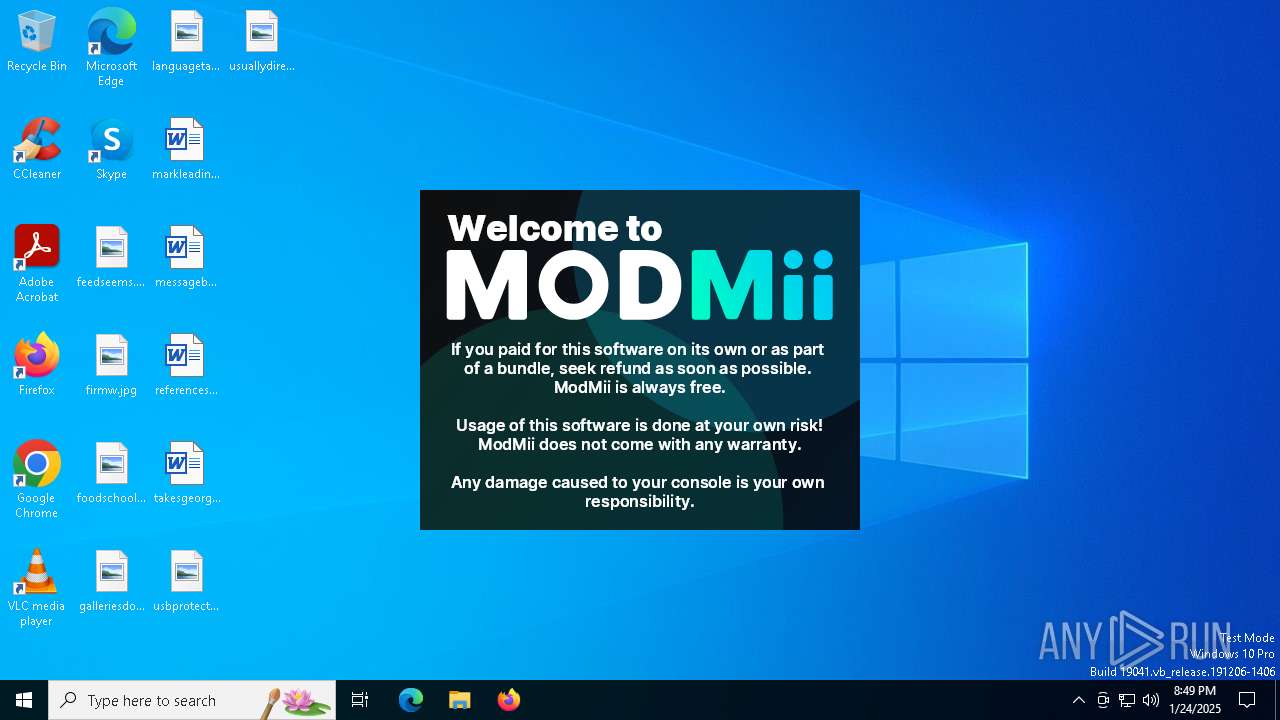
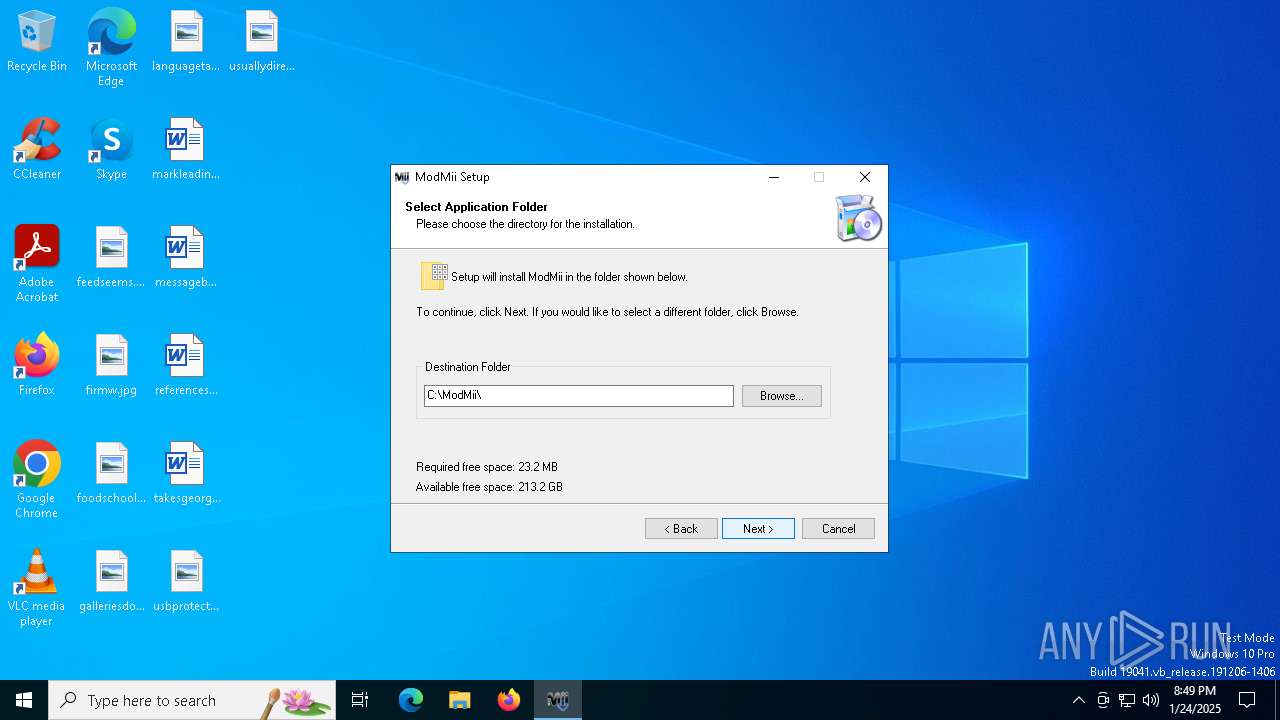
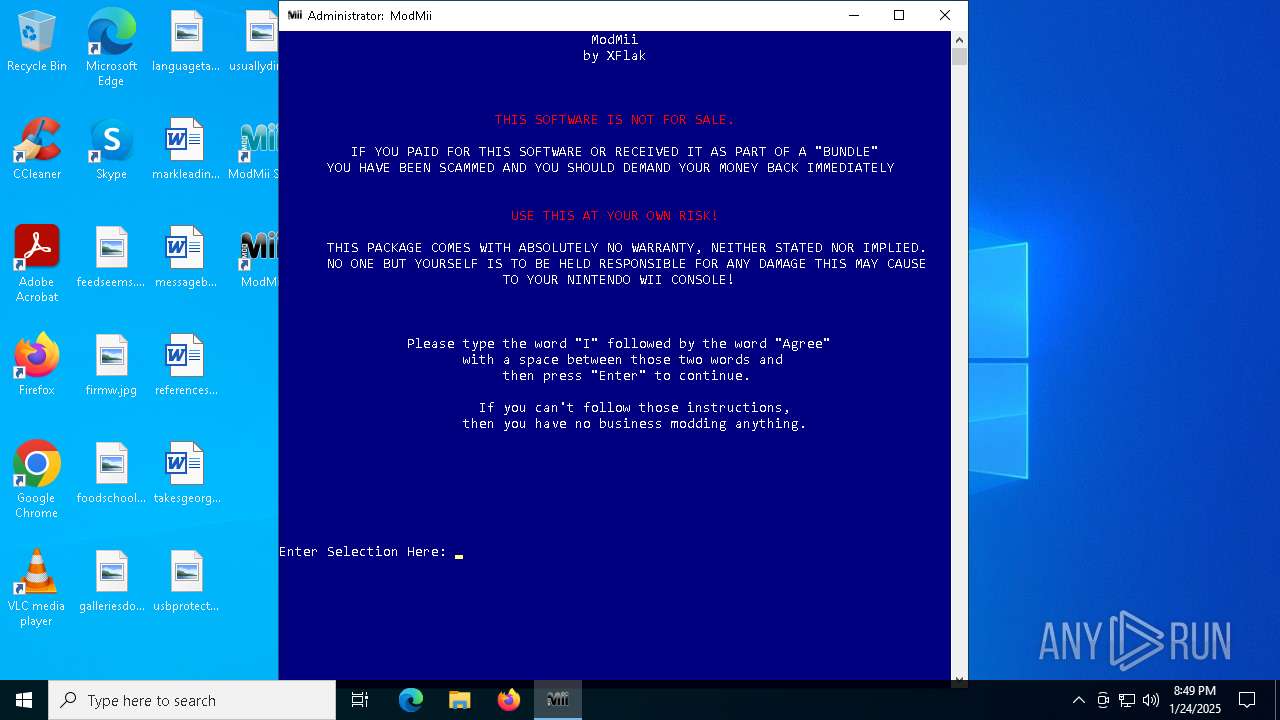
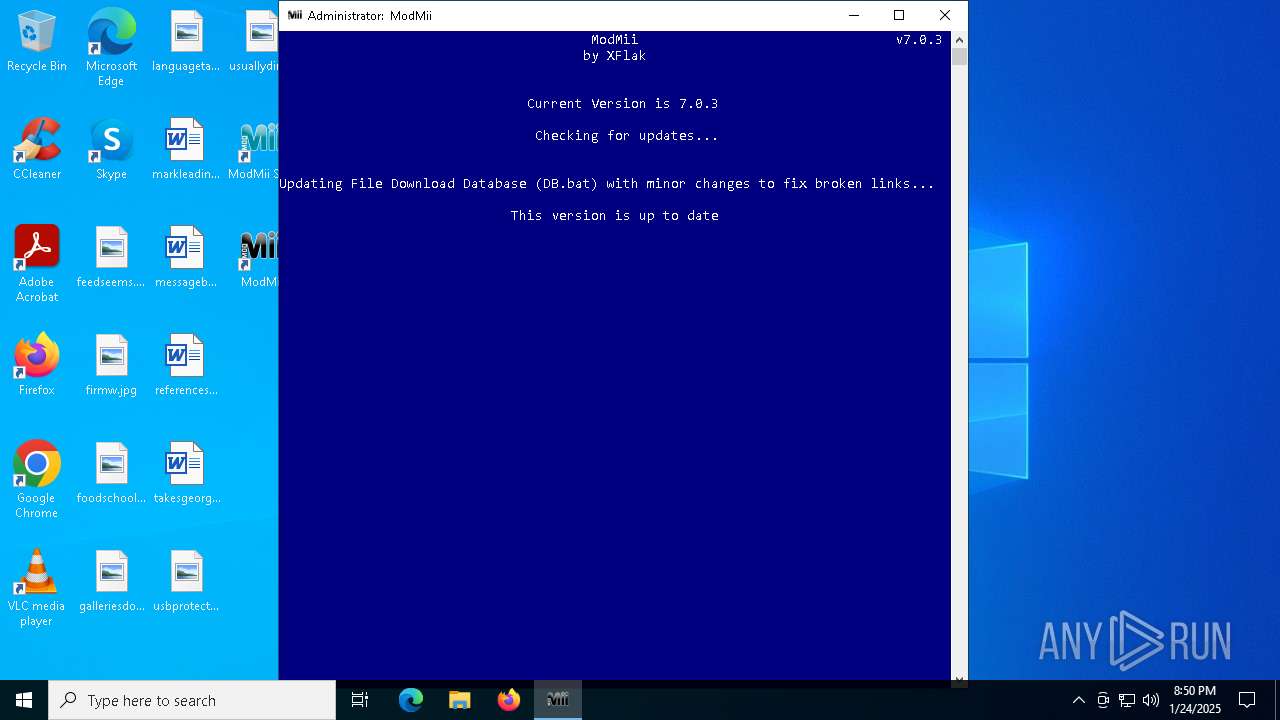
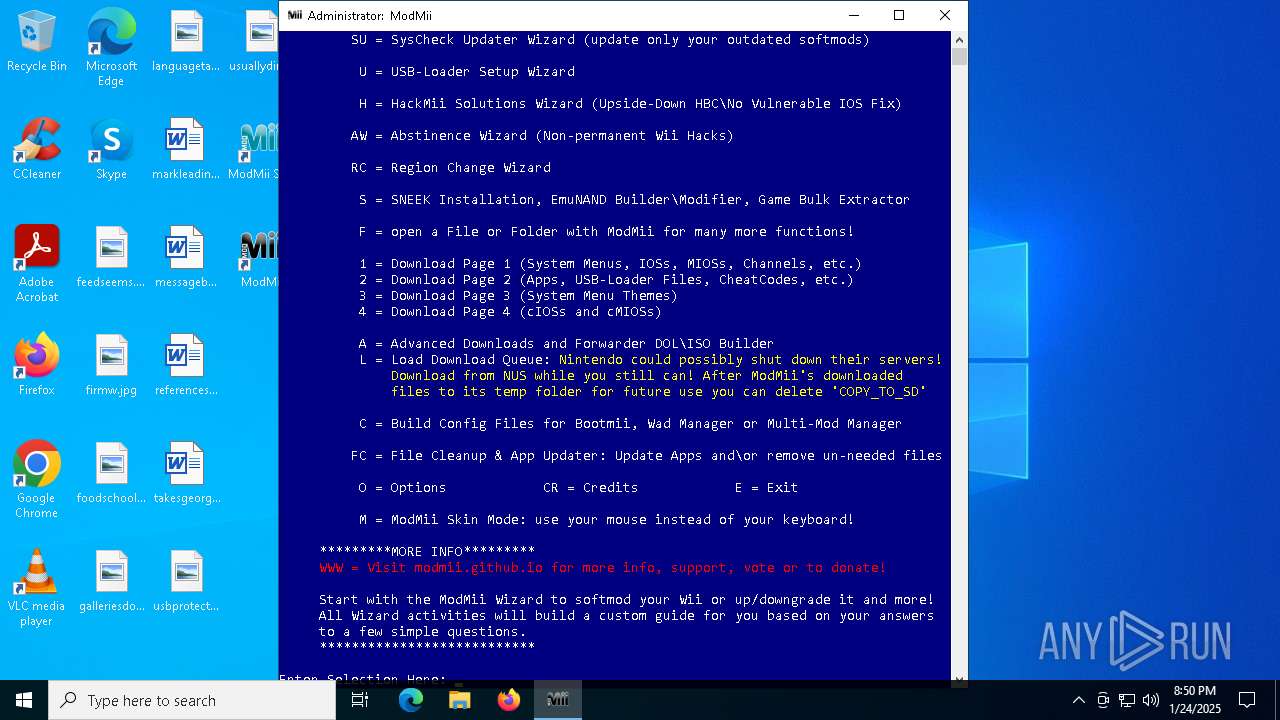
| File name: | ModMiiInstaller.exe |
| Full analysis: | https://app.any.run/tasks/28a9256c-7335-4640-b033-18b41ae89143 |
| Verdict: | Malicious activity |
| Analysis date: | January 24, 2025, 20:49:03 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, InstallShield self-extracting archive, 5 sections |
| MD5: | 8E7FCC949082919F7D15BF1E5A3E04DD |
| SHA1: | 69A6B8256D0748AF358112C34C39C7D5AB66345D |
| SHA256: | 8F7D0E34BA782B9AD03EDD95ECB35387E763ADFAC62ABECAA484EA7CA7A28A5B |
| SSDEEP: | 98304:NKaUakn0XI0Ve6xsyw//9HpXYsIzOb700oi+7Qlycb4Vvk9GcuDhiyM8JXXYxSFv:wRaLW/1TPz7RxXWfZPsiGfyD |
MALICIOUS
Detects Cygwin installation
- ModMiiInstaller.exe (PID: 2216)
SUSPICIOUS
There is functionality for taking screenshot (YARA)
- ModMiiInstaller.exe (PID: 2216)
Executable content was dropped or overwritten
- ModMiiInstaller.exe (PID: 2216)
- cmd.exe (PID: 3820)
The process creates files with name similar to system file names
- ModMiiInstaller.exe (PID: 2216)
Drops 7-zip archiver for unpacking
- ModMiiInstaller.exe (PID: 2216)
The process drops C-runtime libraries
- ModMiiInstaller.exe (PID: 2216)
Process drops legitimate windows executable
- ModMiiInstaller.exe (PID: 2216)
