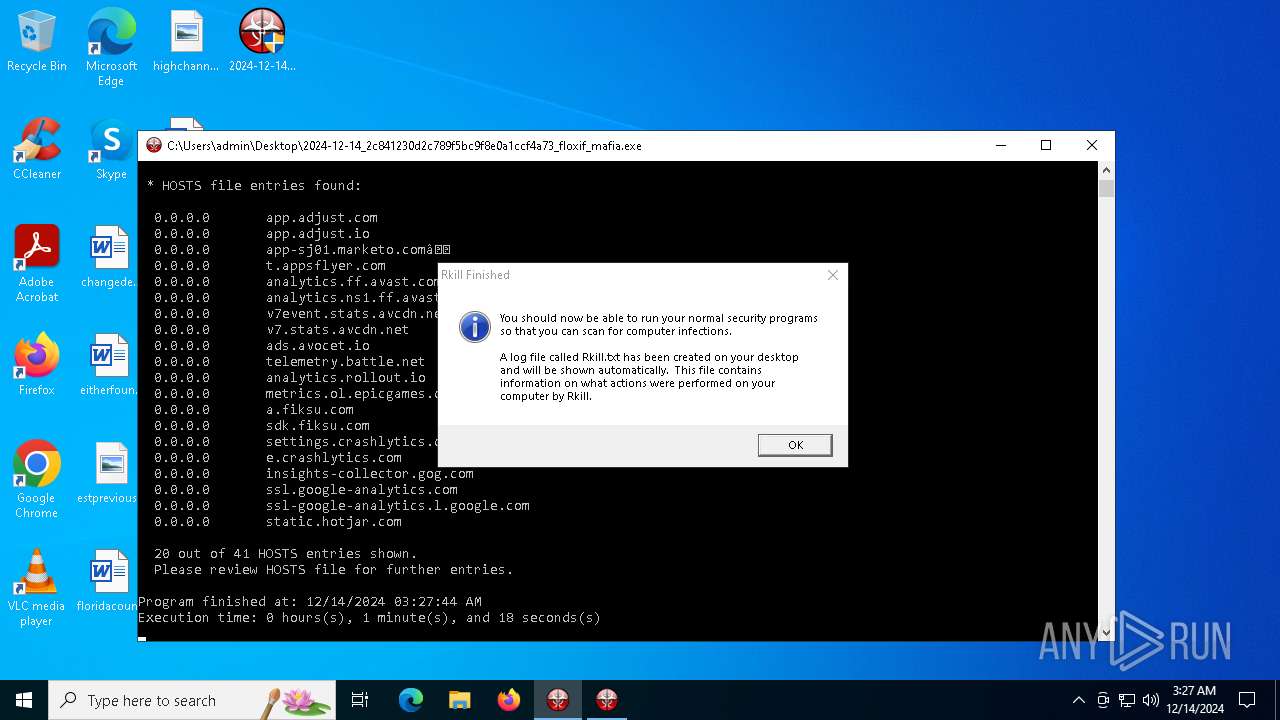
| File name: | 2024-12-14_2c841230d2c789f5bc9f8e0a1ccf4a73_floxif_mafia |
| Full analysis: | https://app.any.run/tasks/159e755b-1b55-474a-816d-6124bd2c68e5 |
| Verdict: | Malicious activity |
| Analysis date: | December 14, 2024, 03:26:11 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (console) Intel 80386, for MS Windows, 5 sections |
| MD5: | 2C841230D2C789F5BC9F8E0A1CCF4A73 |
| SHA1: | 3AC988938B9A260E54529493D8B1180788375455 |
| SHA256: | 8ED089C3EFC21889A22B14DA59FA220B4B89D0C271577D590EF1CE0DC377A5F1 |
| SSDEEP: | 49152:IfDhWV4z4uIs6q/sIkVsxYXtGgAANWQP6tSoqCMVNG60r7mMH56YYS9AlmH9CObz:IfDhWV4z4AYXtHNd6gpCMb0YmH9COb2G |
MALICIOUS
Executing a file with an untrusted certificate
- 2024-12-14_2c841230d2c789f5bc9f8e0a1ccf4a73_floxif_mafia.exe (PID: 3952)
- 2024-12-14_2c841230d2c789f5bc9f8e0a1ccf4a73_floxif_mafia.exe (PID: 936)
Connects to the CnC server
- 2024-12-14_2c841230d2c789f5bc9f8e0a1ccf4a73_floxif_mafia.exe (PID: 936)
FLOXIF has been detected (SURICATA)
- 2024-12-14_2c841230d2c789f5bc9f8e0a1ccf4a73_floxif_mafia.exe (PID: 936)
SUSPICIOUS
Process drops legitimate windows executable
- 2024-12-14_2c841230d2c789f5bc9f8e0a1ccf4a73_floxif_mafia.exe (PID: 936)
Executable content was dropped or overwritten
- 2024-12-14_2c841230d2c789f5bc9f8e0a1ccf4a73_floxif_mafia.exe (PID: 936)
Reads security settings of Internet Explorer
- 2024-12-14_2c841230d2c789f5bc9f8e0a1ccf4a73_floxif_mafia.exe (PID: 936)
- 2024-12-14_2c841230d2c789f5bc9f8e0a1ccf4a73_floxif_mafia64.exe (PID: 6028)
Contacting a server suspected of hosting an CnC
- 2024-12-14_2c841230d2c789f5bc9f8e0a1ccf4a73_floxif_mafia.exe (PID: 936)
Start notepad (likely ransomware note)
- 2024-12-14_2c841230d2c789f5bc9f8e0a1ccf4a73_floxif_mafia64.exe (PID: 6028)
Checks Windows Trust Settings
- 2024-12-14_2c841230d2c789f5bc9f8e0a1ccf4a73_floxif_mafia64.exe (PID: 6028)
INFO
Checks supported languages
- 2024-12-14_2c841230d2c789f5bc9f8e0a1ccf4a73_floxif_mafia.exe (PID: 936)
- 2024-12-14_2c841230d2c789f5bc9f8e0a1ccf4a73_floxif_mafia64.exe (PID: 6028)
The sample compiled with english language support
- 2024-12-14_2c841230d2c789f5bc9f8e0a1ccf4a73_floxif_mafia.exe (PID: 936)
Reads the computer name
- 2024-12-14_2c841230d2c789f5bc9f8e0a1ccf4a73_floxif_mafia.exe (PID: 936)
- 2024-12-14_2c841230d2c789f5bc9f8e0a1ccf4a73_floxif_mafia64.exe (PID: 6028)
Reads product name
- 2024-12-14_2c841230d2c789f5bc9f8e0a1ccf4a73_floxif_mafia64.exe (PID: 6028)
Reads Environment values
- 2024-12-14_2c841230d2c789f5bc9f8e0a1ccf4a73_floxif_mafia64.exe (PID: 6028)
Reads the software policy settings
- 2024-12-14_2c841230d2c789f5bc9f8e0a1ccf4a73_floxif_mafia64.exe (PID: 6028)
Creates files or folders in the user directory
- 2024-12-14_2c841230d2c789f5bc9f8e0a1ccf4a73_floxif_mafia64.exe (PID: 6028)
Checks proxy server information
- 2024-12-14_2c841230d2c789f5bc9f8e0a1ccf4a73_floxif_mafia.exe (PID: 936)
- 2024-12-14_2c841230d2c789f5bc9f8e0a1ccf4a73_floxif_mafia64.exe (PID: 6028)
Creates files in the program directory
- 2024-12-14_2c841230d2c789f5bc9f8e0a1ccf4a73_floxif_mafia.exe (PID: 936)
Reads the machine GUID from the registry
- 2024-12-14_2c841230d2c789f5bc9f8e0a1ccf4a73_floxif_mafia64.exe (PID: 6028)
UPX packer has been detected
- 2024-12-14_2c841230d2c789f5bc9f8e0a1ccf4a73_floxif_mafia.exe (PID: 936)
