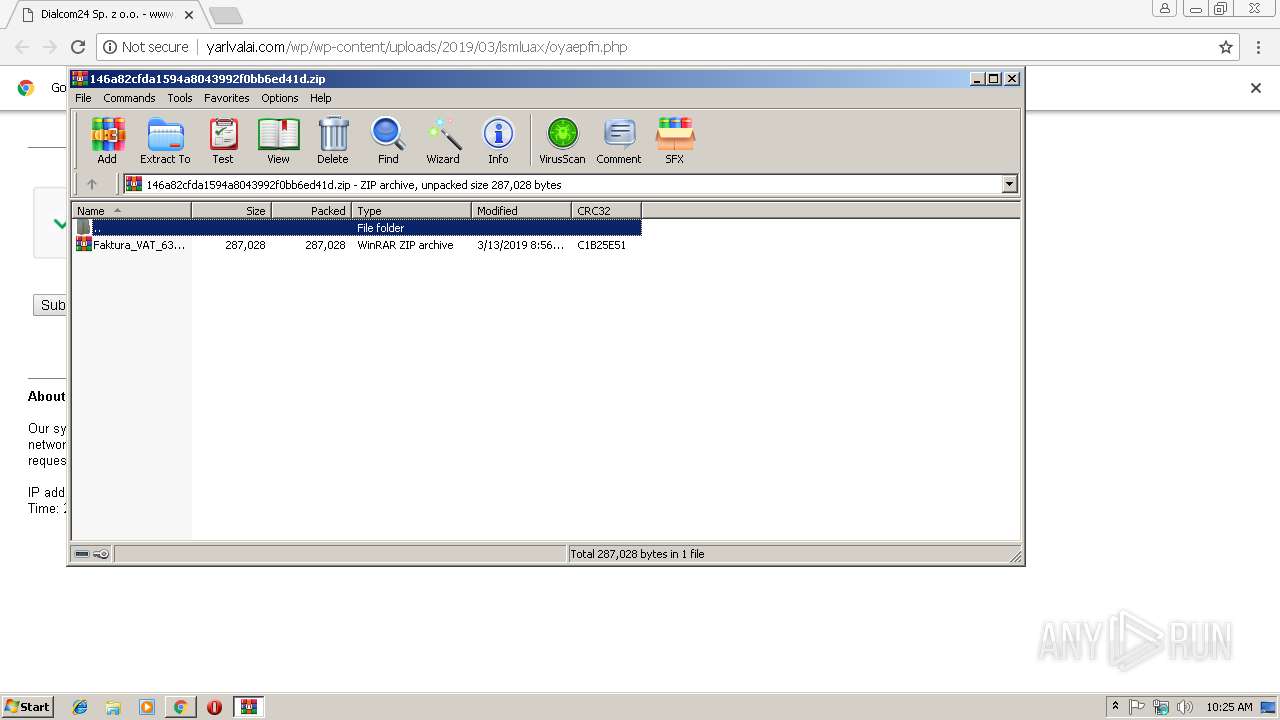
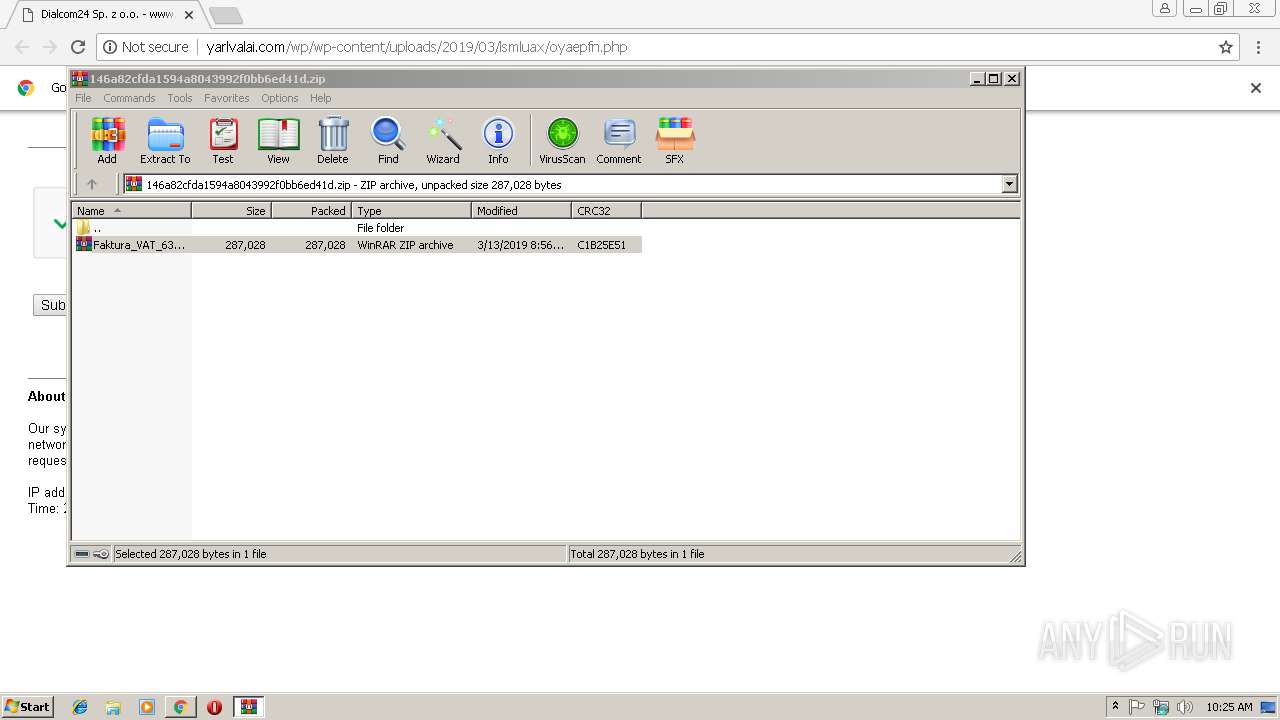
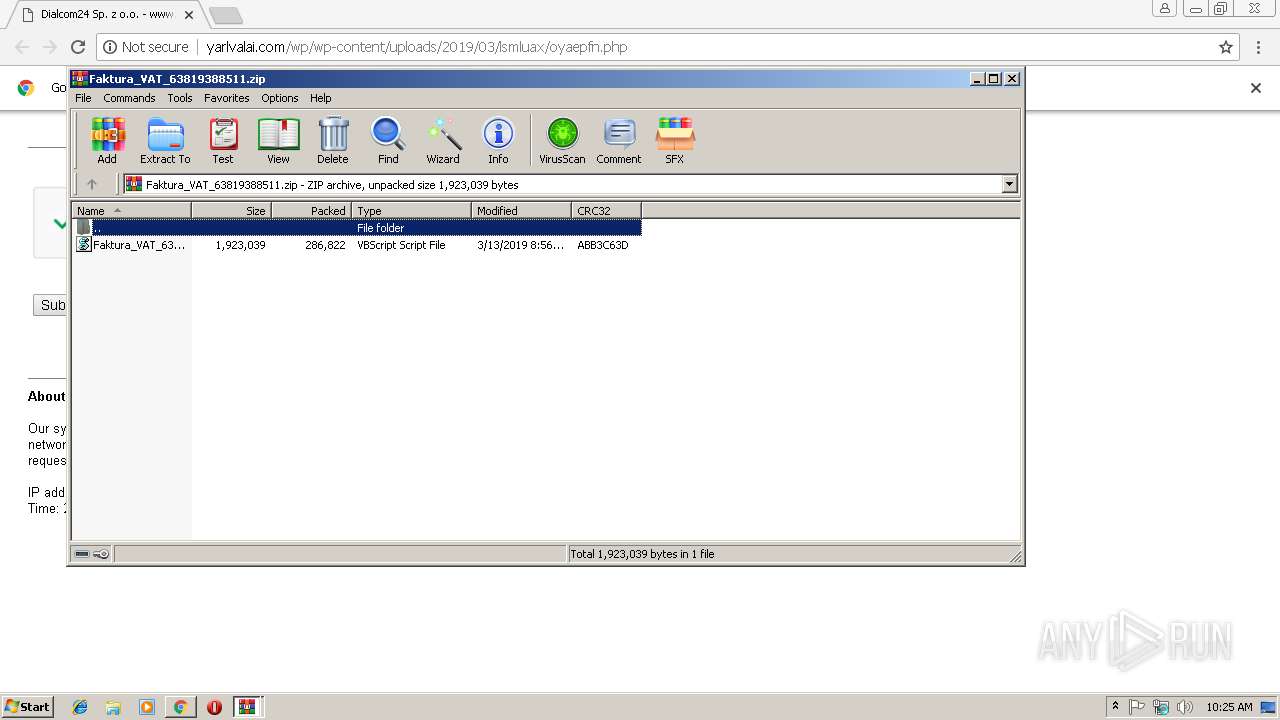
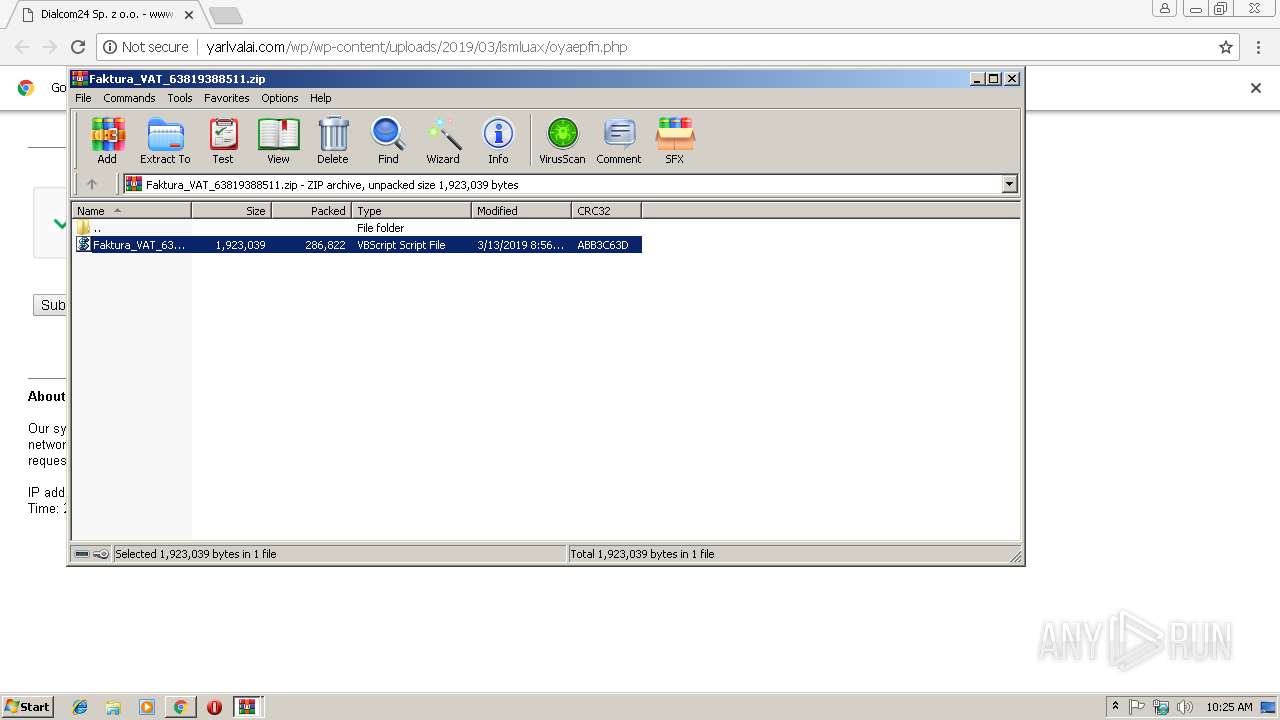
| URL: | http://yarlvalai.com/wp/wp-content/uploads/2019/03/lsmluax/oyaepfn.php |
| Full analysis: | https://app.any.run/tasks/72160659-f61c-4e20-8a86-ad92f30e24f4 |
| Verdict: | Malicious activity |
| Analysis date: | March 14, 2019, 10:24:32 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MD5: | 77E2E6D8F213E0555FCEFF7EB5496383 |
| SHA1: | 13F580EF44832401D1D4A077A33FC3CFC5B7F24C |
| SHA256: | 8F494CF11B591364884A833350AD29242EDE23EA35C335552F32BA587889C808 |
| SSDEEP: | 3:N1KH2TjJifAQyX28KleEdROh:CSsfAZGBeE3Oh |
MALICIOUS
Loads dropped or rewritten executable
- regsvr32.exe (PID: 2444)
- rundll32.exe (PID: 2252)
Registers / Runs the DLL via REGSVR32.EXE
- WScript.exe (PID: 2760)
SUSPICIOUS
Application launched itself
- WinRAR.exe (PID: 3280)
Executable content was dropped or overwritten
- WScript.exe (PID: 2760)
Uses RUNDLL32.EXE to load library
- regsvr32.exe (PID: 2444)
Executes scripts
- WinRAR.exe (PID: 3800)
INFO
Reads Internet Cache Settings
- chrome.exe (PID: 3028)
Application launched itself
- chrome.exe (PID: 3028)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
43
Monitored processes
14
Malicious processes
3
Suspicious processes
3
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1448 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=gpu-process --field-trial-handle=940,7910474326889406434,12995545885406274513,131072 --enable-features=PasswordImport --disable-gpu-sandbox --gpu-preferences=KAAAAAAAAACAAwBAAQAAAAAAAAAAAGAAEAAAAAAAAAAAAAAAAAAAACgAAAAEAAAAIAAAAAAAAAAoAAAAAAAAADAAAAAAAAAAOAAAAAAAAAAQAAAAAAAAAAAAAAAKAAAAEAAAAAAAAAAAAAAACwAAABAAAAAAAAAAAQAAAAoAAAAQAAAAAAAAAAEAAAALAAAA --service-request-channel-token=C6092EACDECACDAF2E79B405EBB53D39 --mojo-platform-channel-handle=3828 /prefetch:2 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google Inc. Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 68.0.3440.106 Modules