Creates a software uninstall entry
- ModMiiInstaller.exe (PID: 2216)
Reads security settings of Internet Explorer
- ModMiiInstaller.exe (PID: 2216)
Starts CMD.EXE for commands execution
- ModMii.exe (PID: 876)
Executing commands from a ".bat" file
- ModMii.exe (PID: 876)
Starts application with an unusual extension
- cmd.exe (PID: 3820)
Runs PING.EXE to delay simulation
- cmd.exe (PID: 3820)
INFO
Reads the computer name
- ModMiiInstaller.exe (PID: 2216)
- ModMii.exe (PID: 876)
- wget.exe (PID: 6316)
- wget.exe (PID: 6420)
Checks supported languages
- ModMiiInstaller.exe (PID: 2216)
- ModMii.exe (PID: 876)
- chcp.com (PID: 3544)
- sfk.exe (PID: 1864)
- sfk.exe (PID: 6796)
- wget.exe (PID: 6316)
- sfk.exe (PID: 6156)
- wget.exe (PID: 6420)
- sfk.exe (PID: 6700)
- sfk.exe (PID: 6724)
- sfk.exe (PID: 6748)
- sfk.exe (PID: 6772)
- nircmd.exe (PID: 732)
Create files in a temporary directory
- ModMiiInstaller.exe (PID: 2216)
The sample compiled with english language support
- ModMiiInstaller.exe (PID: 2216)
- cmd.exe (PID: 3820)
Creates files or folders in the user directory
- ModMiiInstaller.exe (PID: 2216)
Changes the display of characters in the console
- cmd.exe (PID: 3820)
NirSoft software is detected
- nircmd.exe (PID: 732)
Reads the machine GUID from the registry
- wget.exe (PID: 6316)
- wget.exe (PID: 6420)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | InstallShield setup (36.1) |
