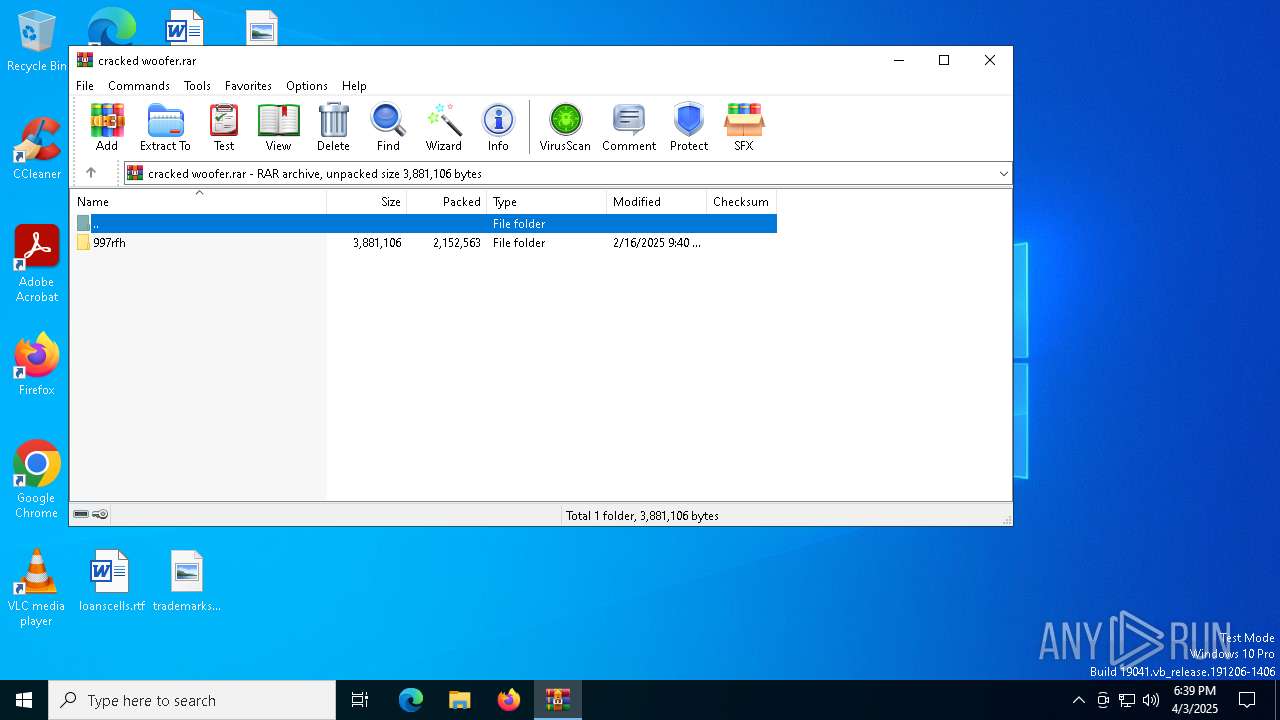
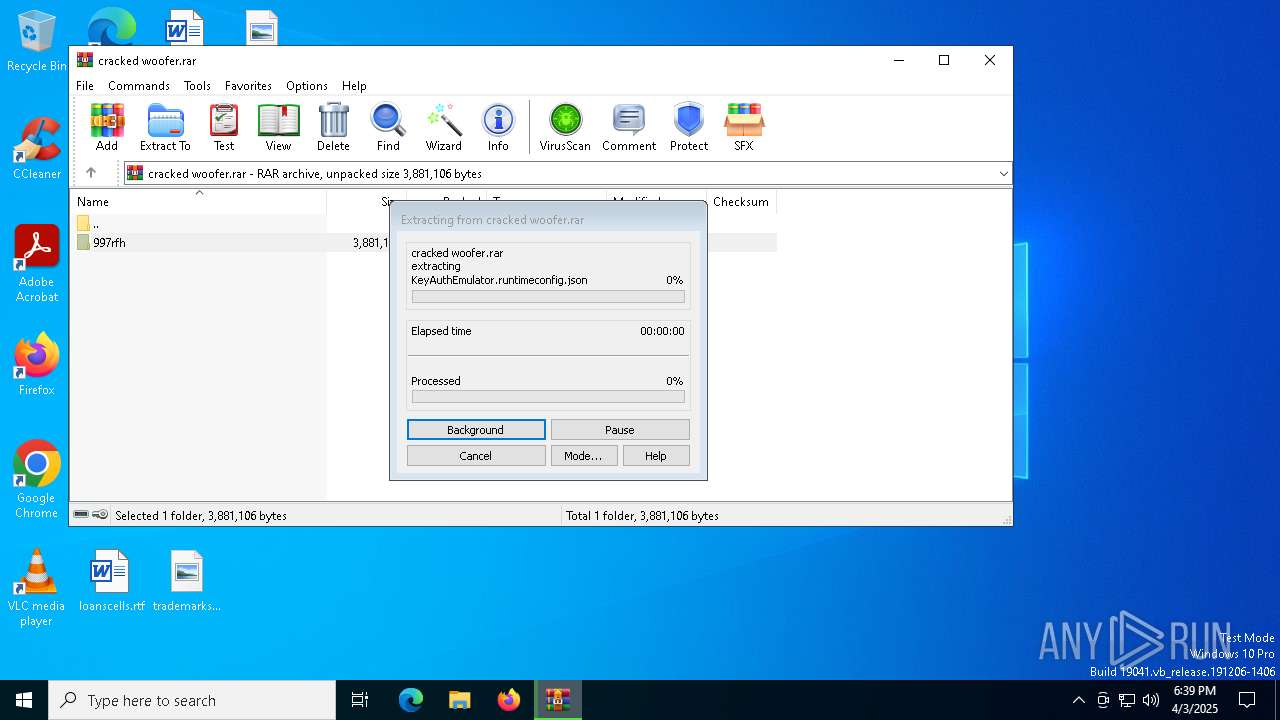
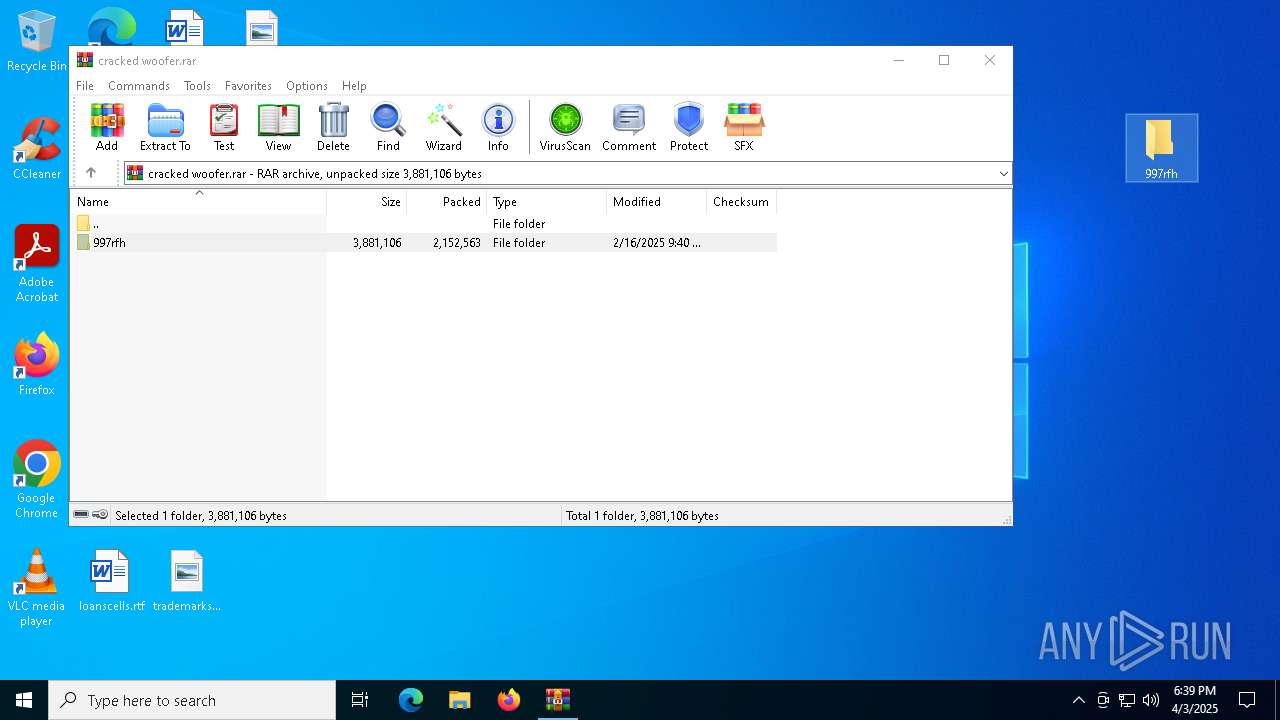
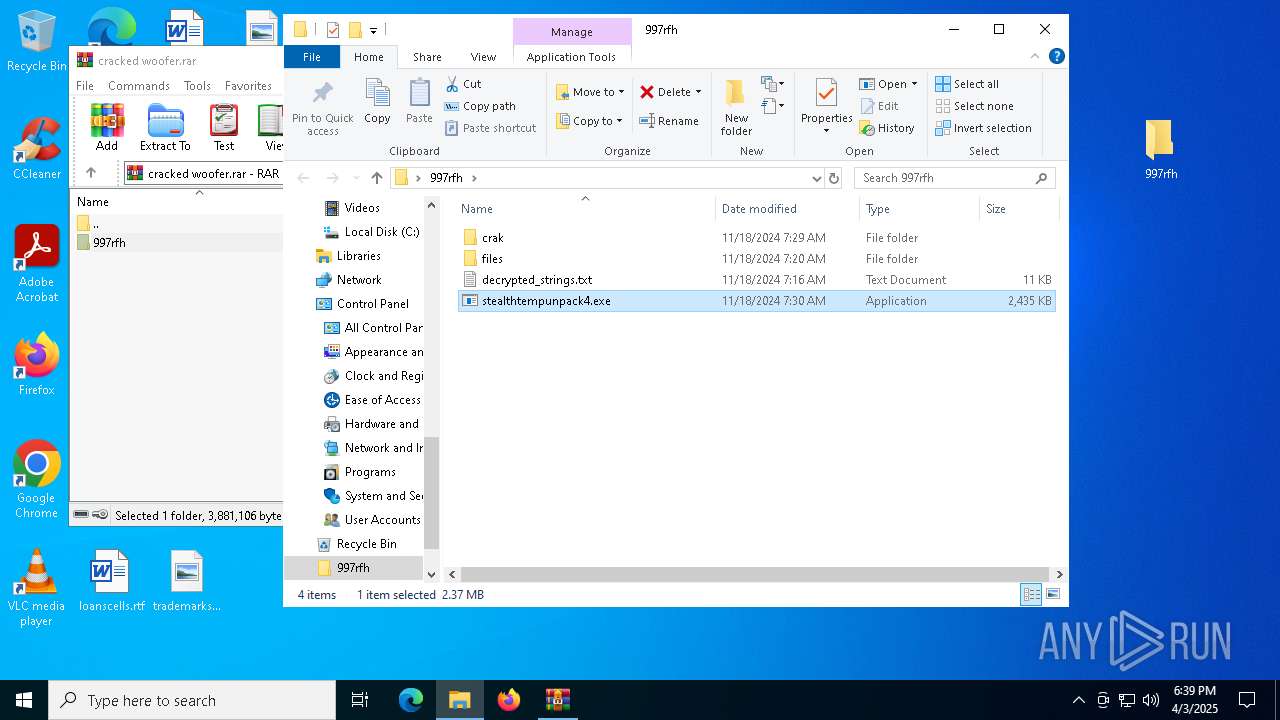
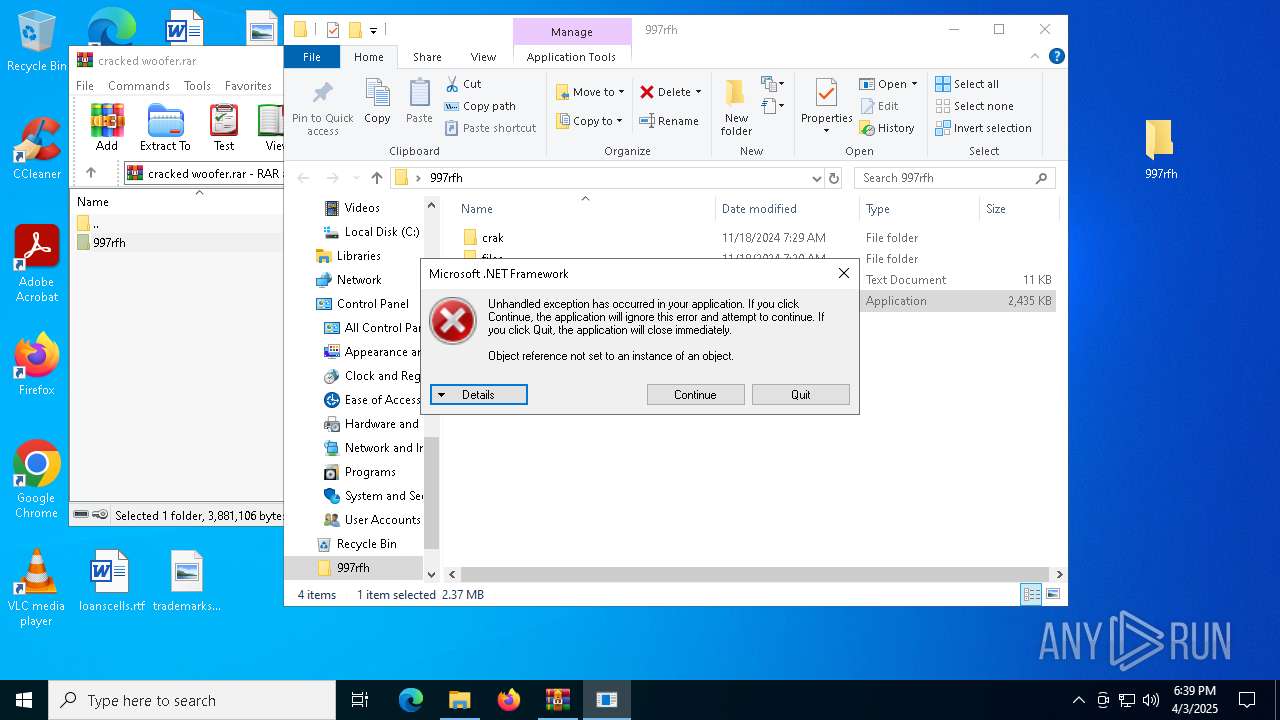
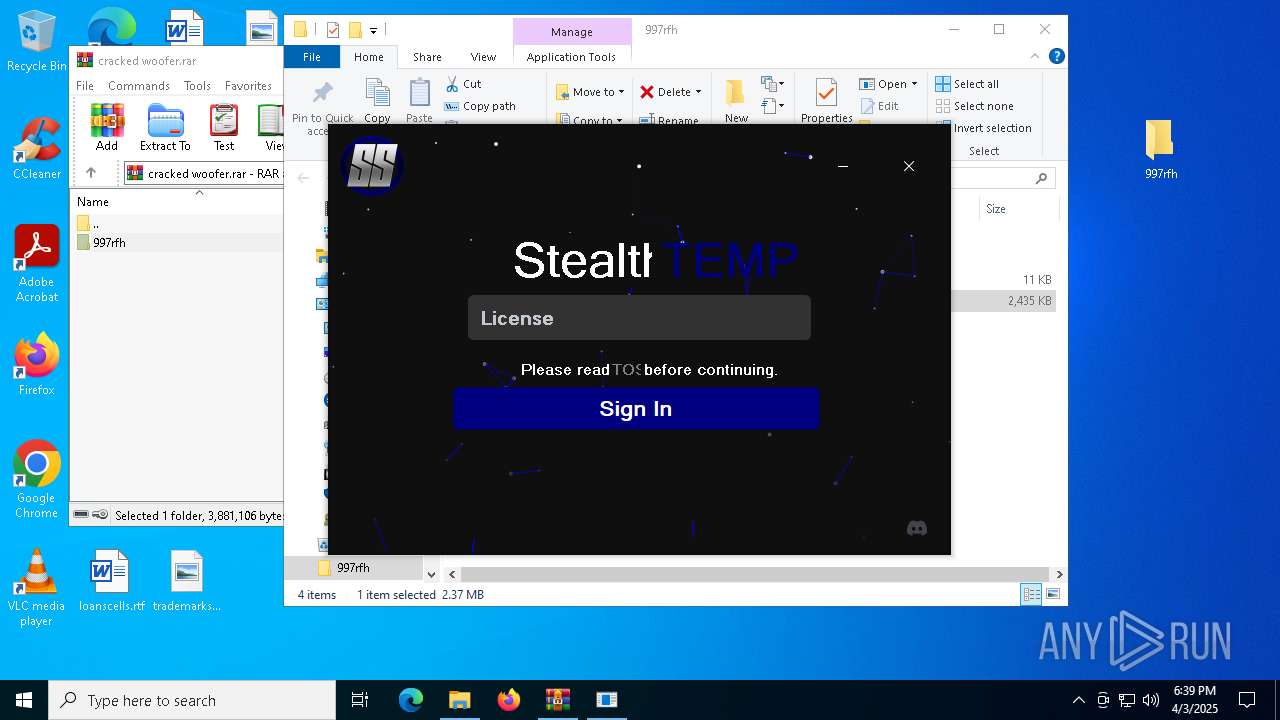
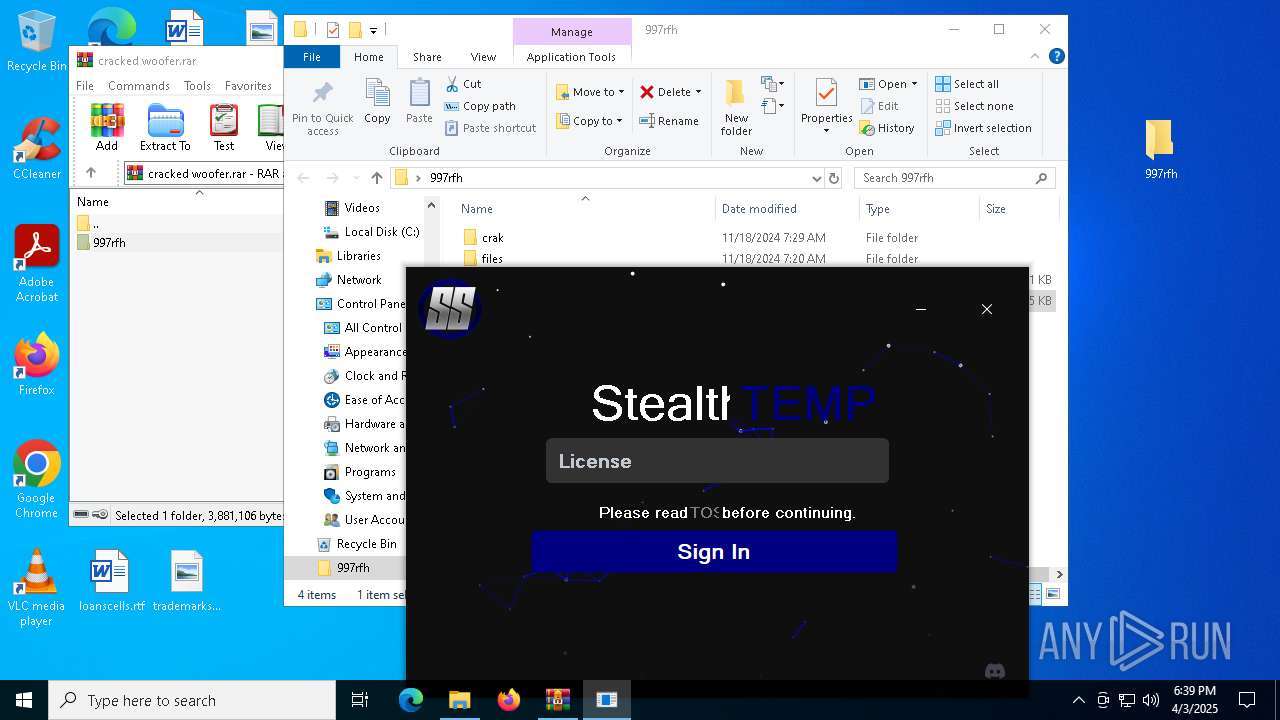
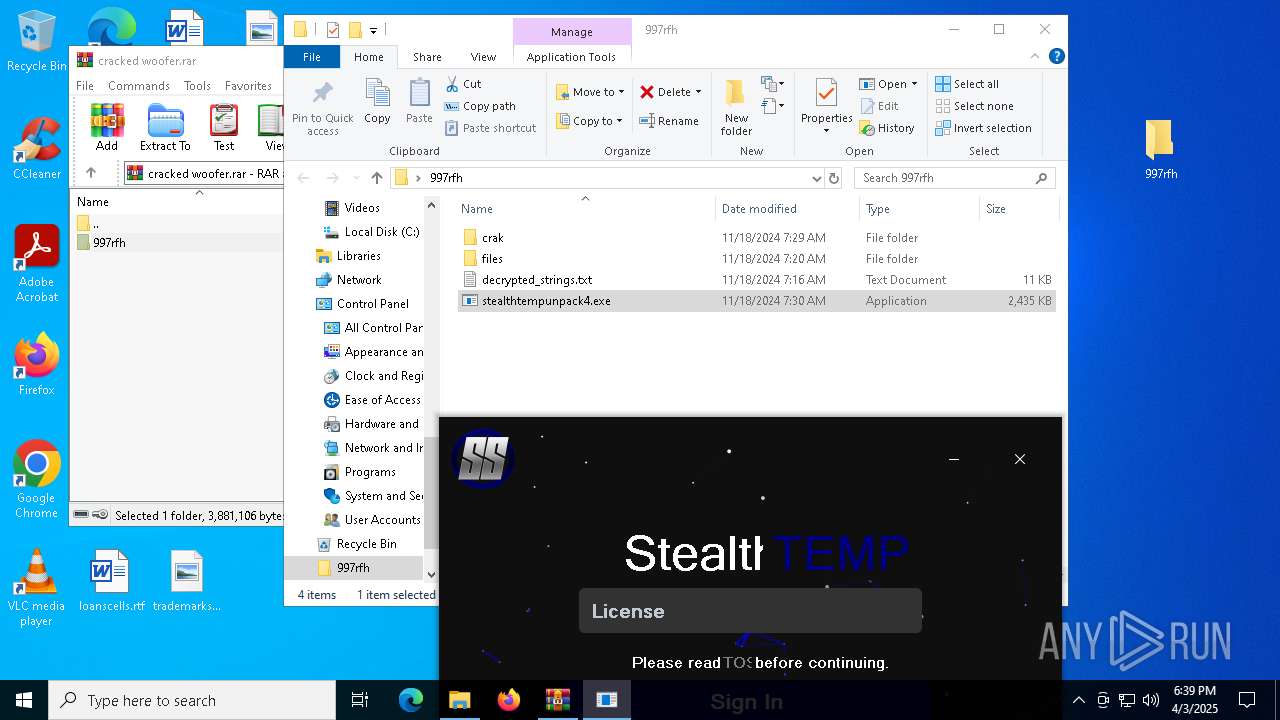
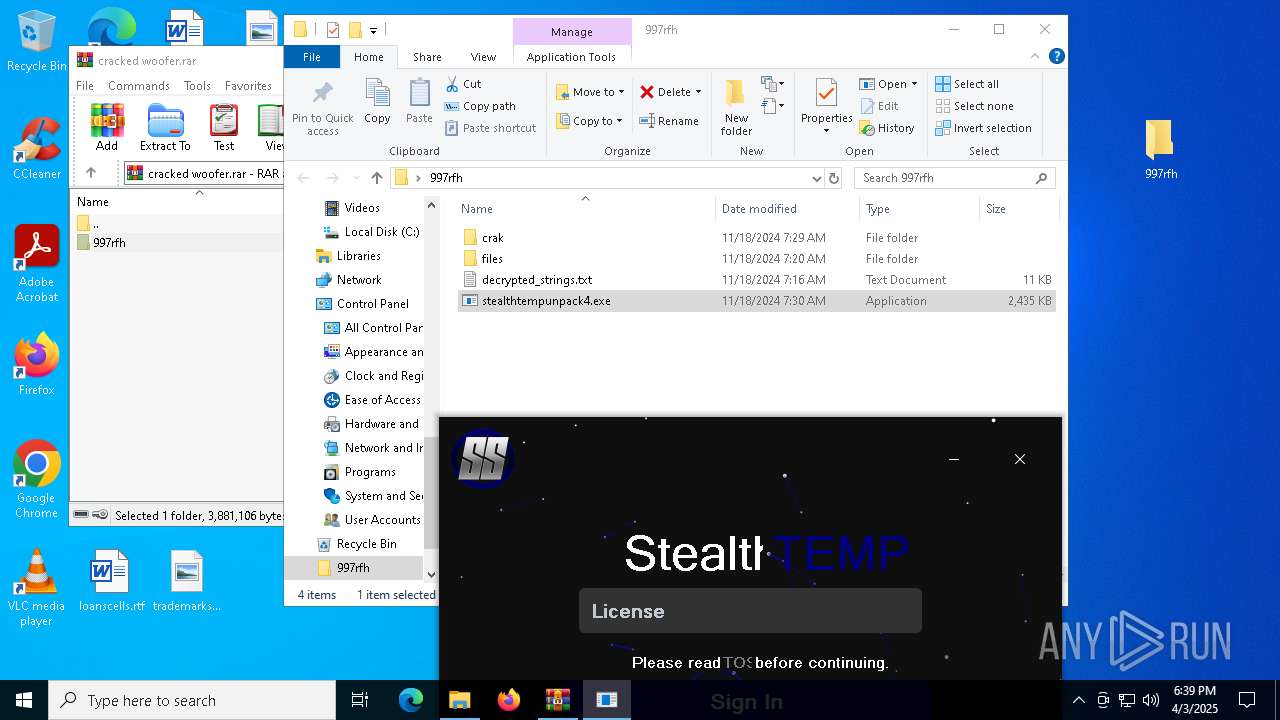
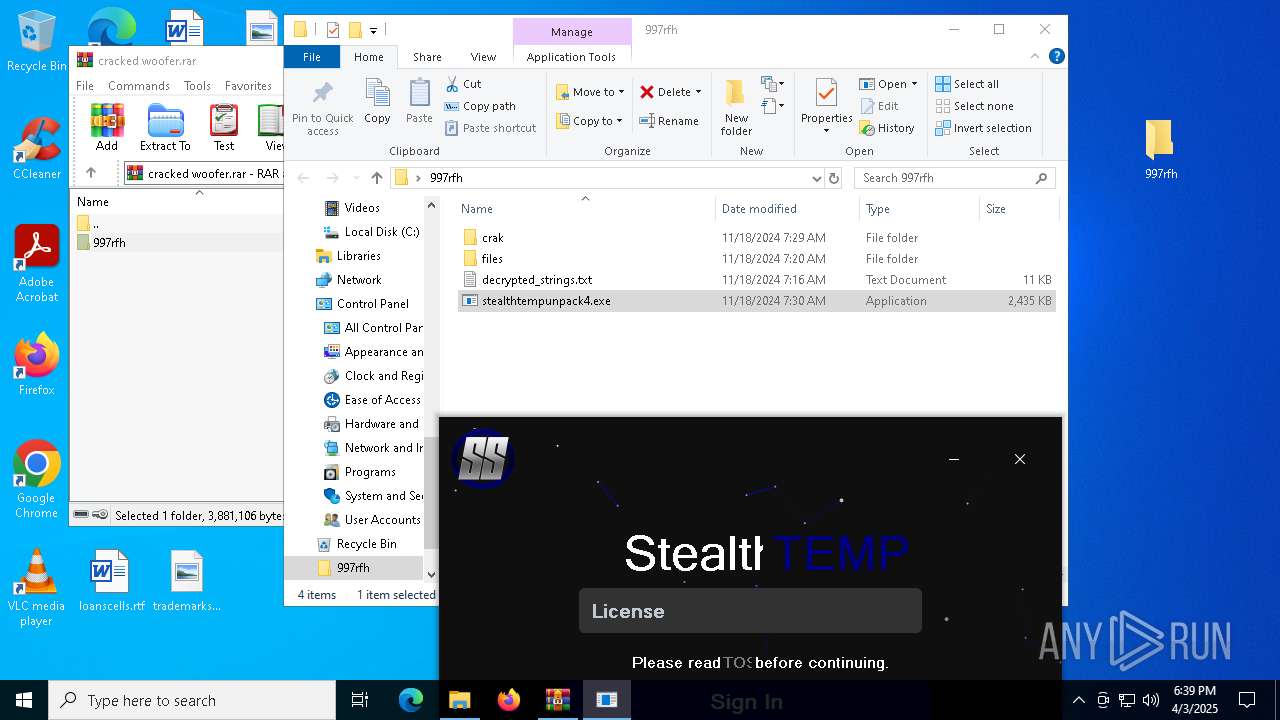
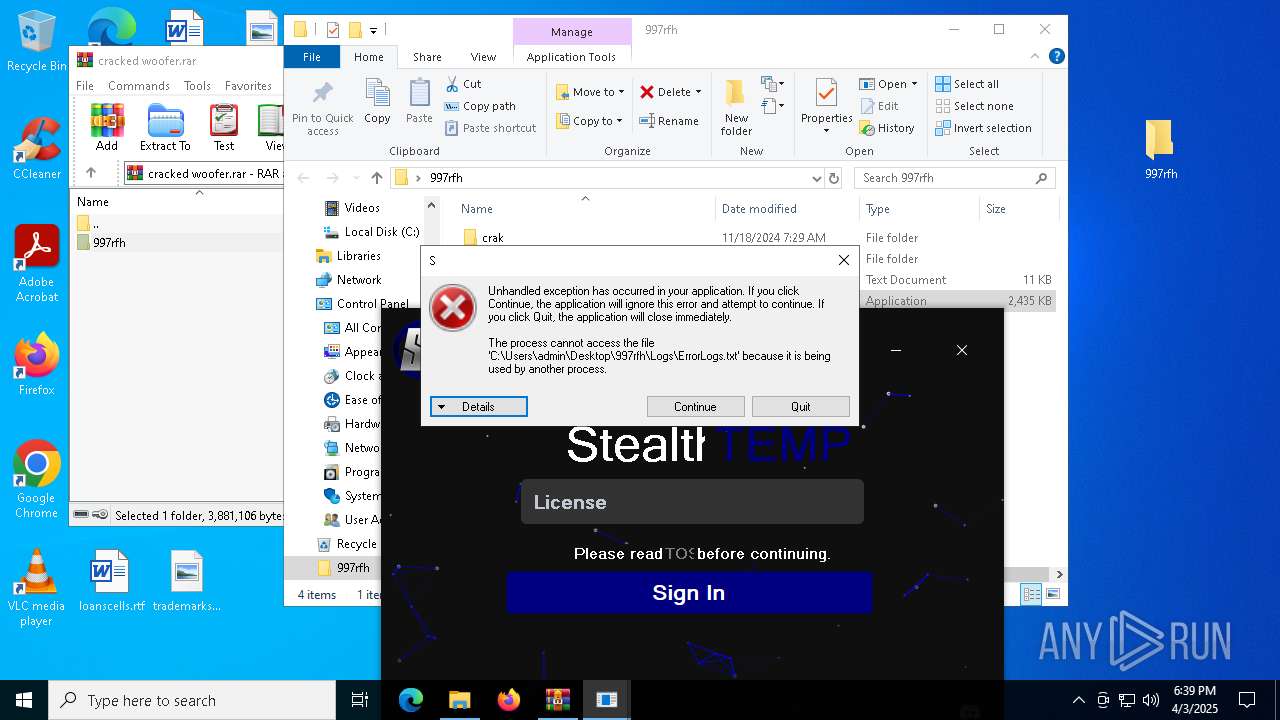
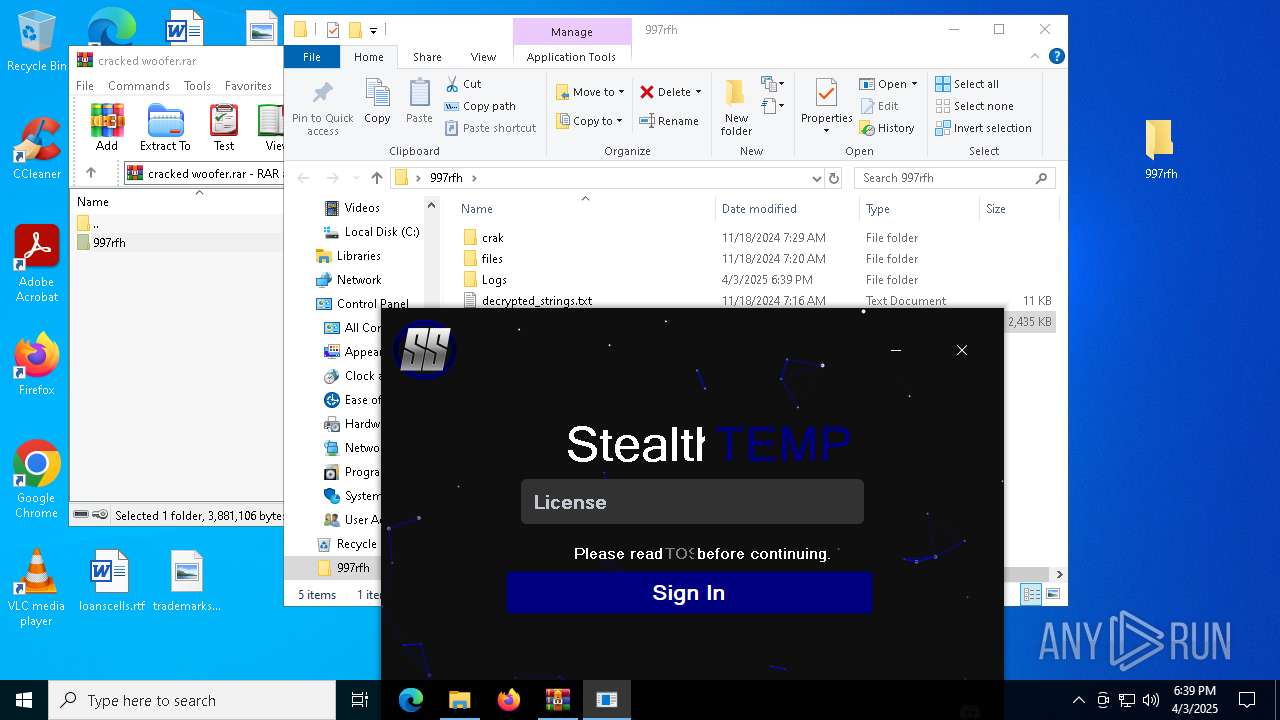
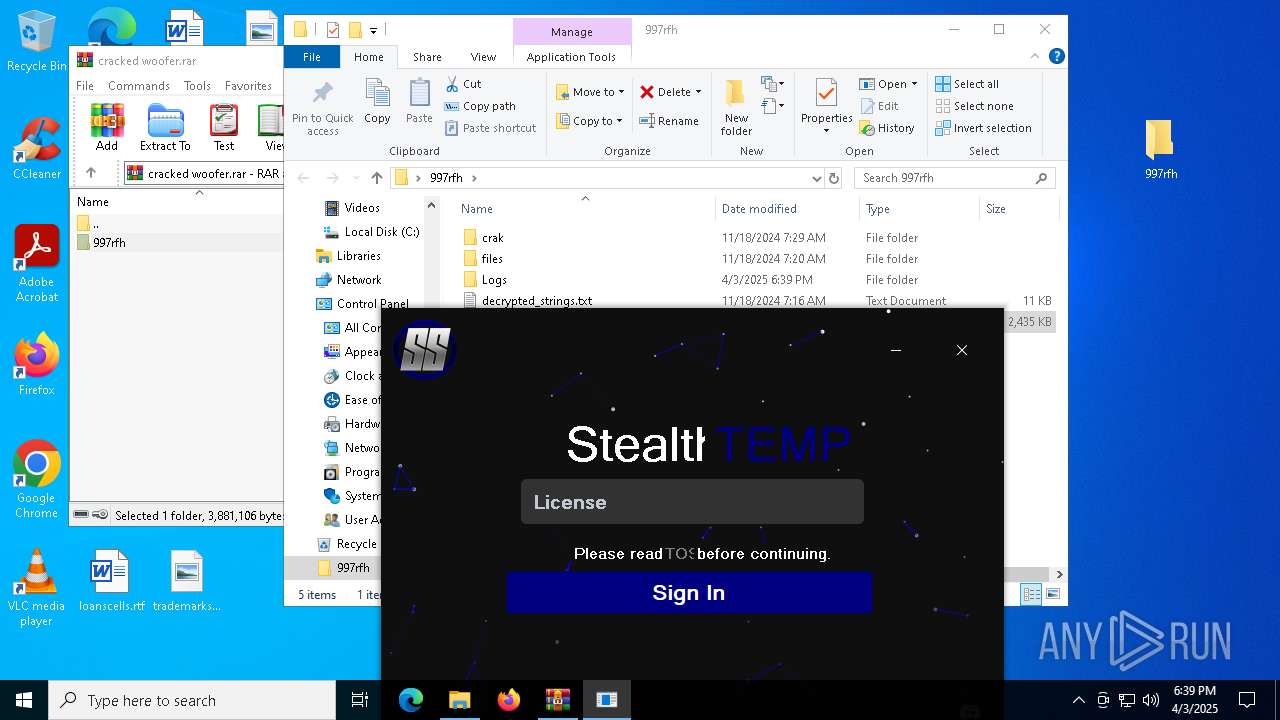
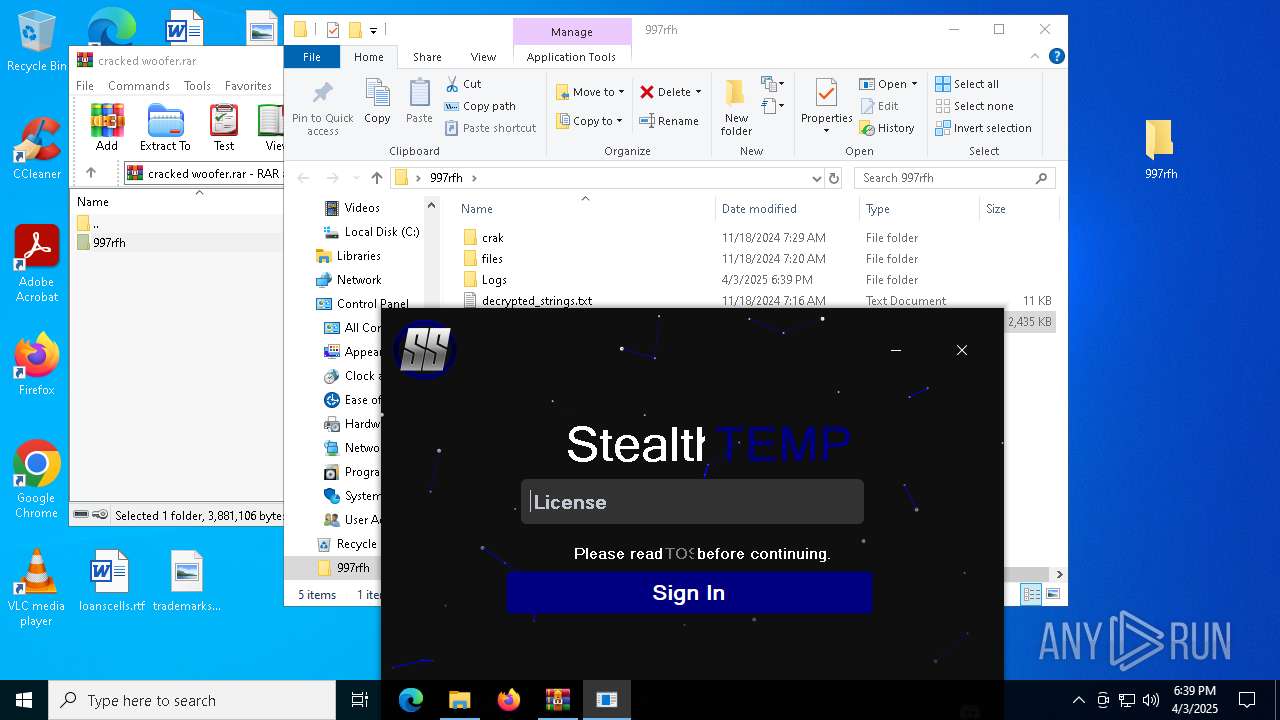
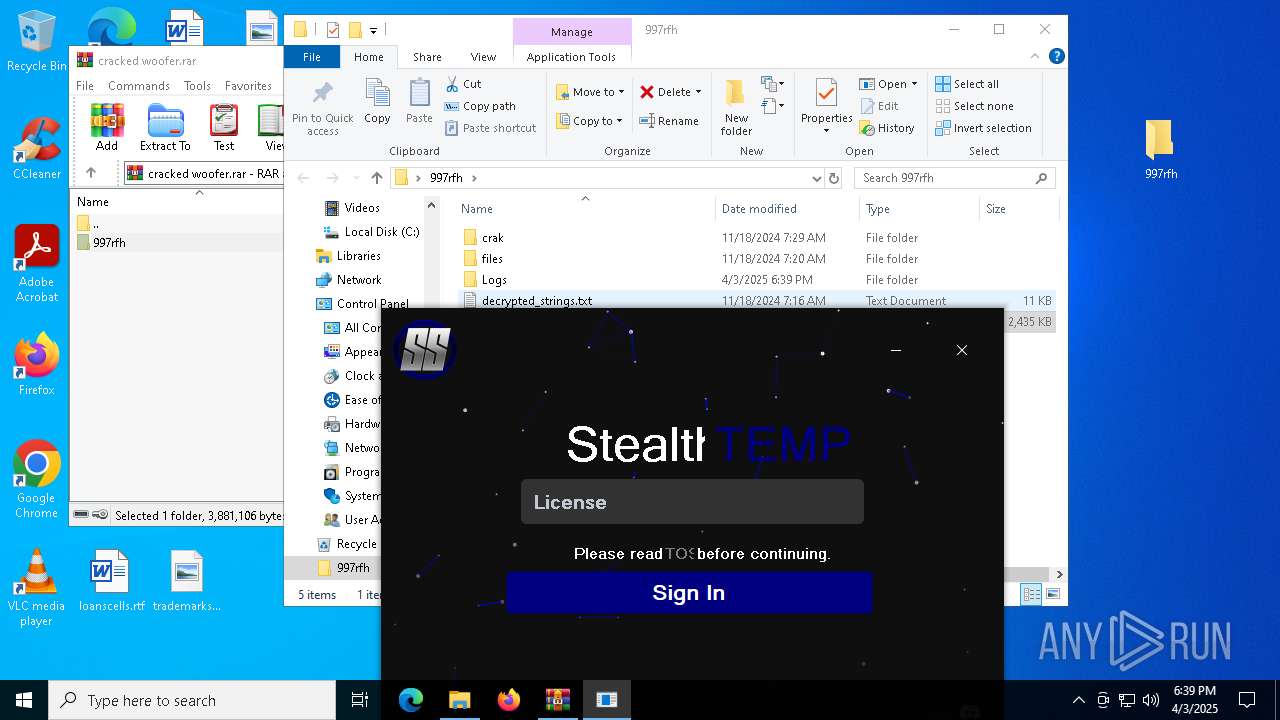
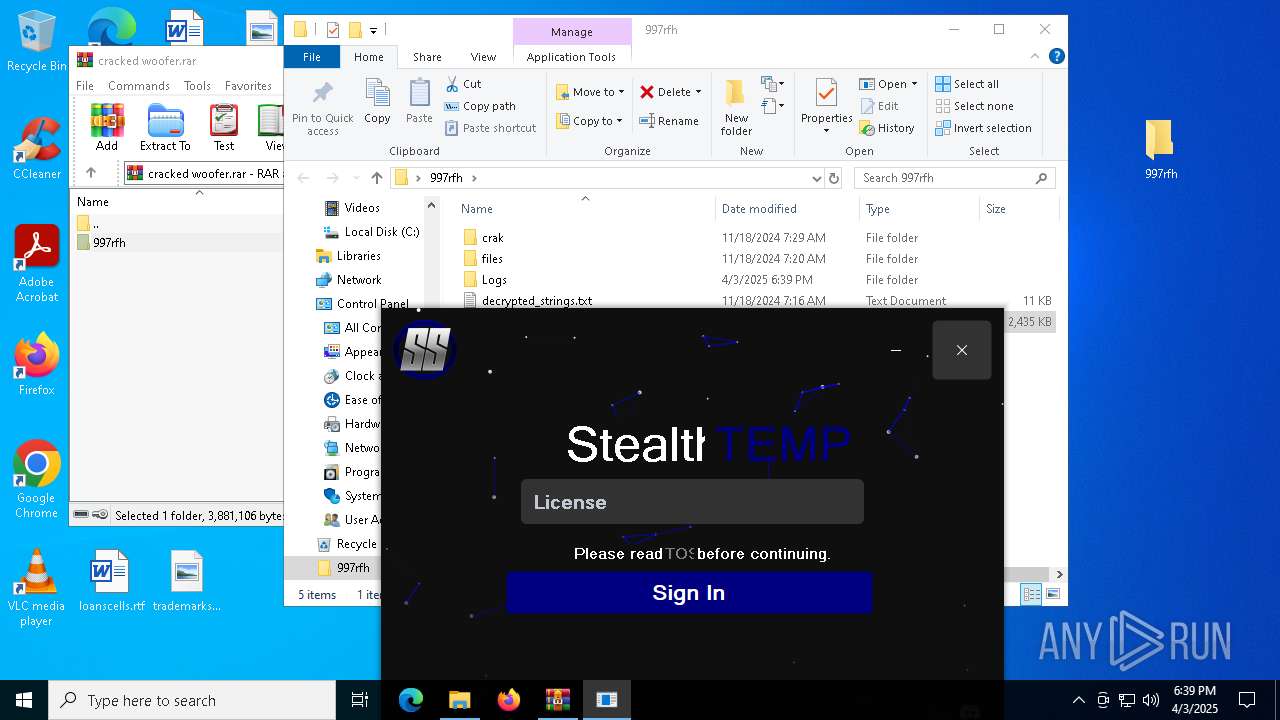
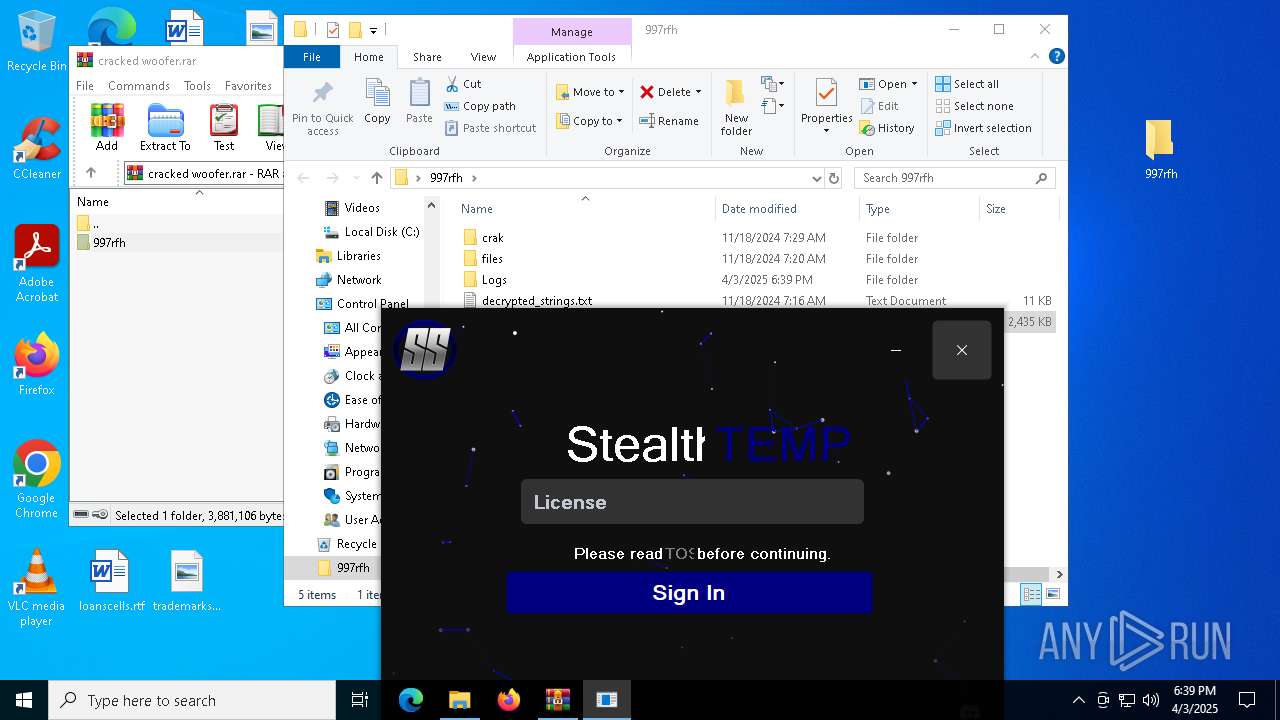
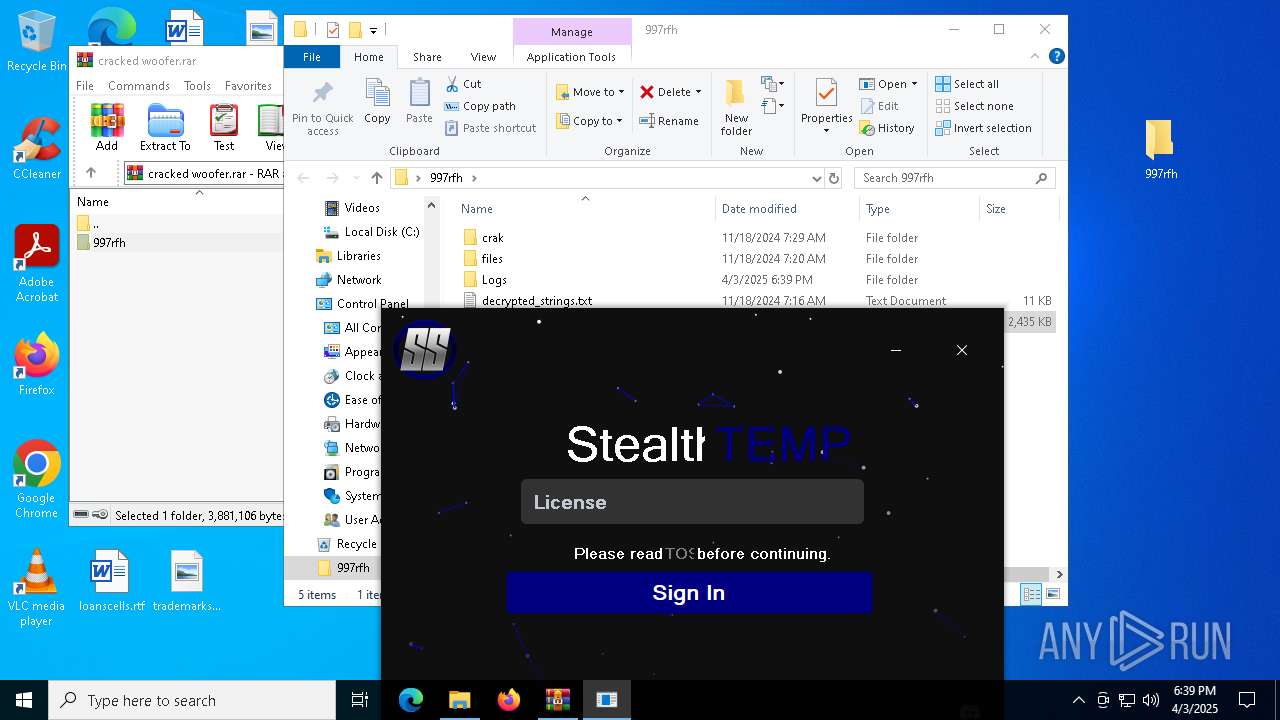
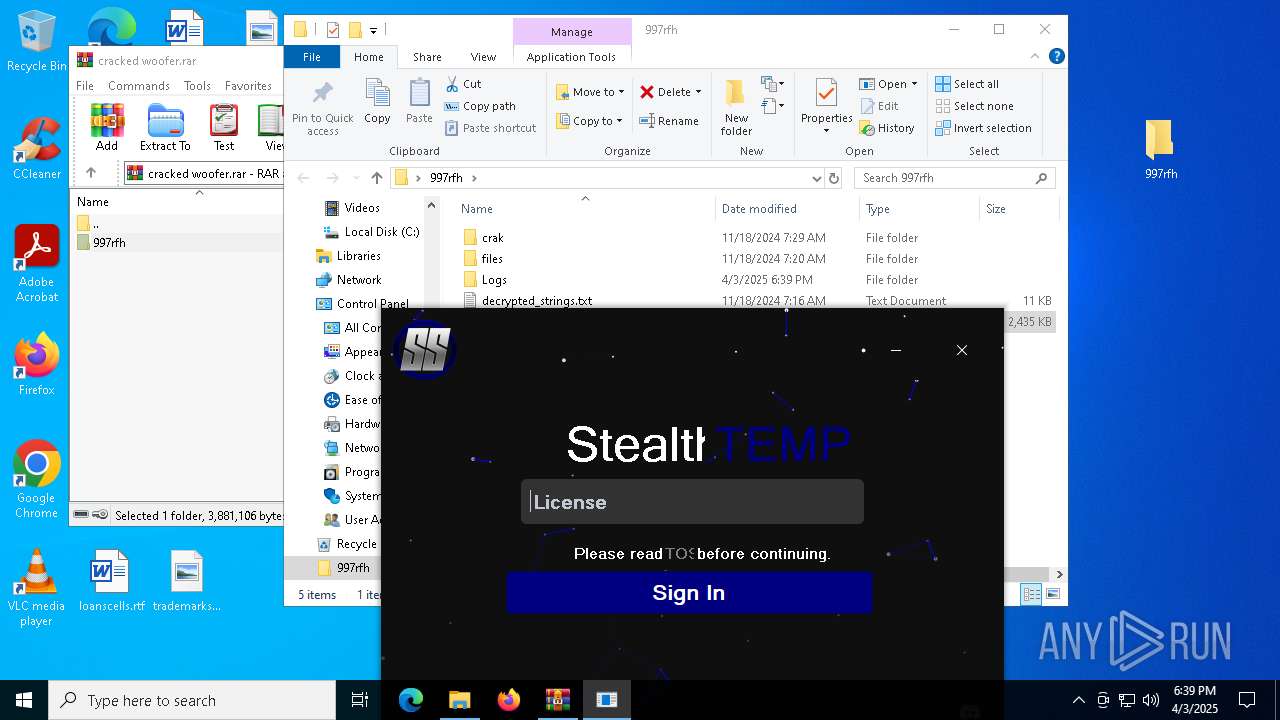
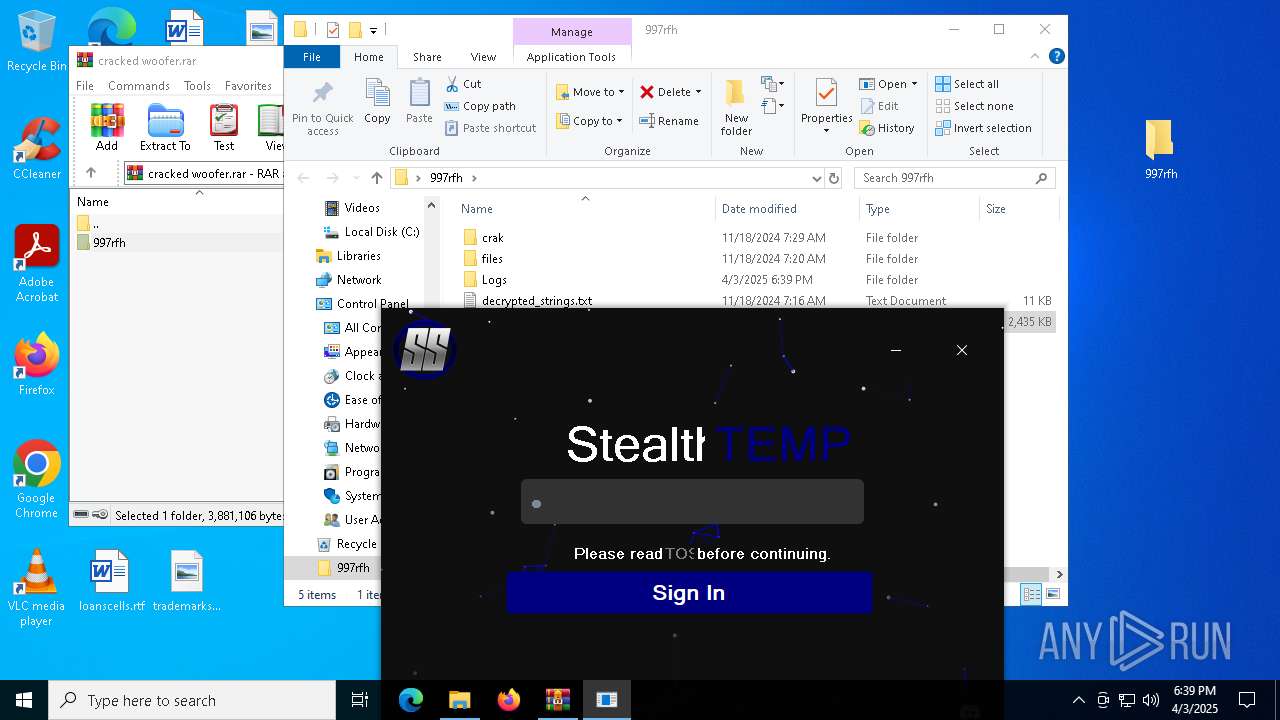
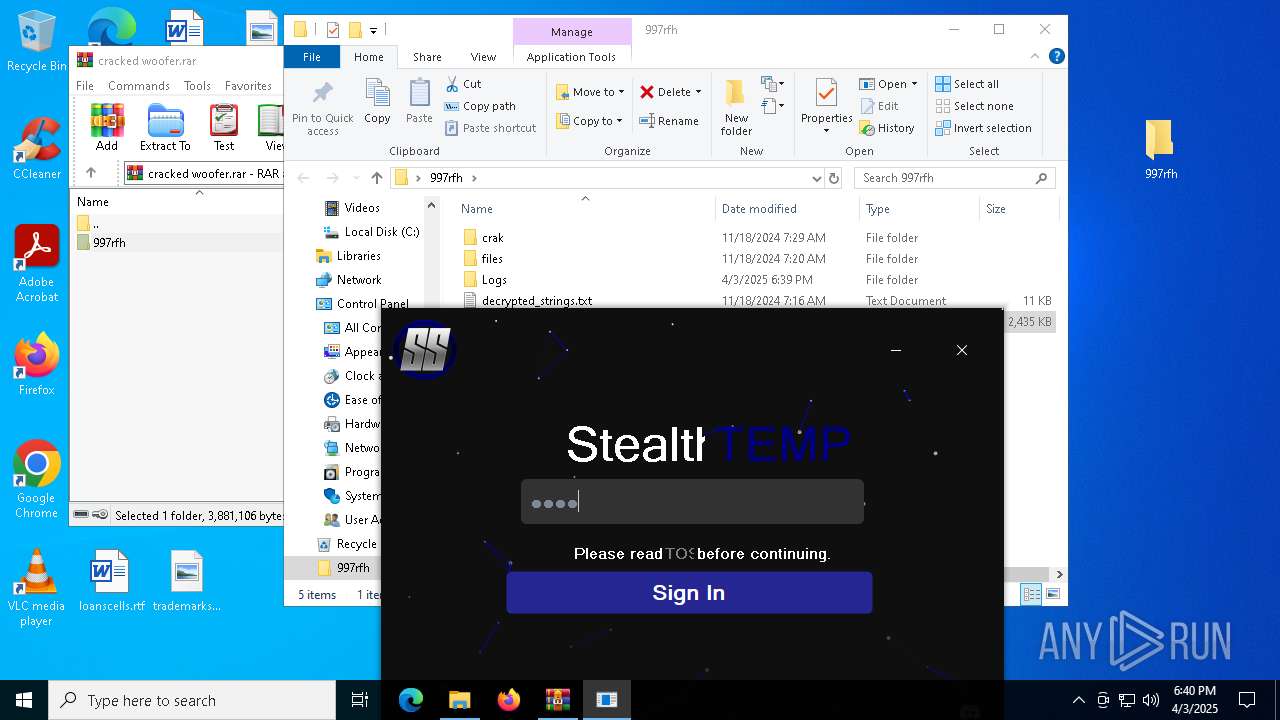
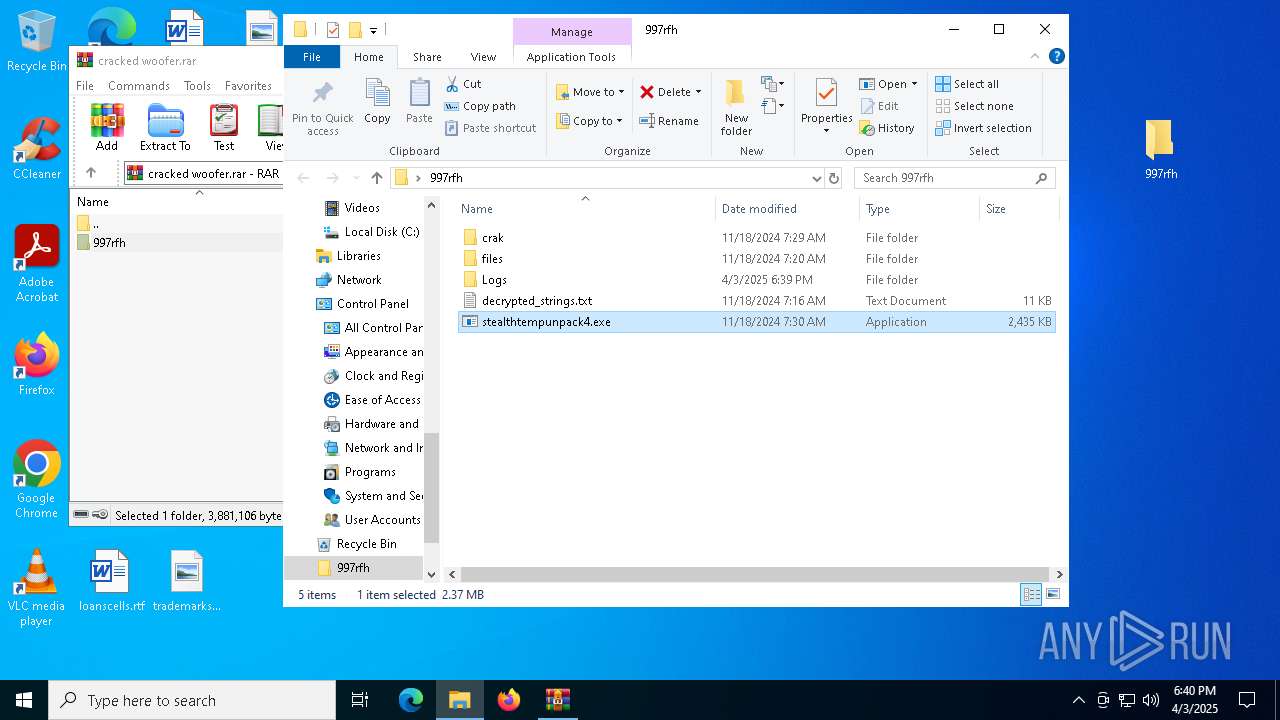
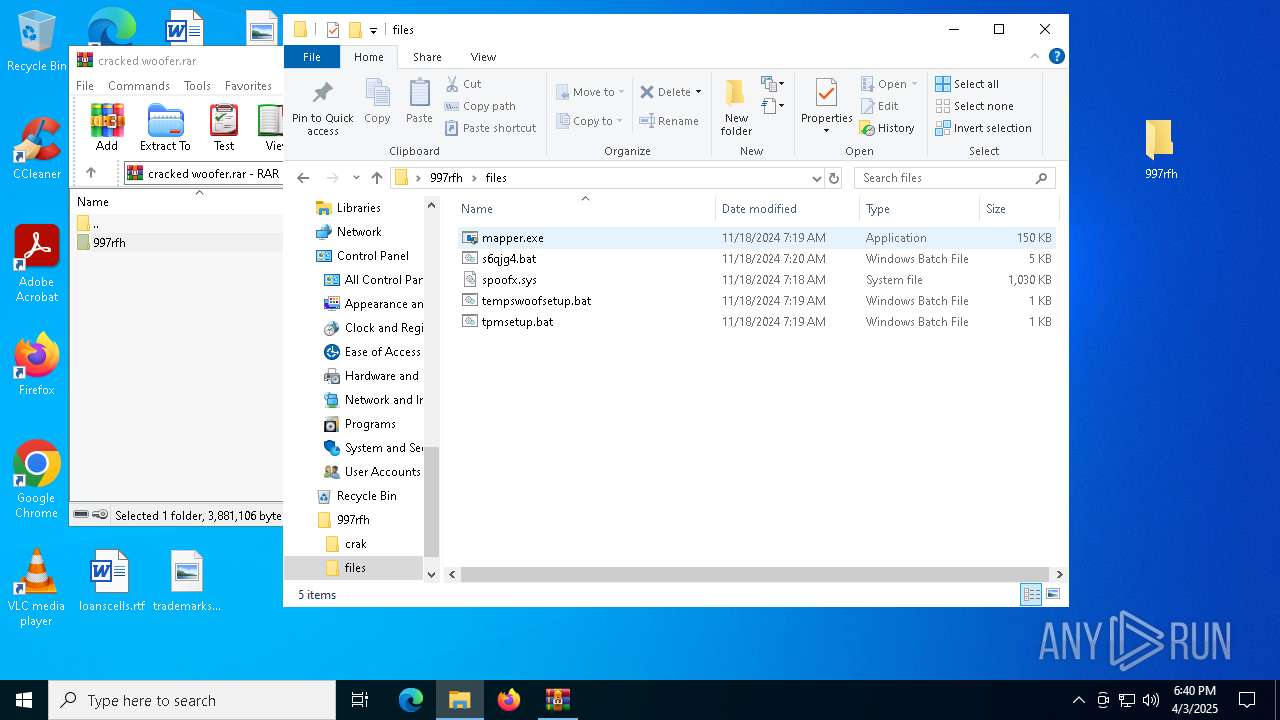
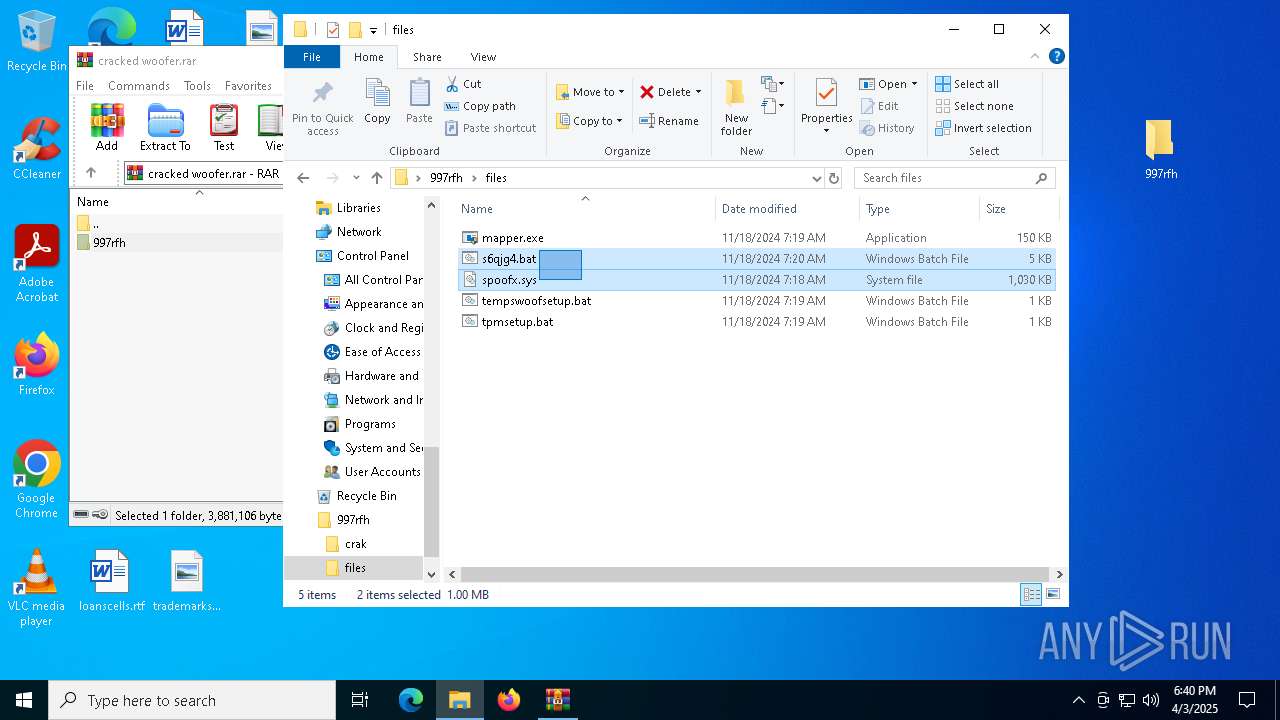
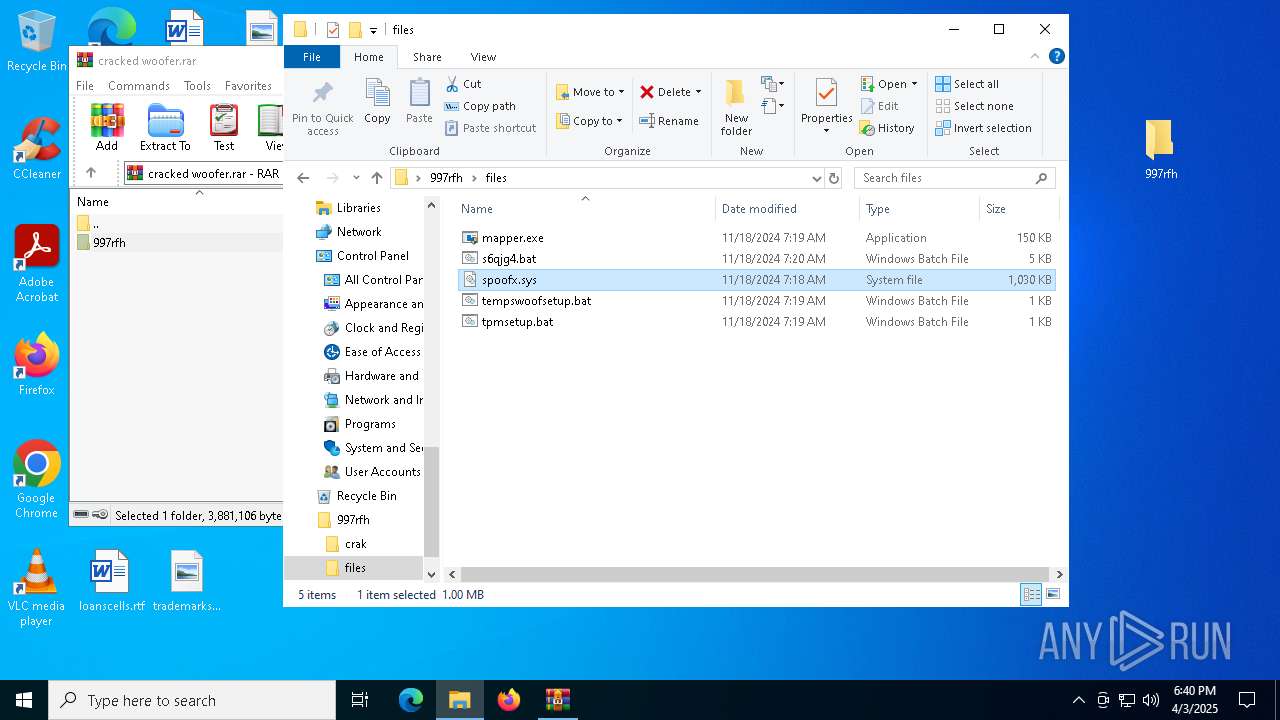
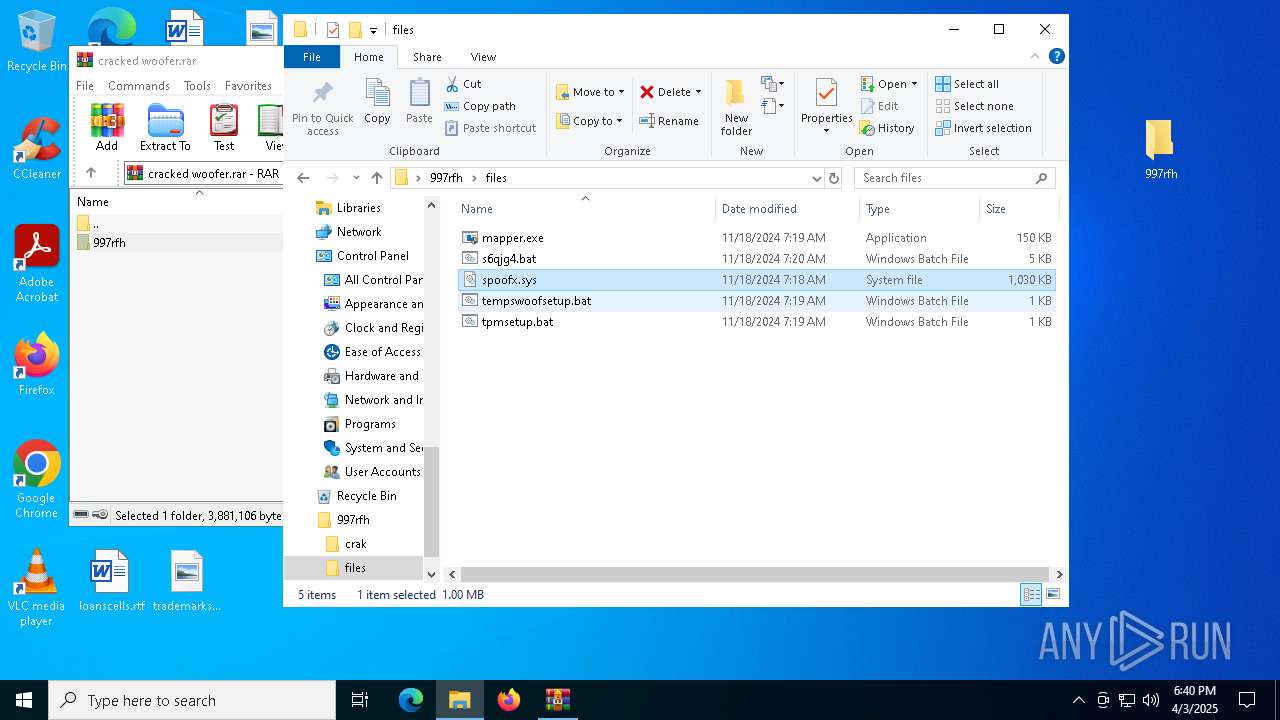
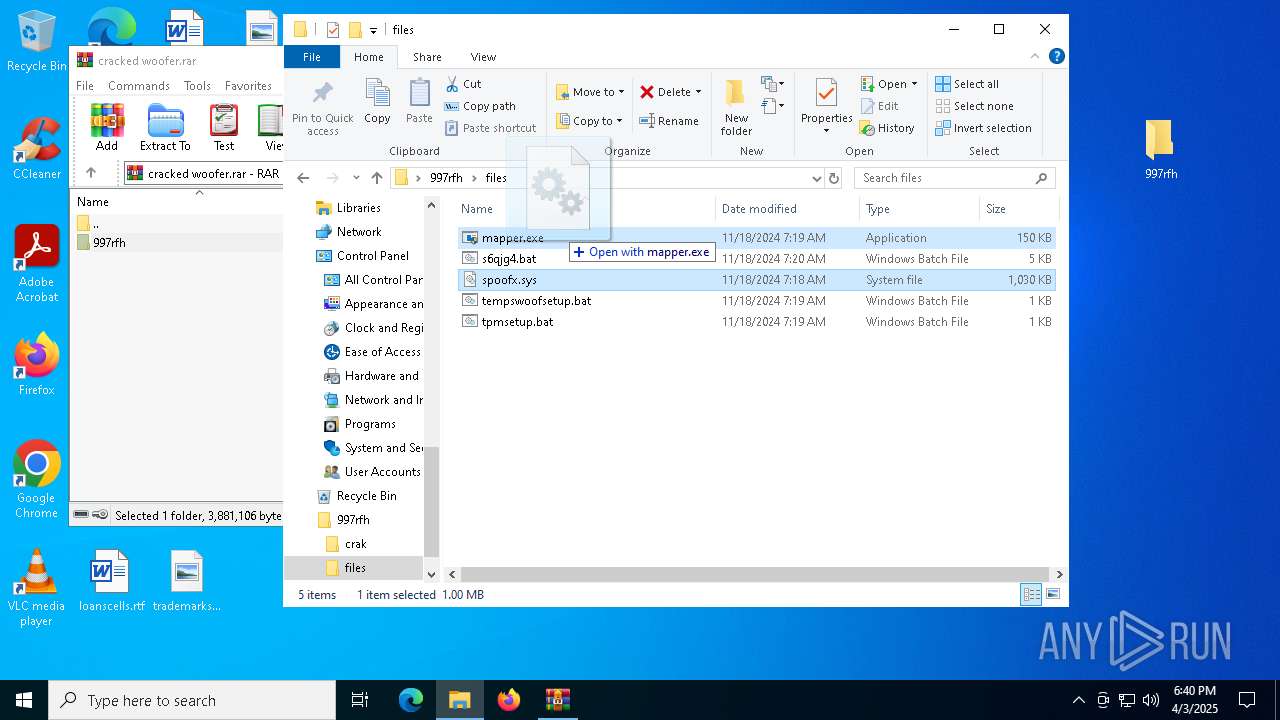
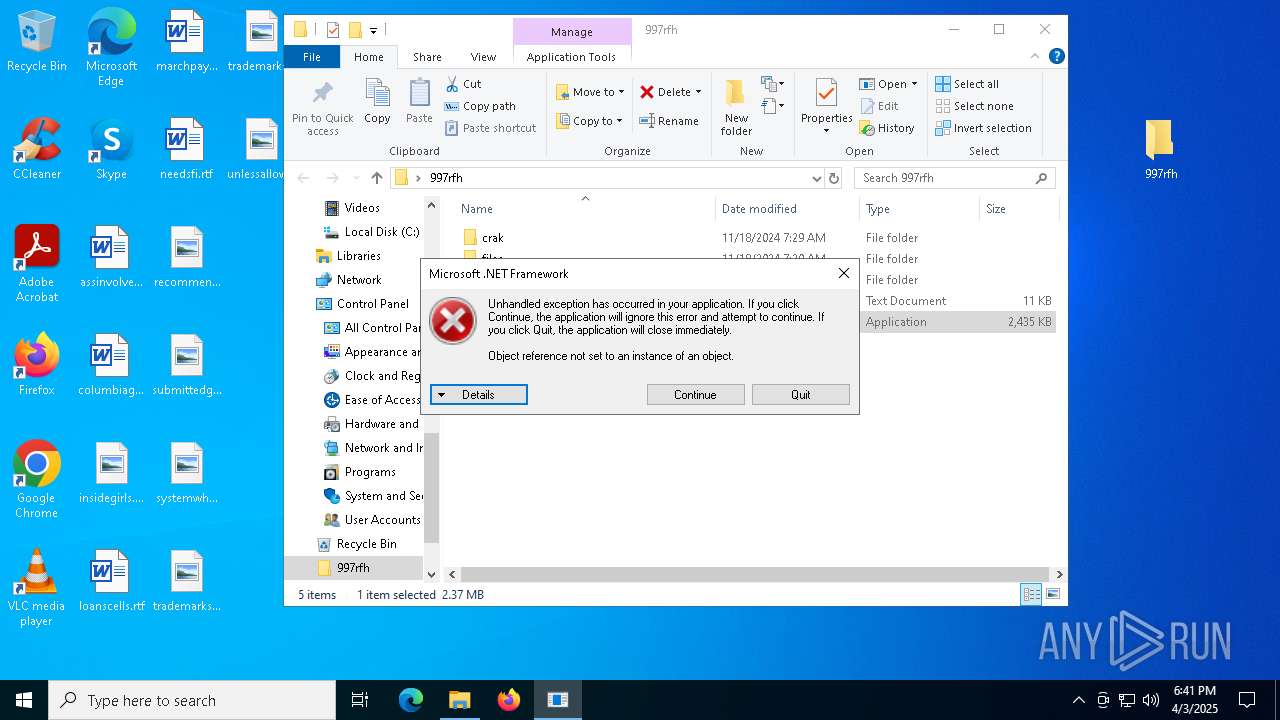
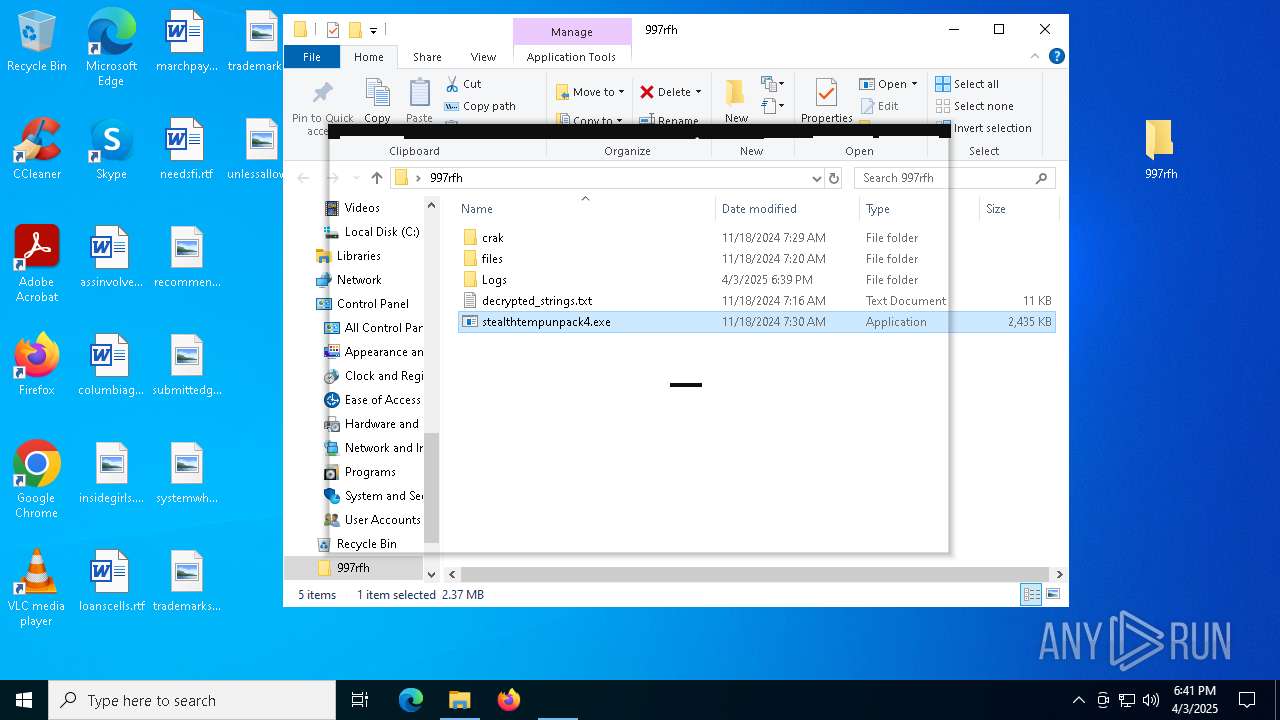
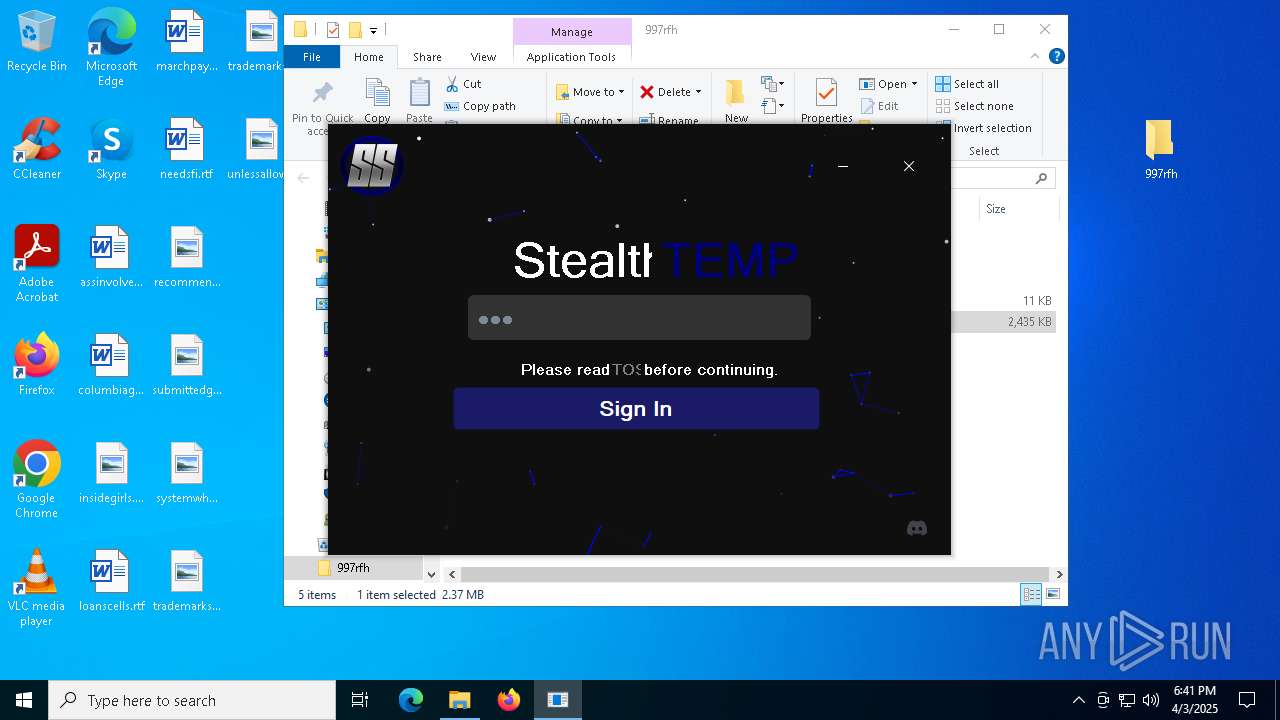
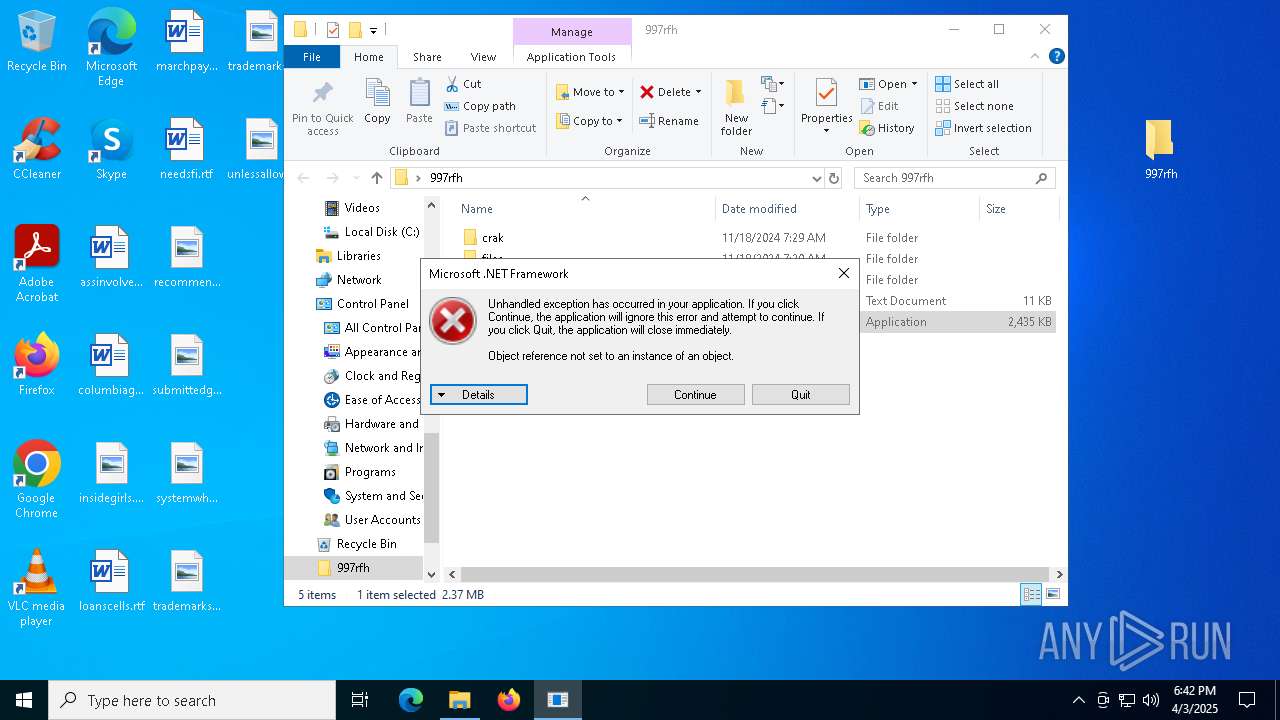
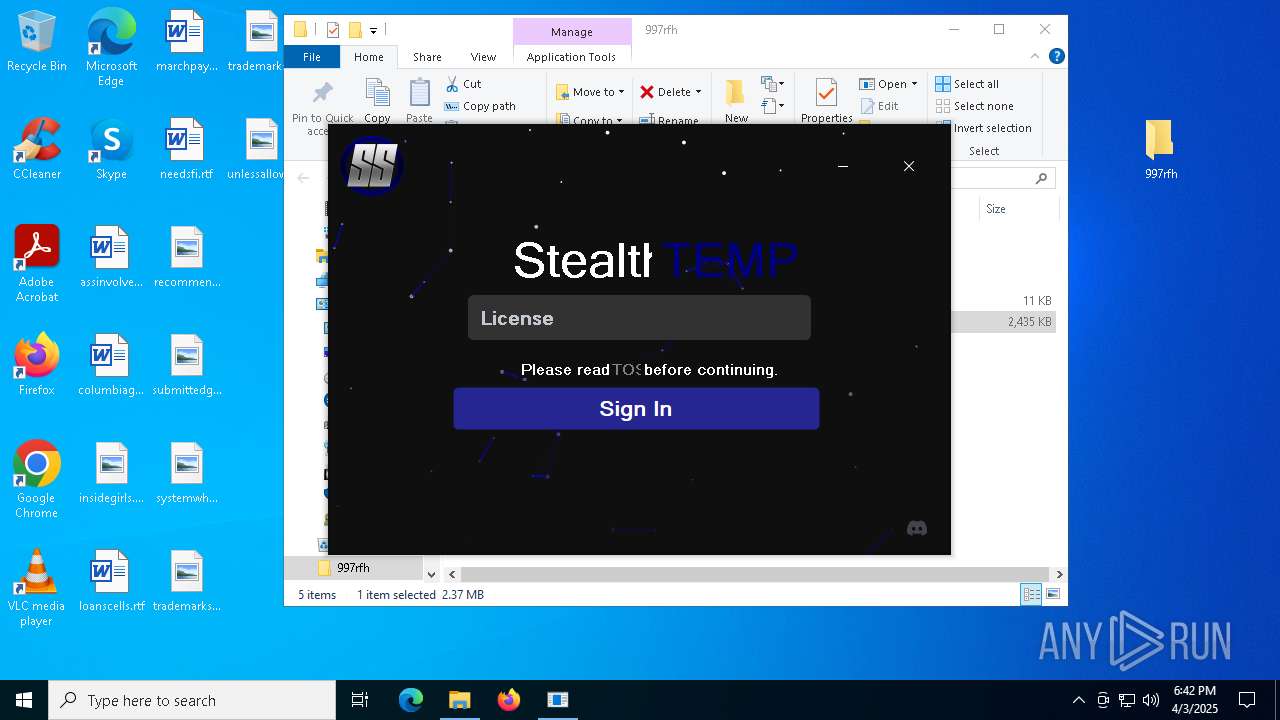
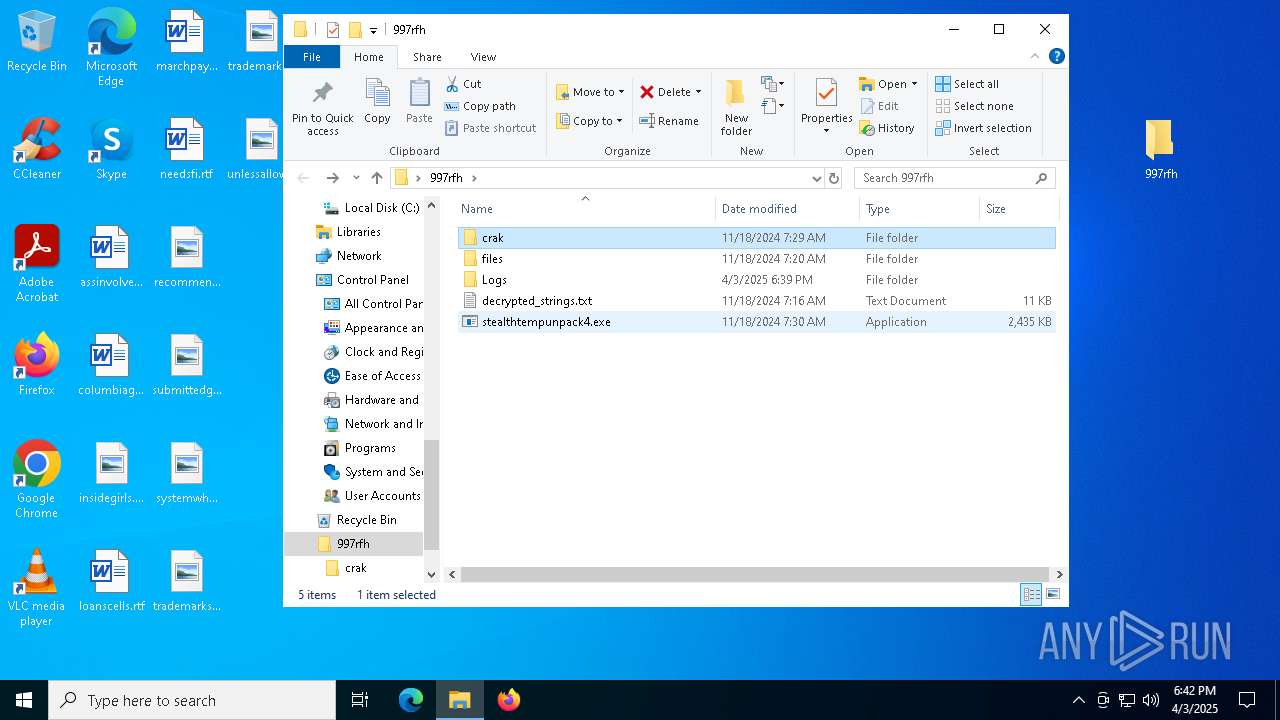
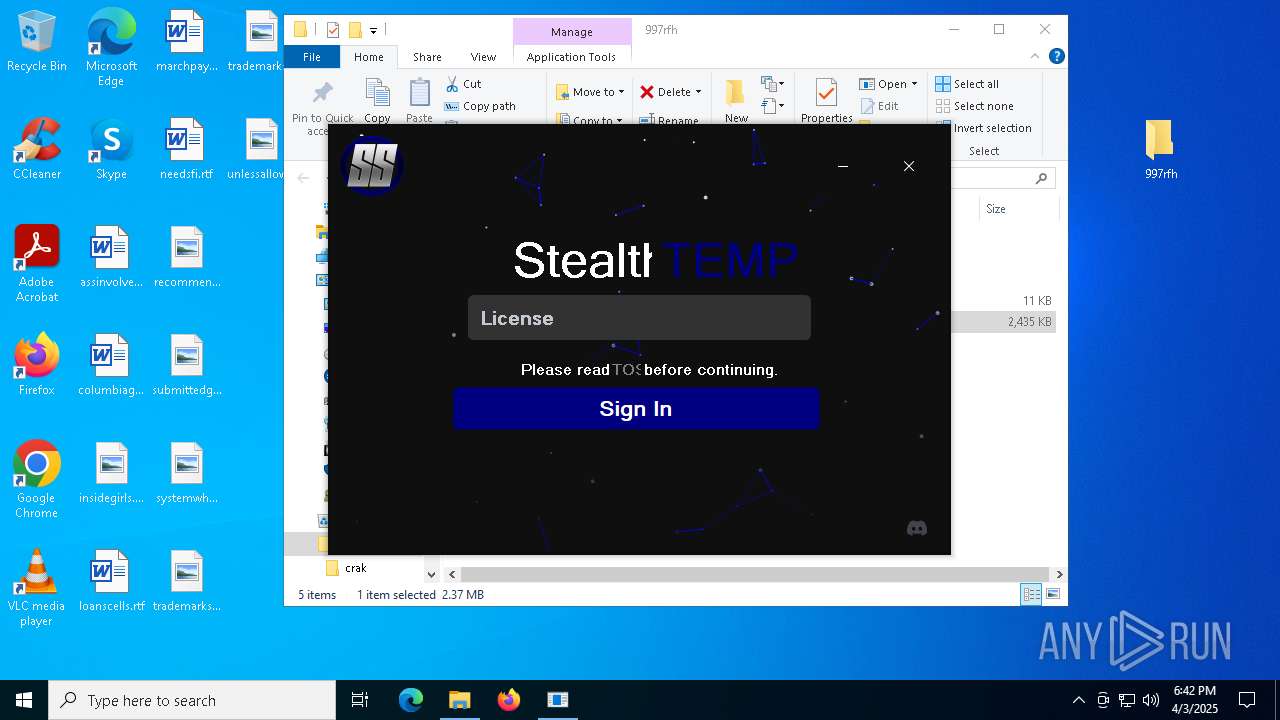
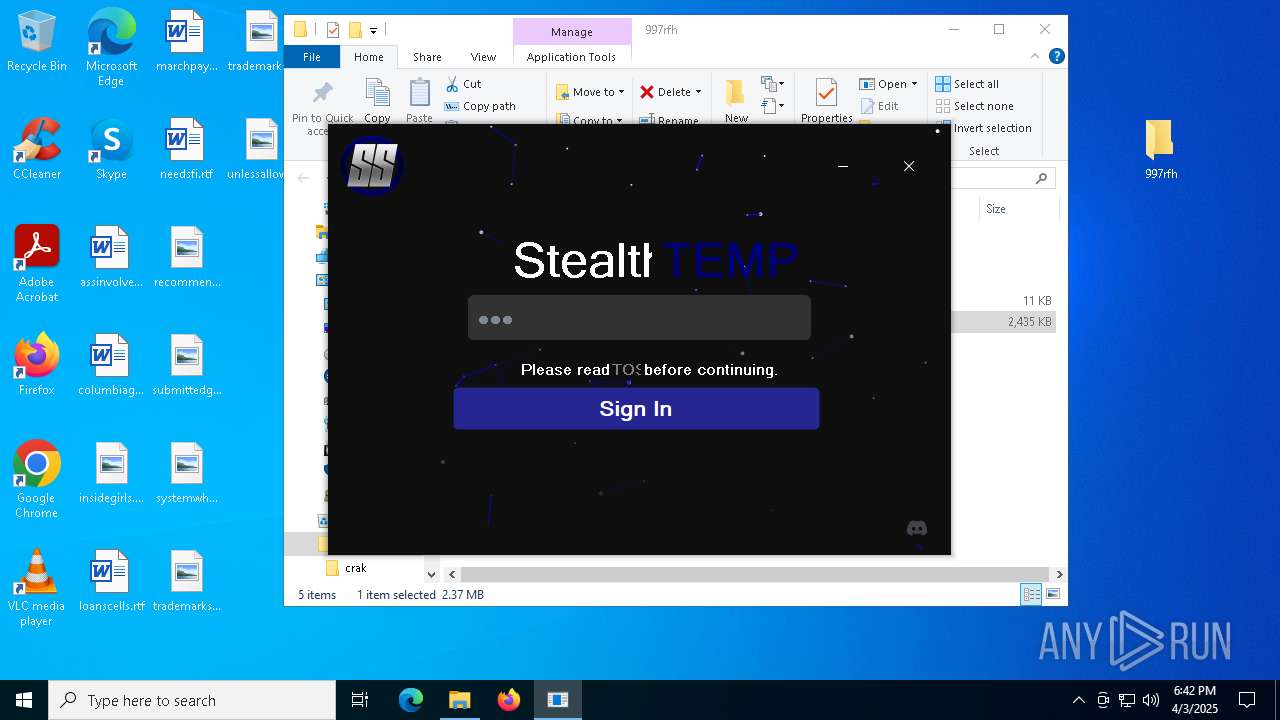
| File name: | cracked woofer.rar |
| Full analysis: | https://app.any.run/tasks/2e85ac1a-2bb6-499a-8193-61fd89af4788 |
| Verdict: | Malicious activity |
| Analysis date: | April 03, 2025, 18:39:13 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-rar |
| File info: | RAR archive data, v5 |
| MD5: | EF43D3BBF7382F0FD67DF260FAD9AE19 |
| SHA1: | C33B4A4FA8D23E81AE594DC098D5966BAAC5588B |
| SHA256: | 8FBDD9042E216467650A26F2E8B89EBD320EDA503F55A85C4C886B64C794AA93 |