| |||||||||||||||
| 2192 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=gpu-process --field-trial-handle=940,7910474326889406434,12995545885406274513,131072 --enable-features=PasswordImport --gpu-preferences=KAAAAAAAAACAAwBAAQAAAAAAAAAAAGAAEAAAAAAAAAAAAAAAAAAAACgAAAAEAAAAIAAAAAAAAAAoAAAAAAAAADAAAAAAAAAAOAAAAAAAAAAQAAAAAAAAAAAAAAAKAAAAEAAAAAAAAAAAAAAACwAAABAAAAAAAAAAAQAAAAoAAAAQAAAAAAAAAAEAAAALAAAA --service-request-channel-token=89663CE0CAAA6F51EF087B73CAD6A349 --mojo-platform-channel-handle=1012 --ignored=" --type=renderer " /prefetch:2 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google Inc. Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 68.0.3440.106 Modules
| |||||||||||||||
| 2252 | C:\Windows\system32\\rundll32.exe C:\Users\admin\AppData\Local\Temp\ofoM.dll,f0 | C:\Windows\system32\rundll32.exe | regsvr32.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2444 | "C:\Windows\System32\regsvr32.exe" -s C:\Users\admin\AppData\Local\Temp/ofoM.dll | C:\Windows\System32\regsvr32.exe | — | WScript.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft(C) Register Server Exit code: 4 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2760 | "C:\Windows\System32\WScript.exe" "C:\Users\admin\AppData\Local\Temp\Rar$DIa3800.11661\Faktura_VAT_638193885112.vbs" | C:\Windows\System32\WScript.exe | WinRAR.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft ® Windows Based Script Host Exit code: 0 Version: 5.8.7600.16385 Modules
| |||||||||||||||