|---|---|---|
| .exe | | | Win32 Executable MS Visual C++ (generic) (26.2) |
| .exe | | | Win64 Executable (generic) (23.1) |
| .dll | | | Win32 Dynamic Link Library (generic) (5.5) |
| .exe | | | Win32 Executable (generic) (3.7) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2016:09:03 22:28:04+00:00 |
| ImageFileCharacteristics: | No relocs, Executable, No line numbers, No symbols, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 2.5 |
| CodeSize: | 201728 |
| InitializedDataSize: | 397312 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x1000 |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
Total processes
139
Monitored processes
19
Malicious processes
1
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 732 | support\nircmd.exe win setsize ititle "ModMii..." 0 0 705 820 | C:\ModMii\Support\nircmd.exe | — | cmd.exe | |||||||||||
User: admin Company: NirSoft Integrity Level: HIGH Description: NirCmd Exit code: 0 Version: 2.65 Modules
| |||||||||||||||
| 876 | "C:\ModMii\ModMii.exe" | C:\ModMii\ModMii.exe | — | ModMiiInstaller.exe | |||||||||||
User: admin Integrity Level: HIGH Description: ModMii Launcher Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
| 1620 | "C:\Users\admin\AppData\Local\Temp\ModMiiInstaller.exe" | C:\Users\admin\AppData\Local\Temp\ModMiiInstaller.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 3221226540 Modules
