| File name: | SWAT.exe |
| Full analysis: | https://app.any.run/tasks/5b15733e-d136-4994-bb3d-5b3bfaadb967 |
| Verdict: | Malicious activity |
| Analysis date: | March 08, 2025, 03:09:45 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32+ executable (console) x86-64, for MS Windows, 7 sections |
| MD5: | 96EE42A2E614609841880141FC3B1B3B |
| SHA1: | 1D0BFEABFCBE823BCB32A39B3FE10F7222C44224 |
| SHA256: | 8F91CB9E705BEBE84CEEFA2EA5D38D96AC2931D53E0B26B2FEC13277A6D8E9BC |
| SSDEEP: | 98304:Xxb2q+lpILYvI9yf+8Gm1nGc4tP2bXnZwhAxc+G5DLfl5m1LY0bRU+uh4/opz2pB:8fJlJFgOwuyVqEkT79Vyw |
MALICIOUS
No malicious indicators.SUSPICIOUS
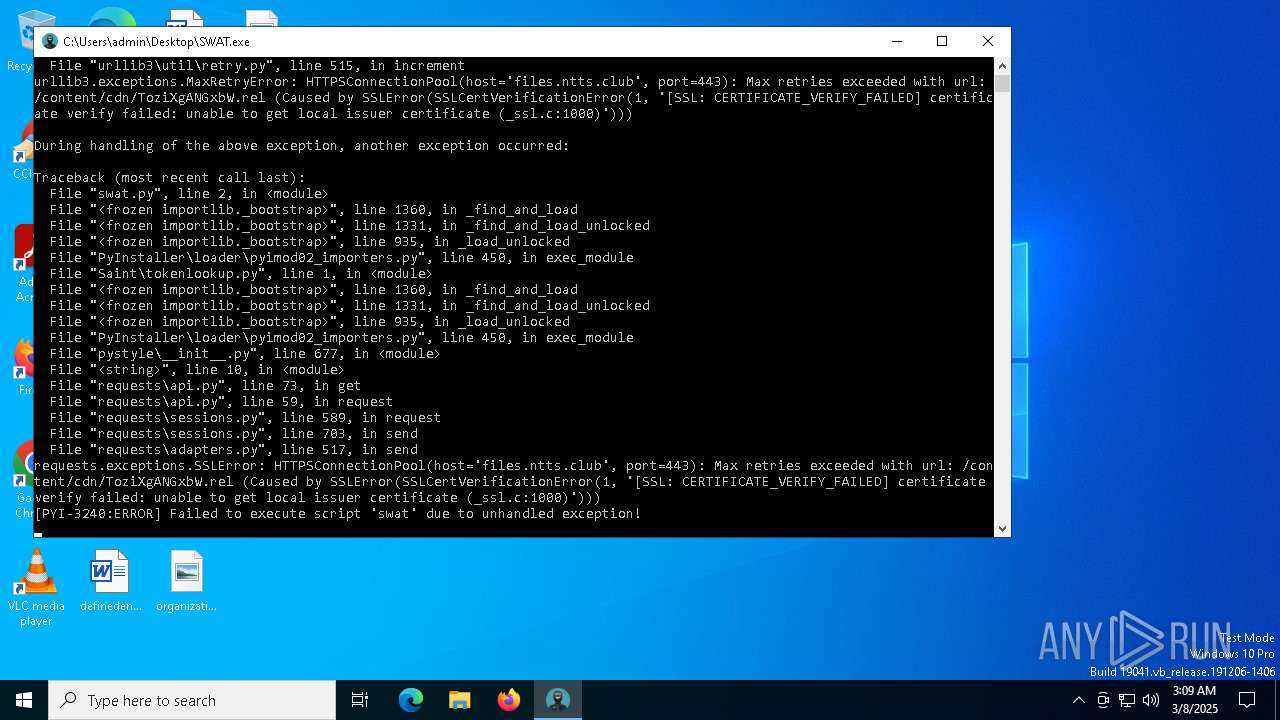
Executable content was dropped or overwritten
- SWAT.exe (PID: 4740)
The process drops C-runtime libraries
- SWAT.exe (PID: 4740)
Process drops python dynamic module
- SWAT.exe (PID: 4740)
Process drops legitimate windows executable
- SWAT.exe (PID: 4740)
Application launched itself
- SWAT.exe (PID: 4740)
Loads Python modules
- SWAT.exe (PID: 3240)
INFO
Checks supported languages
- SWAT.exe (PID: 4740)
- SWAT.exe (PID: 3240)
Reads the computer name
- SWAT.exe (PID: 4740)
- SWAT.exe (PID: 3240)
Reads the software policy settings
- slui.exe (PID: 6456)
Create files in a temporary directory
- SWAT.exe (PID: 4740)
The sample compiled with english language support
- SWAT.exe (PID: 4740)
Checks proxy server information
- slui.exe (PID: 6456)
- SWAT.exe (PID: 3240)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | InstallShield setup (57.6) |
|---|---|---|
| .exe | | | Win64 Executable (generic) (36.9) |
| .exe | | | Generic Win/DOS Executable (2.6) |
| .exe | | | DOS Executable Generic (2.6) |
EXIF
EXE
| MachineType: | AMD AMD64 |
|---|---|
| TimeStamp: | 2025:03:05 03:05:31+00:00 |
| ImageFileCharacteristics: | Executable, Large address aware |
| PEType: | PE32+ |
| LinkerVersion: | 14.42 |
| CodeSize: | 178688 |
| InitializedDataSize: | 98304 |
| UninitializedDataSize: | - |
| EntryPoint: | 0xc380 |
| OSVersion: | 6 |
| ImageVersion: | - |
| SubsystemVersion: | 6 |
| Subsystem: | Windows command line |
Total processes
123
Monitored processes
4
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 3240 | "C:\Users\admin\Desktop\SWAT.exe" | C:\Users\admin\Desktop\SWAT.exe | SWAT.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 1 Modules
| |||||||||||||||
| 4740 | "C:\Users\admin\Desktop\SWAT.exe" | C:\Users\admin\Desktop\SWAT.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 1 Modules
| |||||||||||||||
| 5720 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | SWAT.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6456 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
3 684
Read events
3 684
Write events
0
Delete events
0
Modification events
Executable files
70
Suspicious files
1
Text files
9
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 4740 | SWAT.exe | C:\Users\admin\AppData\Local\Temp\_MEI47402\VCRUNTIME140_1.dll | executable | |
