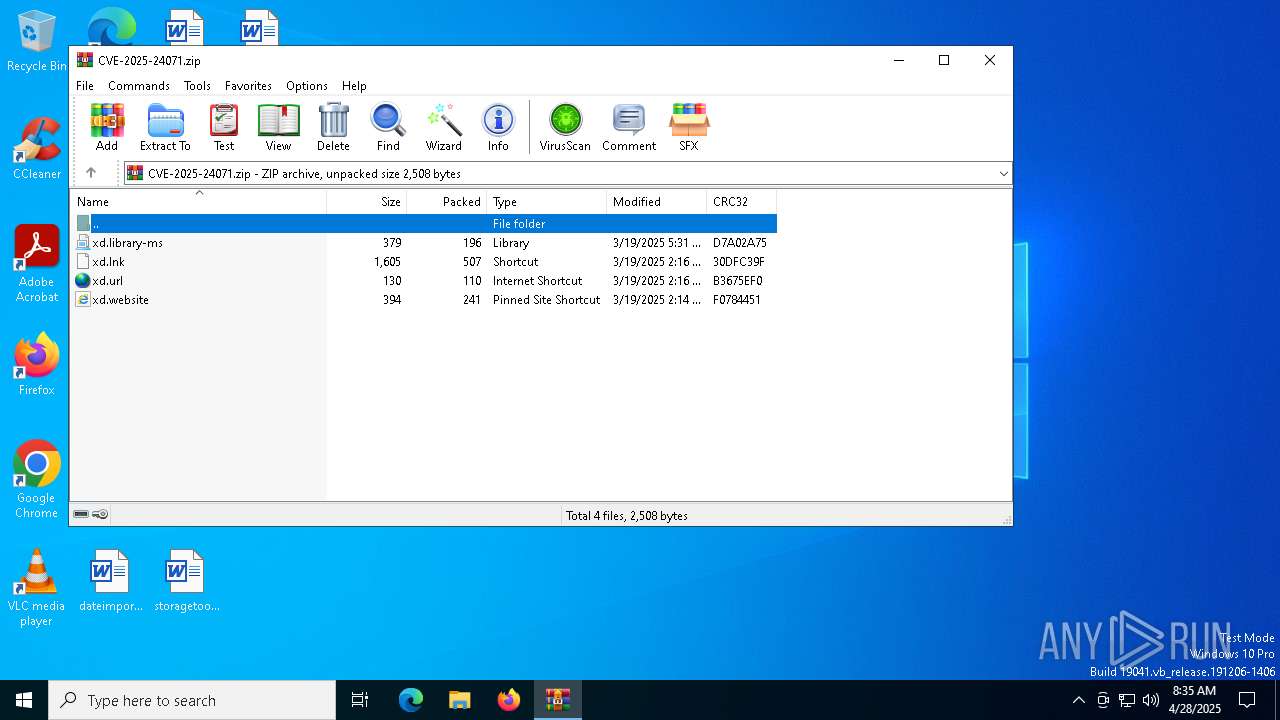
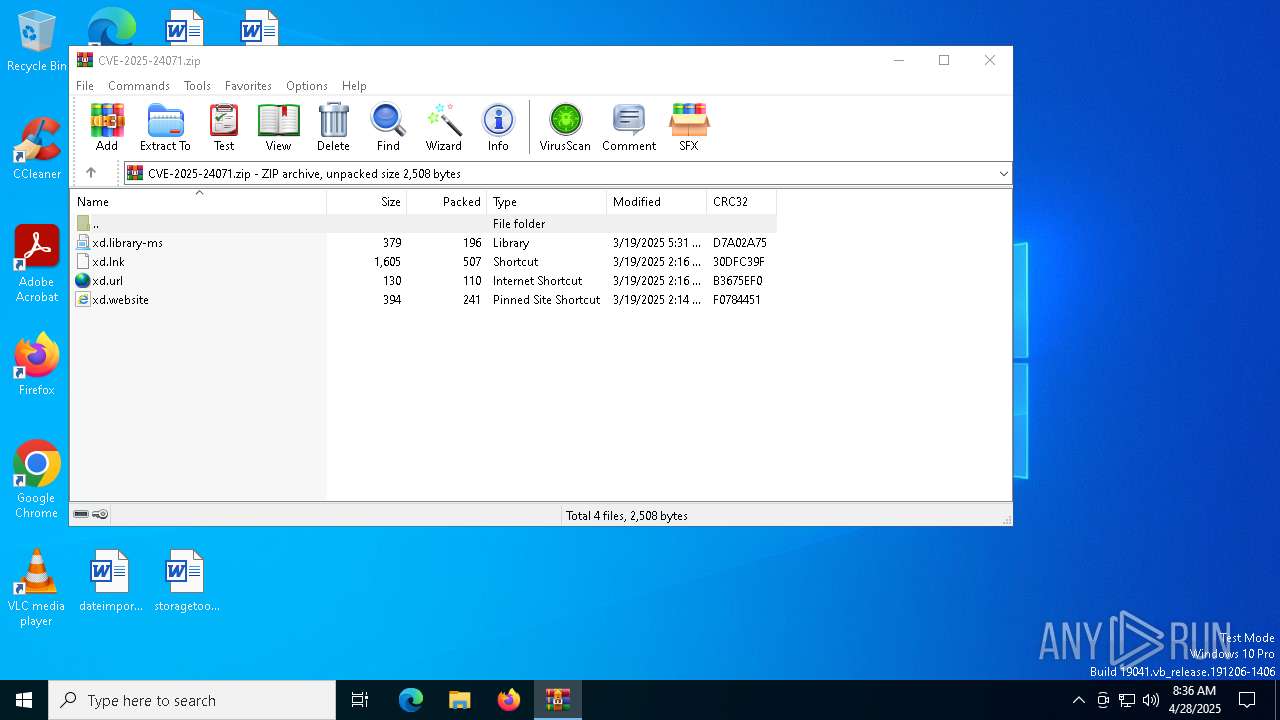
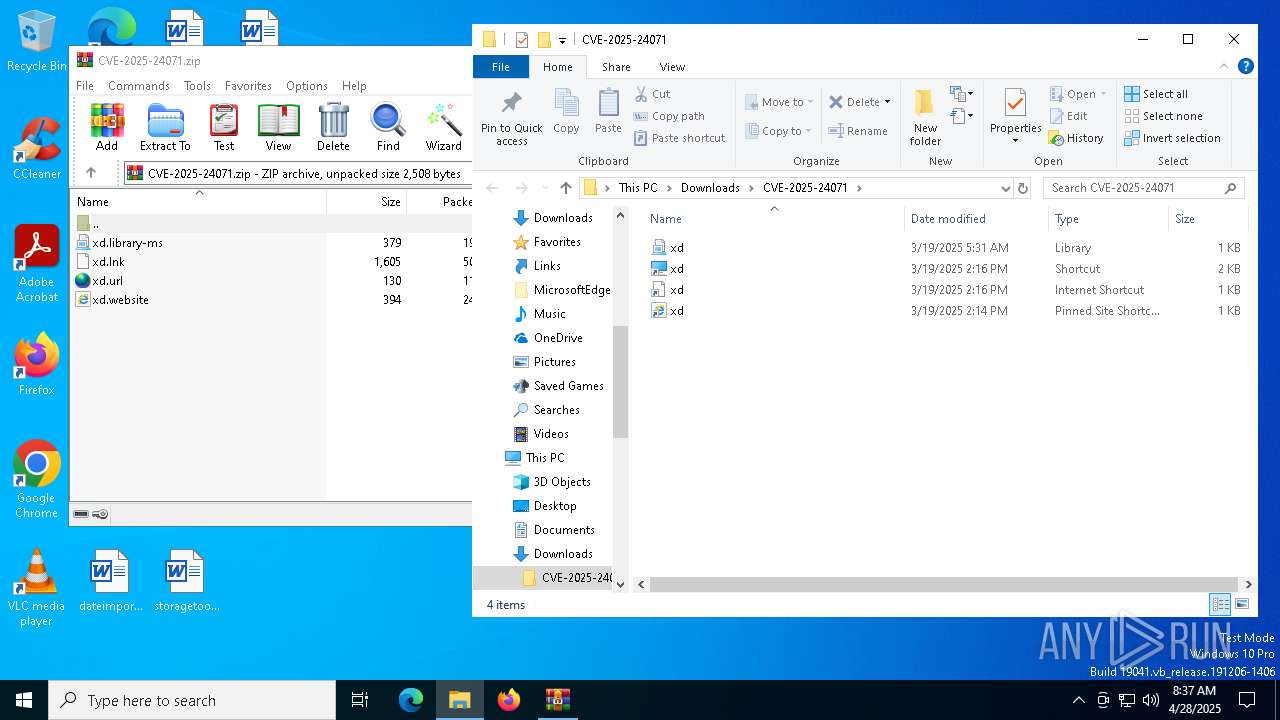
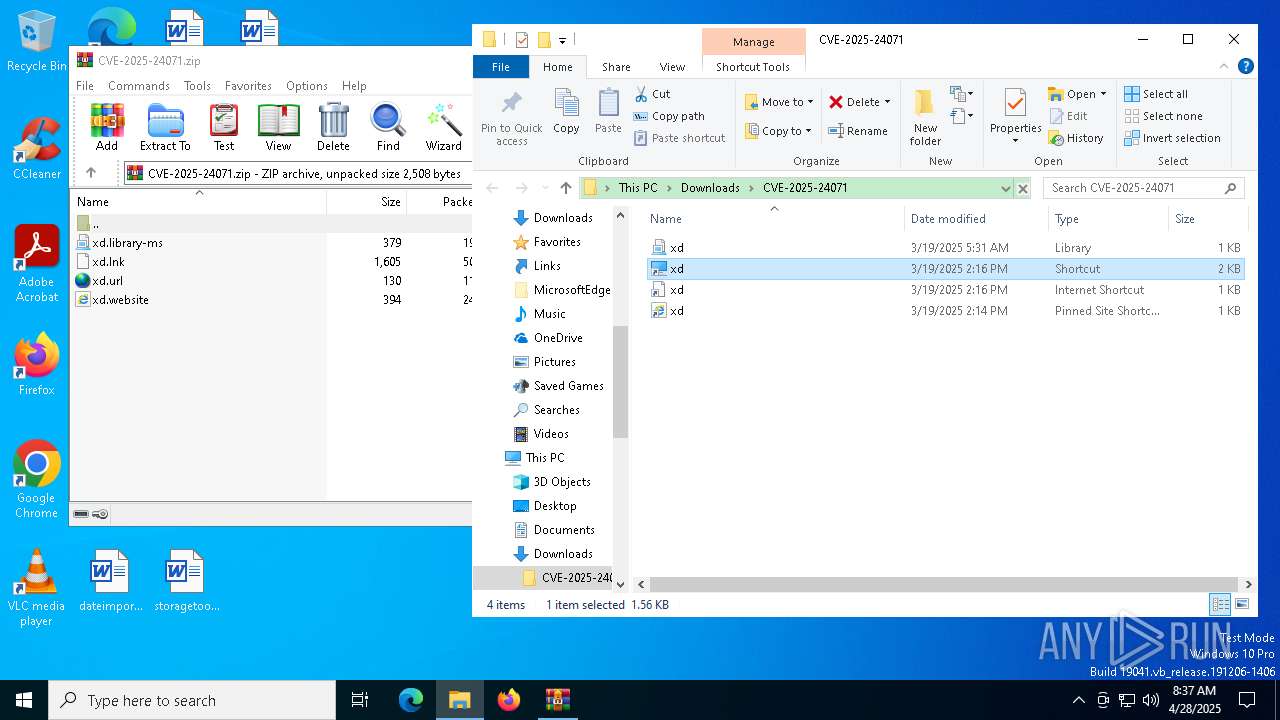
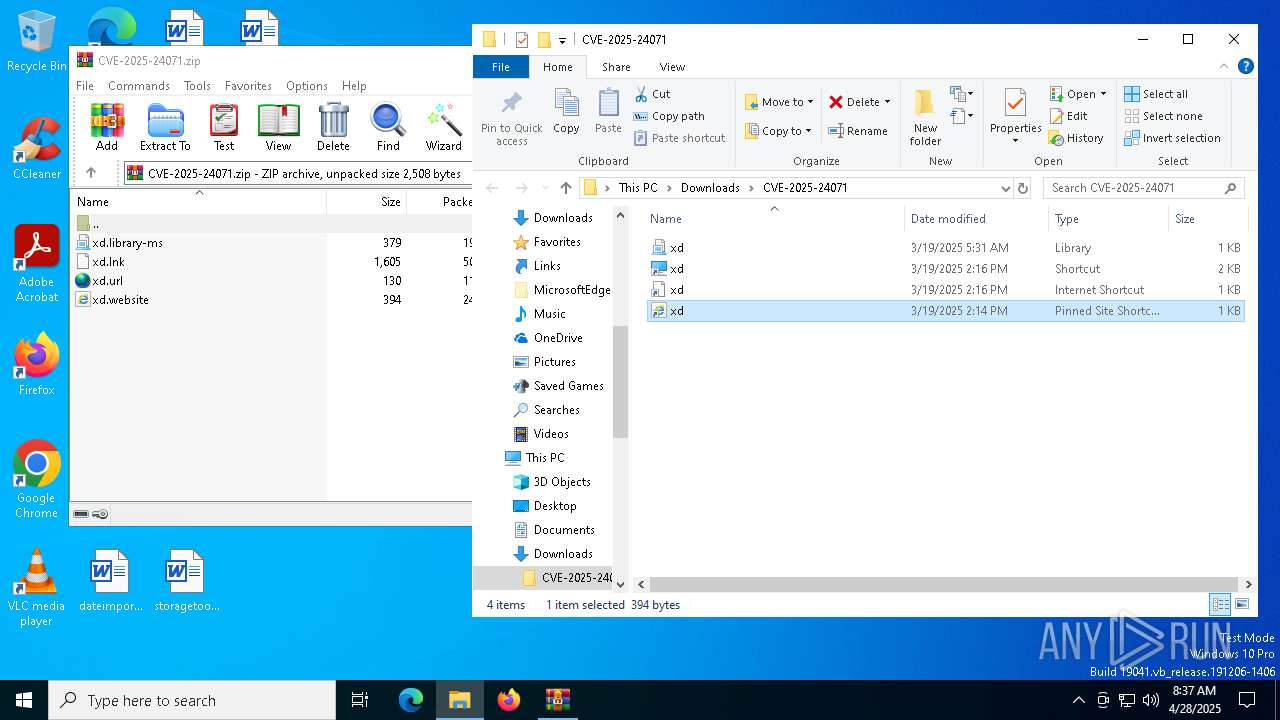
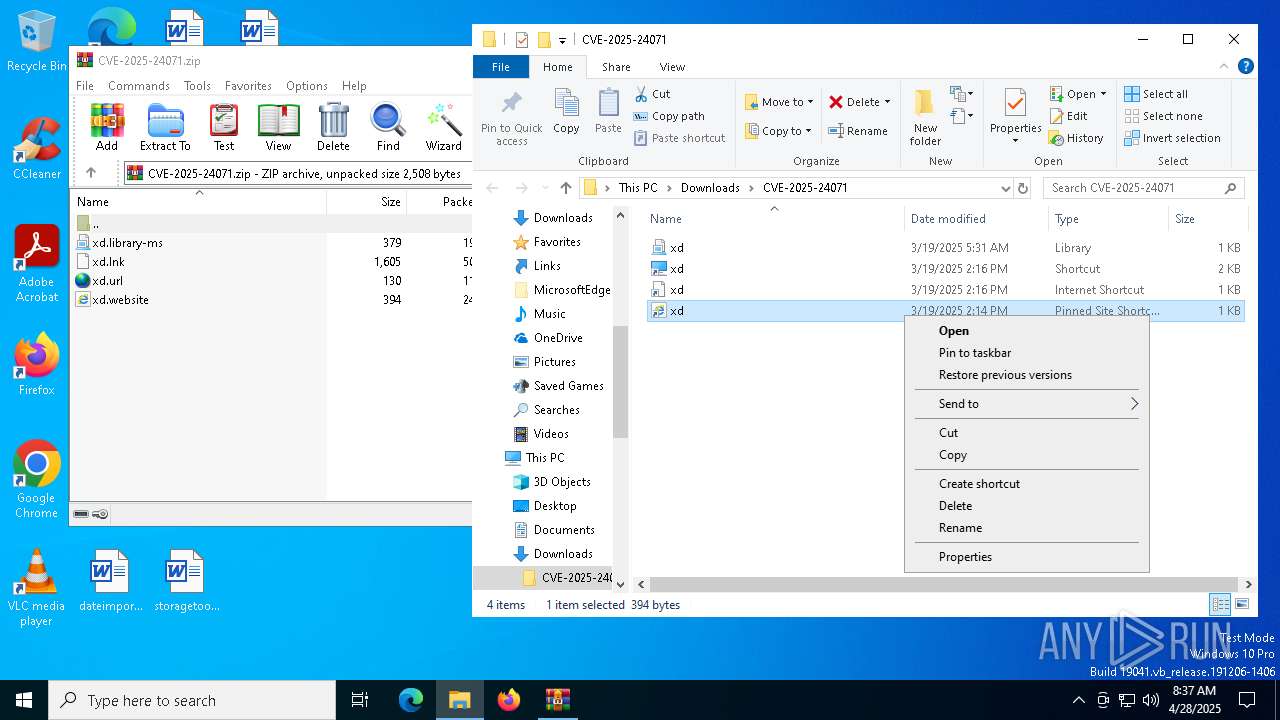
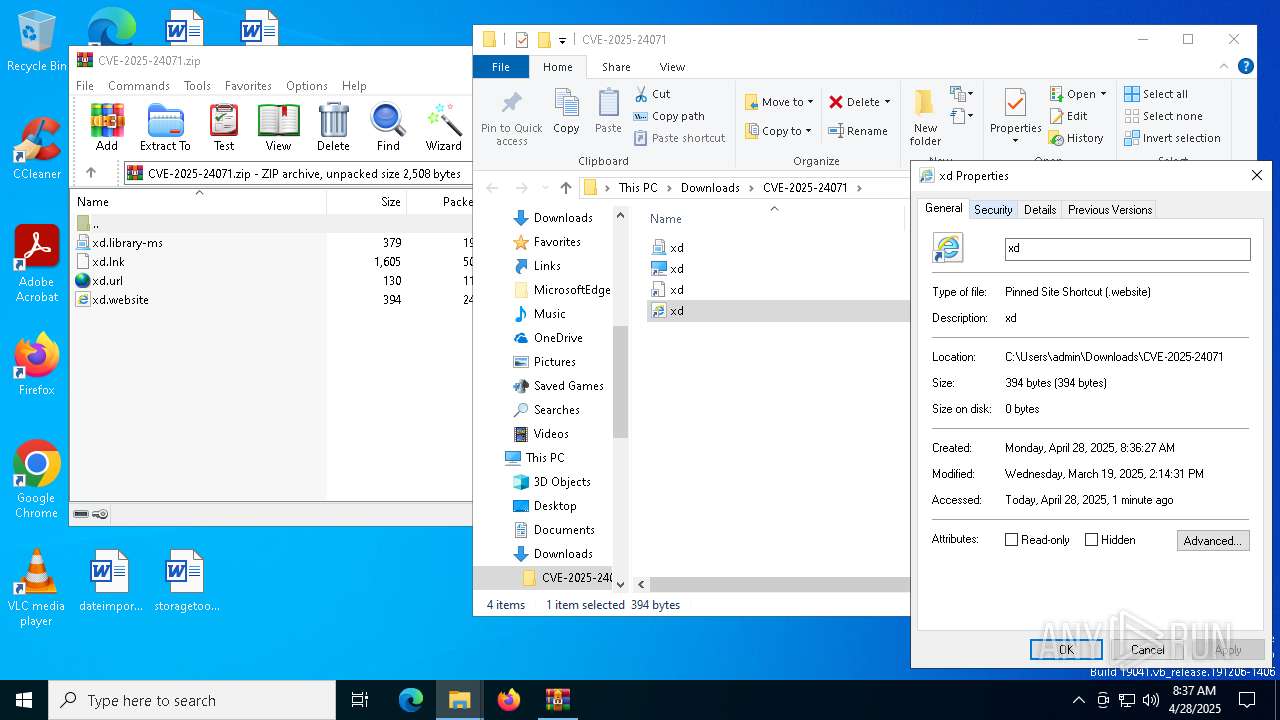
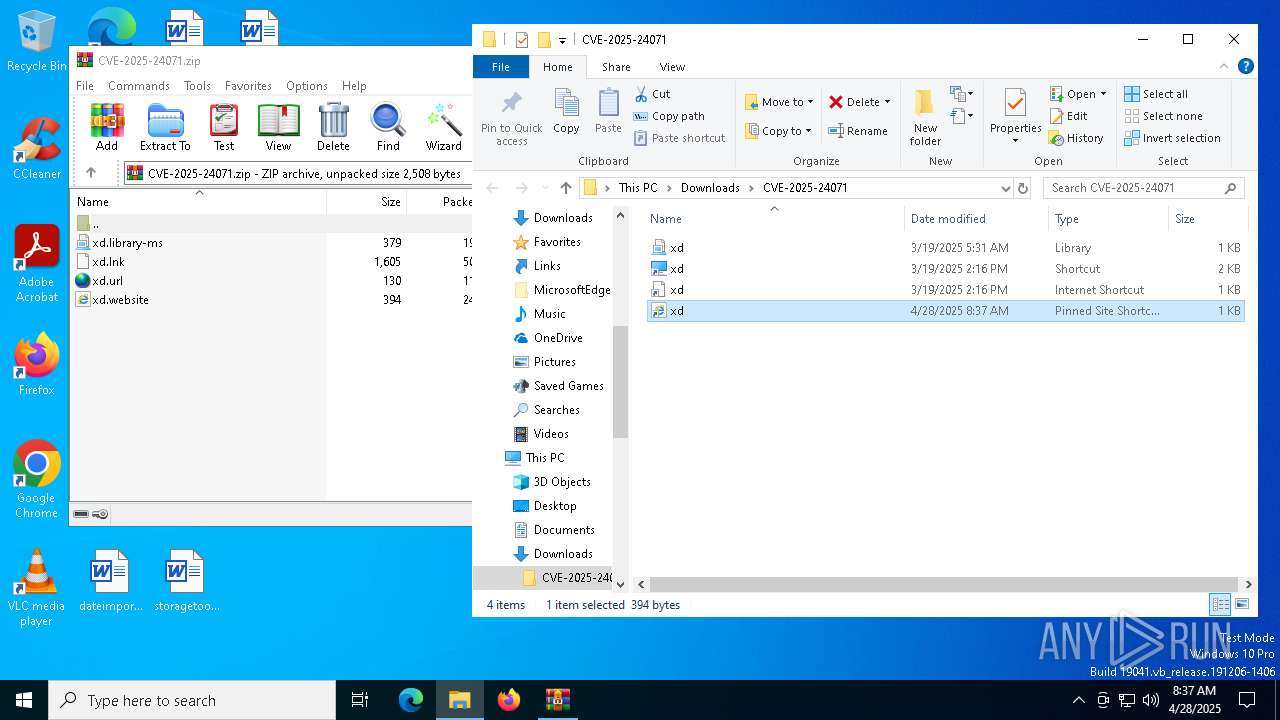
| File name: | CVE-2025-24071.zip |
| Full analysis: | https://app.any.run/tasks/5ea430b8-70e9-44c6-a26f-e06364c2b741 |
| Verdict: | Malicious activity |
| Analysis date: | April 28, 2025, 08:34:51 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract, compression method=deflate |
| MD5: | 489AA539835A09BDFC865ED2FE9B7F5D |
| SHA1: | 9CA72D969D7C5494A30E996324C6C0FCB72AE1AE |
| SHA256: | 8FAE5F0AE6070C39BA099735FE433CDB90EBB186B3F716847F29D7830E91E197 |
| SSDEEP: | 48:9GAfrhNRmY4YOAntait2gauQ2uOAXRwgM7n/lFKkwQXYkowD3y:Rfz4sXQ21+RwgML9XtpW |
MALICIOUS
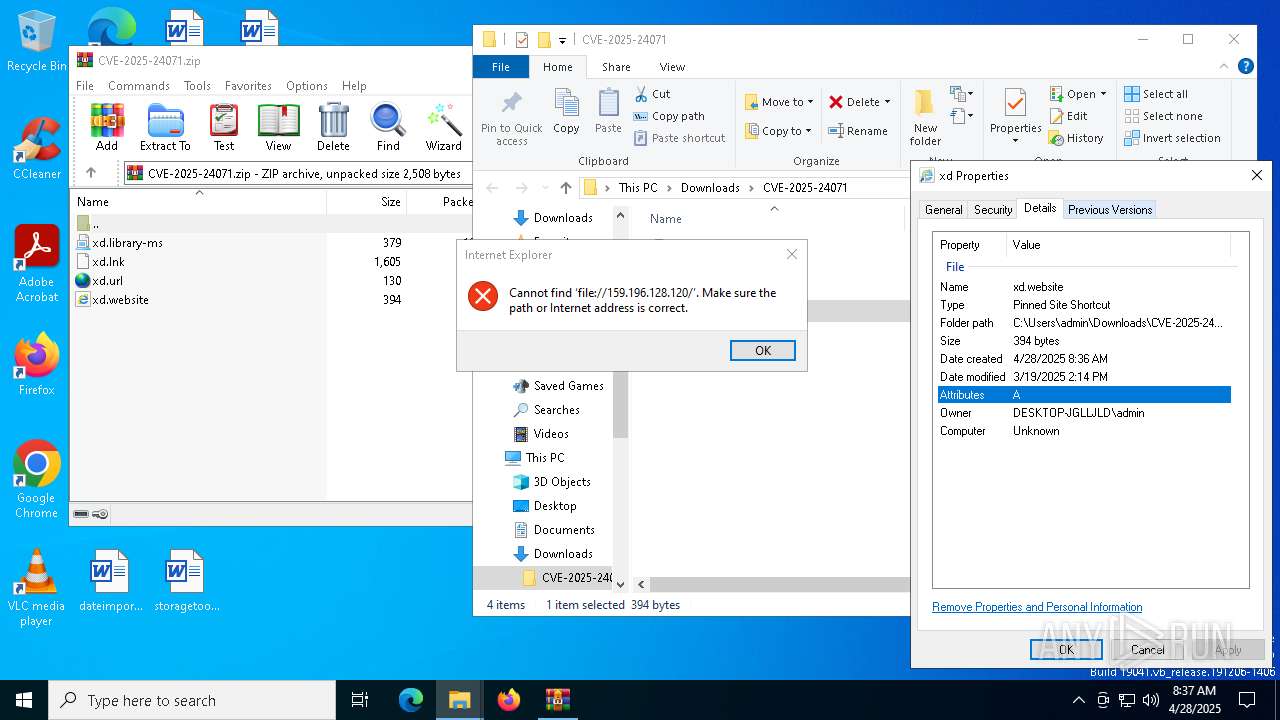
CVE-2024-43451 has been detected
- WinRAR.exe (PID: 6644)
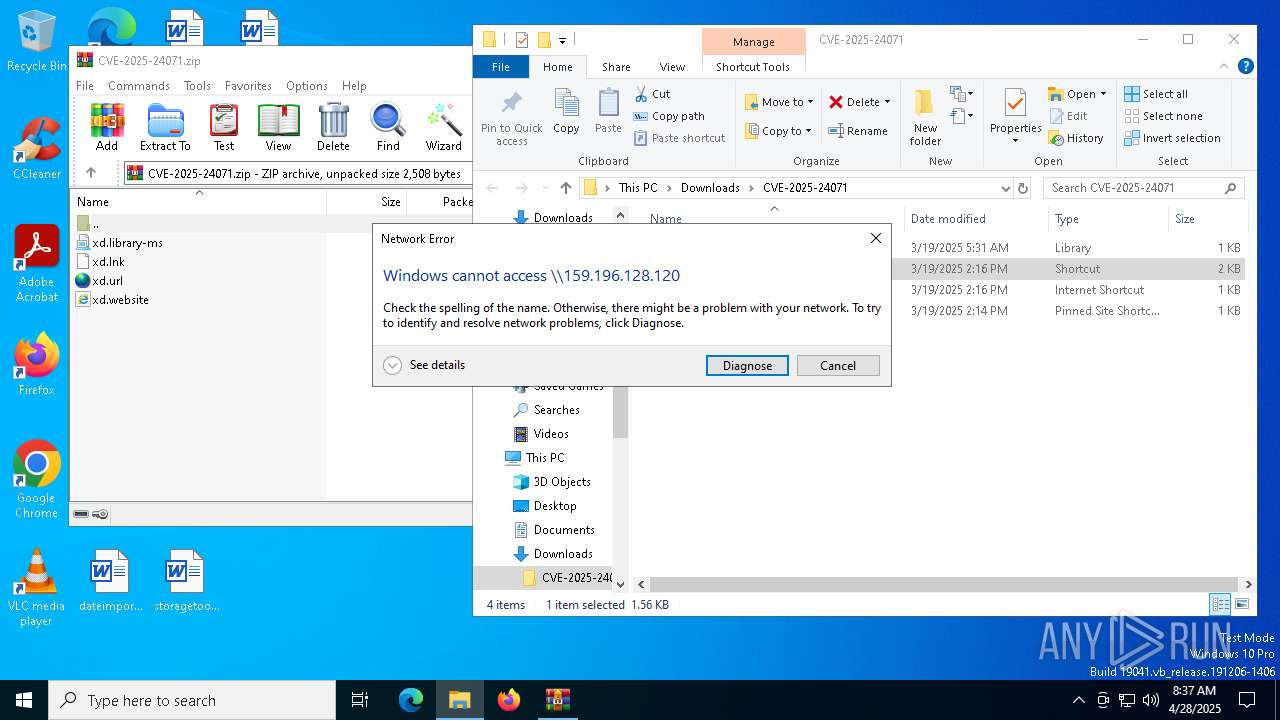
CVE-2025-24071 has been detected
- explorer.exe (PID: 5492)
GENERIC has been found (auto)
- WinRAR.exe (PID: 6644)
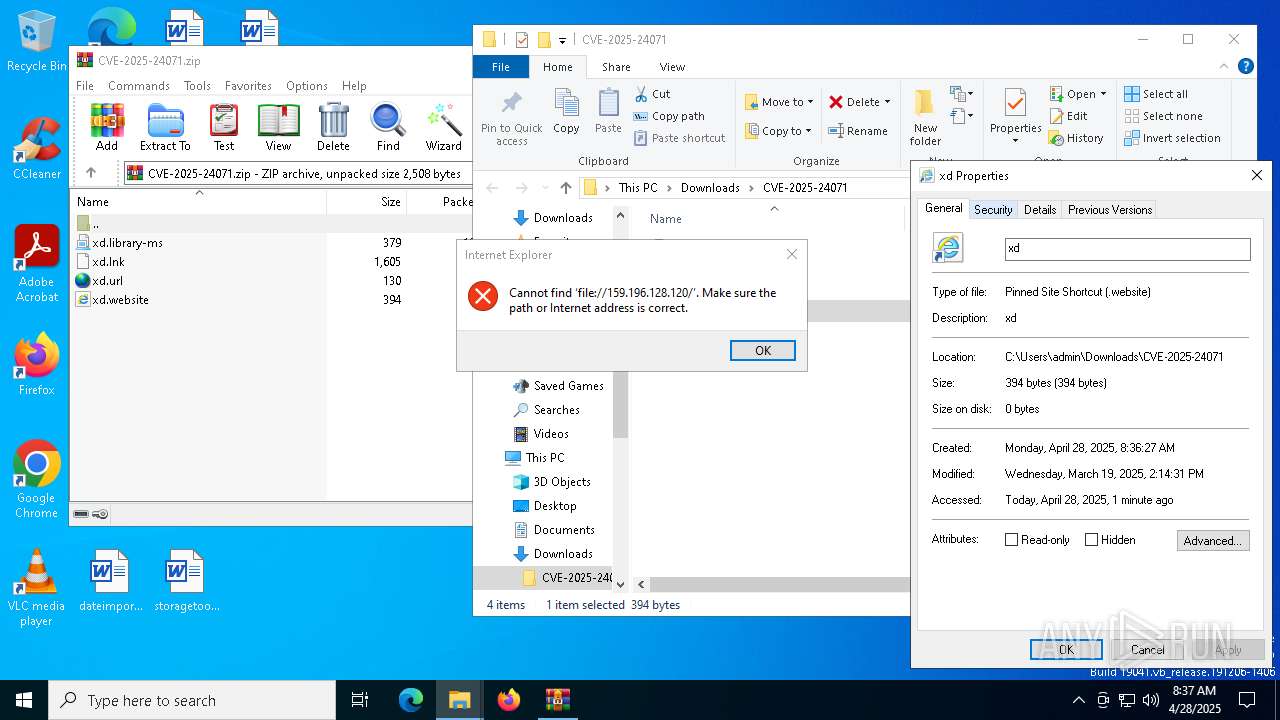
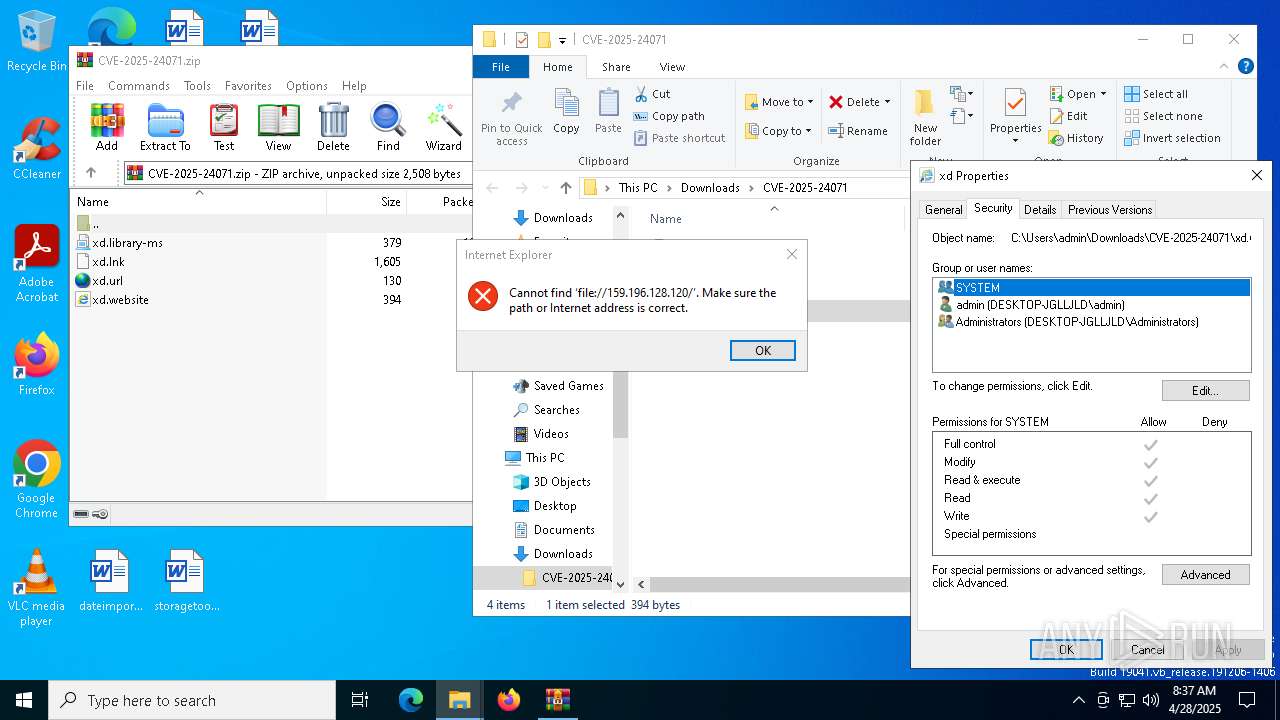
