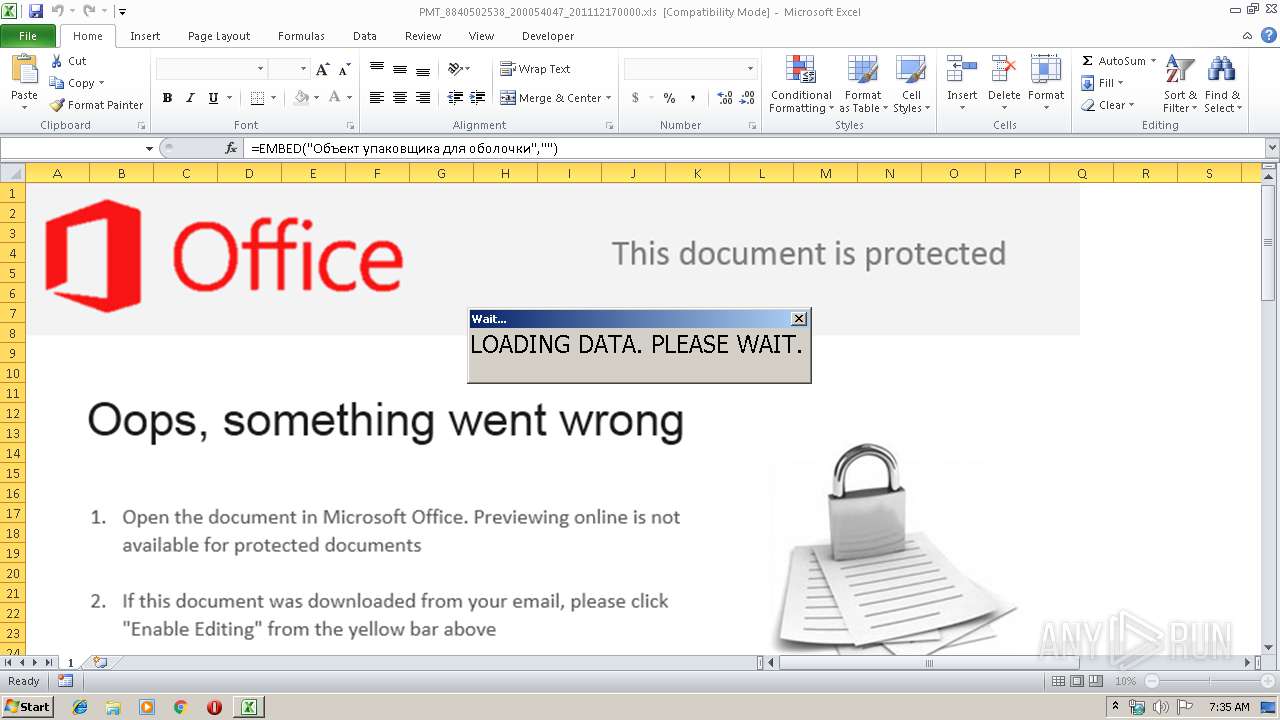
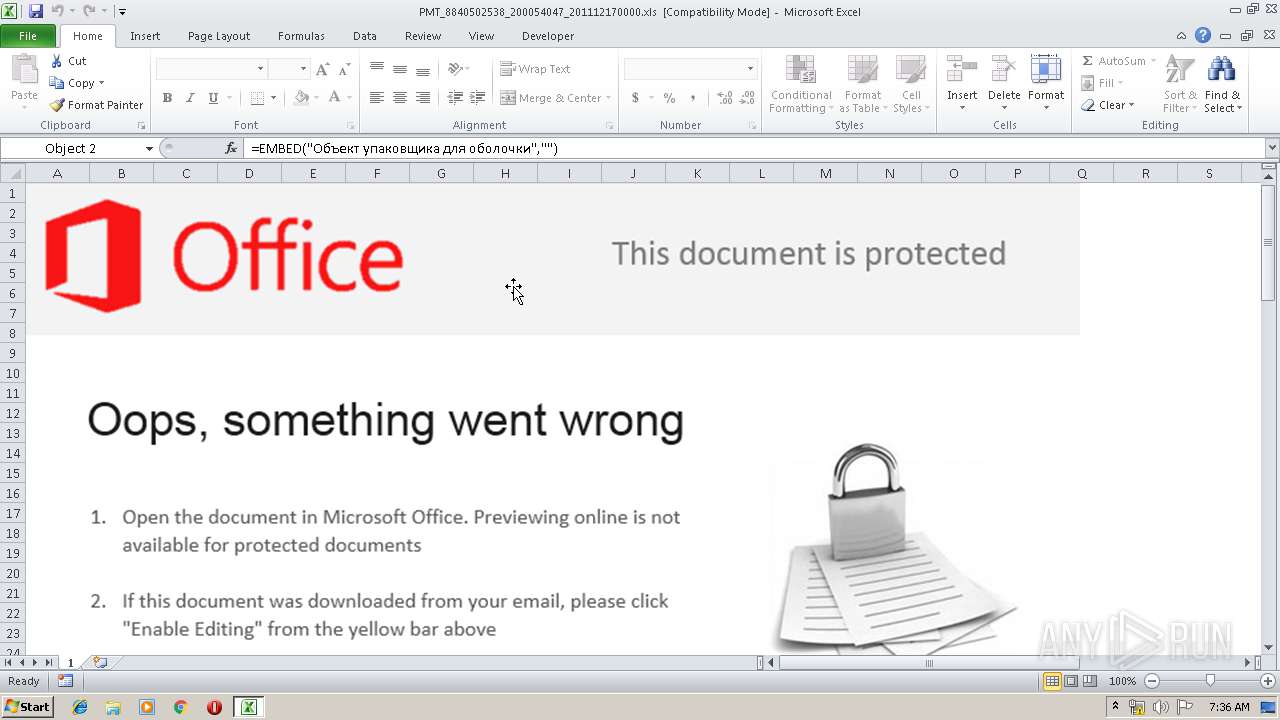
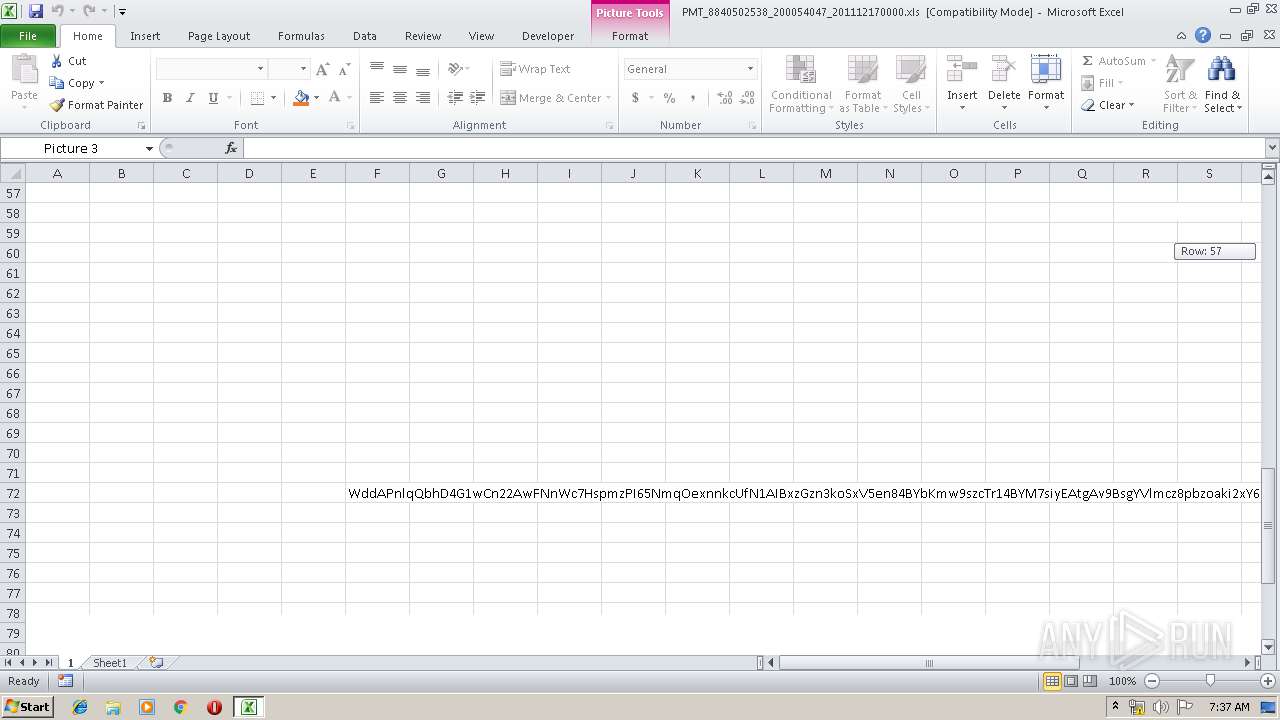
| File name: | PMT_8840502538_200054047_201112170000.xls |
| Full analysis: | https://app.any.run/tasks/b521baed-f2b3-496a-8f7e-48be62353134 |
| Verdict: | Malicious activity |
| Analysis date: | September 11, 2019, 06:34:52 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.ms-excel |
| File info: | Composite Document File V2 Document, Little Endian, Os: Windows, Version 6.1, Code page: 1251, Title: A, Subject: caP, Author: Atl, Last Saved By: Microsoft Office, Revision Number: 699, Name of Creating Application: Microsoft Excel, Total Editing Time: 09:05:00, Create Time/Date: Fri Aug 30 10:14:50 2019, Last Saved Time/Date: Tue Sep 10 11:38:59 2019, Number of Pages: 1, Number of Words: 4669, Number of Characters: 1838, Security: 0 |
| MD5: | 73E8D7D3213A4462EFC116E814904C69 |
| SHA1: | CD270E97760A1AC1BB06C03791EE3E54511173E6 |
| SHA256: | 8FBCC5E457C4E223148820CF4A1B6F760C819BF0BF0B5C61B92DCF8D5F8B5805 |
| SSDEEP: | 6144:F8mdr74qRlm5ibfVdLkUikJdGC1XcONnxusA2:F8UrDtdoUfPTfV |
MALICIOUS
Loads dropped or rewritten executable
- EXCEL.EXE (PID: 3520)
Executable content was dropped or overwritten
- EXCEL.EXE (PID: 3520)
SUSPICIOUS
No suspicious indicators.INFO
Reads Microsoft Office registry keys
- EXCEL.EXE (PID: 3520)
Creates files in the user directory
- EXCEL.EXE (PID: 3520)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .xls | | | Microsoft Excel sheet (48) |
|---|---|---|
