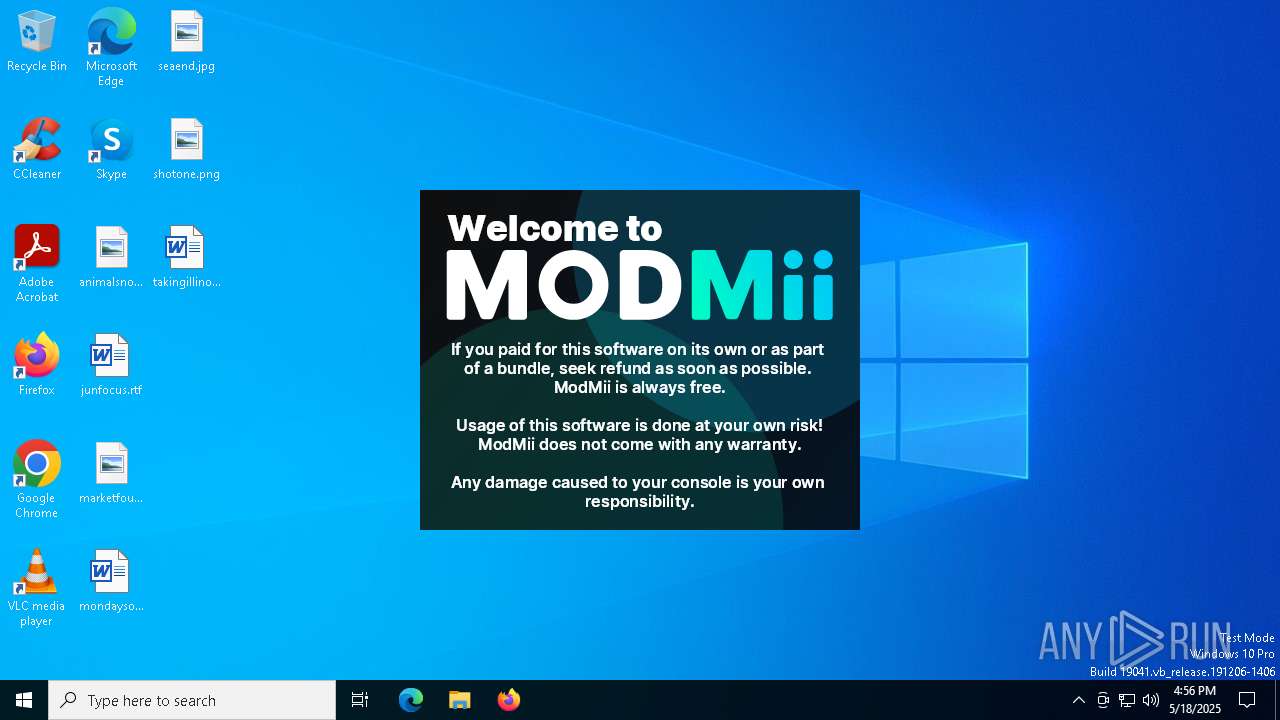
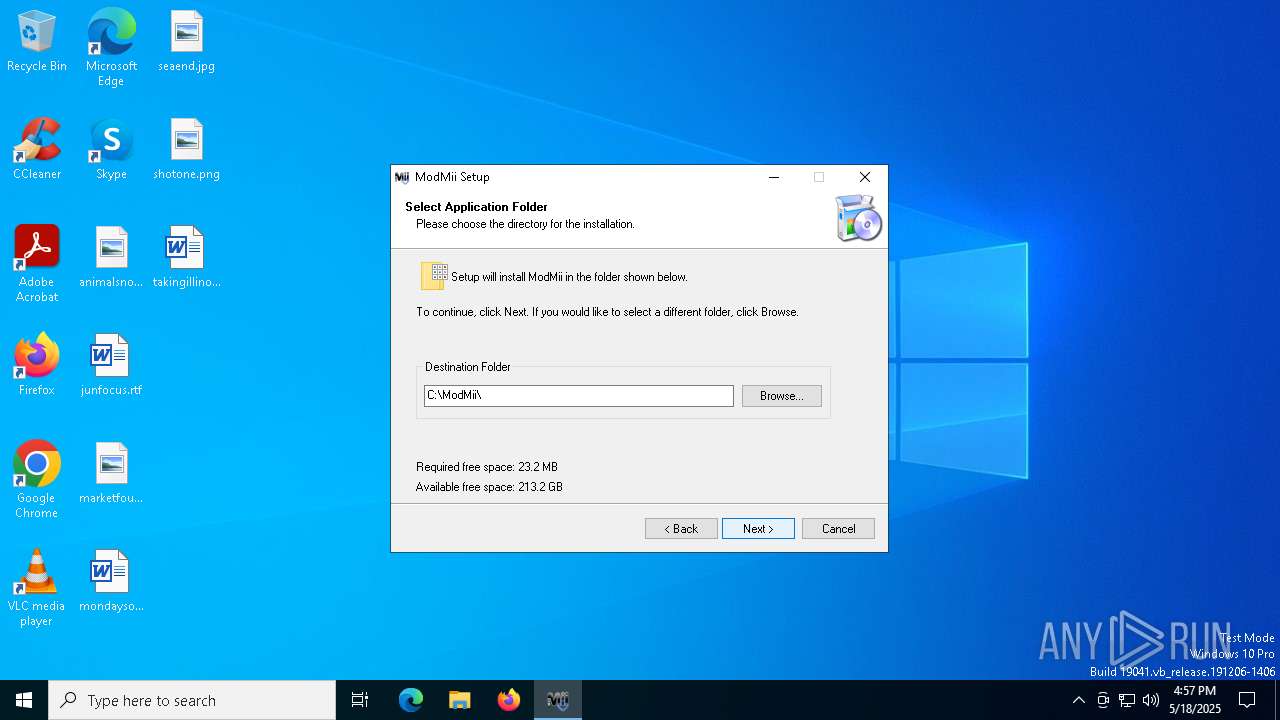
| File name: | ModMiiInstaller.exe |
| Full analysis: | https://app.any.run/tasks/833e3a20-464f-4ff3-b37b-7e89e7ae6c16 |
| Verdict: | Malicious activity |
| Analysis date: | May 18, 2025, 16:56:46 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, InstallShield self-extracting archive, 5 sections |
| MD5: | 8E7FCC949082919F7D15BF1E5A3E04DD |
| SHA1: | 69A6B8256D0748AF358112C34C39C7D5AB66345D |
| SHA256: | 8F7D0E34BA782B9AD03EDD95ECB35387E763ADFAC62ABECAA484EA7CA7A28A5B |
| SSDEEP: | 98304:NKaUakn0XI0Ve6xsyw//9HpXYsIzOb700oi+7Qlycb4Vvk9GcuDhiyM8JXXYxSFv:wRaLW/1TPz7RxXWfZPsiGfyD |
MALICIOUS
Detects Cygwin installation
- ModMiiInstaller.exe (PID: 7756)
SUSPICIOUS
There is functionality for taking screenshot (YARA)
- ModMiiInstaller.exe (PID: 7756)
The process creates files with name similar to system file names
- ModMiiInstaller.exe (PID: 7756)
Process drops legitimate windows executable
- ModMiiInstaller.exe (PID: 7756)
The process drops C-runtime libraries
- ModMiiInstaller.exe (PID: 7756)
Reads security settings of Internet Explorer
- ModMiiInstaller.exe (PID: 7756)
Creates a software uninstall entry
- ModMiiInstaller.exe (PID: 7756)
Creates file in the systems drive root
- explorer.exe (PID: 5776)
Executable content was dropped or overwritten
- ModMiiInstaller.exe (PID: 7756)
- cmd.exe (PID: 1056)
Drops 7-zip archiver for unpacking
- ModMiiInstaller.exe (PID: 7756)
Starts CMD.EXE for commands execution
- ModMiiSkin.exe (PID: 4988)
Executing commands from a ".bat" file
- ModMiiSkin.exe (PID: 4988)
Starts application with an unusual extension
- cmd.exe (PID: 1056)
Application launched itself
- WizApp.exe (PID: 6964)
INFO
Reads the computer name
- ModMiiInstaller.exe (PID: 7756)
- WizApp.exe (PID: 5416)
Create files in a temporary directory
- ModMiiInstaller.exe (PID: 7756)
Checks supported languages
- ModMiiInstaller.exe (PID: 7756)
- ModMiiSkin.exe (PID: 4988)
- nircmd.exe (PID: 5344)
- nircmd.exe (PID: 5892)
- chcp.com (PID: 5376)
- WizApp.exe (PID: 6964)
- nircmd.exe (PID: 4696)
- WizApp.exe (PID: 5416)
- nircmd.exe (PID: 5504)
Creates files or folders in the user directory
- ModMiiInstaller.exe (PID: 7756)
Manual execution by a user
- explorer.exe (PID: 7632)
- ModMiiSkin.exe (PID: 4988)
Reads security settings of Internet Explorer
