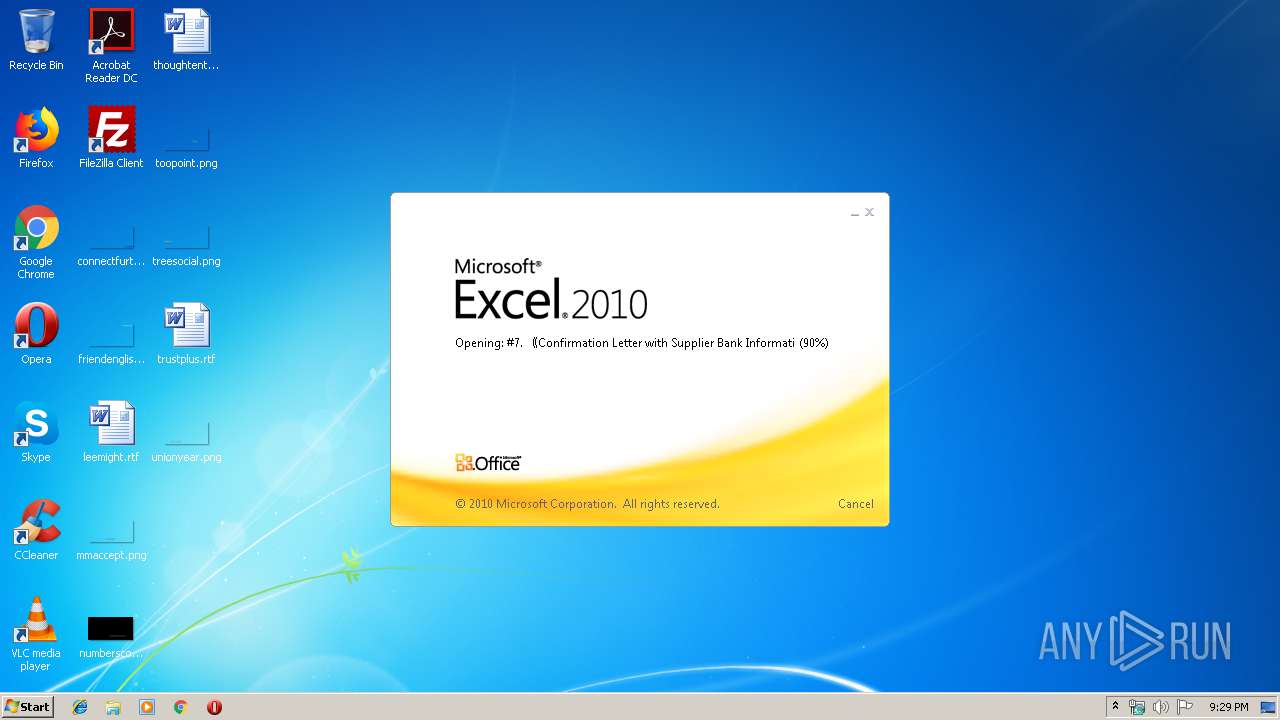
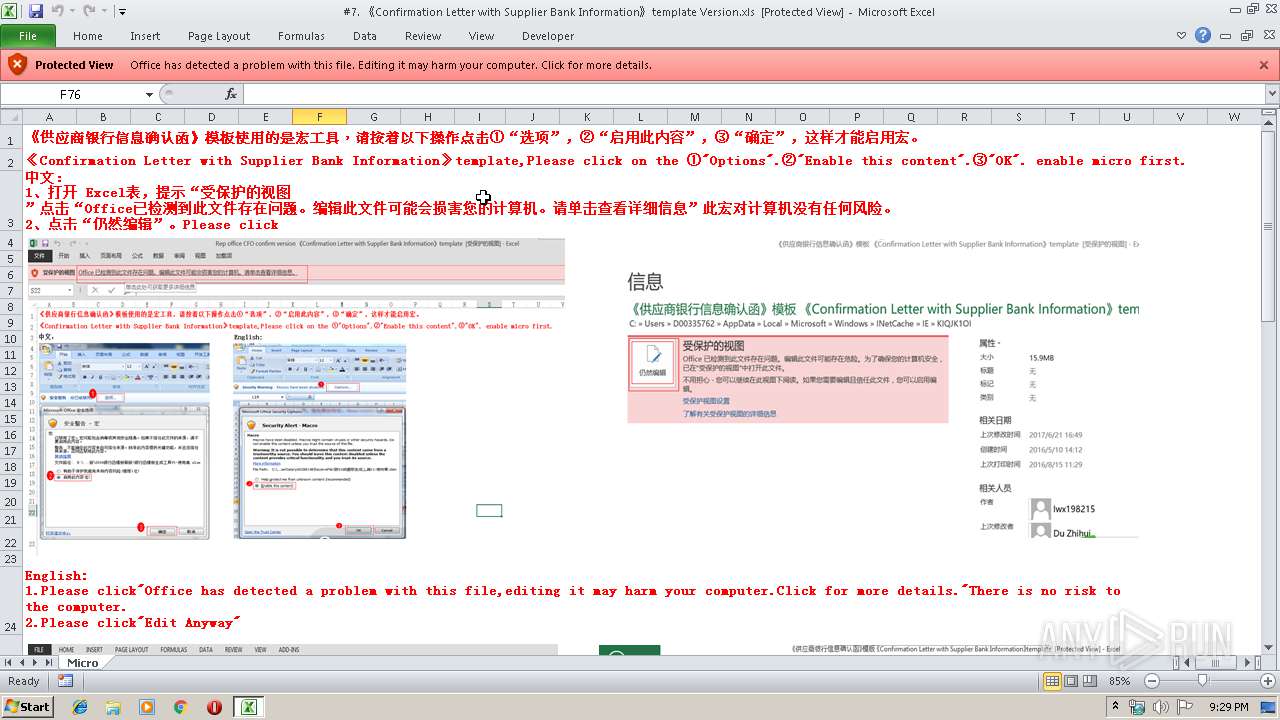
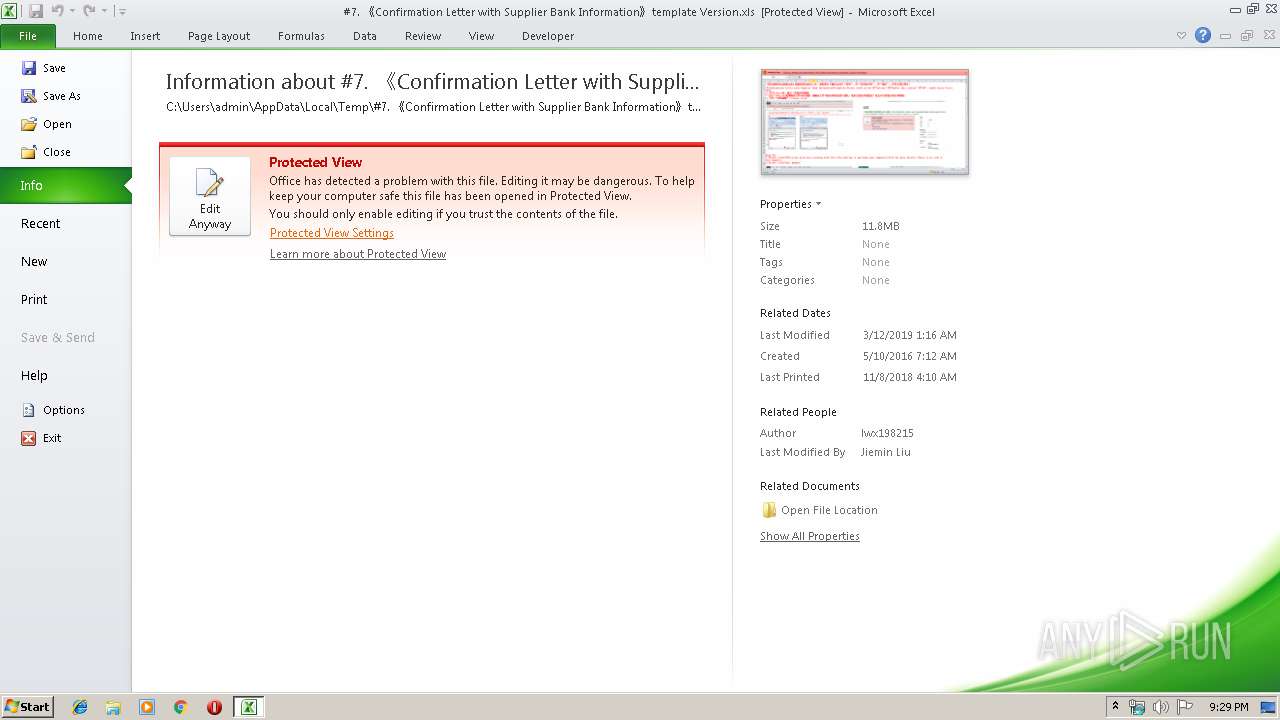
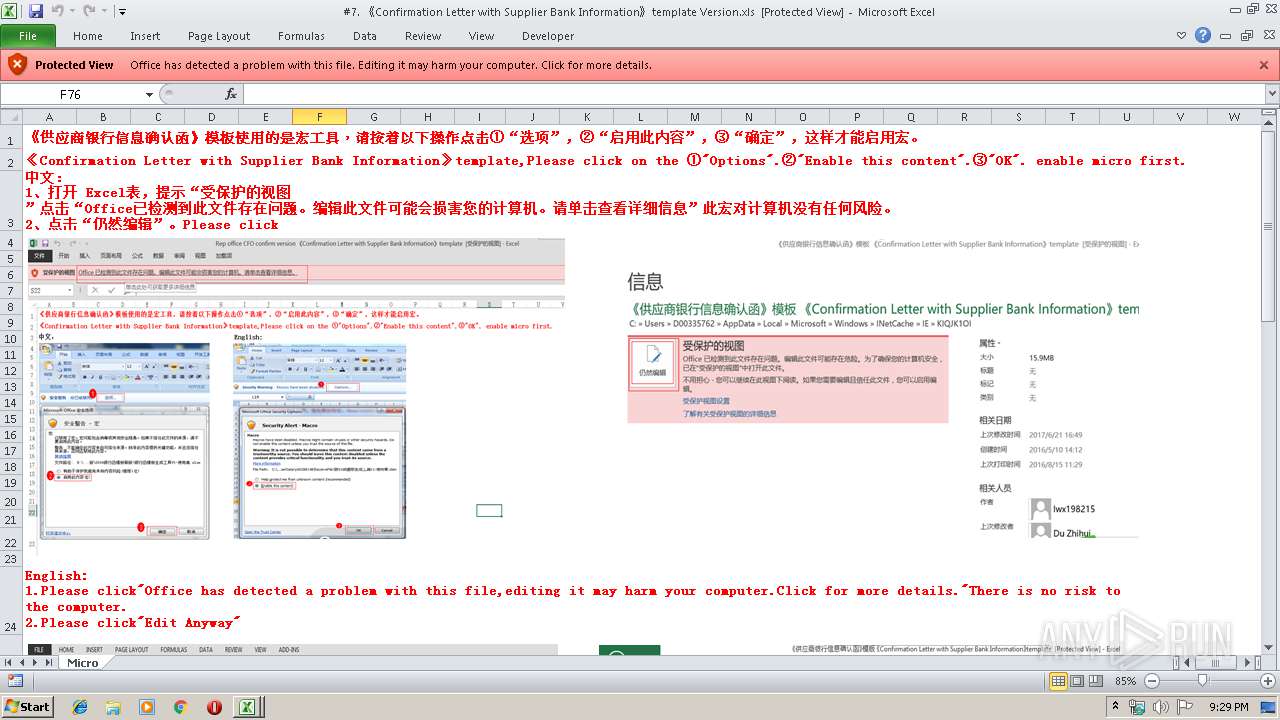
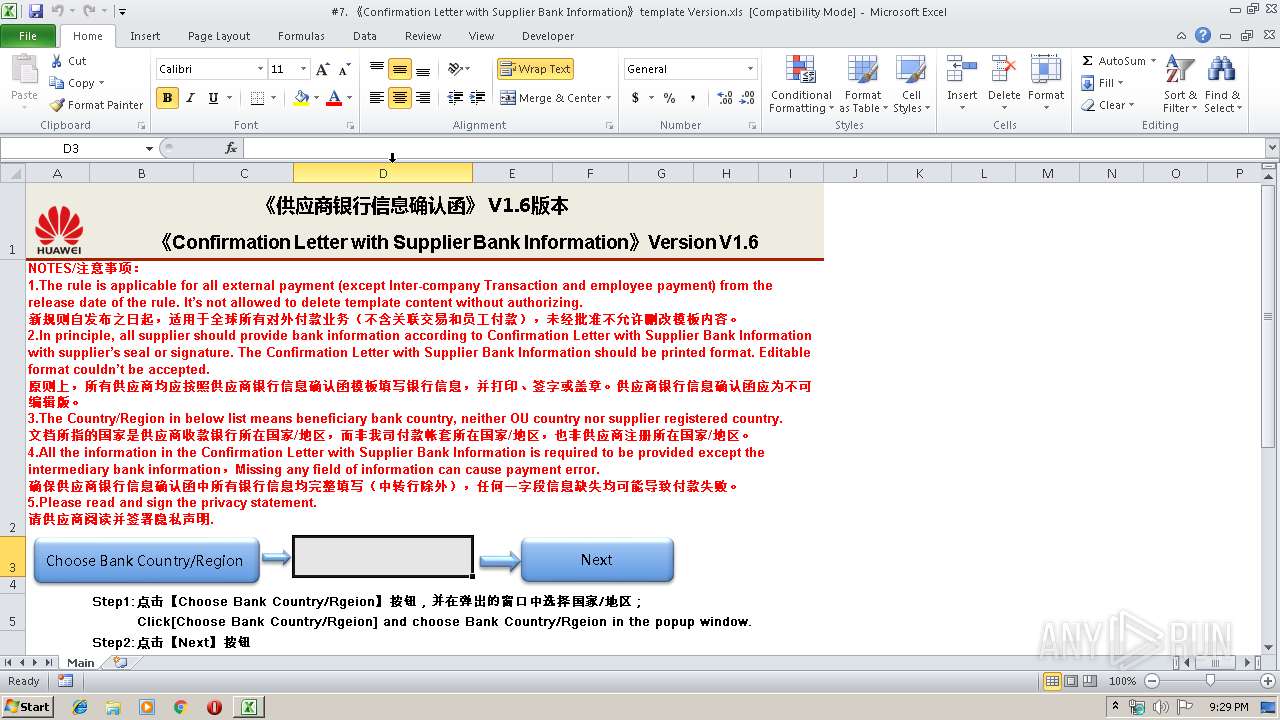
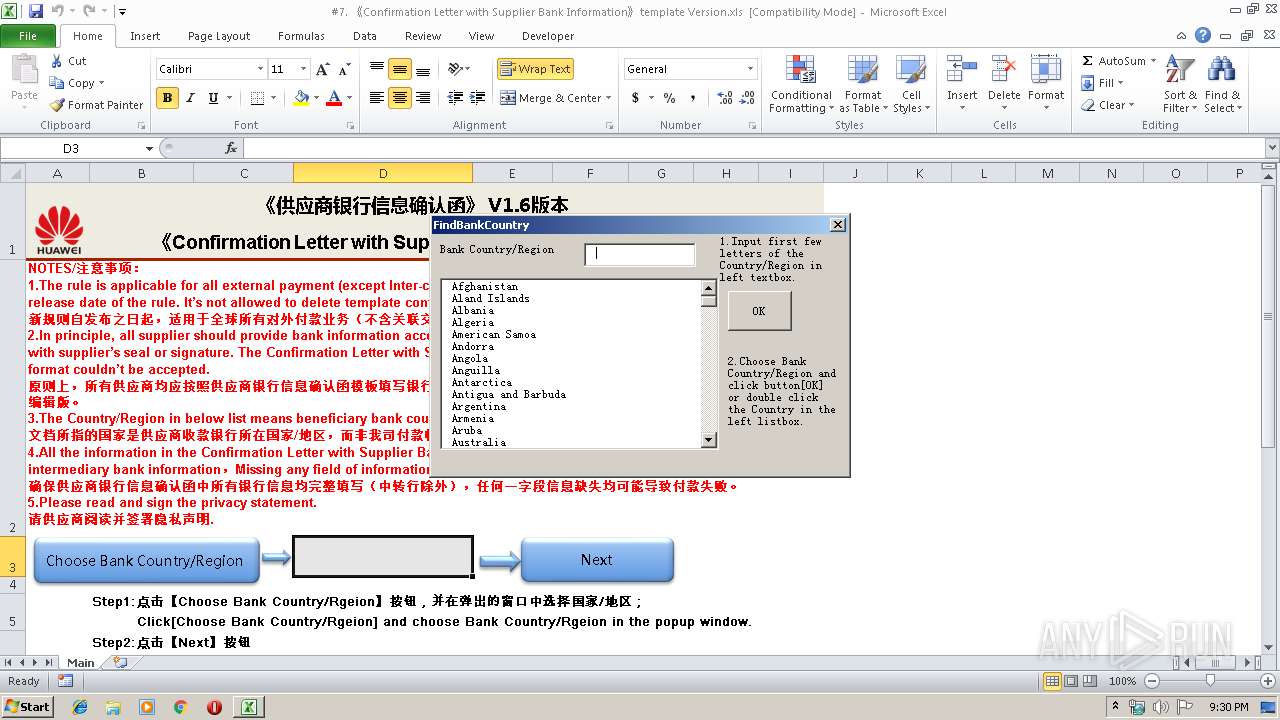
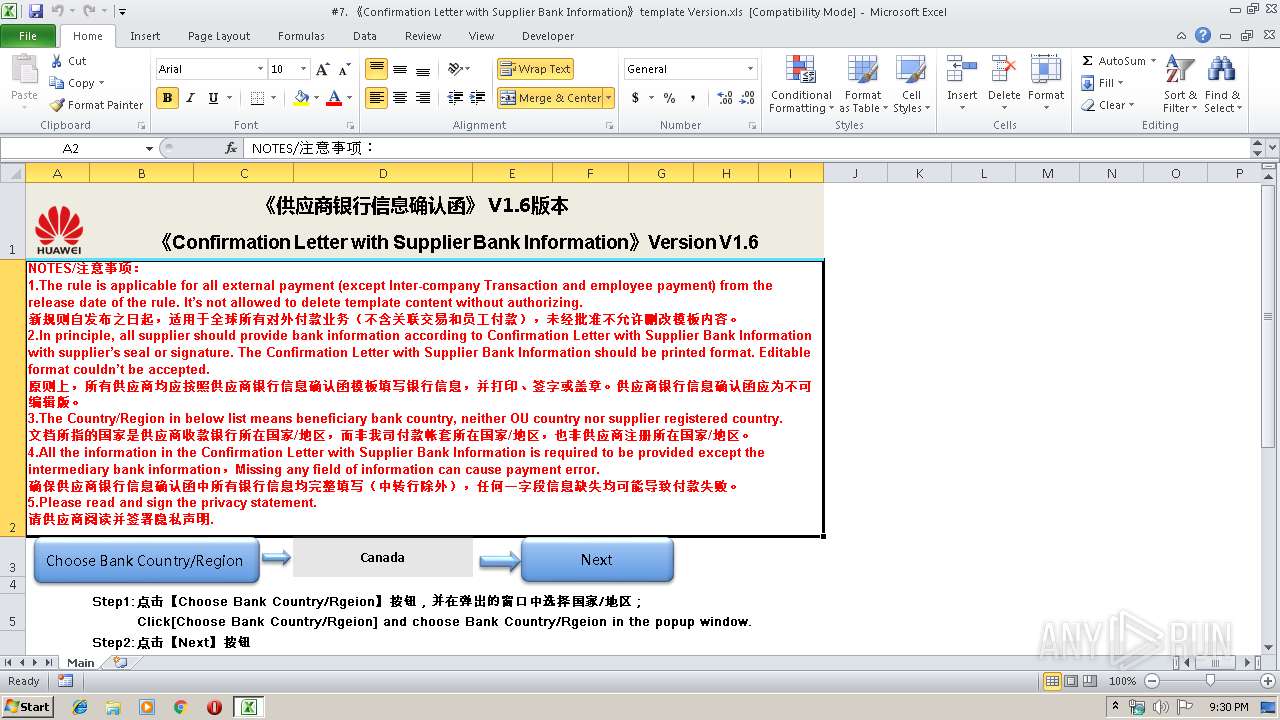
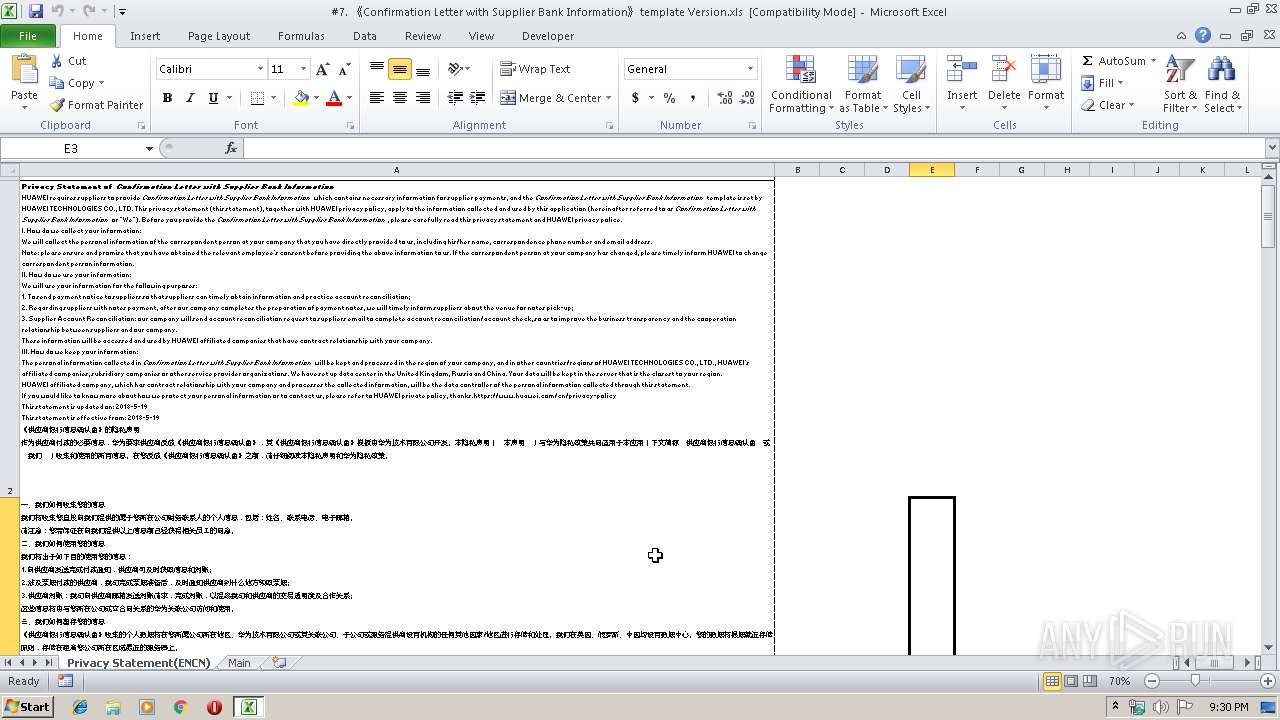
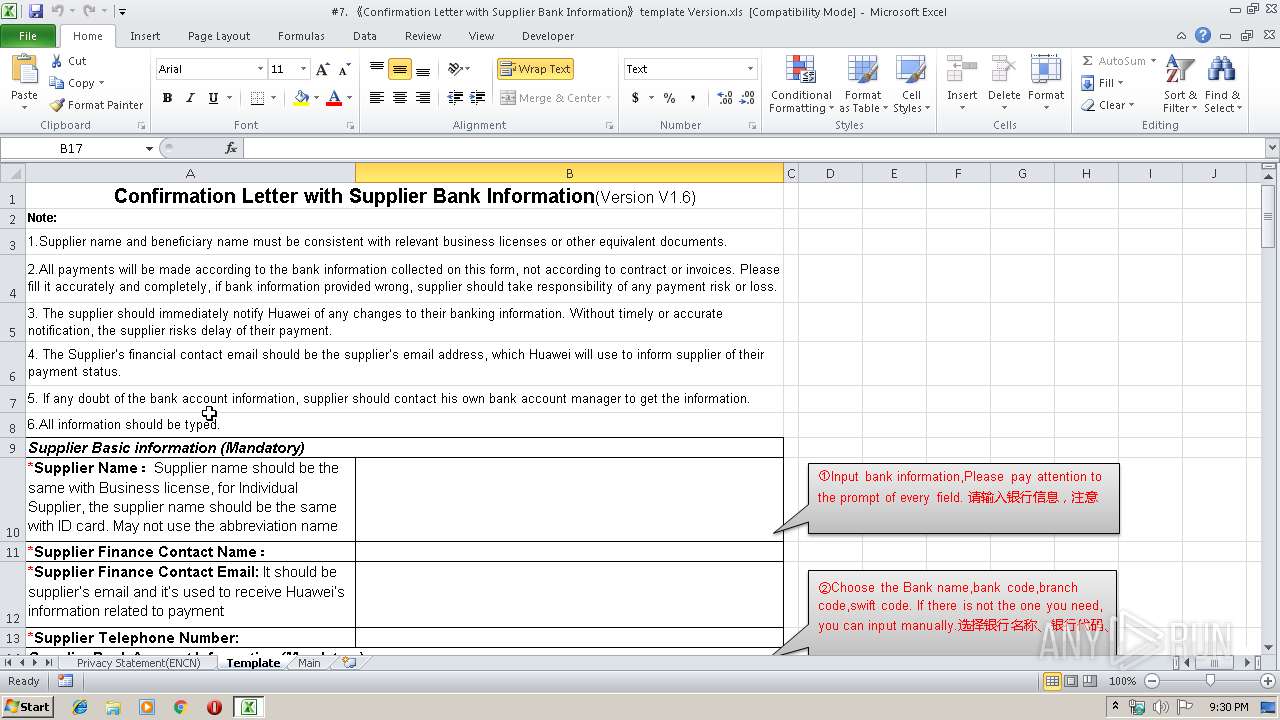
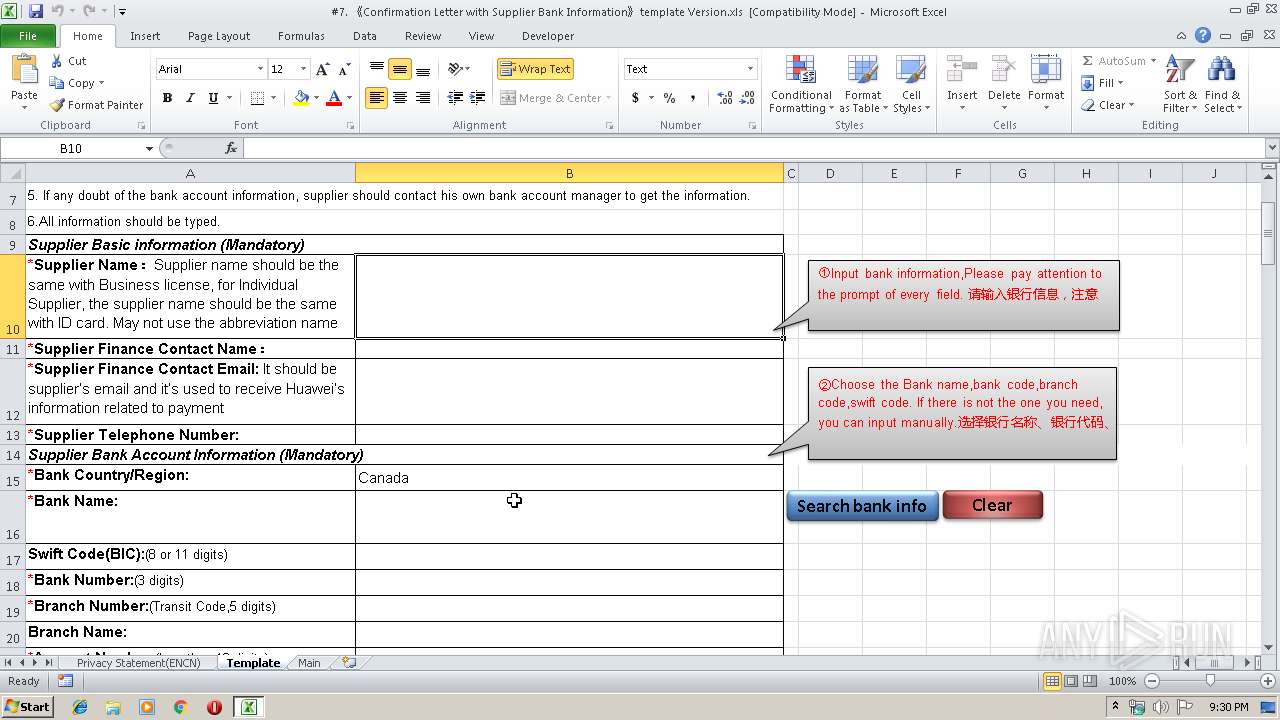
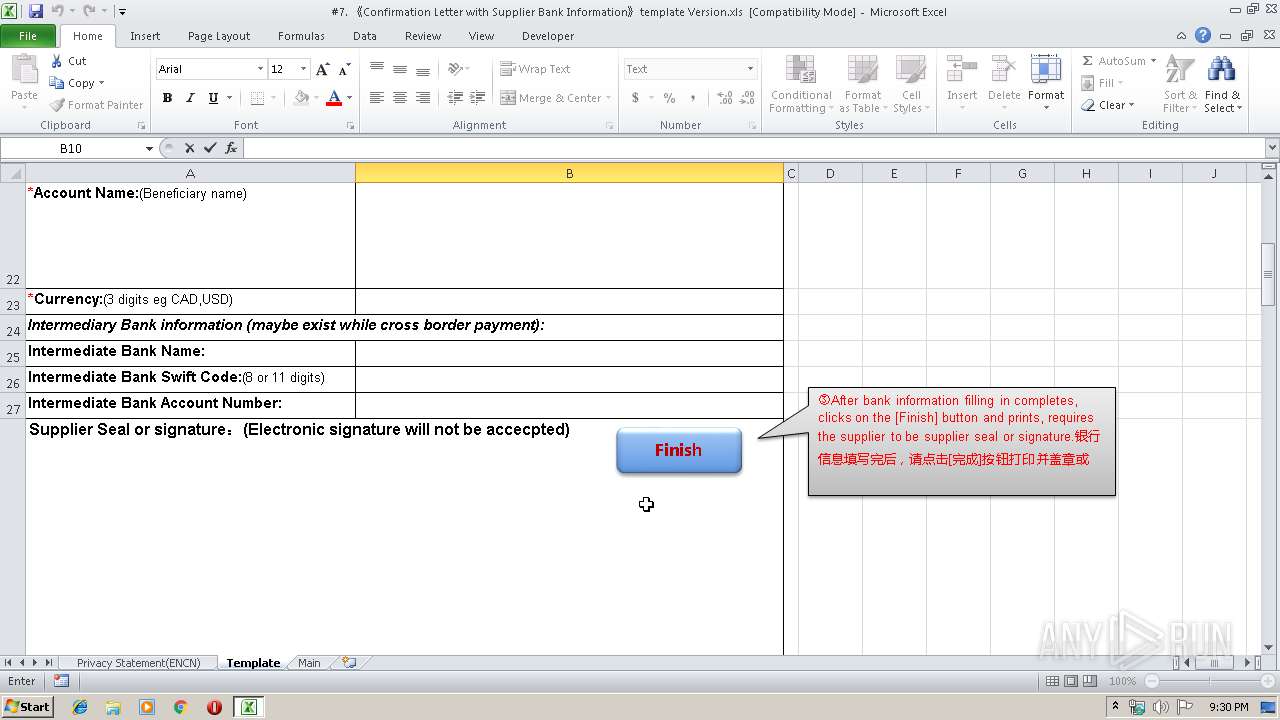
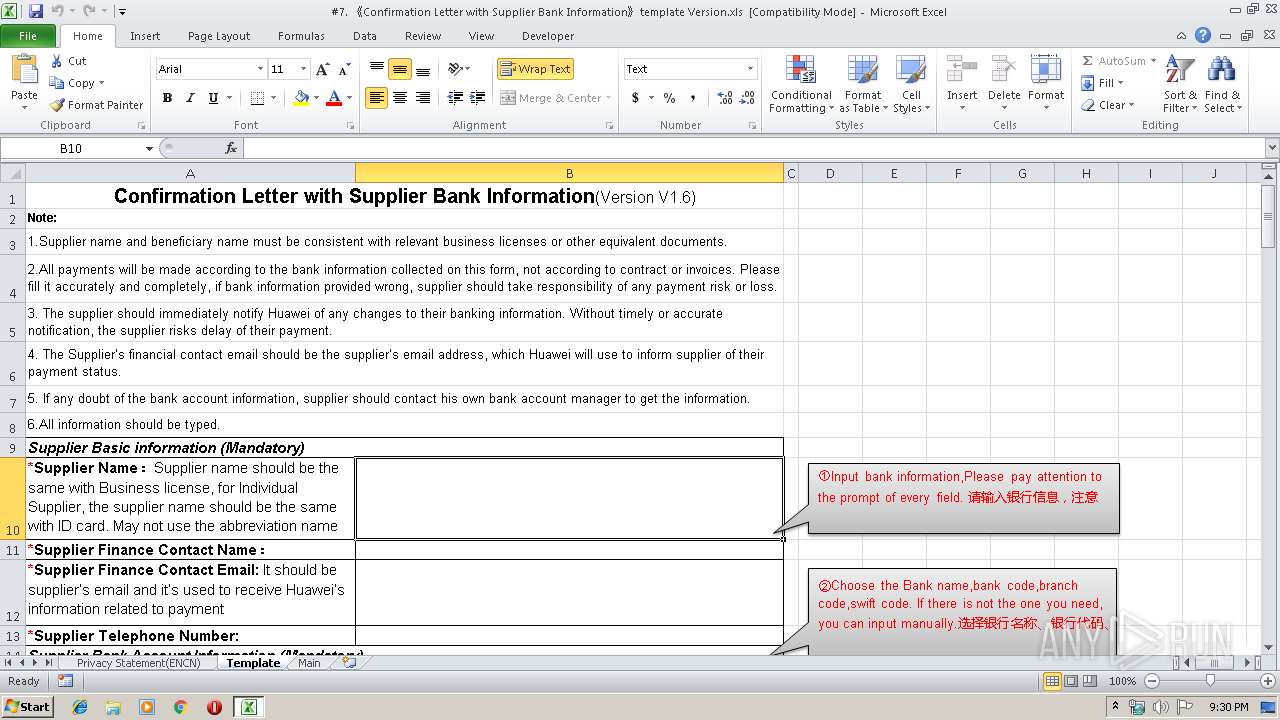
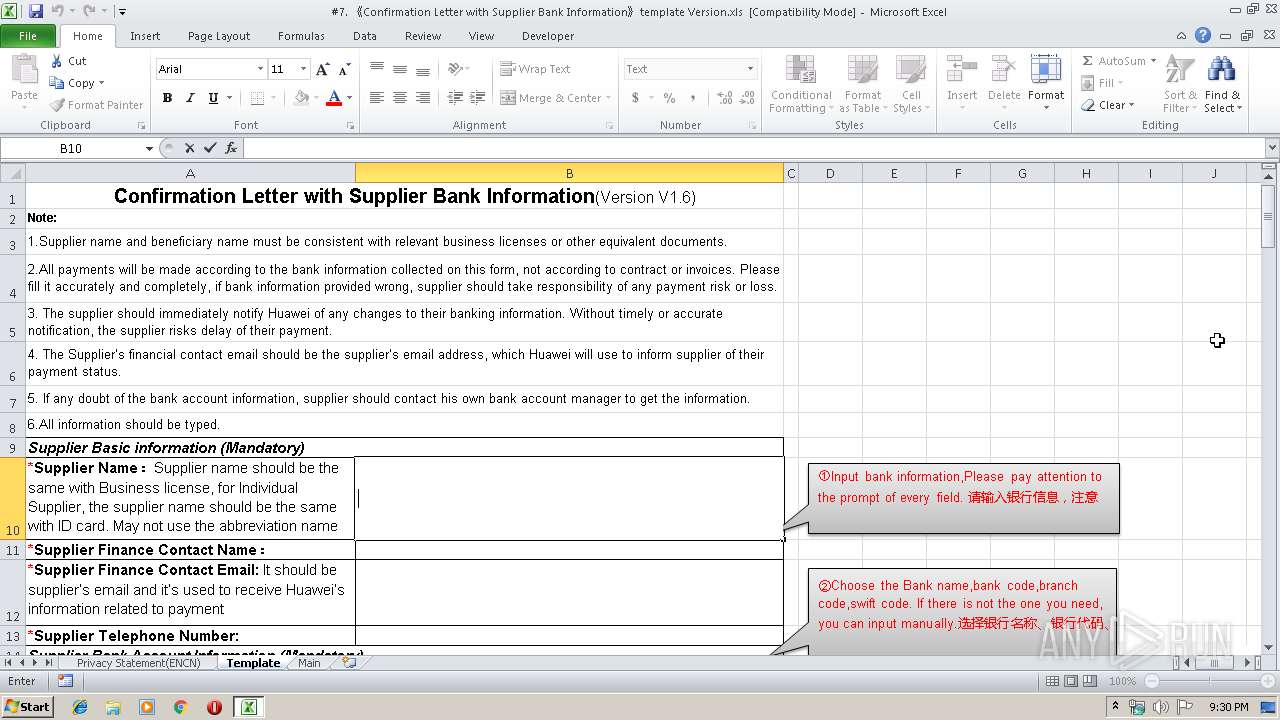
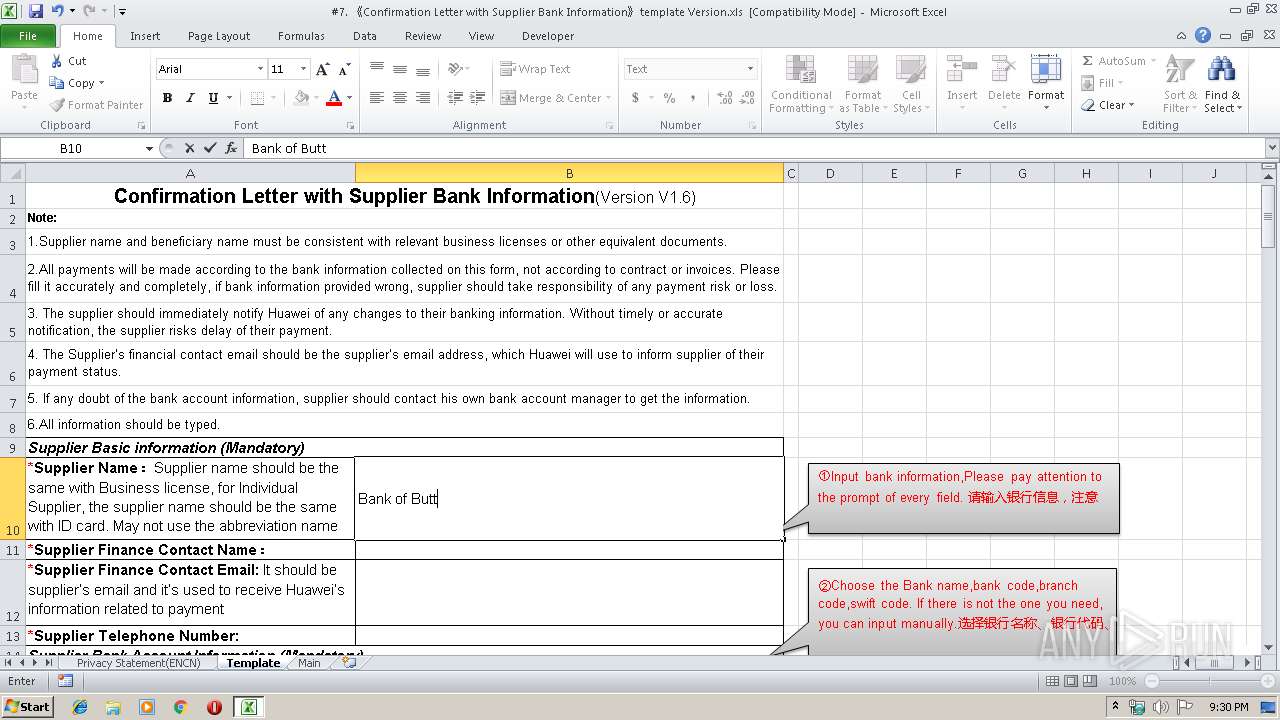
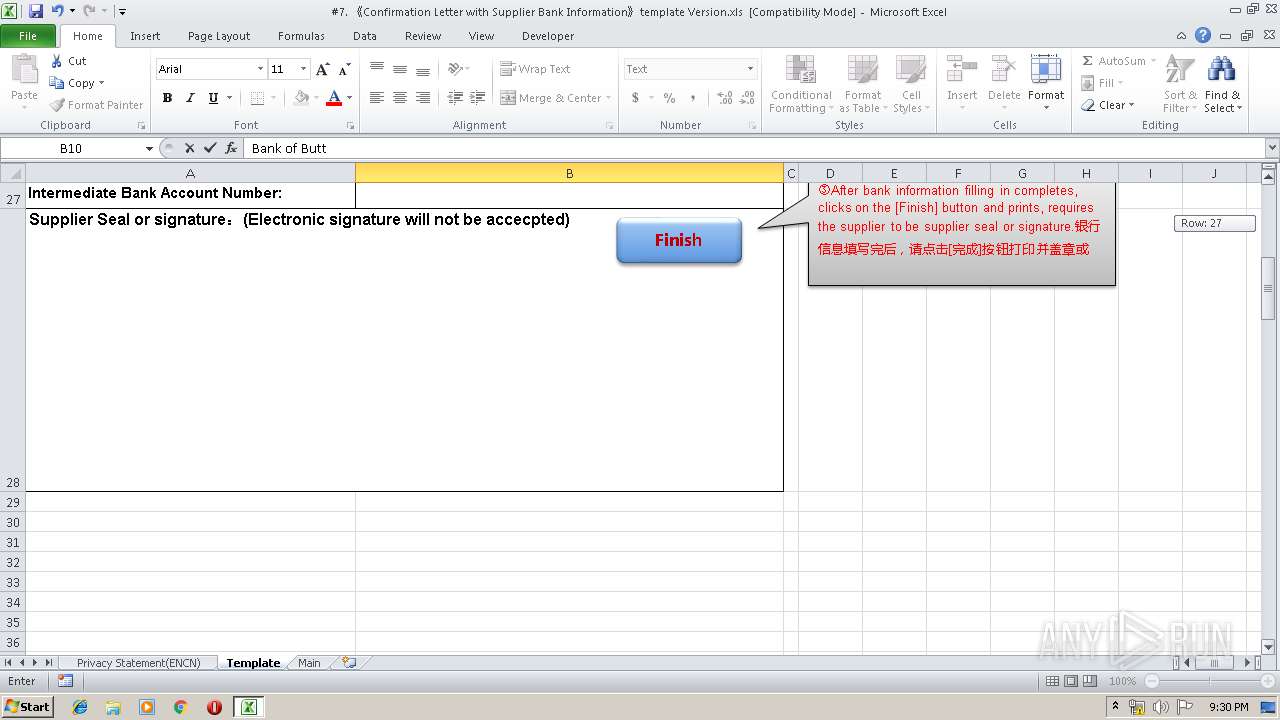
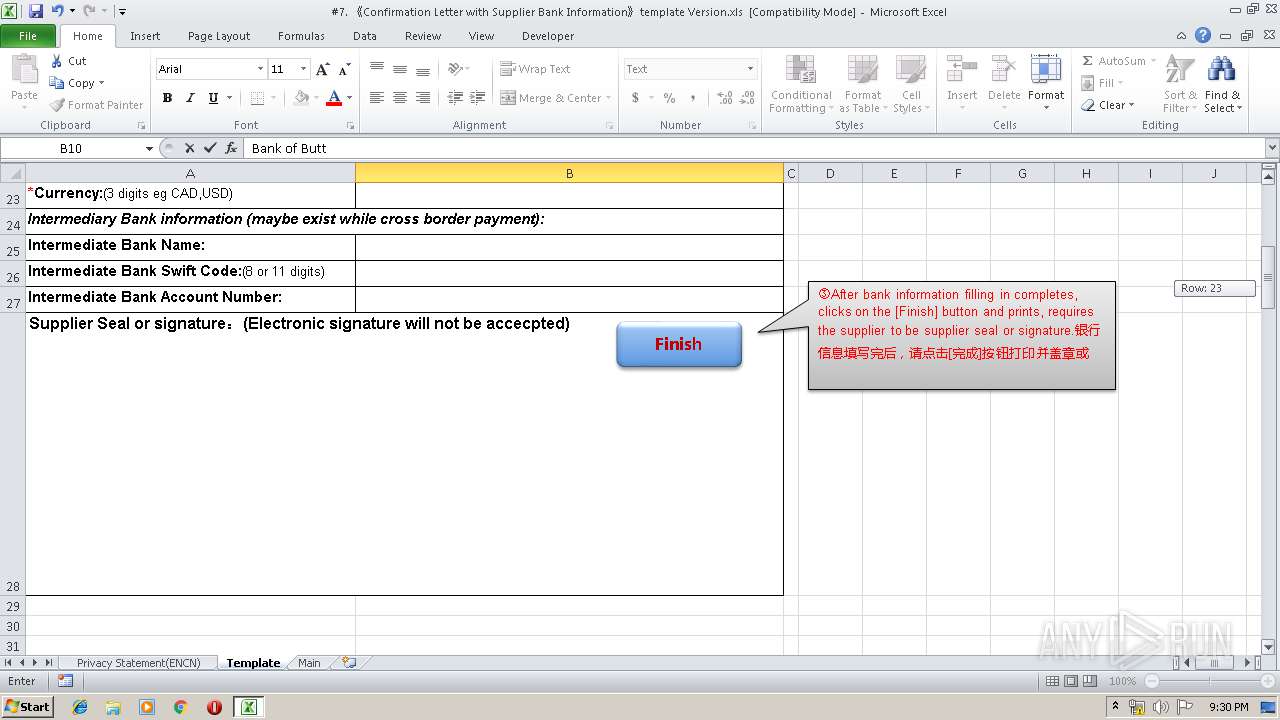
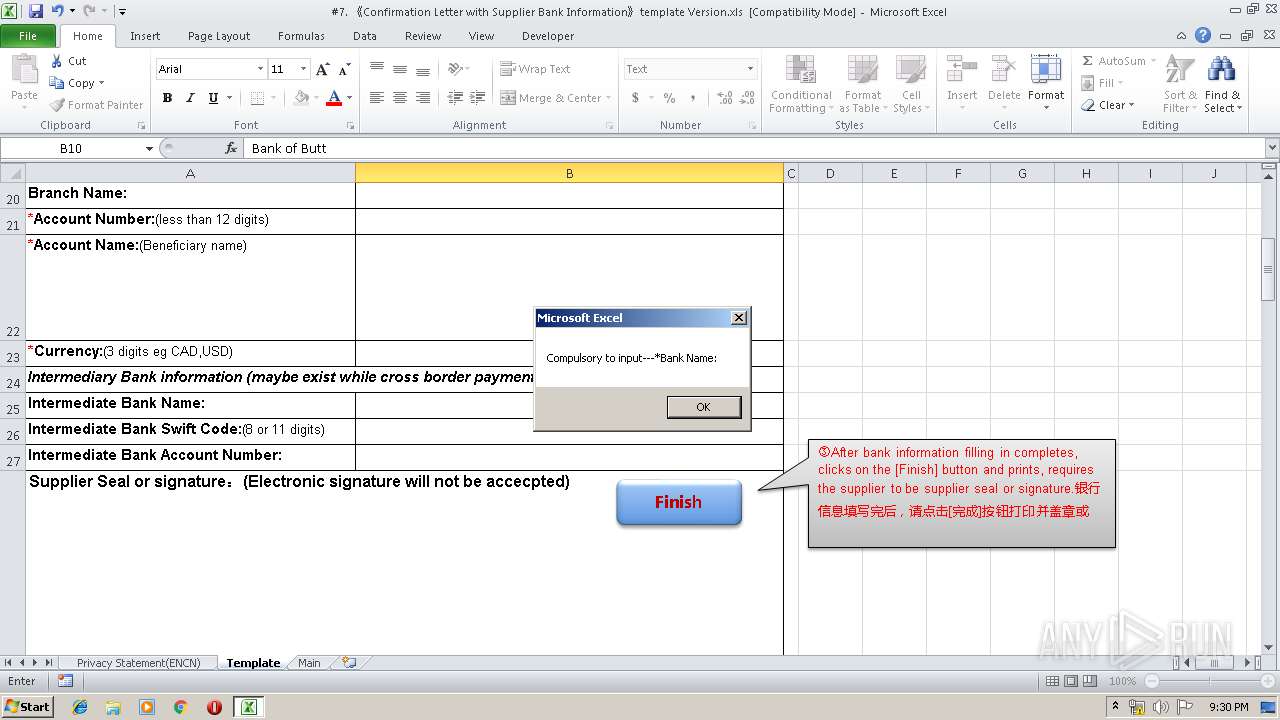
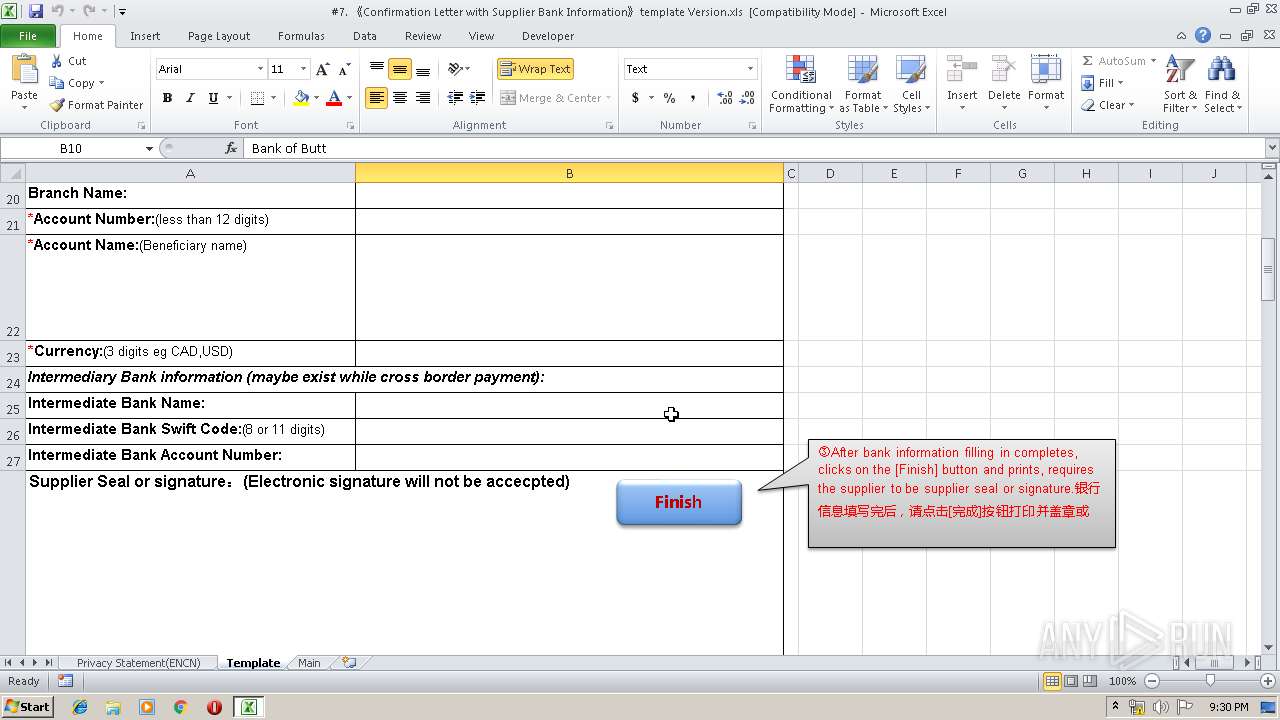
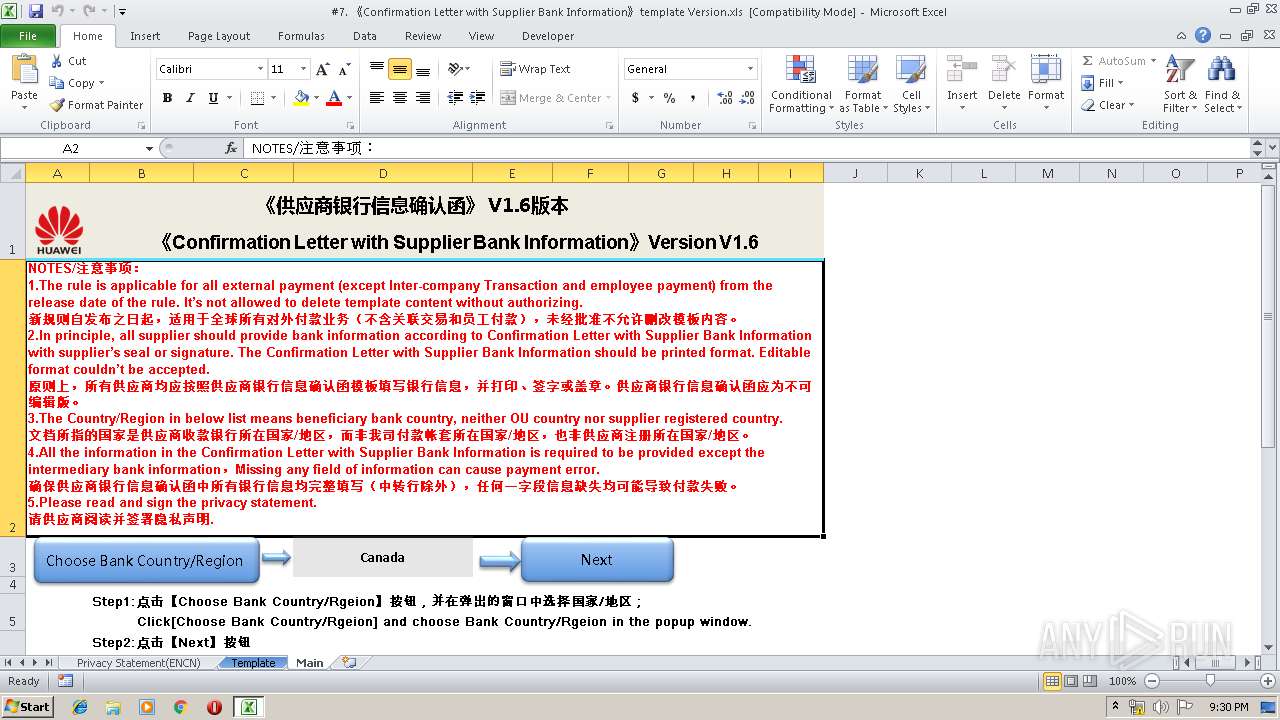
| File name: | #7. 《Confirmation Letter with Supplier Bank Information》template Version.xls |
| Full analysis: | https://app.any.run/tasks/aa7aed69-24f1-4e45-8de7-7ab49a6c65a2 |
| Verdict: | No threats detected |