MD5:F8DFA78045620CF8A732E67D1B1EB53D | SHA256:A113F192195F245F17389E6ECBED8005990BCB2476DDAD33F7C4C6C86327AFE5 | |||
| 4740 | SWAT.exe | C:\Users\admin\AppData\Local\Temp\_MEI47402\_multiprocessing.pyd | executable | |
MD5:A4281E383EF82C482C8BDA50504BE04A | SHA256:467B0FEF42D70B55ABF41D817DFF7631FAEEF84DCE64F8AADB5690A22808D40C | |||
| 4740 | SWAT.exe | C:\Users\admin\AppData\Local\Temp\_MEI47402\_cffi_backend.cp312-win_amd64.pyd | executable | |
MD5:0572B13646141D0B1A5718E35549577C | SHA256:D8A76D1E31BBD62A482DEA9115FC1A109CB39AF4CF6D1323409175F3C93113A7 | |||
| 4740 | SWAT.exe | C:\Users\admin\AppData\Local\Temp\_MEI47402\_brotli.cp312-win_amd64.pyd | executable | |
MD5:9AD5BB6F92EE2CFD29DDE8DD4DA99EB7 | SHA256:788ACBFD0EDD6CA3EF3E97A9487EEAEA86515642C71CB11BBCF25721E6573EC8 | |||
| 4740 | SWAT.exe | C:\Users\admin\AppData\Local\Temp\_MEI47402\_decimal.pyd | executable | |
MD5:3055EDF761508190B576E9BF904003AA | SHA256:E4104E47399D3F635A14D649F61250E9FD37F7E65C81FFE11F099923F8532577 | |||
| 4740 | SWAT.exe | C:\Users\admin\AppData\Local\Temp\_MEI47402\_queue.pyd | executable | |
MD5:6E0CB85DC94E351474D7625F63E49B22 | SHA256:3F57F29ABD86D4DC8F4CA6C3F190EBB57D429143D98F0636FF5117E08ED81F9B | |||
| 4740 | SWAT.exe | C:\Users\admin\AppData\Local\Temp\_MEI47402\_lzma.pyd | executable | |
MD5:05E8B2C429AFF98B3AE6ADC842FB56A3 | SHA256:A6E2A5BB7A33AD9054F178786A031A46EA560FAEEF1FB96259331500AAE9154C | |||
| 4740 | SWAT.exe | C:\Users\admin\AppData\Local\Temp\_MEI47402\_hashlib.pyd | executable | |
MD5:EEDB6D834D96A3DFFFFB1F65B5F7E5BE | SHA256:79C4CDE23397B9A35B54A3C2298B3C7A844454F4387CB0693F15E4FACD227DD2 | |||
| 4740 | SWAT.exe | C:\Users\admin\AppData\Local\Temp\_MEI47402\_wmi.pyd | executable | |
MD5:7EC3FC12C75268972078B1C50C133E9B | SHA256:1A105311A5ED88A31472B141B4B6DAA388A1CD359FE705D9A7A4ABA793C5749F | |||
| 4740 | SWAT.exe | C:\Users\admin\AppData\Local\Temp\_MEI47402\_socket.pyd | executable | |
MD5:DC06F8D5508BE059EAE9E29D5BA7E9EC | SHA256:7DAFF6AA3851A913ED97995702A5DFB8A27CB7CF00FB496597BE777228D7564A | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
2
TCP/UDP connections
20
DNS requests
4
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | POST | 500 | 40.91.76.224:443 | https://activation-v2.sls.microsoft.com/SLActivateProduct/SLActivateProduct.asmx?configextension=Retail | unknown | xml | 512 b | whitelisted |
— | — | POST | 500 | 40.91.76.224:443 | https://activation-v2.sls.microsoft.com/SLActivateProduct/SLActivateProduct.asmx?configextension=Retail | unknown | xml | 512 b | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 192.168.100.255:138 | — | — | — | whitelisted |
— | — | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
3240 | SWAT.exe | 104.21.48.1:443 | files.ntts.club | CLOUDFLARENET | — | unknown |
6068 | slui.exe | 40.91.76.224:443 | activation-v2.sls.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
6456 | slui.exe | 40.91.76.224:443 | activation-v2.sls.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
files.ntts.club |
| unknown |
activation-v2.sls.microsoft.com |
| whitelisted |