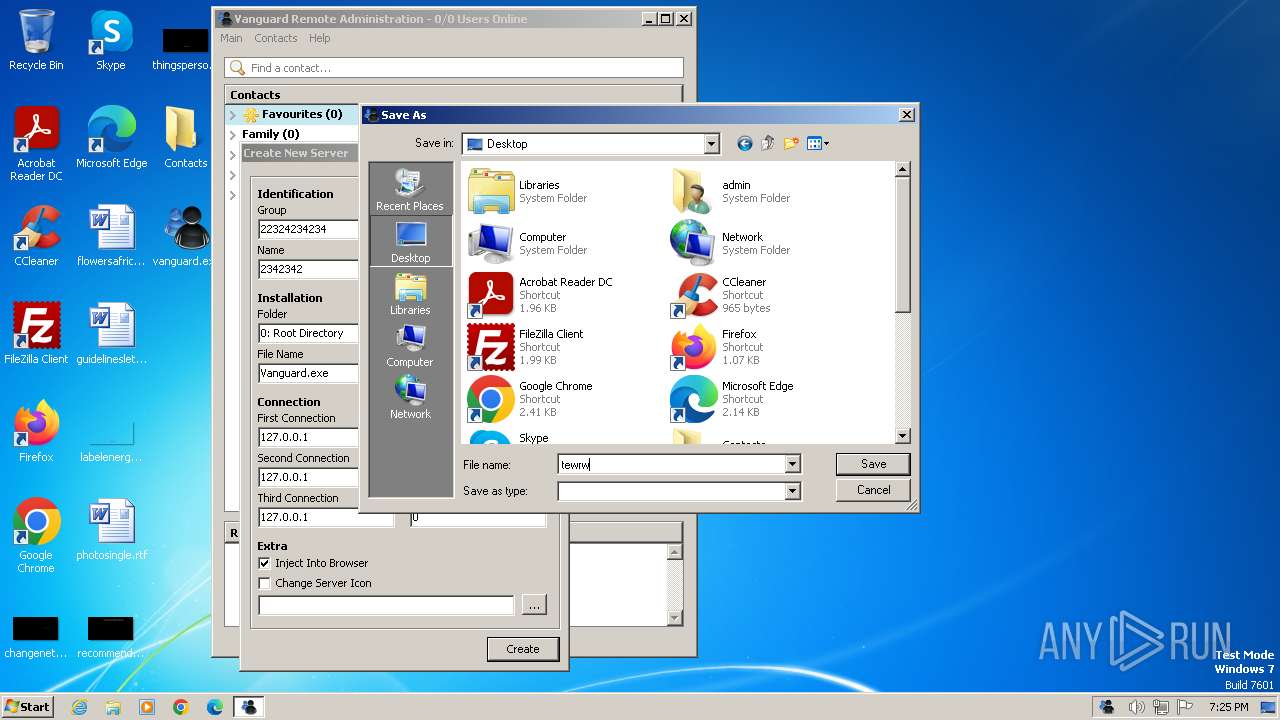
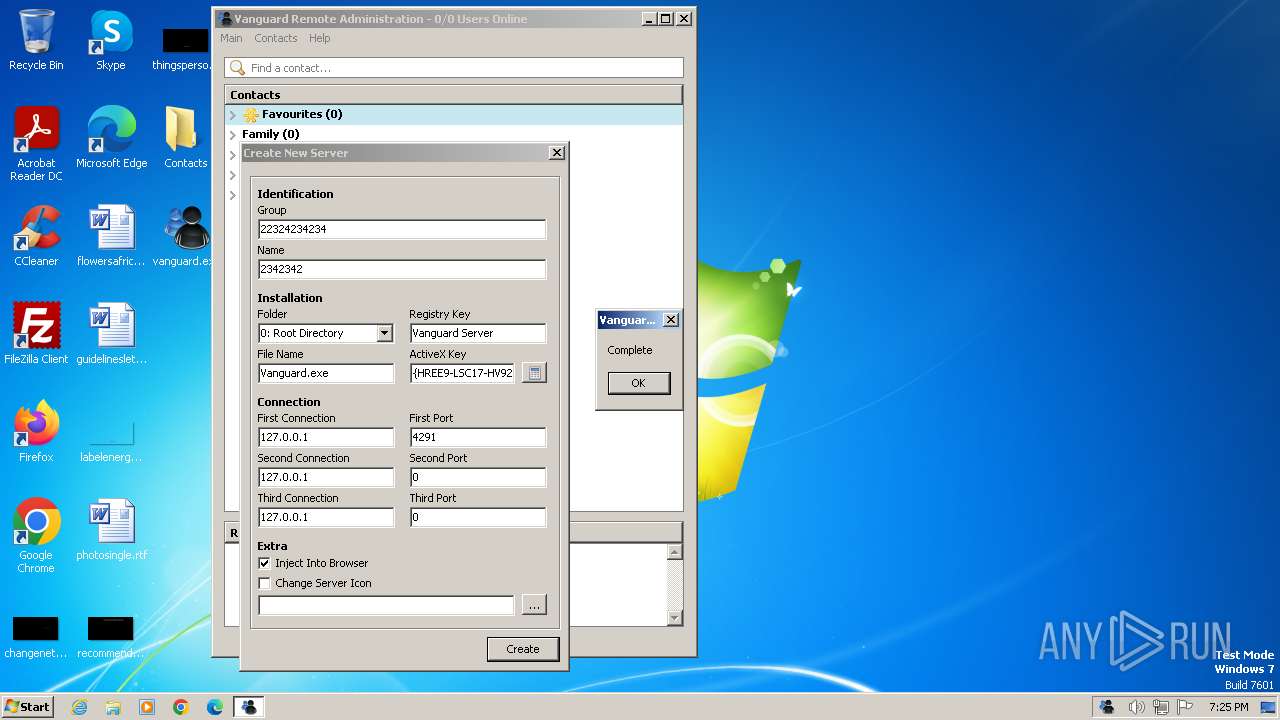
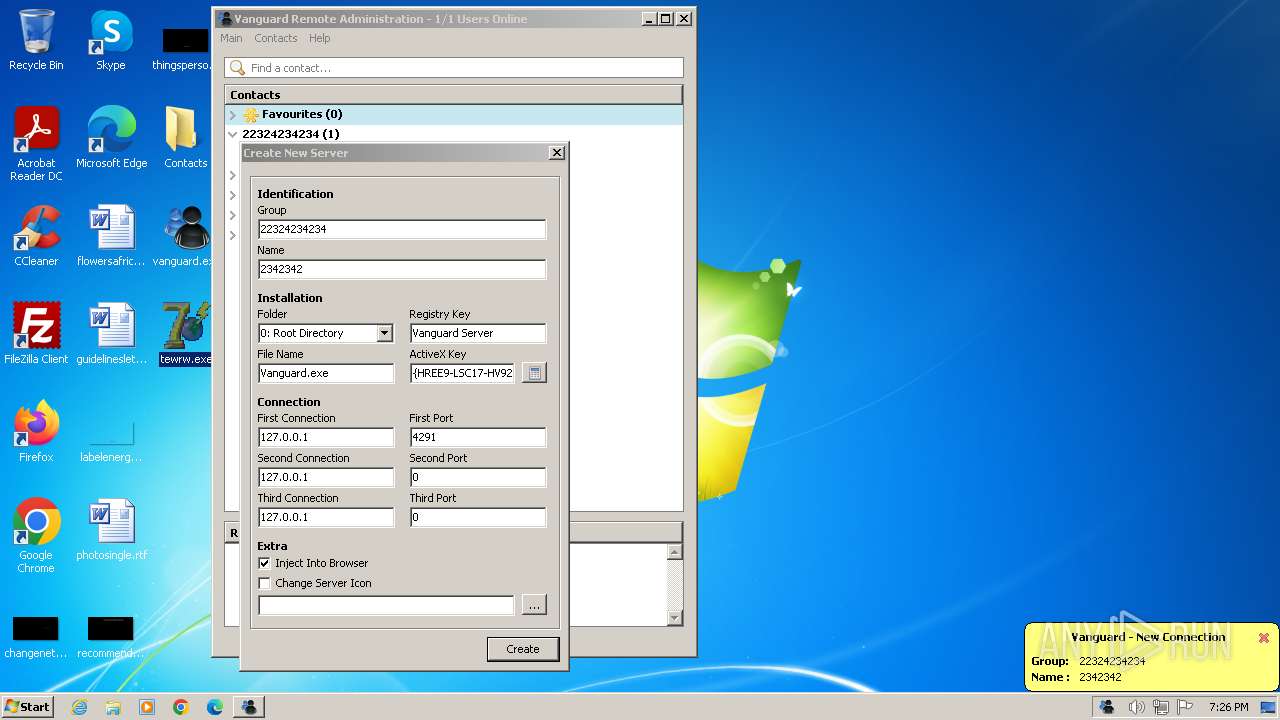
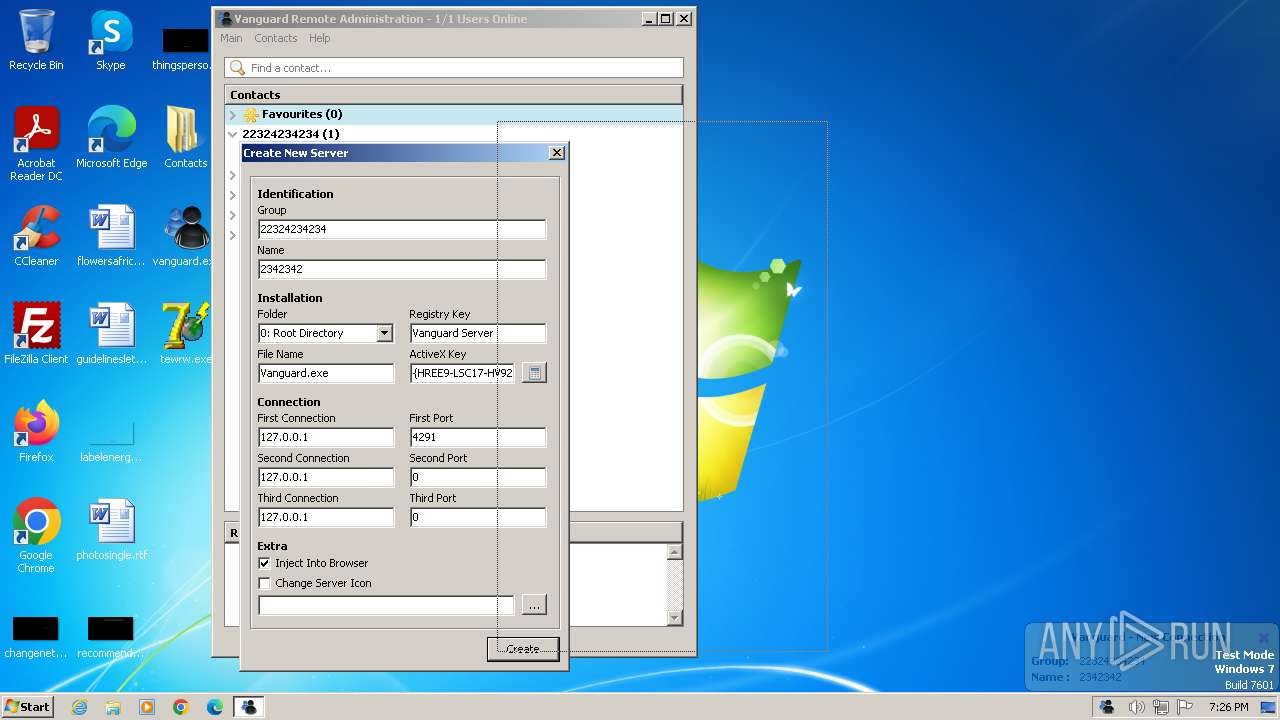
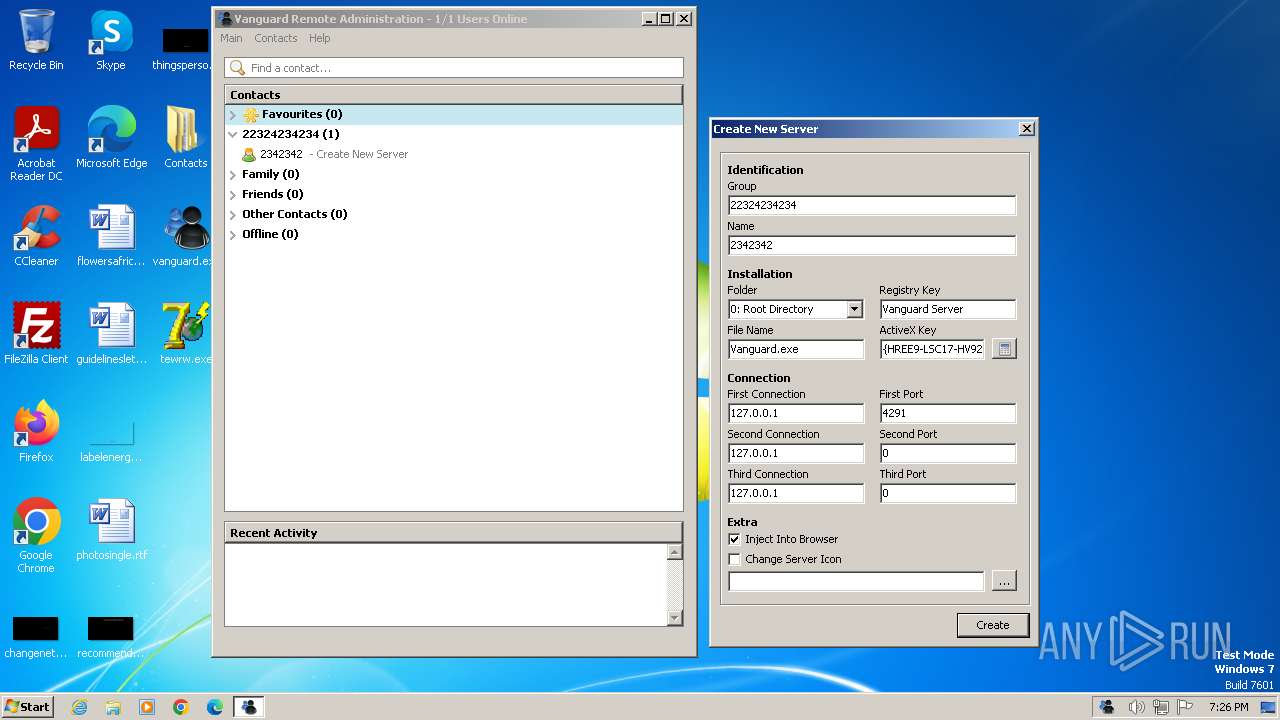
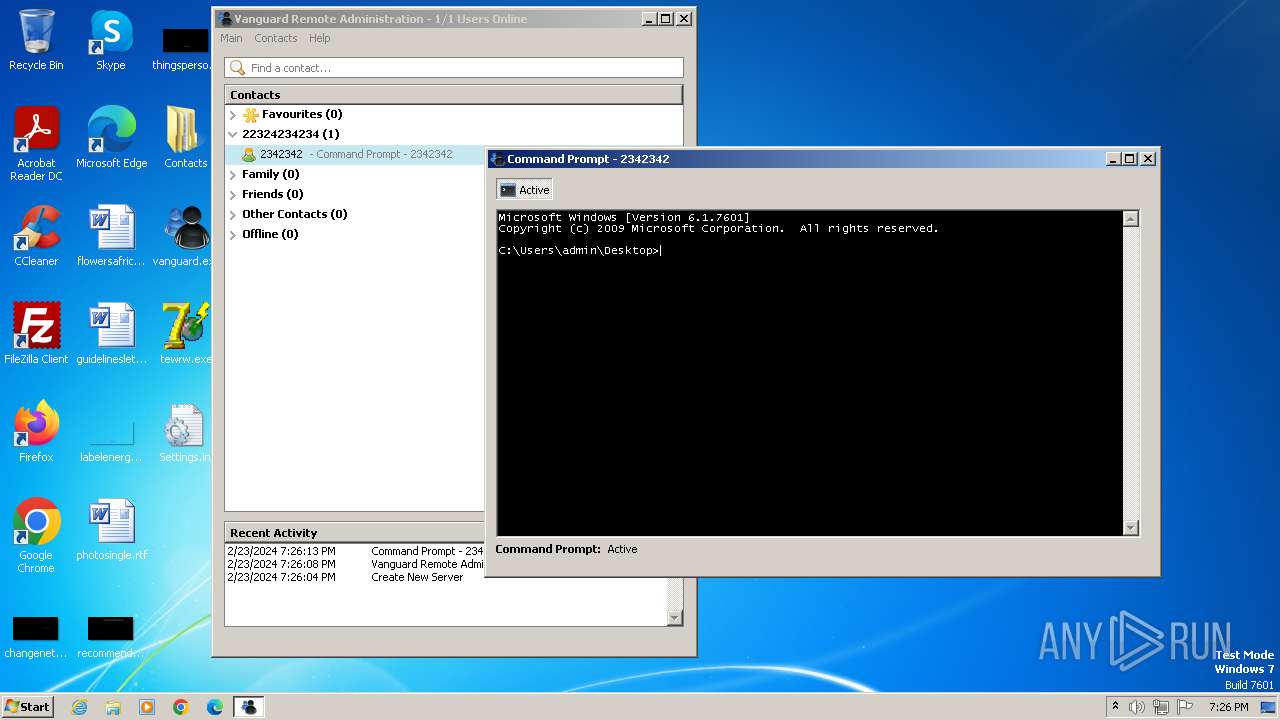
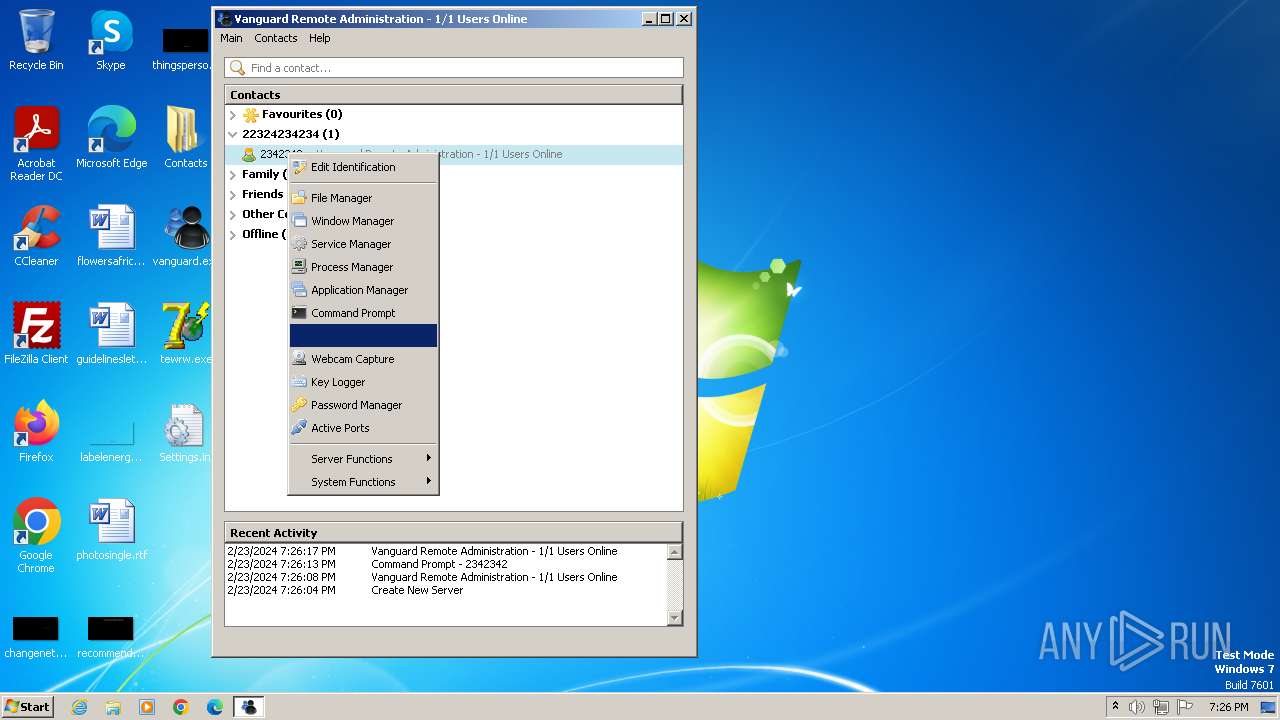
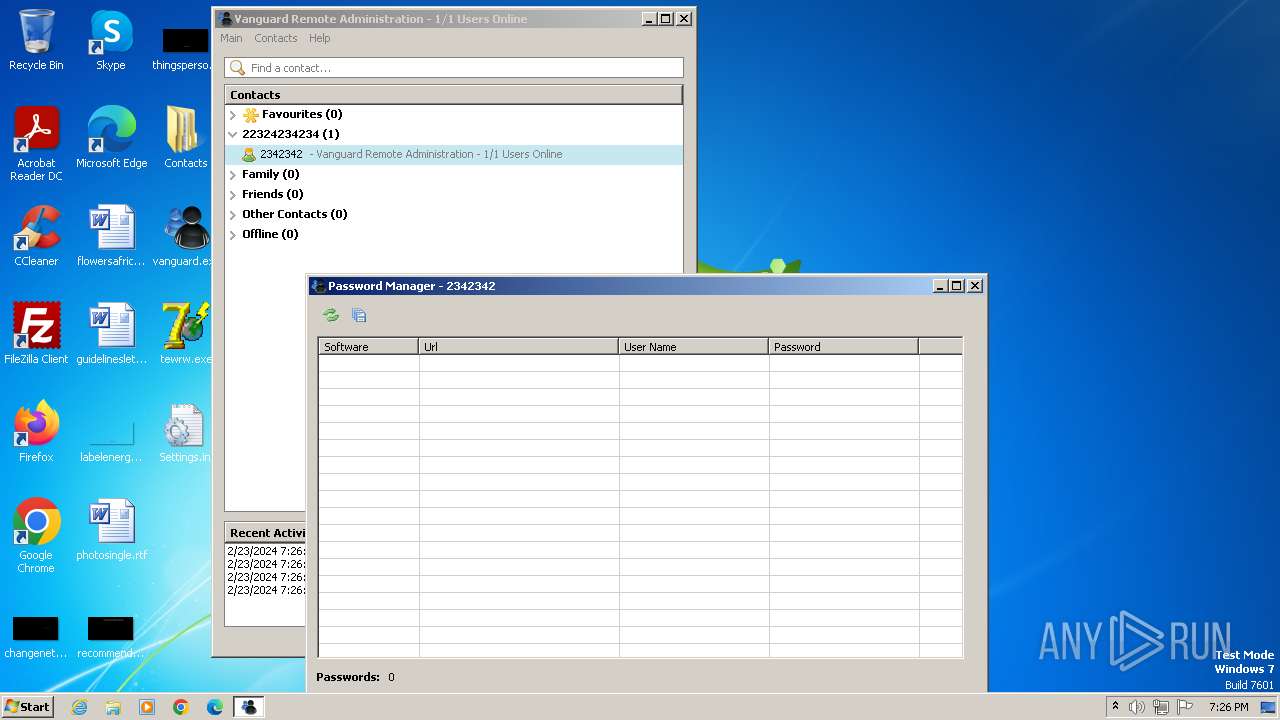
| File name: | vanguard.exe |
| Full analysis: | https://app.any.run/tasks/a0648d38-c14b-4bd7-b60b-2bc0df812041 |
| Verdict: | Malicious activity |
| Analysis date: | February 23, 2024, 19:25:19 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows |
| MD5: | 93CF31AE7470C489B1F093392A8586ED |
| SHA1: | FF403304B271DD2031EA483570A0F324AF8B5AE9 |
| SHA256: | 8EF6CA45B40B33EB22CE42EEA73B6B82268F8FA66D33BCAD1D6024E962FD18F1 |
| SSDEEP: | 49152:O1d/qmXGnNvRg+2FccZDz4+UdRSXuRjSr58ADX+ROIcW73dux+6Ey+DEm4Dkm96h:9FBRgkS34+Udy4jIHKKL+6OEmukmi |
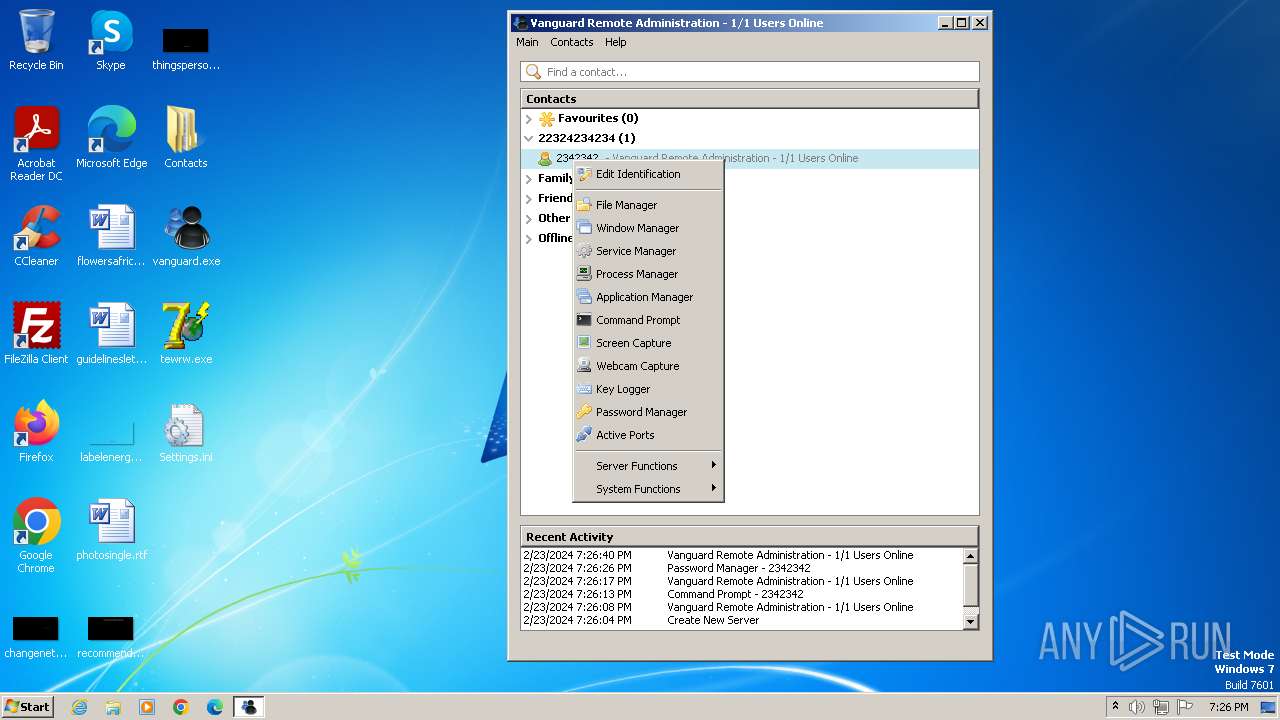
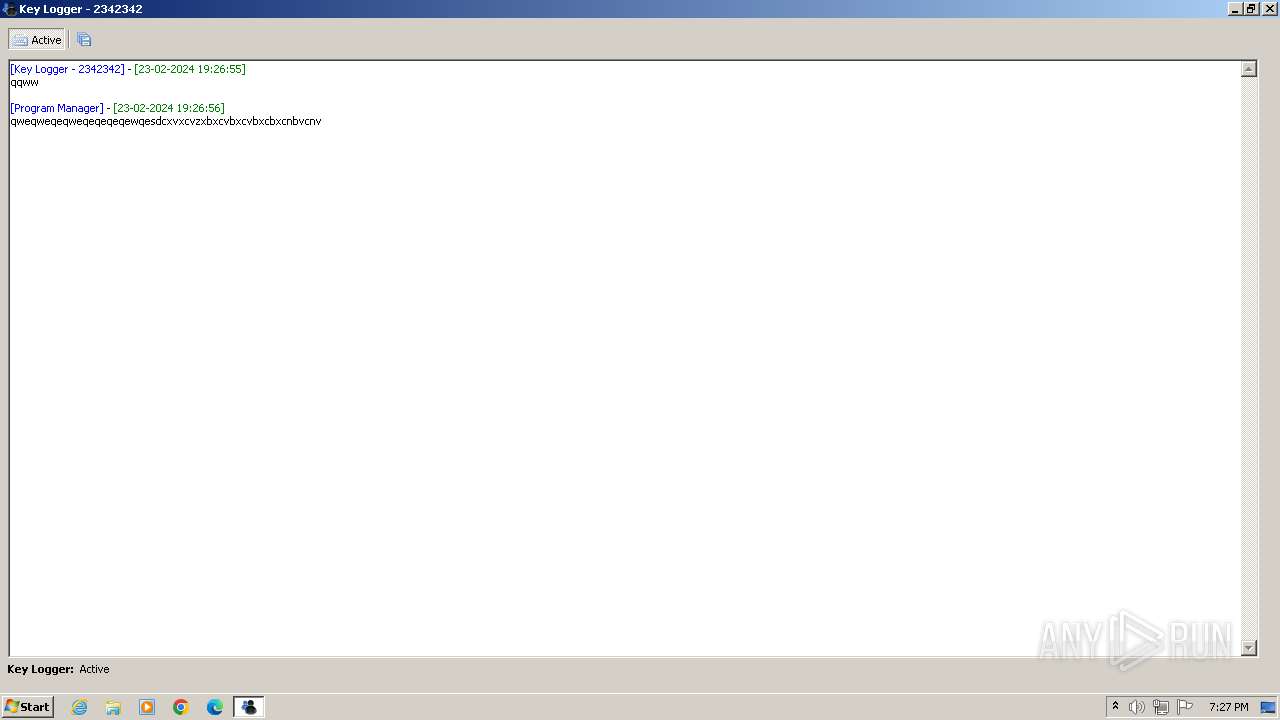
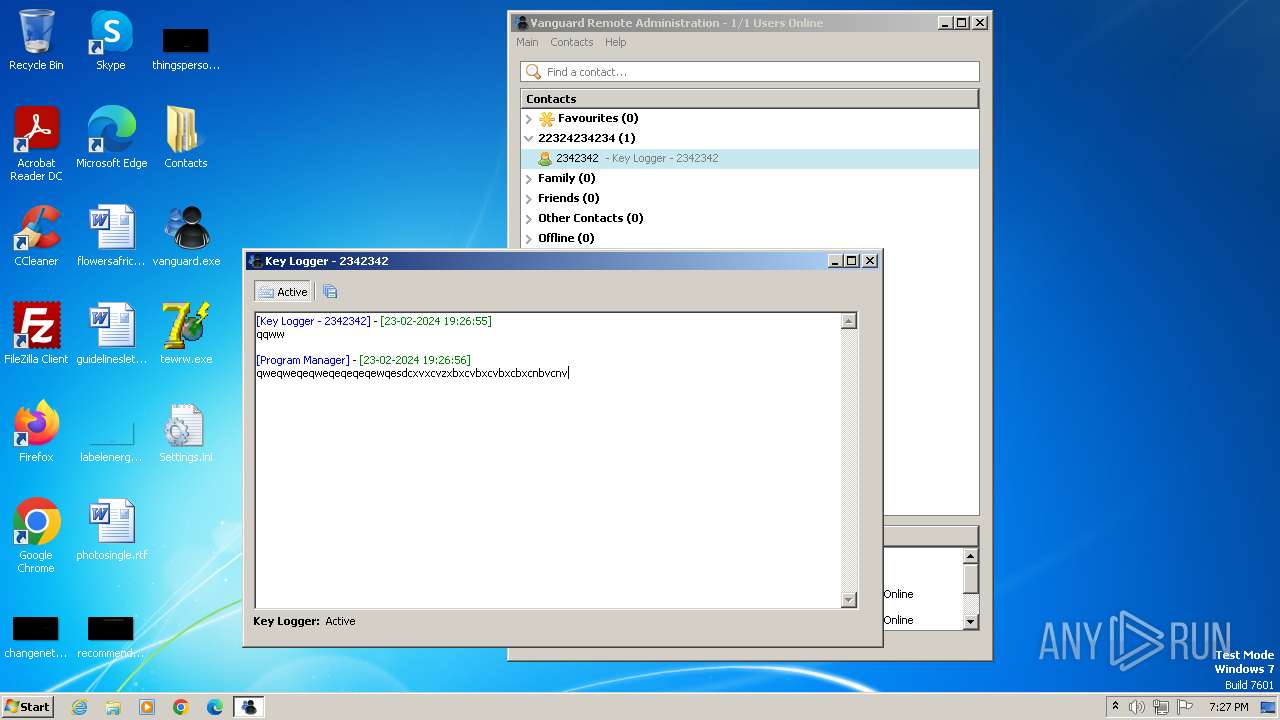
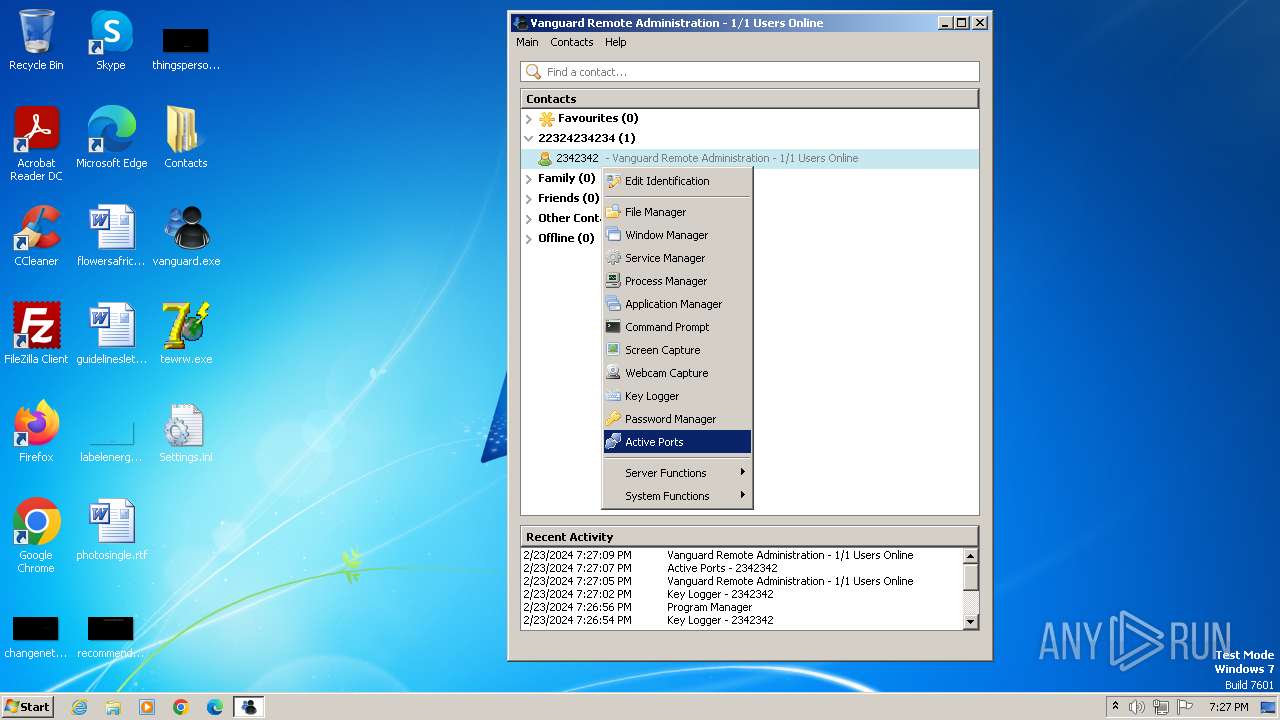
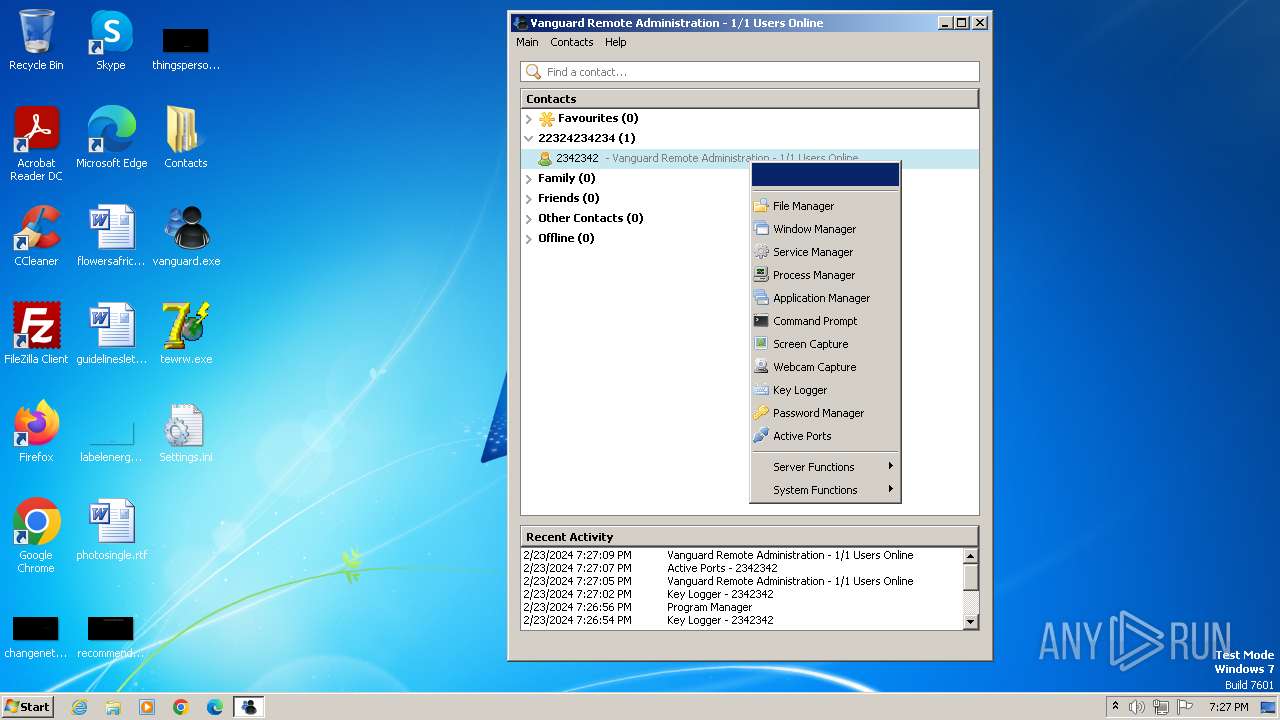
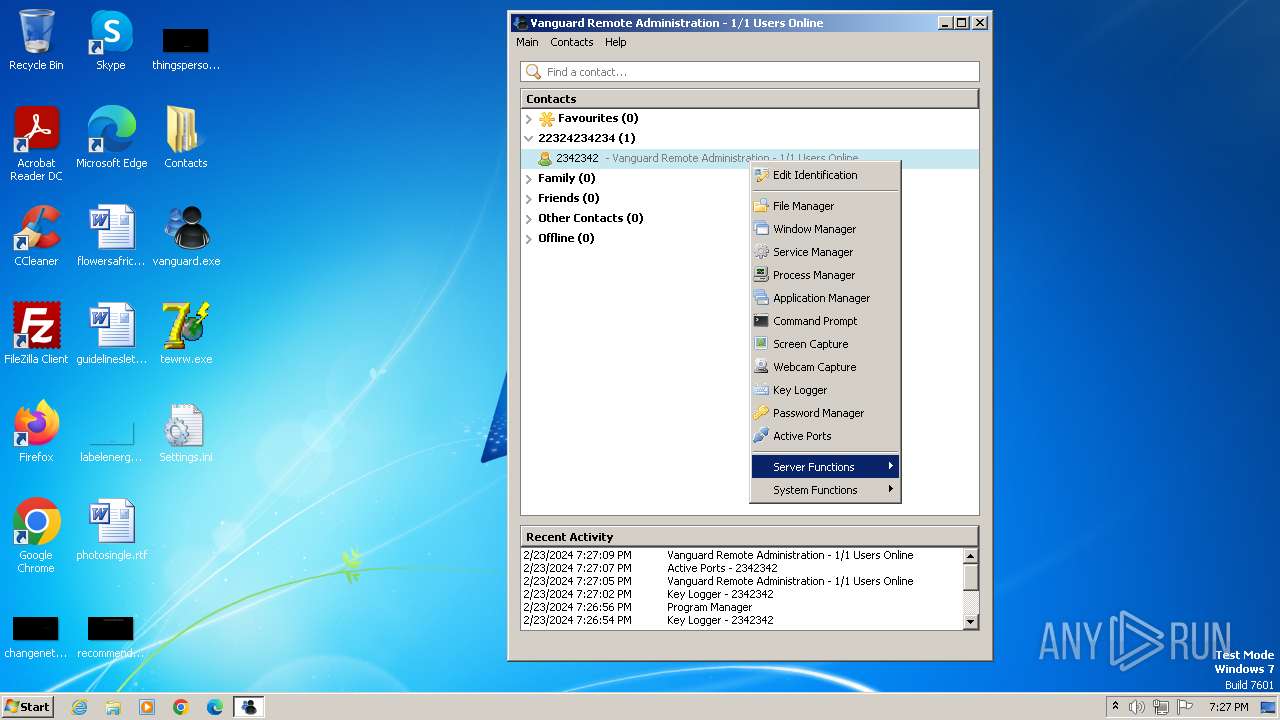
MALICIOUS
Drops the executable file immediately after the start
- vanguard.exe (PID: 3668)
- tewrw.exe (PID: 2332)
Changes the autorun value in the registry
- msedge.exe (PID: 864)
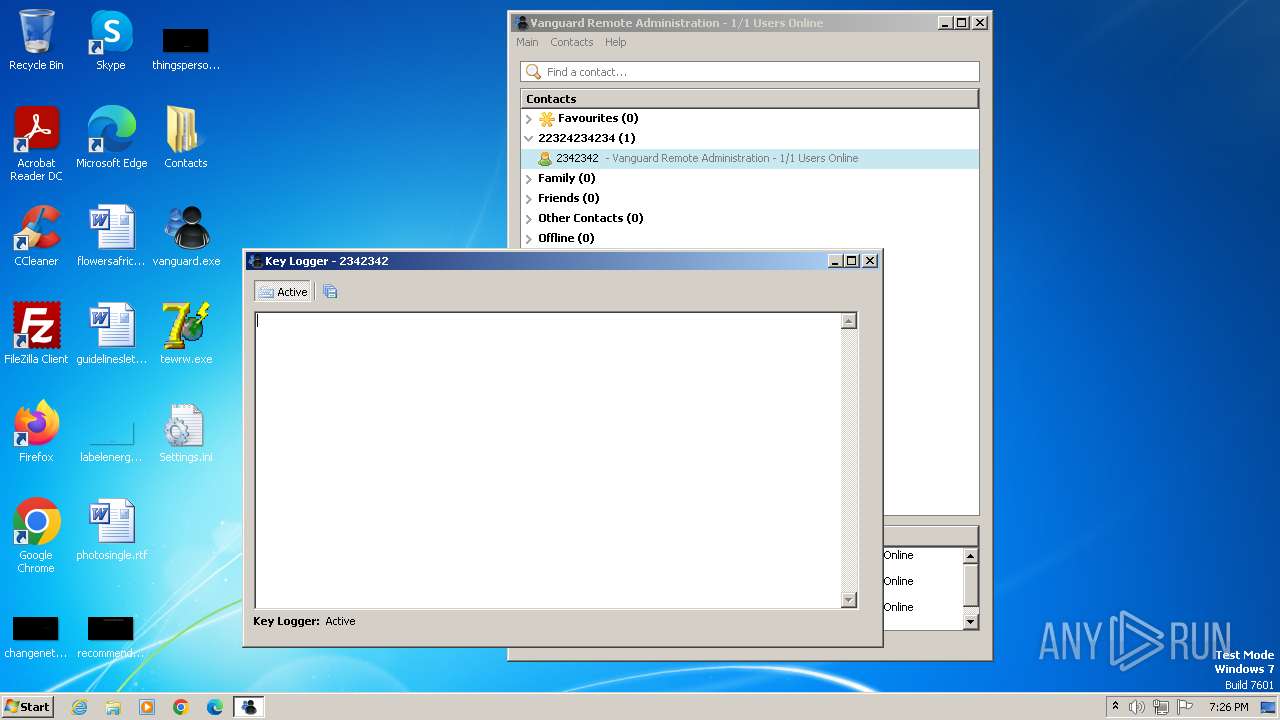
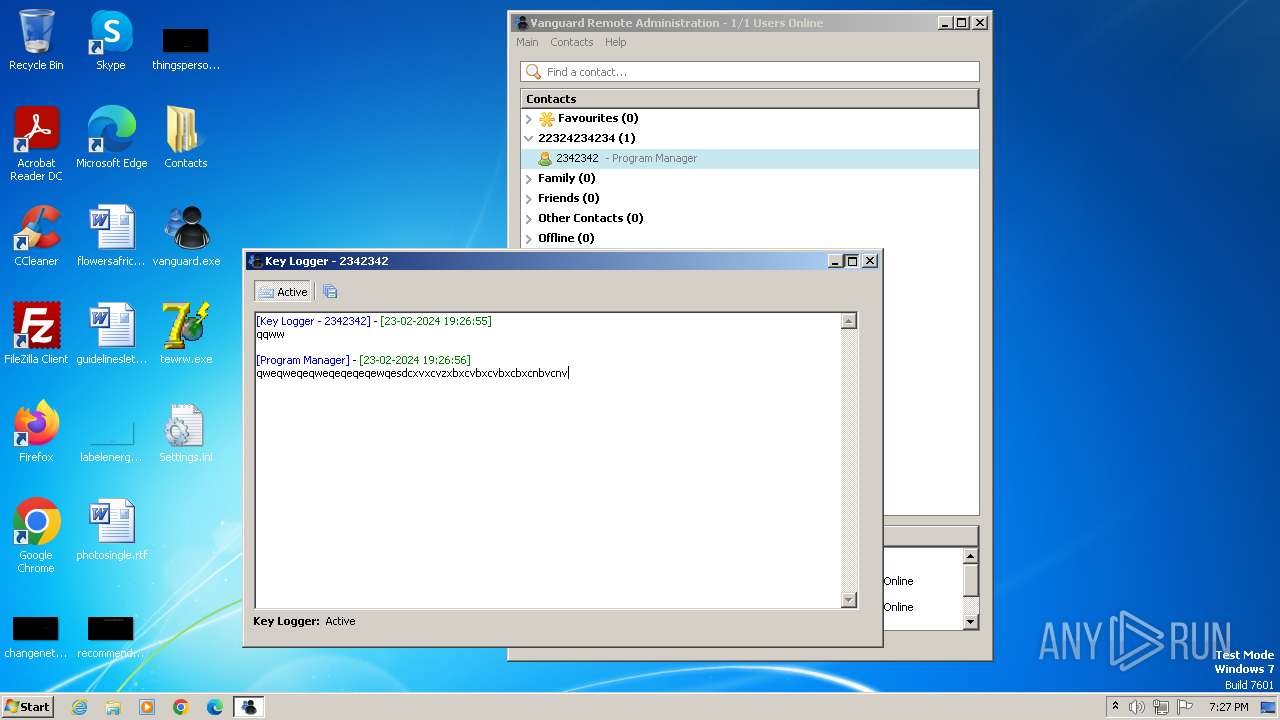
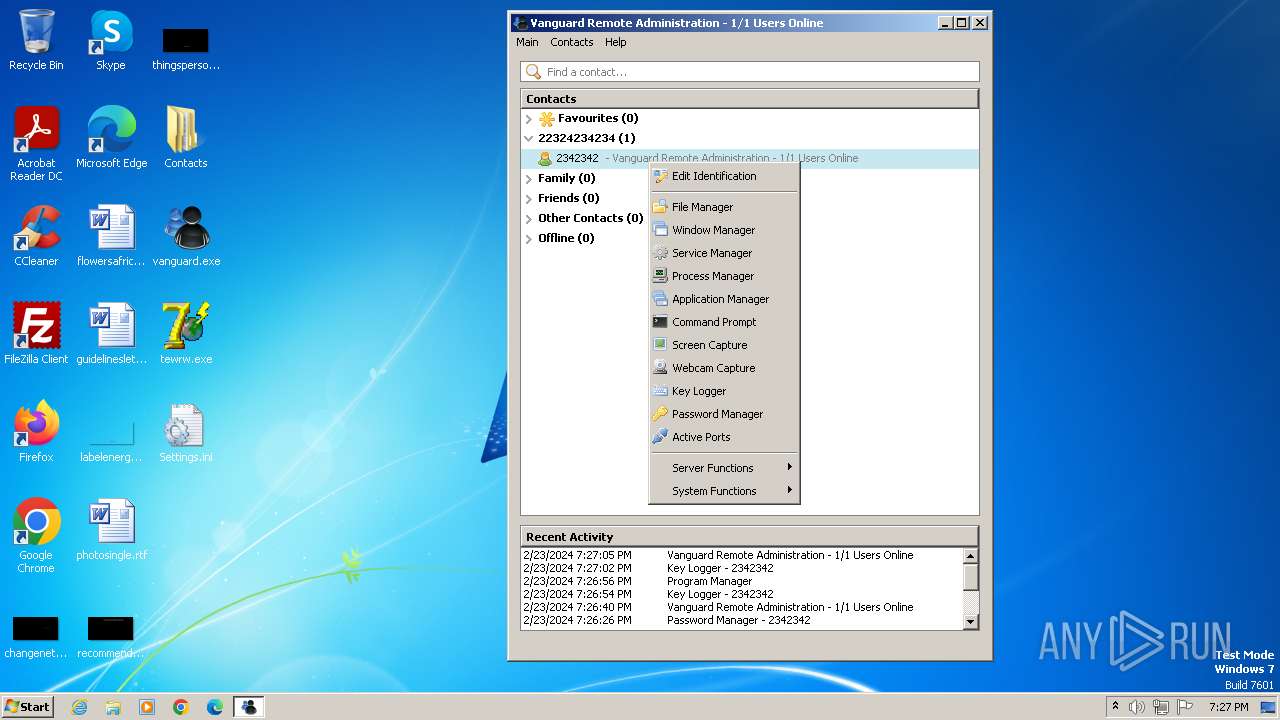
Actions looks like stealing of personal data
- Vanguard.exe (PID: 2364)
- Vanguard.exe (PID: 2440)
SUSPICIOUS
Reads the Internet Settings
- vanguard.exe (PID: 3668)
Starts itself from another location
- tewrw.exe (PID: 2332)
Executable content was dropped or overwritten
- tewrw.exe (PID: 2332)
- vanguard.exe (PID: 3668)
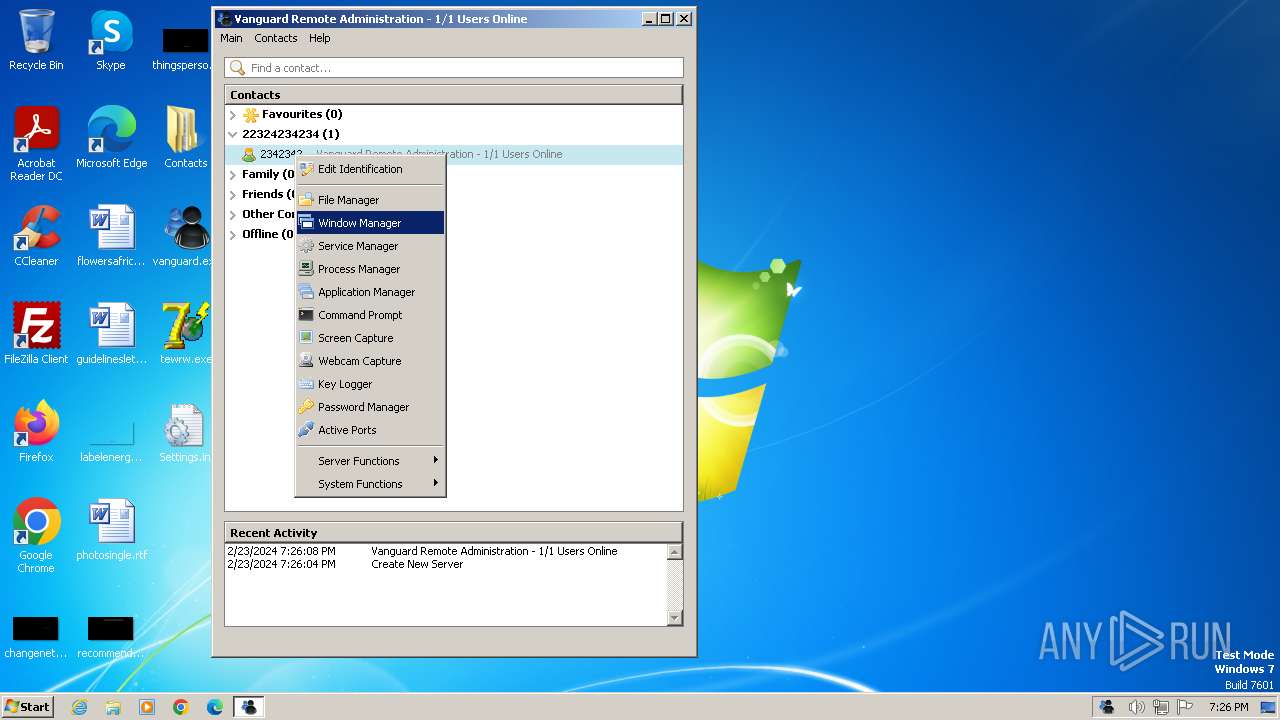
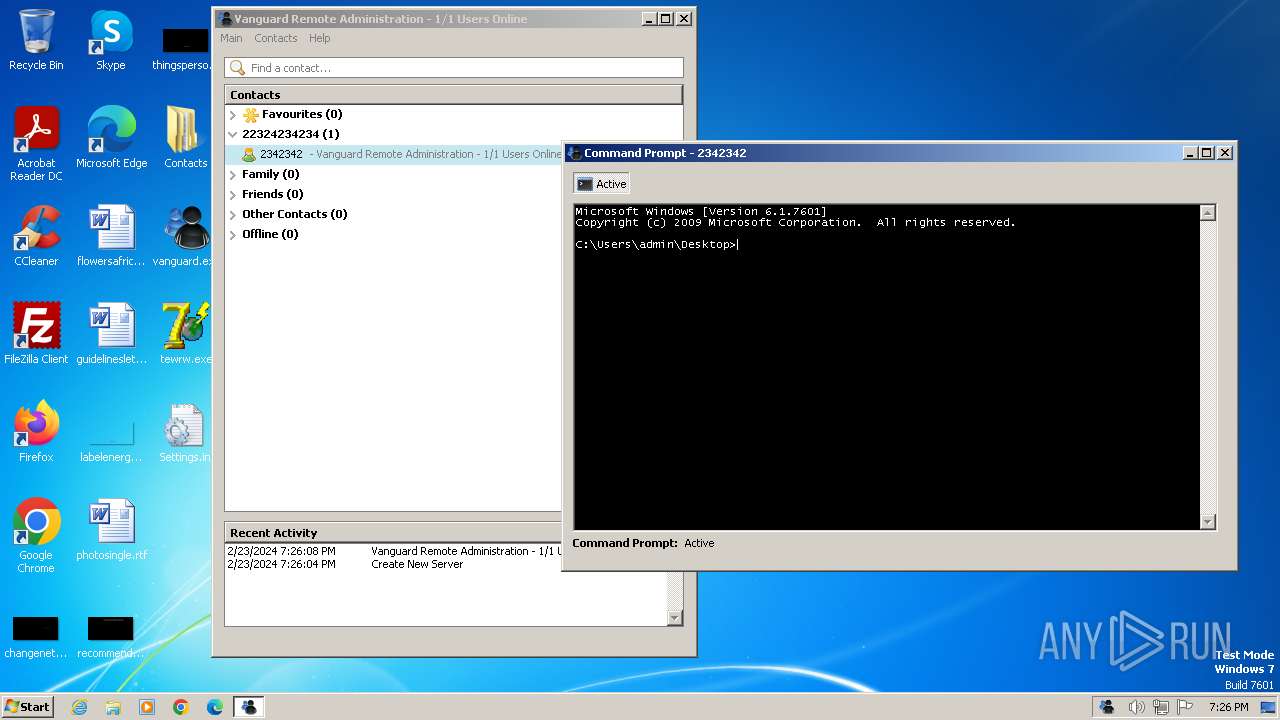
Starts CMD.EXE for commands execution
- msedge.exe (PID: 864)
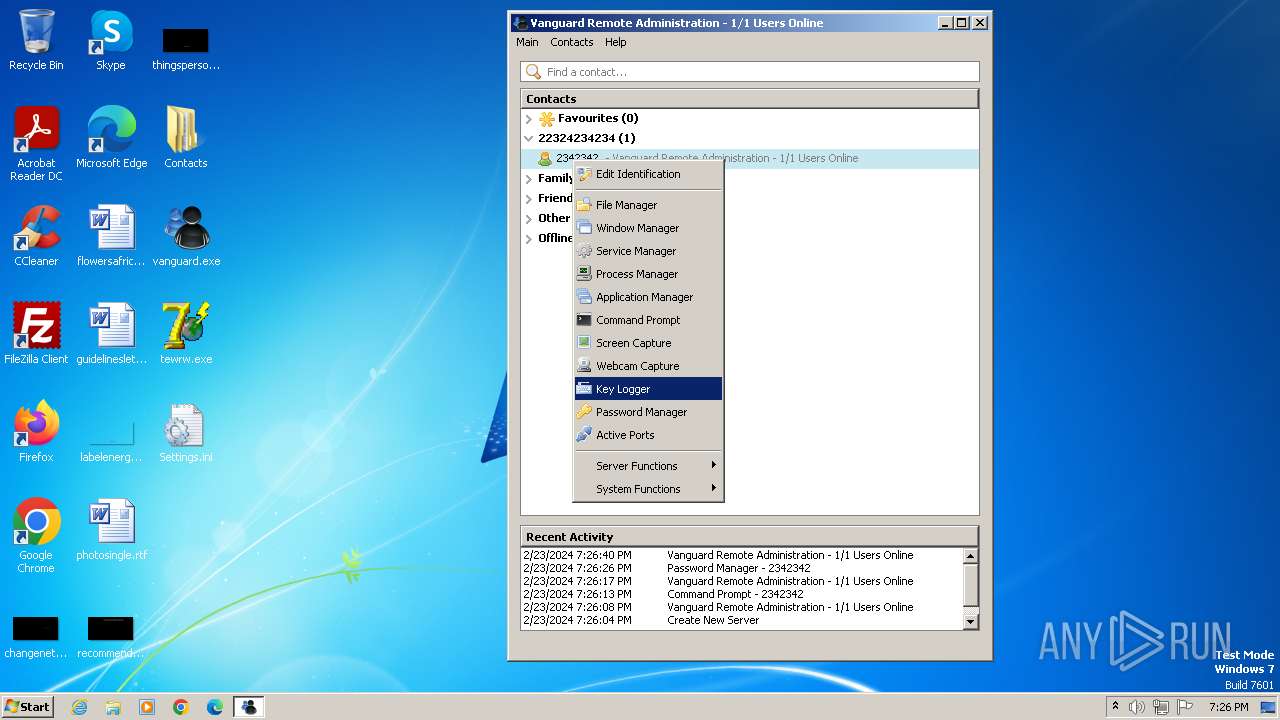
Loads DLL from Mozilla Firefox
- Vanguard.exe (PID: 2072)
- Vanguard.exe (PID: 2440)
Reads Mozilla Firefox installation path
- Vanguard.exe (PID: 2072)
INFO
Reads the computer name
- vanguard.exe (PID: 3668)
- Vanguard.exe (PID: 1972)
- Vanguard.exe (PID: 1040)
- msedge.exe (PID: 864)
- Vanguard.exe (PID: 3516)
- Vanguard.exe (PID: 2440)
- Vanguard.exe (PID: 2564)
- Vanguard.exe (PID: 2832)
- Vanguard.exe (PID: 2644)
Checks supported languages
- vanguard.exe (PID: 3668)
- tewrw.exe (PID: 2332)
- Vanguard.exe (PID: 1972)
- Vanguard.exe (PID: 2364)
- Vanguard.exe (PID: 1040)
- msedge.exe (PID: 864)
- Vanguard.exe (PID: 3516)
- Vanguard.exe (PID: 2072)
- Vanguard.exe (PID: 2440)
- Vanguard.exe (PID: 2564)
- Vanguard.exe (PID: 2644)
- Vanguard.exe (PID: 2832)
Manual execution by a user
- tewrw.exe (PID: 2332)
Reads the machine GUID from the registry
- vanguard.exe (PID: 3668)
- Vanguard.exe (PID: 2440)
- Vanguard.exe (PID: 3516)
Creates files or folders in the user directory
- tewrw.exe (PID: 2332)
Create files in a temporary directory
- Vanguard.exe (PID: 1972)
- Vanguard.exe (PID: 1040)
- msedge.exe (PID: 864)
- Vanguard.exe (PID: 3516)
- Vanguard.exe (PID: 2072)
- Vanguard.exe (PID: 2644)
- Vanguard.exe (PID: 2364)
- Vanguard.exe (PID: 2440)
- Vanguard.exe (PID: 2832)
- Vanguard.exe (PID: 2564)
Reads CPU info
- msedge.exe (PID: 864)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | UPX compressed Win32 Executable (29.5) |
|---|---|---|
| .exe | | | Win32 EXE Yoda's Crypter (29) |
| .exe | | | Win32 Executable Delphi generic (15.4) |
| .scr | | | Windows screen saver (14.3) |
| .exe | | | Win32 Executable (generic) (4.9) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 1992:06:19 22:22:17+00:00 |
| ImageFileCharacteristics: | No relocs, Executable, No line numbers, No symbols, Bytes reversed lo, 32-bit, Bytes reversed hi |
| PEType: | PE32 |
| LinkerVersion: | 2.25 |
| CodeSize: | 765440 |
| InitializedDataSize: | 1453056 |
| UninitializedDataSize: | - |
| EntryPoint: | 0xbbc08 |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 1.0.0.0 |
| ProductVersionNumber: | 1.0.0.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | English (British) |
| CharacterSet: | Windows, Latin1 |
| CompanyName: | - |
| FileDescription: | - |
| FileVersion: | 1.0.0.0 |
| InternalName: | - |
| LegalCopyright: | - |
| LegalTrademarks: | - |
| OriginalFileName: | - |
| ProductName: | - |
| ProductVersion: | 1.0.0.0 |
| Comments: | - |
Total processes
55
Monitored processes
13
Malicious processes
5
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 864 | -r | C:\Program Files\Microsoft\Edge\Application\msedge.exe | Vanguard.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Exit code: 0 Version: 109.0.1518.115 Modules
| |||||||||||||||
| 1040 | -r | C:\Users\admin\AppData\Local\Vanguard.exe | — | tewrw.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 1972 | /stext C:\Users\admin\AppData\Local\Temp\1626062 | C:\Users\admin\AppData\Local\Vanguard.exe | — | msedge.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 2072 | /stext C:\Users\admin\AppData\Local\Temp\1632656 | C:\Users\admin\AppData\Local\Vanguard.exe | — | msedge.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 2332 | "C:\Users\admin\Desktop\tewrw.exe" | C:\Users\admin\Desktop\tewrw.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 2364 | /stext C:\Users\admin\AppData\Local\Temp\1626640 | C:\Users\admin\AppData\Local\Vanguard.exe | msedge.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 2440 | /stext C:\Users\admin\AppData\Local\Temp\1627406 | C:\Users\admin\AppData\Local\Vanguard.exe | msedge.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 2564 | /stext C:\Users\admin\AppData\Local\Temp\1671343 | C:\Users\admin\AppData\Local\Vanguard.exe | — | msedge.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 2644 | /stext C:\Users\admin\AppData\Local\Temp\1666906 | C:\Users\admin\AppData\Local\Vanguard.exe | — | msedge.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 2832 | /stext C:\Users\admin\AppData\Local\Temp\1669125 | C:\Users\admin\AppData\Local\Vanguard.exe | — | msedge.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
Total events
6 617
Read events
6 555
Write events
54
Delete events
8
Modification events
| (PID) Process: | (3668) vanguard.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\182\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3668) vanguard.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\BagMRU |
| Operation: | write | Name: | NodeSlots |
Value: 0202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202 | |||
| (PID) Process: | (3668) vanguard.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\BagMRU |
| Operation: | write | Name: | MRUListEx |
Value: 02000000070000000100000006000000000000000B0000000C0000000D0000000A0000000900000008000000030000000500000004000000FFFFFFFF | |||
| (PID) Process: | (3668) vanguard.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\Bags\50\ComDlgLegacy |
| Operation: | write | Name: | TV_FolderType |
Value: {FBB3477E-C9E4-4B3B-A2BA-D3F5D3CD46F9} | |||
| (PID) Process: | (3668) vanguard.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\Bags\50\ComDlgLegacy |
| Operation: | write | Name: | TV_TopViewID |
Value: {82BA0782-5B7A-4569-B5D7-EC83085F08CC} | |||
| (PID) Process: | (3668) vanguard.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\Bags\50\ComDlgLegacy |
| Operation: | write | Name: | TV_TopViewVersion |
Value: 0 | |||
| (PID) Process: | (3668) vanguard.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\Bags\AllFolders\ComDlgLegacy\{FBB3477E-C9E4-4B3B-A2BA-D3F5D3CD46F9}\{82BA0782-5B7A-4569-B5D7-EC83085F08CC} |
| Operation: | write | Name: | Mode |
Value: 4 | |||
| (PID) Process: | (3668) vanguard.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\Bags\AllFolders\ComDlgLegacy\{FBB3477E-C9E4-4B3B-A2BA-D3F5D3CD46F9}\{82BA0782-5B7A-4569-B5D7-EC83085F08CC} |
| Operation: | write | Name: | LogicalViewMode |
Value: 1 | |||
| (PID) Process: | (3668) vanguard.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\Bags\AllFolders\ComDlgLegacy\{FBB3477E-C9E4-4B3B-A2BA-D3F5D3CD46F9}\{82BA0782-5B7A-4569-B5D7-EC83085F08CC} |
| Operation: | write | Name: | FFlags |
Value: | |||
| (PID) Process: | (3668) vanguard.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\Bags\AllFolders\ComDlgLegacy\{FBB3477E-C9E4-4B3B-A2BA-D3F5D3CD46F9}\{82BA0782-5B7A-4569-B5D7-EC83085F08CC} |
| Operation: | write | Name: | IconSize |
Value: 16 | |||
Executable files
2
Suspicious files
1
Text files
6
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2072 | Vanguard.exe | C:\Users\admin\AppData\Local\Temp\1632656 | — | |
MD5:— | SHA256:— | |||
| 3668 | vanguard.exe | C:\Users\admin\Desktop\Contacts\ContactList | binary | |
MD5:41A158C3FC3B72C6D97DFCF4AB1C46E2 | SHA256:E98492DFBE8E2384A89EF278BA4DE0F9C182EAFE1A3EF004A3C3E80BD07FF141 | |||
| 3668 | vanguard.exe | C:\Users\admin\Desktop\tewrw.exe | executable | |
MD5:36E462CE4666C7BAD2CB0A69F1EB7AC1 | SHA256:882C5D39A5DDD987C29FF7A880D9ECAFDBB4D6A5914AB556EB47F2324DFB8690 | |||
| 2364 | Vanguard.exe | C:\Users\admin\AppData\Local\Temp\1626640 | text | |
MD5:F3B25701FE362EC84616A93A45CE9998 | SHA256:B3D510EF04275CA8E698E5B3CBB0ECE3949EF9252F0CDC839E9EE347409A2209 | |||
| 2832 | Vanguard.exe | C:\Users\admin\AppData\Local\Temp\1669125 | text | |
MD5:6353069ECE7BD12AC36B639B3323EC6B | SHA256:4E5D7122869D55CEC7FBE41BD2775E39EF67607C45A2C3D8DEDB41661DDAE094 | |||
| 3668 | vanguard.exe | C:\Users\admin\Desktop\Settings.ini | text | |
MD5:0050538D9361241FDC50D59661946056 | SHA256:EE94F97F6430E6E558E794510CE1C7E0A85D74432B4C0FADD019B62989B9598C | |||
| 2644 | Vanguard.exe | C:\Users\admin\AppData\Local\Temp\1666906 | text | |
MD5:8BBA7413AE879358BD4924F8F33B70FA | SHA256:68B68AE4D42E3595A8E5E2B481035C0D7D8362B282AD862AB90C1C273DAA5052 | |||
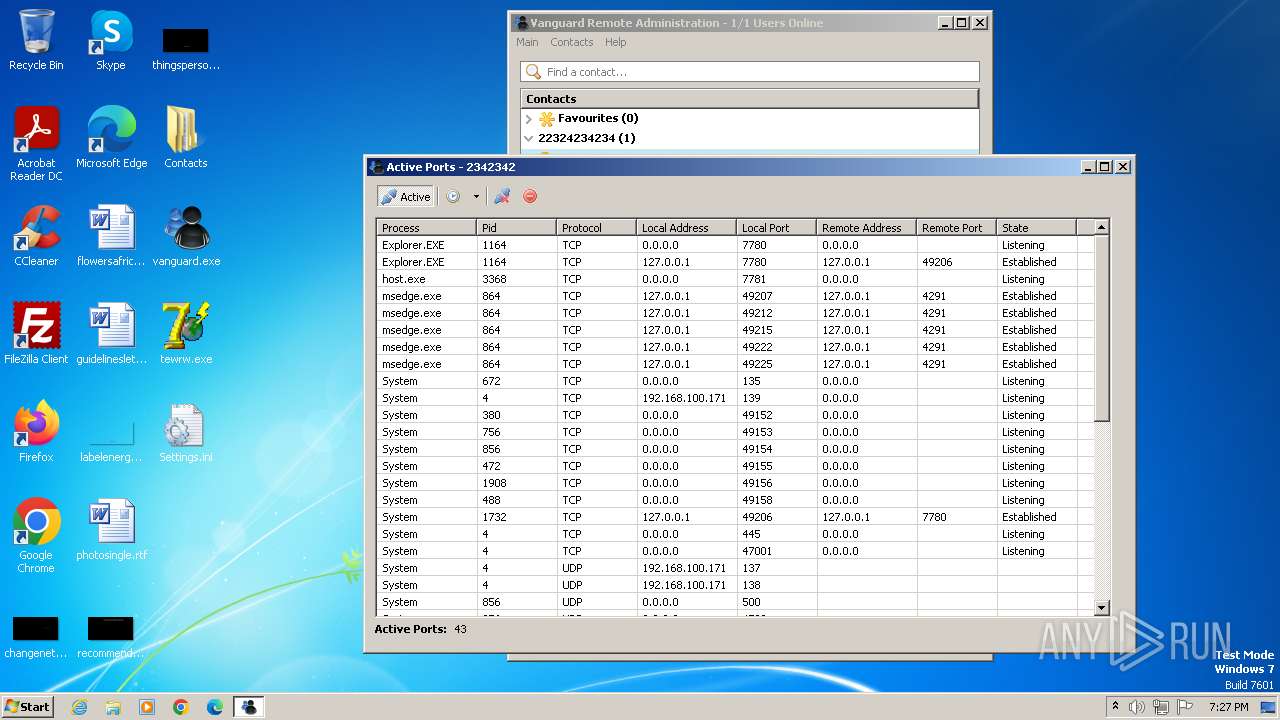
| 864 | msedge.exe | C:\Users\admin\AppData\Local\Temp\cports.cfg | text | |
MD5:E6A152C8963F65A5AD186EE7CDCF8235 | SHA256:57DA1A6C62B6E42589F5784EC73C982BFF376EE4455A56B0D4A29DFC086A125A | |||
| 2564 | Vanguard.exe | C:\Users\admin\AppData\Local\Temp\1671343 | text | |
MD5:F1669F63C0F6B6777AEB877C879BC532 | SHA256:1ACFE9FEE7305B77E7DD27D1C1E1F254377CF5E03B1399B74C5D25A1CE895D4A | |||
| 2332 | tewrw.exe | C:\Users\admin\AppData\Local\Vanguard.exe | executable | |
MD5:36E462CE4666C7BAD2CB0A69F1EB7AC1 | SHA256:882C5D39A5DDD987C29FF7A880D9ECAFDBB4D6A5914AB556EB47F2324DFB8690 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
4
DNS requests
0
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |