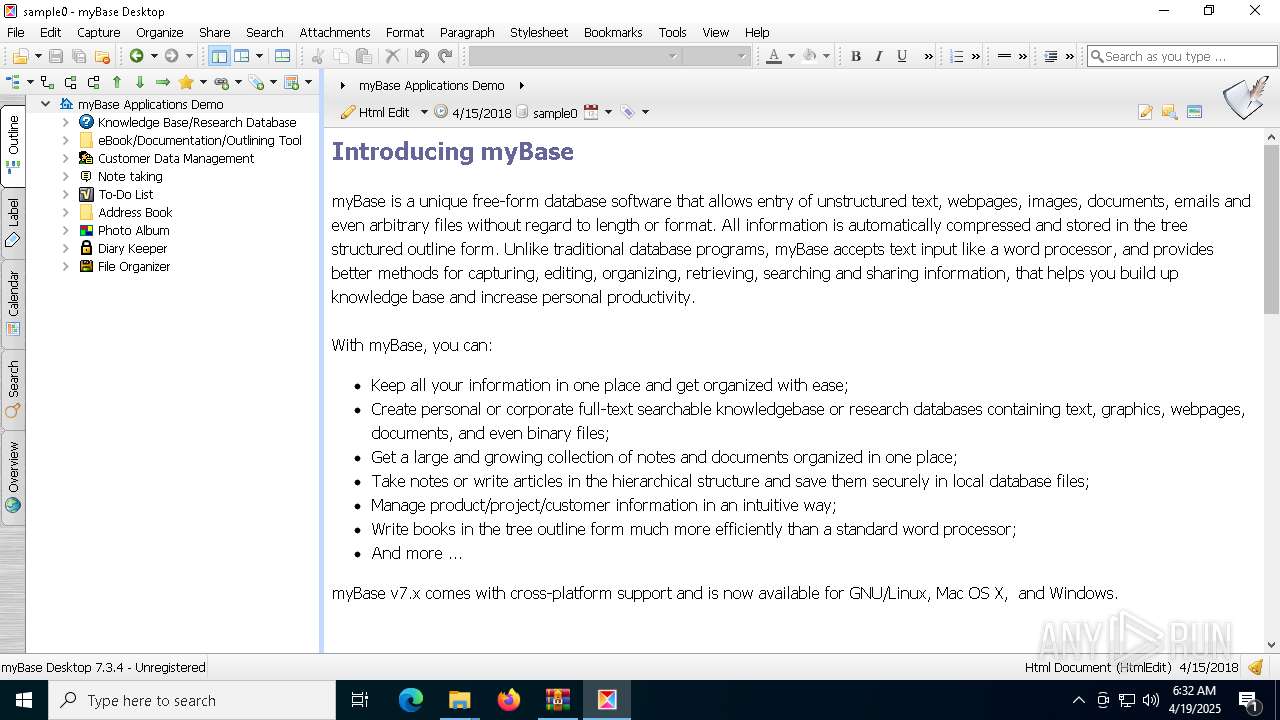
| File name: | myBase Desktop 7.3.4 [FileCR].zip |
| Full analysis: | https://app.any.run/tasks/d9075668-104d-4c26-89ae-3949d51a5461 |
| Verdict: | Malicious activity |
| Analysis date: | April 19, 2025, 06:27:51 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v1.0 to extract, compression method=store |
| MD5: | FCC99B64A550542BA3EF1F603925FA93 |
| SHA1: | 171BF85BD0B795912AA91350F7547D5471EE93CE |
| SHA256: | 8F520AE7779417509EB85B546FD9604CD9D6465E18737EED8619AA40167EDCA7 |
| SSDEEP: | 196608:UzN7go385VFIlfa8sM1jHv0FA5hIQGAPIk:8gos53IlS8sM115hfHPIk |
MALICIOUS
Generic archive extractor
- WinRAR.exe (PID: 896)
SUSPICIOUS
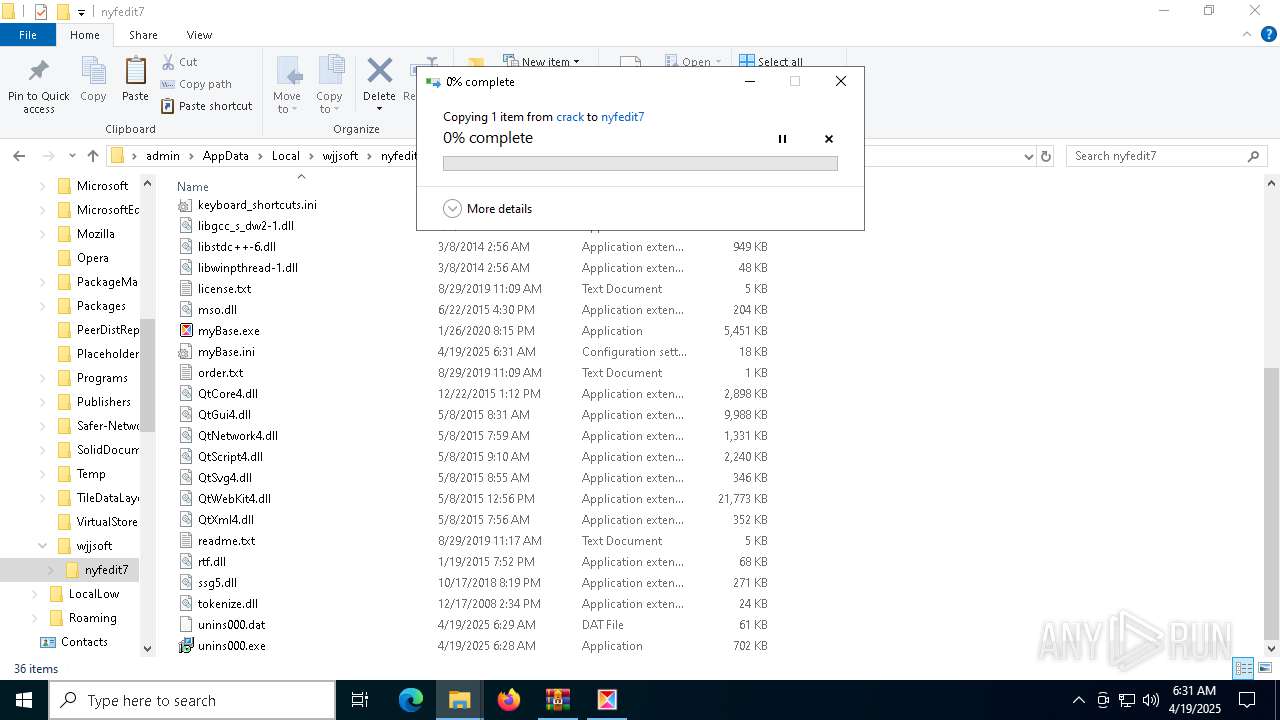
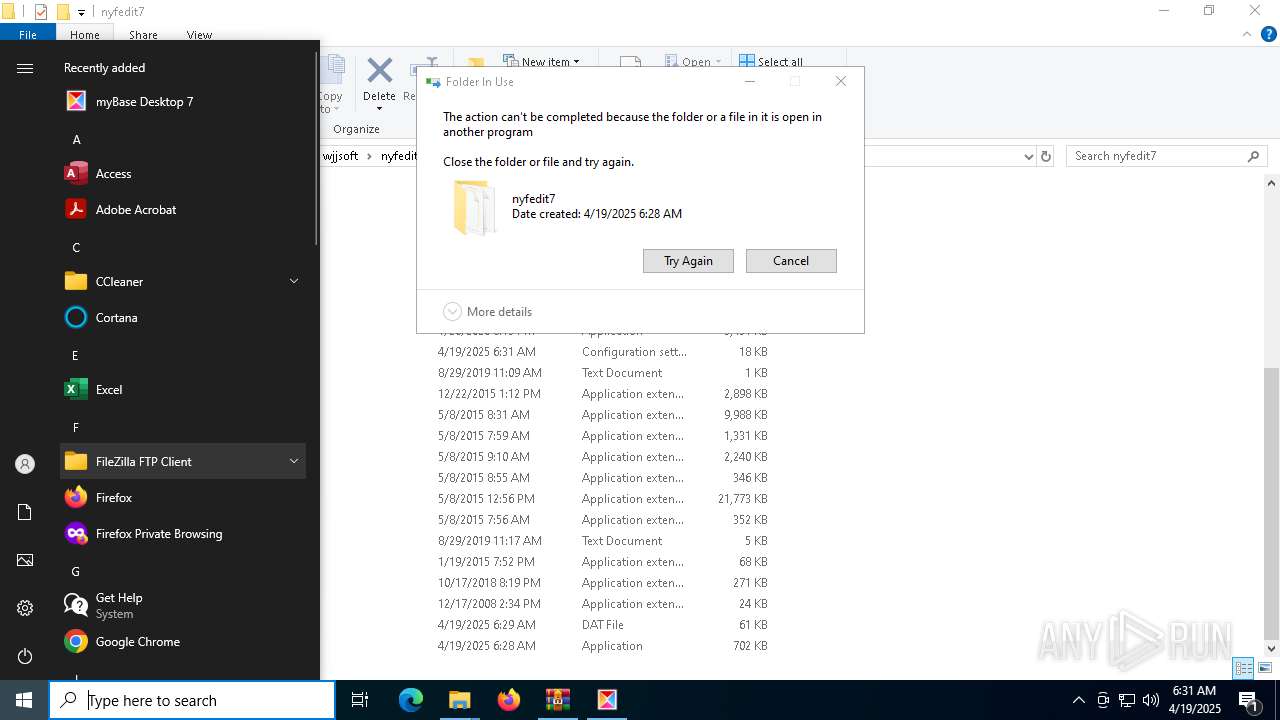
Executable content was dropped or overwritten
- myBase-Desktop-Ver734-Setup.exe (PID: 6272)
- myBase-Desktop-Ver734-Setup.exe (PID: 1184)
- myBase-Desktop-Ver734-Setup.tmp (PID: 6644)
Reads security settings of Internet Explorer
- WinRAR.exe (PID: 896)
- myBase-Desktop-Ver734-Setup.tmp (PID: 4172)
- ShellExperienceHost.exe (PID: 5084)
Process drops legitimate windows executable
- myBase-Desktop-Ver734-Setup.tmp (PID: 6644)
Reads the Windows owner or organization settings
- myBase-Desktop-Ver734-Setup.tmp (PID: 6644)
There is functionality for taking screenshot (YARA)
- myBase.exe (PID: 6852)
INFO
The sample compiled with english language support
- WinRAR.exe (PID: 896)
- myBase-Desktop-Ver734-Setup.tmp (PID: 6644)
Checks supported languages
