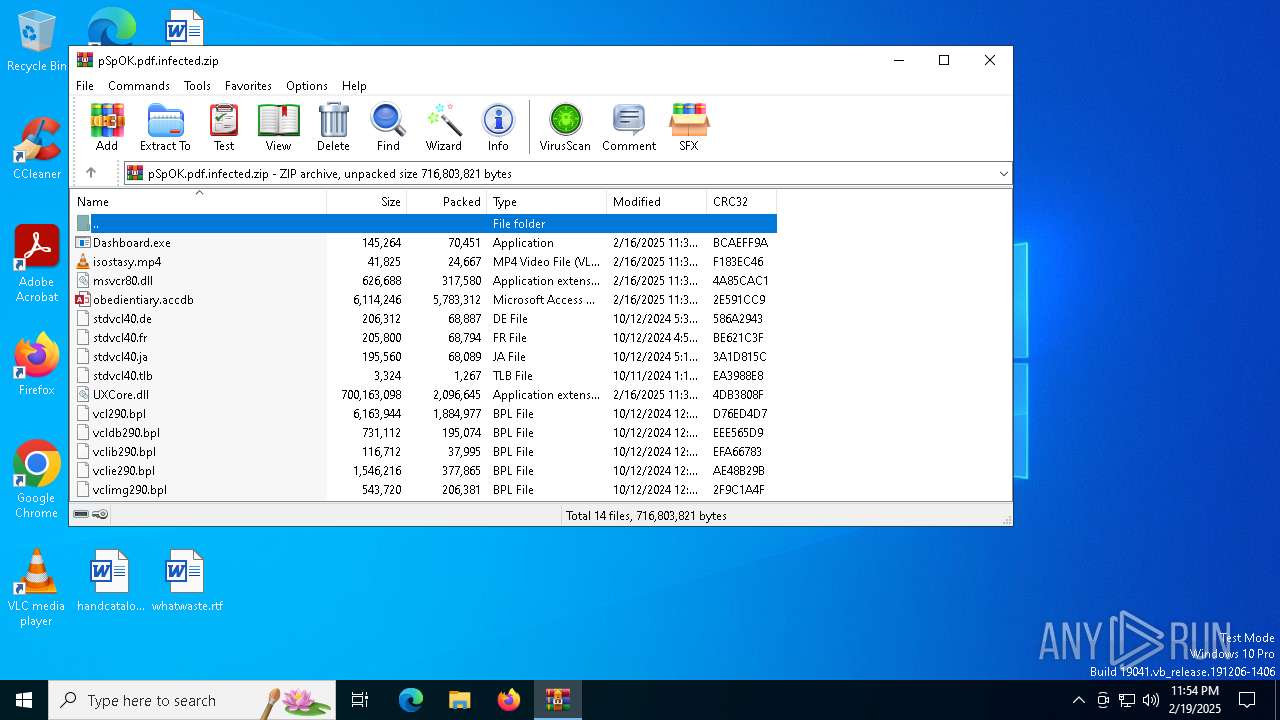
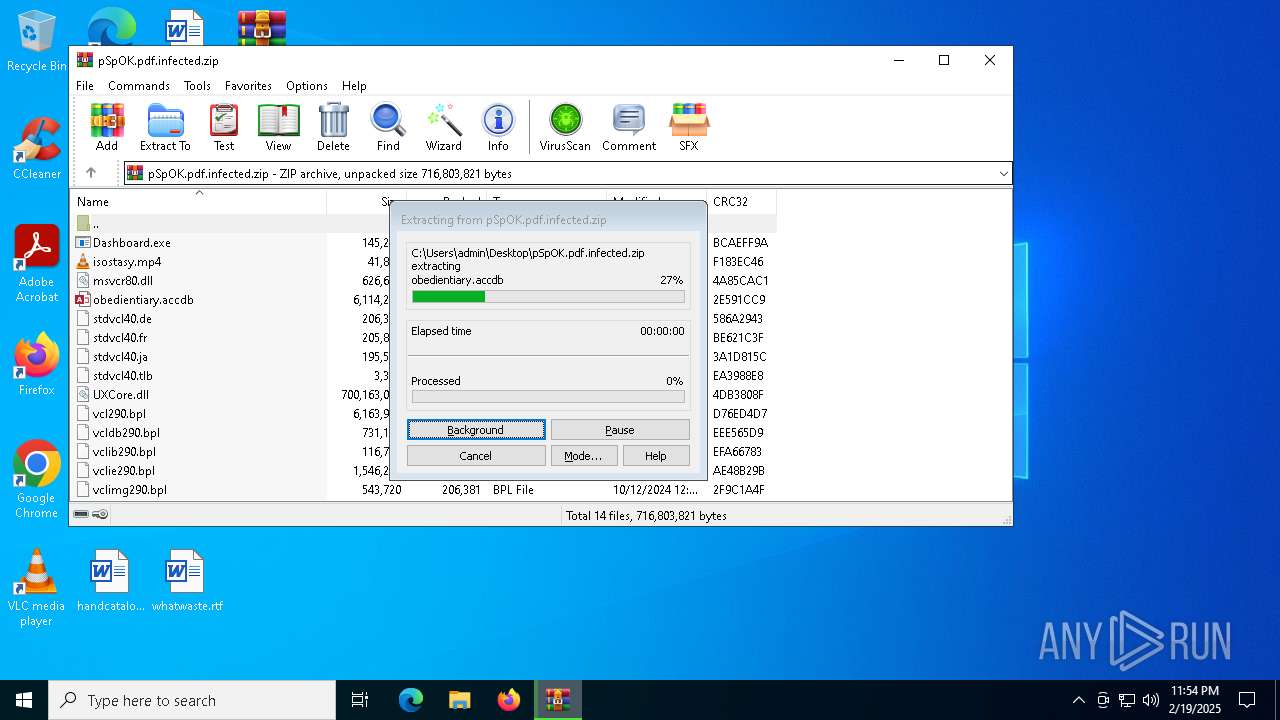
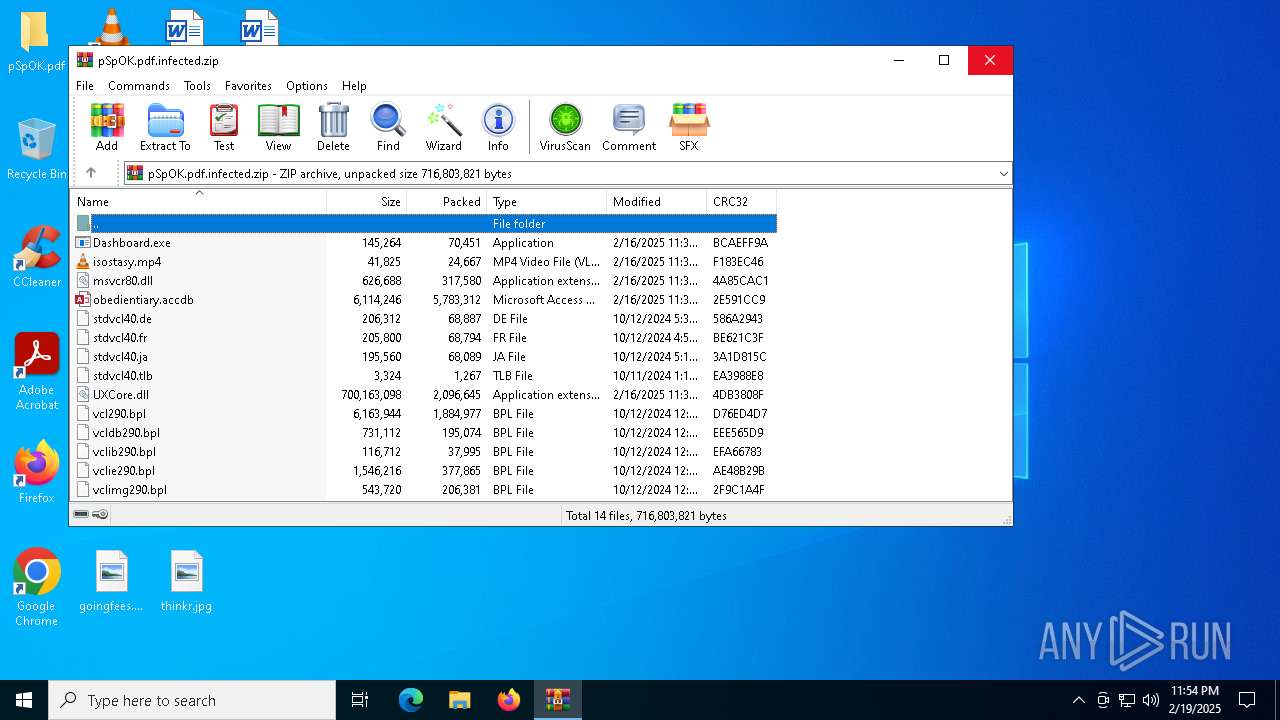
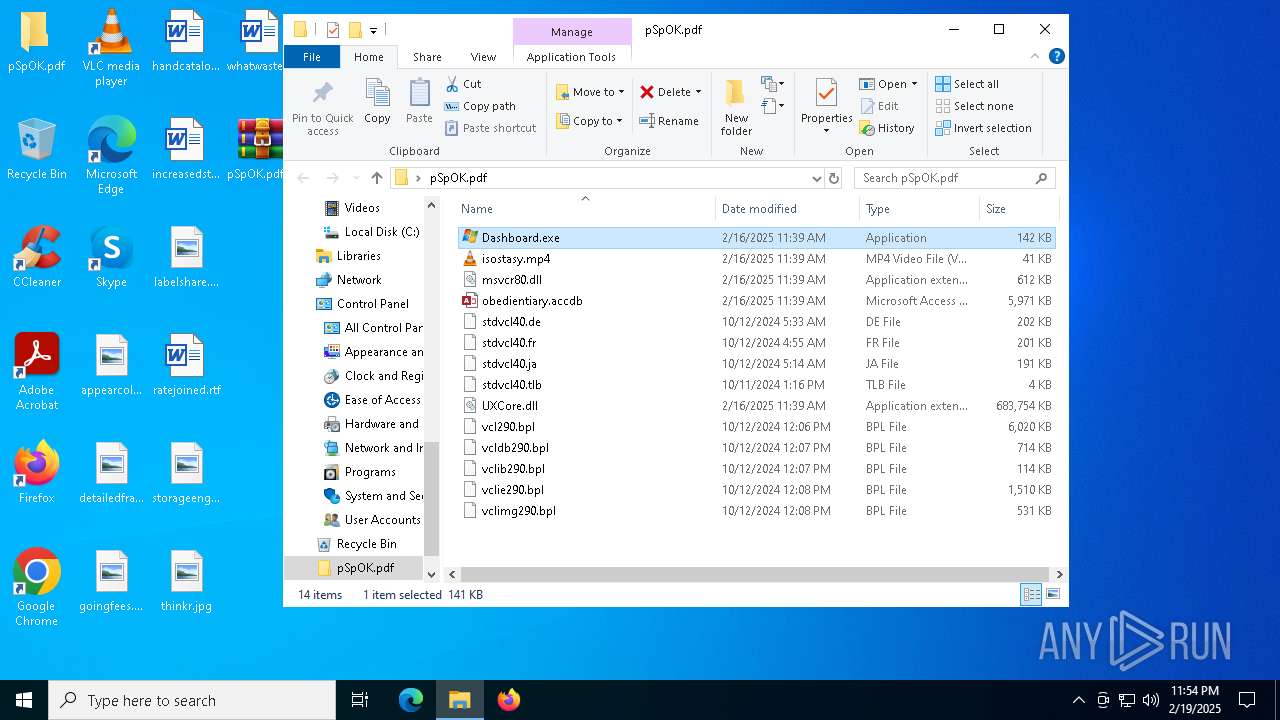
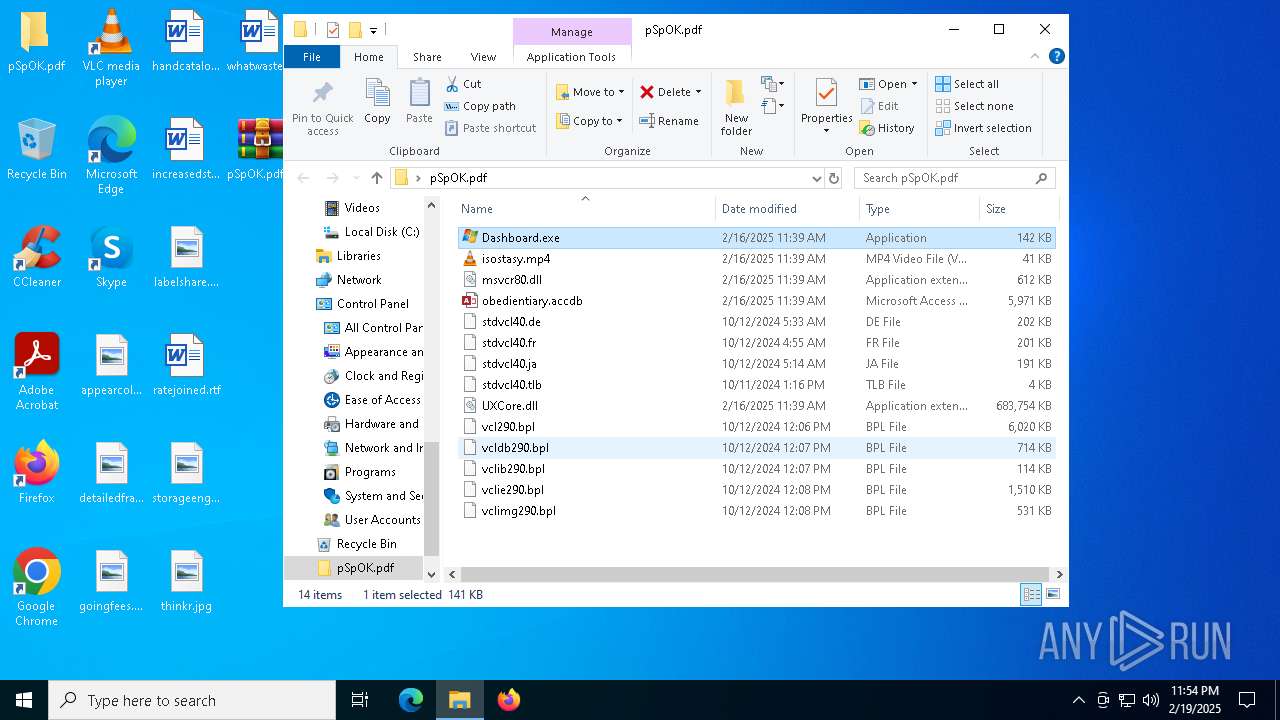
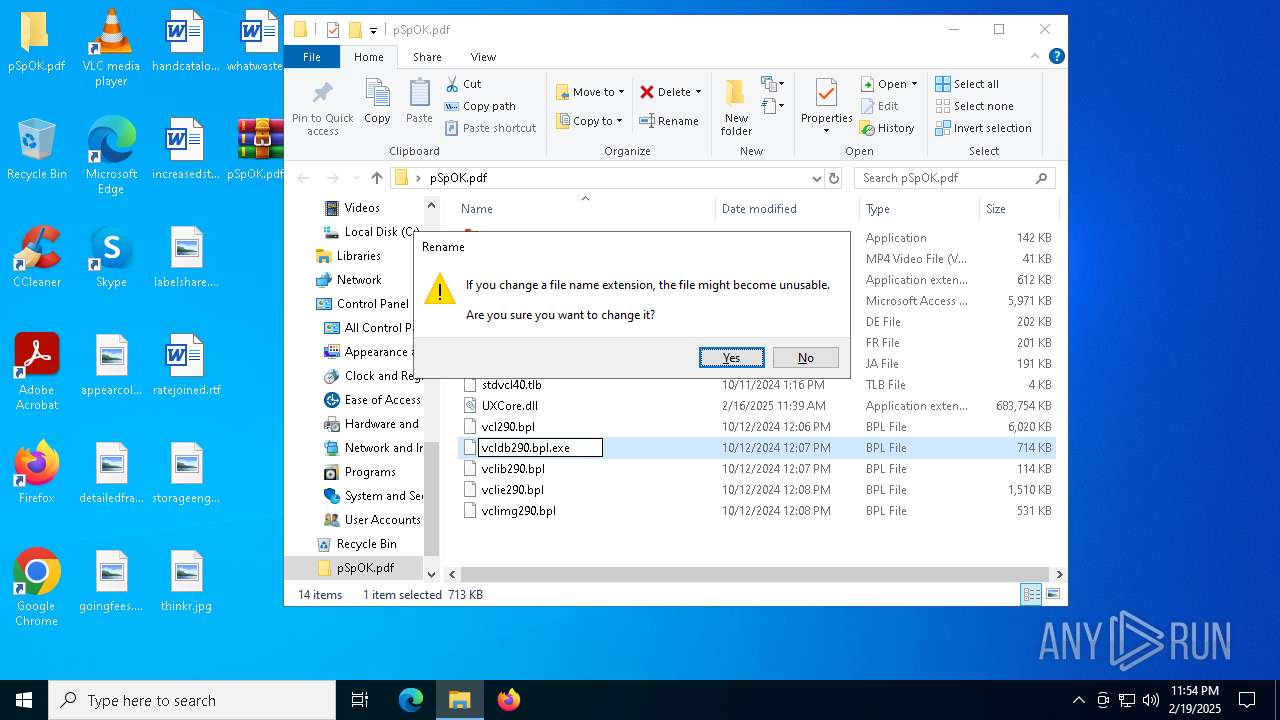
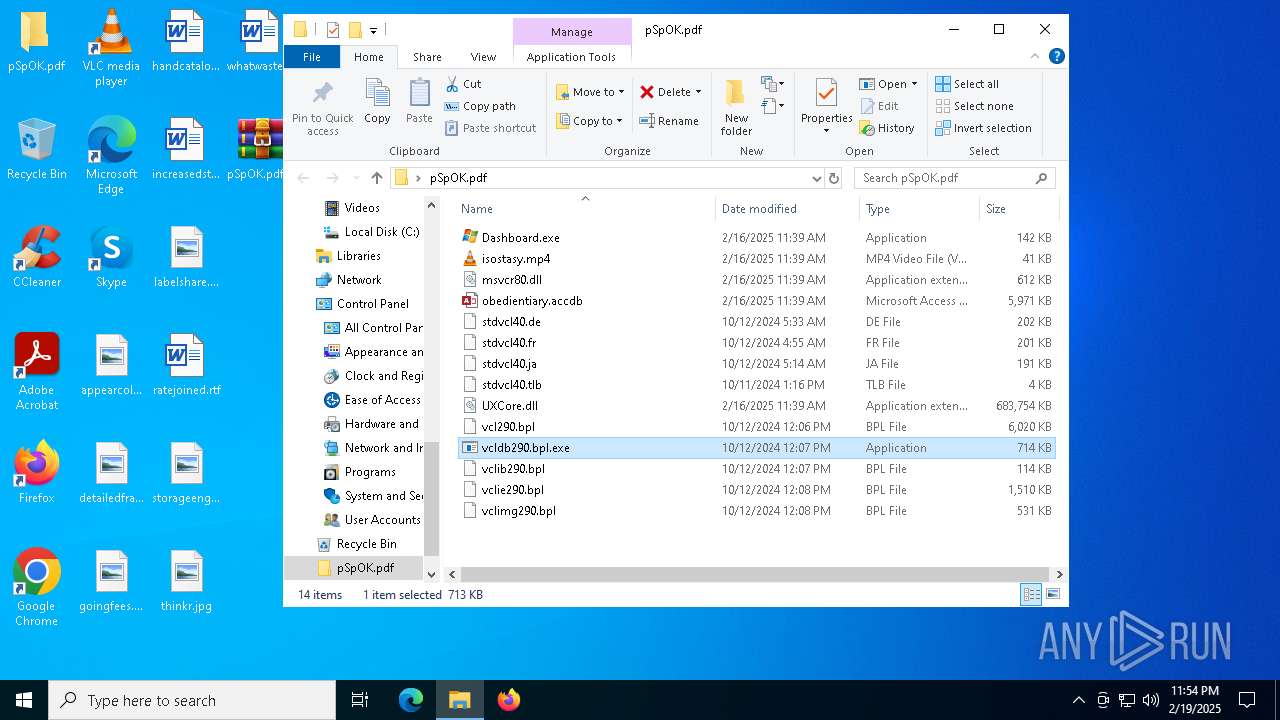
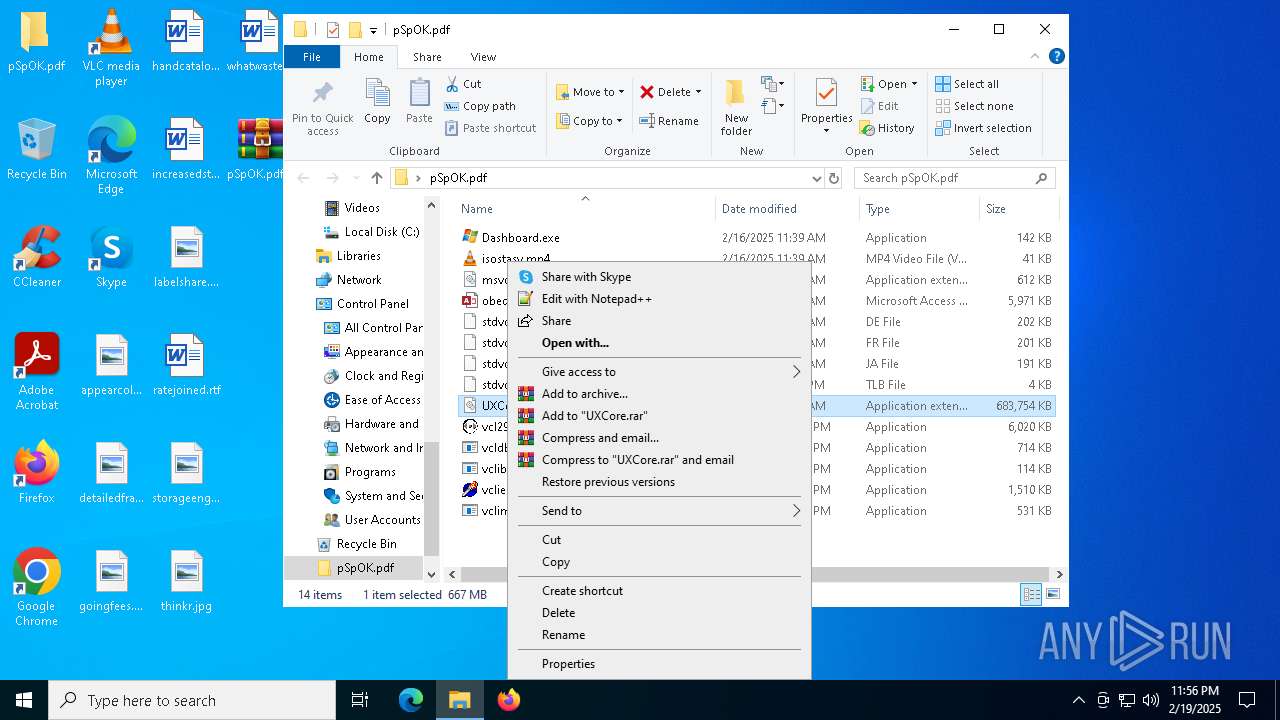
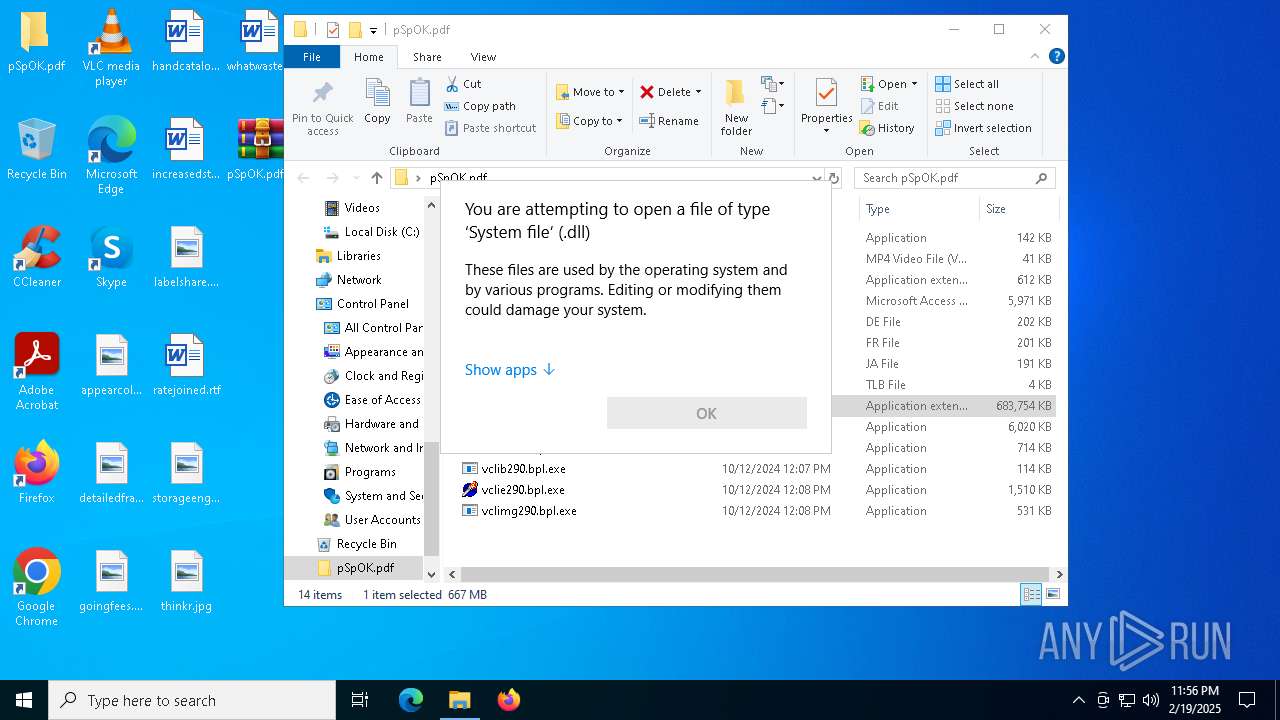
| File name: | pSpOK.pdf.infected |
| Full analysis: | https://app.any.run/tasks/b215cae4-9737-42f9-af62-e1d619e5dab0 |
| Verdict: | Malicious activity |
| Analysis date: | February 19, 2025, 23:53:53 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract, compression method=deflate |
| MD5: | 32EECFDCB03A57FE1DB9B3FF9DC1065F |
| SHA1: | DD3864A93DED8E8018EAED8F8618DF875E8F81A4 |
| SHA256: | 8EA11EC598EEE36D888BFB95720CF9B03581CAD5608387C90BC8C5E84F6A0D63 |
| SSDEEP: | 98304:D0pkDIv0mZptLExge8iroXu7qJgx+guN5mMqSoMuwPhY1zM/FrKGNDpkJj5KH+ei:cOnUDnVEbGEXK48lti |
MALICIOUS
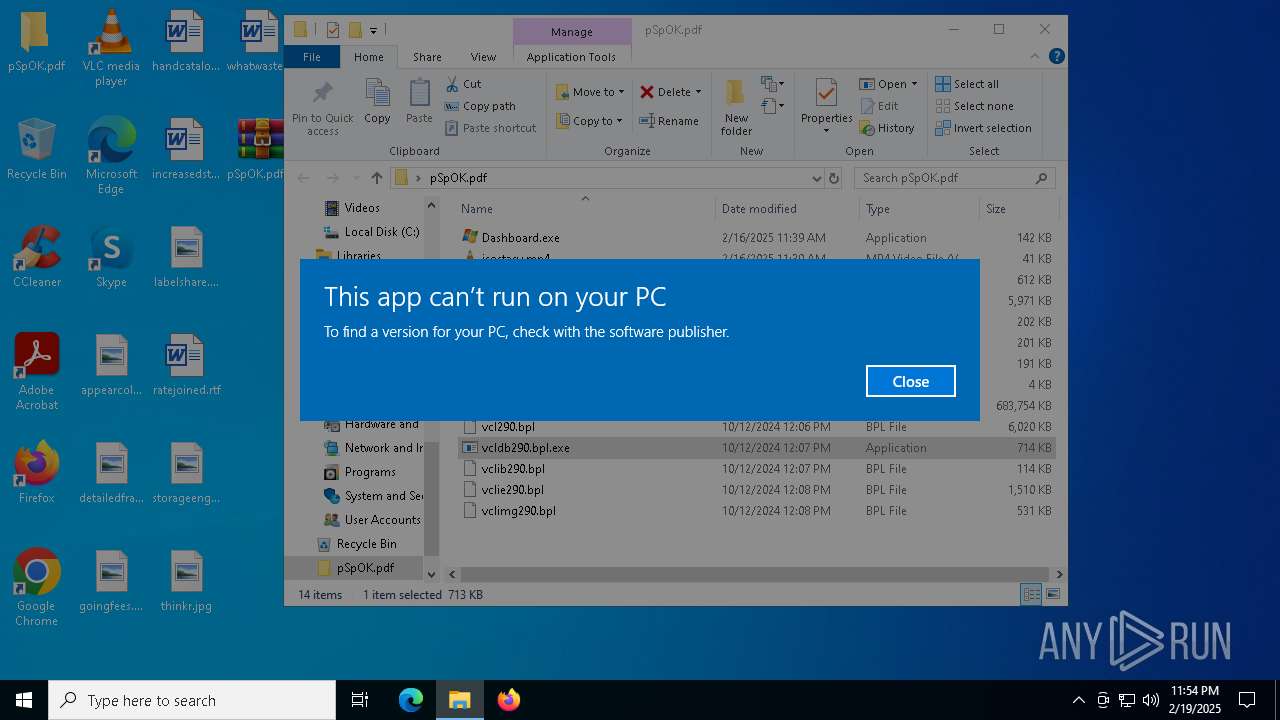
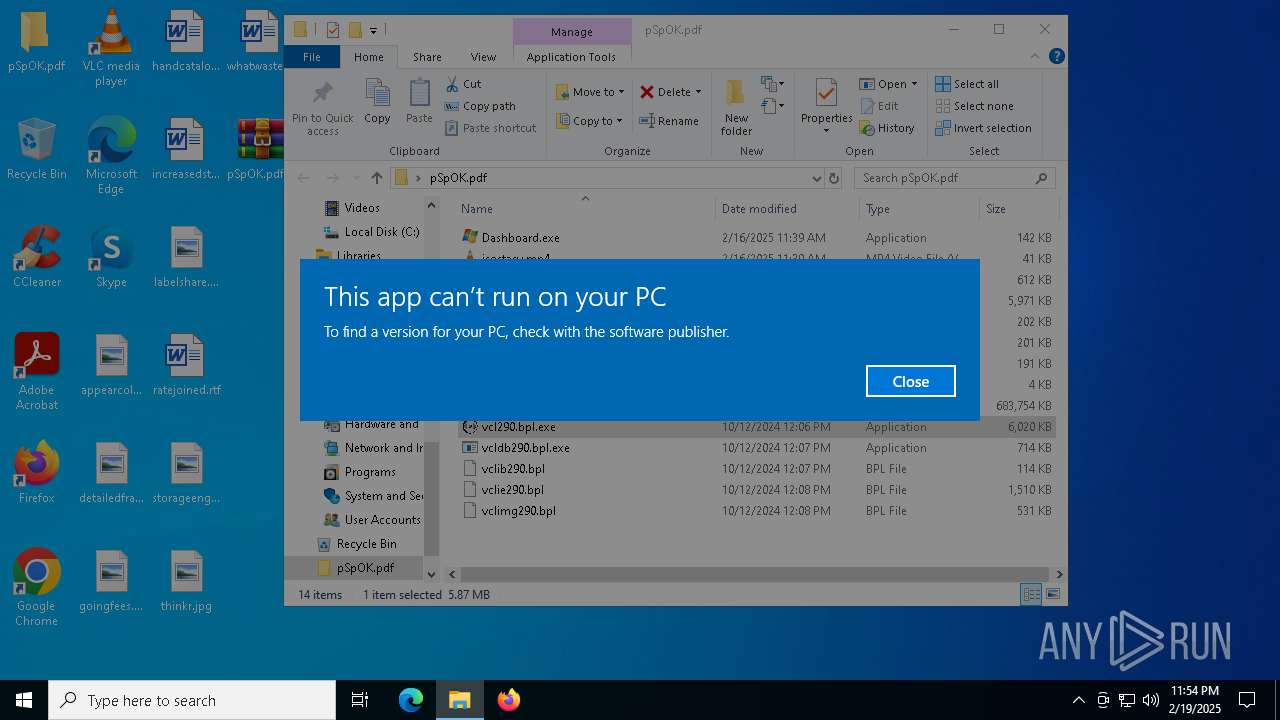
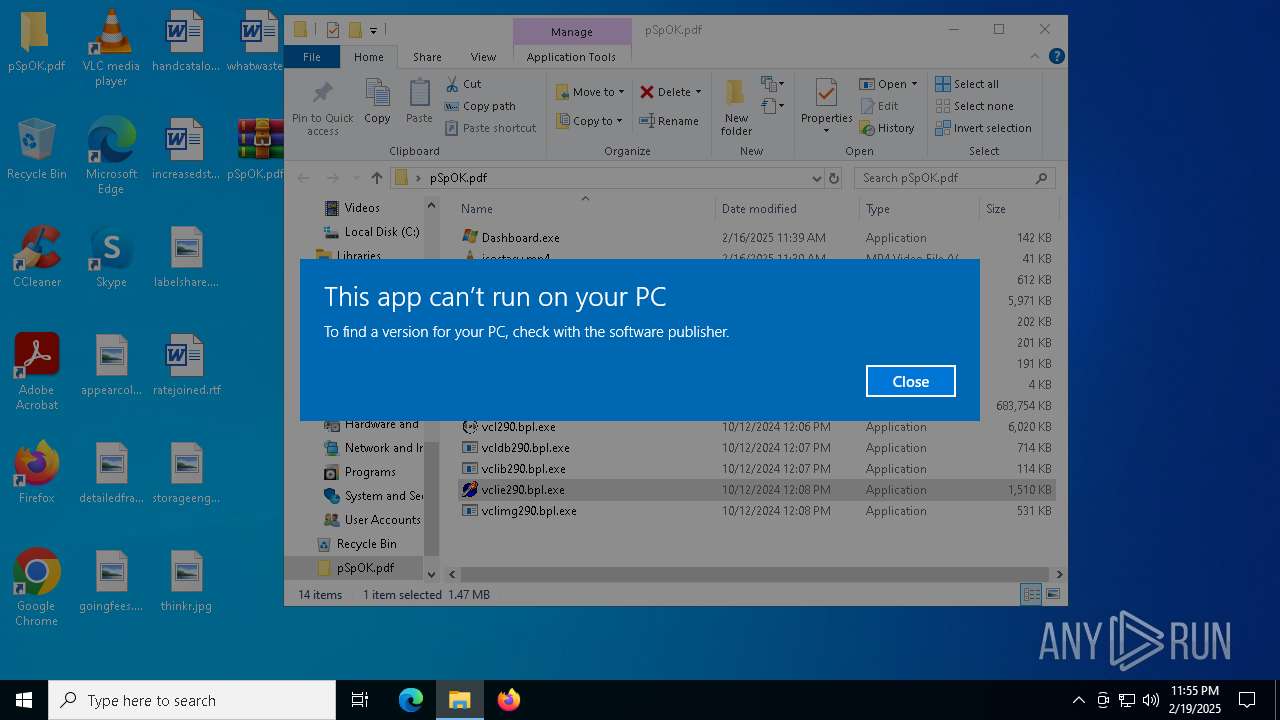
Executing a file with an untrusted certificate
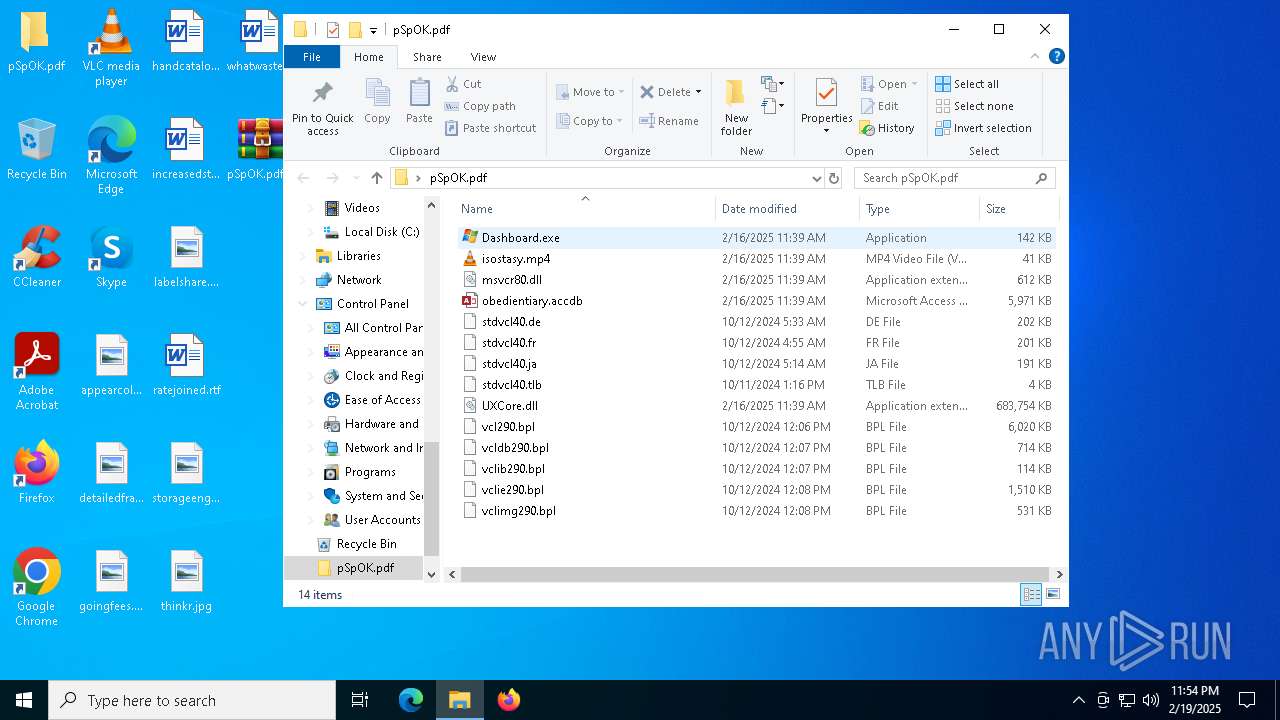
- Dashboard.exe (PID: 5388)
- Dashboard.exe (PID: 188)
- Dashboard.exe (PID: 3848)
Known privilege escalation attack
- dllhost.exe (PID: 2680)
SUSPICIOUS
Starts a Microsoft application from unusual location
- Dashboard.exe (PID: 5388)