| SSDEEP: | 98304:ftv8Wt/em1kOF/MfscmUTbQZ94p00QLEmbpRYEnerJ6AUCTgKgd/G7laND66sWXj:p8Vqvr |
MALICIOUS
Executing a file with an untrusted certificate
- mapper.exe (PID: 5332)
- mapper.exe (PID: 660)
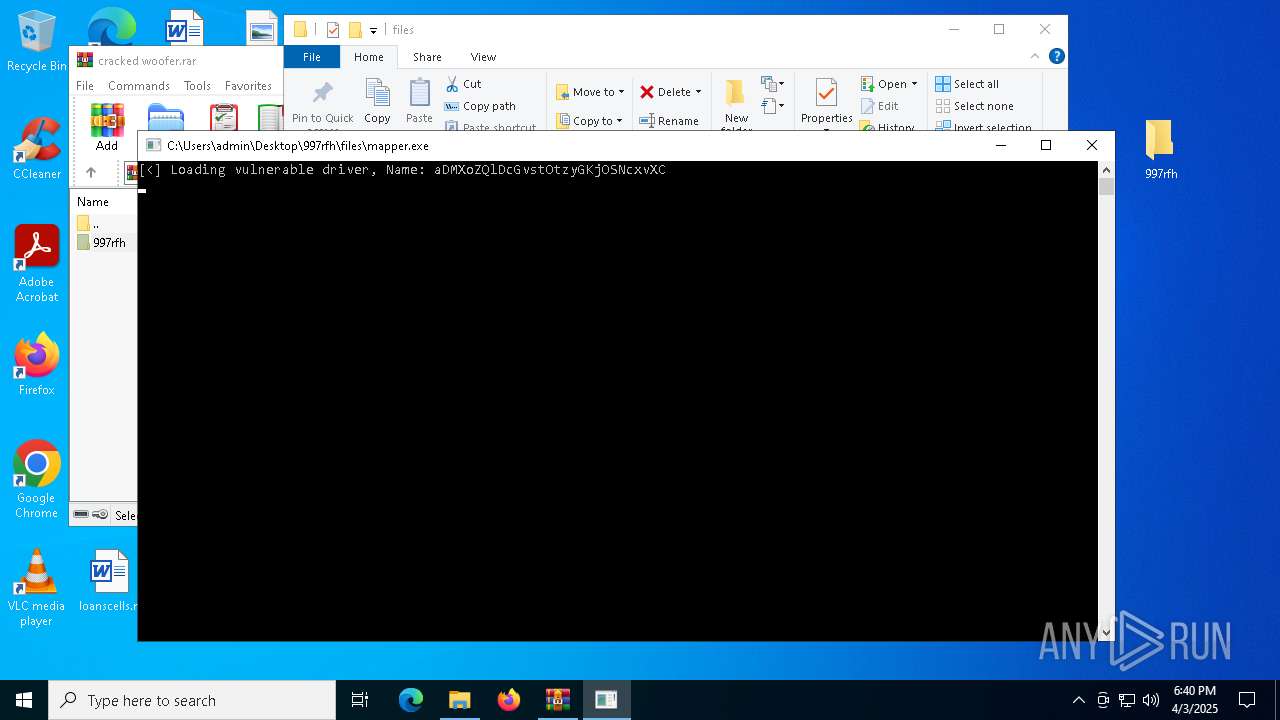
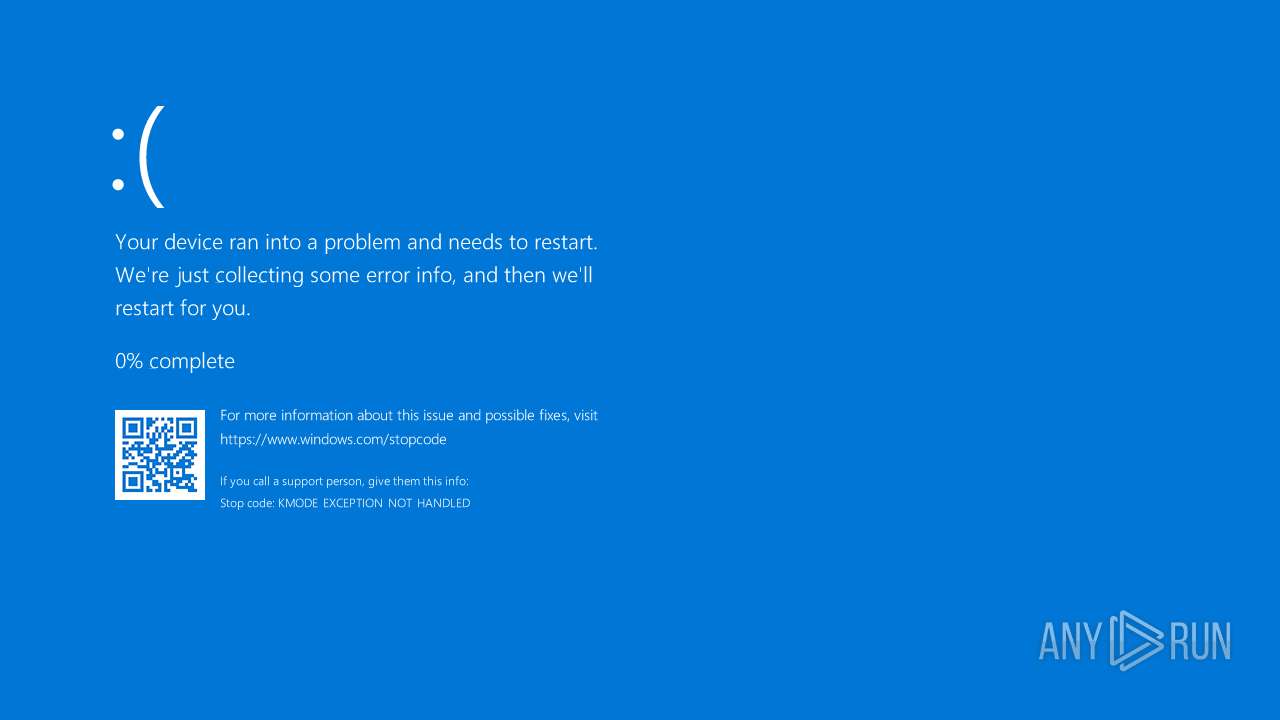
Vulnerable driver has been detected
- mapper.exe (PID: 660)
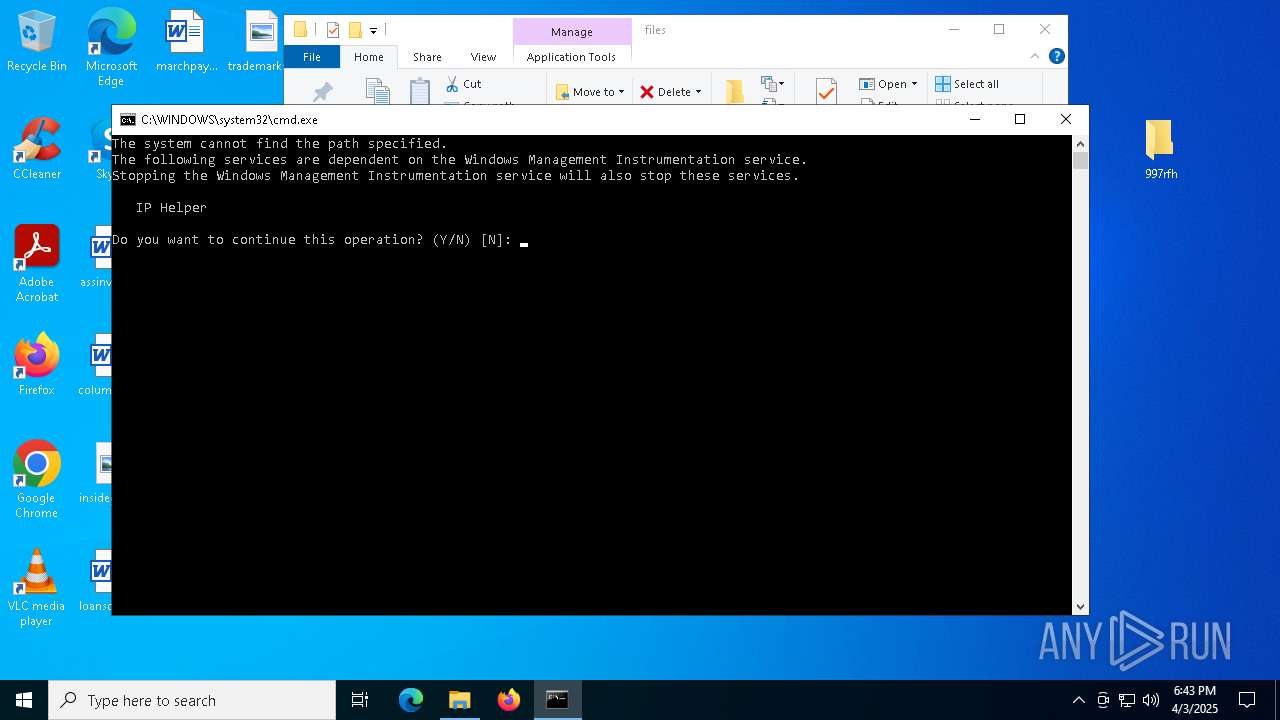
Starts NET.EXE for service management
- net.exe (PID: 1988)
- cmd.exe (PID: 4856)
- net.exe (PID: 6412)
- cmd.exe (PID: 1740)
SUSPICIOUS
Drops a system driver (possible attempt to evade defenses)
- WinRAR.exe (PID: 5960)
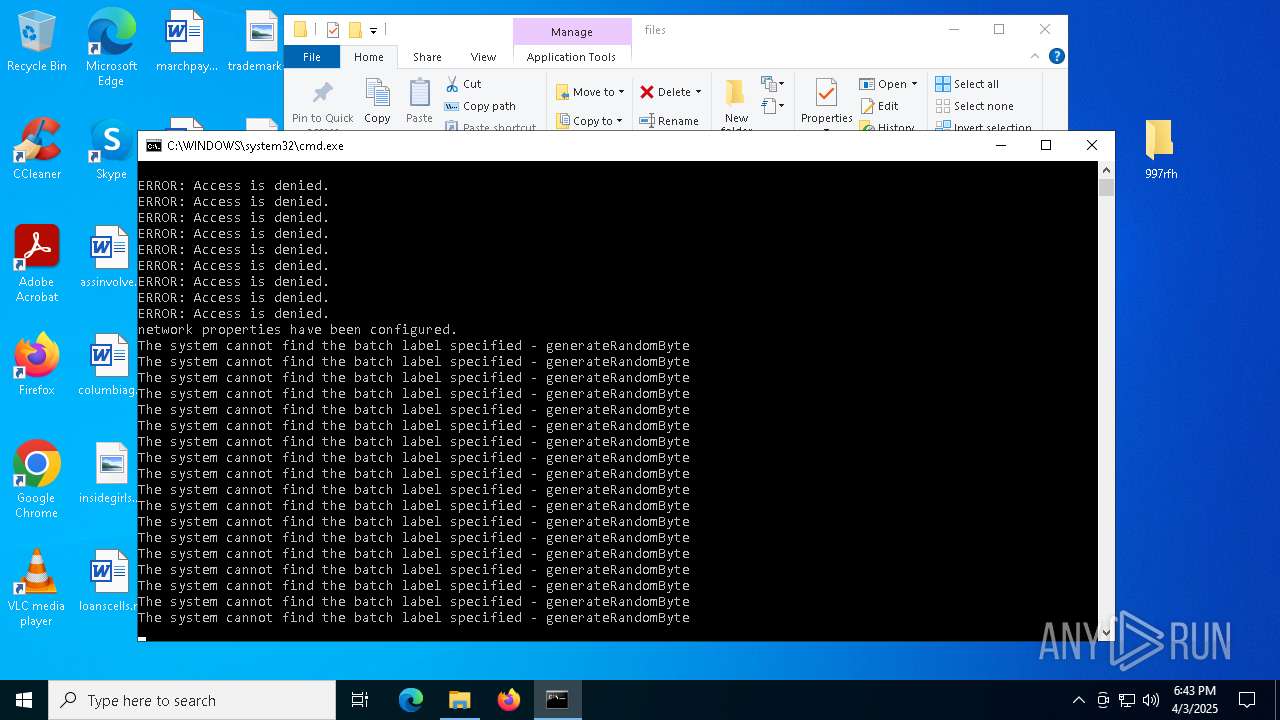
Starts CMD.EXE for commands execution
- stealthtempunpack4.exe (PID: 7700)
- cmd.exe (PID: 8076)
- stealthtempunpack4.exe (PID: 6172)
- cmd.exe (PID: 6948)
- stealthtempunpack4.exe (PID: 6864)
- cmd.exe (PID: 6532)
- stealthtempunpack4.exe (PID: 5604)
- cmd.exe (PID: 768)
- cmd.exe (PID: 2864)
- cmd.exe (PID: 1792)
There is functionality for taking screenshot (YARA)
- stealthtempunpack4.exe (PID: 7700)
Application launched itself
- cmd.exe (PID: 8076)
- cmd.exe (PID: 6532)
- cmd.exe (PID: 6948)
- cmd.exe (PID: 2864)
- cmd.exe (PID: 768)
- cmd.exe (PID: 1792)
Uses TIMEOUT.EXE to delay execution
- cmd.exe (PID: 8132)
- cmd.exe (PID: 7004)
- cmd.exe (PID: 6604)
- cmd.exe (PID: 5780)
Executable content was dropped or overwritten
- mapper.exe (PID: 660)
Creates or modifies Windows services
- mapper.exe (PID: 660)
The process executes via Task Scheduler
- PLUGScheduler.exe (PID: 4296)
Using 'findstr.exe' to search for text patterns in files and output
- cmd.exe (PID: 1080)
- cmd.exe (PID: 956)
- cmd.exe (PID: 6476)
- cmd.exe (PID: 4828)
Uses WMIC.EXE to obtain information about the network interface controller
- cmd.exe (PID: 1080)
- cmd.exe (PID: 956)
- cmd.exe (PID: 6476)
- cmd.exe (PID: 4828)
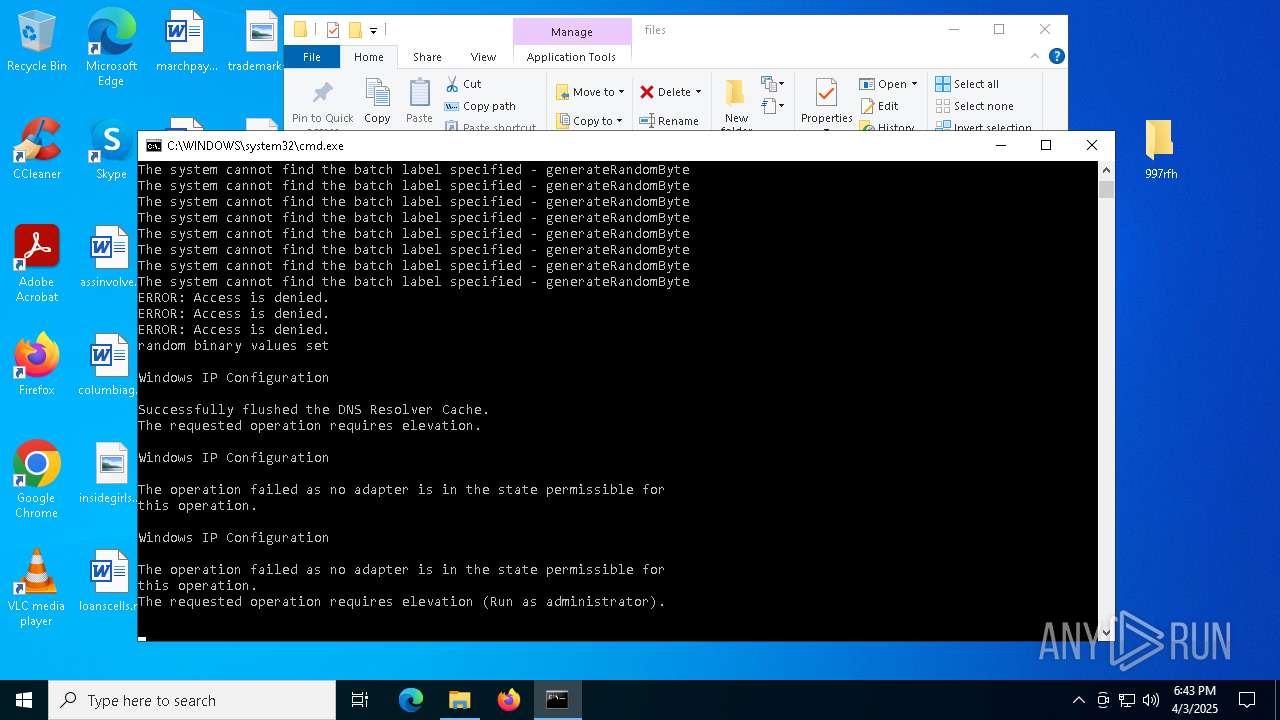
Uses NETSH.EXE to change the status of the firewall