| Analysis date: | October 09, 2019, 20:28:23 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/vnd.ms-excel |
| File info: | Composite Document File V2 Document, Little Endian, Os: Windows, Version 10.0, Code page: 1252, Author: lwx198215, Last Saved By: Jiemin Liu, Name of Creating Application: Microsoft Excel, Last Printed: Thu Nov 8 03:10:40 2018, Create Time/Date: Tue May 10 07:12:41 2016, Last Saved Time/Date: Tue Mar 12 00:16:25 2019, Security: 0 |
| MD5: | FA2E60D638BC39048229D1495C3C0431 |
| SHA1: | 40D32CA7159E1B370132AEF44CF87C6DEB9161DB |
| SHA256: | 8F2A8BD7BA99A7AB4D8A873974E04EC0E06CDB954242452D6FBB72CE775811FA |
| SSDEEP: | 49152:LWvUMDcwRHH5XN6umNxDV+sfO7+v77RSTuemT6fzURgD3zIQthrbf0/HP2nbfdQl:idHtNZKxf10IQnr+P2uEBHoiP |
MALICIOUS
No malicious indicators.SUSPICIOUS
Application launched itself
- EXCEL.EXE (PID: 3568)
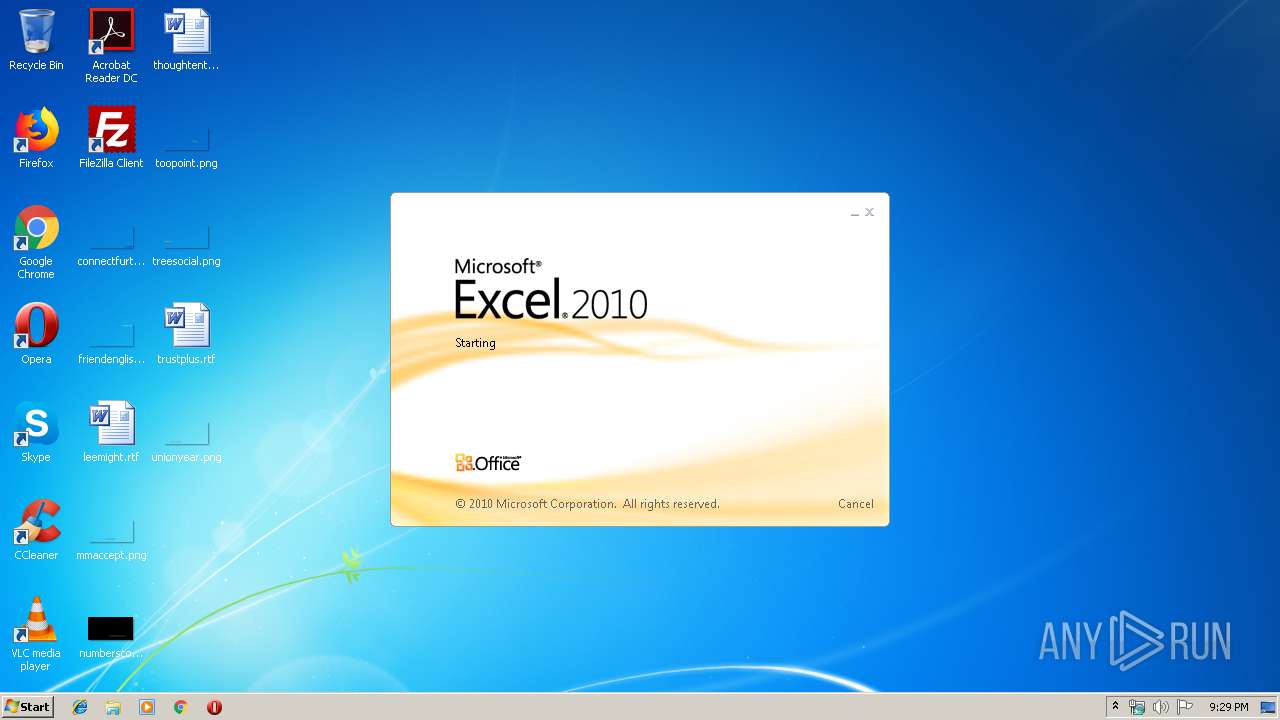
Starts Microsoft Office Application
- EXCEL.EXE (PID: 3568)
INFO
Reads Microsoft Office registry keys
- EXCEL.EXE (PID: 3172)
- EXCEL.EXE (PID: 3568)
Creates files in the user directory