Process drops legitimate windows executable
- WinRAR.exe (PID: 3208)
- Dashboard.exe (PID: 5388)
Executable content was dropped or overwritten
- Dashboard.exe (PID: 5388)
Starts itself from another location
- Dashboard.exe (PID: 5388)
The process drops C-runtime libraries
- Dashboard.exe (PID: 5388)
Starts CMD.EXE for commands execution
- Dashboard.exe (PID: 3848)
- Dashboard.exe (PID: 188)
Connects to unusual port
- explorer.exe (PID: 3884)
INFO
The sample compiled with english language support
- WinRAR.exe (PID: 3208)
- Dashboard.exe (PID: 5388)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 3208)
Creates files or folders in the user directory
- Dashboard.exe (PID: 5388)
Checks supported languages
- Dashboard.exe (PID: 5388)
- Dashboard.exe (PID: 3848)
- Dashboard.exe (PID: 188)
- vlc.exe (PID: 2736)
Reads the computer name
- Dashboard.exe (PID: 5388)
- Dashboard.exe (PID: 188)
- Dashboard.exe (PID: 3848)
- vlc.exe (PID: 2736)
Manual execution by a user
- Dashboard.exe (PID: 5388)
- vlc.exe (PID: 2736)
Reads security settings of Internet Explorer
- dllhost.exe (PID: 2680)
Reads the software policy settings
- explorer.exe (PID: 3884)
Create files in a temporary directory
- Dashboard.exe (PID: 3848)
- Dashboard.exe (PID: 188)
Detects GO elliptic curve encryption (YARA)
- explorer.exe (PID: 3884)
Application based on Golang
- explorer.exe (PID: 3884)
