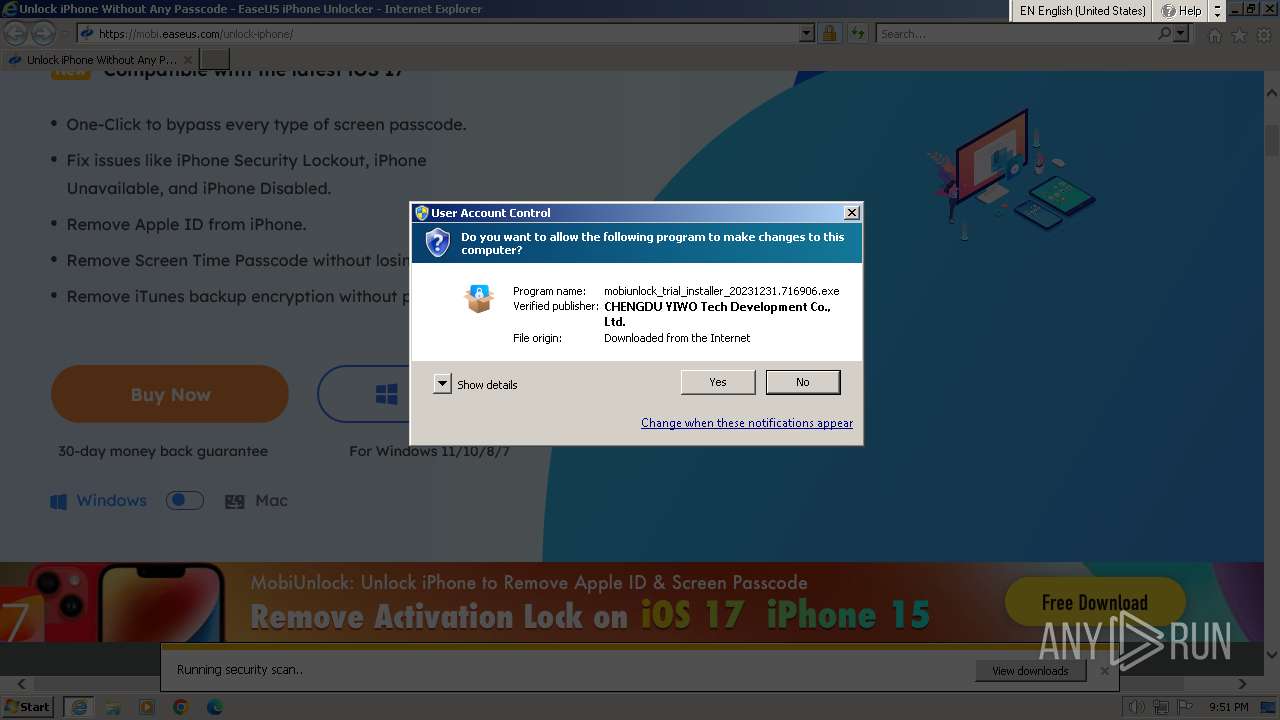
| URL: | https://mobi.easeus.com/unlock-iphone/ |
| Full analysis: | https://app.any.run/tasks/d54ba735-4eb6-4405-b40d-01153f847ede |
| Verdict: | Malicious activity |
| Analysis date: | December 31, 2023, 21:50:55 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MD5: | B3CBD0C2CDC8285995F2A8E205CC36D4 |
| SHA1: | C2C29FF5D3FB874E252E7009DCDA2AFD6B682C6C |
| SHA256: | 8EA338C8562D6E310F786C6A13BFAD21F7749BE4470795AEDE8D1B8214091E2A |
| SSDEEP: | 3:N8lgHmo7Qvn:27oEn |
MALICIOUS
Creates a writable file in the system directory
- drvinst.exe (PID: 1380)
- drvinst.exe (PID: 2480)
SUSPICIOUS
Reads the Internet Settings
- AliyunWrapExe.Exe (PID: 2672)
- EDownloader.exe (PID: 2828)
- AliyunWrapExe.Exe (PID: 3164)
Reads Microsoft Outlook installation path
- EDownloader.exe (PID: 2828)
Reads Internet Explorer settings
- EDownloader.exe (PID: 2828)
Reads the Windows owner or organization settings
- unlock_trial_easeus.tmp (PID: 3132)
Drops a system driver (possible attempt to evade defenses)
- unlock_trial_easeus.tmp (PID: 3132)
- DPInst32.exe (PID: 1736)
- drvinst.exe (PID: 1380)
Uses DRIVERQUERY.EXE to obtain a list of installed device drivers
- cmd.exe (PID: 3792)
- cmd.exe (PID: 2192)
Using 'findstr.exe' to search for text patterns in files and output
- cmd.exe (PID: 3792)
- cmd.exe (PID: 2192)
Starts application with an unusual extension
- cmd.exe (PID: 1624)
Searches for installed software
- repairEnvir.exe (PID: 3868)
Creates files in the driver directory
- drvinst.exe (PID: 1380)
- drvinst.exe (PID: 2480)
Checks Windows Trust Settings
- drvinst.exe (PID: 1380)
- drvinst.exe (PID: 2480)
Starts CMD.EXE for commands execution
- repairEnvir.exe (PID: 3868)
INFO
Application launched itself
- iexplore.exe (PID: 2044)
The process uses the downloaded file
- iexplore.exe (PID: 2044)
Drops the executable file immediately after the start
- iexplore.exe (PID: 296)
- iexplore.exe (PID: 2044)
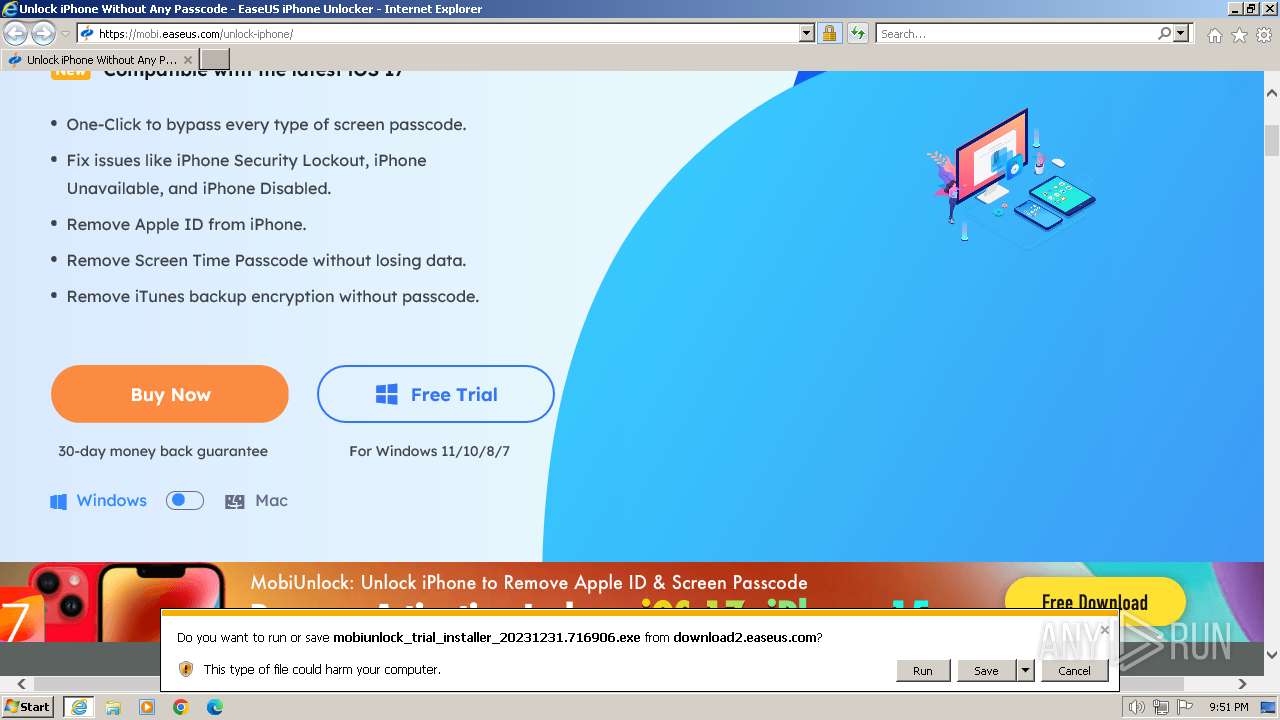
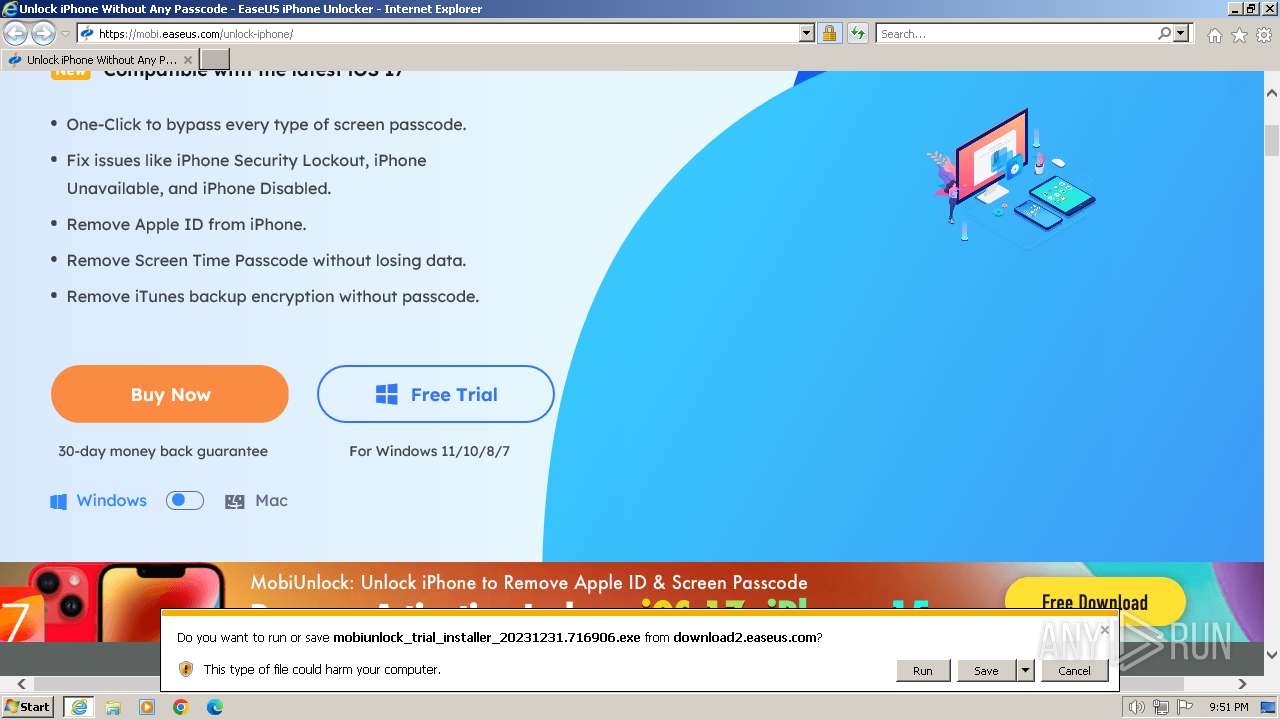
- mobiunlock_trial_installer_20231231.716906.exe (PID: 2388)
- unlock_trial_easeus.exe (PID: 3100)
- DPInst32.exe (PID: 1736)
- drvinst.exe (PID: 1380)
- unlock_trial_easeus.tmp (PID: 3132)
Checks supported languages
- mobiunlock_trial_installer_20231231.716906.exe (PID: 2388)
- EDownloader.exe (PID: 2828)
- InfoForSetup.exe (PID: 2804)
- AliyunWrapExe.Exe (PID: 2672)
- AliyunWrapExe.Exe (PID: 2060)
- InfoForSetup.exe (PID: 2316)
- InfoForSetup.exe (PID: 2800)
- InfoForSetup.exe (PID: 240)
- AliyunWrapExe.Exe (PID: 2788)
- InfoForSetup.exe (PID: 2548)
- InfoForSetup.exe (PID: 2500)
- InfoForSetup.exe (PID: 2528)
- InfoForSetup.exe (PID: 2652)
- InfoForSetup.exe (PID: 3112)
- InfoForSetup.exe (PID: 3108)
- unlock_trial_easeus.tmp (PID: 3132)
- unlock_trial_easeus.exe (PID: 3100)
- InfoForSetup.exe (PID: 3196)
- InfoForSetup.exe (PID: 3268)
- EUinApp.exe (PID: 3968)
- EUinApp.exe (PID: 4084)
- repairEnvir.exe (PID: 3868)
- DPInst32.exe (PID: 1736)
- chcp.com (PID: 2128)
- drvinst.exe (PID: 1380)
- drvinst.exe (PID: 2480)
- aria2c.exe (PID: 2336)
- InfoForSetup.exe (PID: 2956)
- AliyunWrapExe.Exe (PID: 3164)
Reads the computer name
- mobiunlock_trial_installer_20231231.716906.exe (PID: 2388)
- EDownloader.exe (PID: 2828)
- AliyunWrapExe.Exe (PID: 2672)
- unlock_trial_easeus.tmp (PID: 3132)
- DPInst32.exe (PID: 1736)
- drvinst.exe (PID: 2480)
- drvinst.exe (PID: 1380)
- aria2c.exe (PID: 2336)
- AliyunWrapExe.Exe (PID: 3164)
Create files in a temporary directory
- mobiunlock_trial_installer_20231231.716906.exe (PID: 2388)
- EDownloader.exe (PID: 2828)
- InfoForSetup.exe (PID: 2800)
- AliyunWrapExe.Exe (PID: 2672)
- unlock_trial_easeus.exe (PID: 3100)
- unlock_trial_easeus.tmp (PID: 3132)
- AliyunWrapExe.Exe (PID: 3164)
- DPInst32.exe (PID: 1736)
Checks proxy server information
- AliyunWrapExe.Exe (PID: 2672)
- EDownloader.exe (PID: 2828)
- AliyunWrapExe.Exe (PID: 3164)
Reads the machine GUID from the registry
- AliyunWrapExe.Exe (PID: 2672)
- EDownloader.exe (PID: 2828)
- AliyunWrapExe.Exe (PID: 3164)
- DPInst32.exe (PID: 1736)
- drvinst.exe (PID: 1380)
- drvinst.exe (PID: 2480)
- aria2c.exe (PID: 2336)
Creates files or folders in the user directory
- AliyunWrapExe.Exe (PID: 2672)
- EDownloader.exe (PID: 2828)
- AliyunWrapExe.Exe (PID: 3164)
Process drops legitimate windows executable
- unlock_trial_easeus.tmp (PID: 3132)
- DPInst32.exe (PID: 1736)
Creates files in the program directory
- unlock_trial_easeus.tmp (PID: 3132)
Drops 7-zip archiver for unpacking
- unlock_trial_easeus.tmp (PID: 3132)
The process drops C-runtime libraries
- unlock_trial_easeus.tmp (PID: 3132)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
89
Monitored processes
40
Malicious processes
5
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 240 | /SendInfo Window "DownloadInstall_Page" Activity "Info_Finish" Attribute "{\"Country\":\"United States\",\"Language\":\"English\",\"OS\":\"Microsoft Windows 7\",\"Releasetime\":\"2023-02-17_10_28_12\",\"Testid\":\"\",\"Timezone\":\"GMT-00:00\",\"Version\":\"trial\",\"Version_Num\":\"3.1.17\"}" | C:\Users\admin\AppData\Local\Temp\downloader_easeus\1.0.0\9trial\aliyun\InfoForSetup.exe | — | EDownloader.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 296 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:2044 CREDAT:267521 /prefetch:2 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 1380 | DrvInst.exe "4" "8" "C:\Users\admin\AppData\Local\Temp\{686816ef-058a-6a98-3e80-96607352c808}\usbaapl.inf" "0" "6812481e3" "00000558" "WinSta0\Default" "000004B4" "208" "c:\program files\easeus\easeus mobiunlock\bin\appledriver" | C:\Windows\System32\drvinst.exe | — | svchost.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Driver Installation Module Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1624 | cmd /C "chcp 437" & pnputil /enum-devices /connected | C:\Windows\System32\cmd.exe | — | repairEnvir.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 1 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 1736 | "C:\Program Files\EaseUS\EaseUS MobiUnlock\bin\appleDriver\DPInst32" /S /SW /A /PATH "C:\Program Files\EaseUS\EaseUS MobiUnlock\bin\appleDriver" | C:\Program Files\EaseUS\EaseUS MobiUnlock\bin\appleDriver\DPInst32.exe | — | repairEnvir.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Driver Package Installer Exit code: 256 Version: 2.1 Modules
| |||||||||||||||
| 1804 | pnputil /enum-devices /connected | C:\Windows\System32\PnPutil.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft PnP Utility - Tool to add, delete and enumerate driver packages. Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2044 | "C:\Program Files\Internet Explorer\iexplore.exe" "https://mobi.easeus.com/unlock-iphone/" | C:\Program Files\Internet Explorer\iexplore.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 1 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 2060 | C:\Users\admin\AppData\Local\Temp\downloader_easeus\1.0.0\9trial\aliyun\AliyunWrapExe.Exe | C:\Users\admin\AppData\Local\Temp\downloader_easeus\1.0.0\9trial\aliyun\AliyunWrapExe.Exe | — | InfoForSetup.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 2128 | chcp 437 | C:\Windows\System32\chcp.com | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Change CodePage Utility Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2192 | cmd.exe /C "driverquery | findstr /I apple" | C:\Windows\System32\cmd.exe | — | repairEnvir.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 1 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
Total events
30 554
Read events
30 327
Write events
224
Delete events
3
Modification events
| (PID) Process: | (2044) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPDaysSinceLastAutoMigration |
Value: 0 | |||
| (PID) Process: | (2044) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchHighDateTime |
Value: 30847387 | |||
| (PID) Process: | (2044) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateHighDateTime |
Value: 30847437 | |||
| (PID) Process: | (2044) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (2044) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (2044) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
| (PID) Process: | (2044) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (2044) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (2044) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (2044) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
Executable files
555
Suspicious files
463
Text files
1 322
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 296 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\57C8EDB95DF3F0AD4EE2DC2B8CFD4157 | compressed | |
MD5:1BFE591A4FE3D91B03CDF26EAACD8F89 | SHA256:9CF94355051BF0F4A45724CA20D1CC02F76371B963AB7D1E38BD8997737B13D8 | |||
| 296 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\6BADA8974A10C4BD62CC921D13E43B18_28DEA62A0AE77228DD387E155AD0BA27 | binary | |
MD5:5C017FE8B672CD5AF6D8BD60C8ECF6A5 | SHA256:D27A1D72B6E55137040D6C37C4AC7F37DBE9B8DC31F44088BD3EC3C6363C400B | |||
| 296 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\DY534W2X\mobiunlock[1].svg | image | |
MD5:4DA3C6DE83998A3E0C401BAE90E36EC0 | SHA256:909A331641A428CDC88ECF8900275C0FE01E189A7CD7B49EC274CA0F5B52C989 | |||
| 296 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\MFAQUS6V\jquery[1].js | text | |
MD5:32865F8B0518670A04C81659CD3871DB | SHA256:1492D0BB67B07F042F35595A70369DB5BD89E02CCA12DE3140B2519A381ABA69 | |||
| 296 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\MFAQUS6V\globle_pruduct[1].css | text | |
MD5:EBE32A4CD27E57CD397579153A4A61A3 | SHA256:FEFF97D71CA6F97AAAF0CA3431DA78CC65BF42E298C5D5B08F8451F90B805410 | |||
| 296 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\YTOWV792\mobiUnlock-for-android-logo[1].svg | image | |
MD5:C48221FCCC636FB4EBFBC6D2F3151754 | SHA256:3E70FD0556F9605C0CE9570E33B976626EB8E2725D0BB3366A77B4DBD9A71208 | |||
| 296 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\5IWPIAR9\ringroneeditor[1].svg | image | |
MD5:1D90E0A0A650E731001E950996395D3E | SHA256:A4BBE9050620A478D0ED7FB36EAA39BE2105F58EE85376999A73BFFDA8D0FF59 | |||
| 296 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\YTOWV792\ios-system-repair[1].svg | image | |
MD5:117CFCCE11BE121181D7A2351FCEAB02 | SHA256:453A46461172EC9FAB2AE10E9C3DEB4BEE44C793B89E791F8F83E533A414648B | |||
| 296 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\DY534W2X\mobimover[1].svg | image | |
MD5:5532265A7F06E8F2DB0308B23B707EAC | SHA256:8C5823E4E5811AD08B60BA6F2B947C5F0786560819351725FC18BCA06501599D | |||
| 296 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\5IWPIAR9\mobianygo[1].svg | image | |
MD5:9156CCA1060C3232B0CEB1F205D1E711 | SHA256:EE2197F8248343B4DF7560BAE9BA9004DCF060567DB3FBA68666492EEE5C9A37 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
45
TCP/UDP connections
99
DNS requests
46
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
296 | iexplore.exe | GET | 200 | 93.184.221.240:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?608cb4ab6d3f68d3 | unknown | compressed | 4.66 Kb | unknown |
296 | iexplore.exe | GET | 200 | 93.184.221.240:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?f6bf34dbb61e71d7 | unknown | compressed | 4.66 Kb | unknown |
296 | iexplore.exe | GET | 200 | 142.250.181.227:80 | http://ocsp.pki.goog/gsr1/MFEwTzBNMEswSTAJBgUrDgMCGgUABBS3V7W2nAf4FiMTjpDJKg6%2BMgGqMQQUYHtmGkUNl8qJUC99BM00qP%2F8%2FUsCEHe9DWzbNvka6iEPxPBY0w0%3D | unknown | binary | 1.41 Kb | unknown |
296 | iexplore.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTBL0V27RVZ7LBduom%2FnYB45SPUEwQU5Z1ZMIJHWMys%2BghUNoZ7OrUETfACEAo3h2ReX7SMIk79G%2B0UDDw%3D | unknown | binary | 1.47 Kb | unknown |
296 | iexplore.exe | GET | 200 | 142.250.181.227:80 | http://ocsp.pki.goog/gtsr1/ME4wTDBKMEgwRjAJBgUrDgMCGgUABBQwkcLWD4LqGJ7bE7B1XZsEbmfwUAQU5K8rJnEaK0gnhS9SZizv8IkTcT4CDQIDvFNZazTHGPUBUGY%3D | unknown | binary | 724 b | unknown |
296 | iexplore.exe | GET | 200 | 142.250.181.227:80 | http://ocsp.pki.goog/gts1c3/MFIwUDBOMEwwSjAJBgUrDgMCGgUABBTHLnmK3f9hNLO67UdCuLvGwCQHYwQUinR%2Fr4XN7pXNPZzQ4kYU83E1HScCEQCZXmpIP%2Bo%2BHhJmodADfw%2Fc | unknown | binary | 472 b | unknown |
296 | iexplore.exe | GET | 200 | 172.64.149.23:80 | http://ocsp.comodoca.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBRTtU9uFqgVGHhJwXZyWCNXmVR5ngQUoBEKIz6W8Qfs4q8p74Klf9AwpLQCEDlyRDr5IrdR19NsEN0xNZU%3D | unknown | binary | 1.42 Kb | unknown |
296 | iexplore.exe | GET | 200 | 104.18.38.233:80 | http://ocsp.usertrust.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTNMNJMNDqCqx8FcBWK16EHdimS6QQUU3m%2FWqorSs9UgOHYm8Cd8rIDZssCEBN9U5yqfDGppDNwGWiEeo0%3D | unknown | binary | 2.18 Kb | unknown |
296 | iexplore.exe | GET | 200 | 142.250.181.227:80 | http://ocsp.pki.goog/gtsr1/ME4wTDBKMEgwRjAJBgUrDgMCGgUABBQwkcLWD4LqGJ7bE7B1XZsEbmfwUAQU5K8rJnEaK0gnhS9SZizv8IkTcT4CDQIDvFCjJ1PwkYAi7fE%3D | unknown | binary | 724 b | unknown |
296 | iexplore.exe | GET | 200 | 172.64.149.23:80 | http://ocsp.sectigo.com/MFIwUDBOMEwwSjAJBgUrDgMCGgUABBQh80WaEMqmyEvaHjlisSfVM4p8SAQUF9nWJSdn%2BTHCSUPZMDZEjGypT%2BsCEQCUYyh29WemWFA8QAcXZOSB | unknown | binary | 472 b | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
296 | iexplore.exe | 104.18.21.87:443 | mobi.easeus.com | CLOUDFLARENET | — | unknown |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
296 | iexplore.exe | 93.184.221.240:80 | ctldl.windowsupdate.com | EDGECAST | GB | whitelisted |
296 | iexplore.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
296 | iexplore.exe | 216.58.206.46:443 | www.googleoptimize.com | GOOGLE | US | whitelisted |
296 | iexplore.exe | 142.250.181.227:80 | ocsp.pki.goog | GOOGLE | US | whitelisted |
296 | iexplore.exe | 91.212.12.148:443 | secure.trust-provider.com | Sectigo Limited | GB | unknown |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
296 | iexplore.exe | 172.64.149.23:80 | ocsp.comodoca.com | CLOUDFLARENET | US | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
mobi.easeus.com |
| unknown |
ctldl.windowsupdate.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
www.googleoptimize.com |
| whitelisted |
ocsp.pki.goog |
| whitelisted |
secure.trust-provider.com |
| unknown |
www.easeus.com |
| whitelisted |
ocsp.comodoca.com |
| whitelisted |
ocsp.usertrust.com |
| whitelisted |
ocsp.sectigo.com |
| whitelisted |