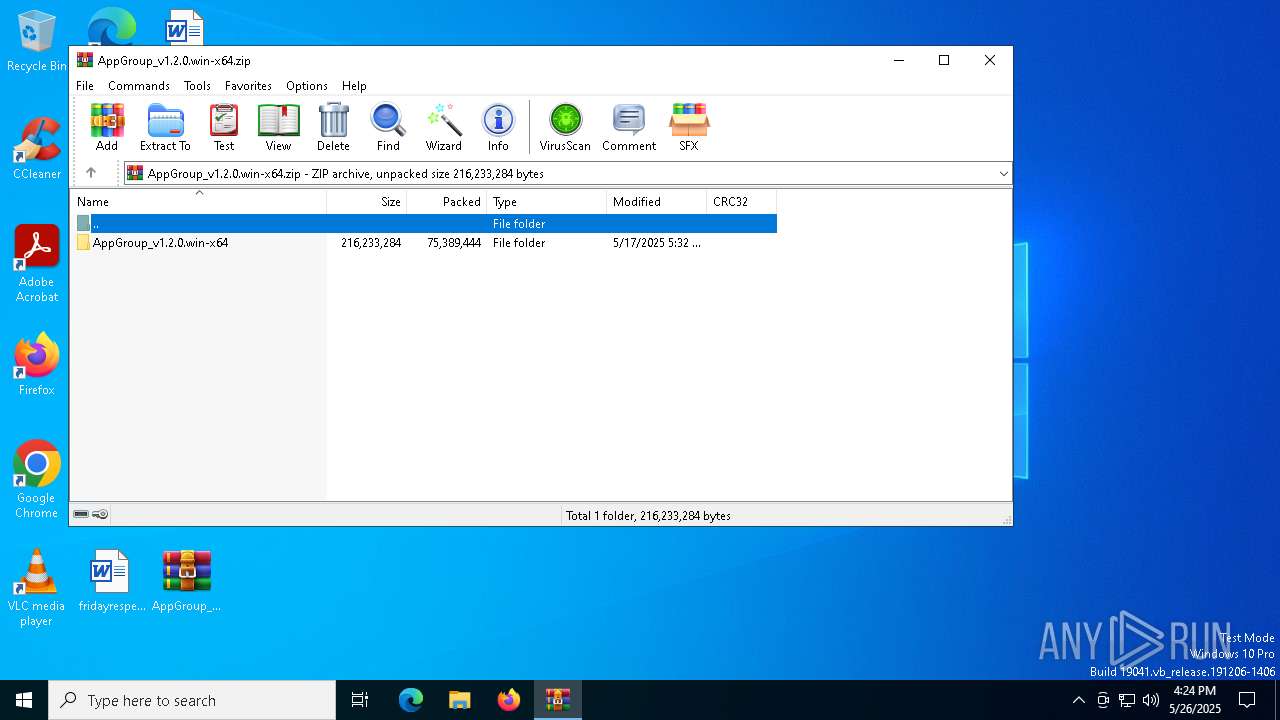
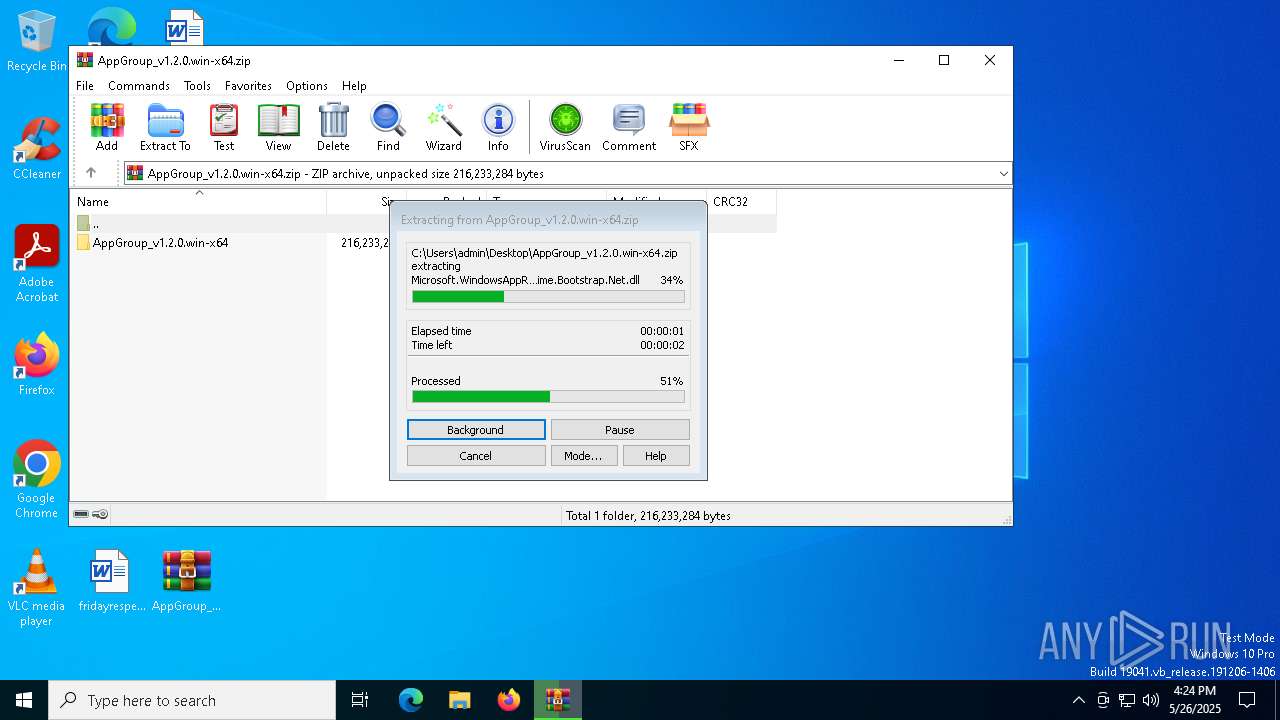
| File name: | AppGroup_v1.2.0.win-x64.zip |
| Full analysis: | https://app.any.run/tasks/4bae1c0c-b6a1-4c41-b1b8-8ea3e1fb0196 |
| Verdict: | Malicious activity |
| Analysis date: | May 26, 2025, 16:23:37 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract, compression method=store |
| MD5: | F68DB09A291D70676851ADF135173D57 |
| SHA1: | 9793B43FC7FAACB14DB2E01016B9E6D8A57FA2A2 |
| SHA256: | 8F17B5A6EDFF0BF74D1ECA8FFCC8A0B97B2E20F1CABB37B059A7BC575CF97353 |
| SSDEEP: | 786432:VqrR6PXIx1ijrA6Uih6MFquEo0Bhi3ushVqB5lKv:srR6PXi1ij06Uih6MFquCBg+sHkKv |
MALICIOUS
No malicious indicators.SUSPICIOUS
Process drops legitimate windows executable
- WinRAR.exe (PID: 6660)
Reads security settings of Internet Explorer
- WinRAR.exe (PID: 6660)
Starts CMD.EXE for commands execution
- WinRAR.exe (PID: 6660)
Executing commands from a ".bat" file
- WinRAR.exe (PID: 6660)
The process creates files with name similar to system file names
- WinRAR.exe (PID: 6660)
INFO
The sample compiled with english language support
- WinRAR.exe (PID: 6660)
The sample compiled with spanish language support
- WinRAR.exe (PID: 6660)
The sample compiled with arabic language support
- WinRAR.exe (PID: 6660)
The sample compiled with bulgarian language support
- WinRAR.exe (PID: 6660)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 6660)
The sample compiled with czech language support
- WinRAR.exe (PID: 6660)
The sample compiled with german language support
- WinRAR.exe (PID: 6660)
The sample compiled with french language support
- WinRAR.exe (PID: 6660)
The sample compiled with chinese language support
- WinRAR.exe (PID: 6660)
The sample compiled with japanese language support
- WinRAR.exe (PID: 6660)
The sample compiled with Italian language support
- WinRAR.exe (PID: 6660)
The sample compiled with Indonesian language support
- WinRAR.exe (PID: 6660)
The sample compiled with korean language support