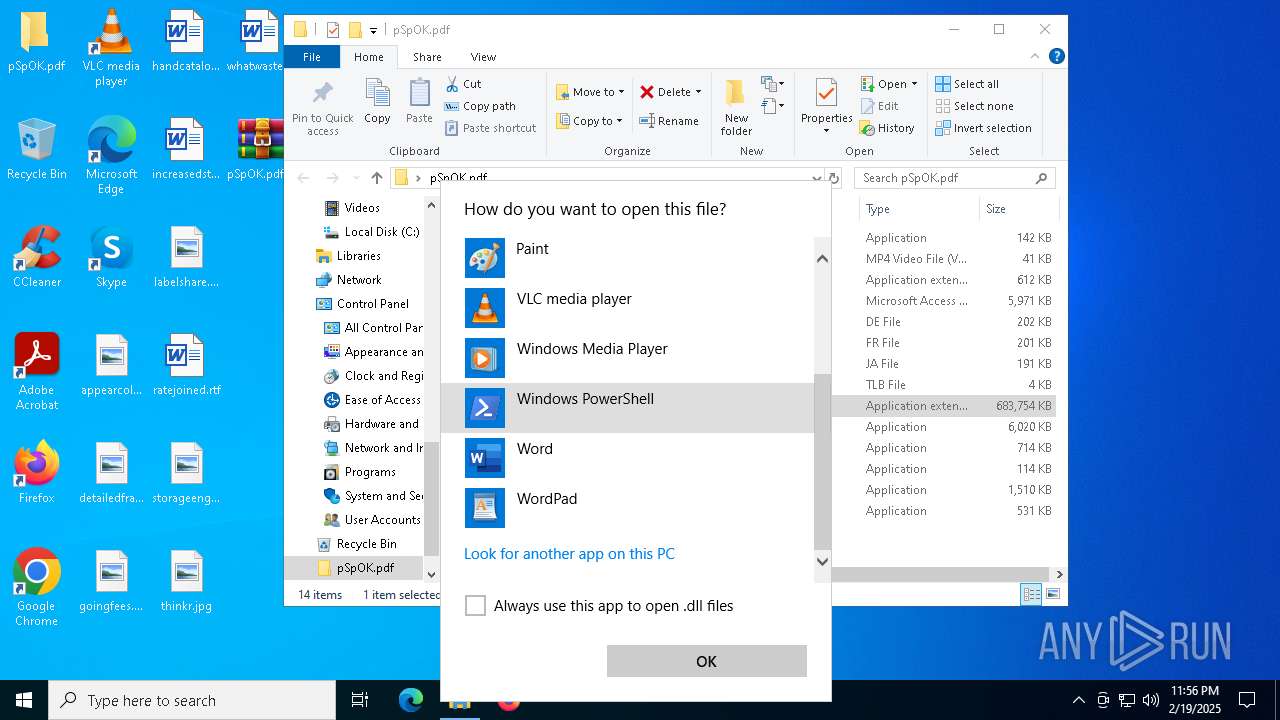
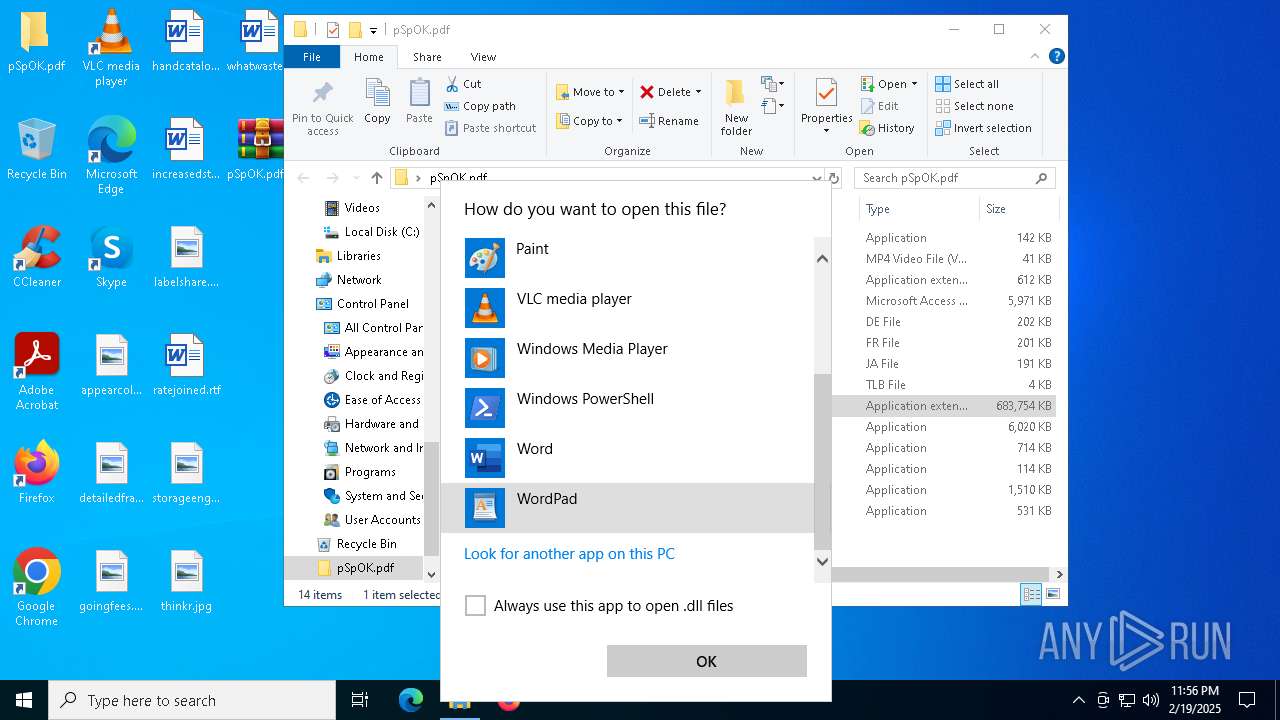
Reads Microsoft Office registry keys
- OpenWith.exe (PID: 1172)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | 0x0008 |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2025:02:16 12:39:14 |
| ZipCRC: | 0xf183ec46 |
| ZipCompressedSize: | 24667 |
| ZipUncompressedSize: | 41825 |
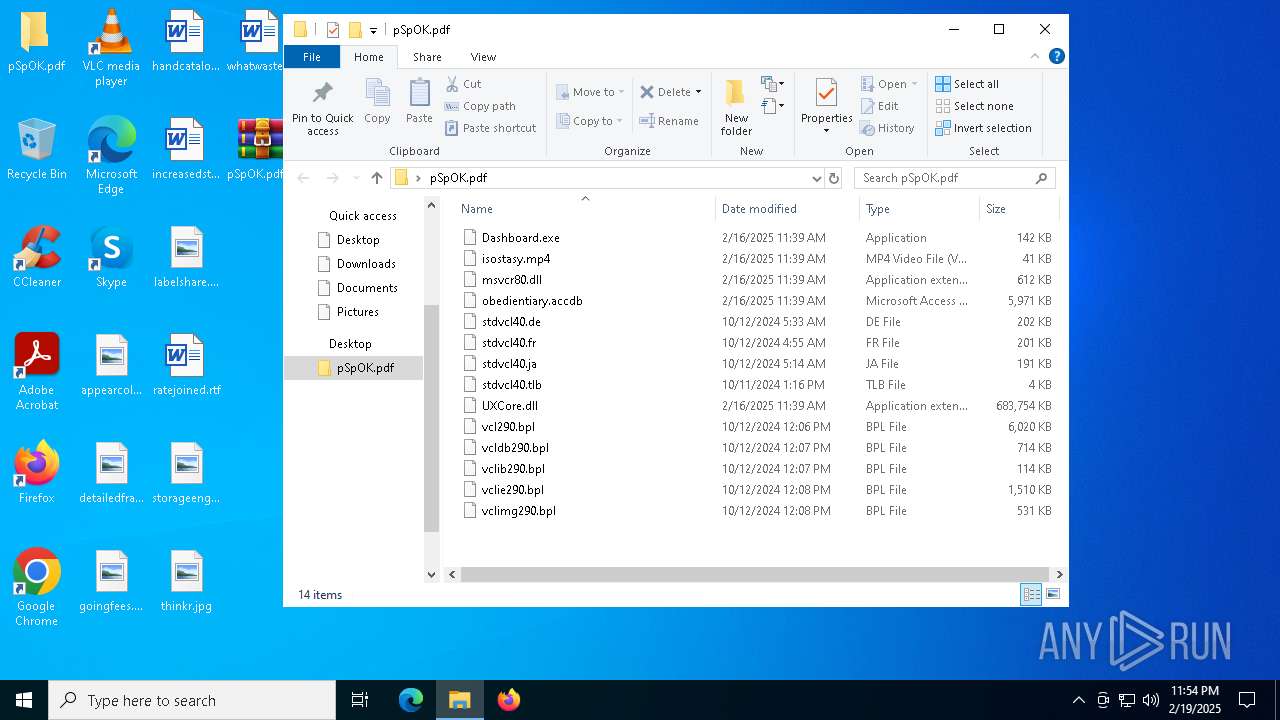
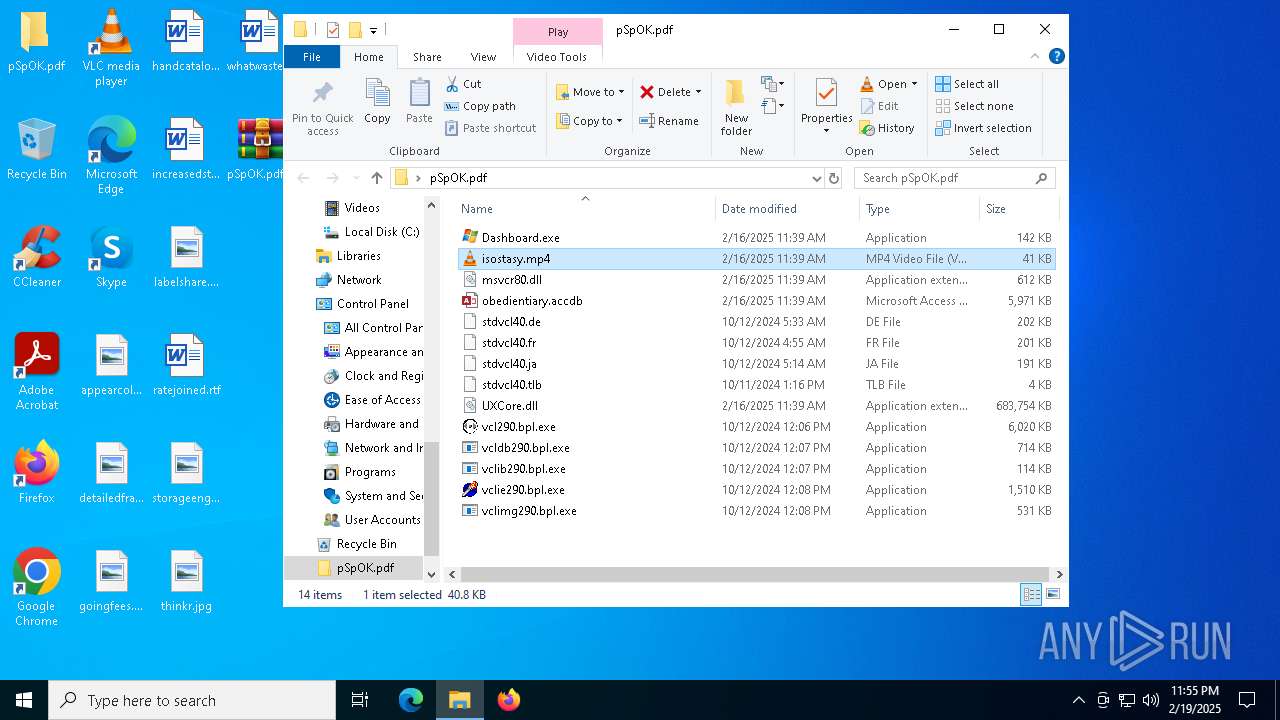
| ZipFileName: | isostasy.mp4 |
Total processes
135
Monitored processes
13
Malicious processes
4
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 188 | C:\Users\admin\AppData\Roaming\GUPM\Dashboard.exe | C:\Users\admin\AppData\Roaming\GUPM\Dashboard.exe | — | Dashboard.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Live installer client executable Exit code: 1 Version: 12.0.1202.0516 Modules
| |||||||||||||||
| 1172 | C:\WINDOWS\system32\OpenWith.exe -Embedding | C:\Windows\System32\OpenWith.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Pick an app Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1876 | C:\WINDOWS\System32\rundll32.exe C:\WINDOWS\System32\shell32.dll,SHCreateLocalServerRunDll {9aa46009-3ce0-458a-a354-715610a075e6} -Embedding | C:\Windows\System32\rundll32.