- explorer.exe (PID: 5776)
Reads mouse settings
- ModMiiSkin.exe (PID: 4988)
The sample compiled with english language support
- ModMiiInstaller.exe (PID: 7756)
- cmd.exe (PID: 1056)
NirSoft software is detected
- nircmd.exe (PID: 5892)
- nircmd.exe (PID: 5344)
- nircmd.exe (PID: 4696)
Changes the display of characters in the console
- cmd.exe (PID: 1056)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | InstallShield setup (36.1) |
|---|---|---|
| .exe | | | Win32 Executable MS Visual C++ (generic) (26.2) |
| .exe | | | Win64 Executable (generic) (23.1) |
| .dll | | | Win32 Dynamic Link Library (generic) (5.5) |
| .exe | | | Win32 Executable (generic) (3.7) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2016:09:03 22:28:04+00:00 |
| ImageFileCharacteristics: | No relocs, Executable, No line numbers, No symbols, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 2.5 |
| CodeSize: | 201728 |
| InitializedDataSize: | 397312 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x1000 |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
Total processes
150
Monitored processes
15
Malicious processes
1
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1056 | C:\WINDOWS\system32\cmd.exe /c Support\ModMiiSkin.bat | C:\Windows\SysWOW64\cmd.exe | ModMiiSkin.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4696 | support\nircmd.exe wait 6000 | C:\ModMii\Support\nircmd.exe | — | cmd.exe | |||||||||||
User: admin Company: NirSoft Integrity Level: MEDIUM Description: NirCmd Exit code: 0 Version: 2.65 Modules
| |||||||||||||||
| 4988 | "C:\ModMii\ModMiiSkin.exe" | C:\ModMii\ModMiiSkin.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Description: ModMii Skin Launcher Version: 2.2.0.0 Modules
| |||||||||||||||
| 5344 | support\nircmd.exe win trans ititle "ModMiiSkinCMD" 0 | C:\ModMii\Support\nircmd.exe | — | cmd.exe | |||||||||||
User: admin Company: NirSoft Integrity Level: MEDIUM Description: NirCmd Exit code: 0 Version: 2.65 Modules
| |||||||||||||||
| 5376 | chcp 437 | C:\Windows\SysWOW64\chcp.com | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Change CodePage Utility Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5416 | C:\ModMii\support\WizApp.exe sync SPLASH OPEN | C:\ModMii\Support\WizApp.exe | — | WizApp.exe | |||||||||||
User: admin Company: Dion Nicolaas Integrity Level: MEDIUM Description: Wizard's Apprentice Version: 1.5 Modules
| |||||||||||||||
| 5504 | support\nircmd.exe wait 2000 | C:\ModMii\Support\nircmd.exe | — | cmd.exe | |||||||||||
User: admin Company: NirSoft Integrity Level: MEDIUM Description: NirCmd Version: 2.65 Modules
| |||||||||||||||
| 5512 | C:\WINDOWS\System32\rundll32.exe C:\WINDOWS\System32\shell32.dll,SHCreateLocalServerRunDll {9aa46009-3ce0-458a-a354-715610a075e6} -Embedding | C:\Windows\System32\rundll32.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5776 | C:\WINDOWS\explorer.exe /factory,{75dff2b7-6936-4c06-a8bb-676a7b00b24b} -Embedding | C:\Windows\explorer.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Explorer Version: 10.0.19041.3758 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5892 | support\nircmd.exe win hide ititle "ModMiiSkinCMD" | C:\ModMii\Support\nircmd.exe | — | cmd.exe | |||||||||||
User: admin Company: NirSoft Integrity Level: MEDIUM Description: NirCmd Exit code: 0 Version: 2.65 Modules
| |||||||||||||||
Total events
14 463
Read events
14 353
Write events
105
Delete events
5
Modification events
| (PID) Process: | (7756) ModMiiInstaller.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Control\MediaResources\DirectSound\Speaker Configuration |
| Operation: | write | Name: | Speaker Configuration |
Value: 4 | |||
| (PID) Process: | (7756) ModMiiInstaller.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Uninstall\ModMii |
| Operation: | write | Name: | DisplayName |
Value: ModMii | |||
| (PID) Process: | (7756) ModMiiInstaller.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Uninstall\ModMii |
| Operation: | write | Name: | DisplayVersion |
Value: 7.0.3 | |||
| (PID) Process: | (7756) ModMiiInstaller.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Uninstall\ModMii |
| Operation: | write | Name: | HelpLink |
Value: https://modmii.github.io | |||
| (PID) Process: | (7756) ModMiiInstaller.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Uninstall\ModMii |
| Operation: | write | Name: | Publisher |
Value: XFlak | |||
| (PID) Process: | (7756) ModMiiInstaller.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Uninstall\ModMii |
| Operation: | write | Name: | UninstallString |
Value: C:\ModMii\Uninstall.exe | |||
| (PID) Process: | (7756) ModMiiInstaller.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Uninstall\ModMii |
| Operation: | write | Name: | DisplayIcon |
