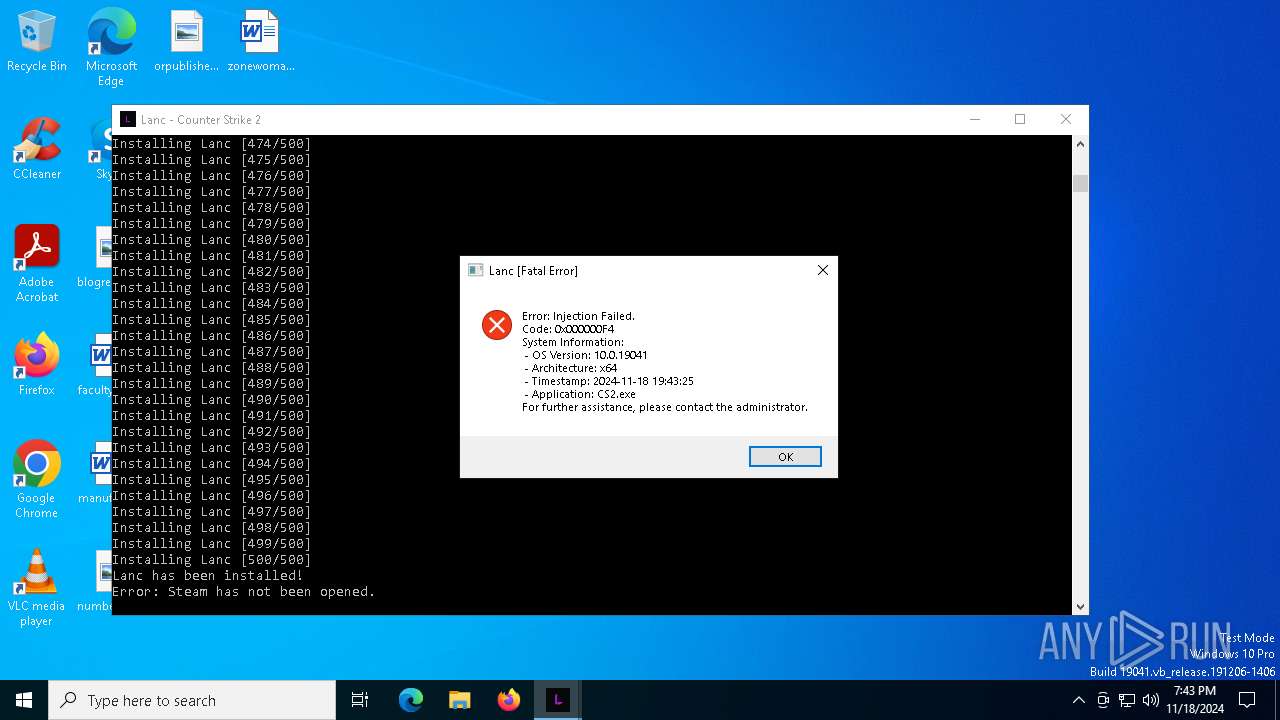
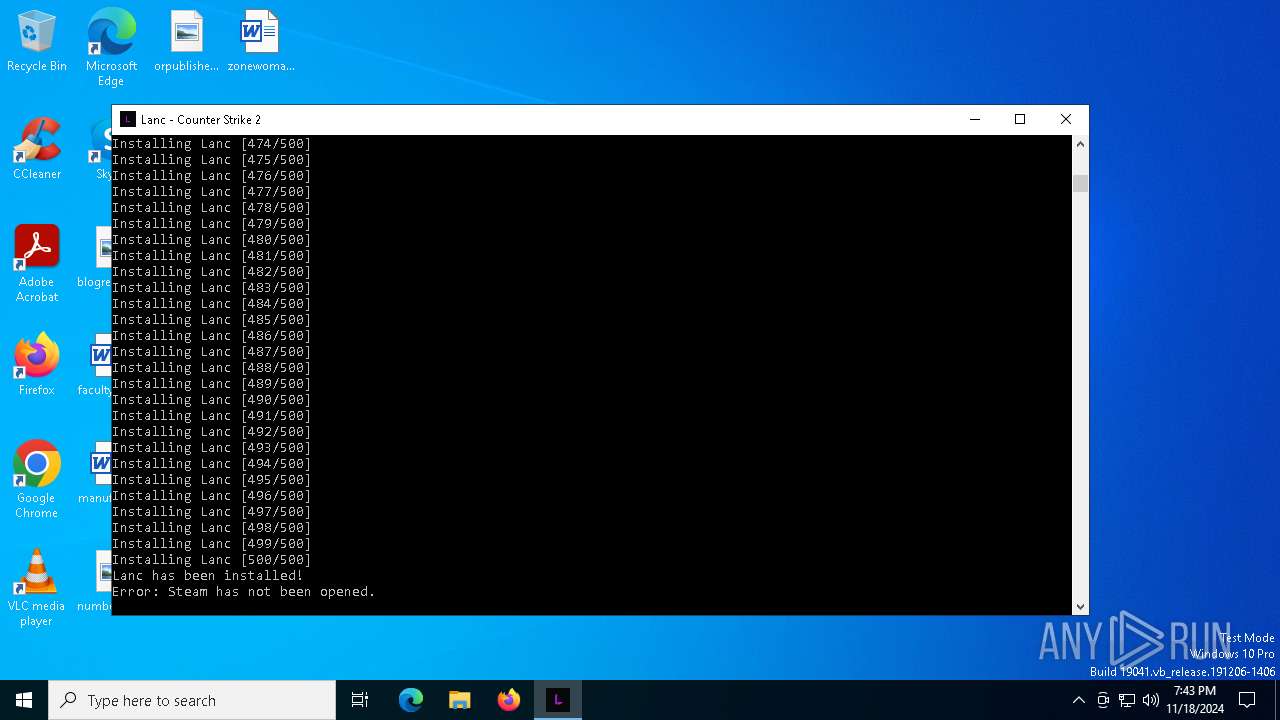
| File name: | Lanc CS2.exe |
| Full analysis: | https://app.any.run/tasks/990a1b2e-8e6b-43be-8cc9-afcf01d9ff3a |
| Verdict: | Malicious activity |
| Analysis date: | November 18, 2024, 19:42:59 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32+ executable (console) x86-64, for MS Windows, 6 sections |
| MD5: | 35C451009B3A5CE350A8905653720666 |
| SHA1: | A862C36C5450EA7132B08F61003CD065E4EC3453 |
| SHA256: | 8FC22D17A729FCF76B5B28F3E3A4E291EEF8BCA63614F3637BF1852CA5EA2E11 |
| SSDEEP: | 98304:EVIyDwwCmSyu4YJbebWn7CvsMh3utHfktEzafhOsE+XZ0PEelmPuxny+TZ0aAkIU:c3r9eUOkm8V |
MALICIOUS
No malicious indicators.SUSPICIOUS
The process drops C-runtime libraries
- Lanc CS2.exe (PID: 3604)
Process drops python dynamic module
- Lanc CS2.exe (PID: 3604)
Application launched itself
- Lanc CS2.exe (PID: 3604)
Process drops legitimate windows executable
- Lanc CS2.exe (PID: 3604)
Executable content was dropped or overwritten
- Lanc CS2.exe (PID: 3604)
INFO
Checks supported languages
- Lanc CS2.exe (PID: 3604)
Reads the computer name
- Lanc CS2.exe (PID: 3604)
PyInstaller has been detected (YARA)
- Lanc CS2.exe (PID: 3604)
Create files in a temporary directory
- Lanc CS2.exe (PID: 3604)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win64 Executable (generic) (87.3) |
|---|---|---|
| .exe | | | Generic Win/DOS Executable (6.3) |
| .exe | | | DOS Executable Generic (6.3) |
EXIF
EXE
| MachineType: | AMD AMD64 |
|---|---|
| TimeStamp: | 2024:11:13 13:32:59+00:00 |
| ImageFileCharacteristics: | Executable, Large address aware |
| PEType: | PE32+ |
| LinkerVersion: | 14.4 |
| CodeSize: | 176640 |
| InitializedDataSize: | 363520 |
| UninitializedDataSize: | - |
| EntryPoint: | 0xc320 |
| OSVersion: | 6 |
| ImageVersion: | - |
| SubsystemVersion: | 6 |
| Subsystem: | Windows command line |
Total processes
132
Monitored processes
4
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 3020 | "C:\Users\admin\AppData\Local\Temp\_MEI36042\loader.exe" | C:\Users\admin\AppData\Local\Temp\_MEI36042\loader.exe | — | Lanc CS2.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 281 Modules
| |||||||||||||||