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1876 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2680 | C:\WINDOWS\SysWOW64\DllHost.exe /Processid:{3E5FC7F9-9A51-4367-9063-A120244FBEC7} | C:\Windows\SysWOW64\dllhost.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: COM Surrogate Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2736 | "C:\Program Files\VideoLAN\VLC\vlc.exe" --started-from-file "C:\Users\admin\Desktop\pSpOK.pdf\isostasy.mp4" | C:\Program Files\VideoLAN\VLC\vlc.exe | explorer.exe | ||||||||||||
User: admin Company: VideoLAN Integrity Level: MEDIUM Description: VLC media player Exit code: 0 Version: 3.0.11 Modules
| |||||||||||||||
| 3208 | "C:\Program Files\WinRAR\WinRAR.exe" C:\Users\admin\Desktop\pSpOK.pdf.infected.zip | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 3848 | "C:\Users\admin\AppData\Roaming\GUPM\Dashboard.exe" | C:\Users\admin\AppData\Roaming\GUPM\Dashboard.exe | — | dllhost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Live installer client executable Exit code: 1 Version: 12.0.1202.0516 Modules
| |||||||||||||||
| 3884 | C:\WINDOWS\SysWOW64\explorer.exe | C:\Windows\SysWOW64\explorer.exe | cmd.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Explorer Version: 10.0.19041.3758 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4144 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
7 683
Read events
7 648
Write events
22
Delete events
13
Modification events
| (PID) Process: | (3208) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (3208) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (3208) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (3208) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\pSpOK.pdf.infected.zip | |||
| (PID) Process: | (3208) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (3208) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (3208) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (3208) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (3208) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\DialogEditHistory\ExtrPath |
| Operation: | delete value | Name: | 15 |
Value: | |||
| (PID) Process: | (3208) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\DialogEditHistory\ExtrPath |
| Operation: | delete value | Name: | 14 |
Value: | |||
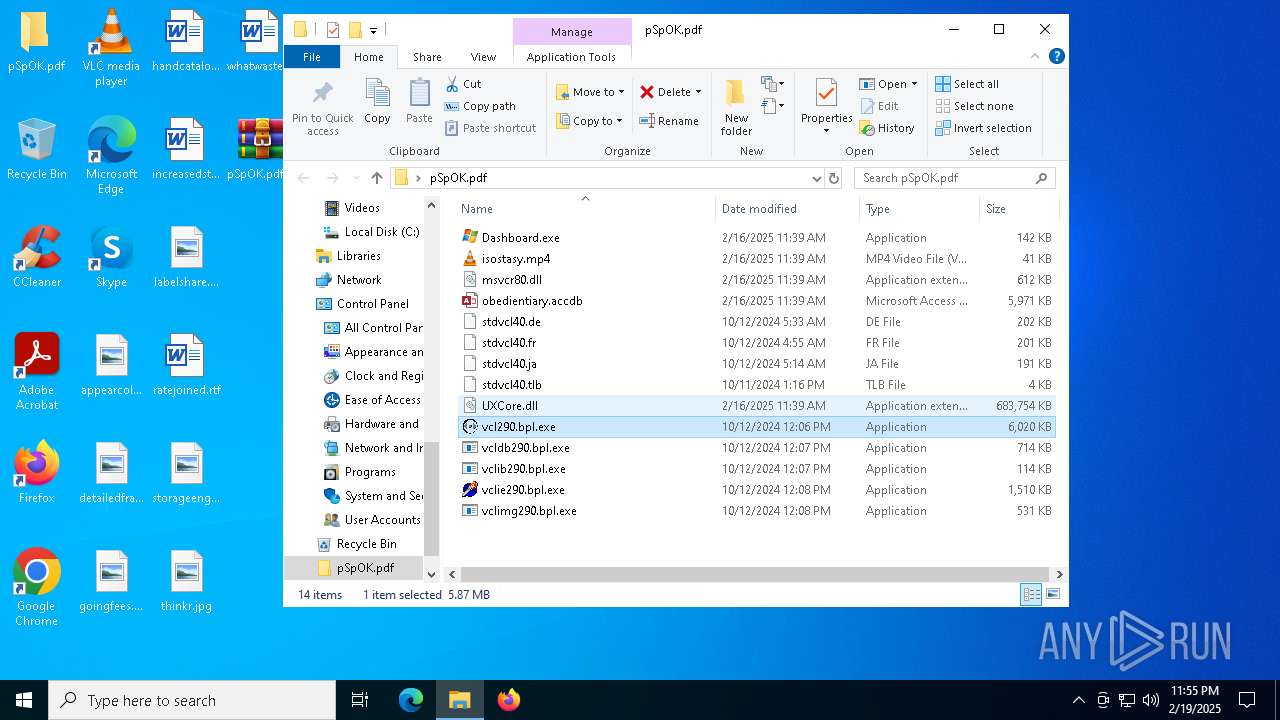
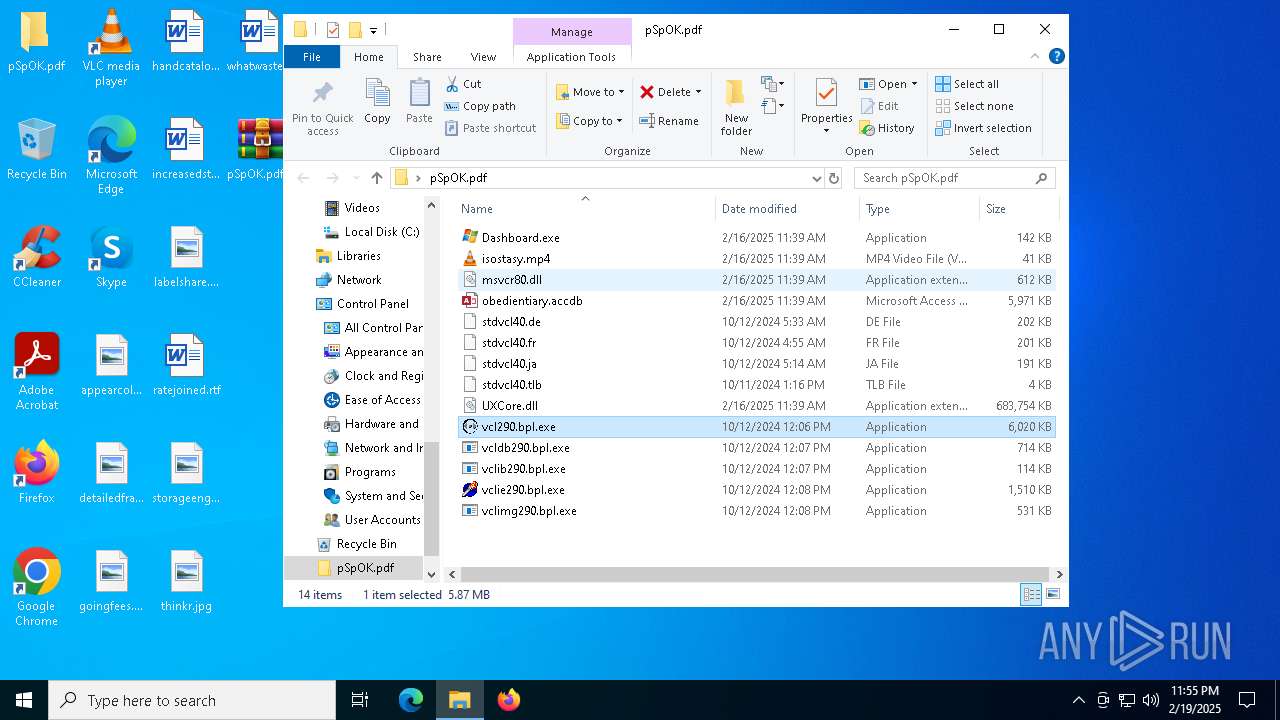
Executable files
14
Suspicious files
3
Text files
3
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
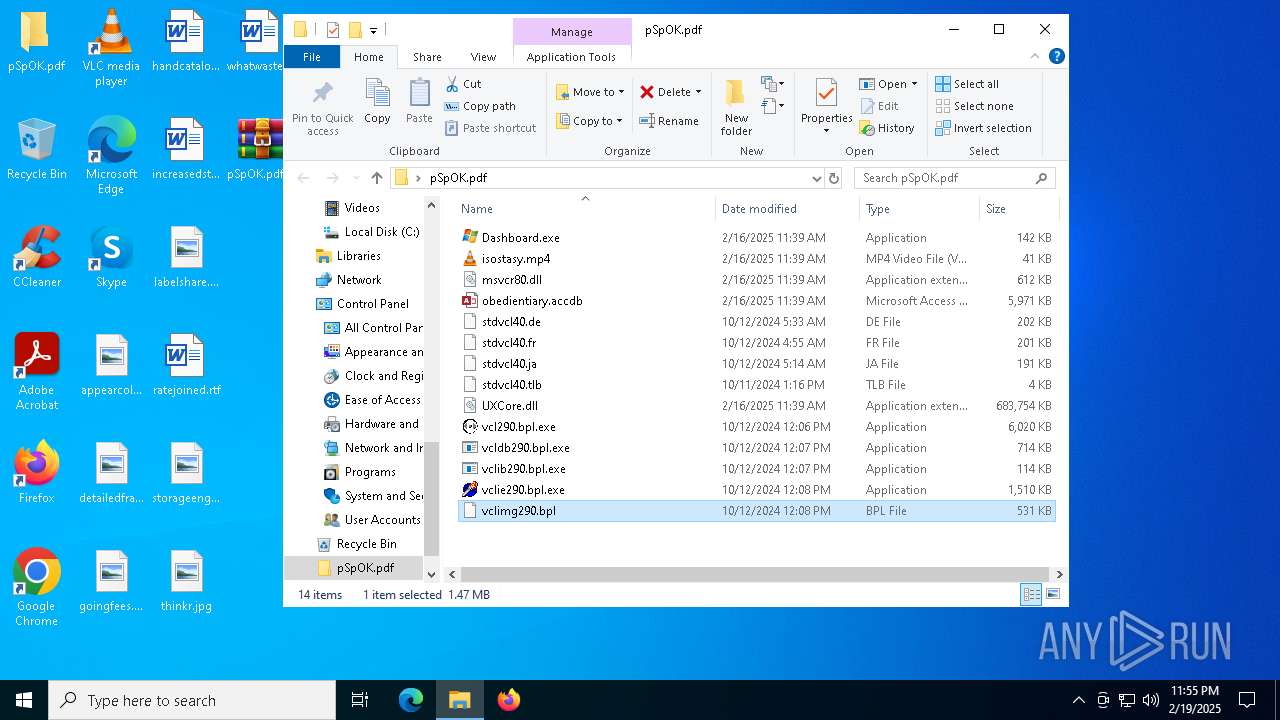
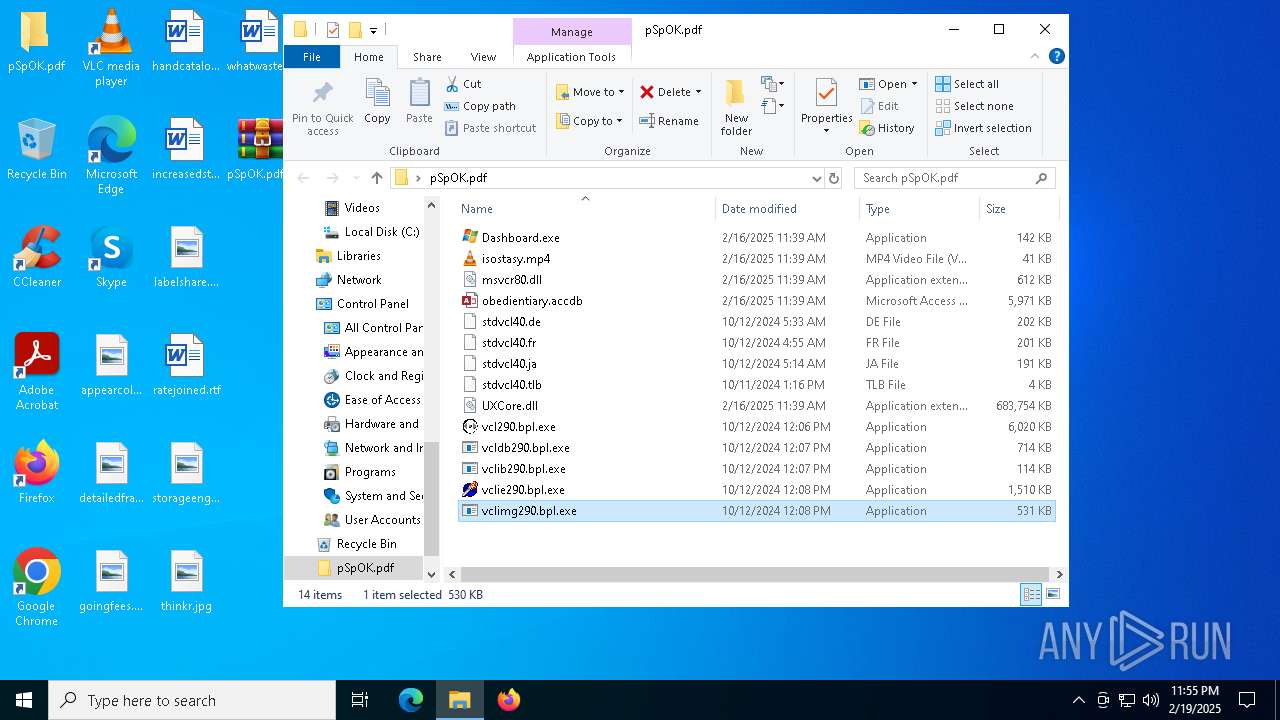
| 3208 | WinRAR.exe | C:\Users\admin\Desktop\pSpOK.pdf\obedientiary.accdb | — | |
MD5:— | SHA256:— | |||
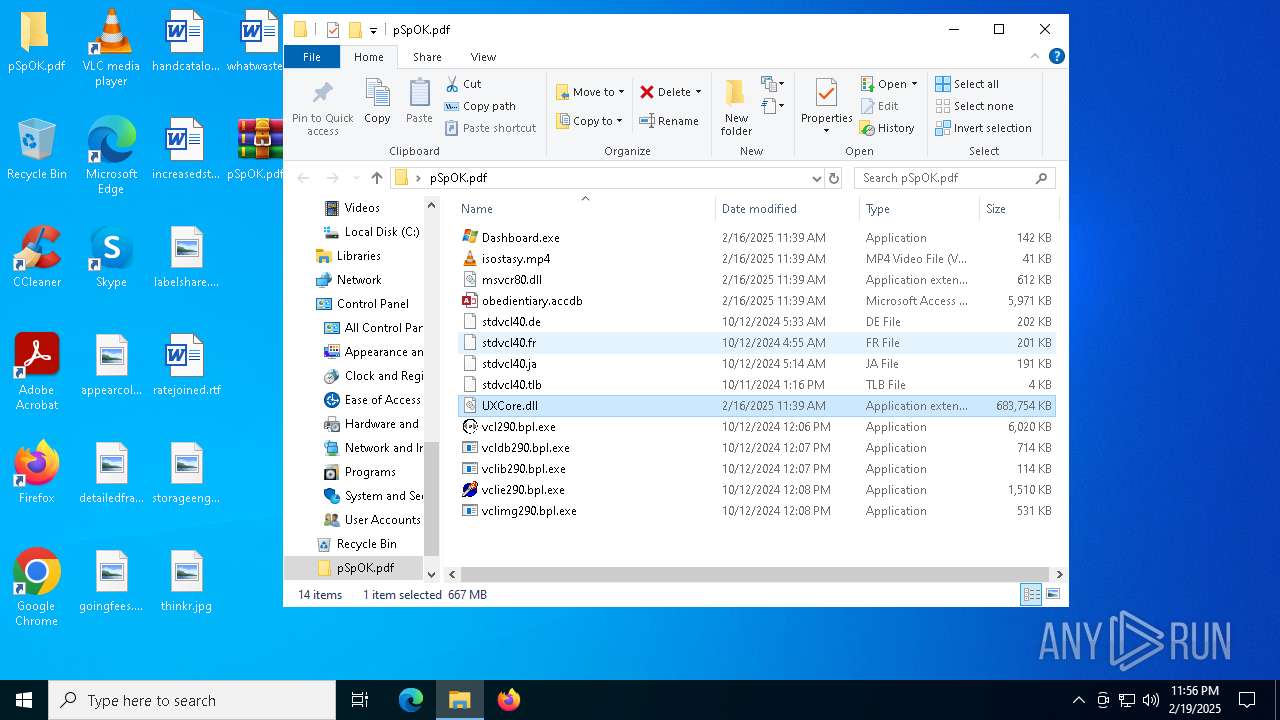
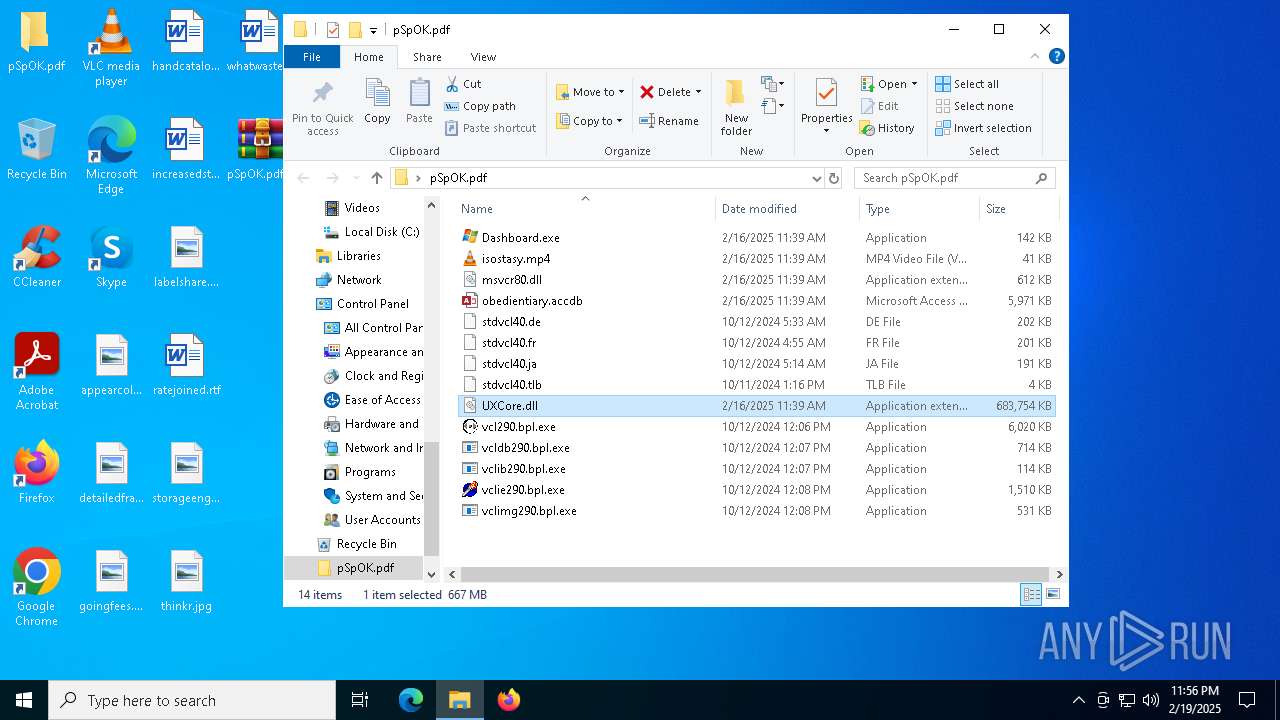
| 3208 | WinRAR.exe | C:\Users\admin\Desktop\pSpOK.pdf\UXCore.dll | — | |
MD5:— | SHA256:— | |||
| 5388 | Dashboard.exe | C:\Users\admin\AppData\Roaming\GUPM\UXCore.dll | — | |
MD5:— | SHA256:— | |||
| 5388 | Dashboard.exe | C:\Users\admin\AppData\Roaming\GUPM\obedientiary.accdb | — | |
MD5:— | SHA256:— | |||
| 188 | Dashboard.exe | C:\Users\admin\AppData\Local\Temp\174fcd01 | — | |
MD5:— | SHA256:— | |||
| 3848 | Dashboard.exe | C:\Users\admin\AppData\Local\Temp\1a302ee6 | — | |
MD5:— | SHA256:— | |||
| 4536 | cmd.exe | C:\Users\admin\AppData\Local\Temp\cvsfqrkeqccb | — | |
MD5:— | SHA256:— | |||
| 2736 | vlc.exe | — | ||
MD5:— | SHA256:— | |||
| 3208 | WinRAR.exe | C:\Users\admin\Desktop\pSpOK.pdf\stdvcl40.de | executable | |
MD5:3A25955EC6CE6DD5CB2E0BEDBB5DB46D | SHA256:55675A656542407D1EE9AB9552B018BC32BB15468689AC9CC716B322AE62D46D | |||
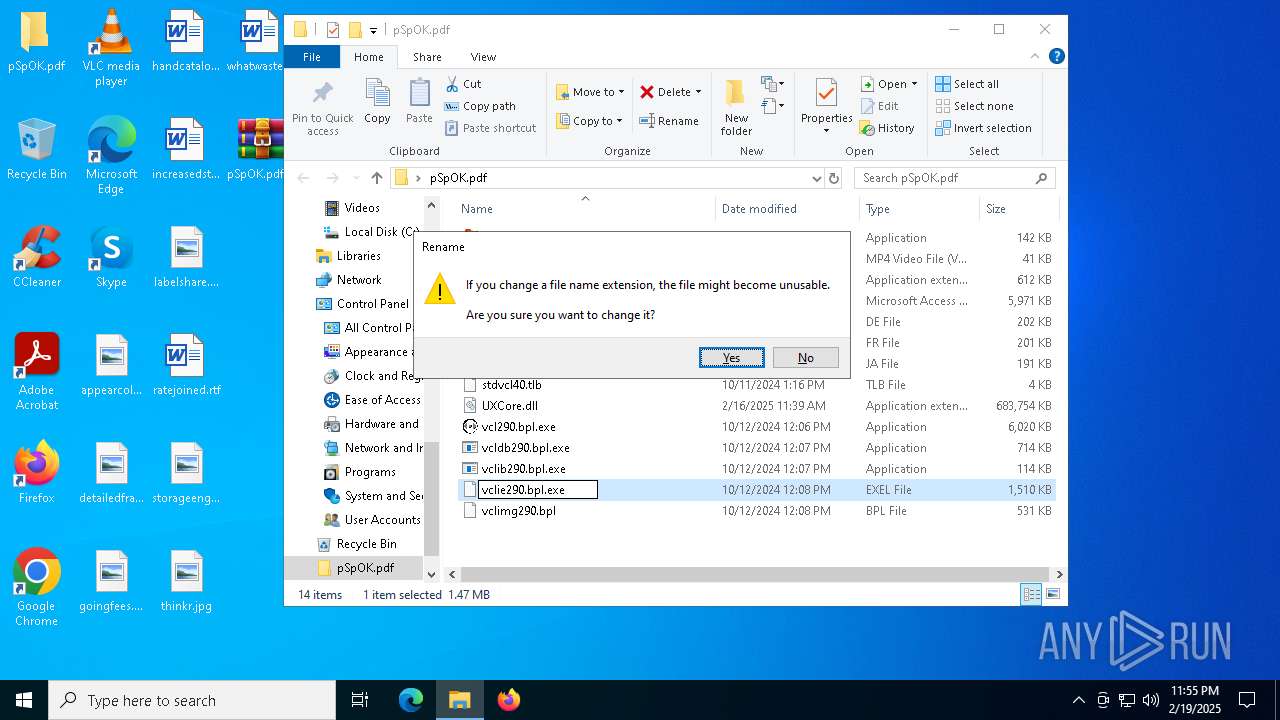
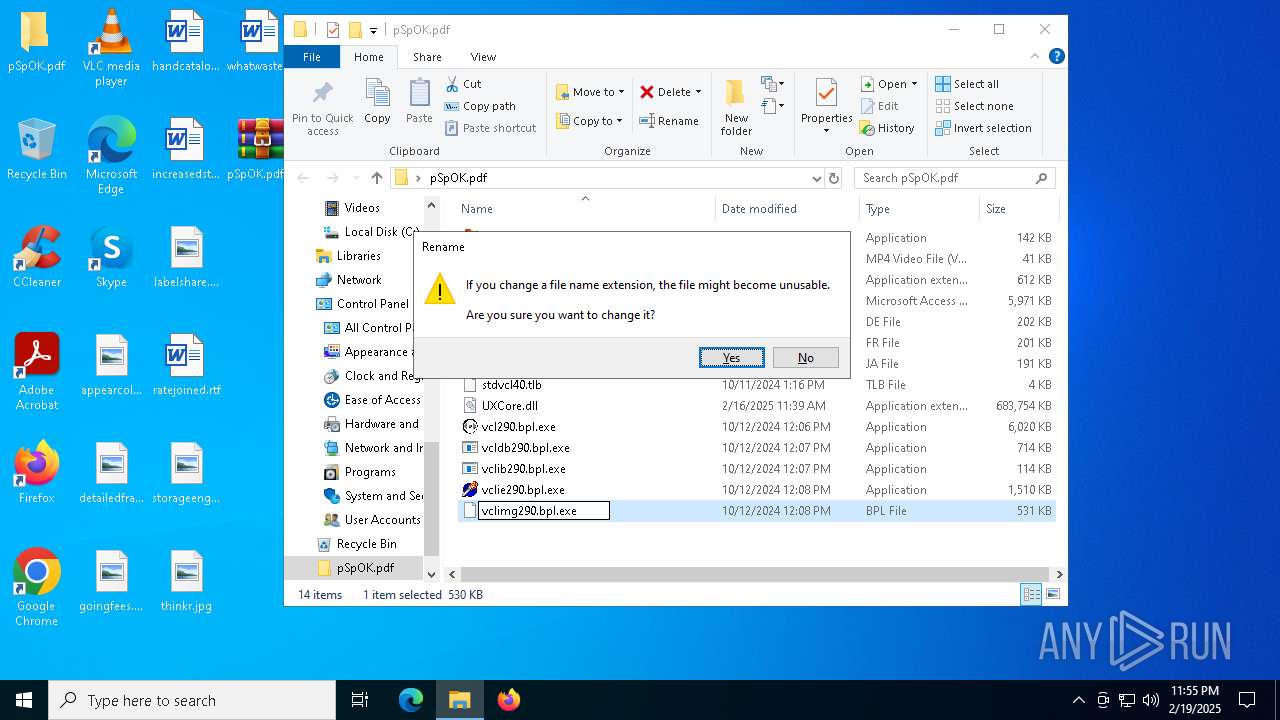
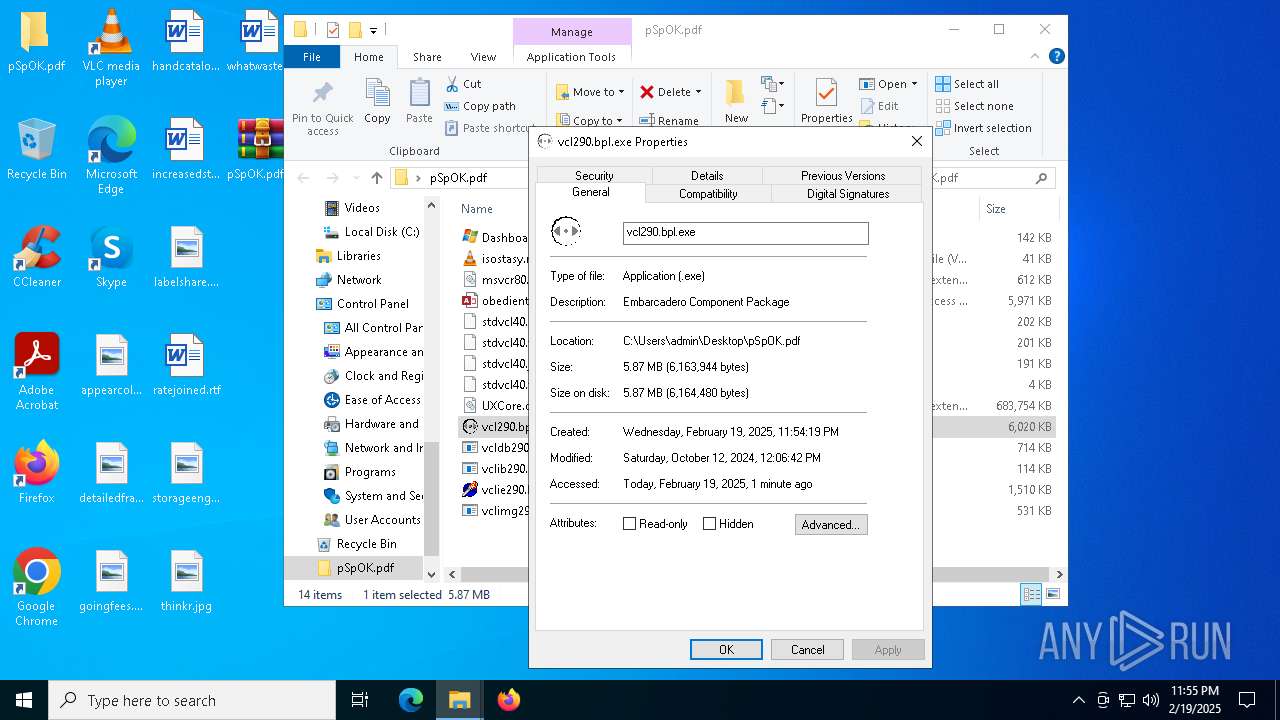
| 3208 | WinRAR.exe | C:\Users\admin\Desktop\pSpOK.pdf\vclie290.bpl | executable | |
MD5:7517C4834AA2C23AC9AB16EA013642D9 | SHA256:10EF9BFA6FD4DF9280A9EEBE8412E91AEF489B056DAE940D7A01F7654FB9332D | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
9
TCP/UDP connections
35
DNS requests
19
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5564 | svchost.exe | GET | 200 | 23.48.23.35:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
5564 | svchost.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | GET | 200 | 23.48.23.35:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