- cmd.exe (PID: 2864)
- cmd.exe (PID: 1792)
Suspicious use of NETSH.EXE
- cmd.exe (PID: 2864)
- cmd.exe (PID: 1792)
Starts SC.EXE for service management
- cmd.exe (PID: 2864)
- cmd.exe (PID: 1792)
Windows service management via SC.EXE
- sc.exe (PID: 6160)
- sc.exe (PID: 3612)
- sc.exe (PID: 1520)
- sc.exe (PID: 2424)
Process uses IPCONFIG to get network configuration information
- cmd.exe (PID: 2864)
- cmd.exe (PID: 1792)
Uses REG/REGEDIT.EXE to modify registry
- cmd.exe (PID: 2864)
- cmd.exe (PID: 1792)
Process uses IPCONFIG to clear DNS cache
- cmd.exe (PID: 2864)
- cmd.exe (PID: 1792)
Process uses IPCONFIG to discard the IP address configuration
- cmd.exe (PID: 2864)
- cmd.exe (PID: 1792)
Uses WMIC.EXE to obtain network information
- cmd.exe (PID: 4932)
- cmd.exe (PID: 6432)
Process uses IPCONFIG to renew DHCP configuration
- cmd.exe (PID: 2864)
- cmd.exe (PID: 1792)
INFO
Executable content was dropped or overwritten
- WinRAR.exe (PID: 5960)
Reads the machine GUID from the registry
- stealthtempunpack4.exe (PID: 7700)
- stealthtempunpack4.exe (PID: 6172)
- stealthtempunpack4.exe (PID: 6864)
- stealthtempunpack4.exe (PID: 5604)
Checks supported languages
- stealthtempunpack4.exe (PID: 7700)
- mapper.exe (PID: 660)
- PLUGScheduler.exe (PID: 4296)
- stealthtempunpack4.exe (PID: 6172)
- KeyAuthEmulator.exe (PID: 7144)
- stealthtempunpack4.exe (PID: 5604)
- stealthtempunpack4.exe (PID: 6864)
Checks proxy server information
- stealthtempunpack4.exe (PID: 7700)
- stealthtempunpack4.exe (PID: 6172)
- stealthtempunpack4.exe (PID: 6864)
- stealthtempunpack4.exe (PID: 5604)
Manual execution by a user
- stealthtempunpack4.exe (PID: 7700)
- mapper.exe (PID: 5332)
- mapper.exe (PID: 660)
- stealthtempunpack4.exe (PID: 6172)
- KeyAuthEmulator.exe (PID: 7144)
- stealthtempunpack4.exe (PID: 5604)
- stealthtempunpack4.exe (PID: 6864)
- cmd.exe (PID: 4856)
- cmd.exe (PID: 1740)
