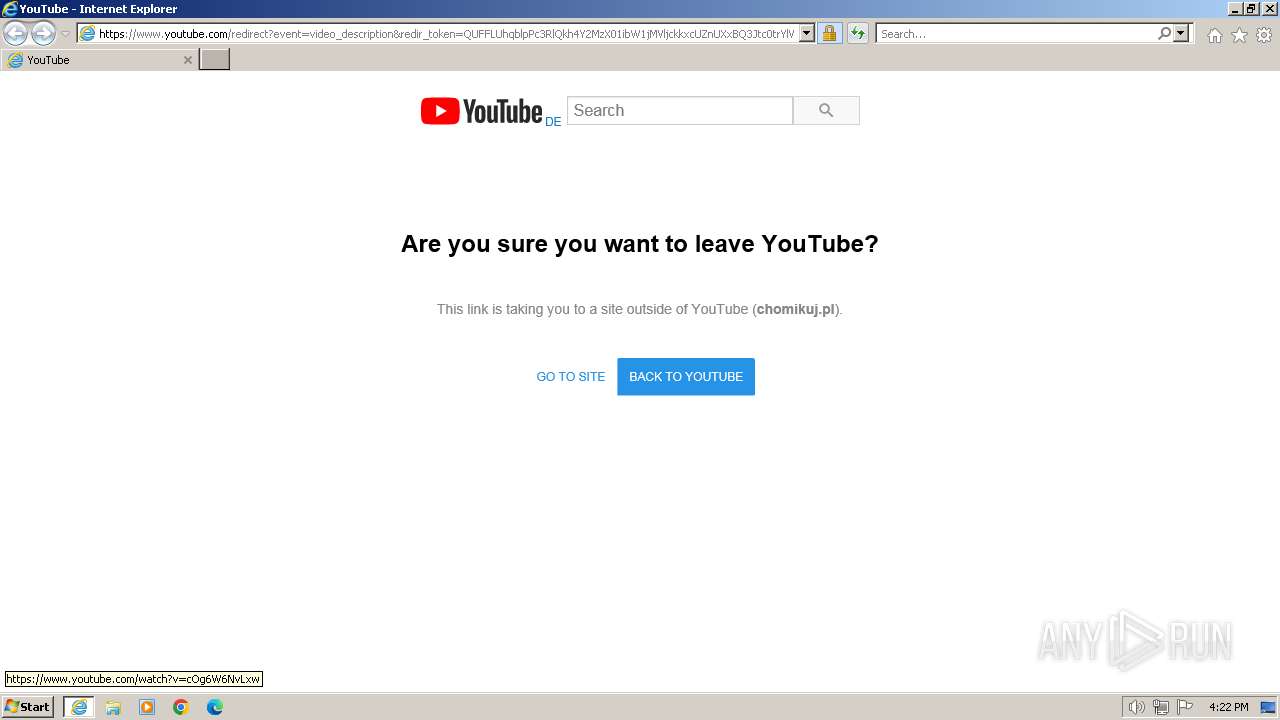
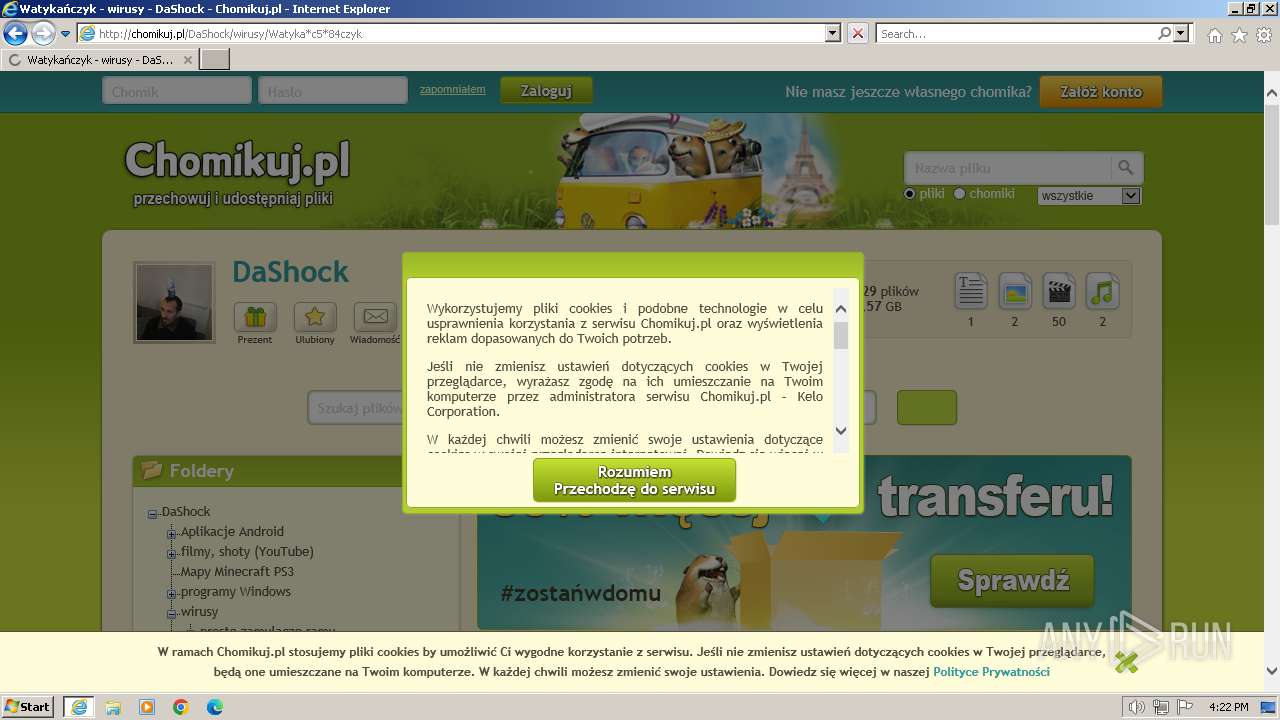
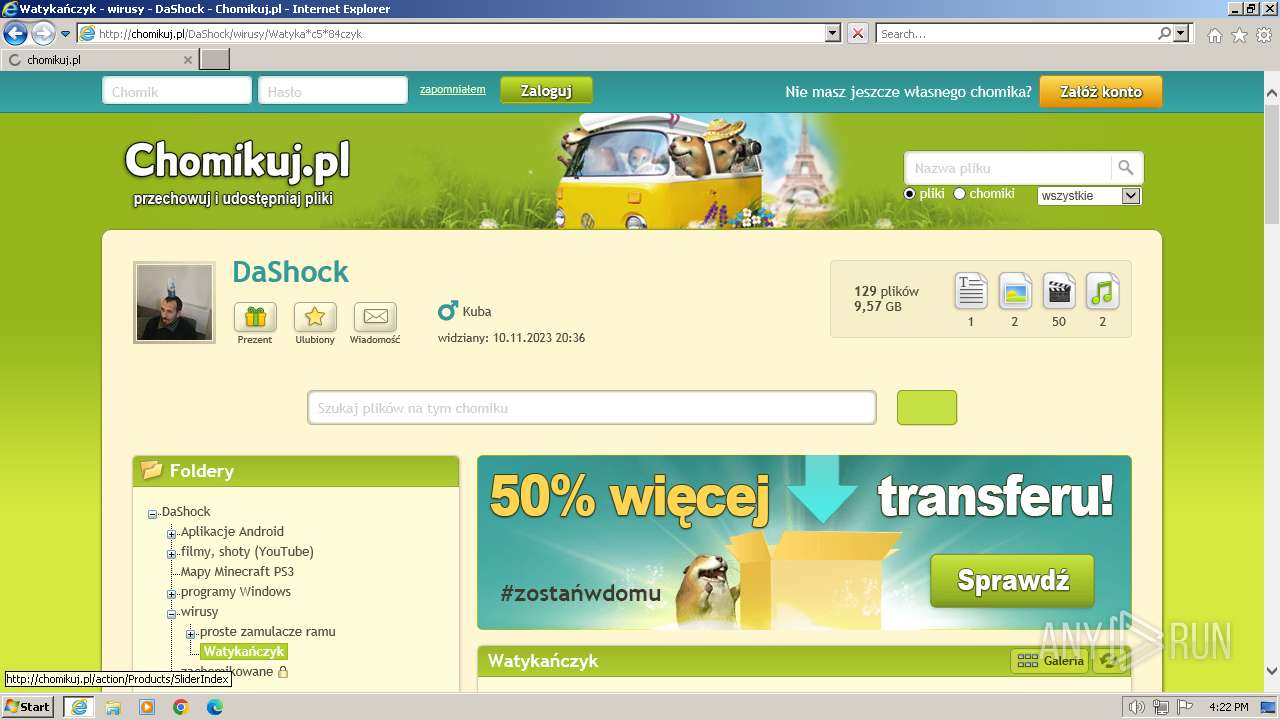
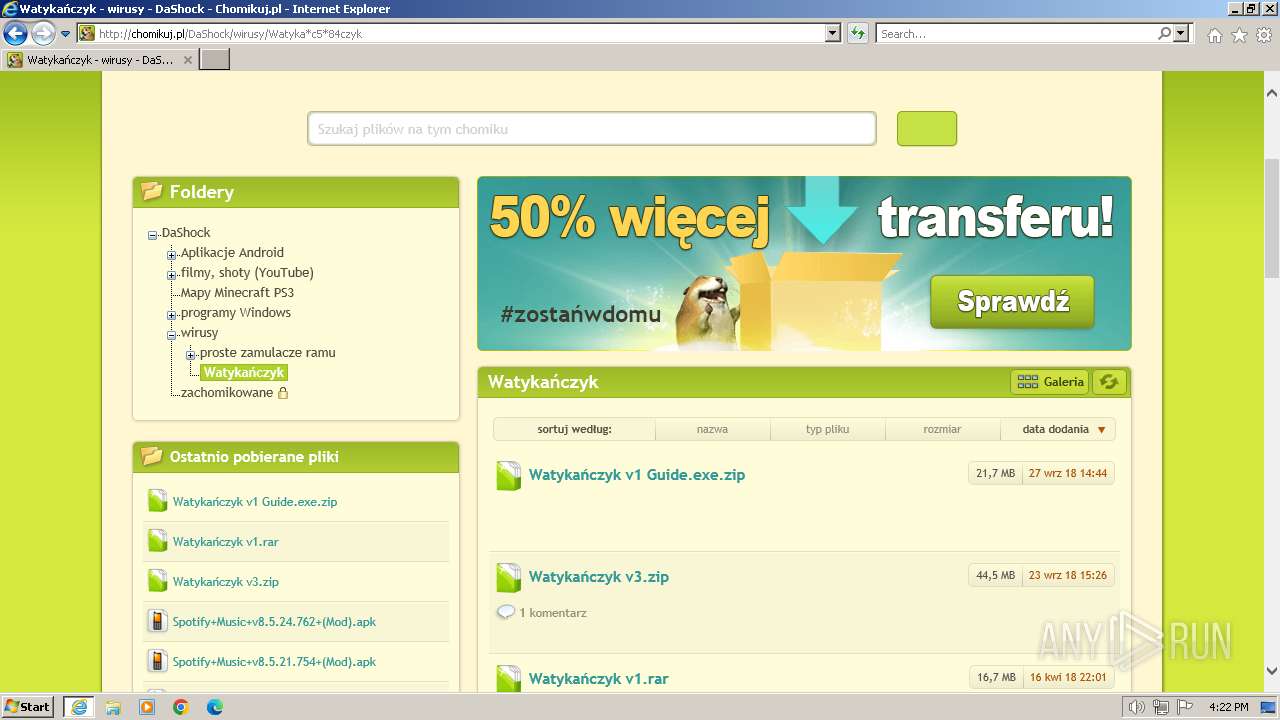
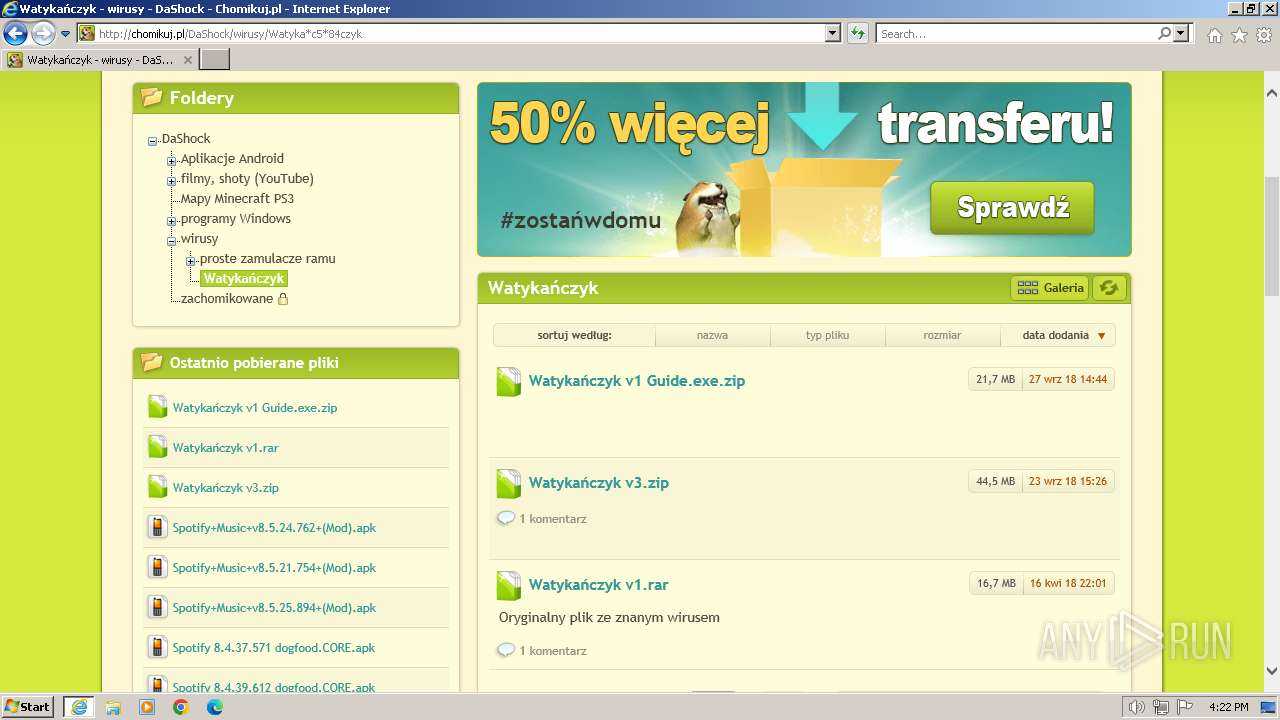
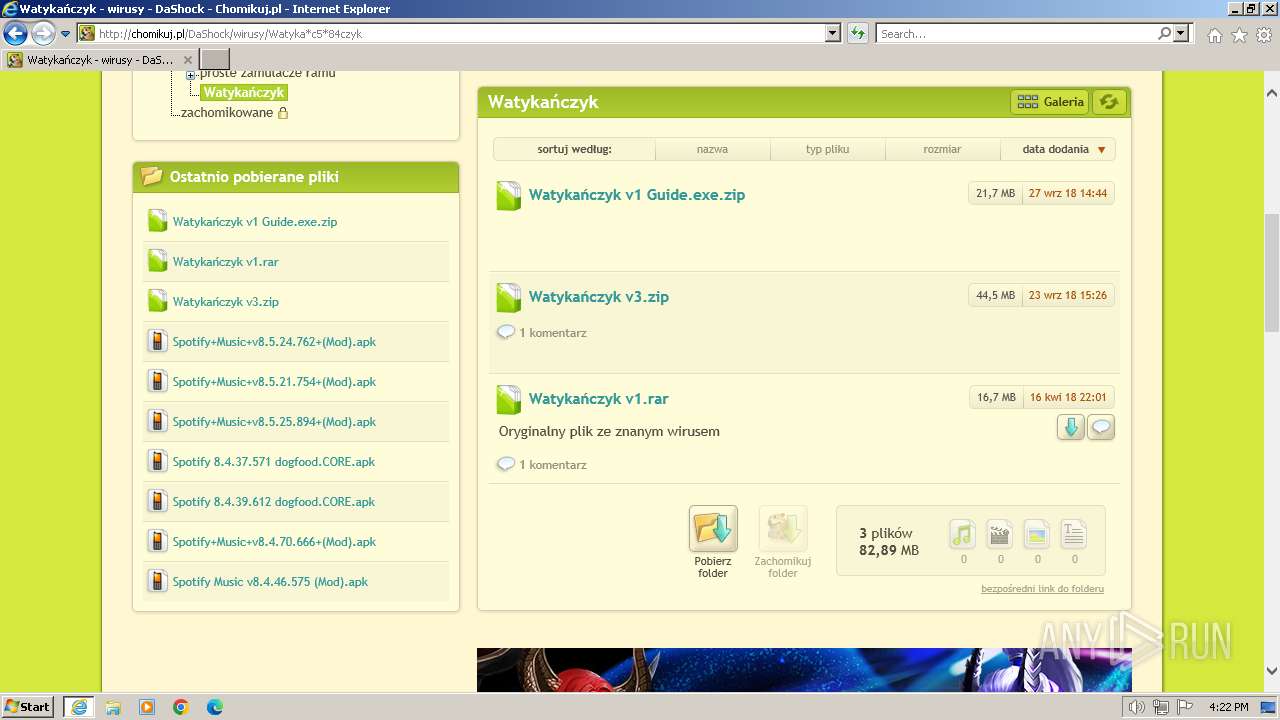
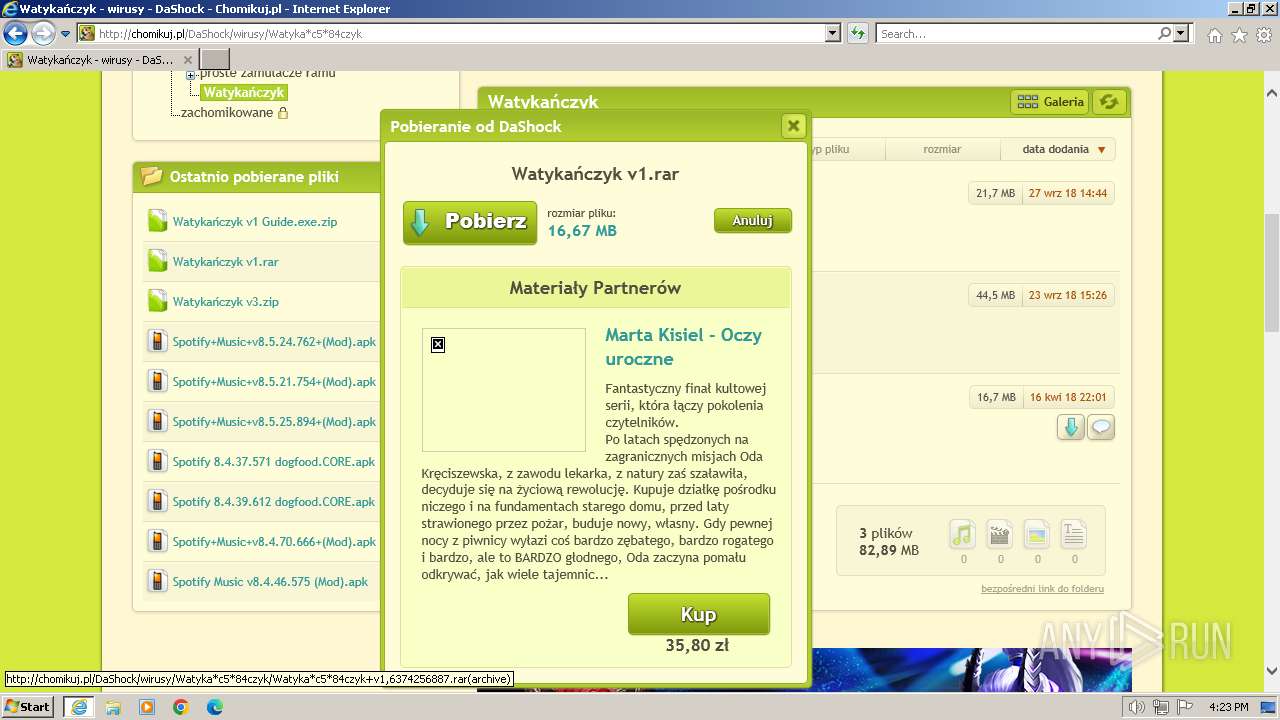
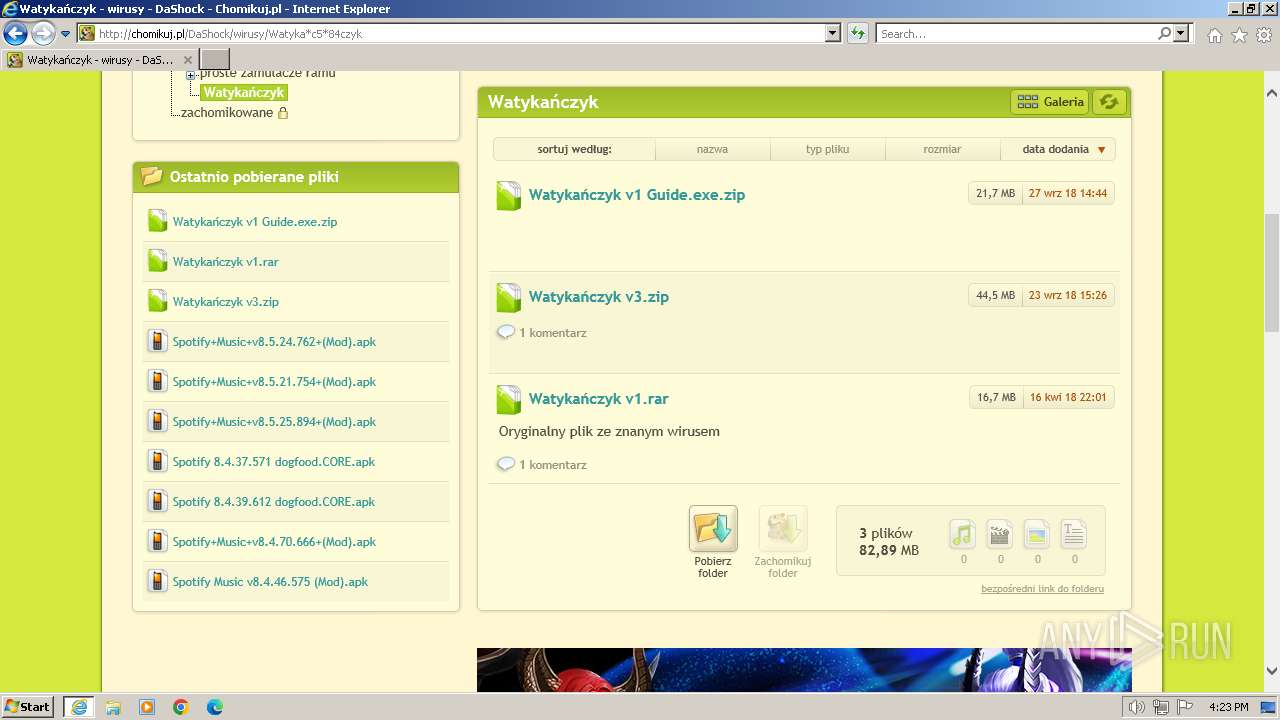
| URL: | https://www.youtube.com/redirect?event=video_description&redir_token=QUFFLUhqblpPc3RlQkh4Y2MzX01ibW1jMVljckkxcUZnUXxBQ3Jtc0trYlVzRk1XNG1WZTZPMGFUcUkzRjBsVkZMcEZYZ2laY29ISmVHUjBXM3ljcmdOMW1ta000SVJsUTMtTEhYdWpZbEtfbERUemV6SXp3ejZaam1HNU15UWxTZ1BKVHEyNDRBZGJuVkd6cENuQmlfMmE2dw&q=http%3A%2F%2Fchomikuj.pl%2FDaShock%2Fwirusy%2FWatyka%2Ac5%2A84czyk&v=cOg6W6NvLxw |
| Full analysis: | https://app.any.run/tasks/e046f97f-884a-4c78-8030-7553585c1f1c |
| Verdict: | Malicious activity |
| Analysis date: | February 08, 2024, 16:22:34 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MD5: | 9C61B53600C15FDEA8283089ACA5D83E |
| SHA1: | BC6A088A886D5A9A323FF26442DCB234C7B52F12 |
| SHA256: | 8FCA80BCADF42A78B9229F59644B25E3D0EBA9D82BF2CA8F85FDF17B206D443B |
| SSDEEP: | 6:2OLUxGKmKLqZbJwMHwzhArz73TXXeZScr04nzQ9/WqXbB3HszzXyG2LrqC+Te:2jGRftwMHT3znoU/Ww3s/N2LrqC7 |