- EXCEL.EXE (PID: 3568)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .xls | | | Microsoft Excel sheet (31.2) |
|---|---|---|
| .xls | | | Microsoft Excel sheet (alternate) (25.5) |
EXIF
FlashPix
| Author: | lwx198215 |
|---|---|
| LastModifiedBy: | Jiemin Liu |
| Software: | Microsoft Excel |
| LastPrinted: | 2018:11:08 03:10:40 |
| CreateDate: | 2016:05:10 06:12:41 |
| ModifyDate: | 2019:03:12 00:16:25 |
| Security: | None |
| Company: | Huawei Technologies Co.,Ltd. |
| AppVersion: | 15 |
| ScaleCrop: | No |
| LinksUpToDate: | No |
| SharedDoc: | No |
| HyperlinksChanged: | No |
| TitleOfParts: |
|
| HeadingPairs: |
|
| CodePage: | Windows Latin 1 (Western European) |
| Hyperlinks: |
|
| Tag_2015_ms_pID_725343: | (3)Rw/AUqRXKzKKsUlnTP+3XKT1WYyya9cxhmr5y3Bq0ijf2zxzHlj6X8J6XHG1VPXaarJ3enMq 4F7NjzpOucEx/V4+tHceiGUC3CIoDzNbnrnykI08zcIEkljcWFCePGMqYlmN5u0IIrhfX+j1 Y6iKajLnG7XUUnFSiJZjEPehyJ10rjV1iQNzk1gPhgE74w8ogFurBFflo+O4pOks8If0SrcF MSrIrA4dUA+KzC00Lg |
| Tag_2015_ms_pID_7253431: | GpCnAxPVKzBBq1uSpo0swQeAdu+9hNO9L33vandAbeivolDblio7a6 YAea19RTyBD/btXA11fd5WX5BW/SDOixBf4ubZyWf+cebym+9lHQIiXOhh6kVnZu3FbBPnij MRpP7SLERpC3CcaCTUDHs4dwE0vqjmJhL8hf3OFKKevdRkSpe1HOTvghjycJrbYkGhg9jO0G scS2gZD8v+DVkMJ6qQjMGatsZoH7CDt8DI7b |
| Tag_2015_ms_pID_7253432: | dGWPWf7jvIDX9ejTWu/WuDQLcHWDDRaSZ1HU x7bDJqV91sWZ0aWysx5wn+V8HfPa/zmwlOezfpn5sgzLLSnCBXE= |
| Tag_2015_ms_pID_725343_00: | _2015_ms_pID_725343 |
| Tag_2015_ms_pID_7253431_00: | _2015_ms_pID_7253431 |
| Tag_2015_ms_pID_7253432_00: | _2015_ms_pID_7253432 |
| Tag_readonly: | - |
| Tag_change: | - |
| Tag_full-control: | - |
| Sflag: | 1532912726 |
| CompObjUserTypeLen: | 31 |
| CompObjUserType: | Microsoft Excel 2003 Worksheet |
Total processes
34
Monitored processes
2
Malicious processes
0
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 3172 | "C:\Program Files\Microsoft Office\Office14\EXCEL.EXE" /Embedding | C:\Program Files\Microsoft Office\Office14\EXCEL.EXE | — | EXCEL.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Excel Exit code: 0 Version: 14.0.6024.1000 Modules