| 2996 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=940,7910474326889406434,12995545885406274513,131072 --enable-features=PasswordImport --service-pipe-token=7902E1C7612ABD71EF83087B4AAD65DB --lang=en-US --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=7902E1C7612ABD71EF83087B4AAD65DB --renderer-client-id=4 --mojo-platform-channel-handle=1868 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google Inc. Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 68.0.3440.106 Modules
| |||||||||||||||
| 3008 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=watcher --main-thread-id=3032 --on-initialized-event-handle=304 --parent-handle=308 /prefetch:6 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google Inc. Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 68.0.3440.106 Modules
| |||||||||||||||
| 3028 | "C:\Program Files\Google\Chrome\Application\chrome.exe" http://yarlvalai.com/wp/wp-content/uploads/2019/03/lsmluax/oyaepfn.php | C:\Program Files\Google\Chrome\Application\chrome.exe | explorer.exe | ||||||||||||
User: admin Company: Google Inc. Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 68.0.3440.106 Modules
| |||||||||||||||
| 3280 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\Downloads\146a82cfda1594a8043992f0bb6ed41d.zip" | C:\Program Files\WinRAR\WinRAR.exe | — | chrome.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.60.0 Modules
| |||||||||||||||
| 3608 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=940,7910474326889406434,12995545885406274513,131072 --enable-features=PasswordImport --service-pipe-token=8F0BEED68A8562FB9730598446CA3539 --lang=en-US --extension-process --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=8F0BEED68A8562FB9730598446CA3539 --renderer-client-id=3 --mojo-platform-channel-handle=1516 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google Inc. Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 68.0.3440.106 Modules
| |||||||||||||||
Total events
1 777
Read events
1 695
Write events
79
Delete events
3
Modification events
| (PID) Process: | (3008) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BrowserExitCodes |
| Operation: | write | Name: | 3028-13197032687846250 |
Value: 259 | |||
| (PID) Process: | (3028) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BLBeacon |
| Operation: | write | Name: | failed_count |
Value: 0 | |||
| (PID) Process: | (3028) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 2 | |||
| (PID) Process: | (3028) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 1 | |||
| (PID) Process: | (3028) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Update\ClientState\{8A69D345-D564-463c-AFF1-A69D9E530F96} |
| Operation: | write | Name: | dr |
Value: 1 | |||
| (PID) Process: | (3028) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome |
| Operation: | write | Name: | UsageStatsInSample |
Value: 0 | |||
| (PID) Process: | (3028) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BrowserExitCodes |
| Operation: | delete value | Name: | 3516-13180984670829101 |
Value: 0 | |||
| (PID) Process: | (3028) chrome.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Google\Update\ClientStateMedium\{8A69D345-D564-463C-AFF1-A69D9E530F96} |
| Operation: | write | Name: | usagestats |
Value: 0 | |||
| (PID) Process: | (3028) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BrowserExitCodes |
| Operation: | delete value | Name: | 3028-13197032687846250 |
Value: 259 | |||
| (PID) Process: | (3028) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Update\ClientState\{8A69D345-D564-463c-AFF1-A69D9E530F96} |
| Operation: | write | Name: | metricsid |
Value: | |||
Executable files
6
Suspicious files
22
Text files
52
