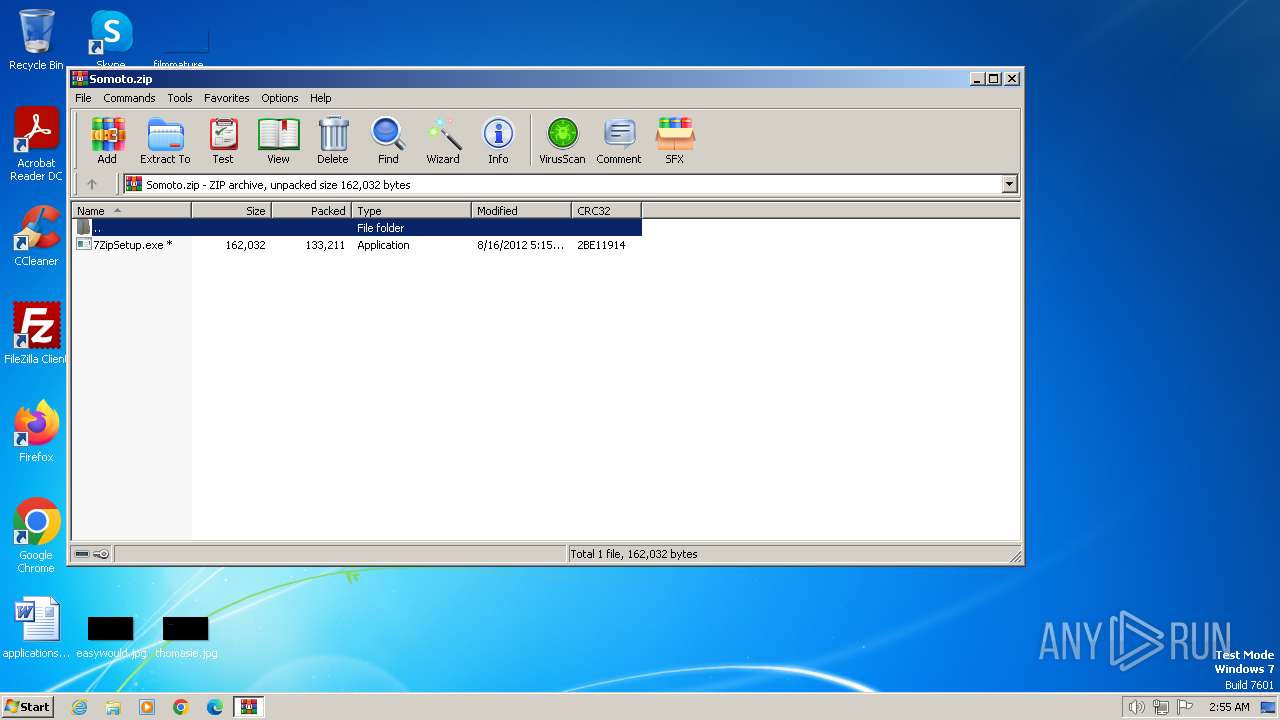
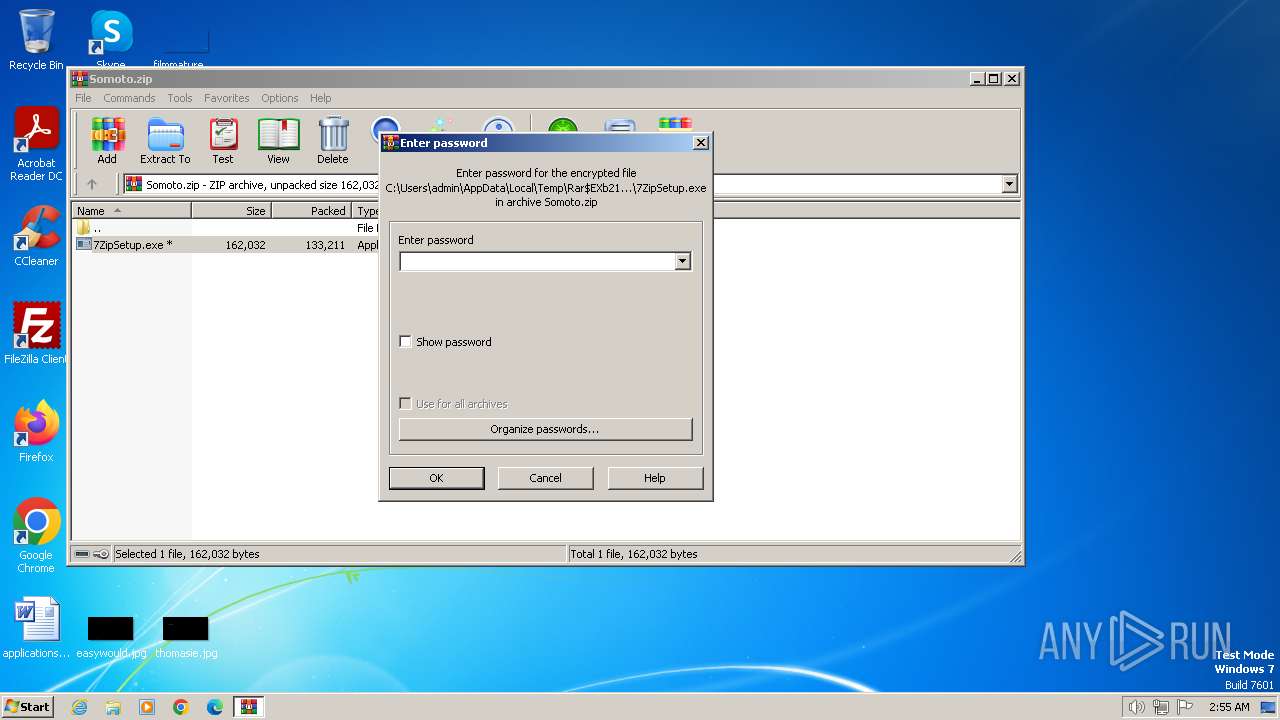
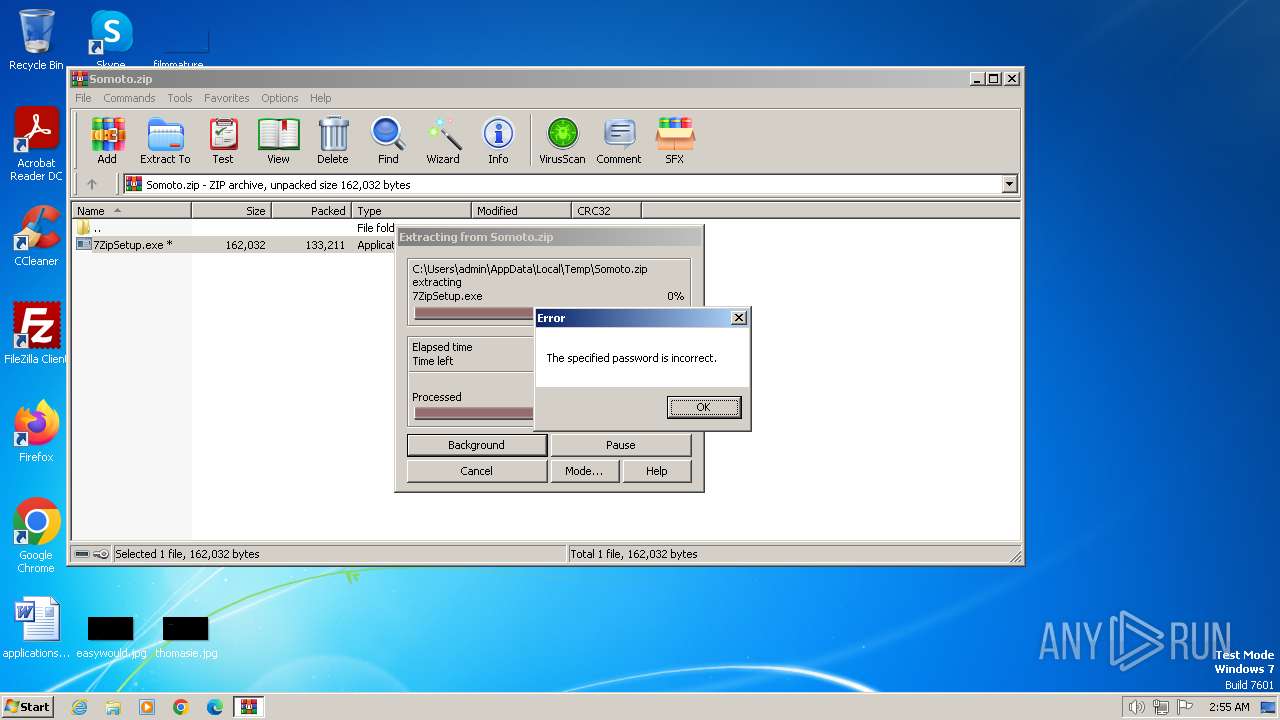
| File name: | Somoto.zip |
| Full analysis: | https://app.any.run/tasks/b12282e7-b295-4513-9875-22f8f94123ec |
| Verdict: | Malicious activity |
| Analysis date: | April 11, 2024, 01:55:03 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract, compression method=deflate |
| MD5: | 3387F0112FA04D36C45A82EE0A5322DB |
| SHA1: | D7C4DA148E0B61D39CD8B895B16F826F4E9AA398 |
| SHA256: | 8EC1C71E228993CFABC0A084C47E3C5EA63E0F8A74F5DC46EAA2E0A2717B4C22 |
| SSDEEP: | 3072:Oa16QcTwP58YZcbArZmNxLm9nD24NMaJs9PHVwWxboMxtDHIZWdI:Oa1/N8YZcboZjnDvN1JC/VwEboMxRod |
MALICIOUS
Drops the executable file immediately after the start
- 7ZipSetup.exe (PID: 2064)
- WinRAR.exe (PID: 2120)
SUSPICIOUS
Reads security settings of Internet Explorer
- biclient.exe (PID: 2688)
- WinRAR.exe (PID: 2120)
Executable content was dropped or overwritten
- 7ZipSetup.exe (PID: 2064)
Reads the Internet Settings
- biclient.exe (PID: 2688)
Reads Microsoft Outlook installation path
- biclient.exe (PID: 2688)
Reads settings of System Certificates
- biclient.exe (PID: 2688)
Reads Internet Explorer settings
- biclient.exe (PID: 2688)
Checks Windows Trust Settings
- biclient.exe (PID: 2688)
INFO
Executable content was dropped or overwritten
- WinRAR.exe (PID: 2120)
Reads the computer name
- 7ZipSetup.exe (PID: 2064)
- biclient.exe (PID: 2688)
Checks supported languages
- 7ZipSetup.exe (PID: 2064)
- biclient.exe (PID: 2688)
Reads the machine GUID from the registry
- biclient.exe (PID: 2688)
Create files in a temporary directory
- 7ZipSetup.exe (PID: 2064)
Checks proxy server information
- biclient.exe (PID: 2688)
Reads the software policy settings
- biclient.exe (PID: 2688)
Creates files or folders in the user directory
- biclient.exe (PID: 2688)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | 0x0009 |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2012:08:16 17:15:42 |
| ZipCRC: | 0x2be11914 |
| ZipCompressedSize: | 133211 |
| ZipUncompressedSize: | 162032 |
| ZipFileName: | 7ZipSetup.exe |
Total processes
43
Monitored processes
4
Malicious processes
3
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2064 | "C:\Users\admin\AppData\Local\Temp\Rar$EXb2120.1879\7ZipSetup.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXb2120.1879\7ZipSetup.exe | WinRAR.exe | ||||||||||||
User: admin Integrity Level: HIGH Description: Powered by BetterInstaller Exit code: 0 Version: 2.0.0.0 Modules
| |||||||||||||||
| 2120 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\Somoto.zip" | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Version: 5.91.0 Modules
| |||||||||||||||
| 2572 | "C:\Users\admin\AppData\Local\Temp\Rar$EXb2120.1879\7ZipSetup.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXb2120.1879\7ZipSetup.exe | — | WinRAR.exe | |||||||||||
User: admin Integrity Level: MEDIUM Description: Powered by BetterInstaller Exit code: 3221226540 Version: 2.0.0.0 Modules
| |||||||||||||||
| 2688 | "C:\Users\admin\AppData\Local\Temp\biclient.exe" /url bi.bisrv.com /affid "awde7zip19538" /id "7zip" /name "7-Zip" /browser ie | C:\Users\admin\AppData\Local\Temp\biclient.exe | 7ZipSetup.exe | ||||||||||||
User: admin Company: Somoto Ltd. Integrity Level: HIGH Description: Better Installer Host Version: 2.0.0.0 Modules
| |||||||||||||||
Total events
13 689
Read events
13 621
Write events
59
Delete events
9
Modification events
| (PID) Process: | (2120) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (2120) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (2120) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\182\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (2120) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\phacker.zip | |||
| (PID) Process: | (2120) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\Win7-KB3191566-x86.zip | |||
| (PID) Process: | (2120) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\curl-8.5.0_1-win32-mingw.zip | |||
| (PID) Process: | (2120) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\Somoto.zip | |||
| (PID) Process: | (2120) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (2120) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (2120) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
Executable files
2
Suspicious files
20
Text files
50
Unknown types
5
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2120 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXb2120.1879\7ZipSetup.exe | executable | |
MD5:— | SHA256:— | |||
| 2064 | 7ZipSetup.exe | C:\Users\admin\AppData\Local\Temp\biclient.exe | executable | |
MD5:— | SHA256:— | |||
| 2064 | 7ZipSetup.exe | C:\Users\admin\AppData\Local\Temp\config.ini | text | |
MD5:— | SHA256:— | |||
| 2064 | 7ZipSetup.exe | C:\Users\admin\AppData\Local\Temp\nsuBF25.tmp | binary | |
MD5:— | SHA256:— | |||
| 2688 | biclient.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\57C8EDB95DF3F0AD4EE2DC2B8CFD4157 | binary | |
MD5:— | SHA256:— | |||
| 2688 | biclient.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\24BD96D5497F70B3F510A6B53CD43F3E_3A89246FB90C5EE6620004F1AE0EB0EA | der | |
MD5:— | SHA256:— | |||
| 2688 | biclient.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\24BD96D5497F70B3F510A6B53CD43F3E_3A89246FB90C5EE6620004F1AE0EB0EA | binary | |
MD5:— | SHA256:— | |||
| 2688 | biclient.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\CAF4703619713E3F18D8A9D5D88D6288_F2DAF19C1F776537105D08FC8D978464 | binary | |
MD5:— | SHA256:— | |||
| 2688 | biclient.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\CAF4703619713E3F18D8A9D5D88D6288_F2DAF19C1F776537105D08FC8D978464 | binary | |
MD5:— | SHA256:— | |||
| 2688 | biclient.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Cookies\XQGHMH0Q.txt | text | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
12
TCP/UDP connections
24
DNS requests
17
Threats
1
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2688 | biclient.exe | GET | 200 | 142.250.186.35:80 | http://ocsp.pki.goog/gsr1/MFEwTzBNMEswSTAJBgUrDgMCGgUABBS3V7W2nAf4FiMTjpDJKg6%2BMgGqMQQUYHtmGkUNl8qJUC99BM00qP%2F8%2FUsCEHe9DWzbNvka6iEPxPBY0w0%3D | unknown | — | — | unknown |
2688 | biclient.exe | GET | 302 | 54.161.222.85:80 | http://bi.bisrv.com/awde7zip19538/7zip/26993648d16697418d1128fbd70bf061?v=2.0&muid=05E28309B8D1983AA928469025E49813 | unknown | — | — | unknown |
2688 | biclient.exe | GET | 304 | 199.232.214.172:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?6cba3083cea0e54e | unknown | — | — | unknown |
2688 | biclient.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTBL0V27RVZ7LBduom%2FnYB45SPUEwQU5Z1ZMIJHWMys%2BghUNoZ7OrUETfACEAo3h2ReX7SMIk79G%2B0UDDw%3D | unknown | — | — | unknown |
2688 | biclient.exe | GET | 200 | 142.250.186.35:80 | http://ocsp.pki.goog/gts1c3/MFIwUDBOMEwwSjAJBgUrDgMCGgUABBTHLnmK3f9hNLO67UdCuLvGwCQHYwQUinR%2Fr4XN7pXNPZzQ4kYU83E1HScCEQDpjUVCgnd2whD%2FCYt5X90R | unknown | — | — | unknown |
2688 | biclient.exe | GET | 200 | 142.250.186.35:80 | http://ocsp.pki.goog/gtsr1/ME4wTDBKMEgwRjAJBgUrDgMCGgUABBQwkcLWD4LqGJ7bE7B1XZsEbmfwUAQU5K8rJnEaK0gnhS9SZizv8IkTcT4CDQIDvFNZazTHGPUBUGY%3D | unknown | — | — | unknown |
2688 | biclient.exe | GET | 200 | 142.250.186.35:80 | http://ocsp.pki.goog/gtsr1/ME4wTDBKMEgwRjAJBgUrDgMCGgUABBQwkcLWD4LqGJ7bE7B1XZsEbmfwUAQU5K8rJnEaK0gnhS9SZizv8IkTcT4CDQIDvFCjJ1PwkYAi7fE%3D | unknown | — | — | unknown |
2688 | biclient.exe | GET | 200 | 142.250.186.35:80 | http://ocsp.pki.goog/gts1c3/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTHLnmK3f9hNLO67UdCuLvGwCQHYwQUinR%2Fr4XN7pXNPZzQ4kYU83E1HScCEHbOEmPcnJ2%2BEsGo2UIm5Ag%3D | unknown | — | — | unknown |
2688 | biclient.exe | GET | 200 | 142.250.186.35:80 | http://ocsp.pki.goog/gts1c3/MFIwUDBOMEwwSjAJBgUrDgMCGgUABBTHLnmK3f9hNLO67UdCuLvGwCQHYwQUinR%2Fr4XN7pXNPZzQ4kYU83E1HScCEQD%2BHROSYYrnDBBlkCpV0EGt | unknown | — | — | unknown |
2688 | biclient.exe | GET | 200 | 142.250.186.35:80 | http://ocsp.pki.goog/gts1c3/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTHLnmK3f9hNLO67UdCuLvGwCQHYwQUinR%2Fr4XN7pXNPZzQ4kYU83E1HScCEC1cuulVn3WlCZhESGDJeH4%3D | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 224.0.0.252:5355 | — | — | — | unknown |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
2688 | biclient.exe | 54.161.222.85:80 | bi.bisrv.com | AMAZON-AES | US | unknown |
2688 | biclient.exe | 104.26.7.37:443 | www.hugedomains.com | CLOUDFLARENET | US | shared |
2688 | biclient.exe | 199.232.214.172:80 | ctldl.windowsupdate.com | FASTLY | US | unknown |
2688 | biclient.exe | 142.250.186.35:80 | ocsp.pki.goog | GOOGLE | US | whitelisted |
2688 | biclient.exe | 104.22.58.91:443 | cdn-cookieyes.com | CLOUDFLARENET | — | unknown |
2688 | biclient.exe | 142.250.185.72:443 | www.googletagmanager.com | GOOGLE | US | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
bi.bisrv.com |
| malicious |
www.hugedomains.com |
| whitelisted |
ctldl.windowsupdate.com |
| whitelisted |
ocsp.pki.goog |
| whitelisted |
cdn.jsdelivr.net |
| whitelisted |
static.hugedomains.com |
| unknown |
cdn-cookieyes.com |
| whitelisted |
fonts.googleapis.com |
| whitelisted |
www.googletagmanager.com |
| whitelisted |
use.typekit.net |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2688 | biclient.exe | Not Suspicious Traffic | INFO [ANY.RUN] A free CDN for open source projects (jsdelivr .net) |