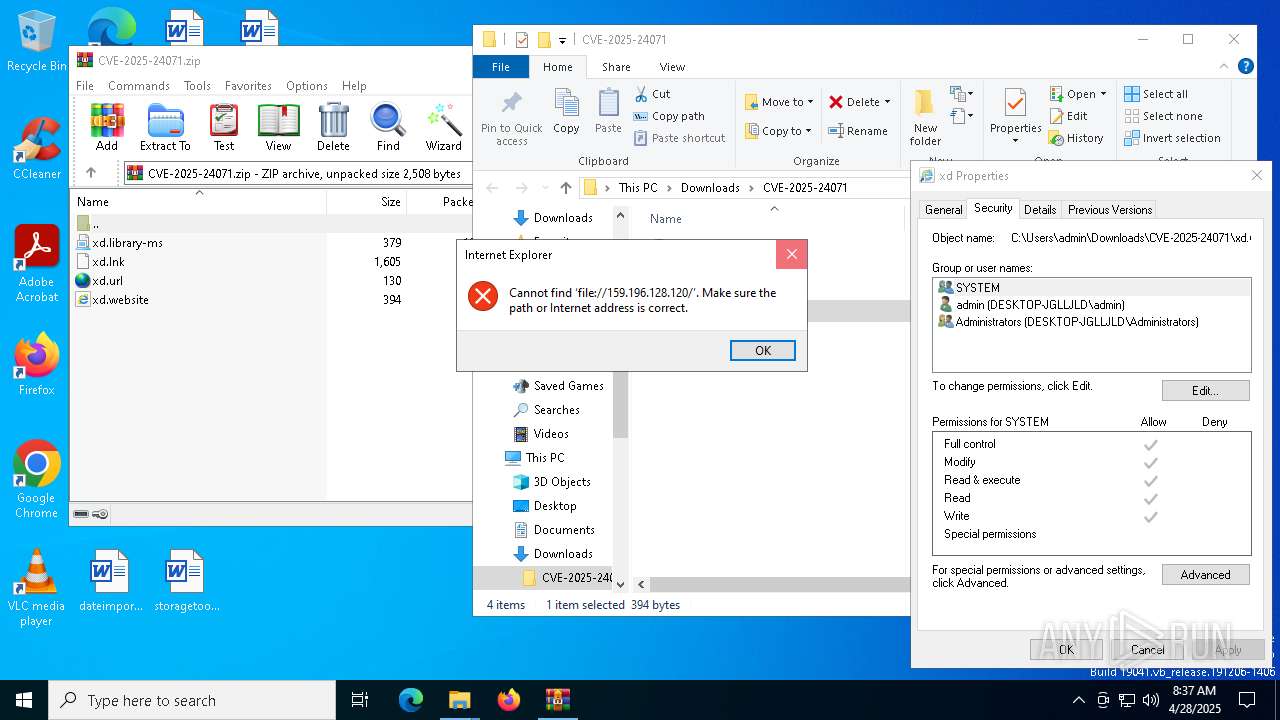
WebDav connection (SURICATA)
- explorer.exe (PID: 5492)
- iexplore.exe (PID: 1760)
- iexplore.exe (PID: 5772)
SUSPICIOUS
Uses pipe srvsvc via SMB (transferring data)
- explorer.exe (PID: 5492)
SMB connection has been detected (probably for file transfer)
- explorer.exe (PID: 5492)
Creates file in the systems drive root
- WinRAR.exe (PID: 6644)
Reads security settings of Internet Explorer
- WinRAR.exe (PID: 6644)
Potential Corporate Privacy Violation
- explorer.exe (PID: 5492)
- iexplore.exe (PID: 1760)
- iexplore.exe (PID: 5772)
INFO
Local mutex for internet shortcut management
- WinRAR.exe (PID: 6644)
- explorer.exe (PID: 5492)
- iexplore.exe (PID: 5772)
- iexplore.exe (PID: 1760)
Checks proxy server information
- explorer.exe (PID: 5492)
- slui.exe (PID: 2240)
Reads the software policy settings
- slui.exe (PID: 2240)
Reads Microsoft Office registry keys
- explorer.exe (PID: 5492)
Reads security settings of Internet Explorer
- explorer.exe (PID: 5492)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2025:03:19 05:31:26 |
| ZipCRC: | 0xd7a02a75 |
| ZipCompressedSize: | 196 |
| ZipUncompressedSize: | 379 |
| ZipFileName: | xd.library-ms |
Total processes
129
Monitored processes
