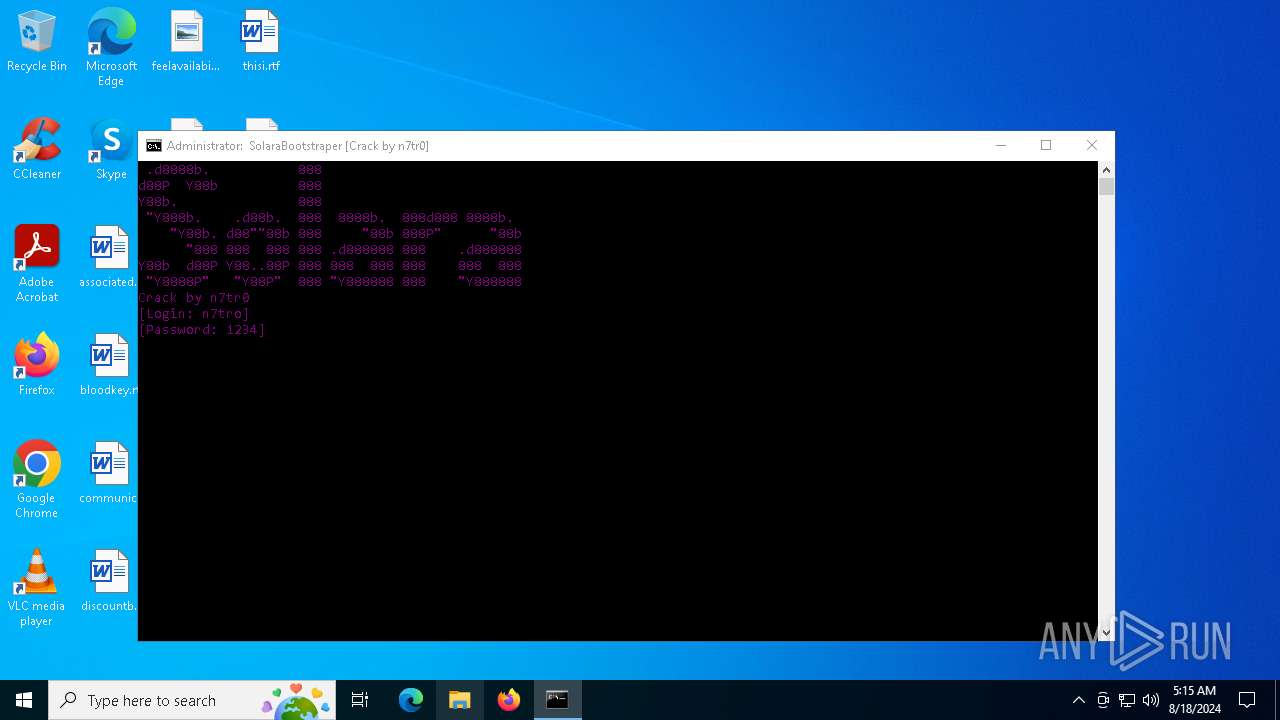
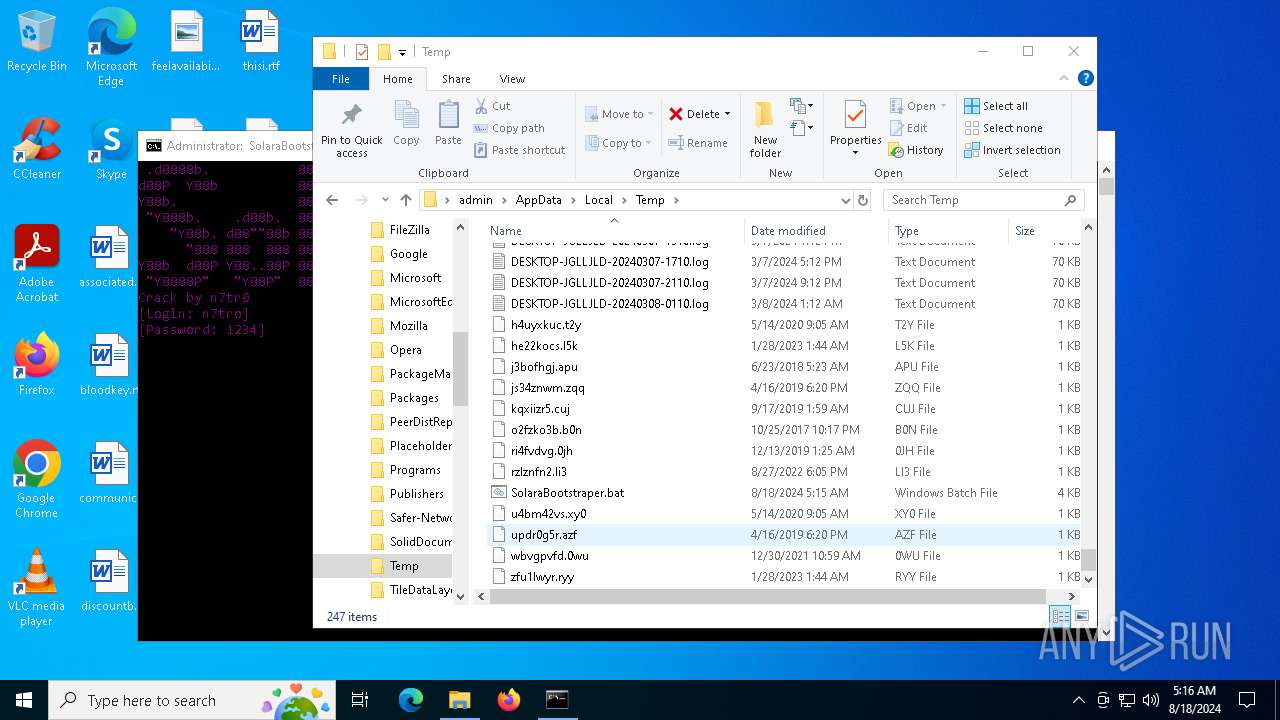
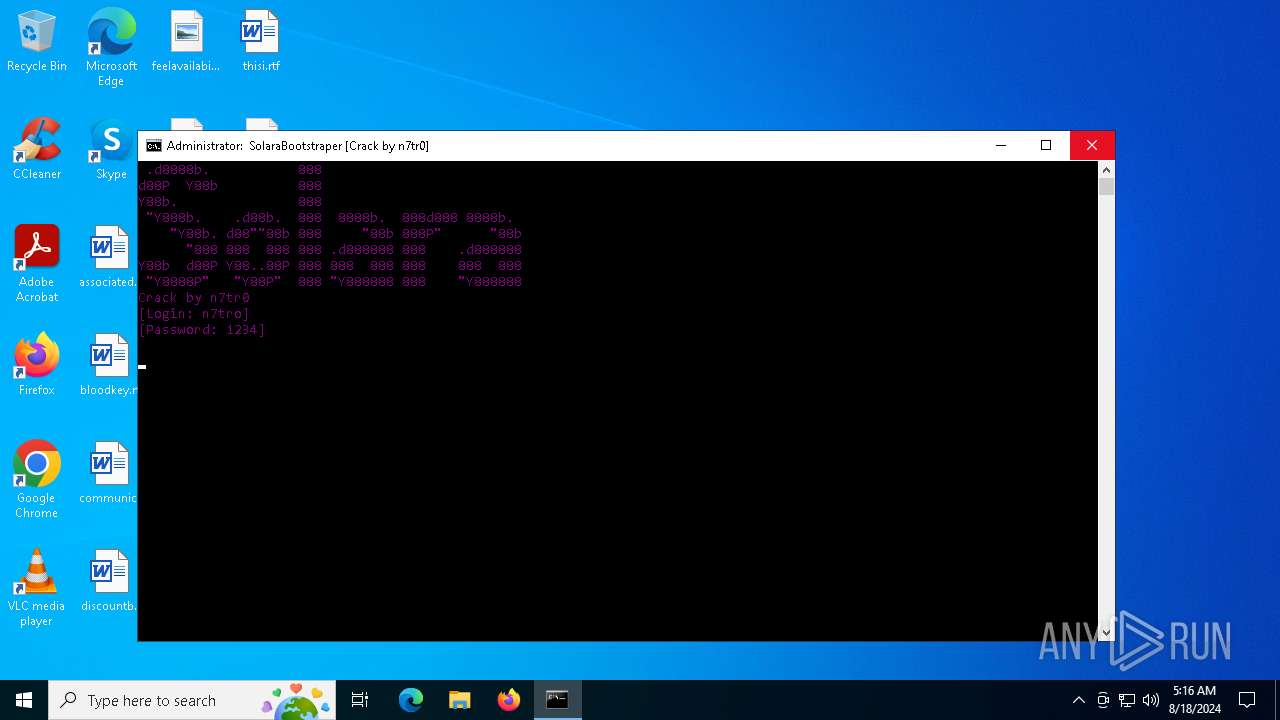
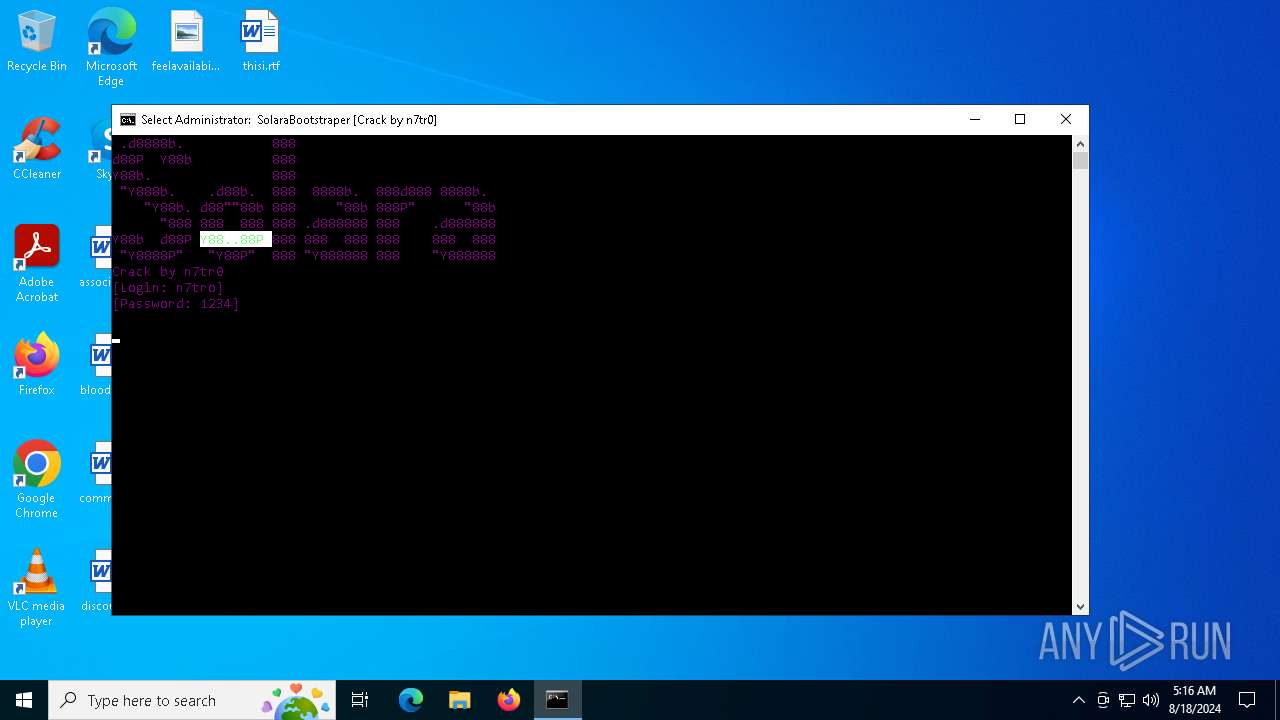
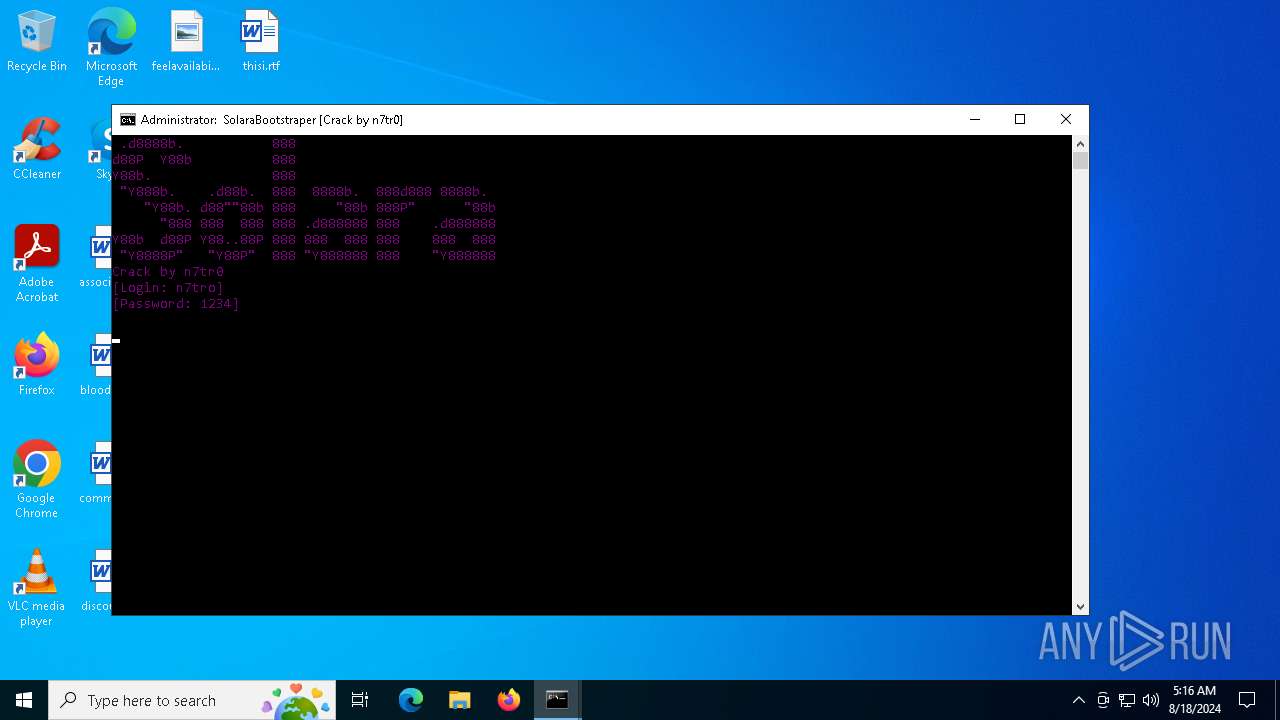
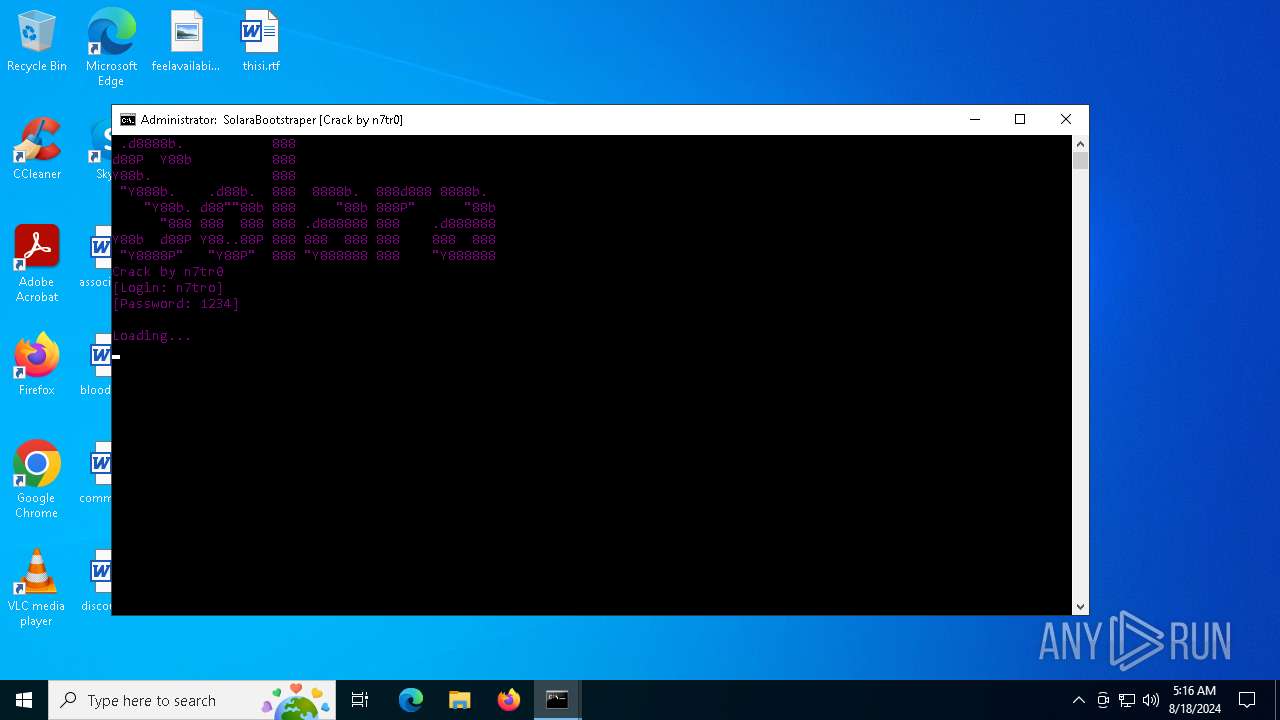
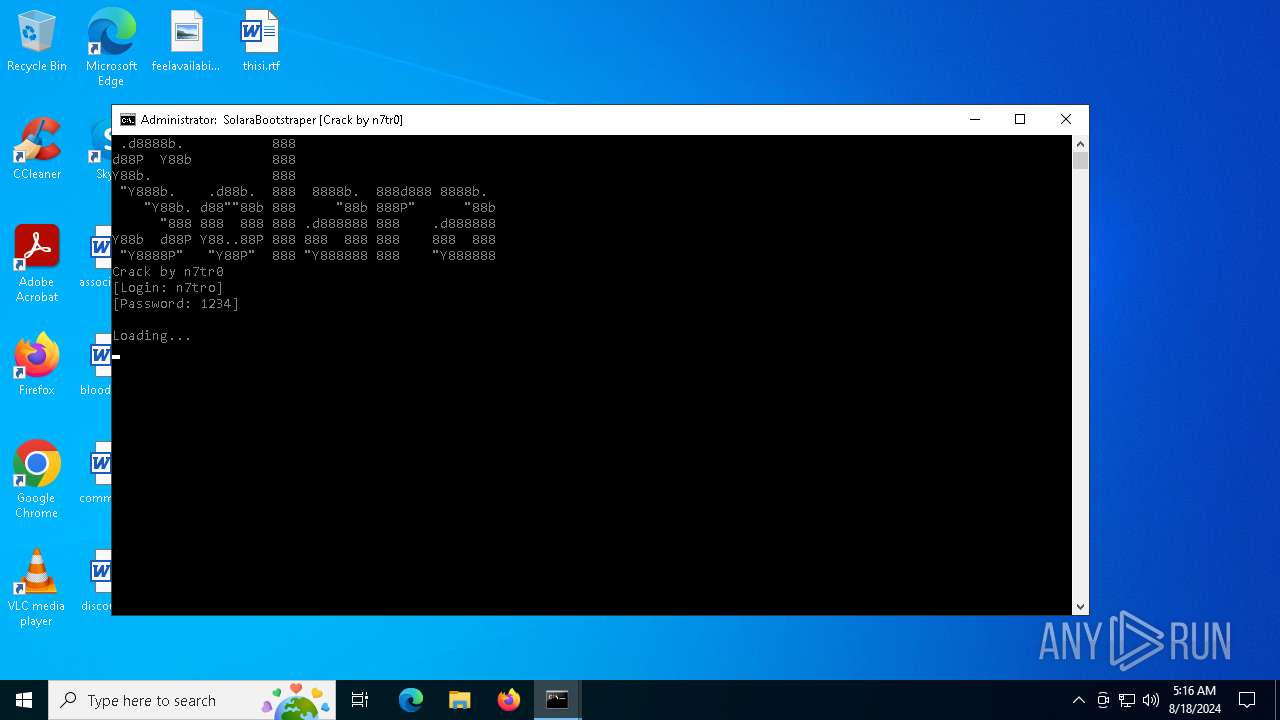
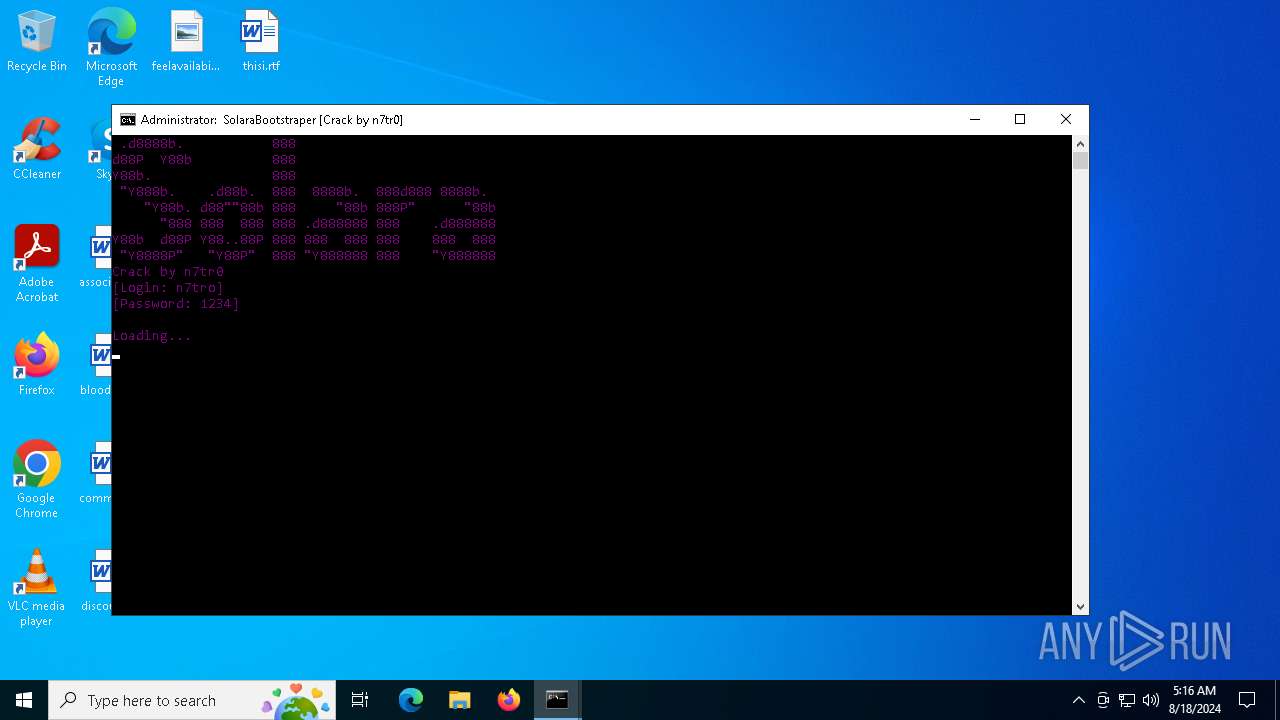
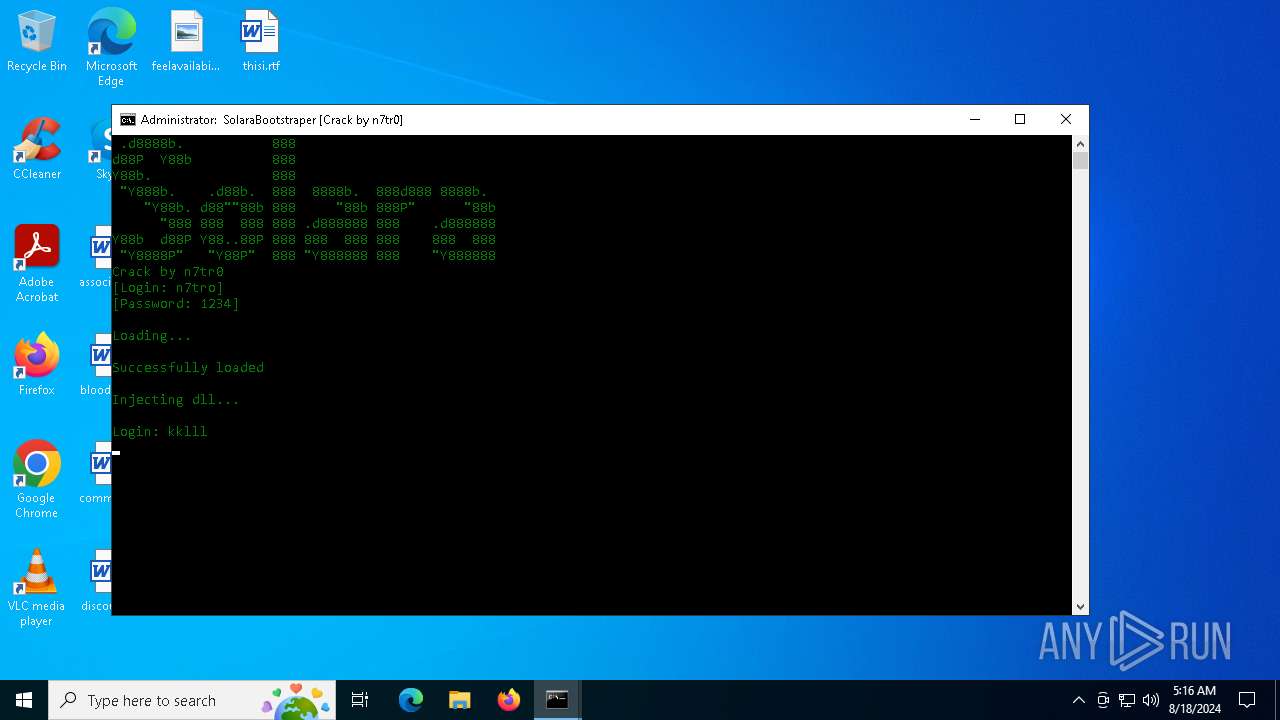
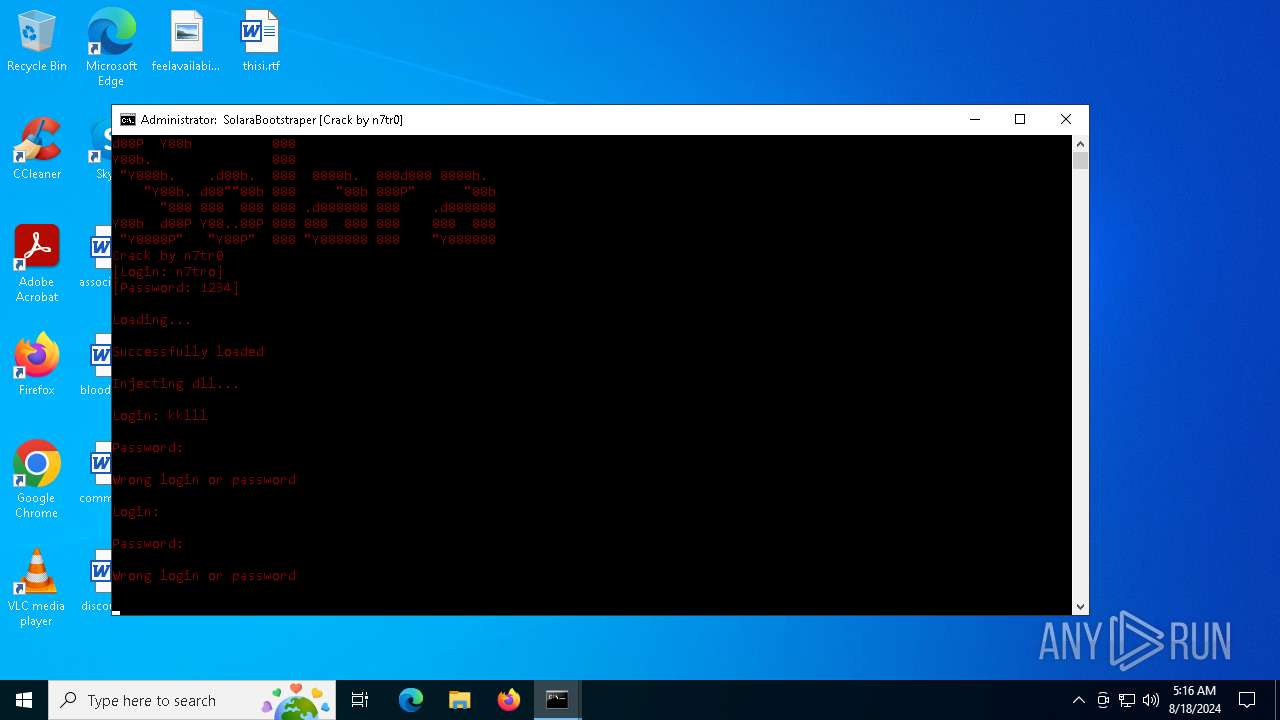
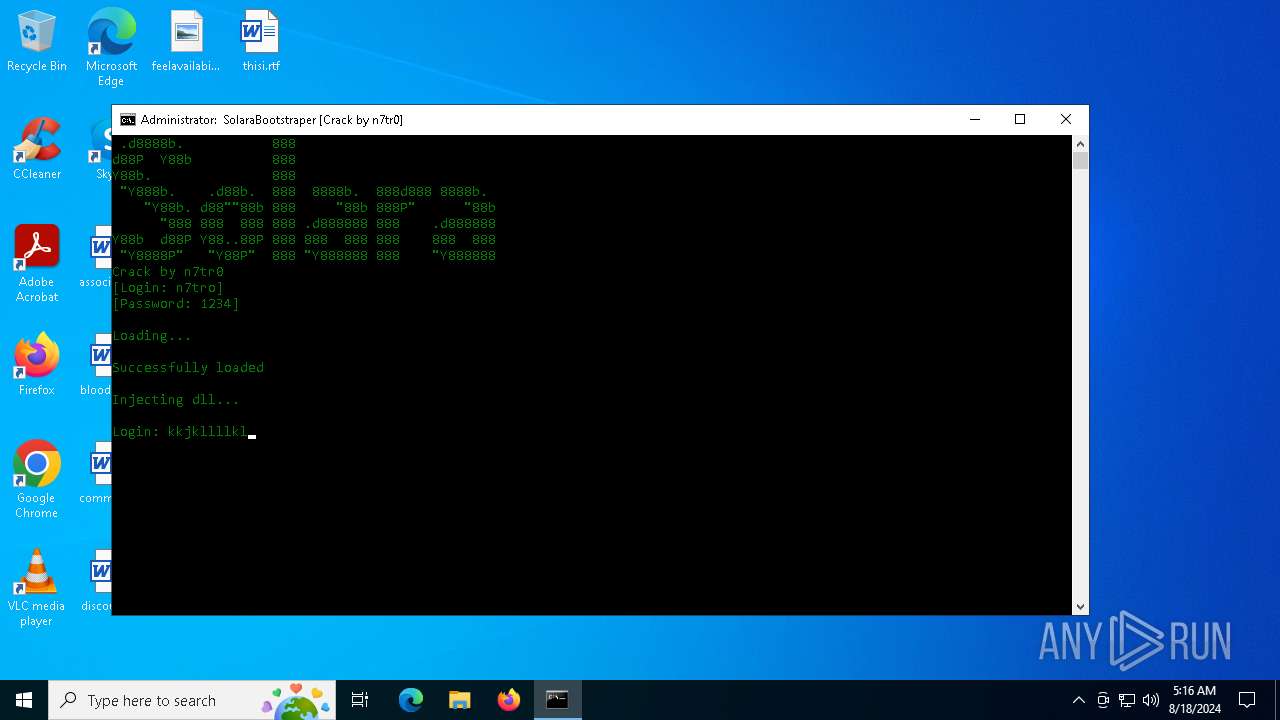
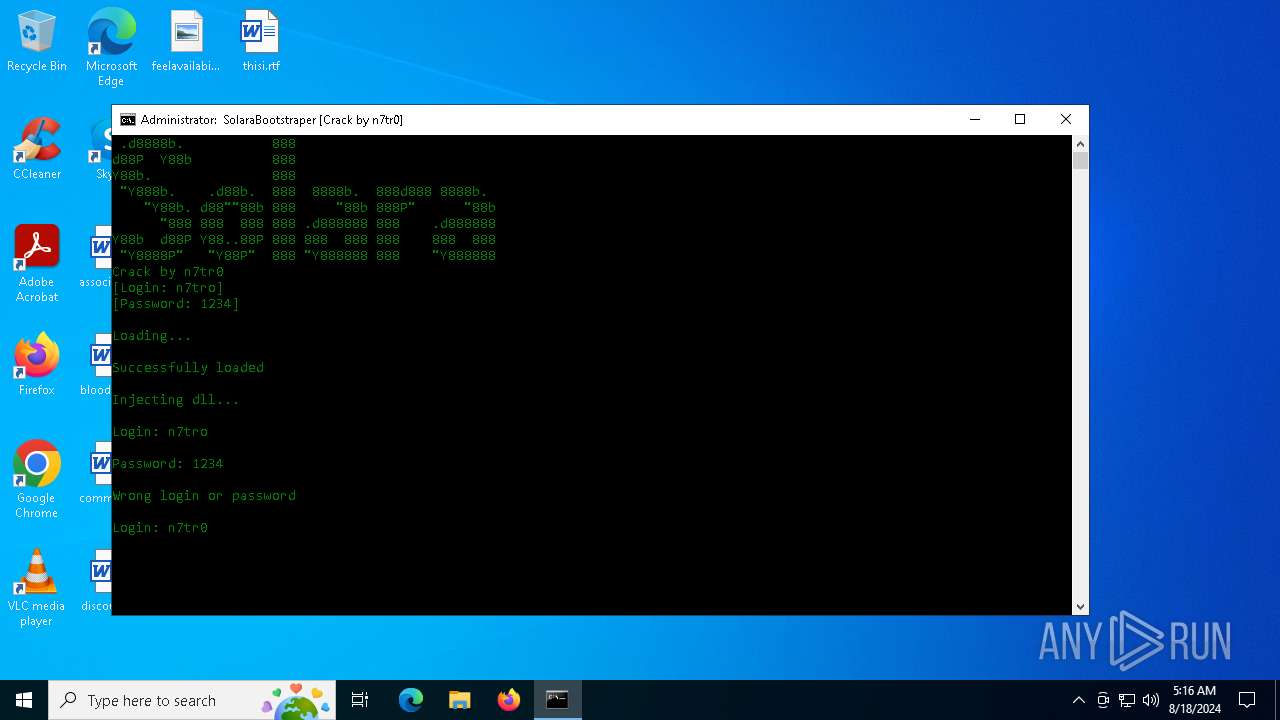
| File name: | SolaraExecutor.exe |
| Full analysis: | https://app.any.run/tasks/5194c327-b5f0-4e88-9899-2e50c8a5b7e9 |
| Verdict: | Malicious activity |
| Analysis date: | August 18, 2024, 05:15:11 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | MS-DOS executable PE32 executable (GUI) Intel 80386, for MS Windows, MZ for MS-DOS |
| MD5: | 1BF387365E4FE91DF1CF6DCBF39C0AE4 |
| SHA1: | 2939542B36D01952019A7F0B8ABEF750826B0F24 |
| SHA256: | 8F7929AF6E6FAD36D05B42ADD4B5023D8511ADCC8CF7C2323448C670BB6ABDCC |
| SSDEEP: | 6144:T0/1Thw5w4qjPRrf2VrRZHMrbLcPNYDTMN4oIYpwm3WjPXQ48xY5Ek/9t+N:GcPNYUN4ozwm34AVxa7o |
MALICIOUS
Bypass execution policy to execute commands
- powershell.exe (PID: 6272)
- powershell.exe (PID: 5116)
- powershell.exe (PID: 2580)
Changes powershell execution policy (Bypass)
- solaraexecutor.exe (PID: 6792)
- solaraexecutor.exe (PID: 6852)
- solaraexecutor.exe (PID: 1692)
Adds path to the Windows Defender exclusion list
- solaraexecutor.exe (PID: 6792)
- solaraexecutor.exe (PID: 6852)
- solaraexecutor.exe (PID: 1692)
Changes appearance of the Explorer extensions
- explorer.exe (PID: 4592)
- svchost.exe (PID: 2468)
Changes the autorun value in the registry
- explorer.exe (PID: 4592)
- svchost.exe (PID: 2468)
- solaraexecutor.exe (PID: 6792)
- solaraexecutor.exe (PID: 6852)
- solaraexecutor.exe (PID: 1692)
SUSPICIOUS
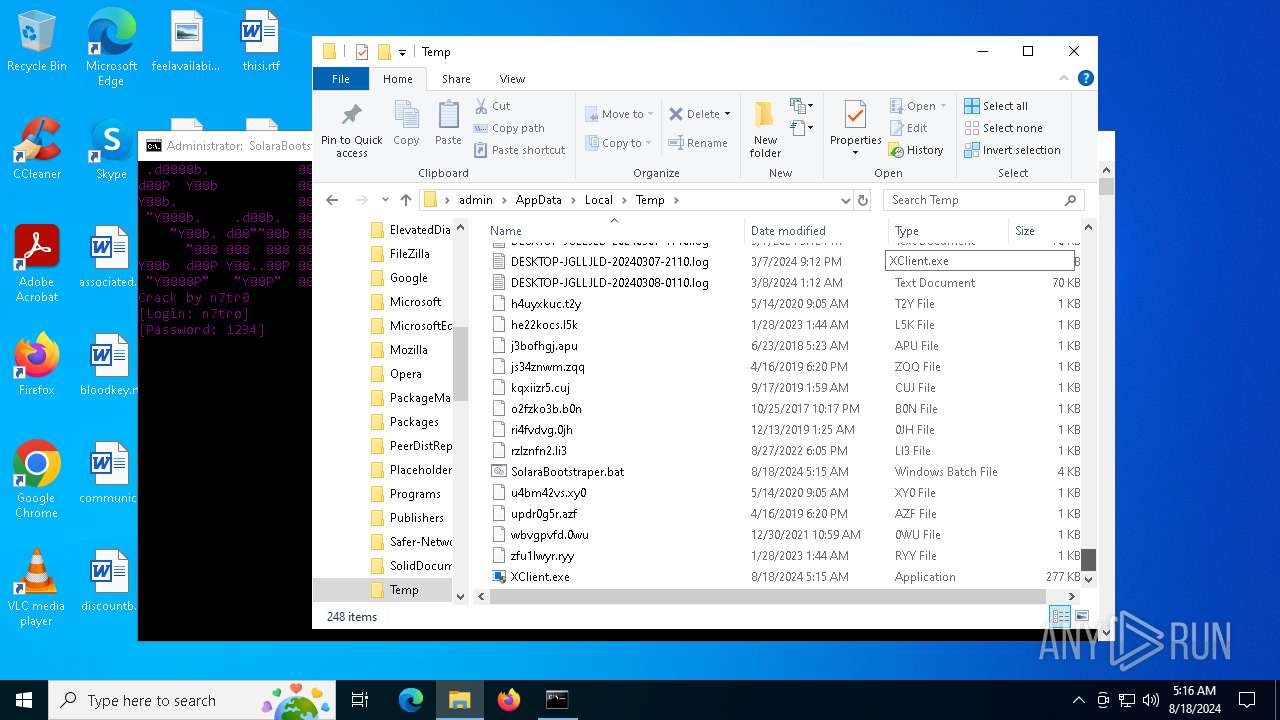
Drops the executable file immediately after the start
- SolaraExecutor.exe (PID: 6732)
- explorer.exe (PID: 4592)
- icsys.icn.exe (PID: 6284)
- spoolsv.exe (PID: 6040)
- solaraexecutor.exe (PID: 6792)
- svchost.exe (PID: 2468)
- SolaraExecutor.exe (PID: 4016)
