| URL: | http://www.ssloffice.to/index.php |
| Full analysis: | https://app.any.run/tasks/18b482bd-b523-494b-9887-bda5df89c227 |
| Verdict: | Malicious activity |
| Analysis date: | May 15, 2019, 14:36:18 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MD5: | C3A6369AF2BA6755D327A82942E81B9B |
| SHA1: | D47C42C9825B0F03A3547299BDFCF08162140766 |
| SHA256: | 8EF973FF0E87E575264591F8130BE92E2383FE394A4C50A63E098BFC4CC2E39C |
| SSDEEP: | 3:N1KJS4wDmHn:Cc42mHn |
MALICIOUS
No malicious indicators.SUSPICIOUS
No suspicious indicators.INFO
Creates files in the user directory
- iexplore.exe (PID: 252)
- iexplore.exe (PID: 3504)
Changes internet zones settings
- iexplore.exe (PID: 252)
Reads Internet Cache Settings
- iexplore.exe (PID: 3504)
Reads internet explorer settings
- iexplore.exe (PID: 3504)
Reads settings of System Certificates
- iexplore.exe (PID: 252)
Adds / modifies Windows certificates
- iexplore.exe (PID: 252)
Changes settings of System certificates
- iexplore.exe (PID: 252)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
37
Monitored processes
2
Malicious processes
0