- cmd.exe (PID: 2864)
- cmd.exe (PID: 1792)
Disables trace logs
- stealthtempunpack4.exe (PID: 7700)
- stealthtempunpack4.exe (PID: 6172)
- stealthtempunpack4.exe (PID: 6864)
- stealthtempunpack4.exe (PID: 5604)
- netsh.exe (PID: 6120)
- netsh.exe (PID: 640)
- netsh.exe (PID: 6044)
- netsh.exe (PID: 6116)
- netsh.exe (PID: 5020)
- netsh.exe (PID: 5280)
- netsh.exe (PID: 5660)
- netsh.exe (PID: 6644)
Reads the computer name
- stealthtempunpack4.exe (PID: 7700)
- PLUGScheduler.exe (PID: 4296)
- stealthtempunpack4.exe (PID: 6172)
- KeyAuthEmulator.exe (PID: 7144)
- stealthtempunpack4.exe (PID: 5604)
- stealthtempunpack4.exe (PID: 6864)
Reads the software policy settings
- slui.exe (PID: 7288)
Create files in a temporary directory
- mapper.exe (PID: 660)
The sample compiled with english language support
- mapper.exe (PID: 660)
Creates files in the program directory
- PLUGScheduler.exe (PID: 4296)
Reads security settings of Internet Explorer
- WMIC.exe (PID: 1184)
- netsh.exe (PID: 6348)
- netsh.exe (PID: 6064)
- WMIC.exe (PID: 2808)
- WMIC.exe (PID: 4968)
- WMIC.exe (PID: 6408)
- netsh.exe (PID: 1364)
- netsh.exe (PID: 3928)
- WMIC.exe (PID: 5632)
- WMIC.exe (PID: 1380)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .rar | | | RAR compressed archive (v5.0) (61.5) |
|---|---|---|
| .rar | | | RAR compressed archive (gen) (38.4) |
EXIF
ZIP
| FileVersion: | RAR v5 |
|---|---|
| CompressedSize: | 220 |
| UncompressedSize: | 437 |
| OperatingSystem: | Win32 |
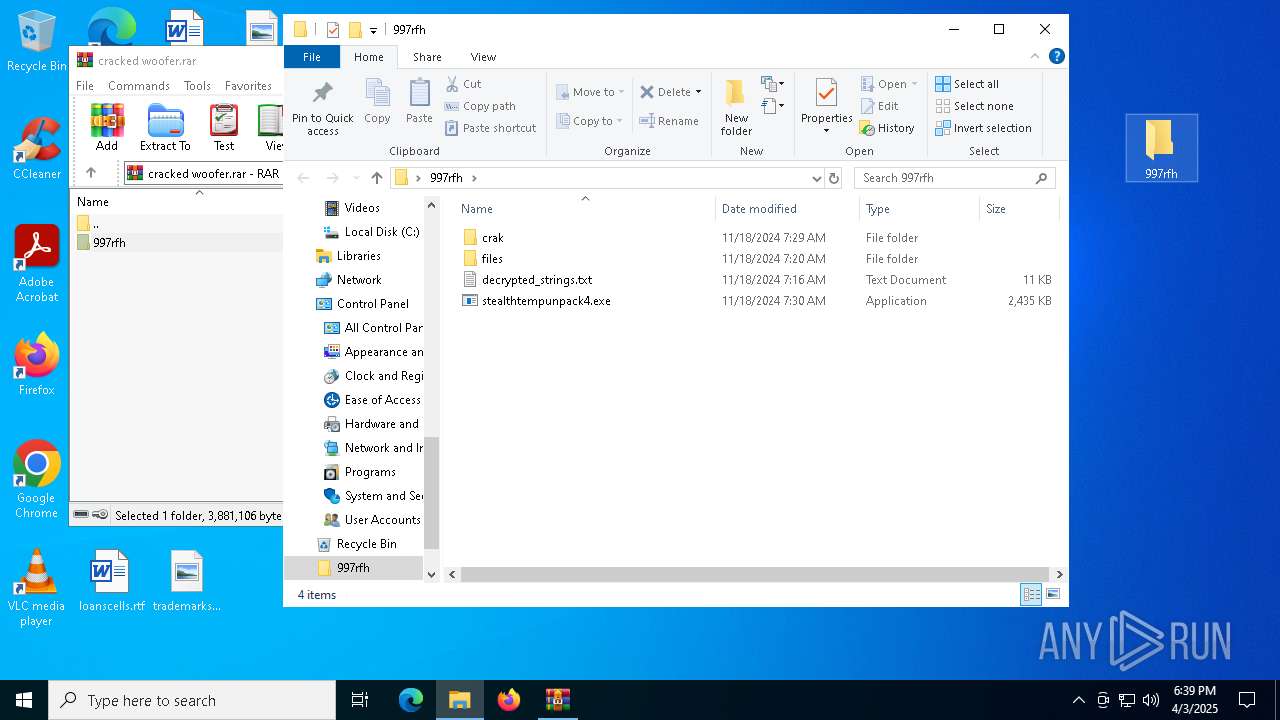
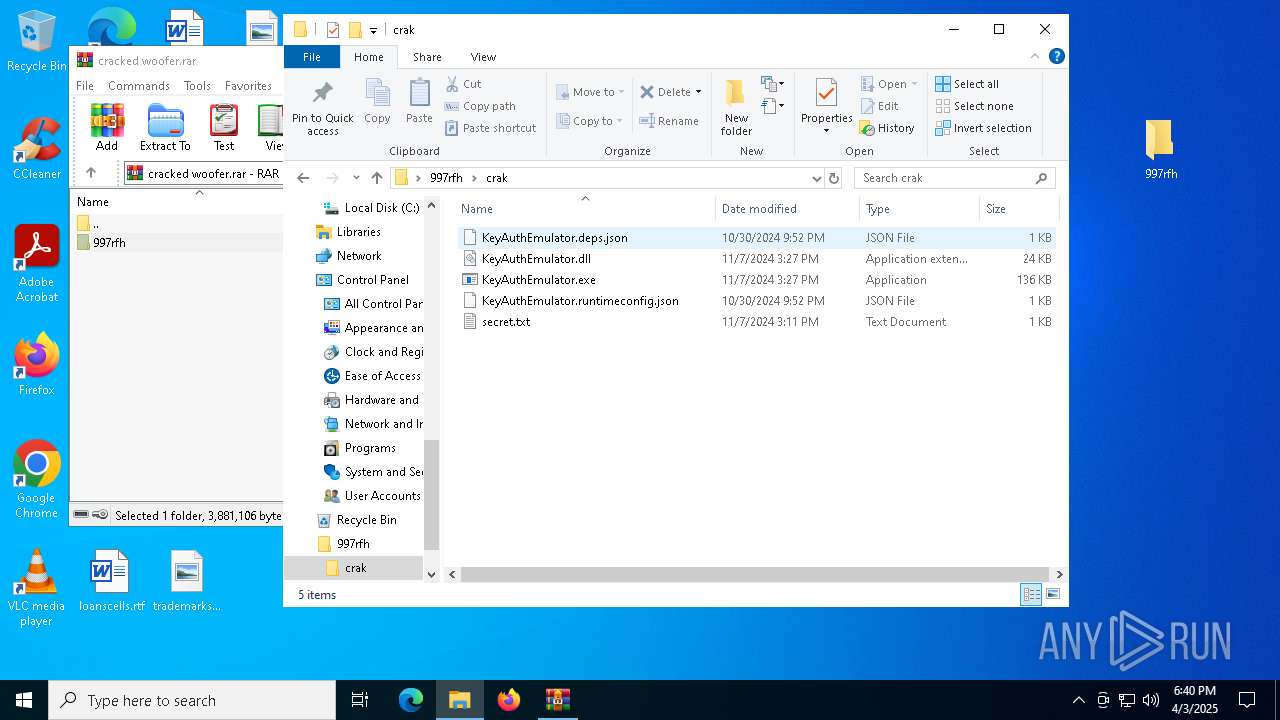
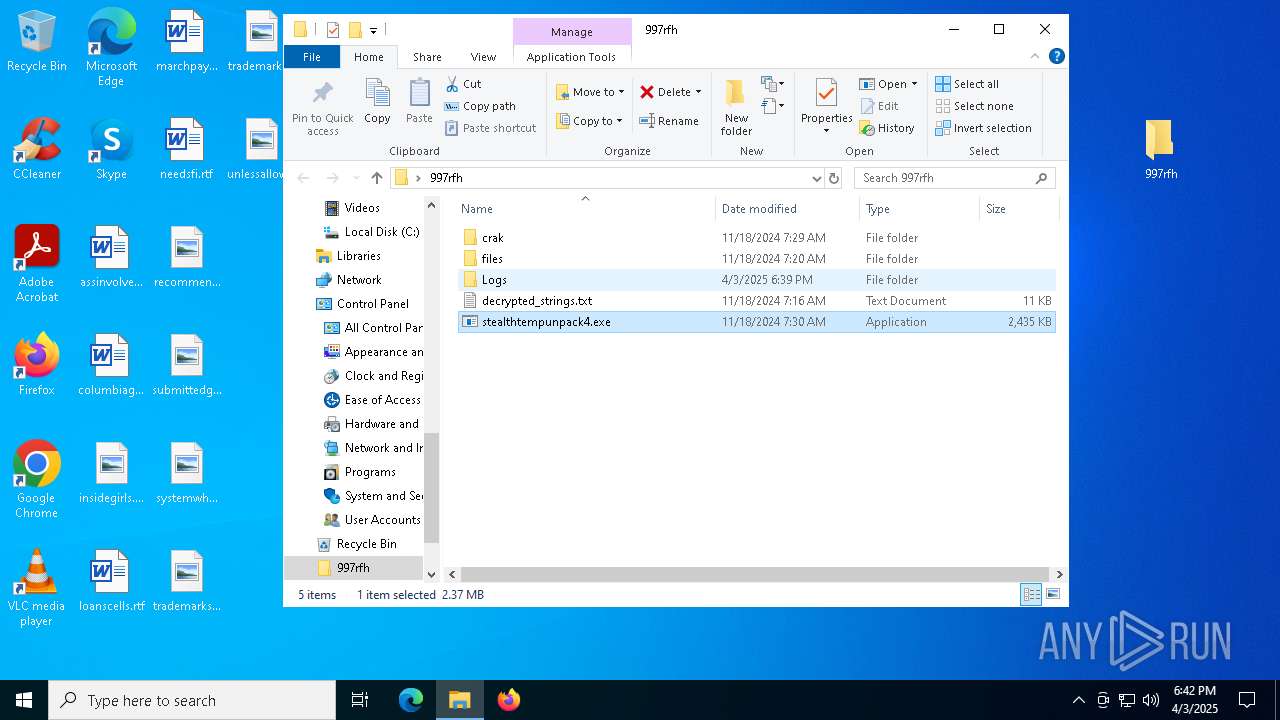
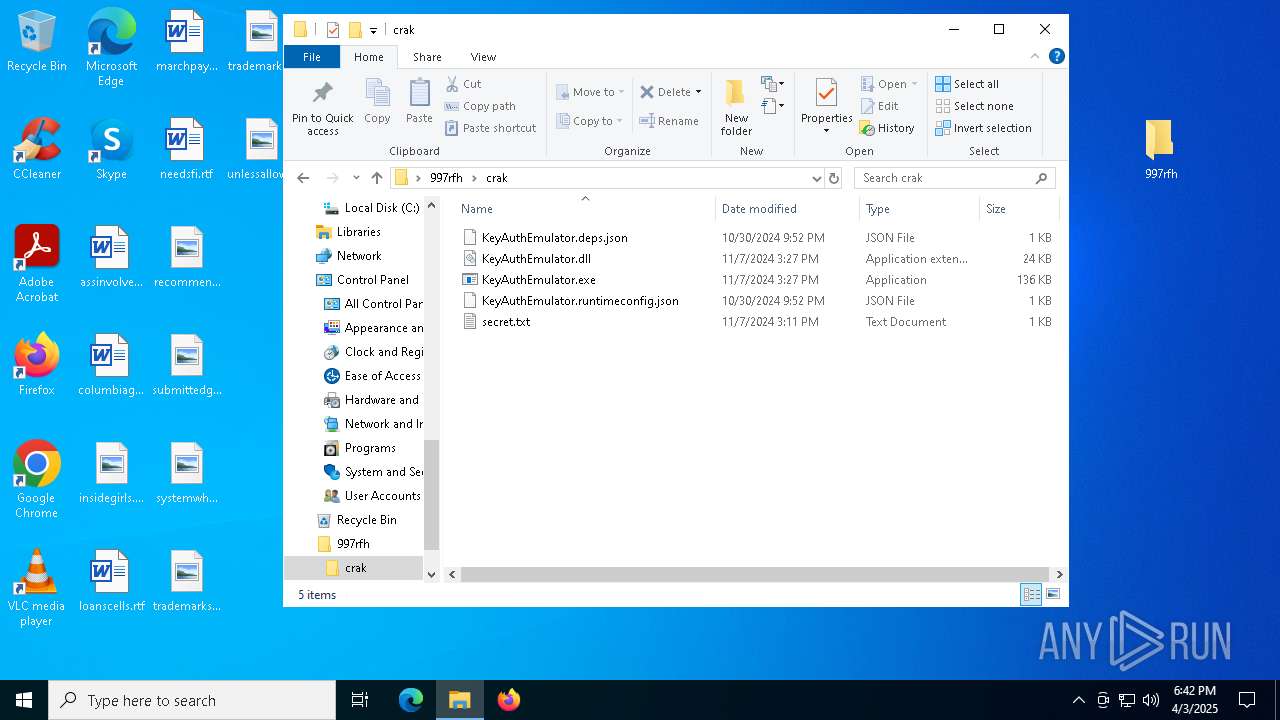
| ArchivedFileName: | 997rfh/crak/KeyAuthEmulator.deps.json |
Total processes
423
Monitored processes
135
Malicious processes
3
Suspicious processes
4
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
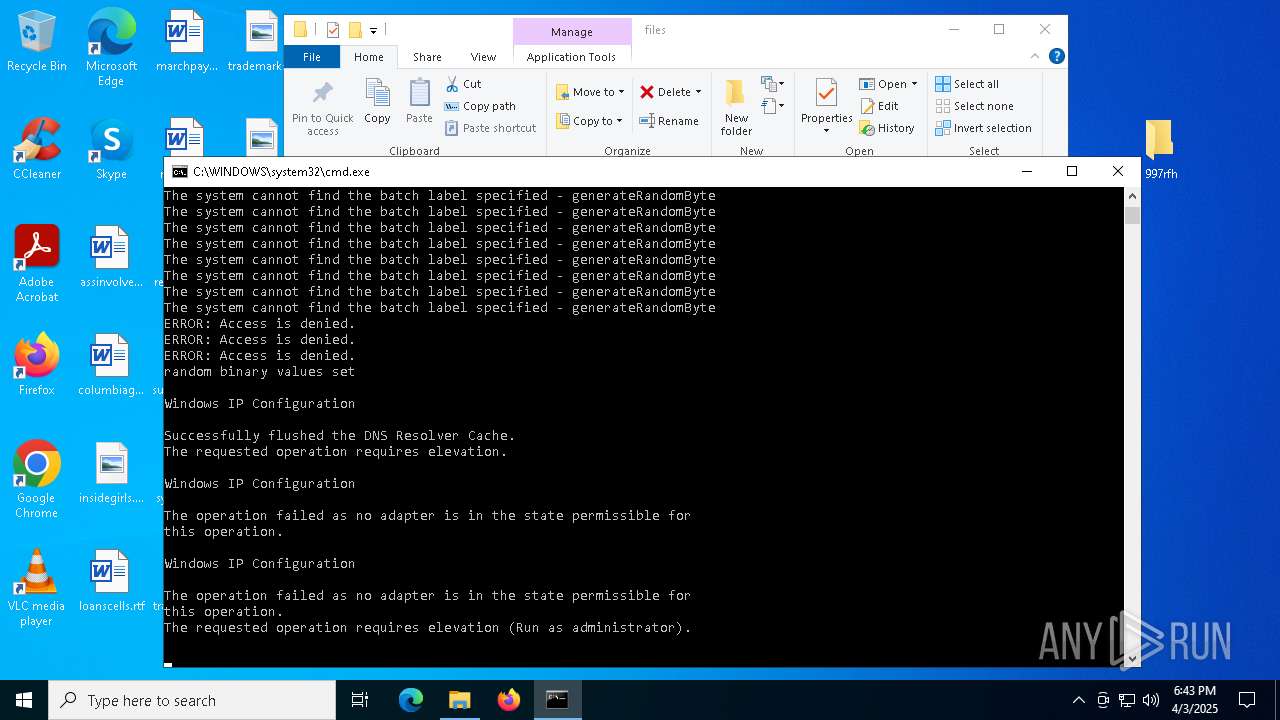
| 204 | reg add "HKLM\SYSTEM\CurrentControlSet\Services\Tcpip\Parameters" /v LargeSendOffloadv2IPv6 /t REG_DWORD /d 0 /f | C:\Windows\System32\reg.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Registry Console Tool Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 488 | reg add "HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\Tcpip6\Parameters" /v "Dhcpv6DomainSearchList" /t REG_BINARY /d /f | C:\Windows\System32\reg.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Registry Console Tool Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 556 | reg add "HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\Tcpip6\Parameters" /v DisabledComponents /t REG_DWORD /d 0xFFFFFFFF /f | C:\Windows\System32\reg.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Registry Console Tool Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 564 | ipconfig /release | C:\Windows\System32\ipconfig.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: IP Configuration Utility Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 640 | netsh interface set interface "Microsoft Network Adapter Multiplexor Protocol" admin=disabled | C:\Windows\System32\netsh.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Network Command Shell Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
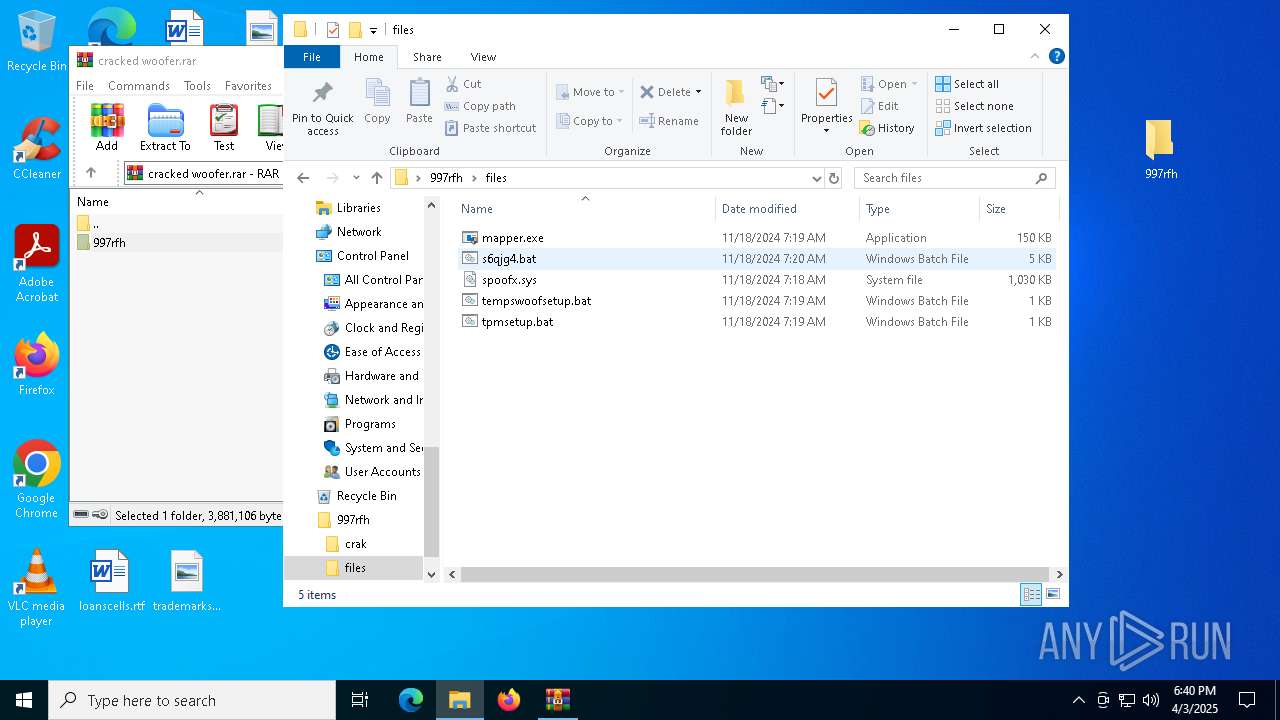
| 660 | "C:\Users\admin\Desktop\997rfh\files\mapper.exe" C:\Users\admin\Desktop\997rfh\files\spoofx.sys | C:\Users\admin\Desktop\997rfh\files\mapper.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 664 | ipconfig /renew | C:\Windows\System32\ipconfig.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: IP Configuration Utility Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
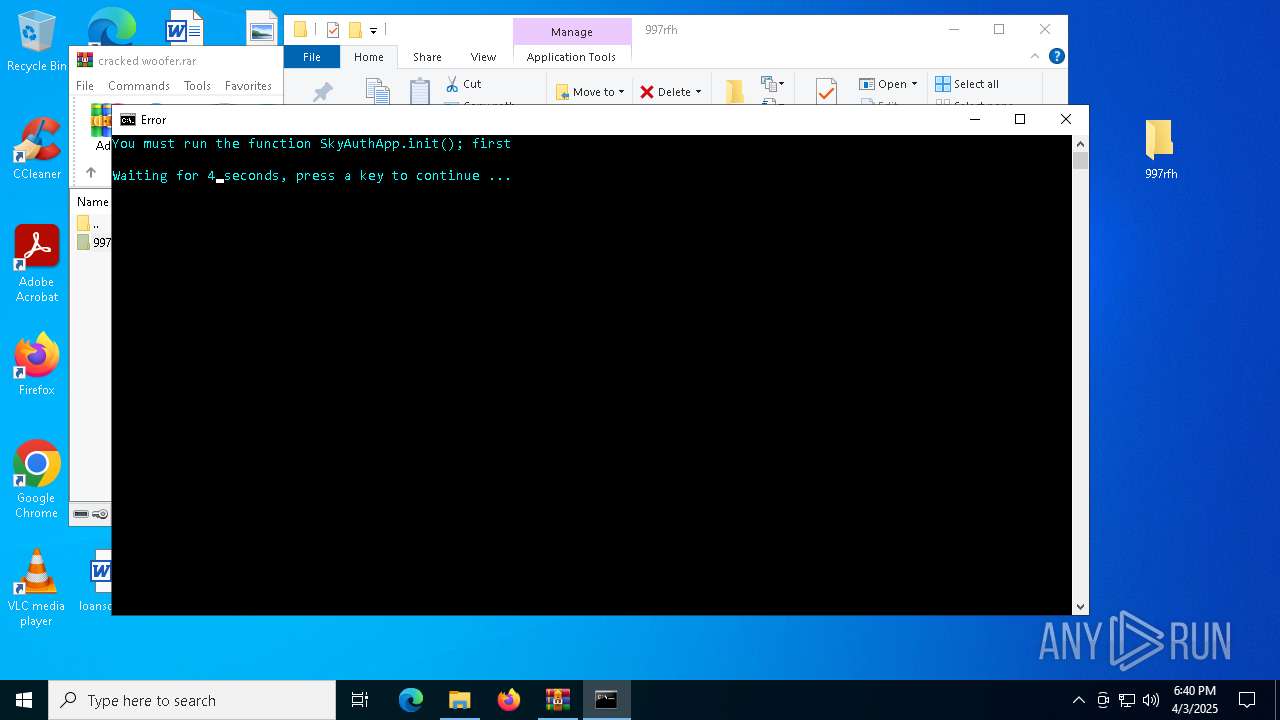
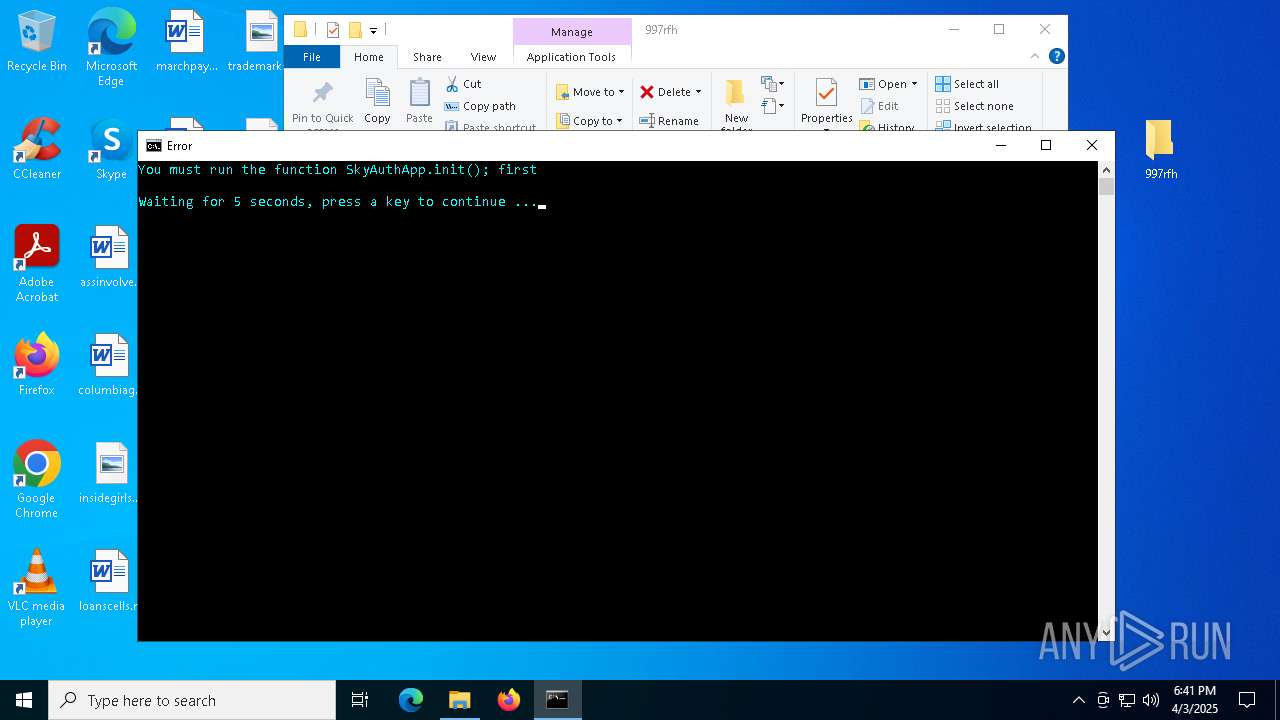
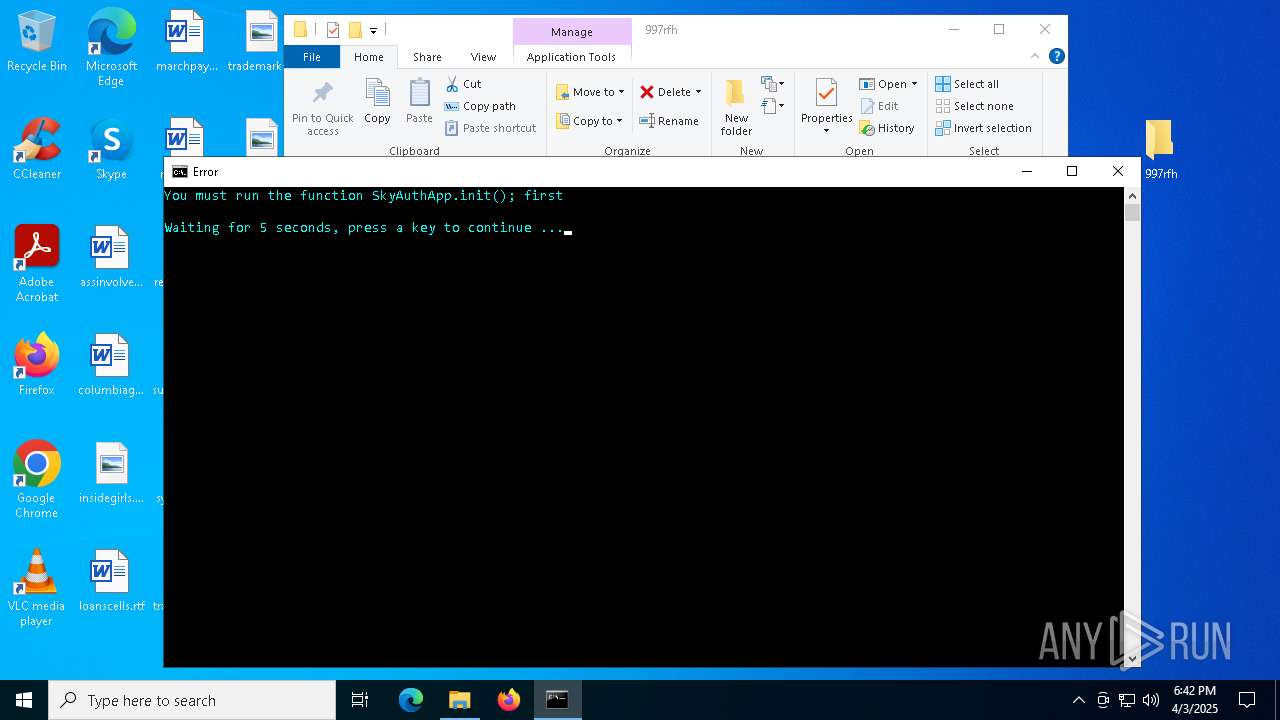
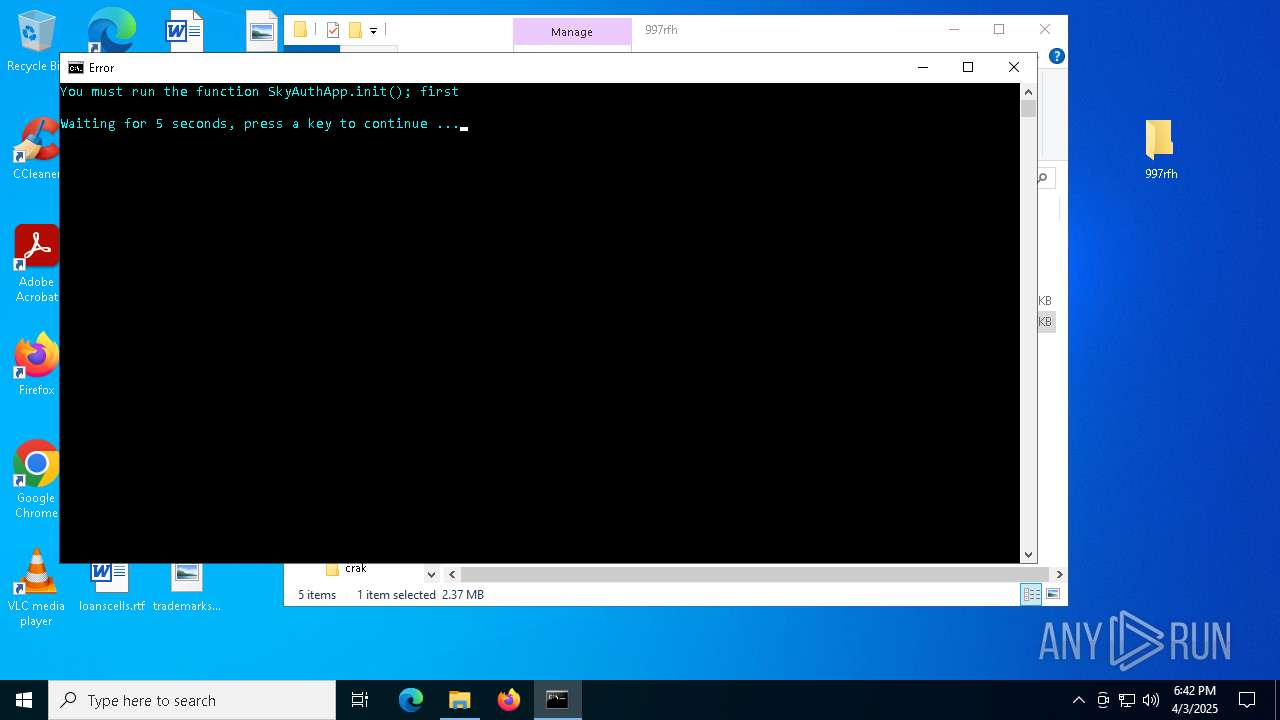
| 768 | "cmd.exe" /c start cmd /C "color b && title Error && echo You must run the function SkyAuthApp.init(); first && timeout /t 5" | C:\Windows\SysWOW64\cmd.exe | — | stealthtempunpack4.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 768 | reg add "HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\Tcpip6\Parameters" /v "Dhcpv6DUID" /t REG_BINARY /d /f | C:\Windows\System32\reg.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Registry Console Tool Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 956 | C:\WINDOWS\system32\cmd.exe /c wmic nic where physicaladapter=true get deviceid | findstr [0-9] | C:\Windows\System32\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
21 114
Read events
21 090
Write events
24
Delete events
0
Modification events
| (PID) Process: | (5960) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (5960) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (5960) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (5960) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\cracked woofer.rar | |||
| (PID) Process: | (5960) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (5960) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (5960) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (5960) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (7700) stealthtempunpack4.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\stealthtempunpack4_RASAPI32 |
| Operation: | write | Name: | EnableFileTracing |
Value: 0 | |||
| (PID) Process: | (7700) stealthtempunpack4.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\stealthtempunpack4_RASAPI32 |
| Operation: | write | Name: | EnableAutoFileTracing |
Value: 0 | |||
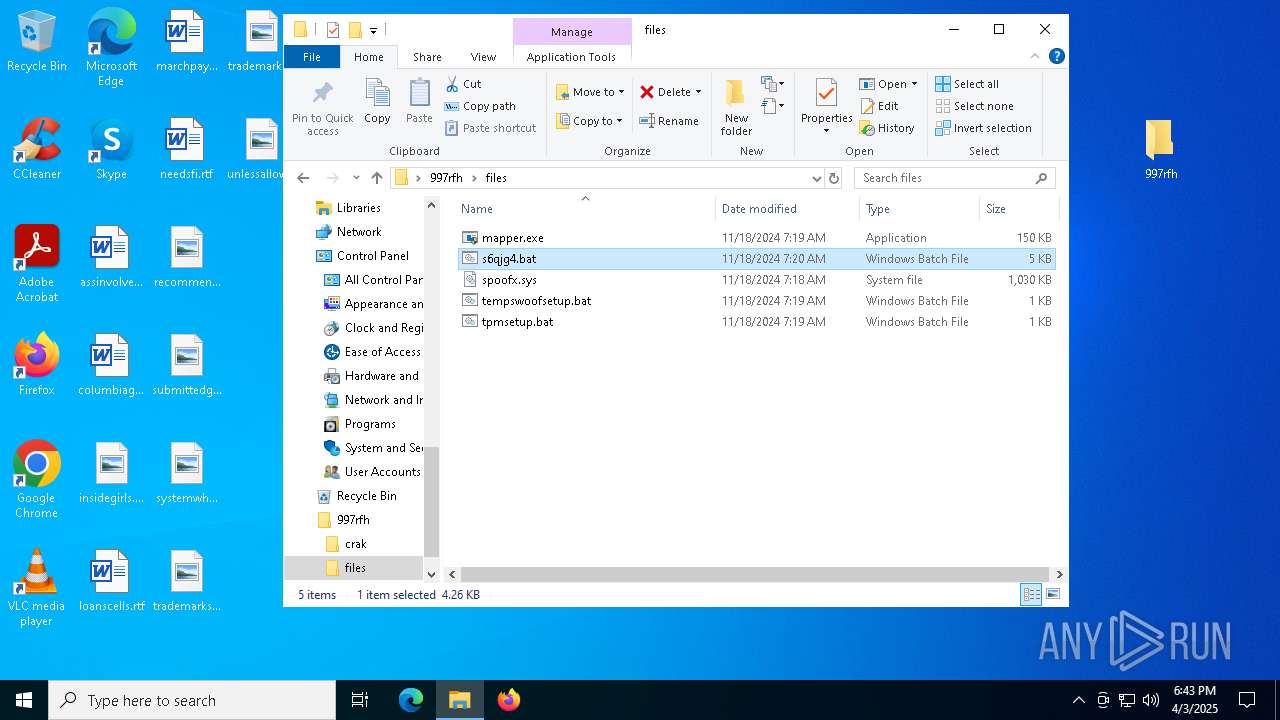
Executable files
6
Suspicious files
47
Text files
6
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
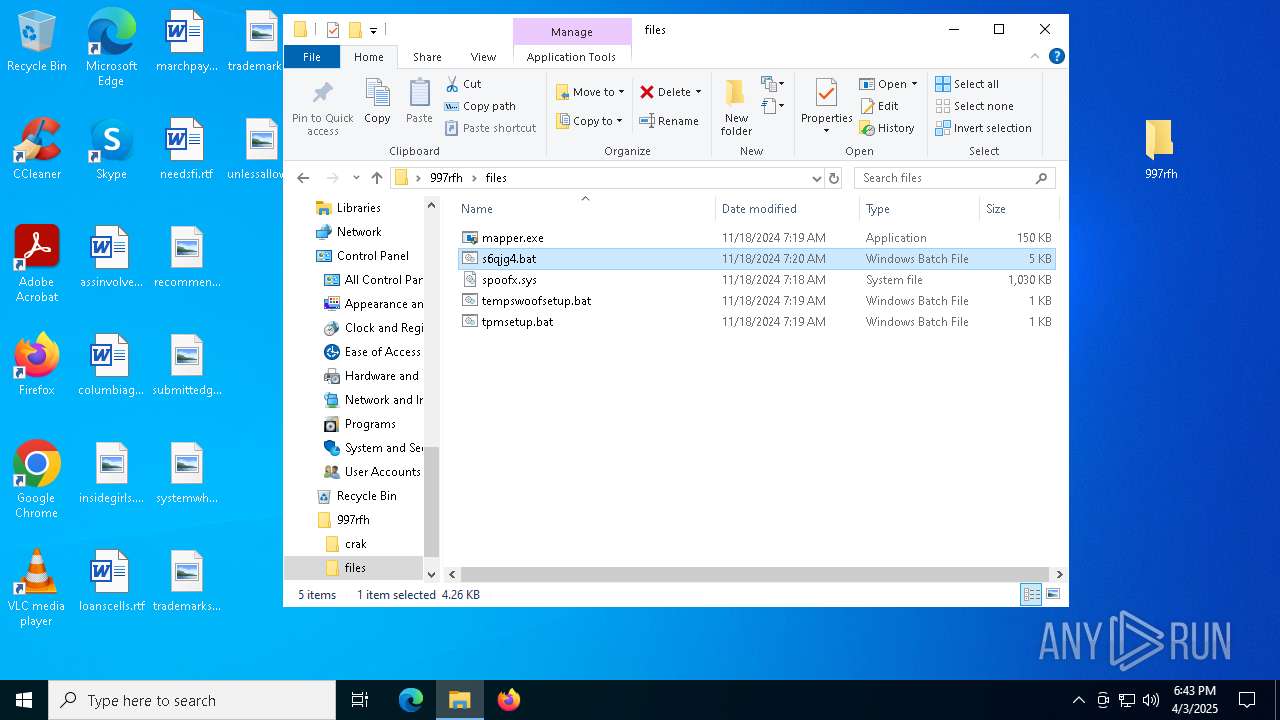
| 5960 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa5960.37221\997rfh\crak\KeyAuthEmulator.deps.json | binary | |
MD5:47306D1FC832C57AB35F197F48E05864 | SHA256:98150B82CBB9F35DC99DAA5116D9EAE18ADF22C11CBE245E1822FF42A254D624 | |||
| 5960 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa5960.37221\997rfh\crak\KeyAuthEmulator.exe | executable | |
MD5:CF78D5995312872C075AE9772A14A5A2 | SHA256:71FEDE3D07F8B24D08E15748ABCD95ABCFE48E21A5A71F0C96D6BF752C12252C | |||
| 4296 | PLUGScheduler.exe | C:\ProgramData\PLUG\Logs\RUXIMLog.049.etl | binary | |
MD5:5EA68411BF8E9EAF4621BAF73F61449E | SHA256:9D4CA5A1D871F819C139A498BB910A63576C2FE6367853544F8D172D8B6EBFF7 | |||
| 660 | mapper.exe | C:\Users\admin\AppData\Local\Temp\aDMXoZQlDcGvstOtzyGKjOSNcxvXC | executable | |
MD5:1898CEDA3247213C084F43637EF163B3 | SHA256:4429F32DB1CC70567919D7D47B844A91CF1329A6CD116F582305F3B7B60CD60B | |||
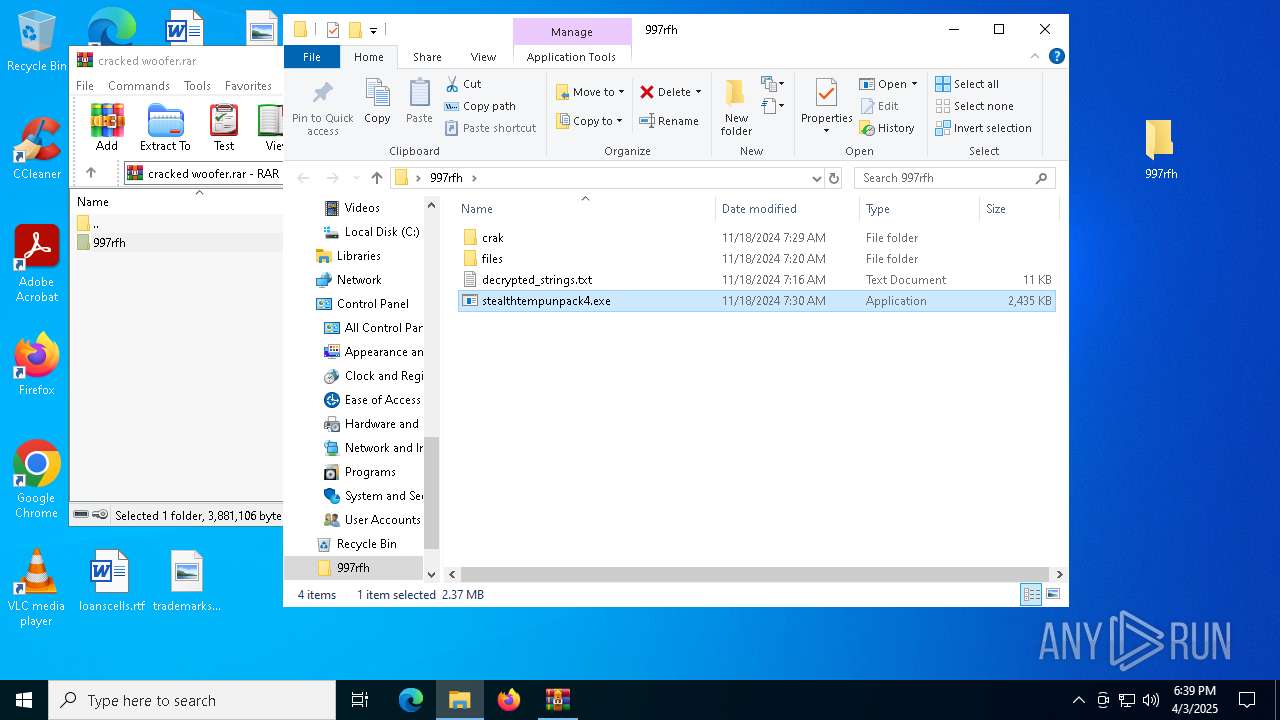
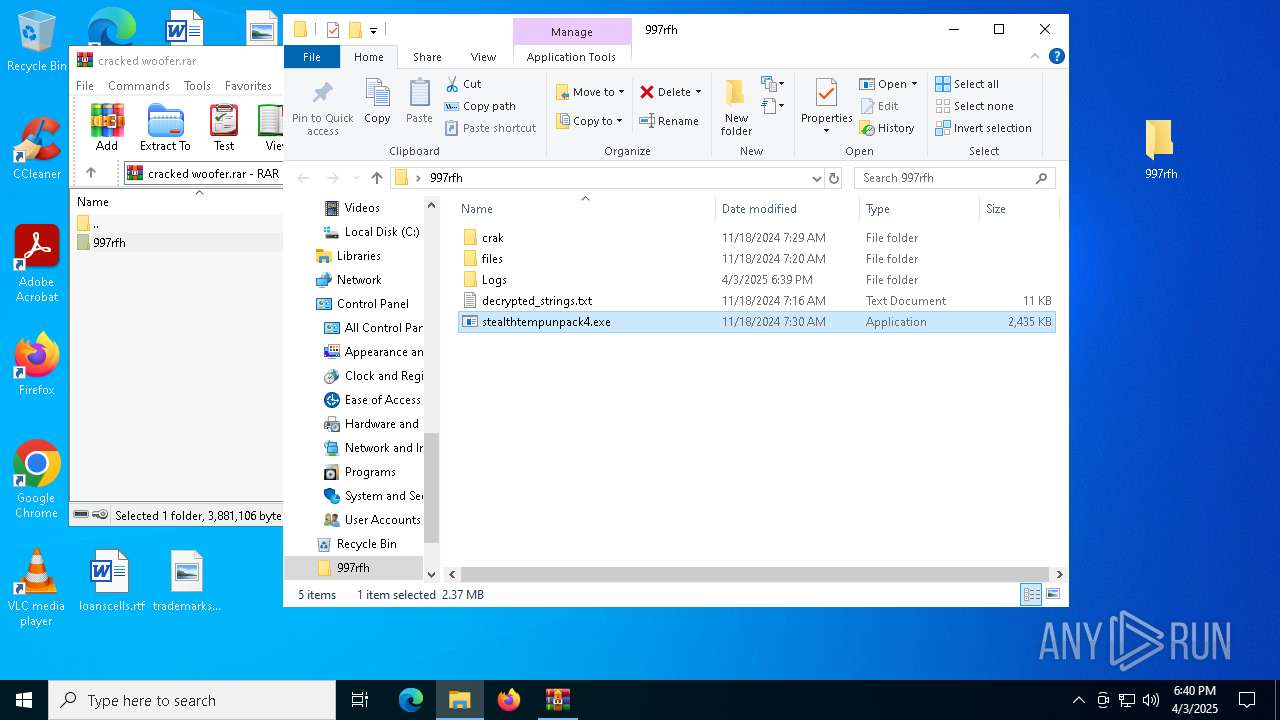
| 5960 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa5960.37221\997rfh\stealthtempunpack4.exe | executable | |
MD5:A4F8C262E57723F13C6F02E3DCF87BBD | SHA256:4D5F575FDAF9E3B53DBBB13BE5729B22D59F9603C0B44660FB19B8149F64B2B6 | |||
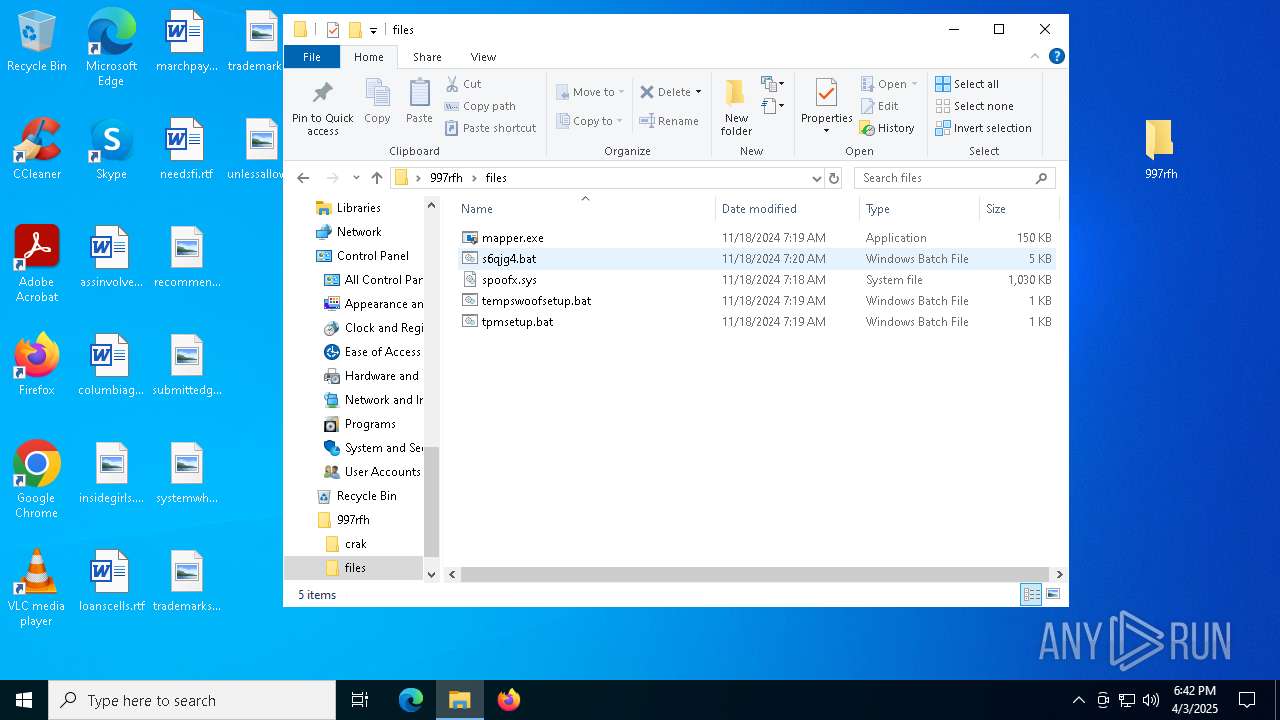
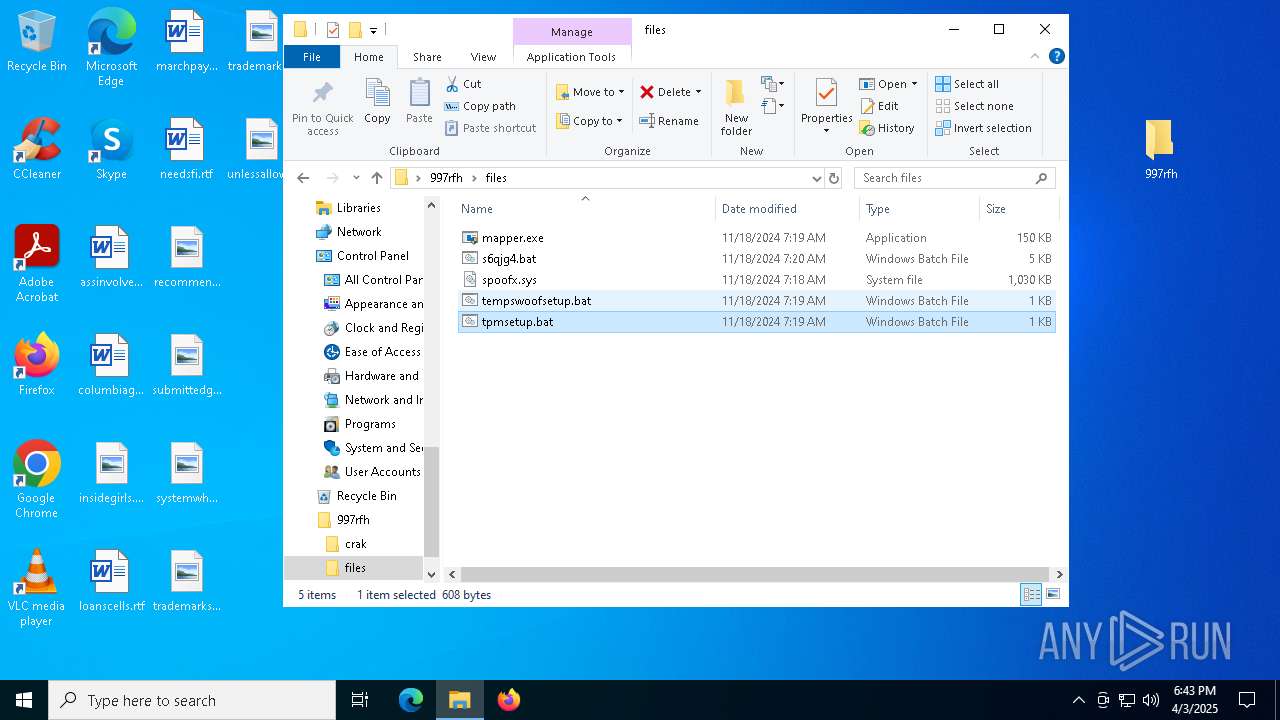
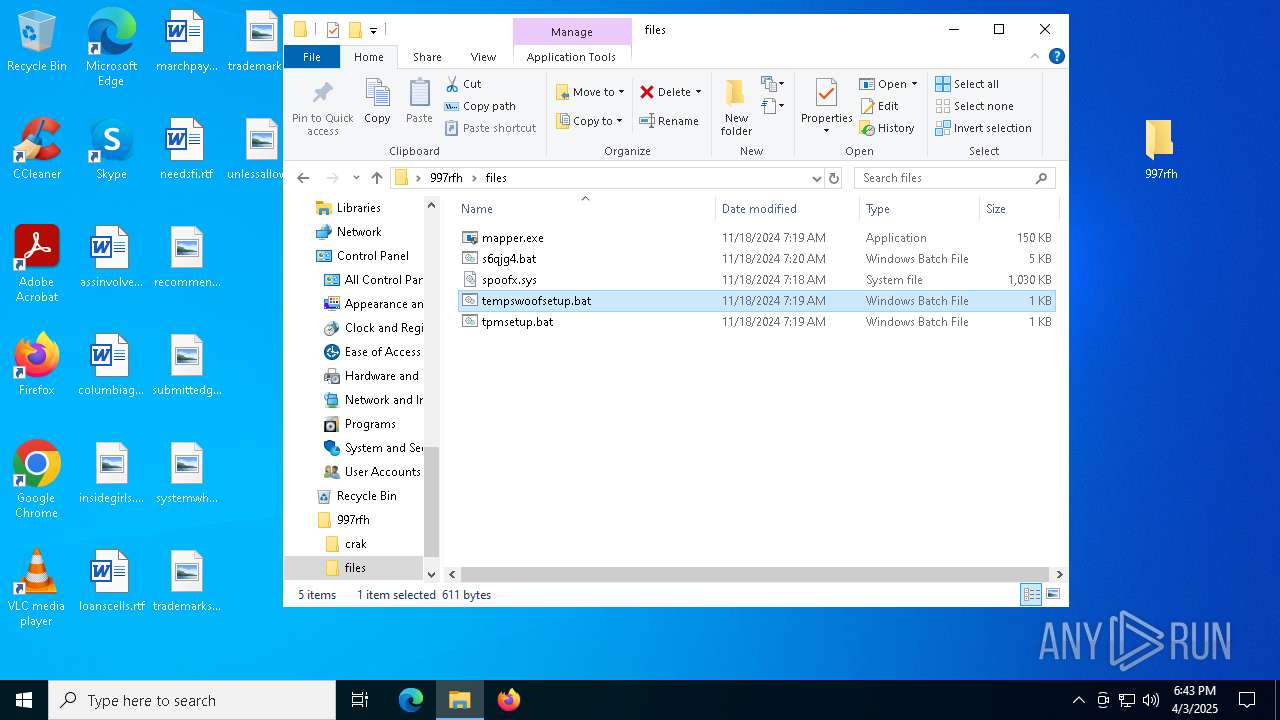
| 5960 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa5960.37221\997rfh\files\tempswoofsetup.bat | text | |
MD5:E625D46D449A82E4D94FEFA3CB2BC429 | SHA256:443E031F17726670E72D9CD787D3B27032B78CF08B6B9FF06DBFF4B854D4062D | |||
| 4296 | PLUGScheduler.exe | C:\ProgramData\PLUG\Logs\RUXIMLog.050.etl | binary | |
MD5:C8834D365FAE073DEDE1F1620454CE71 | SHA256:C6DD793EEE1D5551CA507A3C5BFFECA82DD3E29C63C2C6DD218A7D4BFB37046B | |||
| 4296 | PLUGScheduler.exe | C:\ProgramData\PLUG\Logs\RUXIMLog.046.etl | binary | |
MD5:A7A21FBC9D00F33F186B34A50E170C13 | SHA256:64CAC91E46D4FC832958232A658431CBF9D8D9F265653ACA2BEB32428D4688EC | |||
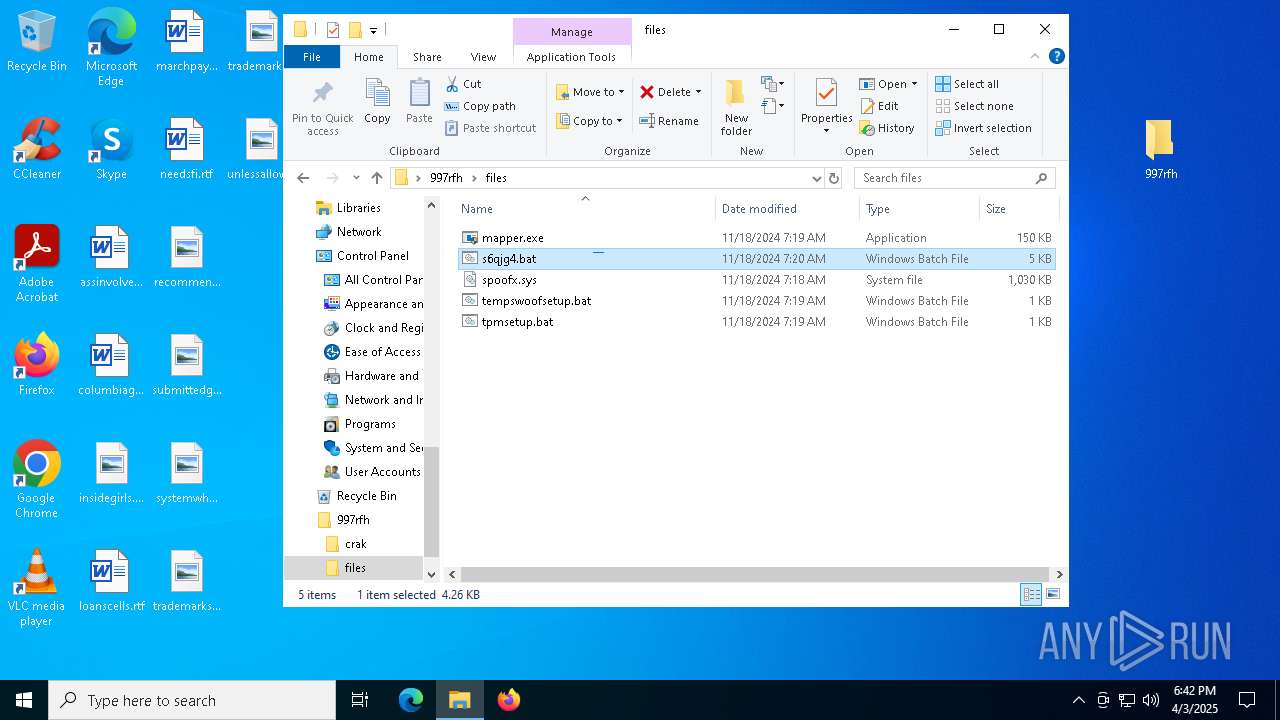
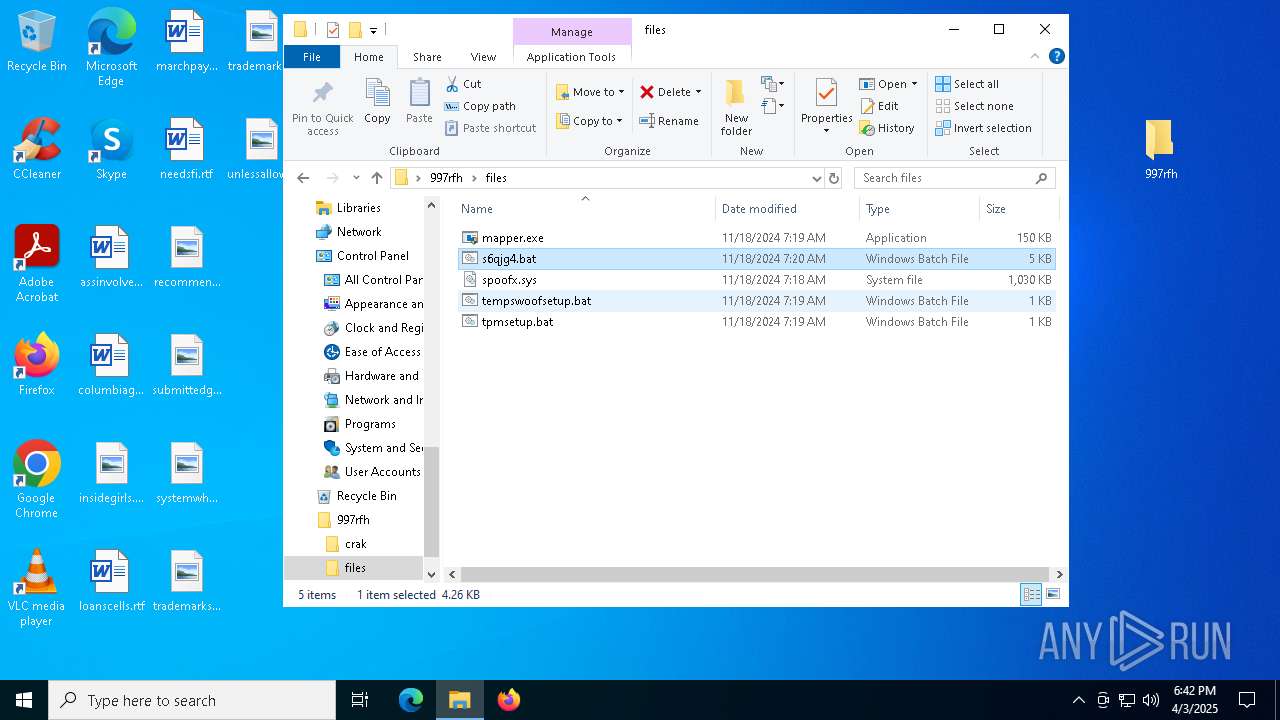
| 5960 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa5960.37221\997rfh\files\s6qjg4.bat | text | |
MD5:4B88777F136A2A75A6839105D74F29A2 | SHA256:63B82535C9C9E3CD735567D8255A294DD8AFFFABF41737F4BD98DCFBFDDAA544 | |||
| 4296 | PLUGScheduler.exe | C:\ProgramData\PLUG\Logs\RUXIMLog.048.etl | binary | |
MD5:A23907B6FDD47DCABFDFD7CF2FCD7671 | SHA256:0C9C33FE9E984A2E5A70EBA51F36B9929A86199E424AF2F8080E1267B87DC970 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
9
TCP/UDP connections
65
DNS requests
39
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5496 | MoUsoCoreWorker.exe | GET | 200 | 23.48.23.140:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
6544 | svchost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
7932 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
7932 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
4908 | svchost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
5148 | SearchApp.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
6284 | backgroundTaskHost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
1084 | BackgroundTransferHost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
6340 | backgroundTaskHost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2104 | svchost.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
5496 | MoUsoCoreWorker.exe | 23.48.23.140:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
3216 | svchost.exe | 172.172.255.218:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
6544 | svchost.exe | 20.190.160.128:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
6544 | svchost.exe | 2.17.190.73:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
2112 | svchost.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
2104 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
nexusrules.officeapps.live.com |
| whitelisted |