- XClient.exe (PID: 6888)
- solaraexecutor.exe (PID: 6852)
- SolaraExecutor.exe (PID: 4192)
Reads the date of Windows installation
- solaraexecutor.exe (PID: 6792)
- solaraexecutor.exe (PID: 6852)
- solaraexecutor.exe (PID: 1692)
Starts itself from another location
- SolaraExecutor.exe (PID: 6732)
- icsys.icn.exe (PID: 6284)
- spoolsv.exe (PID: 6040)
- explorer.exe (PID: 4592)
- svchost.exe (PID: 2468)
- SolaraExecutor.exe (PID: 4016)
- icsys.icn.exe (PID: 3568)
- XClient.exe (PID: 6888)
- icsys.icn.exe (PID: 3904)
- SolaraExecutor.exe (PID: 4192)
- icsys.icn.exe (PID: 2392)
Script adds exclusion path to Windows Defender
- solaraexecutor.exe (PID: 6792)
- solaraexecutor.exe (PID: 6852)
- solaraexecutor.exe (PID: 1692)
The process creates files with name similar to system file names
- icsys.icn.exe (PID: 6284)
- spoolsv.exe (PID: 6040)
Starts POWERSHELL.EXE for commands execution
- solaraexecutor.exe (PID: 6792)
- solaraexecutor.exe (PID: 6852)
- solaraexecutor.exe (PID: 1692)
Executable content was dropped or overwritten
- icsys.icn.exe (PID: 6284)
- SolaraExecutor.exe (PID: 6732)
- spoolsv.exe (PID: 6040)
- explorer.exe (PID: 4592)
- solaraexecutor.exe (PID: 6792)
- svchost.exe (PID: 2468)
- SolaraExecutor.exe (PID: 4016)
- XClient.exe (PID: 6888)
- solaraexecutor.exe (PID: 6852)
- SolaraExecutor.exe (PID: 4192)
Executes application which crashes
- XClient.exe (PID: 2608)
- xclient.exe (PID: 6184)
- XClient.exe (PID: 4296)
- XClient.exe (PID: 6808)
Checks for external IP
- XClient.exe (PID: 2608)
- svchost.exe (PID: 2256)
- xclient.exe (PID: 6184)
- XClient.exe (PID: 6808)
- XClient.exe (PID: 4296)
Reads security settings of Internet Explorer
- svchost.exe (PID: 2468)
- solaraexecutor.exe (PID: 6852)
- solaraexecutor.exe (PID: 6792)
- solaraexecutor.exe (PID: 1692)
Executing commands from a ".bat" file
- solaraexecutor.exe (PID: 6792)
- solaraexecutor.exe (PID: 6852)
- solaraexecutor.exe (PID: 1692)
Starts CMD.EXE for commands execution
- solaraexecutor.exe (PID: 6792)
- solaraexecutor.exe (PID: 6852)
- solaraexecutor.exe (PID: 1692)
Starts application with an unusual extension
- SolaraExecutor.exe (PID: 4016)