Value: C:\ModMii\Uninstall.exe | |||
| (PID) Process: | (5776) explorer.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\BagMRU |
| Operation: | write | Name: | NodeSlots |
Value: 02020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202 | |||
| (PID) Process: | (5776) explorer.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\BagMRU |
| Operation: | write | Name: | MRUListEx |
Value: 04000000030000000E00000000000000100000000F0000000C0000000D0000000B000000050000000A000000090000000800000001000000070000000600000002000000FFFFFFFF | |||
| (PID) Process: | (5776) explorer.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Internet Explorer\Toolbar |
| Operation: | write | Name: | Locked |
Value: 1 | |||
Executable files
34
Suspicious files
192
Text files
131
Unknown types
1
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 7756 | ModMiiInstaller.exe | C:\Users\admin\AppData\Local\Temp\IF{065F50B8-DB03-4C46-84A4-EEE933D6C67D}\languages.dat | text | |
MD5:A6FB0111CBF1CBF35E3AFA2392E206BC | SHA256:59C8B5AE2D98ACAE9FDD97095A908230F28B2A5C4DFB27CEEB5814ADF906727B | |||
| 7756 | ModMiiInstaller.exe | C:\Users\admin\AppData\Local\Temp\IF{065F50B8-DB03-4C46-84A4-EEE933D6C67D}\Image_Left.jpg | image | |
MD5:790E4312FE9C292B4B170C5FACD3C9F8 | SHA256:160DEB45C739E0178A542F8F512D6E3A8DF47259B434CAFF967CD1182E9A9142 | |||
| 7756 | ModMiiInstaller.exe | C:\Users\admin\AppData\Local\Temp\IF{065F50B8-DB03-4C46-84A4-EEE933D6C67D}\Default.ifl | text | |
MD5:DC51022CF78C9B519F2058983A773119 | SHA256:93E28A5125B4864773F53D1C5F87C1756EFA0C2D60D5C3FD6B34AA920080F568 | |||
| 7756 | ModMiiInstaller.exe | C:\Users\admin\AppData\Local\Temp\IF{065F50B8-DB03-4C46-84A4-EEE933D6C67D}\English.ifl | text | |
MD5:DC51022CF78C9B519F2058983A773119 | SHA256:93E28A5125B4864773F53D1C5F87C1756EFA0C2D60D5C3FD6B34AA920080F568 | |||
| 7756 | ModMiiInstaller.exe | C:\ModMii\ModMii.exe | executable | |
MD5:7C73DBE8AEE0014333BA476365EC6200 | SHA256:3B1A07AFFFA80F325BFDC252779E5D41451F176854CE45F51F0B3B08B009C54C | |||
| 7756 | ModMiiInstaller.exe | C:\Users\admin\AppData\Local\Temp\IF{065F50B8-DB03-4C46-84A4-EEE933D6C67D}\isps.dat | image | |
MD5:C1CF7EEC02EC8ECCB8CF8B53743A506C | SHA256:B7E536288C81C37647B51051D71A3955115F3F354DC56ED3448158410CA32DF8 | |||
| 7756 | ModMiiInstaller.exe | C:\Users\admin\AppData\Local\Temp\IF{065F50B8-DB03-4C46-84A4-EEE933D6C67D}\icon.dat | image | |