6
Malicious processes
2
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 856 | C:\WINDOWS\System32\rundll32.exe C:\WINDOWS\System32\shell32.dll,SHCreateLocalServerRunDll {9aa46009-3ce0-458a-a354-715610a075e6} -Embedding | C:\Windows\System32\rundll32.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1760 | "C:\Program Files\Internet Explorer\iexplore.exe" -w "C:\Users\admin\Downloads\CVE-2025-24071\xd.website" | C:\Program Files\Internet Explorer\iexplore.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Version: 11.00.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2240 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5492 | C:\WINDOWS\Explorer.EXE | C:\Windows\explorer.exe | — | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Explorer Version: 10.0.19041.3758 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5772 | "C:\Program Files (x86)\Internet Explorer\IEXPLORE.EXE" SCODEF:1760 CREDAT:75010 APPID:Microsoft.Website.B4BD2547.99055A5E /prefetch:2 | C:\Program Files (x86)\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Version: 11.00.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6644 | "C:\Program Files\WinRAR\WinRAR.exe" C:\Users\admin\Downloads\CVE-2025-24071.zip | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Version: 5.91.0 Modules
| |||||||||||||||
Total events
24 498
Read events
24 337
Write events
138
Delete events
23
Modification events
| (PID) Process: | (6644) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (6644) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (6644) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (6644) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Downloads\CVE-2025-24071.zip | |||
| (PID) Process: | (6644) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (6644) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (6644) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (6644) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (6644) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Shell Extensions\Cached |
| Operation: | write | Name: | {182C3813-DF97-40FA-9C4E-B7D3E74F00CA} {000214FA-0000-0000-C000-000000000046} 0xFFFF |
Value: 0100000000000000739D736E18B8DB01 | |||
| (PID) Process: | (5492) explorer.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\SessionInfo\5\ApplicationViewManagement\W32:00000000000802C6 |
| Operation: | write | Name: | VirtualDesktop |
Value: 1000000030304456BFA0DB55E4278845B426357D5B5F97B3 | |||