- myBase-Desktop-Ver734-Setup.exe (PID: 6272)
- myBase-Desktop-Ver734-Setup.tmp (PID: 4172)
- myBase-Desktop-Ver734-Setup.exe (PID: 1184)
- myBase-Desktop-Ver734-Setup.tmp (PID: 6644)
- myBase.exe (PID: 6388)
- myBase.exe (PID: 1568)
- ShellExperienceHost.exe (PID: 5084)
- myBase.exe (PID: 4108)
- myBase.exe (PID: 6852)
Create files in a temporary directory
- myBase-Desktop-Ver734-Setup.exe (PID: 6272)
- myBase-Desktop-Ver734-Setup.exe (PID: 1184)
- myBase-Desktop-Ver734-Setup.tmp (PID: 6644)
- myBase.exe (PID: 6388)
- myBase.exe (PID: 6852)
- myBase.exe (PID: 1568)
- myBase.exe (PID: 4108)
Reads the computer name
- myBase-Desktop-Ver734-Setup.tmp (PID: 4172)
- myBase-Desktop-Ver734-Setup.tmp (PID: 6644)
- myBase.exe (PID: 6388)
- myBase.exe (PID: 6852)
- myBase.exe (PID: 1568)
- ShellExperienceHost.exe (PID: 5084)
- myBase.exe (PID: 4108)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 896)
Process checks computer location settings
- myBase-Desktop-Ver734-Setup.tmp (PID: 4172)
Detects InnoSetup installer (YARA)
- myBase-Desktop-Ver734-Setup.exe (PID: 6272)
- myBase-Desktop-Ver734-Setup.tmp (PID: 4172)
- myBase-Desktop-Ver734-Setup.exe (PID: 1184)
- myBase-Desktop-Ver734-Setup.tmp (PID: 6644)
Compiled with Borland Delphi (YARA)
- myBase-Desktop-Ver734-Setup.tmp (PID: 4172)
- myBase-Desktop-Ver734-Setup.tmp (PID: 6644)
Creates files or folders in the user directory
- myBase-Desktop-Ver734-Setup.tmp (PID: 6644)
- myBase.exe (PID: 6388)
Creates a software uninstall entry
