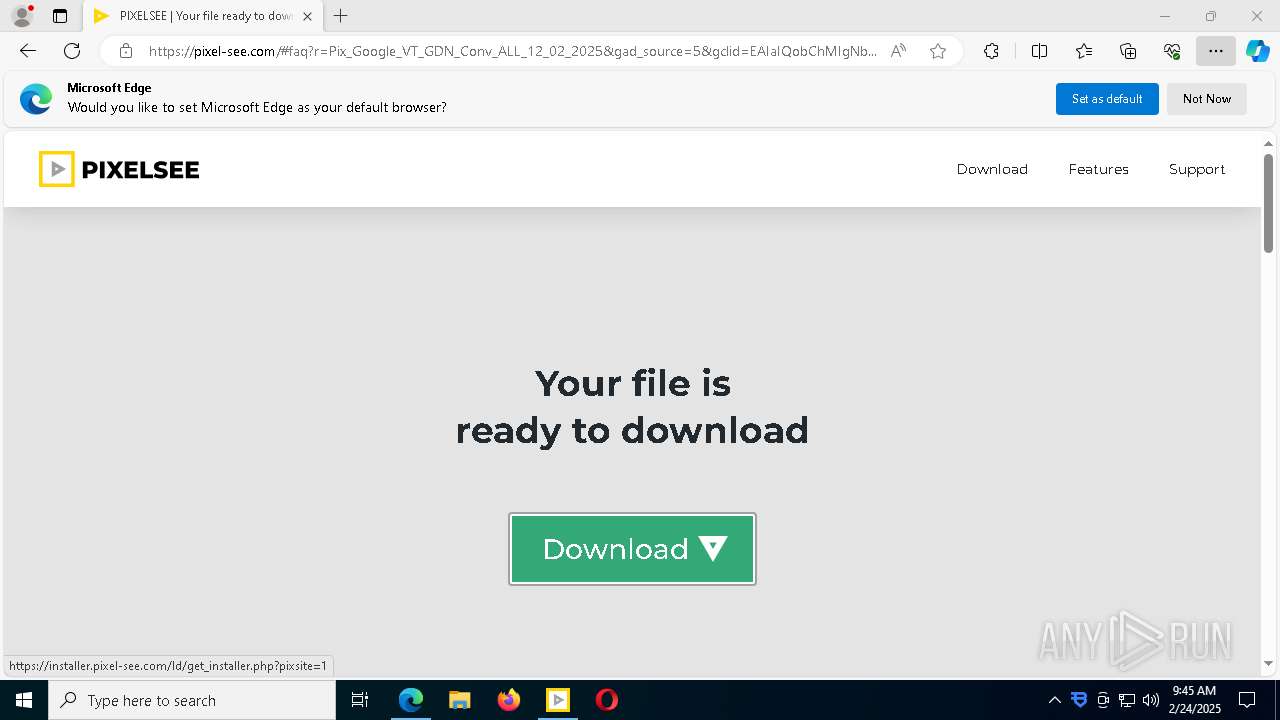
| URL: | https://eraser.heidi.ie/ |
| Full analysis: | https://app.any.run/tasks/5397eed5-883a-4aea-b111-61eb5db955a9 |
| Verdict: | Malicious activity |
| Threats: | A loader is malicious software that infiltrates devices to deliver malicious payloads. This malware is capable of infecting victims’ computers, analyzing their system information, and installing other types of threats, such as trojans or stealers. Criminals usually deliver loaders through phishing emails and links by relying on social engineering to trick users into downloading and running their executables. Loaders employ advanced evasion and persistence tactics to avoid detection. |
| Analysis date: | February 24, 2025, 09:40:59 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MD5: | 1121E9F183CC5B4785C5871119D2FF47 |
| SHA1: | 305958F7196B4F47A6513AADEFE82FE5A9222F16 |
| SHA256: | 8F25436033427B44746BC674F0122F96C6A1AD9548BB2AD0D0FECC0C559E0C61 |
| SSDEEP: | 3:N8NbSMBMLMAK:2Nb/Bf |
MALICIOUS
Actions looks like stealing of personal data
- PixelSee_id2881843id.exe (PID: 6204)
Executing a file with an untrusted certificate
- PixelSee_id2881843id.exe (PID: 6204)
- lum_inst.exe (PID: 7824)
- luminati-m-controller.exe (PID: 4504)
- luminati-m-controller.exe (PID: 6168)
- antivirus360.exe (PID: 904)
Changes the autorun value in the registry
- pixelsee.exe (PID: 4228)
Starts NET.EXE for service management
- bdvpn_setup.exe (PID: 7200)
- net.exe (PID: 4536)
SUSPICIOUS
Reads security settings of Internet Explorer
- PixelSee_id2881843id.exe (PID: 6204)
- lum_inst.tmp (PID: 7064)
- luminati-m-controller.exe (PID: 4504)
- bdvpn_setup.exe (PID: 7200)
- brightvpn_installer.exe (PID: 4444)
- antivirus360.exe (PID: 904)
- net_updater32.exe (PID: 7512)
- setup.exe (PID: 7940)
Reads Microsoft Outlook installation path
- PixelSee_id2881843id.exe (PID: 6204)
Process drops legitimate windows executable
- PixelSee_id2881843id.exe (PID: 6204)
- luminati-m-controller.exe (PID: 4504)
- net_updater32.exe (PID: 7512)
- bdvpn_setup.exe (PID: 7200)
- Assistant_117.0.5408.35_Setup.exe_sfx.exe (PID: 7048)
- 360TS_Setup.exe (PID: 1864)
- assistant_installer.exe (PID: 5208)
Reads Internet Explorer settings
- PixelSee_id2881843id.exe (PID: 6204)
Executable content was dropped or overwritten
- PixelSee_id2881843id.exe (PID: 6204)
- lum_inst.exe (PID: 7824)
- lum_inst.tmp (PID: 7064)
- luminati-m-controller.exe (PID: 4504)
- net_updater32.exe (PID: 2280)
- luminati-m-controller.exe (PID: 6168)
- bdvpn_setup.exe (PID: 7200)
- antivirus360.exe (PID: 904)
- opera_binst.exe (PID: 2928)
- setup.exe (PID: 7940)
- setup.exe (PID: 4976)
- setup.exe (PID: 4188)
- setup.exe (PID: 776)
- net_updater32.exe (PID: 7512)
- setup.exe (PID: 1792)
- 360TS_Setup.exe (PID: 7540)
- 360TS_Setup.exe (PID: 1864)
- Assistant_117.0.5408.35_Setup.exe_sfx.exe (PID: 7048)
- Bright VPN.exe (PID: 1804)
- net_updater32.exe (PID: 4996)
- installer.exe (PID: 7444)
- installer.exe (PID: 1412)
- assistant_installer.exe (PID: 5208)
The process drops C-runtime libraries
- PixelSee_id2881843id.exe (PID: 6204)
- luminati-m-controller.exe (PID: 4504)
- net_updater32.exe (PID: 7512)
Creates a software uninstall entry