- XClient.exe (PID: 6888)
- SolaraExecutor.exe (PID: 6732)
- SolaraExecutor.exe (PID: 4192)
- cmd.exe (PID: 1344)
- cmd.exe (PID: 6192)
Creates or modifies Windows services
- svchost.exe (PID: 2468)
INFO
Checks supported languages
- SolaraExecutor.exe (PID: 6732)
- solaraexecutor.exe (PID: 6792)
- icsys.icn.exe (PID: 6284)
- explorer.exe (PID: 4592)
- svchost.exe (PID: 2468)
- spoolsv.exe (PID: 4308)
- spoolsv.exe (PID: 6040)
- XClient.exe (PID: 2608)
- SolaraExecutor.exe (PID: 4016)
- solaraexecutor.exe (PID: 6852)
- XClient.exe (PID: 6888)
- icsys.icn.exe (PID: 3568)
- explorer.exe (PID: 4280)
- xclient.exe (PID: 6184)
- XClient.exe (PID: 1556)
- XClient.exe (PID: 252)
- XClient.exe (PID: 7116)
- XClient.exe (PID: 6300)
- XClient.exe (PID: 4296)
- SolaraExecutor.exe (PID: 4192)
- icsys.icn.exe (PID: 3904)
- explorer.exe (PID: 6028)
- icsys.icn.exe (PID: 2392)
- solaraexecutor.exe (PID: 1692)
- explorer.exe (PID: 3916)
- XClient.exe (PID: 6808)
- chcp.com (PID: 6856)
- chcp.com (PID: 6156)
Create files in a temporary directory
- SolaraExecutor.exe (PID: 6732)
- icsys.icn.exe (PID: 6284)
- explorer.exe (PID: 4592)
- spoolsv.exe (PID: 6040)
- svchost.exe (PID: 2468)
- spoolsv.exe (PID: 4308)
- solaraexecutor.exe (PID: 6792)
- SolaraExecutor.exe (PID: 4016)
- XClient.exe (PID: 6888)
- icsys.icn.exe (PID: 3568)
- explorer.exe (PID: 4280)
- XClient.exe (PID: 1556)
- XClient.exe (PID: 252)
- XClient.exe (PID: 7116)
- XClient.exe (PID: 6300)
- solaraexecutor.exe (PID: 6852)
- SolaraExecutor.exe (PID: 4192)
- explorer.exe (PID: 6028)
- icsys.icn.exe (PID: 2392)
- icsys.icn.exe (PID: 3904)
- explorer.exe (PID: 3916)
- solaraexecutor.exe (PID: 1692)
Process checks computer location settings
- solaraexecutor.exe (PID: 6792)
- solaraexecutor.exe (PID: 6852)
- solaraexecutor.exe (PID: 1692)
Reads the computer name
- solaraexecutor.exe (PID: 6792)
- svchost.exe (PID: 2468)
- XClient.exe (PID: 2608)
- solaraexecutor.exe (PID: 6852)
- xclient.exe (PID: 6184)
- XClient.exe (PID: 4296)
- solaraexecutor.exe (PID: 1692)
- XClient.exe (PID: 6808)
Checks if a key exists in the options dictionary (POWERSHELL)
- powershell.exe (PID: 6272)