Reads security settings of Internet Explorer
- notepad.exe (PID: 5576)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable MS Visual C++ (generic) (42.2) |
|---|---|---|
| .exe | | | Win64 Executable (generic) (37.3) |
| .dll | | | Win32 Dynamic Link Library (generic) (8.8) |
| .exe | | | Win32 Executable (generic) (6) |
| .exe | | | Generic Win/DOS Executable (2.7) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2018:03:13 15:08:50+00:00 |
| ImageFileCharacteristics: | Executable, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 10 |
| CodeSize: | 448512 |
| InitializedDataSize: | 1341952 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x52cbb |
| OSVersion: | 5.1 |
| ImageVersion: | - |
| SubsystemVersion: | 5.1 |
| Subsystem: | Windows command line |
| FileVersionNumber: | 2.9.1.0 |
| ProductVersionNumber: | 2.9.1.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Windows NT 32-bit |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | English (U.S.) |
| CharacterSet: | Unicode |
| CompanyName: | Bleeping Computer, LLC |
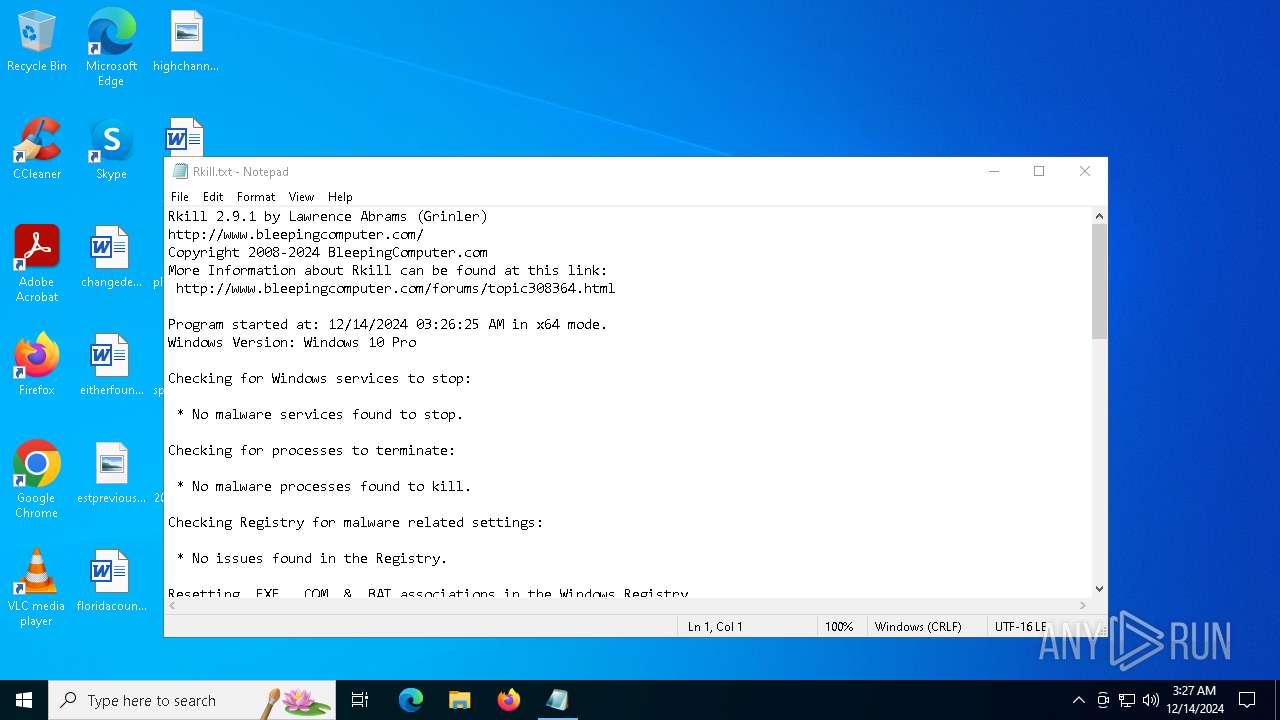
| FileDescription: | Terminates malware processes so that you can run your normal security programs. |
| FileVersion: | 2.9.1 |
| InternalName: | rkill.exe |
| LegalCopyright: | © BleepingComputer.com. All rights reserved. |
| LegalTrademarks1: | - |
| LegalTrademarks2: | - |
| OriginalFileName: | rkill.exe |
| ProductName: | Rkill |
| ProductVersion: | 2.9.1 |
Total processes
123
Monitored processes
5
Malicious processes
2
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
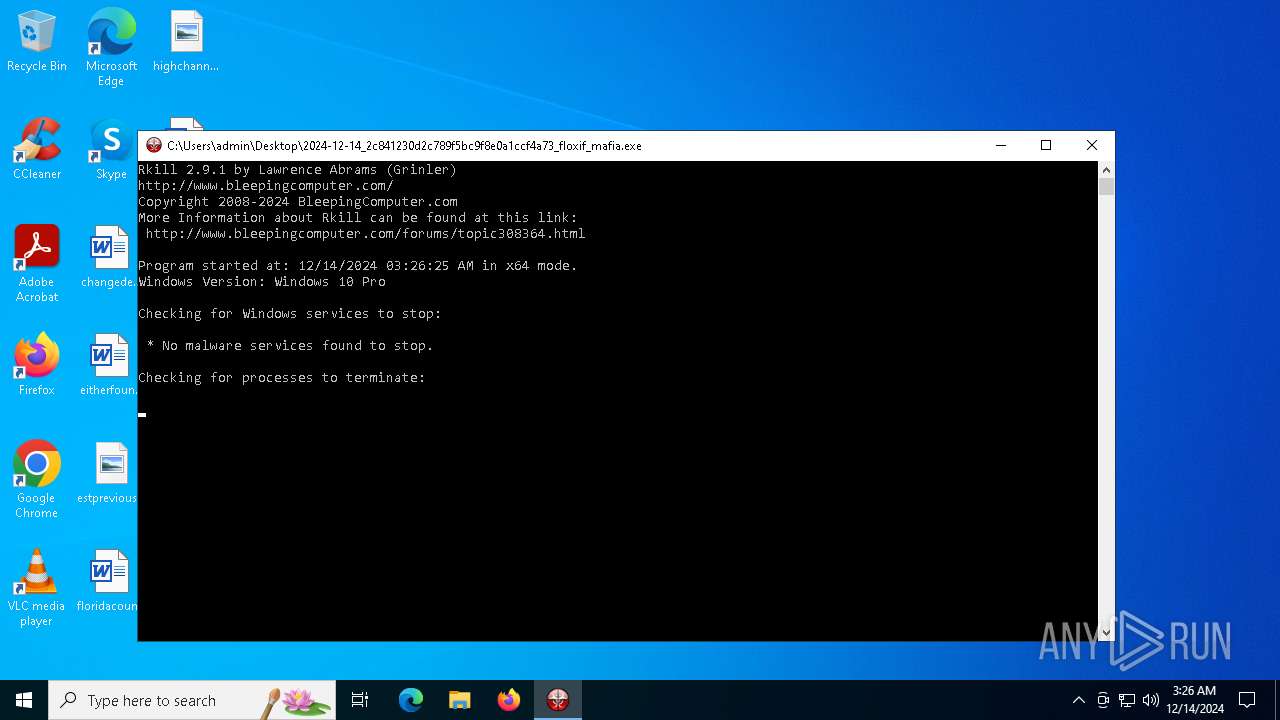