- PixelSee_id2881843id.exe (PID: 6204)
- bdvpn_setup.exe (PID: 7200)
Reads the Windows owner or organization settings
- lum_inst.tmp (PID: 7064)
Detected use of alternative data streams (AltDS)
- luminati-m-controller.exe (PID: 4504)
- net_updater32.exe (PID: 2280)
Executes as Windows Service
- net_updater32.exe (PID: 2280)
- WmiApSrv.exe (PID: 7224)
- net_updater32.exe (PID: 4996)
- WmiApSrv.exe (PID: 5836)
Checks Windows Trust Settings
- net_updater32.exe (PID: 2280)
- bdvpn_setup.exe (PID: 7200)
- net_updater32.exe (PID: 7512)
- setup.exe (PID: 7940)
The process checks if it is being run in the virtual environment
- net_updater32.exe (PID: 2280)
Checks for external IP
- net_updater32.exe (PID: 2280)
- net_updater32.exe (PID: 4996)
Malware-specific behavior (creating "System.dll" in Temp)
- bdvpn_setup.exe (PID: 7200)
Process requests binary or script from the Internet
- antivirus360.exe (PID: 904)
Potential Corporate Privacy Violation
- antivirus360.exe (PID: 904)
Starts itself from another location
- setup.exe (PID: 7940)
- 360TS_Setup.exe (PID: 7540)
Application launched itself
- net_updater32.exe (PID: 3032)
- setup.exe (PID: 7940)
- setup.exe (PID: 776)
- net_updater32.exe (PID: 7512)
- assistant_installer.exe (PID: 7644)
- installer.exe (PID: 1412)
- Bright VPN.exe (PID: 1804)
- assistant_installer.exe (PID: 5208)
- opera.exe (PID: 8372)
- assistant_installer.exe (PID: 8228)
- browser_assistant.exe (PID: 8300)
- opera.exe (PID: 8788)
Uses NETSH.EXE to add a firewall rule or allowed programs
- PixelSee_id2881843id.exe (PID: 6204)
Drops 7-zip archiver for unpacking
- bdvpn_setup.exe (PID: 7200)
- 360TS_Setup.exe (PID: 1864)
Starts CMD.EXE for commands execution
- Bright VPN.exe (PID: 1804)
INFO
Checks supported languages
- identity_helper.exe (PID: 6864)
- PixelSee_id2881843id.exe (PID: 6204)
- lum_inst.exe (PID: 7824)
- lum_inst.tmp (PID: 7064)
- luminati-m-controller.exe (PID: 4504)
- test_wpf.exe (PID: 1856)
- net_updater32.exe (PID: 2224)
- net_updater32.exe (PID: 2280)
- test_wpf.exe (PID: 5040)
- idle_report.exe (PID: 5200)
- pixelsee.exe (PID: 4228)
- brightdata.exe (PID: 7968)
- pixelsee_crashpad_handler.exe (PID: 6984)
- luminati-m-controller.exe (PID: 6168)
- bdvpn_setup.exe (PID: 7200)
- test_wpf.exe (PID: 5460)
- brightvpn_installer.exe (PID: 4444)
- opera_binst.exe (PID: 2928)
- setup.exe (PID: 4976)
- net_updater32.exe (PID: 3032)
- net_updater32.exe (PID: 7512)
- setup.exe (PID: 4188)
- setup.exe (PID: 7940)
- setup.exe (PID: 776)
- setup.exe (PID: 1792)
- net_updater32.exe (PID: 7048)
- antivirus360.exe (PID: 904)
- 360TS_Setup.exe (PID: 7540)
- 360TS_Setup.exe (PID: 1864)
- idle_report.exe (PID: 5988)
- Bright VPN.exe (PID: 1804)
- Bright VPN.exe (PID: 5616)
- test_wpf.exe (PID: 7296)
The sample compiled with english language support
- msedge.exe (PID: 6408)
- PixelSee_id2881843id.exe (PID: 6204)
- msedge.exe (PID: 6096)
- msedge.exe (PID: 7324)
- lum_inst.tmp (PID: 7064)
- luminati-m-controller.exe (PID: 4504)
- opera_binst.exe (PID: 2928)
- antivirus360.exe (PID: 904)
- setup.exe (PID: 7940)
- setup.exe (PID: 4976)
- setup.exe (PID: 4188)
- setup.exe (PID: 776)
- setup.exe (PID: 1792)
- net_updater32.exe (PID: 7512)