- powershell.exe (PID: 5116)
- powershell.exe (PID: 2580)
Script raised an exception (POWERSHELL)
- powershell.exe (PID: 6272)
- powershell.exe (PID: 5116)
- powershell.exe (PID: 2580)
Reads the machine GUID from the registry
- solaraexecutor.exe (PID: 6792)
- XClient.exe (PID: 2608)
- xclient.exe (PID: 6184)
- solaraexecutor.exe (PID: 6852)
- XClient.exe (PID: 4296)
- solaraexecutor.exe (PID: 1692)
- XClient.exe (PID: 6808)
Reads Environment values
- XClient.exe (PID: 2608)
- xclient.exe (PID: 6184)
- XClient.exe (PID: 4296)
- XClient.exe (PID: 6808)
Disables trace logs
- XClient.exe (PID: 2608)
- xclient.exe (PID: 6184)
- XClient.exe (PID: 4296)
- XClient.exe (PID: 6808)
Checks proxy server information
- WerFault.exe (PID: 6268)
- XClient.exe (PID: 2608)
- xclient.exe (PID: 6184)
- WerFault.exe (PID: 1184)
- XClient.exe (PID: 4296)
- WerFault.exe (PID: 5940)
- XClient.exe (PID: 6808)
- WerFault.exe (PID: 3136)
Reads the software policy settings
- WerFault.exe (PID: 6268)
- WerFault.exe (PID: 1184)
- WerFault.exe (PID: 5940)
- WerFault.exe (PID: 3136)
Creates files or folders in the user directory
- WerFault.exe (PID: 6268)
- WerFault.exe (PID: 1184)
- WerFault.exe (PID: 5940)
- WerFault.exe (PID: 3136)
Manual execution by a user
- SolaraExecutor.exe (PID: 4016)
- SolaraExecutor.exe (PID: 4004)
- XClient.exe (PID: 7164)
- XClient.exe (PID: 6888)
- XClient.exe (PID: 5084)
- XClient.exe (PID: 252)
- XClient.exe (PID: 1556)
- XClient.exe (PID: 6568)
- XClient.exe (PID: 1120)
- XClient.exe (PID: 7116)
- XClient.exe (PID: 1964)
- XClient.exe (PID: 6300)
- SolaraExecutor.exe (PID: 4056)
- SolaraExecutor.exe (PID: 4192)
Changes the display of characters in the console
- chcp.com (PID: 6856)
- chcp.com (PID: 6156)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable (generic) (52.9) |
|---|---|---|
| .exe | | | Generic Win/DOS Executable (23.5) |
| .exe | | | DOS Executable Generic (23.5) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2013:04:01 07:08:22+00:00 |
| ImageFileCharacteristics: | No relocs, Executable, No line numbers, No symbols, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 6 |
| CodeSize: | 106496 |
| InitializedDataSize: | 69632 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x290c |
| OSVersion: | 4 |
| ImageVersion: | 1 |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 1.0.0.0 |
| ProductVersionNumber: | 1.0.0.0 |
| FileFlagsMask: | 0x0000 |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | English (U.S.) |
| CharacterSet: | Unicode |
| ProductName: | Project1 |
| FileVersion: | 1 |
| ProductVersion: | 1 |
| InternalName: | TJprojMain |
| OriginalFileName: | TJprojMain.exe |
Total processes
191
Monitored processes
54
Malicious processes
11
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 252 | "C:\Users\admin\Desktop\XClient.exe" | C:\Users\admin\Desktop\XClient.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Version: 1.00 Modules
| |||||||||||||||
| 1120 | "C:\Users\admin\Desktop\XClient.exe" | C:\Users\admin\Desktop\XClient.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 3221226540 Version: 1.00 Modules
| |||||||||||||||
| 1184 | C:\WINDOWS\system32\WerFault.exe -u -p 6184 -s 1788 | C:\Windows\System32\WerFault.exe | xclient.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Problem Reporting Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1248 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
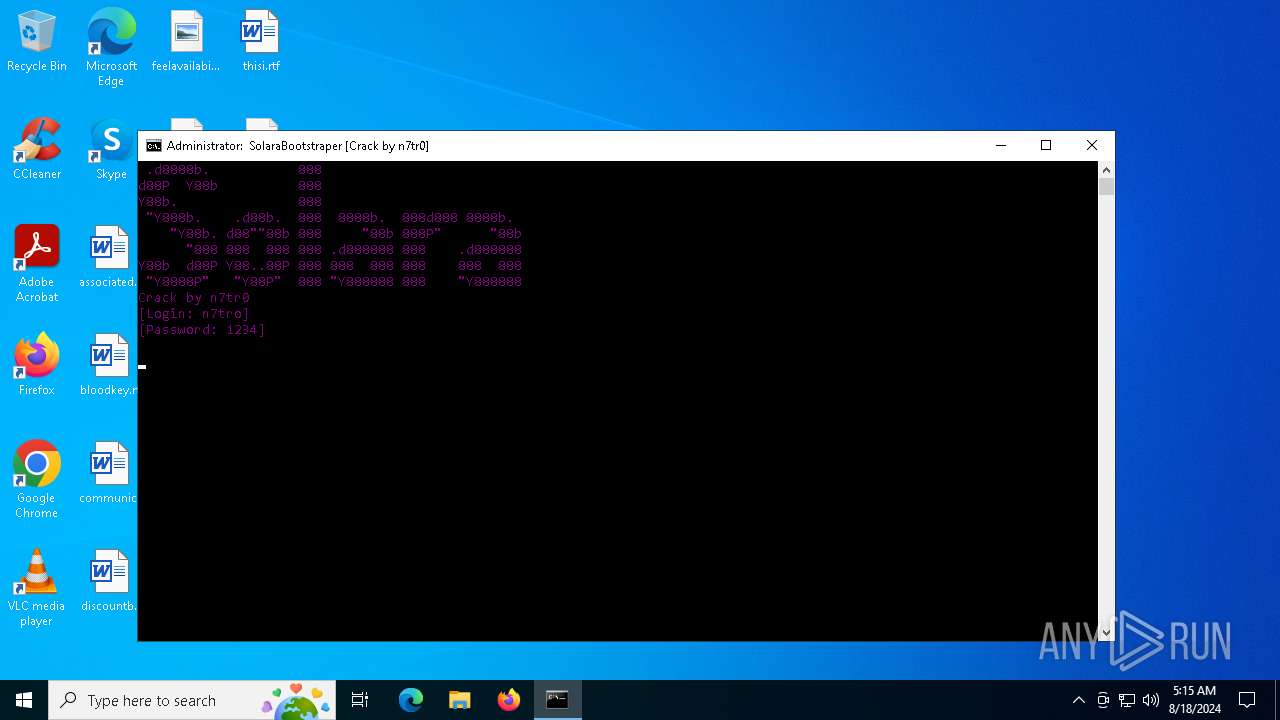
| 1344 | C:\WINDOWS\system32\cmd.exe /c ""C:\Users\admin\AppData\Local\Temp\SolaraBootstraper.bat" " | C:\Windows\System32\cmd.exe | — | solaraexecutor.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1556 | "C:\Users\admin\Desktop\XClient.exe" | C:\Users\admin\Desktop\XClient.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Version: 1.00 Modules
| |||||||||||||||
| 1692 | c:\users\admin\desktop\solaraexecutor.exe | C:\Users\admin\Desktop\solaraexecutor.exe | SolaraExecutor.exe | ||||||||||||
User: admin Integrity Level: HIGH Description: Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
| 1964 | "C:\Users\admin\Desktop\XClient.exe" | C:\Users\admin\Desktop\XClient.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 3221226540 Version: 1.00 Modules
| |||||||||||||||