| 936 | "C:\Users\admin\Desktop\2024-12-14_2c841230d2c789f5bc9f8e0a1ccf4a73_floxif_mafia.exe" | C:\Users\admin\Desktop\2024-12-14_2c841230d2c789f5bc9f8e0a1ccf4a73_floxif_mafia.exe | explorer.exe | ||||||||||||
User: admin Company: Bleeping Computer, LLC Integrity Level: HIGH Description: Terminates malware processes so that you can run your normal security programs. Exit code: 1 Version: 2.9.1 Modules
| |||||||||||||||
| 3952 | "C:\Users\admin\Desktop\2024-12-14_2c841230d2c789f5bc9f8e0a1ccf4a73_floxif_mafia.exe" | C:\Users\admin\Desktop\2024-12-14_2c841230d2c789f5bc9f8e0a1ccf4a73_floxif_mafia.exe | — | explorer.exe | |||||||||||
User: admin Company: Bleeping Computer, LLC Integrity Level: MEDIUM Description: Terminates malware processes so that you can run your normal security programs. Exit code: 3221226540 Version: 2.9.1 Modules
| |||||||||||||||
| 4716 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | 2024-12-14_2c841230d2c789f5bc9f8e0a1ccf4a73_floxif_mafia.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
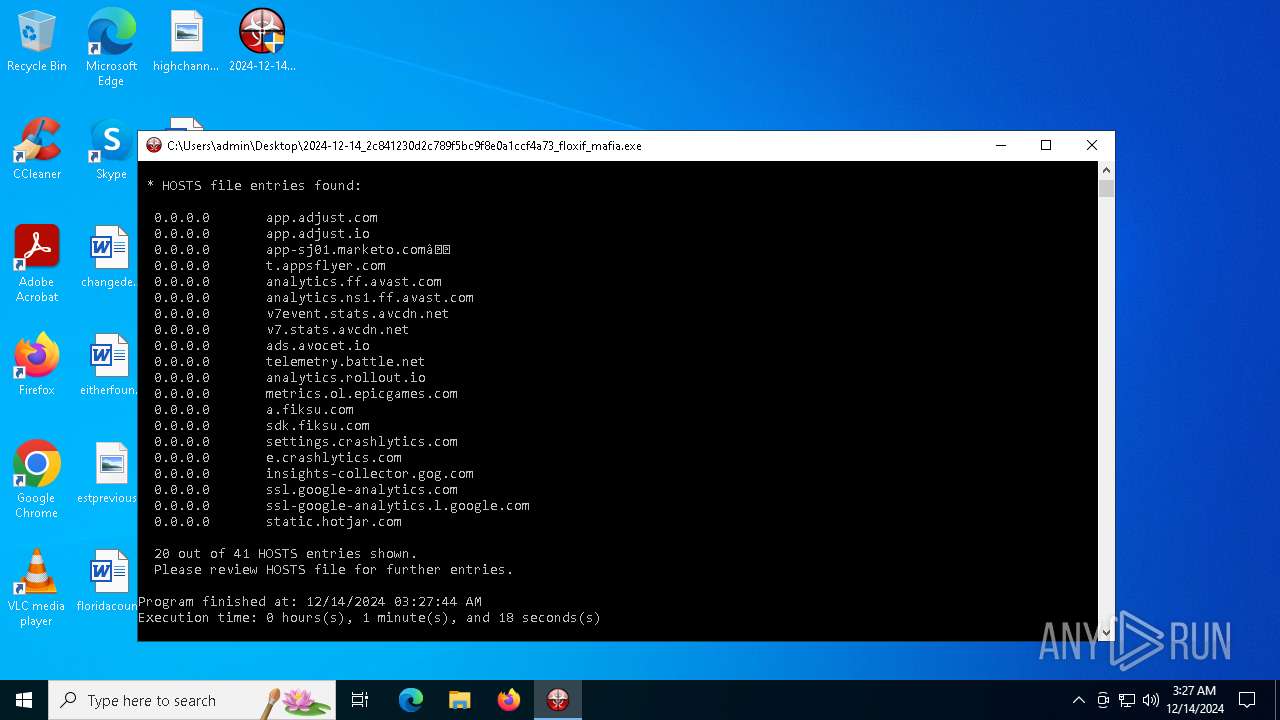
| 5576 | Notepad.exe C:\Users\admin\Desktop\Rkill.txt | C:\Windows\System32\notepad.exe | — | 2024-12-14_2c841230d2c789f5bc9f8e0a1ccf4a73_floxif_mafia64.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Notepad Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
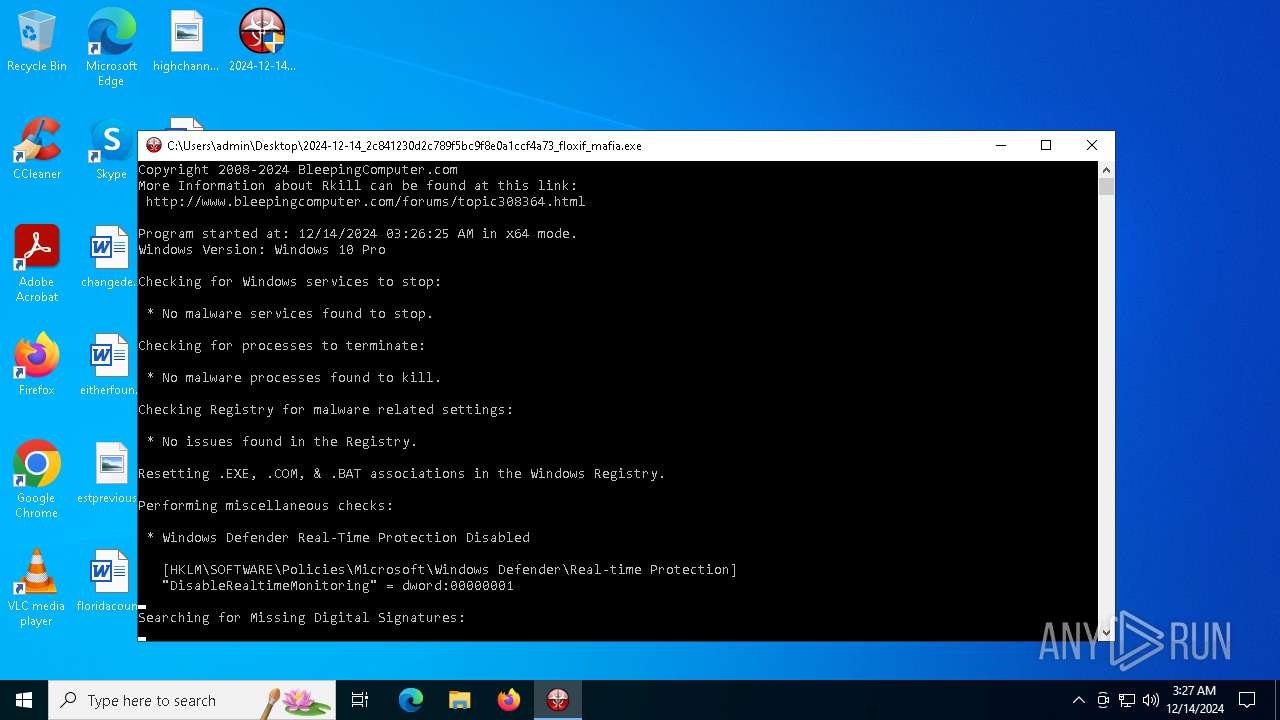
| 6028 | C:\Users\admin\Desktop\2024-12-14_2c841230d2c789f5bc9f8e0a1ccf4a73_floxif_mafia.exe | C:\Users\admin\Desktop\2024-12-14_2c841230d2c789f5bc9f8e0a1ccf4a73_floxif_mafia64.exe | 2024-12-14_2c841230d2c789f5bc9f8e0a1ccf4a73_floxif_mafia.exe | ||||||||||||