| |||||||||||||||
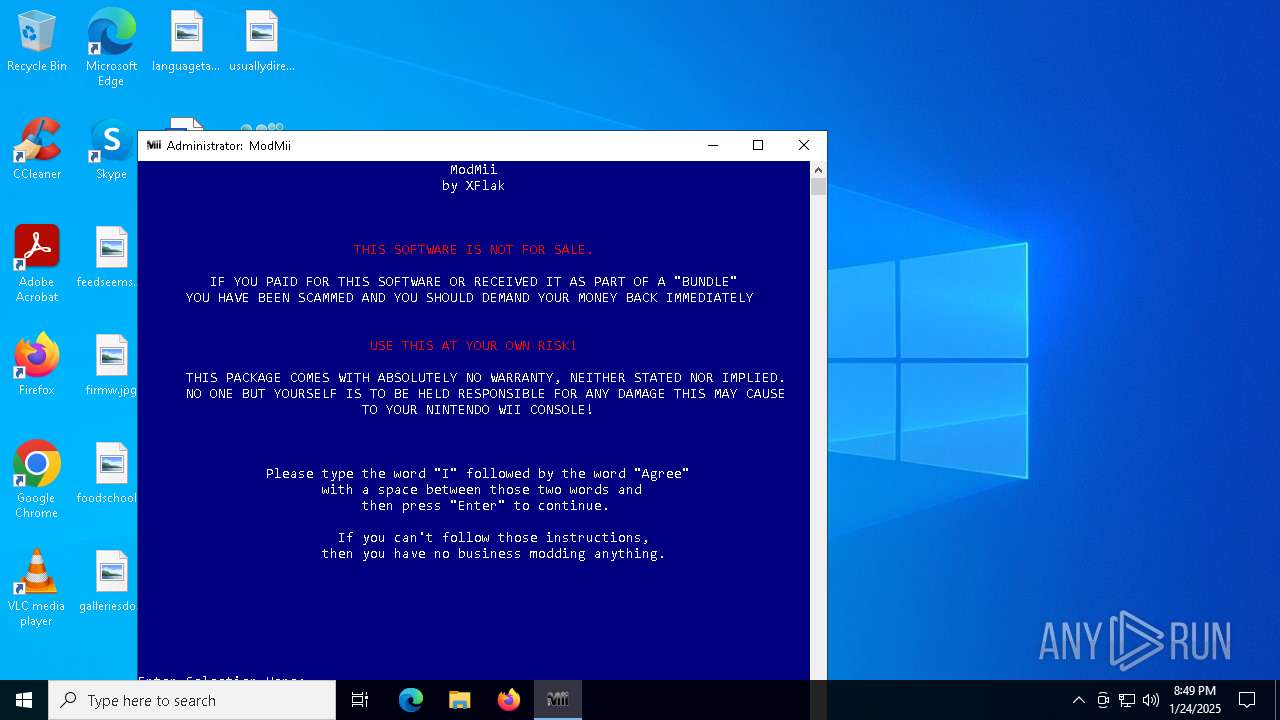
| 1864 | support\sfk echo -spat \x20 \x20 \x20 \x20 \x20 \x20 \x20 \x20 \x20 \x20 \x20 \x20 \x20 [Red] THIS SOFTWARE IS NOT FOR SALE. | C:\ModMii\Support\sfk.exe | — | cmd.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 2216 | "C:\Users\admin\AppData\Local\Temp\ModMiiInstaller.exe" | C:\Users\admin\AppData\Local\Temp\ModMiiInstaller.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 3544 | chcp 437 | C:\Windows\SysWOW64\chcp.com | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Change CodePage Utility Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3820 | C:\WINDOWS\system32\cmd.exe /c ""C:\ModMii/Support/ModMii.bat"" | C:\Windows\SysWOW64\cmd.exe | ModMii.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6092 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | ModMii.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6156 | support\sfk echo -spat \x20 \x20 \x20 \x20 \x20 \x20 \x20 \x20 \x20 \x20 \x20 \x20 \x20 \x20 [Red] USE THIS AT YOUR OWN RISK! | C:\ModMii\Support\sfk.exe | — | cmd.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 6316 | support\wget --no-check-certificate "https://raw.githubusercontent.com/modmii/modmii.github.io/master/temp/updater.bat" -O Updatetemp.bat | C:\ModMii\Support\wget.exe | cmd.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