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3028 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\fef9a774-9f4f-4c4d-9da5-b2421317aaf2.tmp | — | |
MD5:— | SHA256:— | |||
| 3028 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Download Service\EntryDB\000016.dbtmp | — | |
MD5:— | SHA256:— | |||
| 3028 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\data_reduction_proxy_leveldb\000016.dbtmp | — | |
MD5:— | SHA256:— | |||
| 3028 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\89df50f8-66ea-4144-885b-af98b49c31af.tmp | — | |
MD5:— | SHA256:— | |||
| 3028 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\data_reduction_proxy_leveldb\LOG.old | text | |
MD5:— | SHA256:— | |||
| 3028 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\data_reduction_proxy_leveldb\LOG.old~RF20e40b.TMP | text | |
MD5:— | SHA256:— | |||
| 3028 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Sync Data\LevelDB\LOG.old | text | |
MD5:— | SHA256:— | |||
| 3028 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Sync Data\LevelDB\LOG.old~RF20e43a.TMP | text | |
MD5:— | SHA256:— | |||
| 3772 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\CrashpadMetrics.pma | binary | |
MD5:9543068B6751E1F3E11F91D72EE78D95 | SHA256:D060AD21AE6E04CB58668CAA52ADFCA573E018102CC07554D2ED3EAE11AB7785 | |||
| 3028 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Download Service\EntryDB\LOG.old | text | |
MD5:8CA4BA2B95D7089861A48ED69FDE6561 | SHA256:AA64C14D0C68B62BBAB62A6D6FA4662FF89E1FBC7B337C926AC213C191D6406C | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
3
TCP/UDP connections
14
DNS requests
7
Threats
2
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3028 | chrome.exe | GET | 200 | 104.27.190.46:80 | http://yarlvalai.com/wp/wp-content/uploads/2019/03/lsmluax/oyaepfn.php | US | html | 122 Kb | shared |