Executable files
0
Suspicious files
4
Text files
6
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
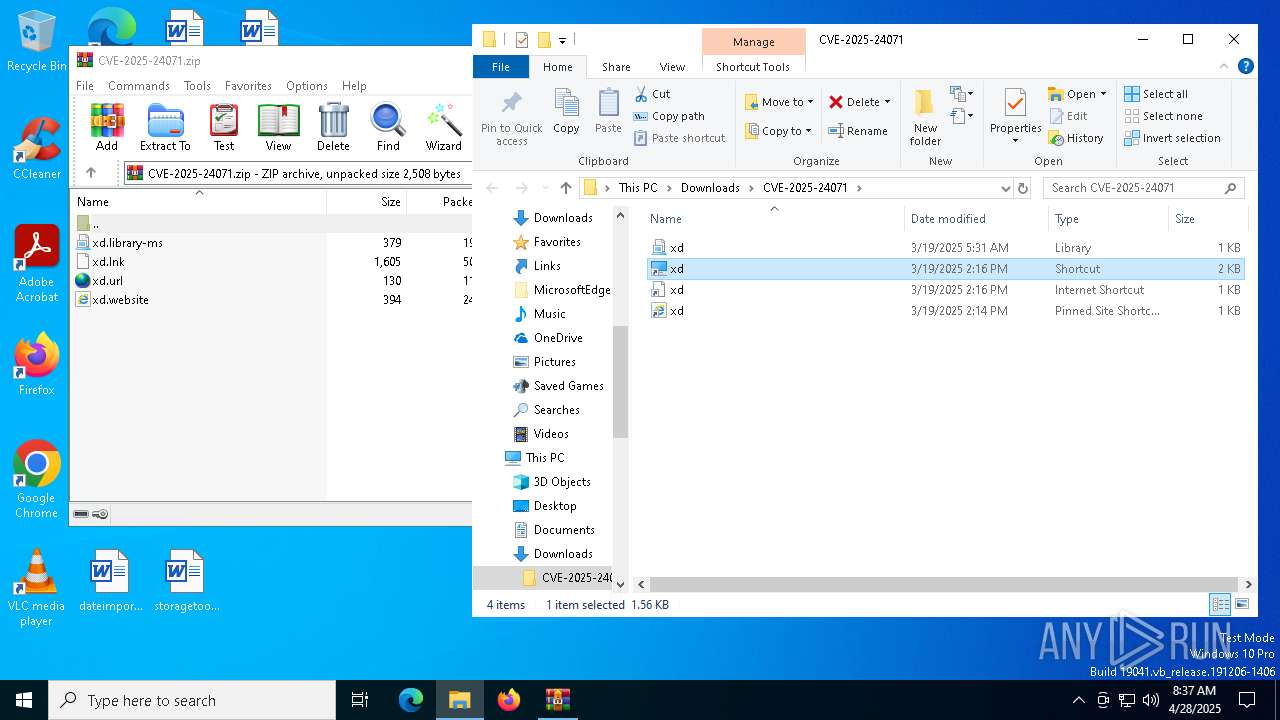
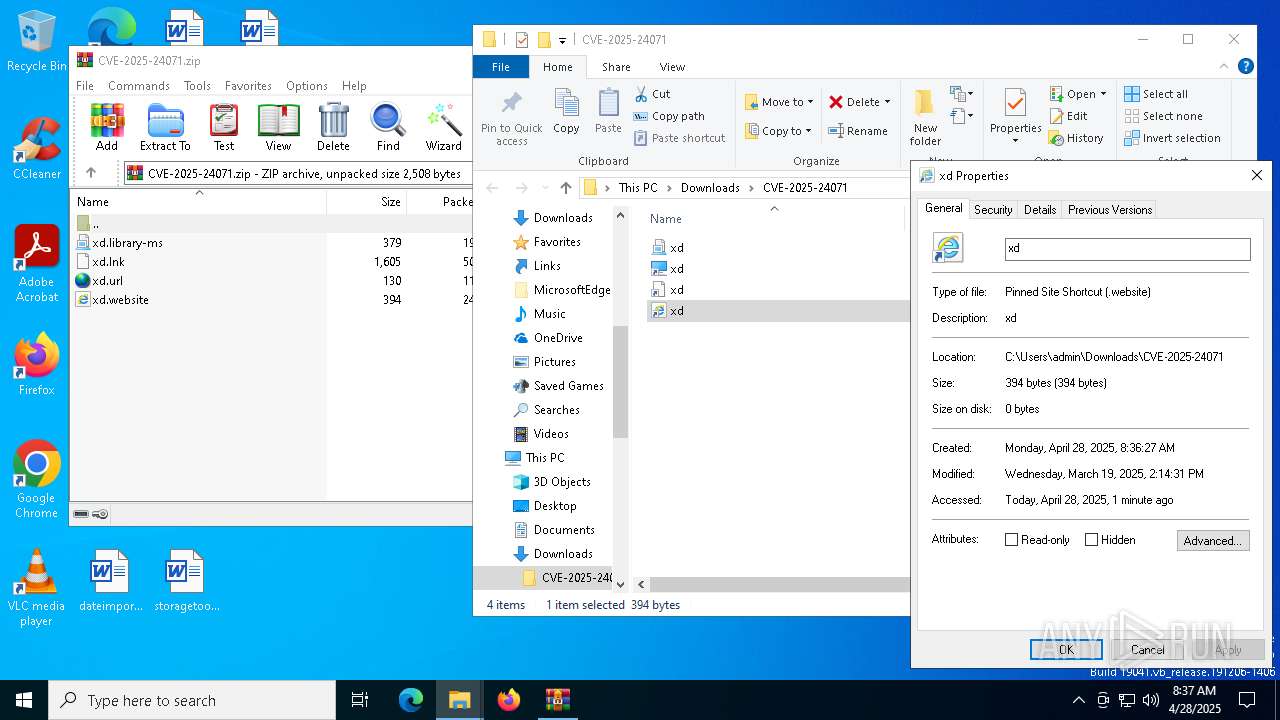
| 6644 | WinRAR.exe | C:\Users\admin\Downloads\CVE-2025-24071\xd.url | binary | |
MD5:82870DE4C0FA07E0D7F7A8267D25DC33 | SHA256:2712870335C5086848C3728E379902B3636AF1053CCD79ECA84609A75EC80910 | |||
| 6644 | WinRAR.exe | C:\Users\admin\Downloads\CVE-2025-24071\xd.website | binary | |
MD5:0F39F48C4D32340FDD65CDF9CA6EB491 | SHA256:2EBE48F08CEE2EC8EAF0B06CBE6901AF486046B3347B336478BB6A879EFF3815 | |||
| 6644 | WinRAR.exe | C:\Users\admin\Downloads\CVE-2025-24071\xd.library-ms | xml | |
MD5:33C11EE285B7CEA97FD7D00CFB40381C | SHA256:2E722603011F25D9BBD9297443B9A561BE6AB3128894B47E8FFCF9933FFCA9CB | |||
| 1760 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\INetCache\IE\RR3E01RZ\favicon[1].ico | image | |
MD5:DA597791BE3B6E732F0BC8B20E38EE62 | SHA256:5B2C34B3C4E8DD898B664DBA6C3786E2FF9869EFF55D673AA48361F11325ED07 | |||
| 5492 | explorer.exe | C:\Users\admin\AppData\Local\Microsoft\PenWorkspace\DiscoverCacheData.dat | binary | |
MD5:E49C56350AEDF784BFE00E444B879672 | SHA256:A8BD235303668981563DFB5AAE338CB802817C4060E2C199B7C84901D57B7E1E | |||