MALICIOUS
No malicious indicators.SUSPICIOUS
No suspicious indicators.INFO
Application launched itself
- iexplore.exe (PID: 1264)
The process uses the downloaded file
- FlashUtil32_32_0_0_453_ActiveX.exe (PID: 3836)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
40
Monitored processes
3
Malicious processes
0
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1264 | "C:\Program Files\Internet Explorer\iexplore.exe" "https://www.youtube.com/redirect?event=video_description&redir_token=QUFFLUhqblpPc3RlQkh4Y2MzX01ibW1jMVljckkxcUZnUXxBQ3Jtc0trYlVzRk1XNG1WZTZPMGFUcUkzRjBsVkZMcEZYZ2laY29ISmVHUjBXM3ljcmdOMW1ta000SVJsUTMtTEhYdWpZbEtfbERUemV6SXp3ejZaam1HNU15UWxTZ1BKVHEyNDRBZGJuVkd6cENuQmlfMmE2dw&q=http%3A%2F%2Fchomikuj.pl%2FDaShock%2Fwirusy%2FWatyka%2Ac5%2A84czyk&v=cOg6W6NvLxw" | C:\Program Files\Internet Explorer\iexplore.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 1 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 3836 | C:\Windows\system32\Macromed\Flash\FlashUtil32_32_0_0_453_ActiveX.exe -Embedding | C:\Windows\System32\Macromed\Flash\FlashUtil32_32_0_0_453_ActiveX.exe | — | svchost.exe | |||||||||||