User: admin Company: Bleeping Computer, LLC Integrity Level: HIGH Description: Terminates malware processes so that you can run your normal security programs. Exit code: 0 Version: 2.9.1 Modules
| |||||||||||||||
Total events
8 514
Read events
8 511
Write events
3
Delete events
0
Modification events
| (PID) Process: | (936) 2024-12-14_2c841230d2c789f5bc9f8e0a1ccf4a73_floxif_mafia.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (936) 2024-12-14_2c841230d2c789f5bc9f8e0a1ccf4a73_floxif_mafia.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (936) 2024-12-14_2c841230d2c789f5bc9f8e0a1ccf4a73_floxif_mafia.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
Executable files
1
Suspicious files
4
Text files
2
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 936 | 2024-12-14_2c841230d2c789f5bc9f8e0a1ccf4a73_floxif_mafia.exe | C:\Program Files\Common Files\System\symsrv.dll | executable | |
MD5:7574CF2C64F35161AB1292E2F532AABF | SHA256:DE055A89DE246E629A8694BDE18AF2B1605E4B9B493C7E4AEF669DD67ACF5085 | |||
| 6028 | 2024-12-14_2c841230d2c789f5bc9f8e0a1ccf4a73_floxif_mafia64.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\A583E2A51BFBDC1E492A57B7C8325850 | binary | |
MD5:5A0FF88B03934F316CABAF56A8B630E7 | SHA256:B2F5F4CD53B65E255D4BB4E41FD35A51B1C522F109B4A6CA4AE01C8563F9C4B5 | |||
| 6028 | 2024-12-14_2c841230d2c789f5bc9f8e0a1ccf4a73_floxif_mafia64.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\A583E2A51BFBDC1E492A57B7C8325850 | der | |
MD5:BEA650E9D669CF1C6C2EA6DEF826B955 | SHA256:E259199F60C1F26999723B5B2C2120DF8D35440B3F606DC0F8B79C896F54B49E | |||
| 6028 | 2024-12-14_2c841230d2c789f5bc9f8e0a1ccf4a73_floxif_mafia64.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\45AE547469FB7137480E06153457A2DD | der | |
MD5:EB96A226DBF9DA7CF68B34D73451A146 | SHA256:BE1C8655CC8E70C71A3DFE6266A325857C5DE2136FB17FD5ECFA8D6F93041D3F | |||
| 936 | 2024-12-14_2c841230d2c789f5bc9f8e0a1ccf4a73_floxif_mafia.exe | C:\Program Files\Common Files\System\symsrv.dll.000 | text | |
MD5:1130C911BF5DB4B8F7CF9B6F4B457623 | SHA256:EBA08CC8182F379392A97F542B350EA0DBBE5E4009472F35AF20E3D857EAFDF1 | |||
| 936 | 2024-12-14_2c841230d2c789f5bc9f8e0a1ccf4a73_floxif_mafia.exe | C:\Users\admin\Desktop\Rkill.txt | text | |
MD5:F3B25701FE362EC84616A93A45CE9998 | SHA256:B3D510EF04275CA8E698E5B3CBB0ECE3949EF9252F0CDC839E9EE347409A2209 | |||
| 6028 | 2024-12-14_2c841230d2c789f5bc9f8e0a1ccf4a73_floxif_mafia64.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\45AE547469FB7137480E06153457A2DD | binary | |
MD5:D701C8A6DF1874F783CA1EC588EA30FC | SHA256:754BE22EBC1AD9EDDBA4FDDFDBC28BE4840C7C458F0E8DC89423EAB3E83E0E7D | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
12
TCP/UDP connections
24
DNS requests
12
Threats
6
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2548 | svchost.exe | GET | 200 | 23.53.40.178:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
2548 | svchost.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | GET | 200 | 23.53.40.178:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
6028 | 2024-12-14_2c841230d2c789f5bc9f8e0a1ccf4a73_floxif_mafia64.exe | GET | 200 | 23.53.40.178:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut_2010-06-23.crl | unknown | — | — | whitelisted |
6028 | 2024-12-14_2c841230d2c789f5bc9f8e0a1ccf4a73_floxif_mafia64.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicWinProPCA2011_2011-10-19.crl%20 | unknown | — | — | whitelisted |
936 | 2024-12-14_2c841230d2c789f5bc9f8e0a1ccf4a73_floxif_mafia.exe | GET | 403 | 45.33.20.235:80 | http://www.aieov.com/logo.gif | unknown | — | — | malicious |
936 | 2024-12-14_2c841230d2c789f5bc9f8e0a1ccf4a73_floxif_mafia.exe | GET | 403 | 45.33.20.235:80 | http://www.aieov.com/logo.gif | unknown | — | — | malicious |
936 | 2024-12-14_2c841230d2c789f5bc9f8e0a1ccf4a73_floxif_mafia.exe | GET | 403 | 45.33.20.235:80 | http://www.aieov.com/logo.gif | unknown | — | — | malicious |
— | — | GET | 403 | 45.33.20.235:80 | http://www.aieov.com/logo.gif | unknown | — | — | malicious |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4712 | MoUsoCoreWorker.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 192.168.100.255:138 | — | — | — | whitelisted |
2548 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4712 | MoUsoCoreWorker.exe | 23.53.40.178:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
2548 | svchost.exe | 23.53.40.178:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
4712 | MoUsoCoreWorker.exe | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
2548 | svchost.exe | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
6028 | 2024-12-14_2c841230d2c789f5bc9f8e0a1ccf4a73_floxif_mafia64.exe | 23.53.40.178:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
4712 | MoUsoCoreWorker.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
5isohu.com |
| whitelisted |
www.aieov.com |
| malicious |
self.events.data.microsoft.com |
| whitelisted |
Threats
6 ETPRO signatures available at the full report