| 2080 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2256 | C:\WINDOWS\system32\svchost.exe -k NetworkService -p -s Dnscache | C:\Windows\System32\svchost.exe | services.exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
55 573
Read events
55 409
Write events
138
Delete events
26
Modification events
| (PID) Process: | (6732) SolaraExecutor.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\VB and VBA Program Settings\Explorer\Process |
| Operation: | write | Name: | LO |
Value: 1 | |||
| (PID) Process: | (6792) solaraexecutor.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (6792) solaraexecutor.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (6792) solaraexecutor.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (6792) solaraexecutor.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
| (PID) Process: | (6284) icsys.icn.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\VB and VBA Program Settings\Explorer\Process |
| Operation: | write | Name: | LO |
Value: 1 | |||
| (PID) Process: | (4592) explorer.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\RunOnce |
| Operation: | write | Name: | Explorer |
Value: c:\windows\resources\themes\explorer.exe RO | |||
| (PID) Process: | (4592) explorer.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\RunOnce |
| Operation: | write | Name: | Svchost |
Value: c:\windows\resources\svchost.exe RO | |||
| (PID) Process: | (4592) explorer.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Run |
| Operation: | delete value | Name: | Explorer |
Value: | |||
| (PID) Process: | (4592) explorer.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Run |
| Operation: | delete value | Name: | Svchost |
Value: | |||
Executable files
14
Suspicious files
25
Text files
16
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6040 | spoolsv.exe | C:\Windows\Resources\svchost.exe | executable | |
MD5:8F39CF5BC76CE61ABCB219A5E5F2AC10 | SHA256:41A810ADAA0CFAB2D468D087A7C5A3411C41BA7B4625D43D7E47A9FFFBB3EEAE | |||
| 6268 | WerFault.exe | C:\ProgramData\Microsoft\Windows\WER\ReportArchive\AppCrash_XClient.exe_c44bfd071a2157ad61e7ca32427edddcbde79_aaa9738d_99904280-e8ef-4859-958b-98b7297e8bf8\Report.wer | — | |