- bdvpn_setup.exe (PID: 7200)
- Assistant_117.0.5408.35_Setup.exe_sfx.exe (PID: 7048)
- 360TS_Setup.exe (PID: 1864)
- installer.exe (PID: 7444)
- assistant_installer.exe (PID: 5208)
- installer.exe (PID: 1412)
Reads Environment values
- identity_helper.exe (PID: 6864)
Create files in a temporary directory
- PixelSee_id2881843id.exe (PID: 6204)
- lum_inst.tmp (PID: 7064)
- lum_inst.exe (PID: 7824)
Checks proxy server information
- PixelSee_id2881843id.exe (PID: 6204)
- luminati-m-controller.exe (PID: 4504)
- pixelsee.exe (PID: 4228)
- bdvpn_setup.exe (PID: 7200)
- brightvpn_installer.exe (PID: 4444)
- antivirus360.exe (PID: 904)
- setup.exe (PID: 7940)
- net_updater32.exe (PID: 7512)
- 360TS_Setup.exe (PID: 1864)
- Bright VPN.exe (PID: 1804)
Reads the computer name
- identity_helper.exe (PID: 6864)
- PixelSee_id2881843id.exe (PID: 6204)
- lum_inst.tmp (PID: 7064)
- luminati-m-controller.exe (PID: 4504)
- test_wpf.exe (PID: 1856)
- net_updater32.exe (PID: 2224)
- net_updater32.exe (PID: 2280)
- test_wpf.exe (PID: 5040)
- idle_report.exe (PID: 5200)
- brightdata.exe (PID: 7968)
- bdvpn_setup.exe (PID: 7200)
- test_wpf.exe (PID: 5460)
- luminati-m-controller.exe (PID: 6168)
- brightvpn_installer.exe (PID: 4444)
- antivirus360.exe (PID: 904)
- setup.exe (PID: 7940)
- net_updater32.exe (PID: 7512)
- setup.exe (PID: 776)
- net_updater32.exe (PID: 7048)
- 360TS_Setup.exe (PID: 1864)
- Bright VPN.exe (PID: 1804)
- Bright VPN.exe (PID: 4128)
- pixelsee.exe (PID: 4228)
Executable content was dropped or overwritten
- msedge.exe (PID: 6096)
- msedge.exe (PID: 6408)
- msedge.exe (PID: 7324)
Process checks computer location settings
- PixelSee_id2881843id.exe (PID: 6204)
- lum_inst.tmp (PID: 7064)
- luminati-m-controller.exe (PID: 4504)
- net_updater32.exe (PID: 2280)
- net_updater32.exe (PID: 7512)
- antivirus360.exe (PID: 904)
- 360TS_Setup.exe (PID: 1864)
- luminati-m-controller.exe (PID: 6168)
- Bright VPN.exe (PID: 1804)
Creates files or folders in the user directory
- PixelSee_id2881843id.exe (PID: 6204)
- luminati-m-controller.exe (PID: 4504)
- pixelsee.exe (PID: 4228)
- pixelsee_crashpad_handler.exe (PID: 6984)
Application launched itself
- msedge.exe (PID: 6096)
Creates files in the program directory
- luminati-m-controller.exe (PID: 4504)
- net_updater32.exe (PID: 2280)
- net_updater32.exe (PID: 2224)
- brightdata.exe (PID: 7968)
- luminati-m-controller.exe (PID: 6168)
Reads the machine GUID from the registry
- luminati-m-controller.exe (PID: 4504)
- test_wpf.exe (PID: 1856)
- net_updater32.exe (PID: 2280)
- test_wpf.exe (PID: 5040)
- idle_report.exe (PID: 5200)
- brightdata.exe (PID: 7968)
- pixelsee.exe (PID: 4228)
- luminati-m-controller.exe (PID: 6168)
- test_wpf.exe (PID: 5460)
- bdvpn_setup.exe (PID: 7200)
- brightvpn_installer.exe (PID: 4444)
- antivirus360.exe (PID: 904)
- net_updater32.exe (PID: 7512)
- setup.exe (PID: 7940)
- test_wpf.exe (PID: 7296)
- Bright VPN.exe (PID: 1804)
Reads the software policy settings
- luminati-m-controller.exe (PID: 4504)
- net_updater32.exe (PID: 2224)
- net_updater32.exe (PID: 2280)
- luminati-m-controller.exe (PID: 6168)
- bdvpn_setup.exe (PID: 7200)
- brightvpn_installer.exe (PID: 4444)
- setup.exe (PID: 7940)
