temporary directory
- msiexec.exe (PID: 3792)
- msiexec.exe (PID: 2512)
- GUI Turbo Assembler.exe (PID: 3580)
- msiexec.exe (PID: 568)
Reads the machine GUID from the registry
- msiexec.exe (PID: 568)
- msiexec.exe (PID: 3792)
- msiexec.exe (PID: 2512)
- GUI Turbo Assembler.exe (PID: 3580)
Application launched itself
- msiexec.exe (PID: 568)
Drops the executable file immediately after the start
- msiexec.exe (PID: 1824)
- ntvdm.exe (PID: 1044)
Manual execution by a user
- GUI Turbo Assembler.exe (PID: 4072)
- GUI Turbo Assembler.exe (PID: 3580)
Reads Environment values
- GUI Turbo Assembler.exe (PID: 3580)
Creates files or folders in the user directory
- GUI Turbo Assembler.exe (PID: 3580)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .msi | | | Microsoft Windows Installer (90.2) |
|---|---|---|
| .msp | | | Windows Installer Patch (8.4) |
| .msi | | | Microsoft Installer (100) |
EXIF
FlashPix
| CreateDate: | 1999:06:21 07:00:00 |
|---|---|
| Software: | Windows Installer |
| Security: | Password protected |
| CodePage: | Windows Latin 1 (Western European) |
| Template: | ;1033 |
| Pages: | 200 |
| RevisionNumber: | {2B855D75-8C6B-447F-843E-D65315C767D3} |
| Title: | GUI Turbo Assembler |
| Subject: | - |
| Author: | Lakhya Jyoti Nath |
| Keywords: | tasm,tlink,td,guitasm,gui |
| Comments: | An essential 32-64bit localized IDE for Assembly Language with TASM, TLINK and TD |
| Words: | 2 |
| ModifyDate: | 2023:10:18 22:13:10 |
| LastPrinted: | 2023:10:18 22:13:10 |
Total processes
63
Monitored processes
17
Malicious processes
3
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 568 | C:\Windows\system32\msiexec.exe /V | C:\Windows\System32\msiexec.exe | — | services.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows® installer Exit code: 0 Version: 5.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 892 | "C:\Windows\system32\ntvdm.exe" | C:\Windows\System32\ntvdm.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: NTVDM.EXE Exit code: 255 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1044 | "C:\Windows\system32\ntvdm.exe" | C:\Windows\System32\ntvdm.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: NTVDM.EXE Exit code: 255 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1336 | "cmd.exe" /c AL "C:\Program Files\GUI Turbo Assembler\EXAMPLES\HELOWRLD.exe" | C:\Windows\System32\cmd.exe | — | GUI Turbo Assembler.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 3221225547 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 1736 | C:\Windows\system32\cmd.exe /c cls | C:\Windows\System32\cmd.exe | — | AL.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 1824 | "C:\Windows\System32\msiexec.exe" /i "C:\Users\admin\AppData\Local\Temp\GUI Turbo Assembler v5.0.msi" | C:\Windows\System32\msiexec.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows® installer Exit code: 0 Version: 5.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
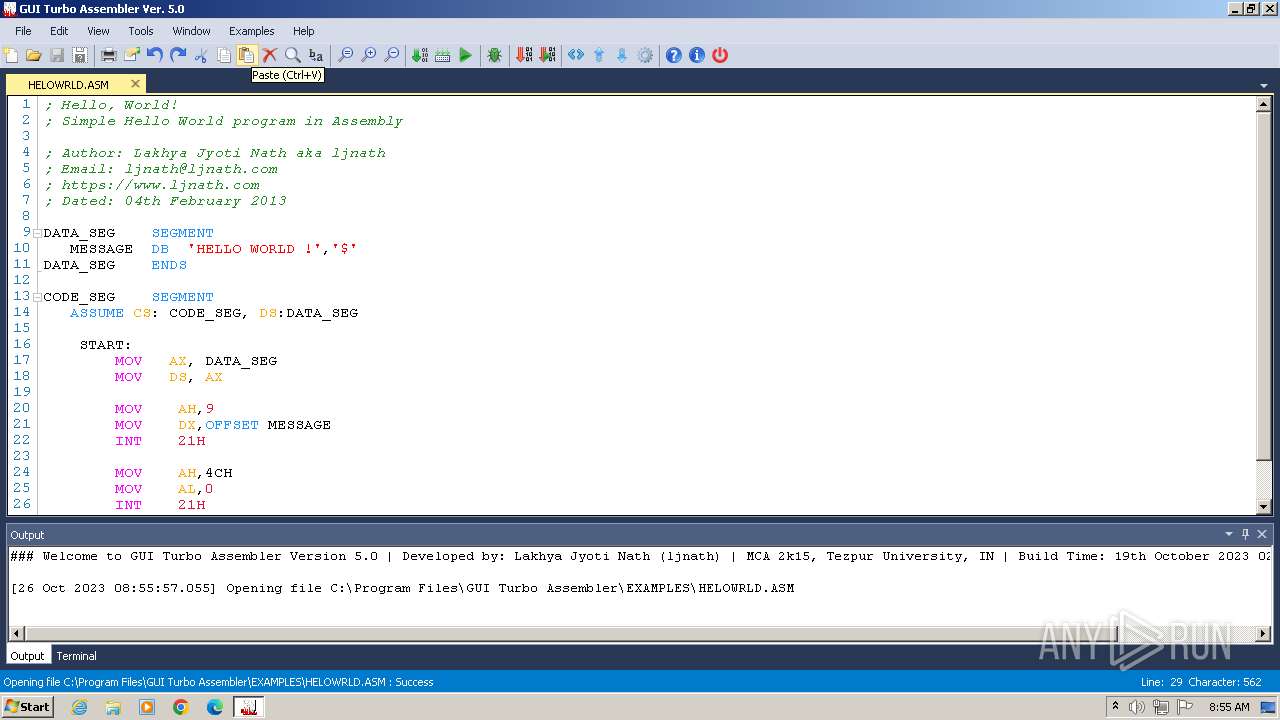
| 1864 | "cmd.exe" /c TASM /z /zi HELOWRLD.ASM | C:\Windows\System32\cmd.exe | — | GUI Turbo Assembler.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
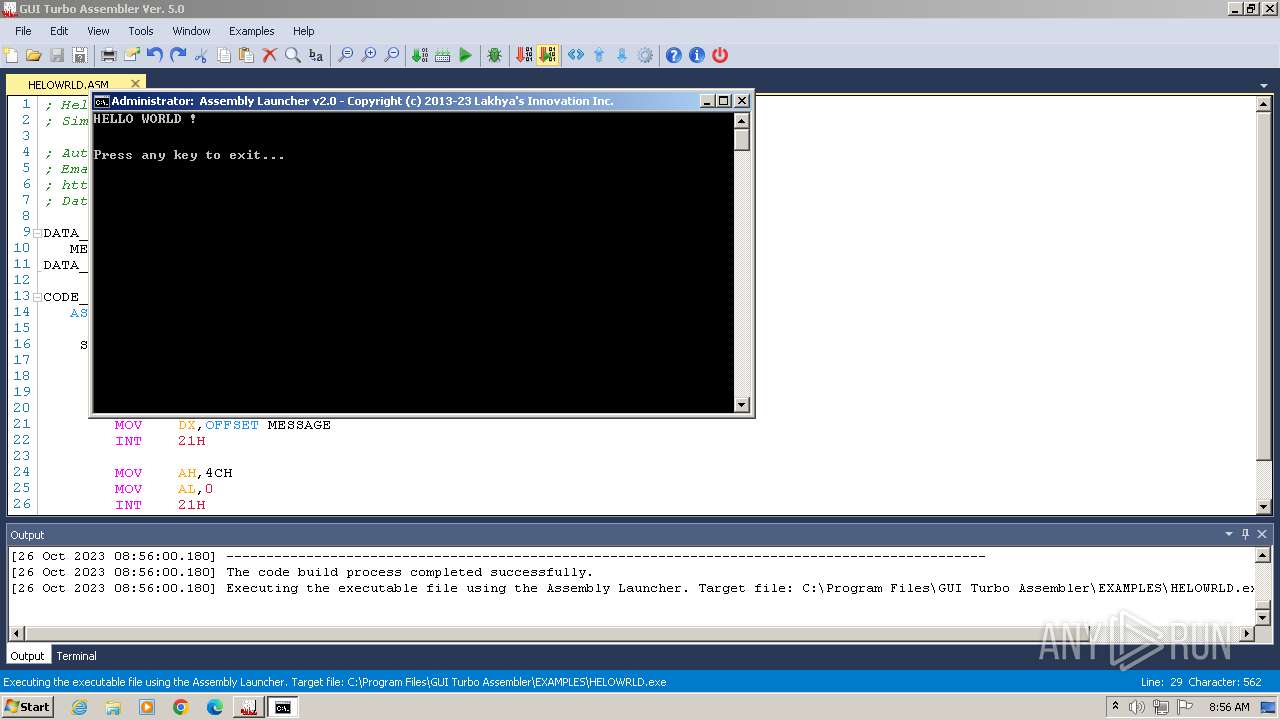
| 1872 | C:\Windows\system32\cmd.exe /c "C:\Program Files\GUI Turbo Assembler\EXAMPLES\HELOWRLD.exe" | C:\Windows\System32\cmd.exe | — | AL.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
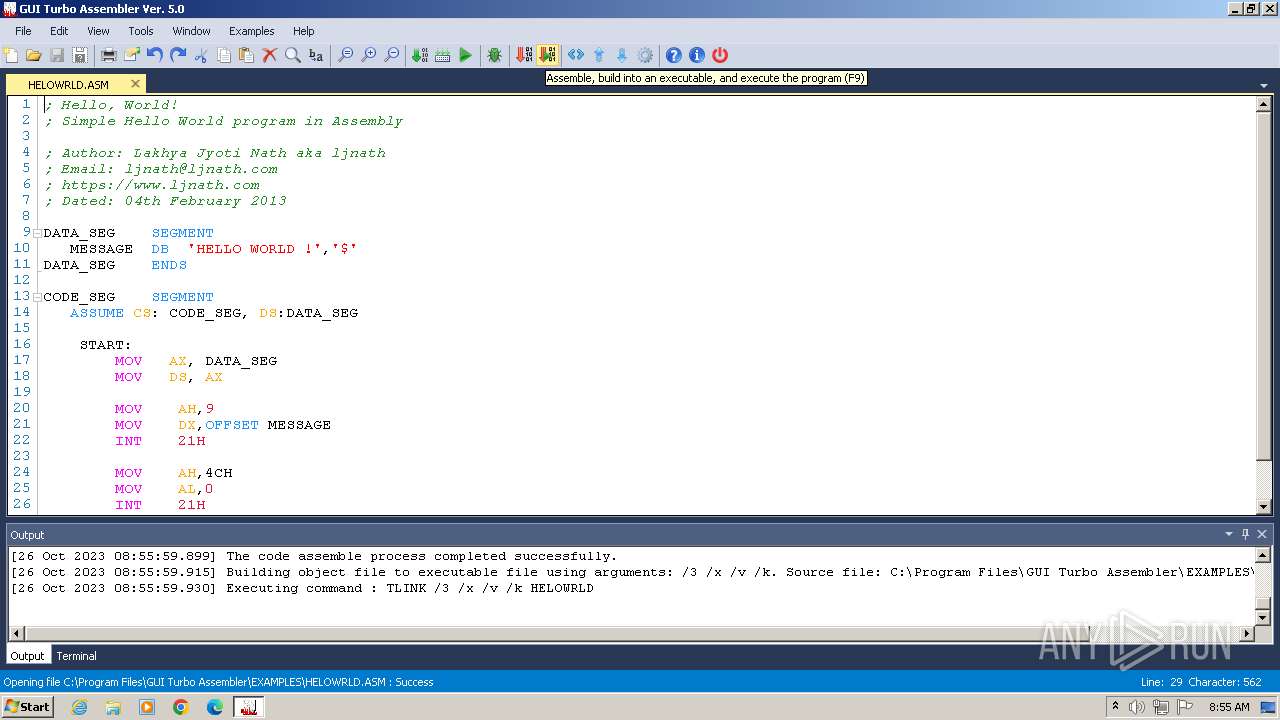
| 2052 | "cmd.exe" /c TLINK /3 /x /v /k HELOWRLD | C:\Windows\System32\cmd.exe | — | GUI Turbo Assembler.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 2372 | "C:\Windows\system32\ntvdm.exe" | C:\Windows\System32\ntvdm.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: NTVDM.EXE Exit code: 255 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
8 588
Read events
8 537
Write events
40
Delete events
11
Modification events
| (PID) Process: | (568) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\VSS\Diag\SystemRestore |
| Operation: | write | Name: | SrCreateRp (Enter) |
Value: 4000000000000000F2B487BA16B0D901C80700002C0A0000D5070000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (568) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\VSS\Diag\SPP |
| Operation: | write | Name: | SppCreate (Enter) |
Value: 4000000000000000F2B487BA16B0D901C80700002C0A0000D0070000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (568) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\SPP |
| Operation: | write | Name: | LastIndex |
Value: 72 | |||
| (PID) Process: | (568) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\VSS\Diag\SPP |
| Operation: | write | Name: | SppGatherWriterMetadata (Enter) |
Value: 40000000000000008C62D6BA16B0D901C80700002C0A0000D3070000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (568) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\VSS\Diag\SPP |
| Operation: | write | Name: | SppGatherWriterMetadata (Leave) |
Value: 400000000000000064514ABC16B0D901C80700002C0A0000D3070000010000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (568) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\VSS\Diag\SPP |
| Operation: | write | Name: | SppAddInterestingComponents (Enter) |
Value: 400000000000000064514ABC16B0D901C80700002C0A0000D4070000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (568) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\VSS\Diag\SPP |
| Operation: | write | Name: | SppAddInterestingComponents (Leave) |
Value: 400000000000000034645DBC16B0D901C80700002C0A0000D4070000010000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (568) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\VSS\Diag\SPP |
| Operation: | write | Name: | SppCreate (Leave) |
Value: 4000000000000000781D5ABD16B0D901C80700002C0A0000D0070000010000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (568) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\VSS\Diag\SystemRestore |
| Operation: | write | Name: | SrCreateRp (Leave) |
Value: 4000000000000000781D5ABD16B0D901C80700002C0A0000D5070000010000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (568) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\SystemRestore |
| Operation: | write | Name: | FirstRun |
Value: 0 | |||
Executable files
72
Suspicious files
63
Text files
202
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 568 | msiexec.exe | C:\System Volume Information\SPP\metadata-2 | — | |
MD5:— | SHA256:— | |||
| 568 | msiexec.exe | C:\Windows\Installer\1f2052.msi | — | |
MD5:— | SHA256:— | |||
| 568 | msiexec.exe | C:\Users\admin\AppData\Local\Temp\~DF94474BBE873361BD.TMP | binary | |
MD5:C48D4AED1FD6C8A18B24FB4F9B3A7019 | SHA256:9C75E1478DA2B35FE215BD0F8A42179289BFFD856864168FE0B2239F4E7497CE | |||
| 1824 | msiexec.exe | C:\Users\admin\AppData\Local\Temp\MSIAE8D.tmp | executable | |
MD5:684F2D21637CB5835172EDAD55B6A8D9 | SHA256:DA1FE86141C446921021BB26B6FE2BD2D1BB51E3E614F46F8103FFAD8042F2C0 | |||
| 1824 | msiexec.exe | C:\Users\admin\AppData\Local\Temp\MSIAEEC.tmp | executable | |
MD5:684F2D21637CB5835172EDAD55B6A8D9 | SHA256:DA1FE86141C446921021BB26B6FE2BD2D1BB51E3E614F46F8103FFAD8042F2C0 | |||
| 3792 | msiexec.exe | C:\Users\admin\AppData\Local\Temp\CFGAEDB.tmp | xml | |
MD5:FDBBDB01EBC78A136A78F17E1E2E40D8 | SHA256:A0314FF4CB7D286BCF94CF5B862E96122DDF6FEA6AF1014B71253E04CF67C94B | |||
| 568 | msiexec.exe | C:\Windows\Installer\MSI2294.tmp | executable | |
MD5:684F2D21637CB5835172EDAD55B6A8D9 | SHA256:DA1FE86141C446921021BB26B6FE2BD2D1BB51E3E614F46F8103FFAD8042F2C0 | |||
| 568 | msiexec.exe | C:\System Volume Information\SPP\OnlineMetadataCache\{18480e8e-9692-4bfa-8812-fe75e7ba5e8f}_OnDiskSnapshotProp | binary | |
MD5:8AB42B62E6E61303AB2DB28F3F0F9392 | SHA256:A2F2D408B3993E90CF252C98A23712A1D39D3EA583956D43F0B942D4DEB4738A | |||
| 568 | msiexec.exe | C:\Windows\Installer\1f2053.ipi | binary | |
MD5:1A8FF9CC3B0B4A9E467966B55AAB8294 | SHA256:D6B5F6AC2C35EA972E8ACC5DE9C217DD887530A86093F2D0BF9FFF01B8C203AB | |||
| 568 | msiexec.exe | C:\Windows\Installer\MSI26EC.tmp | binary | |
MD5:D097F4E34524A2C1953E31C5820442C7 | SHA256:59AB30B07FCC61B188ECF843E3327A972009E1D7282285084139EFEE9DFA03C0 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
1
TCP/UDP connections
8
DNS requests
2
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3580 | GUI Turbo Assembler.exe | GET | 200 | 93.184.221.240:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authrootstl.cab?164ab23c5a0fce87 | unknown | compressed | 61.6 Kb | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
2656 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1088 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
3580 | GUI Turbo Assembler.exe | 104.21.0.103:443 | app.ljnath.com | CLOUDFLARENET | — | unknown |
3580 | GUI Turbo Assembler.exe | 93.184.221.240:80 | ctldl.windowsupdate.com | EDGECAST | GB | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
app.ljnath.com |
| unknown |
ctldl.windowsupdate.com |
| whitelisted |