User: admin Company: Adobe Integrity Level: MEDIUM Description: Adobe® Flash® Player Installer/Uninstaller 32.0 r0 Exit code: 0 Version: 32,0,0,453 Modules
| |||||||||||||||
| 3988 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:1264 CREDAT:267521 /prefetch:2 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
Total events
27 363
Read events
27 231
Write events
125
Delete events
7
Modification events
| (PID) Process: | (1264) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPDaysSinceLastAutoMigration |
Value: 0 | |||
| (PID) Process: | (1264) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchHighDateTime |
Value: 30847387 | |||
| (PID) Process: | (1264) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateHighDateTime |
Value: 30847437 | |||
| (PID) Process: | (1264) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (1264) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (1264) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
| (PID) Process: | (1264) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (1264) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (1264) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (1264) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
Executable files
0
Suspicious files
119
Text files
192
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3988 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\265C0DEB29181DD1891051371C5F863A_DDCF8A1BB8132E191B1D87188F0E5FF4 | binary | |
MD5:CAD81FAD2AB96418942CCF7A83132C26 | SHA256:343A22CE1C80B7675588C481445158EF298B35EBA0C69AD47EF95EF77FBE9969 | |||
| 3988 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\E87CE99F124623F95572A696C80EFCAF_D50E9269859FFB5A738F673D82E63752 | binary | |
MD5:BC0CD685752AFE0C38084FBB5292EE98 | SHA256:7FDC7579C3B8CBD6BD686D660635EADF254E8FD1EE3E95FD8A2F5AC422DCDE77 | |||
| 3988 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\CAF4703619713E3F18D8A9D5D88D6288_A7725538C46DE2D0088EE44974E2CEBA | binary | |
MD5:AC89A852C2AAA3D389B2D2DD312AD367 | SHA256:0B720E19270C672F9B6E0EC40B468AC49376807DE08A814573FE038779534F45 | |||
| 3988 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\57C8EDB95DF3F0AD4EE2DC2B8CFD4157 | binary | |
MD5:B3F11ABA6D556CD4B4D4F09077DAA0E3 | SHA256:0E4BE72F2473E507407F77E15DDEF4E8C17C5B68B5C8306758B7385AC4DC4D61 | |||