MD5:FA63A0160B9FF05DC70CFBCA82B465B6 | SHA256:D3A14188ECCD7761CD20CE86237F481A4BCDDFFCD460871BD7B4504F6162D9DA | |||
| 7756 | ModMiiInstaller.exe | C:\ModMii\uninstall_l.ifl | text | |
MD5:DC51022CF78C9B519F2058983A773119 | SHA256:93E28A5125B4864773F53D1C5F87C1756EFA0C2D60D5C3FD6B34AA920080F568 | |||
| 7756 | ModMiiInstaller.exe | C:\ModMii\Support\00000000-template.app | binary | |
MD5:9C9F9AAA96D49E99C3A2F6A831AFA5C6 | SHA256:246378F5862B5F179F5E866F218E8D7DC33CFEE48DE3BE008CC05E4FC3BB84D7 | |||
| 7756 | ModMiiInstaller.exe | C:\ModMii\Support\7za.exe | executable | |
MD5:42BADC1D2F03A8B1E4875740D3D49336 | SHA256:C136B1467D669A725478A6110EBAAAB3CB88A3D389DFA688E06173C066B76FCF | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
8
TCP/UDP connections
26
DNS requests
20
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5496 | MoUsoCoreWorker.exe | GET | 200 | 23.48.23.143:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
5496 | MoUsoCoreWorker.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
2924 | SearchApp.exe | GET | 200 | 204.79.197.203:80 | http://oneocsp.microsoft.com/ocsp/MFQwUjBQME4wTDAJBgUrDgMCGgUABBSzT%2FzqwcqNvhP9i4c4sCPz2JbzrAQU%2FglxQFUFEETYpIF1uJ4a6UoGiMgCEzMCEaMyGBaB8iJM%2BnUAAAIRozI%3D | unknown | — | — | whitelisted |
6544 | svchost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
2136 | SIHClient.exe | GET | 200 | 2.23.246.101:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
2136 | SIHClient.exe | GET | 200 | 2.23.246.101:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
2924 | SearchApp.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
2924 | SearchApp.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 192.168.100.255:137 | — | — | — | whitelisted |
6404 | RUXIMICS.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
2104 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5496 | MoUsoCoreWorker.exe | 23.48.23.143:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
5496 | MoUsoCoreWorker.exe | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
3216 | svchost.exe | 172.211.123.248:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
6544 | svchost.exe | 20.190.160.17:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
6544 | svchost.exe | 2.17.190.73:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
fp.msedge.net |
| whitelisted |