- WinRAR.exe (PID: 6660)
The sample compiled with polish language support
- WinRAR.exe (PID: 6660)
The sample compiled with portuguese language support
- WinRAR.exe (PID: 6660)
The sample compiled with slovak language support
- WinRAR.exe (PID: 6660)
The sample compiled with swedish language support
- WinRAR.exe (PID: 6660)
The sample compiled with turkish language support
- WinRAR.exe (PID: 6660)
The sample compiled with russian language support
- WinRAR.exe (PID: 6660)
Reads the computer name
- MpCmdRun.exe (PID: 5568)
Checks supported languages
- MpCmdRun.exe (PID: 5568)
Create files in a temporary directory
- MpCmdRun.exe (PID: 5568)
Checks proxy server information
- slui.exe (PID: 5960)
Reads the software policy settings
- slui.exe (PID: 5960)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | None |
| ZipModifyDate: | 2025:05:17 13:33:00 |
| ZipCRC: | 0x00000000 |
| ZipCompressedSize: | - |
| ZipUncompressedSize: | - |
| ZipFileName: | AppGroup_v1.2.0.win-x64/ |
Total processes
125
Monitored processes
5
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2616 | C:\WINDOWS\system32\cmd.exe /c ""C:\Users\admin\AppData\Local\Temp\Rar$VR6660.48345\Rar$Scan33174.bat" " | C:\Windows\System32\cmd.exe | — | WinRAR.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5568 | "C:\Program Files\Windows Defender\MpCmdRun.exe" -Scan -ScanType 3 -File "C:\Users\admin\AppData\Local\Temp\Rar$VR6660.48345" | C:\Program Files\Windows Defender\MpCmdRun.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Malware Protection Command Line Utility Exit code: 2 Version: 4.18.1909.6 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5960 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6660 | "C:\Program Files\WinRAR\WinRAR.exe" C:\Users\admin\Desktop\AppGroup_v1.2.0.win-x64.zip | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Version: 5.91.0 Modules
| |||||||||||||||
| 6760 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
4 934
Read events
4 925
Write events
9
Delete events
0
Modification events
| (PID) Process: | (6660) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (6660) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (6660) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (6660) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\AppGroup_v1.2.0.win-x64.zip | |||
| (PID) Process: | (6660) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (6660) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (6660) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (6660) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
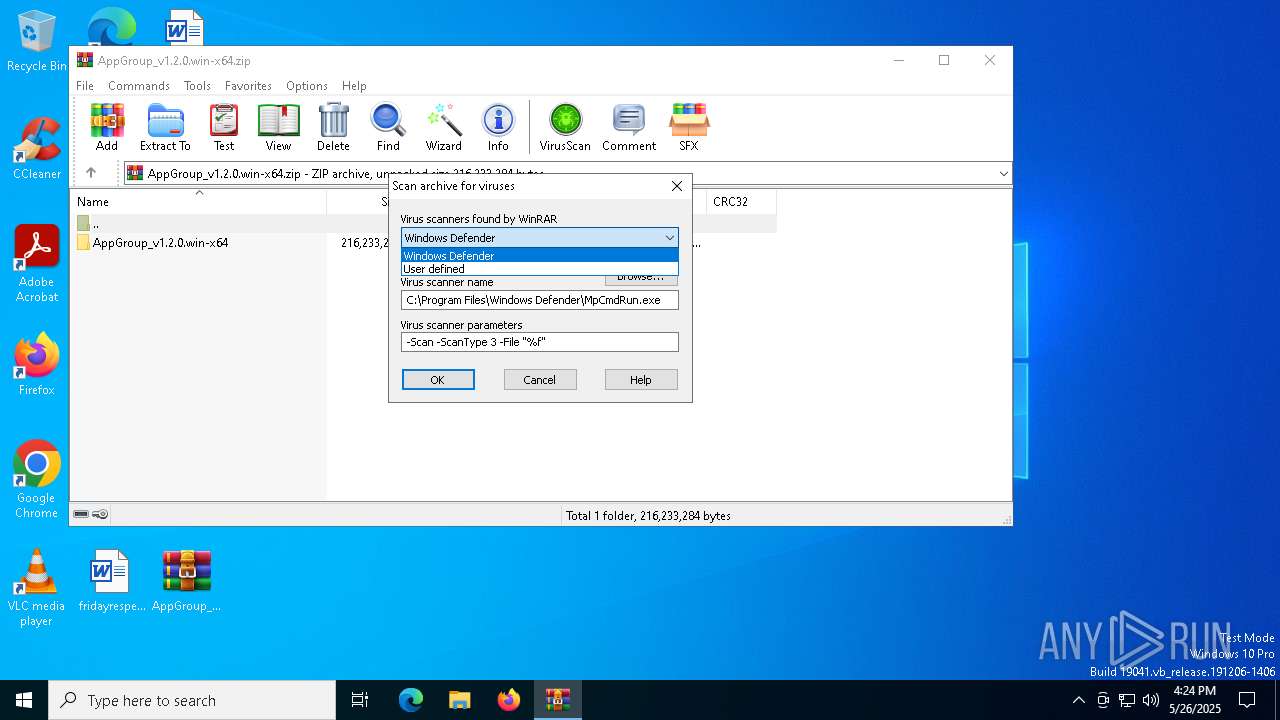
| (PID) Process: | (6660) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\VirusScan |
| Operation: | write | Name: | DefScanner |
Value: Windows Defender | |||
Executable files
437
Suspicious files
9
Text files
13
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6660 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$VR6660.48345\AppGroup_v1.2.0.win-x64.zip\AppGroup_v1.2.0.win-x64\AppGroup.deps.json | binary | |
MD5:AD1BACD177A47CE0CB401730CA65B86A | SHA256:1588DF7F9E803E05CA00741973B25C30969DE54B4B4F8BEC7DCE1AF3DE2E7453 | |||
| 6660 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$VR6660.48345\AppGroup_v1.2.0.win-x64.zip\AppGroup_v1.2.0.win-x64\AppGroup.dll | executable | |
MD5:D26CA28A4453A7F79D6D5AB7707565BA | SHA256:237CE3DEDEB5AD5498593AB80AE87B0FDE4362023F1D35F39797B3038691762E | |||
| 6660 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$VR6660.48345\AppGroup_v1.2.0.win-x64.zip\AppGroup_v1.2.0.win-x64\af-ZA\Microsoft.UI.Xaml.Phone.dll.mui | executable | |
MD5:D973F5932B8CD04EDFE58D538D145386 | SHA256:D527AC95E4EEB7464B3E83A8FA33264CD2A2FFE8B63F02F2DB42235F06F3C748 | |||
| 6660 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$VR6660.48345\AppGroup_v1.2.0.win-x64.zip\AppGroup_v1.2.0.win-x64\AppGroup.pdb | binary | |
MD5:944856E38FA9AED13A1124543208AD34 | SHA256:B930D1F4298FF92D347626BE2F596A8893F0626DC595307377CC68FEE6AEFEC2 | |||