| 1760 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\Kno5576.tmp | xml | |
MD5:002D5646771D31D1E7C57990CC020150 | SHA256:1E2E25BF730FF20C89D57AA38F7F34BE7690820E8279B20127D0014DD27B743F | |||
| 1760 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\INetCache\IE\RR3E01RZ\known_providers_download_v1[1].xml | xml | |
MD5:002D5646771D31D1E7C57990CC020150 | SHA256:1E2E25BF730FF20C89D57AA38F7F34BE7690820E8279B20127D0014DD27B743F | |||
| 1760 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\Internet Explorer\Services\search_{0633EE93-D776-472f-A0FF-E1416B8B2E3A}.ico | image | |
MD5:DA597791BE3B6E732F0BC8B20E38EE62 | SHA256:5B2C34B3C4E8DD898B664DBA6C3786E2FF9869EFF55D673AA48361F11325ED07 | |||
| 6644 | WinRAR.exe | C:\Users\admin\Downloads\CVE-2025-24071\xd.lnk | binary | |
MD5:A28CE9A89F152FE99178C611B22FE7F7 | SHA256:20D43A2EB68047A93CC6CCA56E059BD3FEE8CE5264FD92C5EC5F43407B38F72B | |||
| 1760 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\INetCache\IE\KCV3KQBA\favicon[1].ico | image | |
MD5:DA597791BE3B6E732F0BC8B20E38EE62 | SHA256:5B2C34B3C4E8DD898B664DBA6C3786E2FF9869EFF55D673AA48361F11325ED07 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
41
TCP/UDP connections