- myBase-Desktop-Ver734-Setup.tmp (PID: 6644)
Reads the software policy settings
- slui.exe (PID: 4380)
Creates files in the program directory
- myBase-Desktop-Ver734-Setup.tmp (PID: 6644)
Checks proxy server information
- slui.exe (PID: 4380)
Manual execution by a user
- myBase.exe (PID: 6388)
- myBase.exe (PID: 1568)
- myBase.exe (PID: 4108)
- myBase.exe (PID: 6852)
Reads the machine GUID from the registry
- myBase.exe (PID: 6852)
- myBase.exe (PID: 1568)
- myBase.exe (PID: 6388)
- myBase.exe (PID: 4108)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 10 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | None |
| ZipModifyDate: | 2020:08:21 17:57:56 |
| ZipCRC: | 0x00000000 |
| ZipCompressedSize: | - |
| ZipUncompressedSize: | - |
| ZipFileName: | myBase Desktop 7.3.4 [FileCR]/ |
Total processes
149
Monitored processes
12
Malicious processes
1
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 896 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\myBase Desktop 7.3.4 [FileCR].zip" | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Version: 5.91.0 Modules
| |||||||||||||||
| 1012 | C:\WINDOWS\System32\rundll32.exe C:\WINDOWS\System32\shell32.dll,SHCreateLocalServerRunDll {9aa46009-3ce0-458a-a354-715610a075e6} -Embedding | C:\Windows\System32\rundll32.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
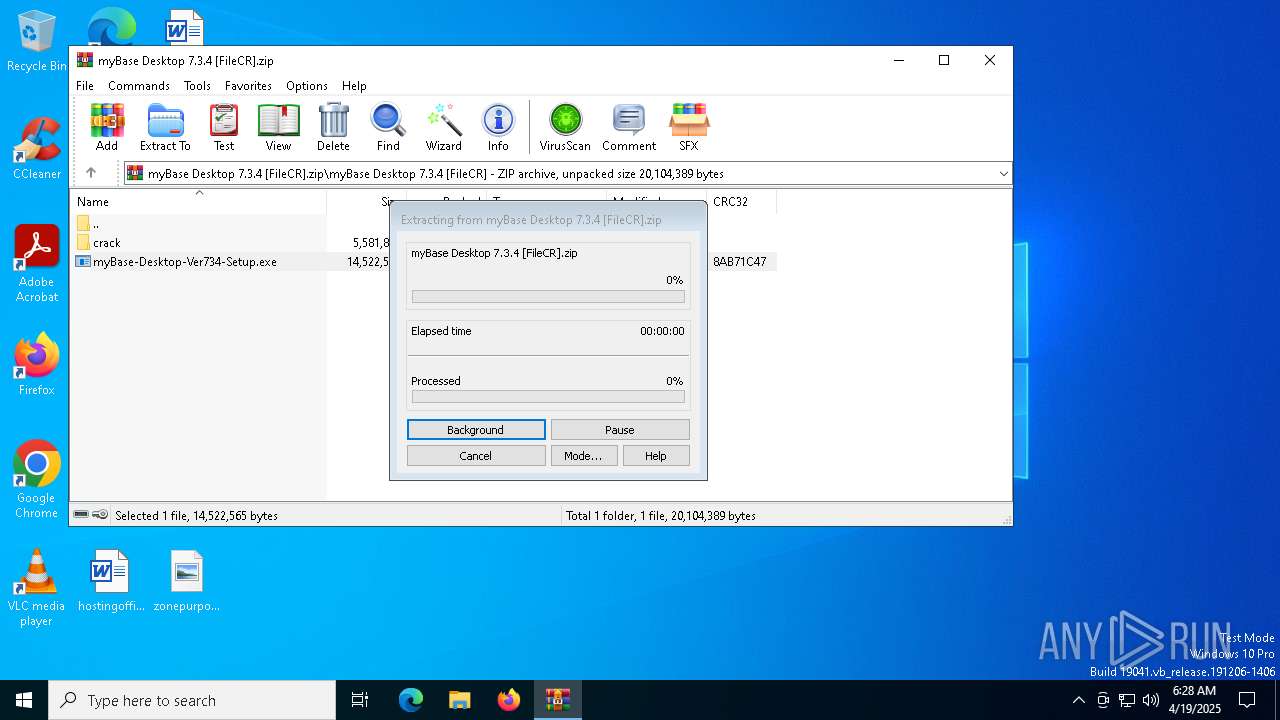