- net_updater32.exe (PID: 7512)
- net_updater32.exe (PID: 7048)
- 360TS_Setup.exe (PID: 1864)
- net_updater32.exe (PID: 4996)
Disables trace logs
- luminati-m-controller.exe (PID: 4504)
- net_updater32.exe (PID: 2280)
- brightvpn_installer.exe (PID: 4444)
- antivirus360.exe (PID: 904)
- net_updater32.exe (PID: 7512)
Compiled with Borland Delphi (YARA)
- lum_inst.exe (PID: 7824)
- lum_inst.tmp (PID: 7064)
Detects InnoSetup installer (YARA)
- lum_inst.tmp (PID: 7064)
- lum_inst.exe (PID: 7824)
Reads CPU info
- net_updater32.exe (PID: 2280)
Reads the time zone
- net_updater32.exe (PID: 2280)
The sample compiled with chinese language support
- 360TS_Setup.exe (PID: 7540)
- 360TS_Setup.exe (PID: 1864)
The sample compiled with turkish language support
- 360TS_Setup.exe (PID: 1864)
Manual execution by a user
- Bright VPN.exe (PID: 1804)
- assistant_installer.exe (PID: 8228)
- opera.exe (PID: 8788)
The sample compiled with russian language support
- 360TS_Setup.exe (PID: 1864)
OPERA mutex has been found
- opera.exe (PID: 8372)
- browser_assistant.exe (PID: 8300)
- opera.exe (PID: 8788)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
303
Monitored processes
170
Malicious processes
11
Suspicious processes
10
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 624 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=entity_extraction_service.mojom.Extractor --lang=en-US --service-sandbox-type=entity_extraction --onnx-enabled-for-ee --no-appcompat-clear --mojo-platform-channel-handle=5852 --field-trial-handle=2456,i,4082737090409648929,18246508234716892314,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 624 | C:\WINDOWS\SysWOW64\DllHost.exe /Processid:{60A90A2F-858D-42AF-8929-82BE9D99E8A1} | C:\Windows\SysWOW64\dllhost.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: COM Surrogate Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 776 | "C:\Users\admin\AppData\Local\Temp\7zS07BA3756\setup.exe" --backend --install --import-browser-data=0 --enable-crash-reporting=1 --enable-stats=1 --enable-installer-stats=1 --consent-given=0 --general-interests=0 --general-location=0 --personalized-content=0 --personalized-ads=0 --launchopera=1 --showunbox=0 --installfolder="C:\Users\admin\AppData\Local\Programs\Opera" --profile-folder --language=en --singleprofile=0 --copyonly=0 --allusers=0 --setdefaultbrowser=1 --pintotaskbar=1 --pintostartmenu=1 --run-at-startup=1 --show-intro-overlay --server-tracking-data=server_tracking_data --initial-pid=7940 --package-dir-prefix="C:\Users\admin\AppData\Local\Temp\.opera\Opera Installer Temp\opera_package_20250224094404" --session-guid=92fc78f5-d44c-4e3a-8444-b61cbb12c886 --server-tracking-blob="ZTc4MzI5NzYwOTU2OTIyNGMxZWIzOTQ0ZDMwYzUxNjVhOTVhYzY1ZjE2NWJlZmY5ODZiNzE3NDMxOTUzYWQyODp7ImNvdW50cnkiOiJVUyIsImluc3RhbGxlcl9uYW1lIjoiT3BlcmFTZXR1cC5leGUiLCJwcm9kdWN0Ijp7Im5hbWUiOiJvcGVyYSJ9LCJxdWVyeSI6Ii9vcGVyYS9zdGFibGUvd2luZG93cz91dG1fc291cmNlPW1ndCZ1dG1fbWVkaXVtPWFwYiZ1dG1fY2FtcGFpZ249cGl4ZWwyIiwic3lzdGVtIjp7InBsYXRmb3JtIjp7ImFyY2giOiJ4ODZfNjQiLCJvcHN5cyI6IldpbmRvd3MiLCJvcHN5cy12ZXJzaW9uIjoiMTAiLCJwYWNrYWdlIjoiRVhFIn19LCJ0aW1lc3RhbXAiOiIxNzQwMzkwMjQxLjI4MzMiLCJ1c2VyYWdlbnQiOiJNb3ppbGxhLzUuMCAoV2luZG93cyBOVCAxMC4wOyBXaW42NDsgeDY0KSBBcHBsZVdlYktpdC81MzcuMzYgKEtIVE1MLCBsaWtlIEdlY2tvKSBDaHJvbWUvMTE0LjAuMC4wIFNhZmFyaS81MzcuMzYiLCJ1dG0iOnsiY2FtcGFpZ24iOiJwaXhlbDIiLCJtZWRpdW0iOiJhcGIiLCJzb3VyY2UiOiJtZ3QifSwidXVpZCI6ImUzZDIwMzU3LWZjNDYtNDA5Yi1iZWRkLWVkZDcxNzE1ZDgyNiJ9 " --silent --desktopshortcut=1 --wait-for-package --initial-proc-handle=D005000000000000 | C:\Users\admin\AppData\Local\Temp\7zS07BA3756\setup.exe | setup.exe | ||||||||||||
User: admin Company: Opera Software Integrity Level: HIGH Description: Opera Installer Exit code: 0 Version: 117.0.5408.35 Modules
| |||||||||||||||
| 904 | "C:\Users\admin\AppData\Local\Temp\antivirus360\antivirus360.exe" /s | C:\Users\admin\AppData\Local\Temp\antivirus360\antivirus360.exe | PixelSee_id2881843id.exe | ||||||||||||
User: admin Company: Qihoo 360 Technology Co. Ltd. Integrity Level: HIGH Description: 360 Total Security Online Installer Exit code: 1 Version: 6, 6, 0, 1060 Modules
| |||||||||||||||
| 1292 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=unzip.mojom.Unzipper --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=6048 --field-trial-handle=2456,i,4082737090409648929,18246508234716892314,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 1412 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=renderer --no-appcompat-clear --disable-gpu-compositing --lang=en-US --js-flags=--ms-user-locale= --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=25 --mojo-platform-channel-handle=6604 --field-trial-handle=2456,i,4082737090409648929,18246508234716892314,262144 --variations-seed-version /prefetch:1 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 1412 | "C:\Users\admin\AppData\Local\Programs\Opera\117.0.5408.35\installer.exe" --backend --initial-pid=7940 --install --import-browser-data=0 --enable-crash-reporting=1 --enable-stats=1 --enable-installer-stats=1 --consent-given=0 --general-interests=0 --general-location=0 --personalized-content=0 --personalized-ads=0 --launchopera=1 --showunbox=0 --installfolder="C:\Users\admin\AppData\Local\Programs\Opera" --profile-folder --language=en --singleprofile=0 --copyonly=0 --allusers=0 --setdefaultbrowser=1 --pintotaskbar=1 --pintostartmenu=1 --run-at-startup=1 --server-tracking-data=server_tracking_data --show-intro-overlay --package-dir="C:\Users\admin\AppData\Local\Temp\.opera\Opera Installer Temp\opera_package_202502240944041" --session-guid=92fc78f5-d44c-4e3a-8444-b61cbb12c886 --server-tracking-blob="ZTc4MzI5NzYwOTU2OTIyNGMxZWIzOTQ0ZDMwYzUxNjVhOTVhYzY1ZjE2NWJlZmY5ODZiNzE3NDMxOTUzYWQyODp7ImNvdW50cnkiOiJVUyIsImluc3RhbGxlcl9uYW1lIjoiT3BlcmFTZXR1cC5leGUiLCJwcm9kdWN0Ijp7Im5hbWUiOiJvcGVyYSJ9LCJxdWVyeSI6Ii9vcGVyYS9zdGFibGUvd2luZG93cz91dG1fc291cmNlPW1ndCZ1dG1fbWVkaXVtPWFwYiZ1dG1fY2FtcGFpZ249cGl4ZWwyIiwic3lzdGVtIjp7InBsYXRmb3JtIjp7ImFyY2giOiJ4ODZfNjQiLCJvcHN5cyI6IldpbmRvd3MiLCJvcHN5cy12ZXJzaW9uIjoiMTAiLCJwYWNrYWdlIjoiRVhFIn19LCJ0aW1lc3RhbXAiOiIxNzQwMzkwMjQxLjI4MzMiLCJ1c2VyYWdlbnQiOiJNb3ppbGxhLzUuMCAoV2luZG93cyBOVCAxMC4wOyBXaW42NDsgeDY0KSBBcHBsZVdlYktpdC81MzcuMzYgKEtIVE1MLCBsaWtlIEdlY2tvKSBDaHJvbWUvMTE0LjAuMC4wIFNhZmFyaS81MzcuMzYiLCJ1dG0iOnsiY2FtcGFpZ24iOiJwaXhlbDIiLCJtZWRpdW0iOiJhcGIiLCJzb3VyY2UiOiJtZ3QifSwidXVpZCI6ImUzZDIwMzU3LWZjNDYtNDA5Yi1iZWRkLWVkZDcxNzE1ZDgyNiJ9 " --silent --desktopshortcut=1 --install-subfolder=117.0.5408.35 | C:\Users\admin\AppData\Local\Programs\Opera\117.0.5408.35\installer.exe | setup.exe | ||||||||||||