| .xls | | | Microsoft Excel sheet (alternate) (39.2) |
EXIF
FlashPix
| CompObjUserTypeLen: | 25 |
|---|---|
| CompObjUserType: | Microsoft Forms 2.0 Form |
| Title: | A |
| Subject: | caP |
| Author: | Atl |
| LastModifiedBy: | Microsoft Office |
| RevisionNumber: | 699 |
| Software: | Microsoft Excel |
| TotalEditTime: | 9.1 hours |
| CreateDate: | 2019:08:30 09:14:50 |
| ModifyDate: | 2019:09:10 10:38:59 |
| Pages: | 1 |
| Words: | 4669 |
| Characters: | 1838 |
| Security: | None |
| CodePage: | Windows Cyrillic |
| Company: | - |
| Bytes: | 86400 |
| Lines: | 526 |
| Paragraphs: | 46 |
| AppVersion: | 11.9999 |
| ScaleCrop: | No |
| LinksUpToDate: | No |
| SharedDoc: | No |
| HyperlinksChanged: | No |
| TitleOfParts: | 1 |
| HeadingPairs: |
|
Total processes
33
Monitored processes
1
Malicious processes
0
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 3520 | "C:\Program Files\Microsoft Office\Office14\EXCEL.EXE" /dde | C:\Program Files\Microsoft Office\Office14\EXCEL.EXE | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Excel Exit code: 0 Version: 14.0.6024.1000 Modules
| |||||||||||||||
Total events
680
Read events
575
Write events
94
Delete events
11
Modification events
| (PID) Process: | (3520) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Excel\Resiliency\StartupItems |
| Operation: | write | Name: | .|$ |
Value: 2E7C2400C00D0000010000000000000000000000 | |||
| (PID) Process: | (3520) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1033 |
Value: Off | |||
| (PID) Process: | (3520) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1033 |
Value: On | |||
| (PID) Process: | (3520) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Excel |
| Operation: | write | Name: | MTTT |
Value: C00D0000C626A00E6B68D50100000000 | |||
| (PID) Process: | (3520) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Excel\Resiliency\StartupItems |
| Operation: | delete value | Name: | .|$ |
Value: 2E7C2400C00D0000010000000000000000000000 | |||
| (PID) Process: | (3520) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Excel\Resiliency\StartupItems |
| Operation: | delete key | Name: | |
Value: | |||
| (PID) Process: | (3520) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Excel\Resiliency |
| Operation: | delete key | Name: | |
Value: | |||
| (PID) Process: | (3520) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
| (PID) Process: | (3520) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 1 | |||
| (PID) Process: | (3520) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Excel\Resiliency\DocumentRecovery\169C36 |
| Operation: | write | Name: | 169C36 |
Value: 04000000C00D00004B00000043003A005C00550073006500720073005C00610064006D0069006E005C0041007000700044006100740061005C004C006F00630061006C005C00540065006D0070005C0050004D0054005F0038003800340030003500300032003500330038005F003200300030003000350034003000340037005F003200300031003100310032003100370030003000300030002E0078006C007300000000002200000043003A005C00550073006500720073005C00610064006D0069006E005C0041007000700044006100740061005C004C006F00630061006C005C00540065006D0070005C000100000000000000F05C7B0F6B68D501369C1600369C160000000000AC020000001000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
Executable files
1
Suspicious files
3
Text files
0
Unknown types
2
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3520 | EXCEL.EXE | C:\Users\admin\AppData\Local\Temp\CVR982E.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 3520 | EXCEL.EXE | C:\Users\admin\AppData\Local\Temp\VB9F26.tmp | — | |
MD5:— | SHA256:— | |||
| 3520 | EXCEL.EXE | C:\Users\admin\AppData\Local\Temp\VB9F25.tmp | — | |
MD5:— | SHA256:— | |||
| 3520 | EXCEL.EXE | C:\Users\admin\AppData\Local\Temp\~DF462E7DBCDA9F21B8.TMP | — | |
MD5:— | SHA256:— | |||
| 3520 | EXCEL.EXE | C:\Users\admin\AppData\Local\Temp\8F961000 | — | |
MD5:— | SHA256:— | |||
| 3520 | EXCEL.EXE | C:\Users\admin\AppData\Local\Temp\~DF38A92CF967B01532.TMP | — | |
MD5:— | SHA256:— | |||
| 3520 | EXCEL.EXE | C:\Users\admin\AppData\Local\Temp\~$13.xlsx | — | |
MD5:— | SHA256:— | |||
| 3520 | EXCEL.EXE | C:\Users\admin\AppData\Local\Temp\~DF200D2935987783B0.TMP | — | |
MD5:— | SHA256:— | |||
| 3520 | EXCEL.EXE | C:\Users\admin\AppData\Local\Temp\VBE\MSForms.exd | tlb | |
MD5:— | SHA256:— | |||
| 3520 | EXCEL.EXE | C:\Users\admin\AppData\Local\Temp\13.xlsx.zip | document | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
1
DNS requests
2
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3520 | EXCEL.EXE | 95.216.147.100:443 | windows-update-02-en.com | Hetzner Online GmbH | DE | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
windows-update-02-en.com |
| malicious |