MD5:— | SHA256:— | |||
| 6268 | WerFault.exe | C:\Users\admin\AppData\Local\CrashDumps\XClient.exe.2608.dmp | — | |
MD5:— | SHA256:— | |||
| 4308 | spoolsv.exe | C:\Users\admin\AppData\Local\Temp\~DF875C277EFF536C15.TMP | binary | |
MD5:57B4C6EE1FDB799B2F41F4A60586B1DB | SHA256:9FCAC341495EFBA7F9D0F59DDC1FFF60D9CBEF3011A02EC6E95D22CDE41F6DFA | |||
| 6284 | icsys.icn.exe | C:\Users\admin\AppData\Local\Temp\~DF7C0EC65074205B8A.TMP | binary | |
MD5:C575D1EE47D823BF2B2289454D962087 | SHA256:255328B2C6696E240B7E6D99CE5FF76ABB3E57D5D9AD485B211E3B71A714133D | |||
| 6272 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_2wldiyj4.gyu.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 6040 | spoolsv.exe | C:\Users\admin\AppData\Local\Temp\~DF10B7499D2FB496D0.TMP | binary | |
MD5:8B6C29CE33BBA8BE54EC9E3EC6F499DA | SHA256:6D70AB559C541F498BC9D746508FC0828DDB63B5BD70361FE1A0C67380402F61 | |||
| 6284 | icsys.icn.exe | C:\Windows\Resources\Themes\explorer.exe | executable | |
MD5:366A6190A4E9D1013A04B14D83C9F86A | SHA256:A8083B2967008B43AC5EC7F451CD162015B539A3BA8525FEF84D4E45B82010D7 | |||
| 6732 | SolaraExecutor.exe | C:\Windows\Resources\Themes\icsys.icn.exe | executable | |
MD5:C9D9CD368716F7273E2C3F4C3F9E9F24 | SHA256:666BB736F6E52A51F208C357FEEA44211D1E9CE0D0C818E5DA00CE657927C62E | |||
| 4592 | explorer.exe | C:\Windows\Resources\spoolsv.exe | executable | |
MD5:329D13CD335239172E8531D5050B31A8 | SHA256:28DCAA292C6CFBBB312C282CD0F3C6CD837A10A6FD5CCD7FE5006B58F5CF575A | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
7
TCP/UDP connections
37
DNS requests
19
Threats
6
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
6736 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
2208 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
6684 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
2608 | XClient.exe | GET | 200 | 208.95.112.1:80 | http://ip-api.com/line/?fields=hosting | unknown | — | — | shared |
6184 | xclient.exe | GET | 200 | 208.95.112.1:80 | http://ip-api.com/line/?fields=hosting | unknown | — | — | shared |
4296 | XClient.exe | GET | 200 | 208.95.112.1:80 | http://ip-api.com/line/?fields=hosting | unknown | — | — | shared |
6808 | XClient.exe | GET | 200 | 208.95.112.1:80 | http://ip-api.com/line/?fields=hosting | unknown | — | — | shared |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3508 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
3888 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1664 | RUXIMICS.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
— | — | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
3260 | svchost.exe | 40.113.110.67:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
2208 | svchost.exe | 40.126.32.134:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
2208 | svchost.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
6684 | backgroundTaskHost.exe | 20.103.156.88:443 | arc.msn.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | unknown |
6684 | backgroundTaskHost.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
arc.msn.com |
| whitelisted |
ip-api.com |
| shared |
watson.events.data.microsoft.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2608 | XClient.exe | Device Retrieving External IP Address Detected | ET POLICY External IP Lookup ip-api.com |
2256 | svchost.exe | Device Retrieving External IP Address Detected | ET INFO External IP Lookup Domain in DNS Lookup (ip-api .com) |
6184 | xclient.exe | Device Retrieving External IP Address Detected | ET POLICY External IP Lookup ip-api.com |
4296 | XClient.exe | Device Retrieving External IP Address Detected | ET POLICY External IP Lookup ip-api.com |
2256 | svchost.exe | Device Retrieving External IP Address Detected | ET INFO External IP Lookup Domain in DNS Lookup (ip-api .com) |
6808 | XClient.exe | Device Retrieving External IP Address Detected | ET POLICY External IP Lookup ip-api.com |
Process | Message |
|---|---|
XClient.exe | CLR: Managed code called FailFast without specifying a reason.
|
xclient.exe | CLR: Managed code called FailFast without specifying a reason.
|
XClient.exe | CLR: Managed code called FailFast without specifying a reason.
|
XClient.exe | CLR: Managed code called FailFast without specifying a reason.
|