3028 | chrome.exe | GET | 200 | 104.27.190.46:80 | http://yarlvalai.com/favicon.ico | US | html | 123 b | shared |
3028 | chrome.exe | GET | 200 | 104.27.190.46:80 | http://yarlvalai.com/wp/wp-content/uploads/2019/03/lsmluax/oyaepfn.php?downdb4271b1511828a4e325e73cbdc1d546 | US | compressed | 280 Kb | shared |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3028 | chrome.exe | 172.217.23.163:443 | www.gstatic.com | Google Inc. | US | whitelisted |
3028 | chrome.exe | 104.27.190.46:80 | yarlvalai.com | Cloudflare Inc | US | shared |
3028 | chrome.exe | 216.58.205.237:443 | accounts.google.com | Google Inc. | US | whitelisted |
3028 | chrome.exe | 216.58.206.10:443 | ajax.googleapis.com | Google Inc. | US | whitelisted |
3028 | chrome.exe | 216.58.207.67:443 | ssl.gstatic.com | Google Inc. | US | whitelisted |
2252 | rundll32.exe | 153.182.78.20:443 | — | NTT Communications Corporation | JP | malicious |
3028 | chrome.exe | 216.58.210.3:443 | clientservices.googleapis.com | Google Inc. | US | whitelisted |
2252 | rundll32.exe | 62.187.103.29:443 | — | — | GB | malicious |
3028 | chrome.exe | 172.217.22.78:443 | sb-ssl.google.com | Google Inc. | US | whitelisted |
3028 | chrome.exe | 104.27.191.46:80 | yarlvalai.com | Cloudflare Inc | US | shared |
DNS requests
Domain | IP | Reputation |
|---|---|---|
clientservices.googleapis.com |
| whitelisted |
yarlvalai.com |
| unknown |
www.gstatic.com |
| whitelisted |
accounts.google.com |
| shared |
ajax.googleapis.com |
| whitelisted |
ssl.gstatic.com |
| whitelisted |
sb-ssl.google.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2252 | rundll32.exe | A Network Trojan was detected | MALWARE [PTsecurity] Win32/Spy.Danabot.I |
2252 | rundll32.exe | A Network Trojan was detected | MALWARE [PTsecurity] Win32/Spy.Danabot.I |