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 252 | "C:\Program Files\Internet Explorer\iexplore.exe" http://www.ssloffice.to/index.php | C:\Program Files\Internet Explorer\iexplore.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 0 Version: 8.00.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3504 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:252 CREDAT:71937 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 8.00.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
521
Read events
437
Write events
78
Delete events
6
Modification events
| (PID) Process: | (252) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
| (PID) Process: | (252) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
| (PID) Process: | (252) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 1 | |||
| (PID) Process: | (252) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\Zones |
| Operation: | write | Name: | SecuritySafe |
Value: 1 | |||
| (PID) Process: | (252) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings |
| Operation: | write | Name: | ProxyEnable |
Value: 0 | |||
| (PID) Process: | (252) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\Connections |
| Operation: | write | Name: | SavedLegacySettings |
Value: 4600000071000000010000000000000000000000000000000000000000000000C0E333BBEAB1D301000000000000000000000000020000001700000000000000FE800000000000007D6CB050D9C573F70B000000000000006D00330032005C004D00530049004D004700330032002E0064006C000100000004AA400014AA4000040000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000002000000C0A8016400000000000000000000000000000000000000000800000000000000805D3F00983740000008000002000000000000600000002060040000B8A94000020000008802000060040000B8A9400004000000F8010000B284000088B64000B84B400043003A000000000000000000000000000000000000000000 | |||
| (PID) Process: | (252) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Recovery\Active |
| Operation: | write | Name: | {D62BC911-771E-11E9-A370-5254004A04AF} |
Value: 0 | |||
| (PID) Process: | (252) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Ext\Stats\{2670000A-7350-4F3C-8081-5663EE0C6C49}\iexplore |
| Operation: | write | Name: | Type |
Value: 4 | |||
| (PID) Process: | (252) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Ext\Stats\{2670000A-7350-4F3C-8081-5663EE0C6C49}\iexplore |
| Operation: | write | Name: | Count |
Value: 1 | |||
| (PID) Process: | (252) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Ext\Stats\{2670000A-7350-4F3C-8081-5663EE0C6C49}\iexplore |