110
DNS requests
22
Threats
3
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2104 | svchost.exe | GET | 200 | 23.216.77.30:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
2104 | svchost.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
— | — | GET | 304 | 4.175.87.197:443 | https://slscr.update.microsoft.com/SLS/%7B522D76A4-93E1-47F8-B8CE-07C937AD1A1E%7D/x64/10.0.19045.4046/0?CH=686&L=en-US&P=&PT=0x30&WUA=10.0.19041.3996&MK=DELL&MD=DELL | unknown | — | — | unknown |
6480 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20Update%20Signing%20CA%202.2.crl | unknown | — | — | whitelisted |
6480 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20Update%20Signing%20CA%202.1.crl | unknown | — | — | whitelisted |
6480 | SIHClient.exe | GET | 200 | 23.216.77.18:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut_2010-06-23.crl | unknown | — | — | whitelisted |
6480 | SIHClient.exe | GET | 200 | 23.216.77.18:80 | http://crl.microsoft.com/pki/crl/products/MicTimStaPCA_2010-07-01.crl | unknown | — | — | whitelisted |
6480 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
6480 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Signing%20CA%202.1.crl | unknown | — | — | whitelisted |
6480 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Signing%20CA%202.2.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
2104 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
— | — | 172.211.123.248:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
2104 | svchost.exe | 23.216.77.30:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
2104 | svchost.exe | 23.35.229.160:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
6544 | svchost.exe | 40.126.31.67:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
3216 | svchost.exe | 172.211.123.248:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
2104 | svchost.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
login.live.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
activation-v2.sls.microsoft.com |
| whitelisted |
nexusrules.officeapps.live.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
5492 | explorer.exe | Potential Corporate Privacy Violation | POLICY [ANY.RUN] WebDav activity has been detected |
1760 | iexplore.exe | Potential Corporate Privacy Violation | POLICY [ANY.RUN] WebDav activity has been detected |
5772 | iexplore.exe | Potential Corporate Privacy Violation | POLICY [ANY.RUN] WebDav activity has been detected |