| 1184 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa896.39371\myBase Desktop 7.3.4 [FileCR]\myBase-Desktop-Ver734-Setup.exe" /SPAWNWND=$3026A /NOTIFYWND=$3025A | C:\Users\admin\AppData\Local\Temp\Rar$EXa896.39371\myBase Desktop 7.3.4 [FileCR]\myBase-Desktop-Ver734-Setup.exe | myBase-Desktop-Ver734-Setup.tmp | ||||||||||||
User: admin Company: Wjj Software Integrity Level: HIGH Description: myBase Desktop 7 Setup Exit code: 0 Version: 7.3.4 Modules
| |||||||||||||||
| 1568 | "C:\Users\admin\AppData\Local\wjjsoft\nyfedit7\myBase.exe" | C:\Users\admin\AppData\Local\wjjsoft\nyfedit7\myBase.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 4108 | "C:\Users\admin\AppData\Local\wjjsoft\nyfedit7\myBase.exe" | C:\Users\admin\AppData\Local\wjjsoft\nyfedit7\myBase.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Modules
| |||||||||||||||
| 4172 | "C:\Users\admin\AppData\Local\Temp\is-NLQ0S.tmp\myBase-Desktop-Ver734-Setup.tmp" /SL5="$3025A,14232458,56832,C:\Users\admin\AppData\Local\Temp\Rar$EXa896.39371\myBase Desktop 7.3.4 [FileCR]\myBase-Desktop-Ver734-Setup.exe" | C:\Users\admin\AppData\Local\Temp\is-NLQ0S.tmp\myBase-Desktop-Ver734-Setup.tmp | — | myBase-Desktop-Ver734-Setup.exe | |||||||||||
User: admin Integrity Level: MEDIUM Description: Setup/Uninstall Exit code: 0 Version: 51.52.0.0 Modules
| |||||||||||||||
| 4380 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5084 | "C:\WINDOWS\SystemApps\ShellExperienceHost_cw5n1h2txyewy\ShellExperienceHost.exe" -ServerName:App.AppXtk181tbxbce2qsex02s8tw7hfxa9xb3t.mca | C:\Windows\SystemApps\ShellExperienceHost_cw5n1h2txyewy\ShellExperienceHost.