| Operation: | write | Name: | Time |
Value: E307050003000F000E00240023004700 | |||
Executable files
0
Suspicious files
0
Text files
40
Unknown types
8
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 252 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\H6QNMHE9\favicon[1].ico | — | |
MD5:— | SHA256:— | |||
| 252 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\Internet Explorer\Services\search_{0633EE93-D776-472f-A0FF-E1416B8B2E3A}.ico | — | |
MD5:— | SHA256:— | |||
| 3504 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\History\Low\History.IE5\index.dat | dat | |
MD5:— | SHA256:— | |||
| 3504 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\Z3X7S4O6\login[1].htm | html | |
MD5:— | SHA256:— | |||
| 3504 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\52TNA8WR\base-vflQGhUQE[1].css | text | |
MD5:— | SHA256:— | |||
| 3504 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\desktop.ini | ini | |
MD5:4A3DEB274BB5F0212C2419D3D8D08612 | SHA256:2842973D15A14323E08598BE1DFB87E54BF88A76BE8C7BC94C56B079446EDF38 | |||
| 3504 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\U5N689J1\animation-vflzHcTyC[1].css | text | |
MD5:CC7713C829F9CE536C471FD215C11040 | SHA256:79F96700543DBD7A21C830FA974FAE3AD275A4994BD850C2CAC7DFF05A5CAC29 | |||
| 3504 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\U5N689J1\desktop.ini | ini | |
MD5:4A3DEB274BB5F0212C2419D3D8D08612 | SHA256:2842973D15A14323E08598BE1DFB87E54BF88A76BE8C7BC94C56B079446EDF38 | |||
| 3504 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\Z3X7S4O6\desktop.ini | ini | |
MD5:4A3DEB274BB5F0212C2419D3D8D08612 | SHA256:2842973D15A14323E08598BE1DFB87E54BF88A76BE8C7BC94C56B079446EDF38 | |||
| 252 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\H6QNMHE9\favicon[1].png | image | |
MD5:9FB559A691078558E77D6848202F6541 | SHA256:6D8A01DC7647BC218D003B58FE04049E24A9359900B7E0CEBAE76EDF85B8B914 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
35
TCP/UDP connections
29
DNS requests
8
Threats
4
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
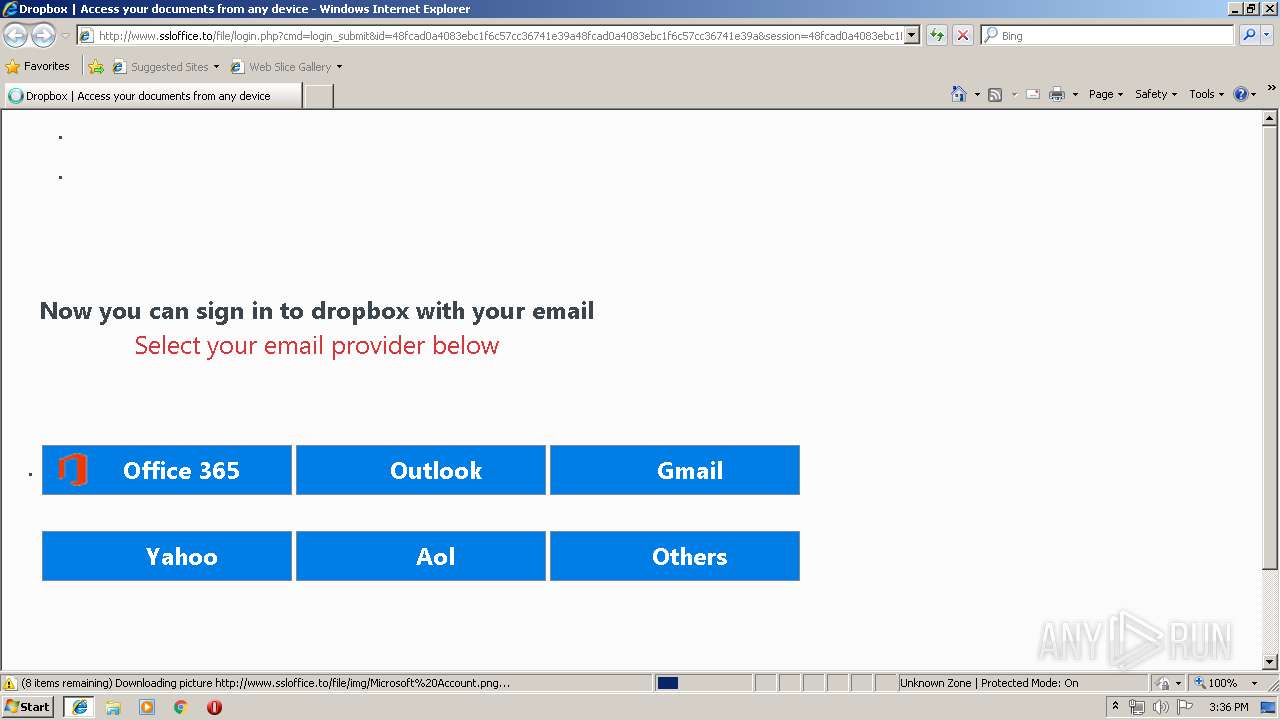
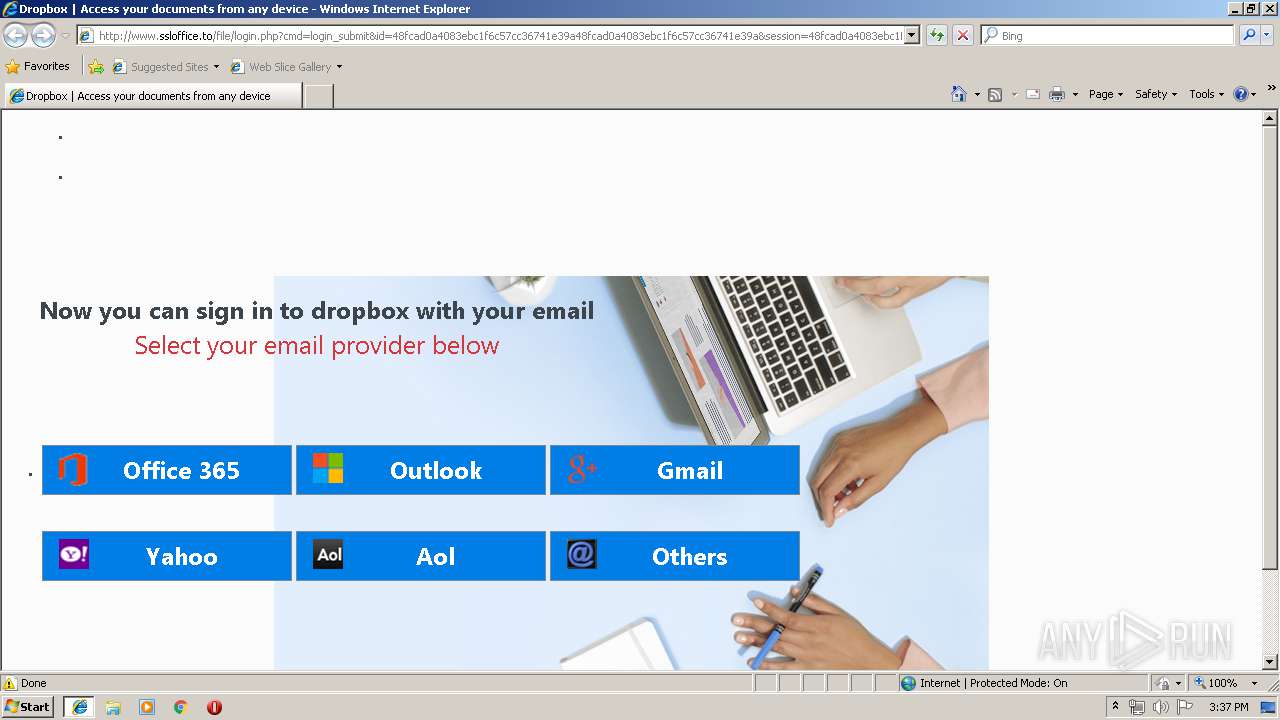
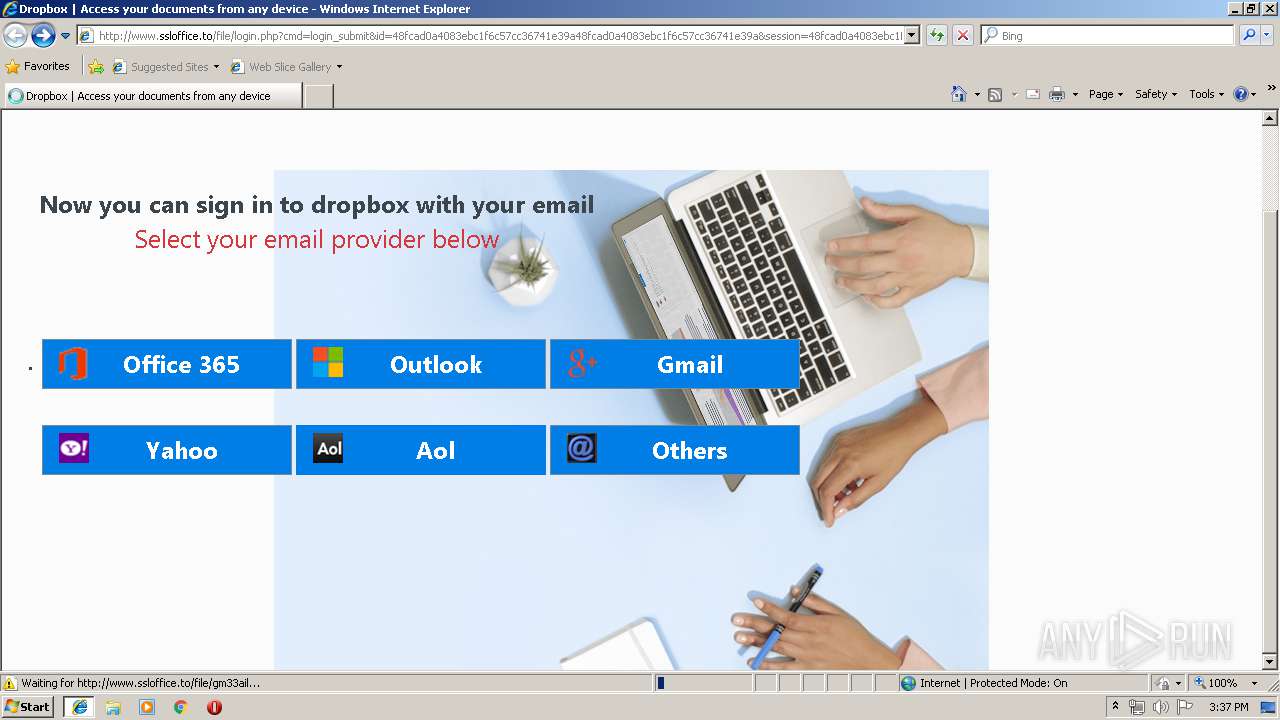
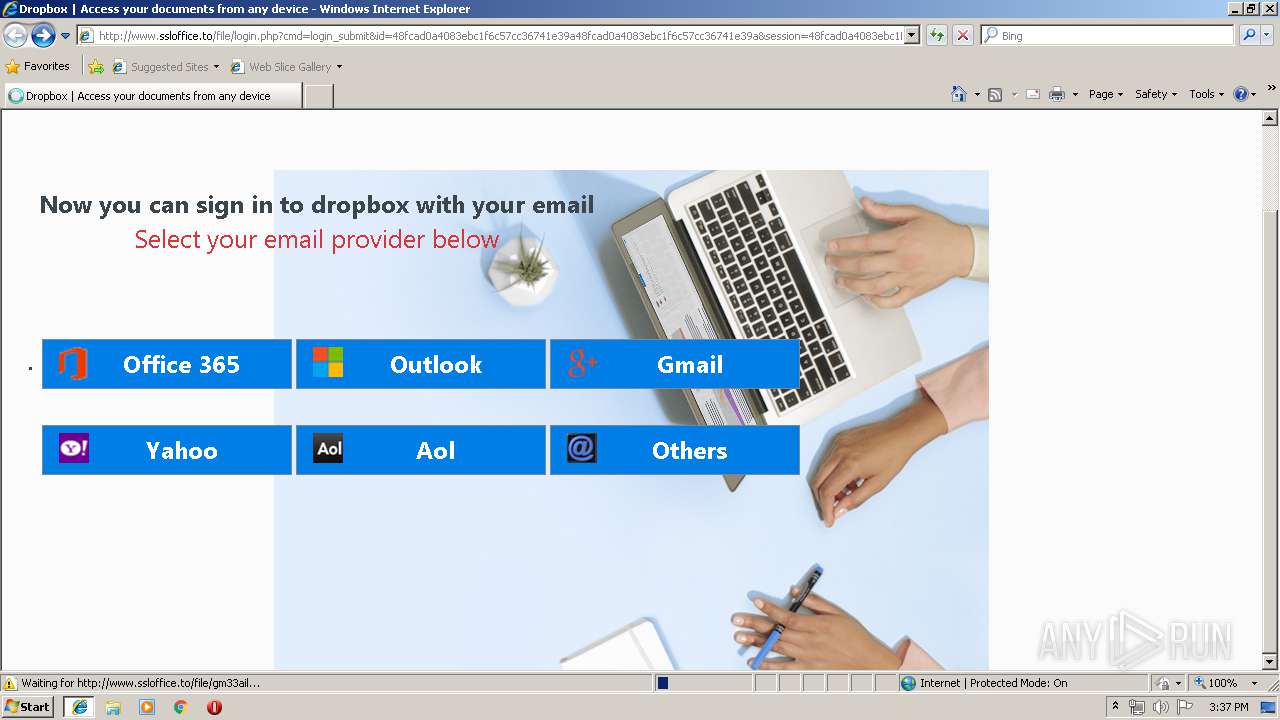
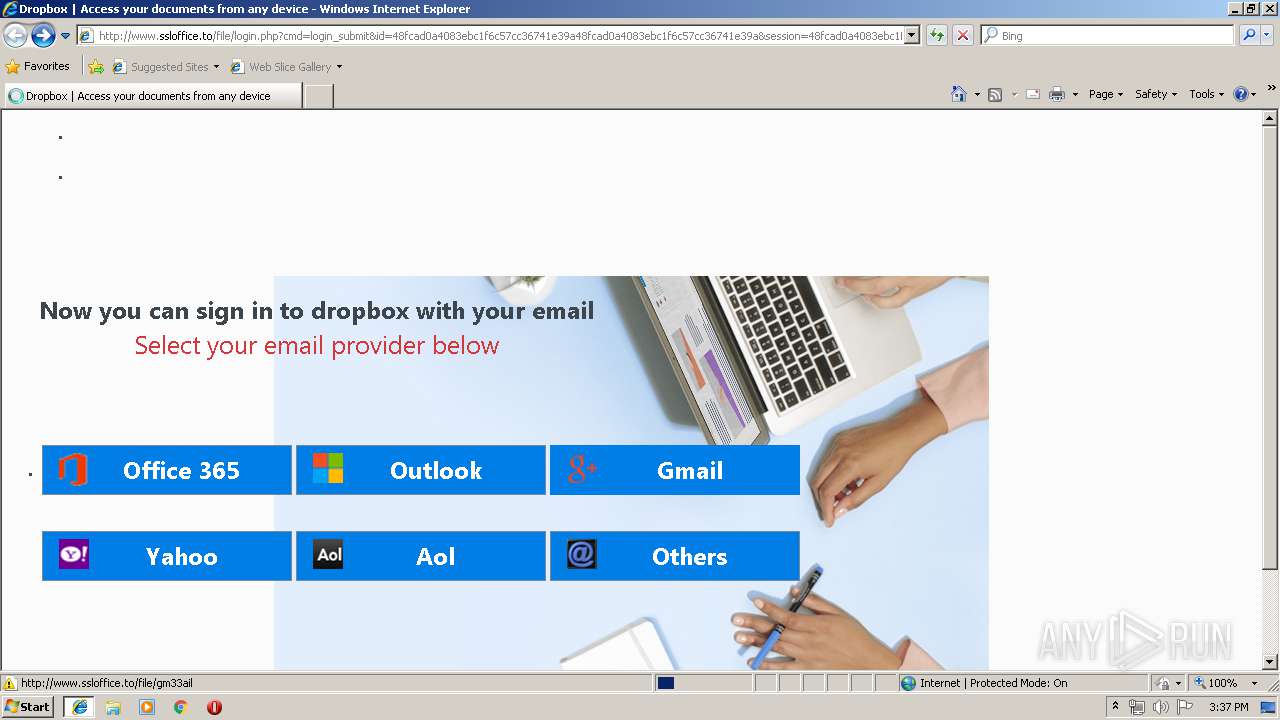
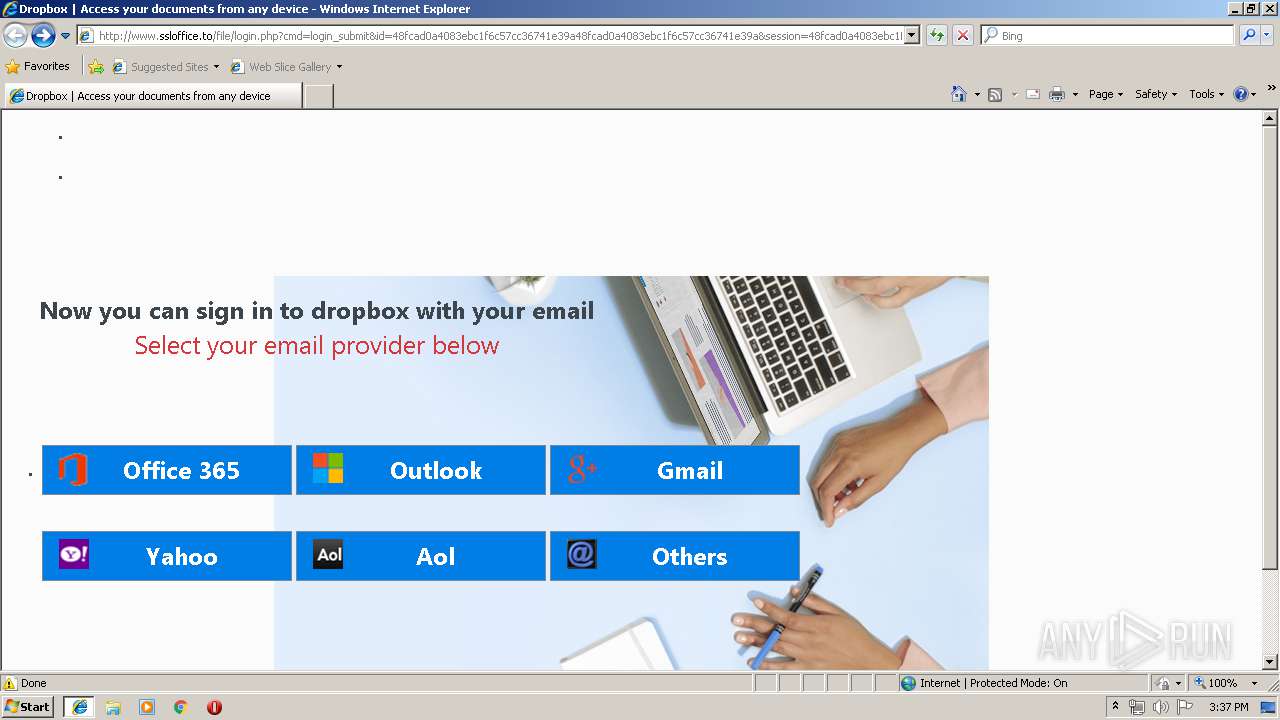
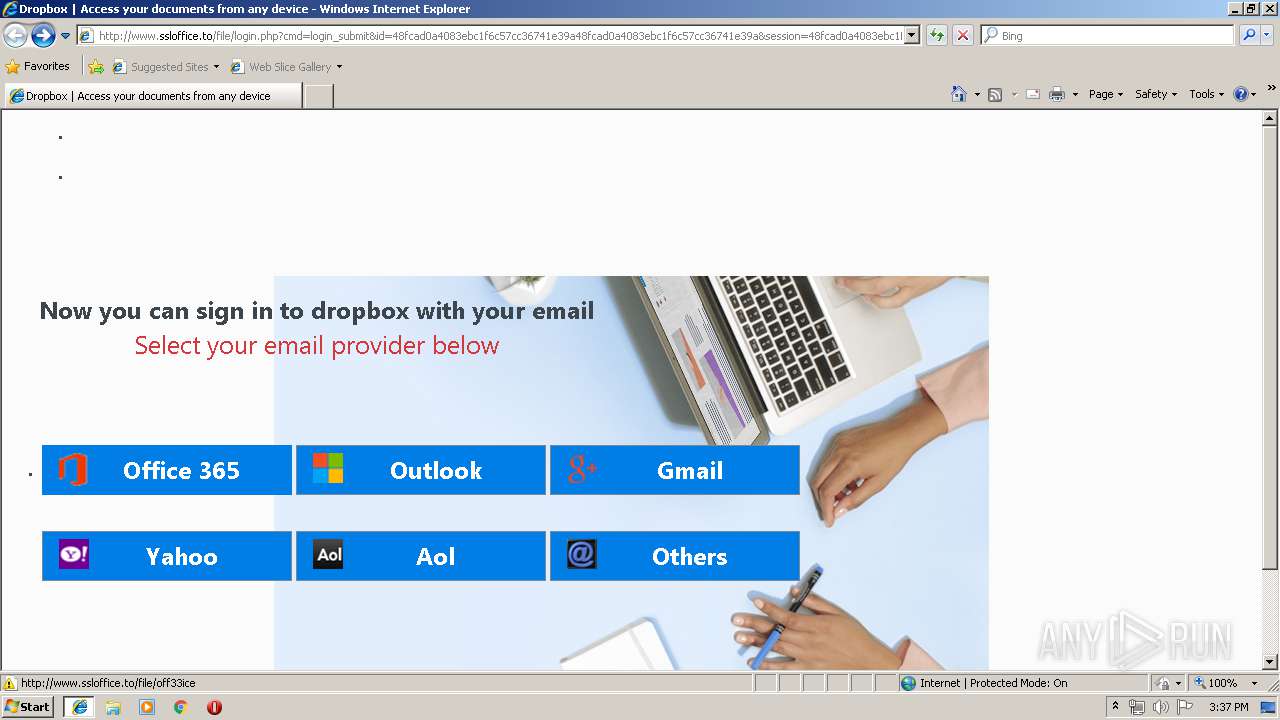
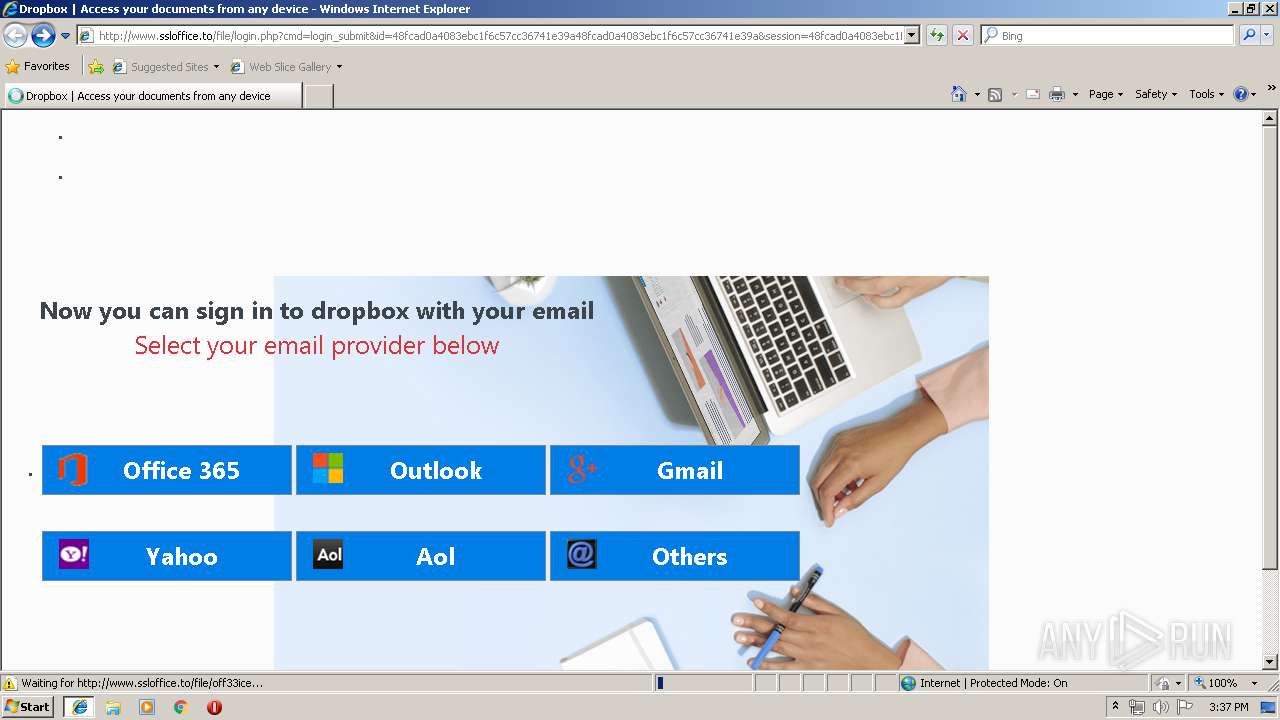
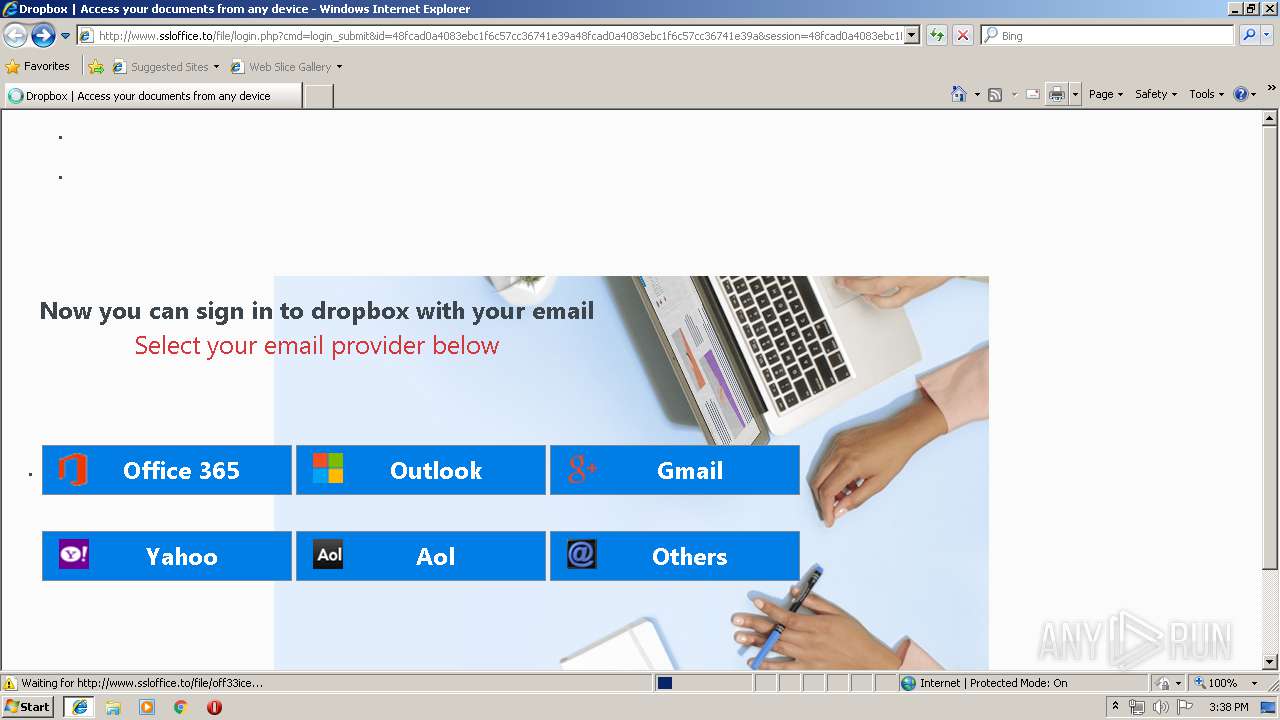
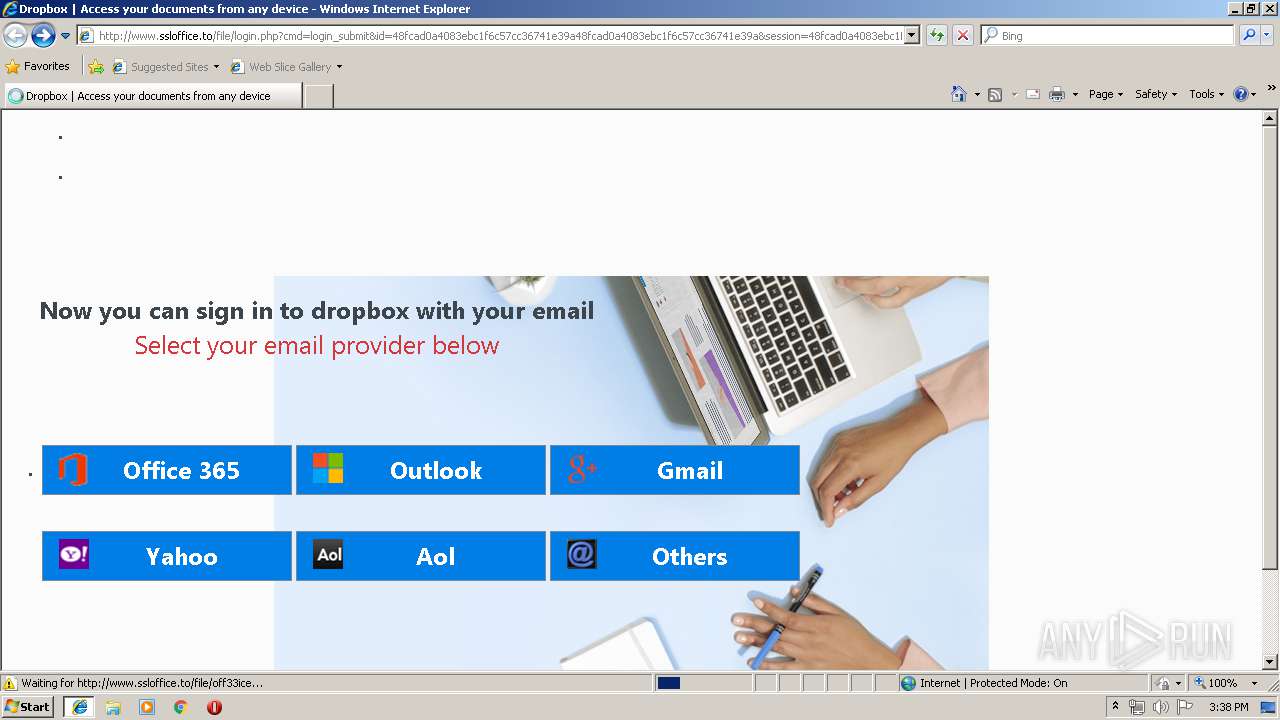
3504 | iexplore.exe | GET | 302 | 111.90.157.58:80 | http://www.ssloffice.to/index.php | MY | — | — | malicious |
3504 | iexplore.exe | GET | 302 | 111.90.157.58:80 | http://www.ssloffice.to/file/?email= | MY | — | — | malicious |
3504 | iexplore.exe | GET | 200 | 111.90.157.58:80 | http://www.ssloffice.to/file/asset/hero-poster.png | MY | image | 294 Kb | malicious |
3504 | iexplore.exe | GET | 200 | 111.90.157.58:80 | http://www.ssloffice.to/file/img/Microsoft%20Account.png | MY | image | 315 b | malicious |
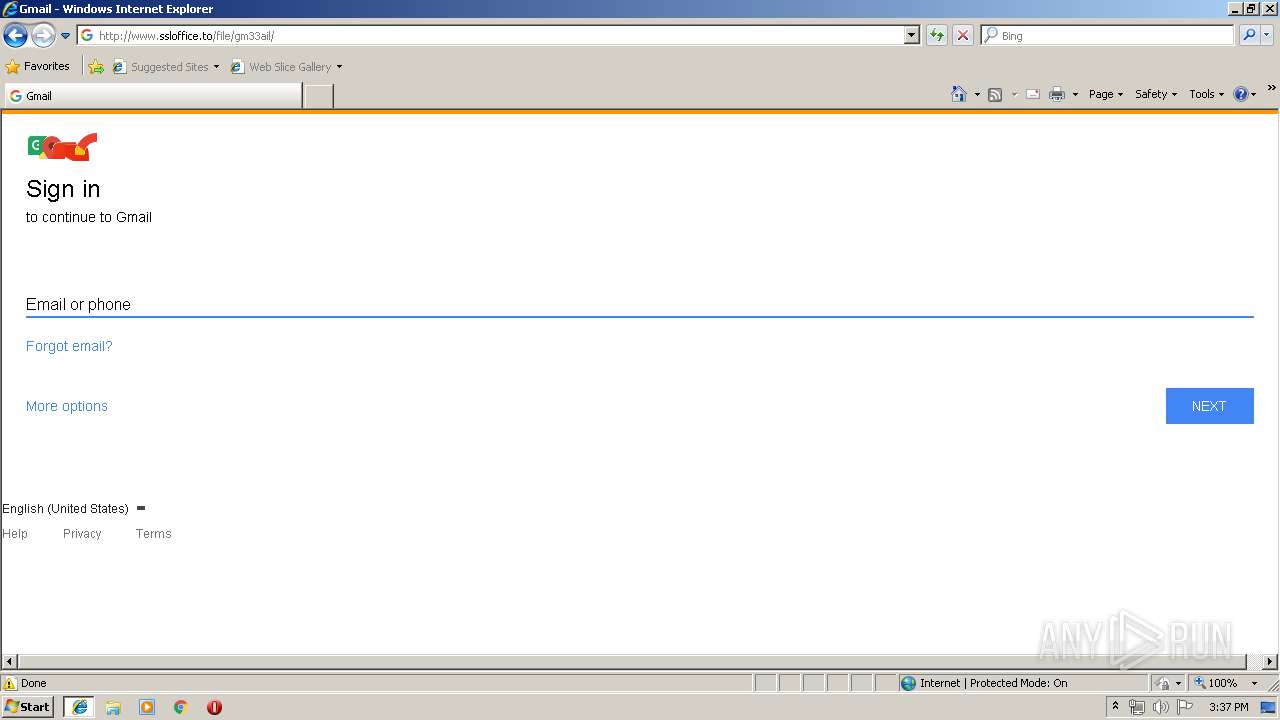
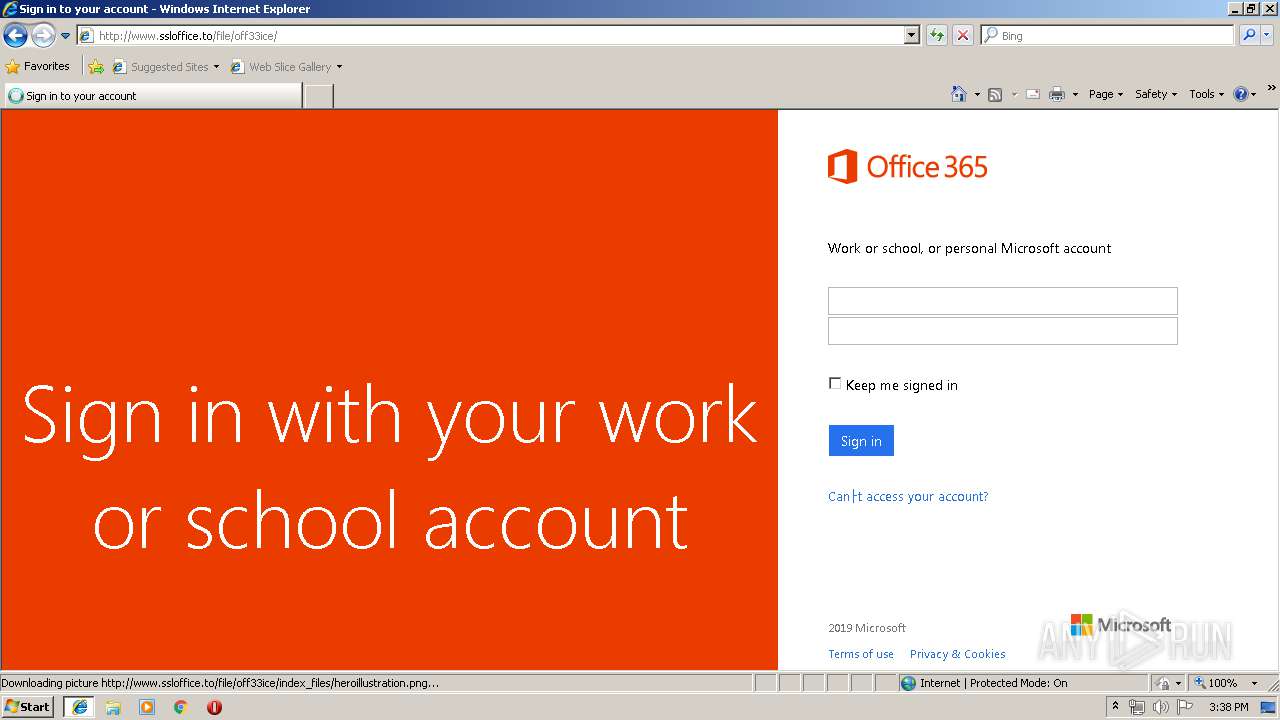
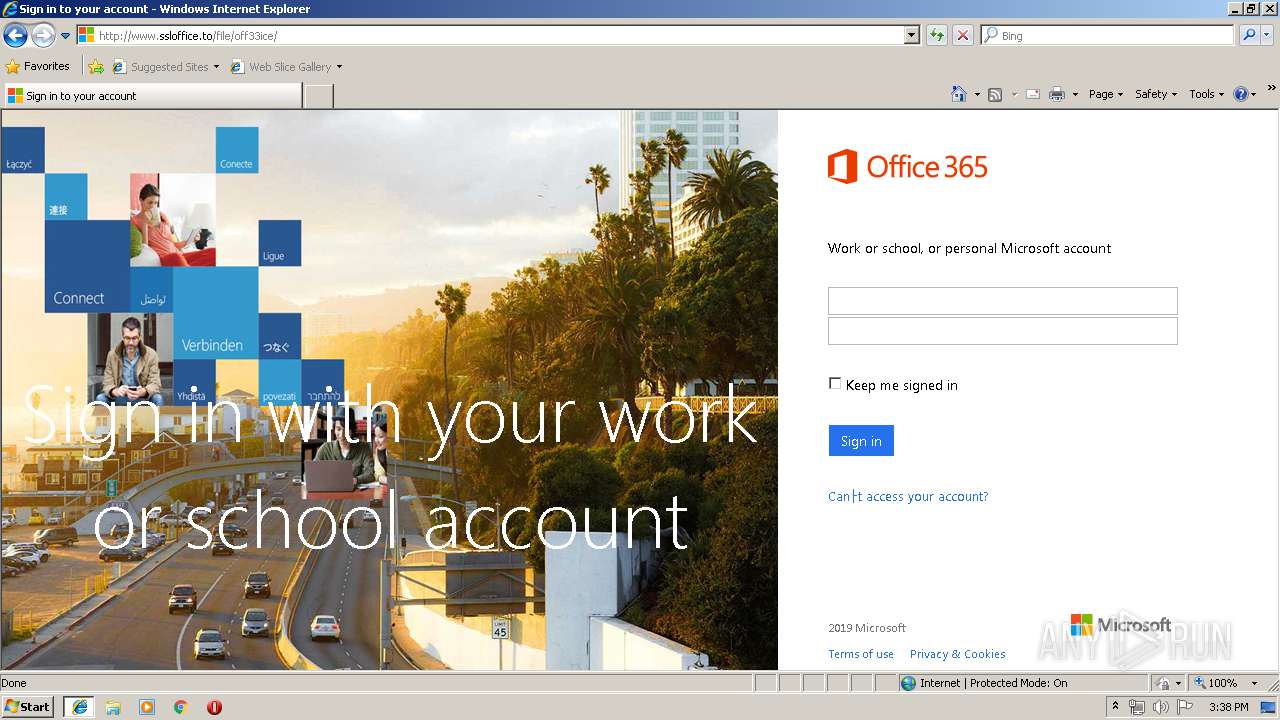
3504 | iexplore.exe | GET | 200 | 111.90.157.58:80 | http://www.ssloffice.to/file/login.php?cmd=login_submit&id=48fcad0a4083ebc1f6c57cc36741e39a48fcad0a4083ebc1f6c57cc36741e39a&session=48fcad0a4083ebc1f6c57cc36741e39a48fcad0a4083ebc1f6c57cc36741e39a | MY | html | 1.63 Kb | malicious |
3504 | iexplore.exe | GET | 200 | 111.90.157.58:80 | http://www.ssloffice.to/file/asset/modal-vflS6pGZb.css | MY | text | 2.51 Kb | malicious |
3504 | iexplore.exe | GET | 200 | 111.90.157.58:80 | http://www.ssloffice.to/file/asset/components-vflfxQtKp.css | MY | text | 9.34 Kb | malicious |
3504 | iexplore.exe | GET | 200 | 111.90.157.58:80 | http://www.ssloffice.to/file/asset/animation-vflzHcTyC.css | MY | text | 258 b | malicious |
3504 | iexplore.exe | GET | 200 | 111.90.157.58:80 | http://www.ssloffice.to/file/asset/index-vfl0GyzuL.css | MY | text | 3.17 Kb | malicious |
3504 | iexplore.exe | GET | 200 | 111.90.157.58:80 | http://www.ssloffice.to/file/asset/base-vflQGhUQE.css | MY | text | 3.97 Kb | malicious |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
252 | iexplore.exe | 13.107.21.200:80 | www.bing.com | Microsoft Corporation | US | whitelisted |
3504 | iexplore.exe | 111.90.157.58:80 | www.ssloffice.to | Asia Web Service Ltd | MY | suspicious |
3504 | iexplore.exe | 216.58.207.42:443 | ajax.googleapis.com | Google Inc. | US | whitelisted |
3504 | iexplore.exe | 172.217.16.170:443 | fonts.googleapis.com | Google Inc. | US | whitelisted |
3504 | iexplore.exe | 172.217.22.3:443 | fonts.gstatic.com | Google Inc. | US | whitelisted |
252 | iexplore.exe | 172.217.21.228:443 | www.google.com | Google Inc. | US | whitelisted |