| |||||||||||||||
| 3568 | "C:\Program Files\Microsoft Office\Office14\EXCEL.EXE" /dde | C:\Program Files\Microsoft Office\Office14\EXCEL.EXE | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Excel Exit code: 0 Version: 14.0.6024.1000 Modules
| |||||||||||||||
Total events
1 178
Read events
1 025
Write events
134
Delete events
19
Modification events
| (PID) Process: | (3568) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Excel\Resiliency\StartupItems |
| Operation: | write | Name: | b!> |
Value: 62213E00F00D0000010000000000000000000000 | |||
| (PID) Process: | (3568) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1033 |
Value: Off | |||
| (PID) Process: | (3568) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1033 |
Value: On | |||
| (PID) Process: | (3568) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Excel |
| Operation: | write | Name: | MTTT |
Value: F00D00004C59C649E07ED50100000000 | |||
| (PID) Process: | (3568) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Excel\Resiliency\StartupItems |
| Operation: | delete value | Name: | b!> |
Value: 62213E00F00D0000010000000000000000000000 | |||
| (PID) Process: | (3568) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Excel\Resiliency\StartupItems |
| Operation: | delete key | Name: | |
Value: | |||
| (PID) Process: | (3568) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Excel\Resiliency |
| Operation: | delete key | Name: | |
Value: | |||
| (PID) Process: | (3568) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
| (PID) Process: | (3568) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 1 | |||
| (PID) Process: | (3568) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Excel\Resiliency\DocumentRecovery\1026A5 |
| Operation: | write | Name: | 1026A5 |
Value: 04000000F00D00006E00000043003A005C00550073006500720073005C00610064006D0069006E005C0041007000700044006100740061005C004C006F00630061006C005C00540065006D0070005C00230037002E0020000A3043006F006E006600690072006D006100740069006F006E0020004C006500740074006500