| 3600 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | Lanc CS2.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3604 | "C:\Users\admin\AppData\Local\Temp\Lanc CS2.exe" | C:\Users\admin\AppData\Local\Temp\Lanc CS2.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 4680 | "C:\Users\admin\AppData\Local\Temp\Lanc CS2.exe" | C:\Users\admin\AppData\Local\Temp\Lanc CS2.exe | — | Lanc CS2.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
Total events
533
Read events
533
Write events
0
Delete events
0
Modification events
Executable files
53
Suspicious files
1
Text files
2
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3604 | Lanc CS2.exe | C:\Users\admin\AppData\Local\Temp\_MEI36042\api-ms-win-core-datetime-l1-1-0.dll | executable | |
MD5:CFE0C1DFDE224EA5FED9BD5FF778A6E0 | SHA256:0D0F80CBF476AF5B1C9FD3775E086ED0DFDB510CD0CC208EC1CCB04572396E3E | |||
| 3604 | Lanc CS2.exe | C:\Users\admin\AppData\Local\Temp\_MEI36042\_ctypes.pyd | executable | |
MD5:C8AFA1EBB28828E1115C110313D2A810 | SHA256:8978972CF341CCD0EDF8435D63909A739DF7EF29EC7DD57ED5CAB64B342891F0 | |||
| 3604 | Lanc CS2.exe | C:\Users\admin\AppData\Local\Temp\_MEI36042\VCRUNTIME140.dll | executable | |
MD5:BE8DBE2DC77EBE7F88F910C61AEC691A | SHA256:4D292623516F65C80482081E62D5DADB759DC16E851DE5DB24C3CBB57B87DB83 | |||
| 3604 | Lanc CS2.exe | C:\Users\admin\AppData\Local\Temp\_MEI36042\_hashlib.pyd | executable | |
MD5:D19CB5CA144AE1FD29B6395B0225CF40 | SHA256:F95EC2562A3C70FB1A6E44D72F4223CE3C7A0F0038159D09DCE629F59591D5AA | |||
| 3604 | Lanc CS2.exe | C:\Users\admin\AppData\Local\Temp\_MEI36042\_socket.pyd | executable | |
MD5:E43AED7D6A8BCD9DDFC59C2D1A2C4B02 | SHA256:2C2A6A6BA360E38F0C2B5A53B4626F833A3111844D95615EBF35BE0E76B1EF7A | |||
| 3604 | Lanc CS2.exe | C:\Users\admin\AppData\Local\Temp\_MEI36042\_bz2.pyd | executable | |
MD5:DD26ED92888DE9C57660A7AD631BB916 | SHA256:324268786921EC940CBD4B5E2F71DAFD08E578A12E373A715658527E5B211697 | |||
| 3604 | Lanc CS2.exe | C:\Users\admin\AppData\Local\Temp\_MEI36042\api-ms-win-core-file-l1-2-0.dll | executable | |
MD5:1C58526D681EFE507DEB8F1935C75487 | SHA256:EF13DCE8F71173315DFC64AB839B033AB19A968EE15230E9D4D2C9D558EFEEE2 | |||