Total events
4 942
Read events
4 934
Write events
8
Delete events
0
Modification events
| (PID) Process: | (2216) ModMiiInstaller.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Control\MediaResources\DirectSound\Speaker Configuration |
| Operation: | write | Name: | Speaker Configuration |
Value: 4 | |||
| (PID) Process: | (2216) ModMiiInstaller.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Uninstall\ModMii |
| Operation: | write | Name: | DisplayName |
Value: ModMii | |||
| (PID) Process: | (2216) ModMiiInstaller.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Uninstall\ModMii |
| Operation: | write | Name: | DisplayVersion |
Value: 7.0.3 | |||
| (PID) Process: | (2216) ModMiiInstaller.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Uninstall\ModMii |
| Operation: | write | Name: | HelpLink |
Value: https://modmii.github.io | |||
| (PID) Process: | (2216) ModMiiInstaller.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Uninstall\ModMii |
| Operation: | write | Name: | Publisher |
Value: XFlak | |||
| (PID) Process: | (2216) ModMiiInstaller.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Uninstall\ModMii |
| Operation: | write | Name: | UninstallString |
Value: C:\ModMii\Uninstall.exe | |||
| (PID) Process: | (2216) ModMiiInstaller.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Uninstall\ModMii |
| Operation: | write | Name: | DisplayIcon |
Value: C:\ModMii\Uninstall.exe | |||
Executable files
34
Suspicious files
193
Text files
132
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2216 | ModMiiInstaller.exe | C:\Users\admin\AppData\Local\Temp\IF{0B1A0639-7E55-49A1-9A96-9FCAFC348885}\SC.dat | text | |
MD5:32D59C7F497E32C97C8DB0D91329CBFB | SHA256:E194B8CA8BE257393EC00366E2EA805B194065E8580E8607EC64328618F31330 | |||
| 2216 | ModMiiInstaller.exe | C:\Users\admin\AppData\Local\Temp\IF{0B1A0639-7E55-49A1-9A96-9FCAFC348885}\Startmenu.dat | text | |
MD5:225D18F979D98CEB003F05BB80F88423 | SHA256:7EE7D12E55093A871A4E5F204D3C1EBC8804B521FE222312B4A0DC5312344910 | |||
| 2216 | ModMiiInstaller.exe | C:\Users\admin\AppData\Local\Temp\IF{0B1A0639-7E55-49A1-9A96-9FCAFC348885}\Default.ifl | text | |
MD5:DC51022CF78C9B519F2058983A773119 | SHA256:93E28A5125B4864773F53D1C5F87C1756EFA0C2D60D5C3FD6B34AA920080F568 | |||
| 2216 | ModMiiInstaller.exe | C:\Users\admin\AppData\Local\Temp\IF{0B1A0639-7E55-49A1-9A96-9FCAFC348885}\Desktop.dat | text | |
MD5:08F2AEB57B351C9DBBAF313B1533785A | SHA256:D22C5DF17381B1238B7D54CA281CBEC50983B23857E5B1D8871EFC09DA7AE9F4 | |||
| 2216 | ModMiiInstaller.exe | C:\Users\admin\AppData\Local\Temp\IF{0B1A0639-7E55-49A1-9A96-9FCAFC348885}\languages.dat | text | |
MD5:A6FB0111CBF1CBF35E3AFA2392E206BC | SHA256:59C8B5AE2D98ACAE9FDD97095A908230F28B2A5C4DFB27CEEB5814ADF906727B | |||
| 2216 | ModMiiInstaller.exe | C:\Users\admin\AppData\Local\Temp\IF{0B1A0639-7E55-49A1-9A96-9FCAFC348885}\OS.dat | text | |
MD5:3EA758C891F82C9941EF1BAA63EAD48B | SHA256:AB332F3596C8C9C99422EDC0202D4C5187B73A3D00AE235B9CE4ACDF54DE0452 | |||
| 2216 | ModMiiInstaller.exe | C:\Users\admin\AppData\Local\Temp\IF{0B1A0639-7E55-49A1-9A96-9FCAFC348885}\licence.rtf | text | |
MD5:F8EC4A4CD1BB53B3EB3121F8A5CC063B | SHA256:0DDD63075FB125D19D055B672073F455E439B32D65C85126B2D9B42B4F9DDB81 | |||
| 2216 | ModMiiInstaller.exe | C:\Users\admin\AppData\Local\Temp\IF{0B1A0639-7E55-49A1-9A96-9FCAFC348885}\English.ifl | text | |
MD5:DC51022CF78C9B519F2058983A773119 | SHA256:93E28A5125B4864773F53D1C5F87C1756EFA0C2D60D5C3FD6B34AA920080F568 | |||
| 2216 | ModMiiInstaller.exe | C:\Users\admin\AppData\Local\Temp\IF{0B1A0639-7E55-49A1-9A96-9FCAFC348885}\Image_Left.jpg | image | |
MD5:790E4312FE9C292B4B170C5FACD3C9F8 | SHA256:160DEB45C739E0178A542F8F512D6E3A8DF47259B434CAFF967CD1182E9A9142 | |||
| 2216 | ModMiiInstaller.exe | C:\ModMii\Uninstall.exe | executable | |
MD5:7AE89C6074B7CF3D03081EA6616D873B | SHA256:AE326F86AA8BBB88831B0339C820859467EF910DADED5B430DC88DA97D203772 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
7
TCP/UDP connections
34
DNS requests
18
Threats
1
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
4712 | MoUsoCoreWorker.exe | GET | 200 | 2.19.11.120:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
1176 | svchost.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
5064 | SearchApp.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
2148 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
2148 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
5592 | backgroundTaskHost.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
— | — | 2.23.227.208:443 | — | Ooredoo Q.S.C. | QA | unknown |
4712 | MoUsoCoreWorker.exe | 2.19.11.120:80 | crl.microsoft.com | Elisa Oyj | NL | whitelisted |
4712 | MoUsoCoreWorker.exe | 95.101.149.131:80 | www.microsoft.com | Akamai International B.V. | NL | whitelisted |
5064 | SearchApp.exe | 2.23.227.215:443 | — | Ooredoo Q.S.C. | QA | unknown |
5064 | SearchApp.exe | 2.23.77.188:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
1176 | svchost.exe | 40.126.32.76:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
1176 | svchost.exe | 2.23.77.188:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
1076 | svchost.exe | 184.28.89.167:443 | go.microsoft.com | AKAMAI-AS | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
login.live.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
arc.msn.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2192 | svchost.exe | Not Suspicious Traffic | INFO [ANY.RUN] Attempting to access raw user content on GitHub |