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Shell Experience Host Version: 10.0.19041.3758 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6272 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa896.39371\myBase Desktop 7.3.4 [FileCR]\myBase-Desktop-Ver734-Setup.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXa896.39371\myBase Desktop 7.3.4 [FileCR]\myBase-Desktop-Ver734-Setup.exe | WinRAR.exe | ||||||||||||
User: admin Company: Wjj Software Integrity Level: MEDIUM Description: myBase Desktop 7 Setup Exit code: 0 Version: 7.3.4 Modules
| |||||||||||||||
| 6388 | "C:\Users\admin\AppData\Local\wjjsoft\nyfedit7\myBase.exe" | C:\Users\admin\AppData\Local\wjjsoft\nyfedit7\myBase.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
Total events
7 121
Read events
7 067
Write events
54
Delete events
0
Modification events
| (PID) Process: | (896) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (896) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (896) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (896) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\myBase Desktop 7.3.4 [FileCR].zip | |||
| (PID) Process: | (896) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (896) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (896) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (896) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (6644) myBase-Desktop-Ver734-Setup.tmp | Key: | HKEY_CURRENT_USER\SOFTWARE\WJJSOFT\NYFEDIT7 |
| Operation: | write | Name: | AppSetupPath |
Value: C:\Users\admin\AppData\Local\wjjsoft\nyfedit7 | |||
| (PID) Process: | (6644) myBase-Desktop-Ver734-Setup.tmp | Key: | HKEY_CURRENT_USER\SOFTWARE\WJJSOFT\NYFEDIT7 |
| Operation: | write | Name: | SetupSrcExe |
Value: C:\Users\admin\AppData\Local\Temp\Rar$EXa896.39371\myBase Desktop 7.3.4 [FileCR]\myBase-Desktop-Ver734-Setup.exe | |||
Executable files
57
Suspicious files
36
Text files
1 239
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6272 | myBase-Desktop-Ver734-Setup.exe | C:\Users\admin\AppData\Local\Temp\is-NLQ0S.tmp\myBase-Desktop-Ver734-Setup.tmp | executable | |
MD5:A2C4D52C66B4B399FACADB8CC8386745 | SHA256:6C0465CE64C07E729C399A338705941D77727C7D089430957DF3E91A416E9D2A | |||
| 896 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa896.39371\myBase Desktop 7.3.4 [FileCR]\myBase-Desktop-Ver734-Setup.exe | executable | |
MD5:32CA1A46724BF77235C39C53015F9626 | SHA256:DC7D5EDF5B7919D18EF4D8C8F05B00D8AB49E71B96917FAE296BF34D4A459072 | |||
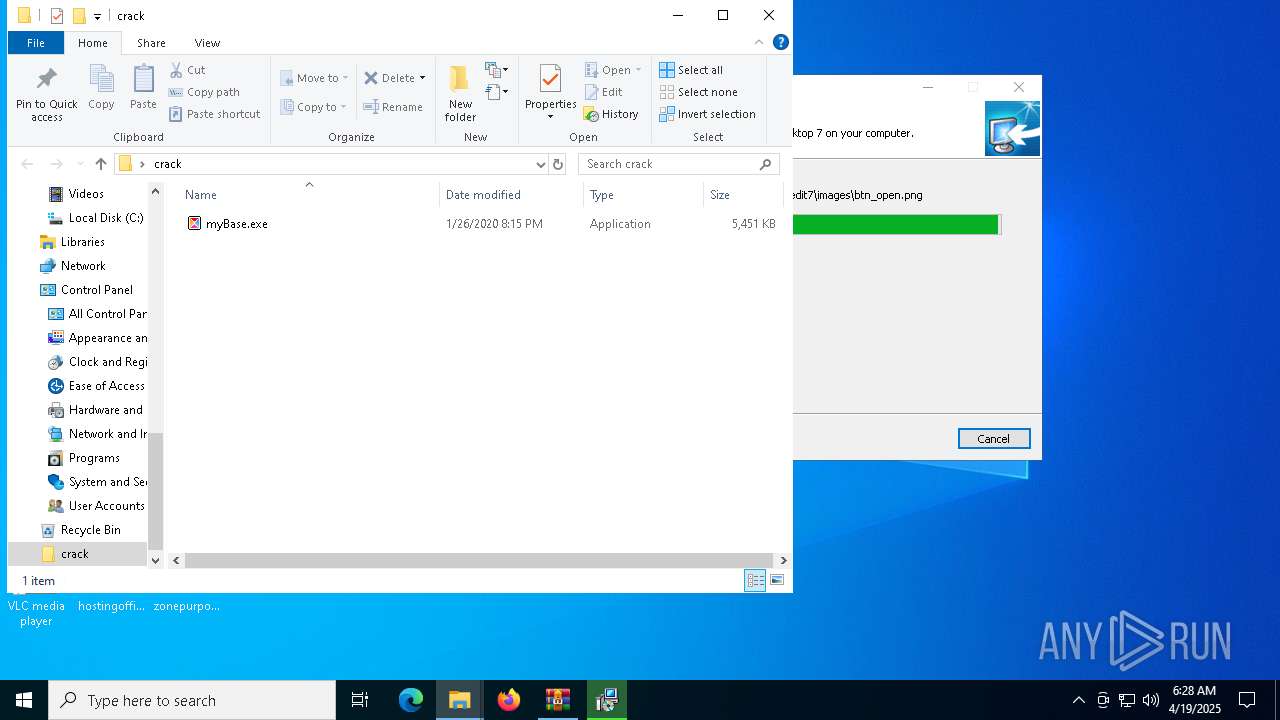
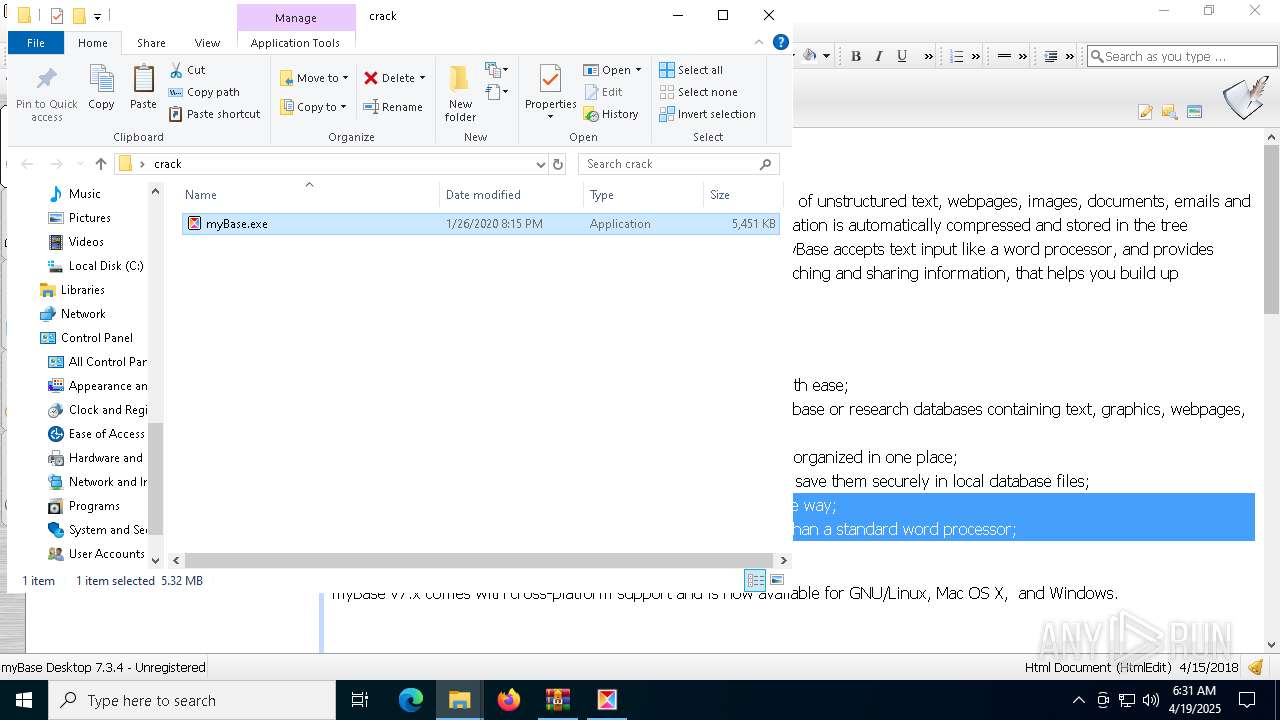
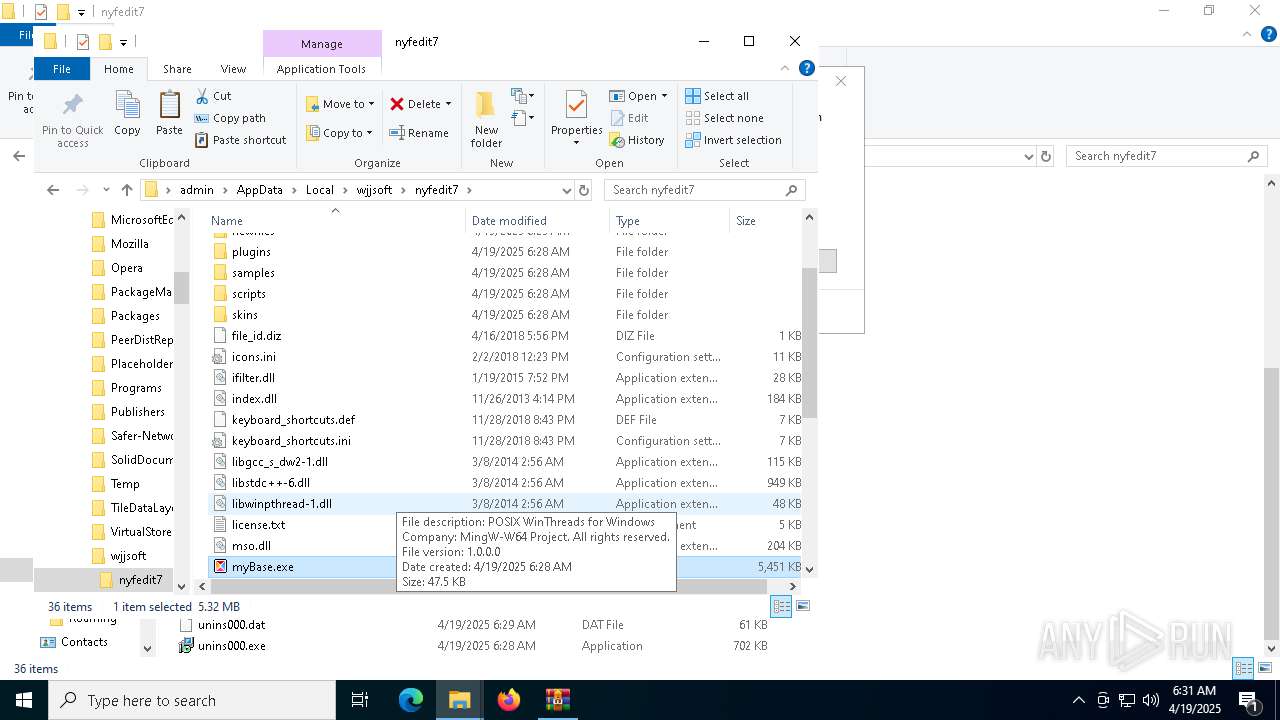
| 896 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa896.39371\myBase Desktop 7.3.4 [FileCR]\crack\myBase.exe | executable | |
MD5:96936B899B7B52BA04D3039B1CFA3661 | SHA256:BE2288C645232837EC0F6A90767CA14A4741536B27AE61FFECB59875094FFE38 | |||
| 6644 | myBase-Desktop-Ver734-Setup.tmp | C:\Users\admin\AppData\Local\wjjsoft\nyfedit7\unins000.exe | executable | |
MD5:376F56C9755F31E9B2B6A2615D3C2342 | SHA256:273BBBEDB9EEA3D9DB6D43B6701FEA4FC5B0FCD21116DEEA85958580AB645FE0 | |||