| 3604 | Lanc CS2.exe | C:\Users\admin\AppData\Local\Temp\_MEI36042\api-ms-win-core-console-l1-1-0.dll | executable | |
MD5:E8B9D74BFD1F6D1CC1D99B24F44DA796 | SHA256:B1B3FD40AB437A43C8DB4994CCFFC7F88000CC8BB6E34A2BCBFF8E2464930C59 | |||
| 3604 | Lanc CS2.exe | C:\Users\admin\AppData\Local\Temp\_MEI36042\api-ms-win-core-file-l1-1-0.dll | executable | |
MD5:EFAD0EE0136532E8E8402770A64C71F9 | SHA256:3D2C55902385381869DB850B526261DDEB4628B83E690A32B67D2E0936B2C6ED | |||
| 3604 | Lanc CS2.exe | C:\Users\admin\AppData\Local\Temp\_MEI36042\api-ms-win-core-debug-l1-1-0.dll | executable | |
MD5:33BBECE432F8DA57F17BF2E396EBAA58 | SHA256:7CF0944901F7F7E0D0B9AD62753FC2FE380461B1CCE8CDC7E9C9867C980E3B0E | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
7
TCP/UDP connections
39
DNS requests
14
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5488 | MoUsoCoreWorker.exe | GET | 200 | 69.192.161.161:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
5488 | MoUsoCoreWorker.exe | GET | 200 | 23.48.23.156:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
4360 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
5012 | SIHClient.exe | GET | 200 | 69.192.161.161:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
6316 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
5012 | SIHClient.exe | GET | 200 | 69.192.161.161:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
7040 | RUXIMICS.exe | 4.231.128.59:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
— | — | 4.231.128.59:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5488 | MoUsoCoreWorker.exe | 23.48.23.156:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
— | — | 104.126.37.171:443 | th.bing.com | Akamai International B.V. | DE | whitelisted |
5488 | MoUsoCoreWorker.exe | 69.192.161.161:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
6944 | svchost.exe | 4.231.128.59:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4020 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
4904 | svchost.exe | 20.190.160.20:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
— | — | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
th.bing.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
arc.msn.com |
| whitelisted |