User: admin Company: Opera Software Integrity Level: HIGH Description: Opera Installer Exit code: 0 Version: 117.0.5408.35 Modules
| |||||||||||||||
| 1496 | C:\ProgramData\BrightData\b85f5ef603041f1fc4e7f943c177a0d440a01266\idle_report.exe --id 50367 | C:\ProgramData\BrightData\b85f5ef603041f1fc4e7f943c177a0d440a01266\idle_report.exe | — | net_updater32.exe | |||||||||||
User: admin Company: BrightData Ltd. Integrity Level: MEDIUM Description: idle_report Exit code: 0 Version: 1.474.630 Modules
| |||||||||||||||
| 1792 | C:\Users\admin\AppData\Local\Temp\7zS07BA3756\setup.exe --type=crashpad-handler /prefetch:4 --monitor-self-annotation=ptype=crashpad-handler "--database=C:\Users\admin\AppData\Roaming\Opera Software\Opera Stable\Crash Reports" "--crash-count-file=C:\Users\admin\AppData\Roaming\Opera Software\Opera Stable\crash_count.txt" --url=https://crashstats-collector-2.opera.com/ --annotation=channel=Stable --annotation=plat=Win32 --annotation=prod=OperaDesktop --annotation=ver=117.0.5408.35 --initial-client-data=0x33c,0x340,0x344,0x300,0x348,0x72fb70f4,0x72fb7100,0x72fb710c | C:\Users\admin\AppData\Local\Temp\7zS07BA3756\setup.exe | setup.exe | ||||||||||||
User: admin Company: Opera Software Integrity Level: HIGH Description: Opera Installer Exit code: 0 Version: 117.0.5408.35 Modules
| |||||||||||||||
| 1804 | "C:\Program Files (x86)\Bright VPN\Bright VPN.exe" --install --silent | C:\Program Files (x86)\Bright VPN\Bright VPN.exe | explorer.exe | ||||||||||||
User: admin Company: Bright Data Ltd. Integrity Level: MEDIUM Description: Bright VPN Version: 1.482.985 Modules
| |||||||||||||||
Total events
65 465
Read events
64 822
Write events
536
Delete events
107
Modification events
| (PID) Process: | (6096) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\BLBeacon |
| Operation: | write | Name: | failed_count |
Value: 0 | |||
| (PID) Process: | (6096) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\BLBeacon |
| Operation: | write | Name: | state |
Value: 2 | |||
| (PID) Process: | (6096) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\BLBeacon |
| Operation: | write | Name: | state |
Value: 1 | |||
| (PID) Process: | (6096) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\StabilityMetrics |
| Operation: | write | Name: | user_experience_metrics.stability.exited_cleanly |
Value: 0 | |||
| (PID) Process: | (6096) msedge.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\EdgeUpdate\ClientStateMedium\{56EB18F8-B008-4CBD-B6D2-8C97FE7E9062}\LastWasDefault |
| Operation: | write | Name: | S-1-5-21-1693682860-607145093-2874071422-1001 |
Value: BD380C6C768D2F00 | |||
| (PID) Process: | (6096) msedge.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\EdgeUpdate\ClientStateMedium\{56EB18F8-B008-4CBD-B6D2-8C97FE7E9062}\LastWasDefault |
| Operation: | write | Name: | S-1-5-21-1693682860-607145093-2874071422-1001 |
Value: 220A156C768D2F00 | |||
| (PID) Process: | (6096) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\WindowProperties\393880 |