| 3988 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\CAF4703619713E3F18D8A9D5D88D6288_A7725538C46DE2D0088EE44974E2CEBA | binary | |
MD5:64FAA5D43ABC539FF022EE45248573E7 | SHA256:71271C62599852C46EB66703D587CCFBD8697DBBCAD29872895CC2B9428DC5F2 | |||
| 3988 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\24BD96D5497F70B3F510A6B53CD43F3E_3A89246FB90C5EE6620004F1AE0EB0EA | binary | |
MD5:4460C4AD7009A73AD2C7936E7D3A7E1B | SHA256:929A3042593755980BB3F998ADAABD13C185D779A391C5E31689E8F2DB6558F0 | |||
| 3988 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\MFAQUS6V\redirect[1].htm | html | |
MD5:666B844F7B46CE5205DB689081725971 | SHA256:5918473031A5BECB8BCD8C3EB2AA7C12C21F1C01AAC1C2297B8EA0370413F4A6 | |||
| 3988 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\E87CE99F124623F95572A696C80EFCAF_D50E9269859FFB5A738F673D82E63752 | binary | |
MD5:5166E581E3475BF2470C4D6F594CBA58 | SHA256:78BE177F403C02259BB300AE80D9127C11925D063BD52A4C23F06A3571506DC2 | |||
| 3988 | iexplore.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Cookies\Low\YC3GKRMJ.txt | text | |
MD5:C336FFFA879A2F5C70EA15B70C0BBF72 | SHA256:08BD18E2548E033F046397A75A9699EEB691F5EDE0DE04688D7AA62A2E9E63AF | |||