252 | iexplore.exe | 104.16.99.29:443 | cfl.dropboxstatic.com | Cloudflare Inc | US | shared |
3504 | iexplore.exe | 184.31.91.84:443 | secure.aadcdn.microsoftonline-p.com | Akamai International B.V. | NL | whitelisted |
252 | iexplore.exe | 184.31.91.84:443 | secure.aadcdn.microsoftonline-p.com | Akamai International B.V. | NL | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
www.ssloffice.to |
| malicious |
www.bing.com |
| whitelisted |
ajax.googleapis.com |
| whitelisted |
fonts.googleapis.com |
| whitelisted |
fonts.gstatic.com |
| whitelisted |
cfl.dropboxstatic.com |
| shared |
www.google.com |
| malicious |
secure.aadcdn.microsoftonline-p.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
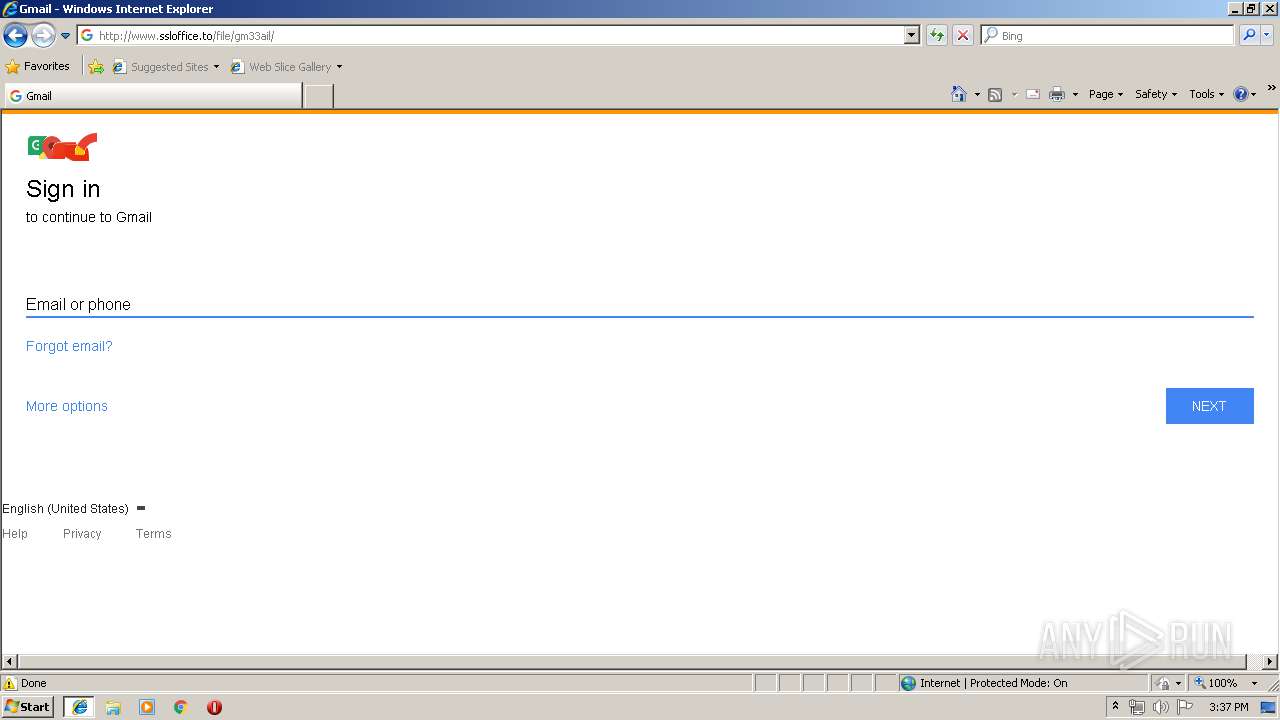
3504 | iexplore.exe | A Network Trojan was detected | MALWARE [PTsecurity] Google Drive Phishing Landing |
3504 | iexplore.exe | A Network Trojan was detected | ET CURRENT_EVENTS Dropbox Phishing Landing 2018-01-18 |
3504 | iexplore.exe | A Network Trojan was detected | ET CURRENT_EVENTS Dropbox Phishing Landing May 31 2017 |
3504 | iexplore.exe | A Network Trojan was detected | ET CURRENT_EVENTS Possible Office 365 Phishing Landing Aug 24 2016 |