1176 | svchost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
4624 | SIHClient.exe | GET | 200 | 2.23.246.101:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
4624 | SIHClient.exe | GET | 200 | 2.23.246.101:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
4308 | backgroundTaskHost.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
1876 | RUXIMICS.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5564 | svchost.exe | 23.48.23.35:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
4712 | MoUsoCoreWorker.exe | 23.48.23.35:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
4712 | MoUsoCoreWorker.exe | 23.35.229.160:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
5564 | svchost.exe | 23.35.229.160:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
5064 | SearchApp.exe | 92.123.104.32:443 | www.bing.com | Akamai International B.V. | DE | whitelisted |
— | — | 2.17.190.73:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
5564 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
www.bing.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
login.live.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
arc.msn.com |
| whitelisted |
fd.api.iris.microsoft.com |
| whitelisted |
Threats
Process | Message |
|---|---|
vlc.exe | main libvlc debug: Copyright © 1996-2020 the VideoLAN team
|
vlc.exe | main libvlc debug: revision 3.0.11-0-gdc0c5ced72
|
vlc.exe | main libvlc debug: configured with ../extras/package/win32/../../../configure '--enable-update-check' '--enable-lua' '--enable-faad' '--enable-flac' '--enable-theora' '--enable-avcodec' '--enable-merge-ffmpeg' '--enable-dca' '--enable-mpc' '--enable-libass' '--enable-schroedinger' '--enable-realrtsp' '--enable-live555' '--enable-dvdread' '--enable-shout' '--enable-goom' '--enable-caca' '--enable-qt' '--enable-skins2' '--enable-sse' '--enable-mmx' '--enable-libcddb' '--enable-zvbi' '--disable-telx' '--enable-nls' '--host=x86_64-w64-mingw32' '--with-breakpad=https://win.crashes.videolan.org' 'host_alias=x86_64-w64-mingw32' 'PKG_CONFIG_LIBDIR=/home/jenkins/workspace/vlc-release/windows/vlc-release-win32-x64/contrib/x86_64-w64-mingw32/lib/pkgconfig'
|
vlc.exe | main libvlc debug: VLC media player - 3.0.11 Vetinari
|
vlc.exe | main libvlc debug: min period: 1 ms, max period: 1000000 ms
|
vlc.exe | main libvlc debug: using multimedia timers as clock source
|
vlc.exe | main libvlc debug: loading plugins cache file C:\Program Files\VideoLAN\VLC\plugins\plugins.dat
|
vlc.exe | main libvlc debug: searching plug-in modules
|
vlc.exe | main libvlc debug: recursively browsing `C:\Program Files\VideoLAN\VLC\plugins'
|
vlc.exe | main libvlc debug: plug-ins loaded: 494 modules
|