| 3988 | iexplore.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Cookies\Low\87N2QR56.txt | text | |
MD5:DFBD8D2A50E26A538174099F14F643B2 | SHA256:AF4C55330BD729DF9CA102065B2C607F6CA136324C052D455D01DB601E70D6A1 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
158
TCP/UDP connections
152
DNS requests
60
Threats
1
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3988 | iexplore.exe | GET | 304 | 93.184.221.240:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?58b09451c6662268 | unknown | — | — | unknown |
3988 | iexplore.exe | GET | 304 | 93.184.221.240:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?83c23cd8118a42bc | unknown | — | — | unknown |
3988 | iexplore.exe | GET | 200 | 216.58.206.35:80 | http://ocsp.pki.goog/gsr1/MFEwTzBNMEswSTAJBgUrDgMCGgUABBS3V7W2nAf4FiMTjpDJKg6%2BMgGqMQQUYHtmGkUNl8qJUC99BM00qP%2F8%2FUsCEHe9DWzbNvka6iEPxPBY0w0%3D | unknown | binary | 1.41 Kb | unknown |
3988 | iexplore.exe | GET | 200 | 216.58.206.35:80 | http://ocsp.pki.goog/gtsr1/ME4wTDBKMEgwRjAJBgUrDgMCGgUABBQwkcLWD4LqGJ7bE7B1XZsEbmfwUAQU5K8rJnEaK0gnhS9SZizv8IkTcT4CDQIDvFNZazTHGPUBUGY%3D | unknown | binary | 724 b | unknown |
3988 | iexplore.exe | GET | 200 | 216.58.206.35:80 | http://ocsp.pki.goog/gts1c3/MFIwUDBOMEwwSjAJBgUrDgMCGgUABBTHLnmK3f9hNLO67UdCuLvGwCQHYwQUinR%2Fr4XN7pXNPZzQ4kYU83E1HScCEQCw14DGj8KB%2FwqJau317vru | unknown | binary | 472 b | unknown |
3988 | iexplore.exe | GET | 200 | 216.58.206.35:80 | http://ocsp.pki.goog/gts1c3/MFIwUDBOMEwwSjAJBgUrDgMCGgUABBTHLnmK3f9hNLO67UdCuLvGwCQHYwQUinR%2Fr4XN7pXNPZzQ4kYU83E1HScCEQDf%2FqechPhkiAm5teJWf%2BUv | unknown | binary | 472 b | unknown |
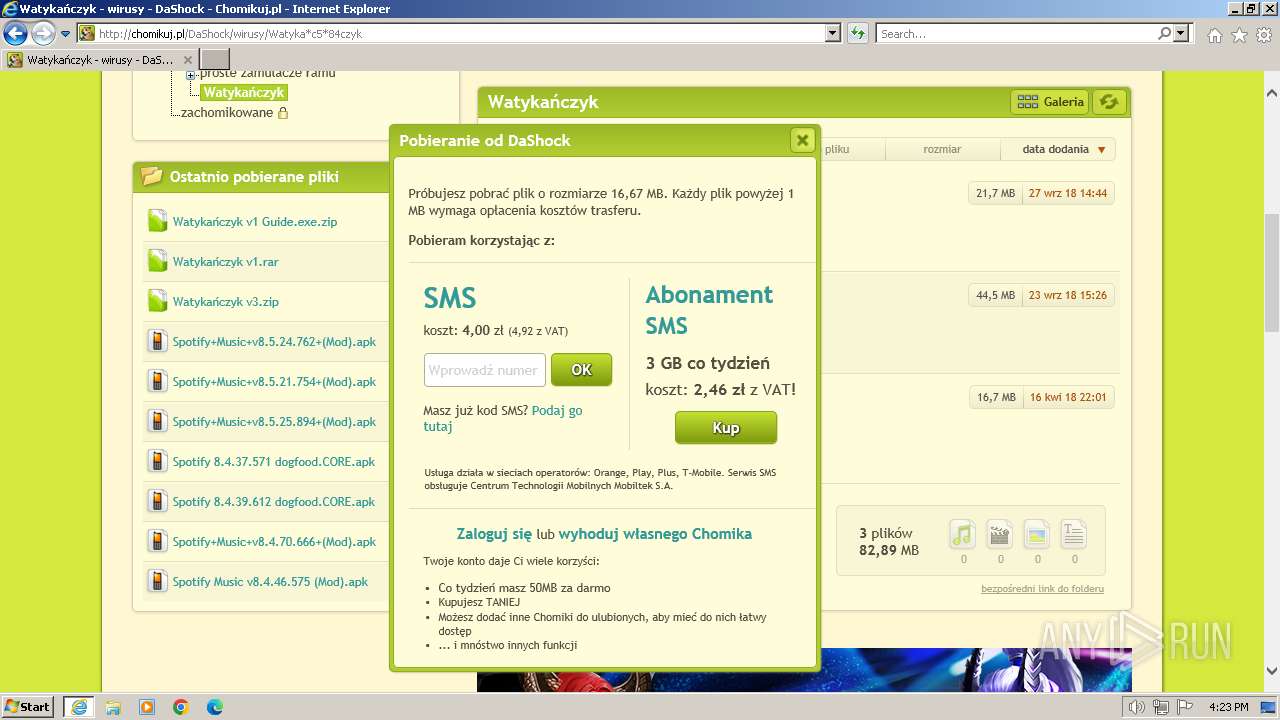
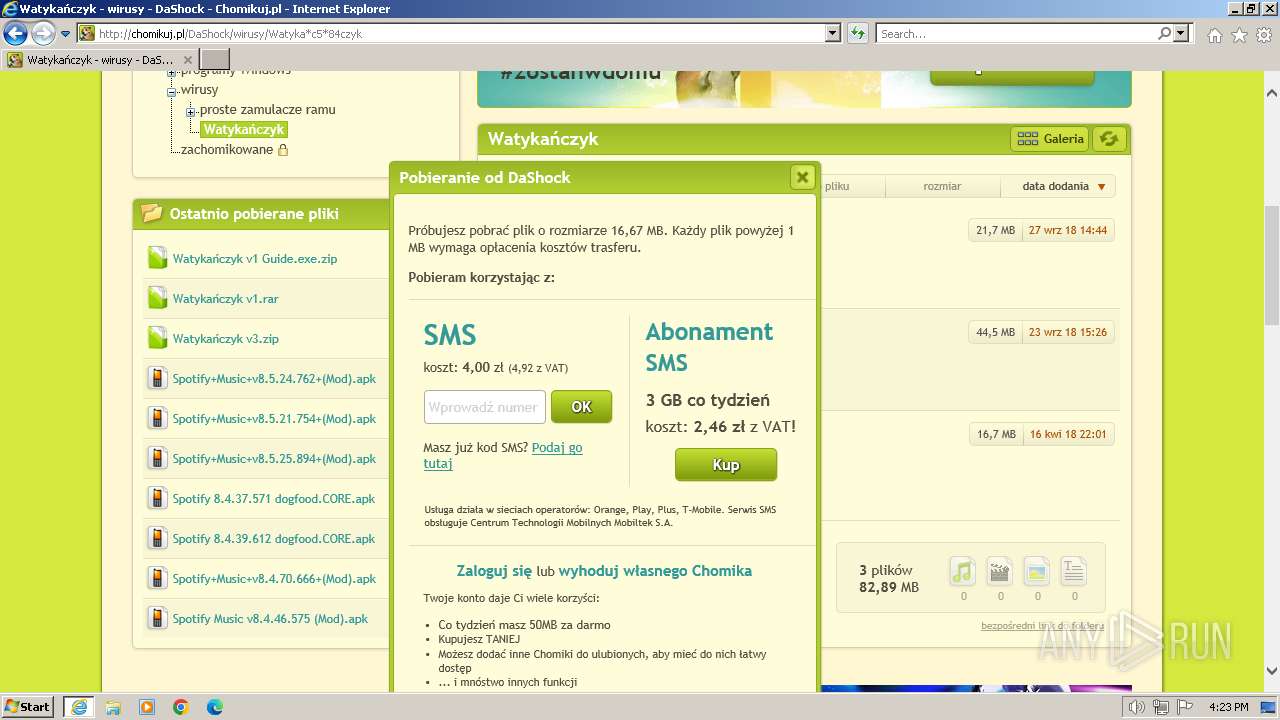
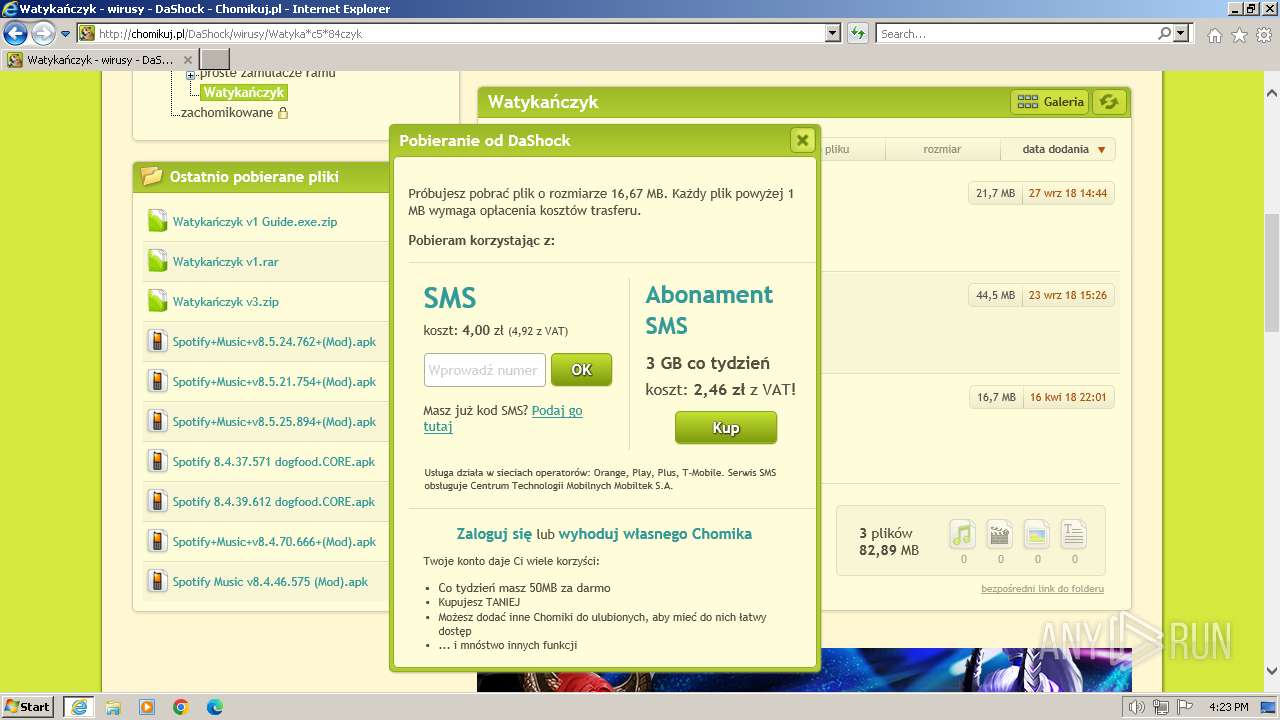
3988 | iexplore.exe | GET | 200 | 104.22.25.70:80 | http://chomikuj.pl/DaShock/wirusy/Watyka*c5*84czyk | unknown | compressed | 15.1 Kb | unknown |
3988 | iexplore.exe | GET | 200 | 188.114.97.3:80 | http://x4.static-chomikuj.pl/res/0ba441af03.css | unknown | image | 743 b | unknown |
3988 | iexplore.exe | GET | 200 | 188.114.97.3:80 | http://x4.static-chomikuj.pl/res/fecf21247f.css | unknown | image | 15.9 Kb | unknown |
3988 | iexplore.exe | GET | 200 | 188.114.97.3:80 | http://x4.static-chomikuj.pl/res/fa469fce2f.css | unknown | text | 1.39 Kb | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
3988 | iexplore.exe | 216.58.212.142:443 | www.youtube.com | GOOGLE | US | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
3988 | iexplore.exe | 93.184.221.240:80 | ctldl.windowsupdate.com | EDGECAST | GB | whitelisted |
3988 | iexplore.exe | 216.58.206.35:80 | ocsp.pki.goog | GOOGLE | US | whitelisted |
3988 | iexplore.exe | 142.250.181.227:443 | www.gstatic.com | GOOGLE | US | whitelisted |
1264 | iexplore.exe | 216.58.212.142:443 | www.youtube.com | GOOGLE | US | whitelisted |
1264 | iexplore.exe | 93.184.221.240:80 | ctldl.windowsupdate.com | EDGECAST | GB | whitelisted |
3988 | iexplore.exe | 104.22.25.70:80 | chomikuj.pl | CLOUDFLARENET | — | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
www.youtube.com |
| whitelisted |
ctldl.windowsupdate.com |
| whitelisted |
ocsp.pki.goog |
| whitelisted |
www.gstatic.com |
| whitelisted |
chomikuj.pl |
| whitelisted |
x4.static-chomikuj.pl |
| unknown |
pro.hit.gemius.pl |
| whitelisted |
www.google.com |
| whitelisted |
www.yetipay.pl |
| whitelisted |
profile.static-chomikuj.pl |
| unknown |
Threats
PID | Process | Class | Message |
|---|---|---|---|
1080 | svchost.exe | Misc activity | ET INFO URL Shortener Service Domain in DNS Lookup (rebrand .ly) |