| 6644 | myBase-Desktop-Ver734-Setup.tmp | C:\Users\admin\AppData\Local\Temp\is-3383U.tmp\_isetup\_shfoldr.dll | executable | |
MD5:92DC6EF532FBB4A5C3201469A5B5EB63 | SHA256:9884E9D1B4F8A873CCBD81F8AD0AE257776D2348D027D811A56475E028360D87 | |||
| 6644 | myBase-Desktop-Ver734-Setup.tmp | C:\Users\admin\AppData\Local\wjjsoft\nyfedit7\myBase.exe | executable | |
MD5:DBCCA506208053F33D5539808A1BC833 | SHA256:E8E2E085E615DA88D7A803218BB1E95ADE10566CE25A30BCDE2A41BB0E27D26A | |||
| 6644 | myBase-Desktop-Ver734-Setup.tmp | C:\Users\admin\AppData\Local\wjjsoft\nyfedit7\is-I8K1K.tmp | executable | |
MD5:376F56C9755F31E9B2B6A2615D3C2342 | SHA256:273BBBEDB9EEA3D9DB6D43B6701FEA4FC5B0FCD21116DEEA85958580AB645FE0 | |||
| 6644 | myBase-Desktop-Ver734-Setup.tmp | C:\Users\admin\AppData\Local\Temp\is-3383U.tmp\_isetup\_setup64.tmp | executable | |
MD5:C8871EFD8AF2CF4D9D42D1FF8FADBF89 | SHA256:E4FC574A01B272C2D0AED0EC813F6D75212E2A15A5F5C417129DD65D69768F40 | |||
| 6644 | myBase-Desktop-Ver734-Setup.tmp | C:\Users\admin\AppData\Local\wjjsoft\nyfedit7\is-BT7UO.tmp | executable | |
MD5:4E2FECB70364515BD577BE14871DC577 | SHA256:A87119900D46CC87B9AC54BC331F509A8BA7FDBDBF57377F537E31F8431DAD24 | |||
| 6644 | myBase-Desktop-Ver734-Setup.tmp | C:\Users\admin\AppData\Local\wjjsoft\nyfedit7\is-3J1M8.tmp | executable | |
MD5:DBCCA506208053F33D5539808A1BC833 | SHA256:E8E2E085E615DA88D7A803218BB1E95ADE10566CE25A30BCDE2A41BB0E27D26A | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
6
TCP/UDP connections
29
DNS requests
24
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 23.53.40.176:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
6544 | svchost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
7152 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
7152 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
2924 | SearchApp.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
6852 | myBase.exe | GET | 200 | 104.238.158.201:80 | http://www.wjjsoft.com/cgi-bin/app_nyf7_renew_zrb.cgi?q=daily&d1=0_1d&d2=0_7&ver=7.3.4&os=Win32&uses=2&nags=0&lang=en-US&uid=&skey=&pass=0&mid=26b799fa&exe=60d2-5e0b_20200126&max5=885.3KiB&open5=2&res=1280x720&fmts=0_0_0_0&fmt0= | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
— | — | 23.53.40.176:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
3216 | svchost.exe | 172.211.123.249:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
6544 | svchost.exe | 20.190.159.75:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
6544 | svchost.exe | 2.17.190.73:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
2104 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
7152 | SIHClient.exe | 172.202.163.200:443 | slscr.update.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | GB | whitelisted |
7152 | SIHClient.exe | 95.101.149.131:80 | www.microsoft.com | Akamai International B.V. | NL | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
activation-v2.sls.microsoft.com |
| whitelisted |