| Operation: | write | Name: | WindowTabManagerFileMappingId |
Value: {5FFBF32C-C44F-49A6-84D3-BADBBDA8CA6B} | |||
| (PID) Process: | (6096) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\WindowProperties\393880 |
| Operation: | write | Name: | WindowTabManagerFileMappingId |
Value: {5CBFF33D-4B20-4D8B-816F-6A493429D37C} | |||
| (PID) Process: | (6096) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\WindowProperties\393880 |
| Operation: | write | Name: | WindowTabManagerFileMappingId |
Value: {8A4FF819-F09C-41ED-9F2C-90FD68C321C1} | |||
| (PID) Process: | (6096) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\WindowProperties\393880 |
| Operation: | write | Name: | WindowTabManagerFileMappingId |
Value: {D6F9A26A-75BF-4C09-9FFD-3B124C121409} | |||
Executable files
987
Suspicious files
1 429
Text files
475
Unknown types
3
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6096 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\parcel_tracking_db\LOG.old~RF137061.TMP | — | |
MD5:— | SHA256:— | |||
| 6096 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\commerce_subscription_db\LOG.old~RF137061.TMP | — | |
MD5:— | SHA256:— | |||
| 6096 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\discounts_db\LOG.old~RF137061.TMP | — | |
MD5:— | SHA256:— | |||
| 6096 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\commerce_subscription_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 6096 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\discounts_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 6096 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\PersistentOriginTrials\LOG.old~RF137061.TMP | — | |
MD5:— | SHA256:— | |||
| 6096 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\PersistentOriginTrials\LOG.old | — | |
MD5:— | SHA256:— | |||
| 6096 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\parcel_tracking_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 6096 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\EdgePushStorageWithConnectTokenAndKey\LOG.old~RF137061.TMP | — | |
MD5:— | SHA256:— | |||
| 6096 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\EdgePushStorageWithConnectTokenAndKey\LOG.old | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
98
TCP/UDP connections
350
DNS requests
240
Threats
5
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
4712 | MoUsoCoreWorker.exe | GET | 200 | 23.48.23.149:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
7432 | SIHClient.exe | GET | 200 | 92.123.22.101:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
1176 | svchost.exe | GET | 200 | 184.30.131.245:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
— | — | GET | 200 | 184.30.131.245:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
5548 | svchost.exe | GET | 200 | 199.232.210.172:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/fb6dd03b-99d7-4cc8-a878-91c8e655c2d3?P1=1740991809&P2=404&P3=2&P4=hPojhf16%2fCFv6z%2f%2fMlE02PKM1HpvDucs2YIQCbZ%2fdNwJrjJRDAWl6DmJGQfDXRK%2fH%2bLAdFqY%2b5zZz%2fs9o6nv3A%3d%3d | unknown | — | — | whitelisted |
5268 | backgroundTaskHost.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
5548 | svchost.exe | GET | 206 | 199.232.210.172:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/7800e4ef-77a6-478d-979e-60a169311c1e?P1=1740636909&P2=404&P3=2&P4=AdnrWTikMyZsaWmTPAppOV794MozXoEqi6Z15EHCd60DIGZOYCqSIDDp036%2fFOHwC8IEQSBI12lTwWWPP9QmvA%3d%3d | unknown | — | — | whitelisted |
7432 | SIHClient.exe | GET | 200 | 92.123.22.101:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
5548 | svchost.exe | GET | 206 | 199.232.210.172:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/9b9f8fb4-8a65-41e4-bda3-5416858f0aeb?P1=1740397810&P2=404&P3=2&P4=ZwnjjiDRjpO4tCm4FQaSBtaJk3PIA38Qferg%2buje2xW5a%2bHloqq1vnP8GSnqE9WSAtGga1rVOkoXj03QTAFoDw%3d%3d | unknown | — | — | whitelisted |
5548 | svchost.exe | GET | 206 | 199.232.210.172:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/9b9f8fb4-8a65-41e4-bda3-5416858f0aeb?P1=1740397810&P2=404&P3=2&P4=ZwnjjiDRjpO4tCm4FQaSBtaJk3PIA38Qferg%2buje2xW5a%2bHloqq1vnP8GSnqE9WSAtGga1rVOkoXj03QTAFoDw%3d%3d | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
5496 | svchost.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
— | — | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4712 | MoUsoCoreWorker.exe | 23.48.23.149:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
4712 | MoUsoCoreWorker.exe | 23.35.229.160:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
5064 | SearchApp.exe | 92.123.104.34:443 | www.bing.com | Akamai International B.V. | DE | whitelisted |
— | — | 184.30.131.245:80 | ocsp.digicert.com | AKAMAI-AS | US | whitelisted |
6096 | msedge.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
6408 | msedge.exe | 13.107.42.16:443 | config.edge.skype.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
6408 | msedge.exe | 13.107.21.239:443 | edge.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
www.bing.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
config.edge.skype.com |
| whitelisted |
edge.microsoft.com |
| whitelisted |
edge-mobile-static.azureedge.net |
| whitelisted |
eraser.heidi.ie |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2192 | svchost.exe | Misc activity | ET INFO External IP Lookup Domain (ipify .org) in DNS Lookup |
2280 | net_updater32.exe | Misc activity | ET INFO External IP Address Lookup Domain (ipify .org) in TLS SNI |
904 | antivirus360.exe | Potential Corporate Privacy Violation | ET INFO PE EXE or DLL Windows file download HTTP |
904 | antivirus360.exe | Misc activity | ET INFO Packed Executable Download |
4996 | net_updater32.exe | Misc activity | ET INFO External IP Address Lookup Domain (ipify .org) in TLS SNI |
Process | Message |
|---|---|
pixelsee.exe | > __thiscall Application::Application(int &,char *[])
|
pixelsee.exe | os version: "10.0.19045v" __ os name: "Windows 10 Version 2009"
|
pixelsee.exe | > int __thiscall Application::exec(void)
|
pixelsee.exe | > __thiscall PixelseeSettings::PixelseeSettings(void)
|
pixelsee.exe | INSTALL ID: "" _ OLD ID: ""
|
pixelsee.exe | reseller - "" installId ""
|
pixelsee.exe | > void __thiscall PixelseeSettings::flushSettings(void)
|
pixelsee.exe | main libvlc debug: VLC media player - 3.0.16 Vetinari
|
pixelsee.exe | main libvlc debug: Copyright © 1996-2021 the VideoLAN team
|
pixelsee.exe | main libvlc debug: revision 3.0.16-0-g5e70837d8d
|