720020007700690074006800200053007500700070006C006900650072002000420061006E006B00200049006E0066006F0072006D006100740069006F006E000B30740065006D0070006C006100740065002000560065007200730069006F006E002E0078006C007300000000002200000043003A005C00550073006500720073005C00610064006D0069006E005C0041007000700044006100740061005C004C006F00630061006C005C00540065006D0070005C000100000000000000A004B74AE07ED501A5261000A526100000000000AC020000001000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
Executable files
0
Suspicious files
1
Text files
1
Unknown types
3
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3568 | EXCEL.EXE | C:\Users\admin\AppData\Local\Temp\CVR21E2.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 3568 | EXCEL.EXE | C:\Users\admin\AppData\Local\Temp\Excel\#7. 《Confirmation Letter with Supplier Bank Information》template Version.xls | — | |
MD5:— | SHA256:— | |||
| 3568 | EXCEL.EXE | C:\Users\admin\AppData\Local\Temp\~DF340CCD3647D9B944.TMP | — | |
MD5:— | SHA256:— | |||
| 3568 | EXCEL.EXE | C:\Users\admin\AppData\Local\Temp\#7. 《Confirmation Letter with Supplier Bank Information》template Version.xls | — | |
MD5:— | SHA256:— | |||
| 3568 | EXCEL.EXE | C:\Users\admin\AppData\Local\Temp\OICE_2BBBED8A-06C8-472D-AD58-A85AB59B4EE0.0\32E241B5.xls | — | |
MD5:— | SHA256:— | |||
| 3172 | EXCEL.EXE | C:\Users\admin\AppData\Local\Temp\OICE_2BBBED8A-06C8-472D-AD58-A85AB59B4EE0.0\~DF1B8F5F81035CF246.TMP | — | |
MD5:— | SHA256:— | |||
| 3172 | EXCEL.EXE | C:\Users\admin\AppData\Local\Temp\OICE_2BBBED8A-06C8-472D-AD58-A85AB59B4EE0.0\~DF046FEDCABCF81563.TMP | — | |
MD5:— | SHA256:— | |||
| 3568 | EXCEL.EXE | C:\Users\admin\Documents\VB760E.tmp | — | |
MD5:— | SHA256:— | |||
| 3568 | EXCEL.EXE | C:\Users\admin\AppData\Local\Temp\VB760D.tmp | — | |
MD5:— | SHA256:— | |||
| 3172 | EXCEL.EXE | C:\Users\admin\AppData\Local\Temp\OICE_2BBBED8A-06C8-472D-AD58-A85AB59B4EE0.0\mso2FCC.tmp | compressed | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
0
DNS requests
0
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report