| 6660 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$VR6660.48345\AppGroup_v1.2.0.win-x64.zip\AppGroup_v1.2.0.win-x64\AppGroupBackground.pdb | binary | |
MD5:B3E5587B22100A9E976FBDF59F8C14F7 | SHA256:CAB106726F7E2C046B847CA3C80FE388732568FD01C14192D3AC4848BA8B12E6 | |||
| 6660 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$VR6660.48345\AppGroup_v1.2.0.win-x64.zip\AppGroup_v1.2.0.win-x64\AppGroup.ico | image | |
MD5:D0B6B9AD457D1F8A97A170B963051141 | SHA256:7C7F7AA1A1DA2C898F8241F2F414C056B363BB1B3E094CC34AD9FA9C3C19EC07 | |||
| 6660 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$VR6660.48345\AppGroup_v1.2.0.win-x64.zip\AppGroup_v1.2.0.win-x64\AppGroup.runtimeconfig.json | binary | |
MD5:BF76BF080D4C6EE0A9F76359FAD7AF9D | SHA256:9620279397F70B38BE668DA4D425D356BEBA0C3F98EFADE48568FB346FADE305 | |||
| 6660 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$VR6660.48345\AppGroup_v1.2.0.win-x64.zip\AppGroup_v1.2.0.win-x64\am-ET\Microsoft.UI.Xaml.Phone.dll.mui | executable | |
MD5:960EFF650E4246EDDDFB619313C82541 | SHA256:39B993F2DC9E2C0C6608A8062A679E98C6B3CCA407CE11A49CA08626024455F9 | |||
| 6660 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$VR6660.48345\AppGroup_v1.2.0.win-x64.zip\AppGroup_v1.2.0.win-x64\AppGroupBackground.deps.json | binary | |
MD5:8B5F7BC1365AF71EC98E117240A029D6 | SHA256:B6DA637FA2691427168AAAF68A8FBE6C9E20DFAE160AF2853FFE2EA7A8A20574 | |||
| 6660 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$VR6660.48345\AppGroup_v1.2.0.win-x64.zip\AppGroup_v1.2.0.win-x64\ar-SA\Microsoft.ui.xaml.dll.mui | executable | |
MD5:050E9540E4D239B7F553C399096BE621 | SHA256:A75820FB7760387108748C481B3F4943186E8F415821186CA83FBEB3C88E91A0 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
23
TCP/UDP connections
37
DNS requests
15
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 2.16.168.124:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
5796 | svchost.exe | GET | 200 | 2.16.168.124:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
5796 | svchost.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
— | — | POST | 500 | 20.83.72.98:443 | https://activation-v2.sls.microsoft.com/SLActivateProduct/SLActivateProduct.asmx?configextension=Retail | unknown | xml | 512 b | whitelisted |
— | — | POST | 200 | 40.126.31.131:443 | https://login.live.com/RST2.srf | unknown | xml | 11.1 Kb | whitelisted |
— | — | GET | 304 | 52.149.20.212:443 | https://slscr.update.microsoft.com/SLS/%7B522D76A4-93E1-47F8-B8CE-07C937AD1A1E%7D/x64/10.0.19045.4046/0?CH=686&L=en-US&P=&PT=0x30&WUA=10.0.19041.3996&MK=DELL&MD=DELL | unknown | — | — | unknown |
— | — | POST | 200 | 20.190.159.0:443 | https://login.live.com/RST2.srf | unknown | xml | 11.0 Kb | whitelisted |
— | — | GET | 200 | 52.149.20.212:443 | https://slscr.update.microsoft.com/SLS/%7B522D76A4-93E1-47F8-B8CE-07C937AD1A1E%7D/x64/10.0.19045.4046/0?CH=686&L=en-US&P=&PT=0x30&WUA=10.0.19041.3996&MK=DELL&MD=DELL | unknown | — | — | unknown |
3304 | SIHClient.exe | GET | 200 | 23.53.40.176:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut_2010-06-23.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
5796 | svchost.exe | 2.16.168.124:80 | crl.microsoft.com | Akamai International B.V. | RU | whitelisted |
— | — | 2.16.168.124:80 | crl.microsoft.com | Akamai International B.V. | RU | whitelisted |
5796 | svchost.exe | 95.101.149.131:80 | www.microsoft.com | Akamai International B.V. | NL | whitelisted |
— | — | 95.101.149.131:80 | www.microsoft.com | Akamai International B.V. | NL | whitelisted |
— | — | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5344 | slui.exe | 40.91.76.224:443 | activation-v2.sls.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
6544 | svchost.exe | 40.126.32.138:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
activation-v2.sls.microsoft.com |
| whitelisted |
login.live.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |