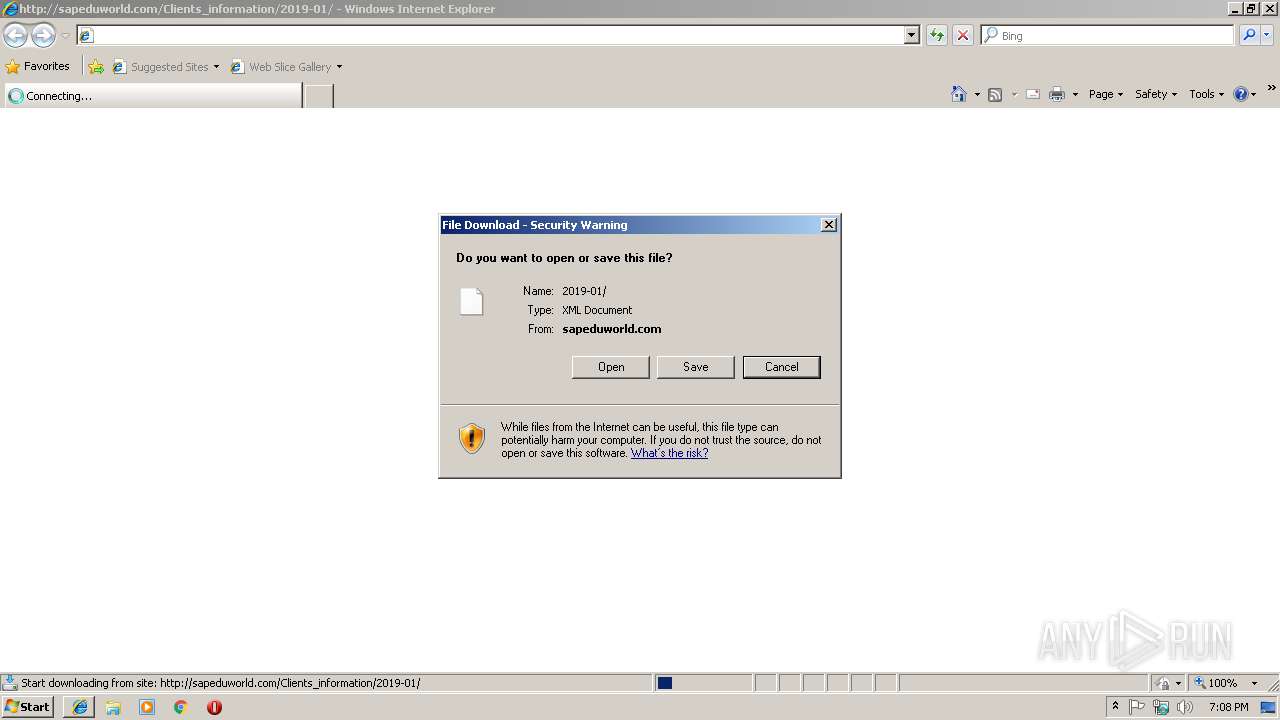
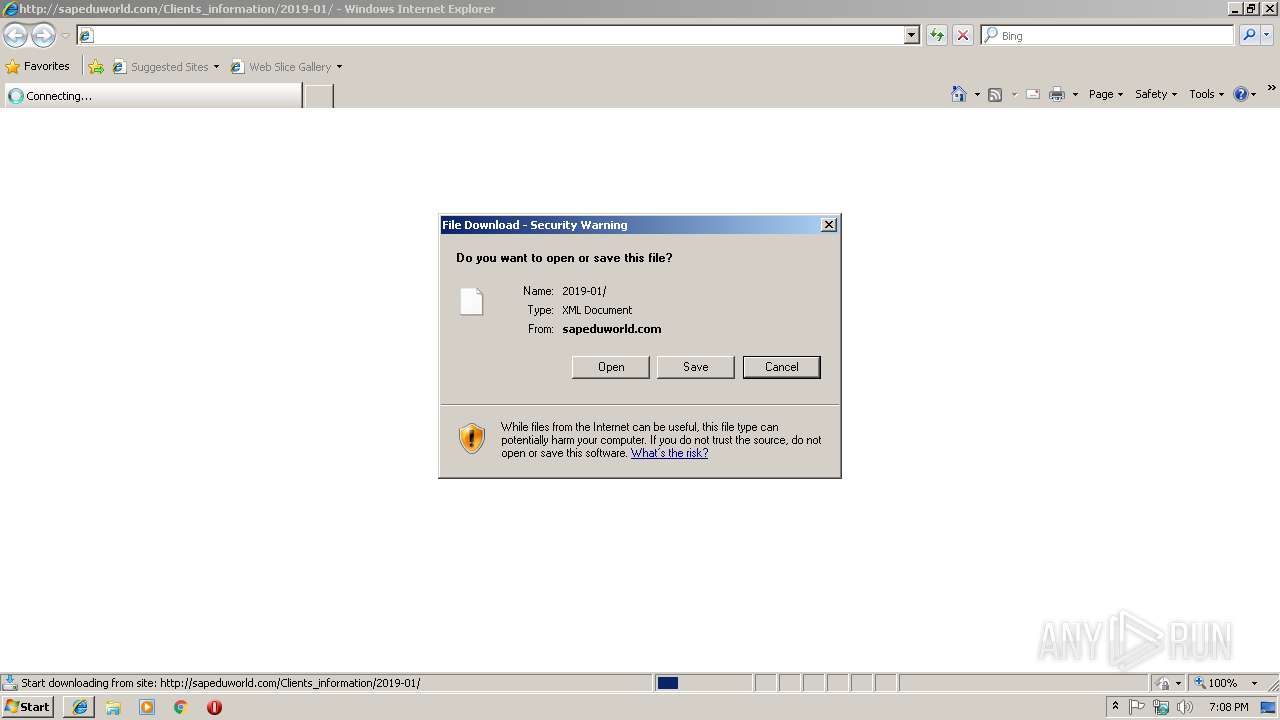
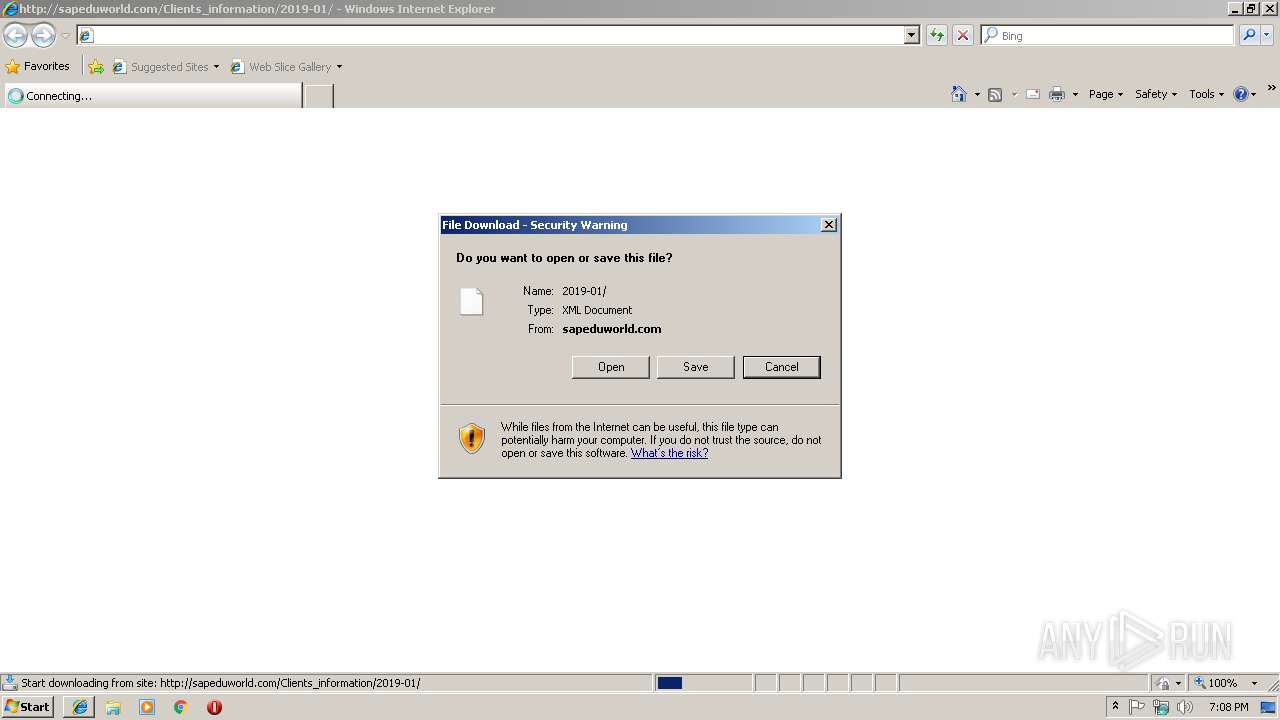
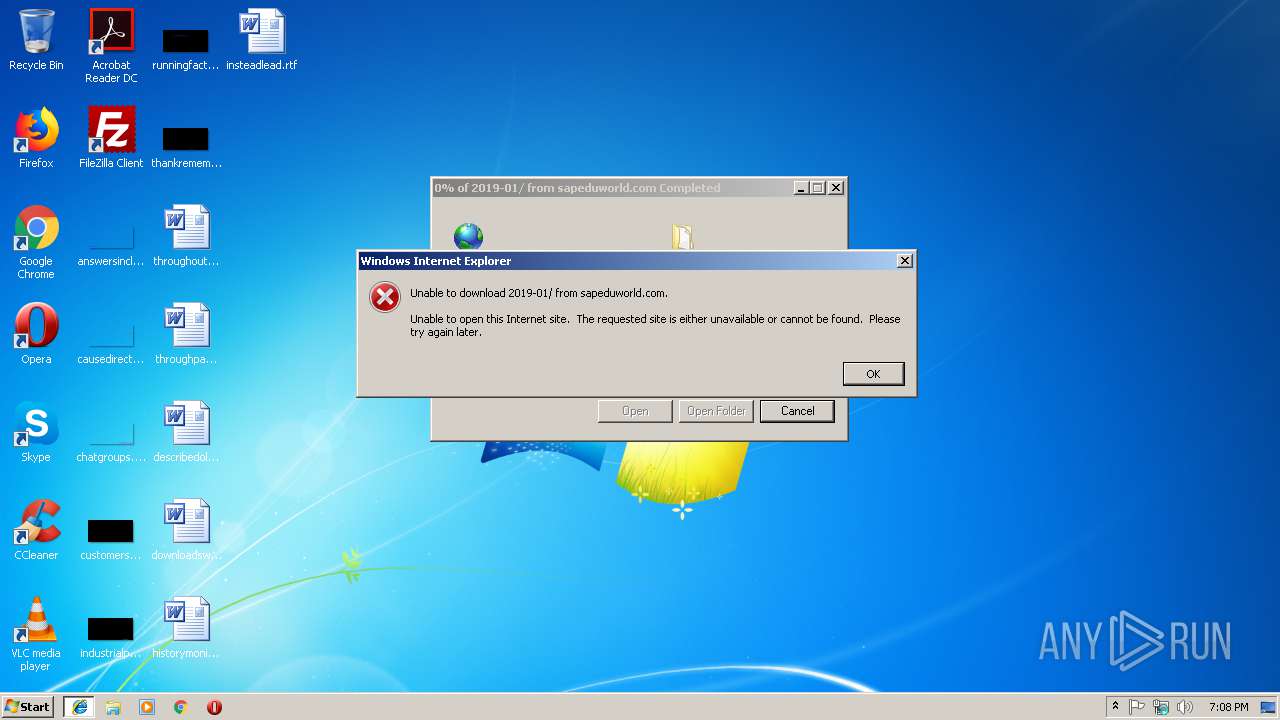
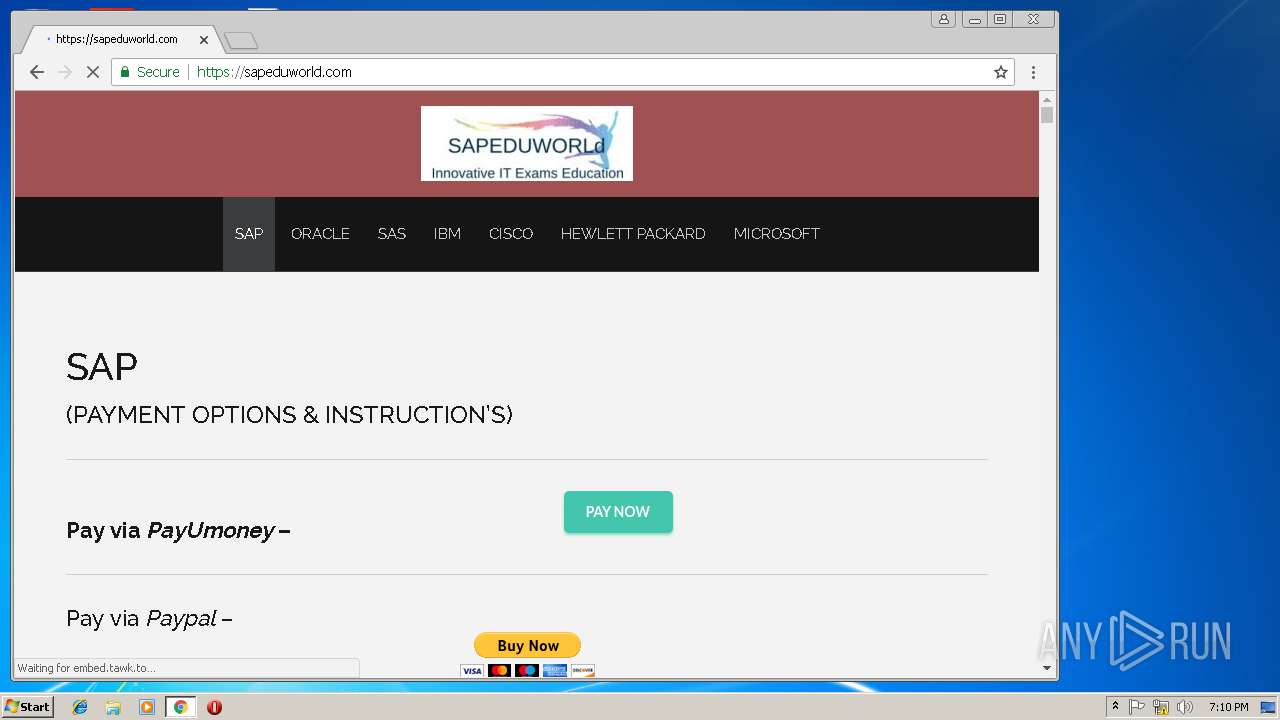
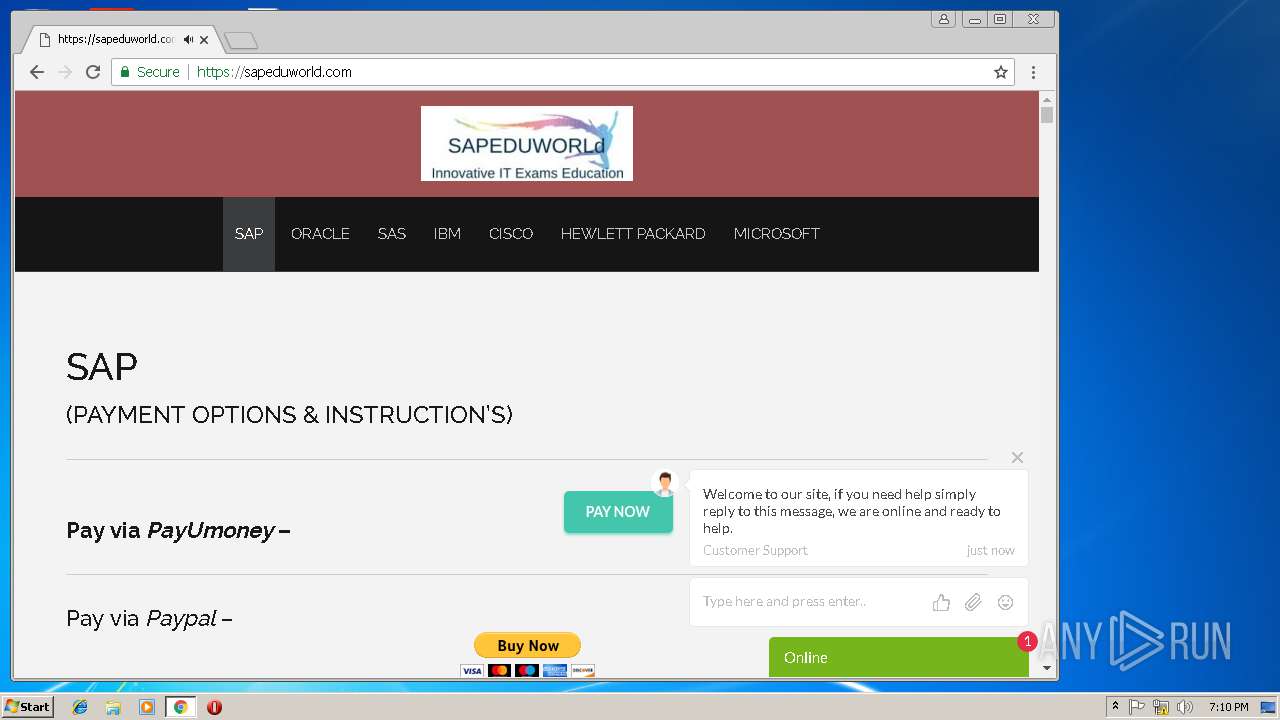
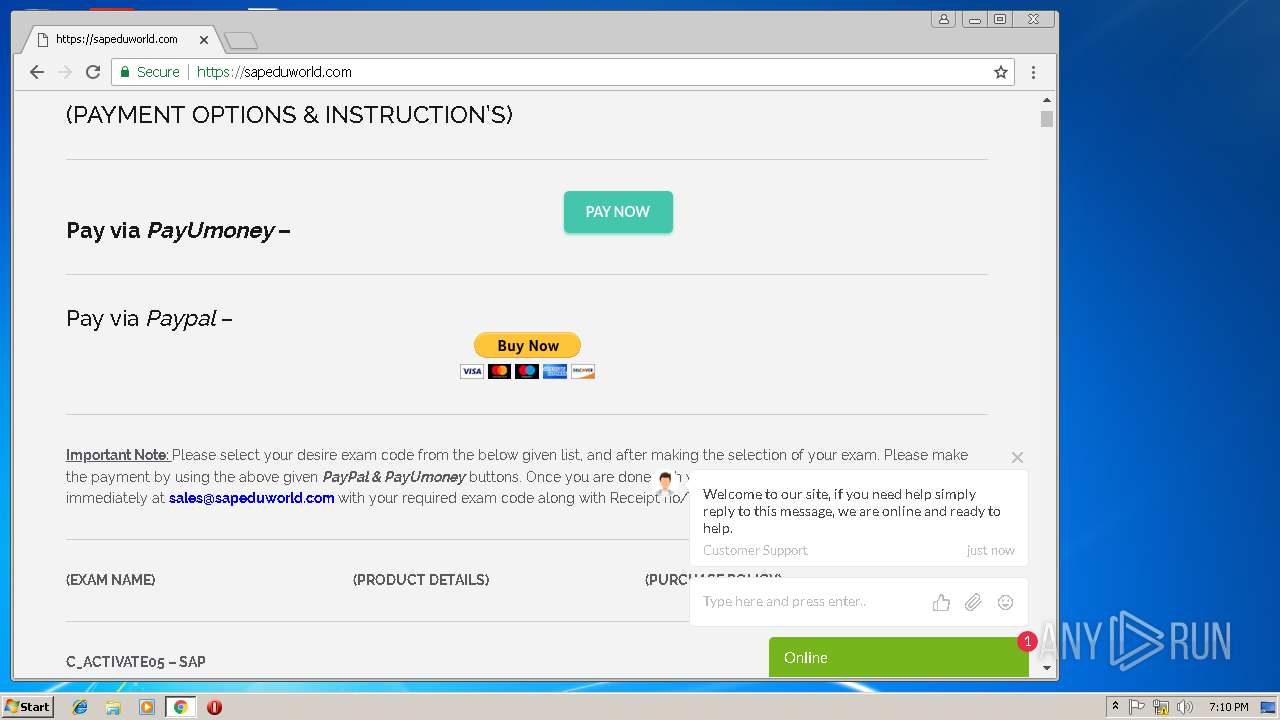
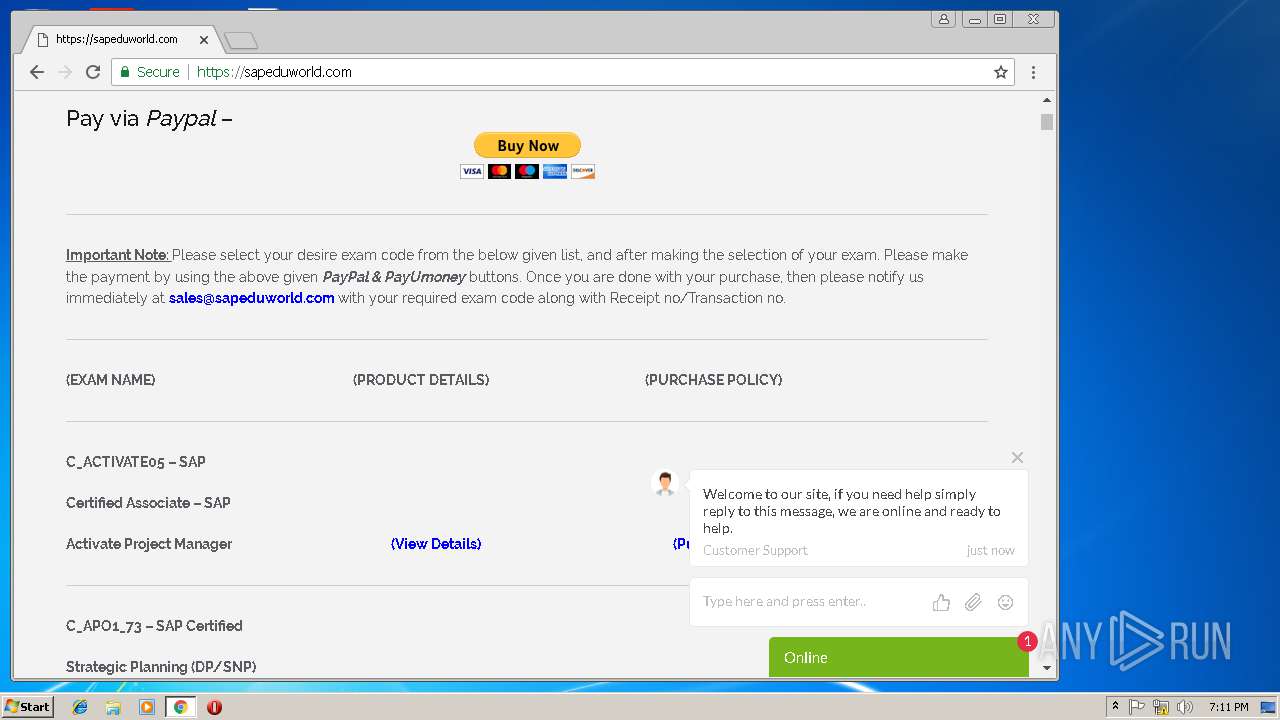
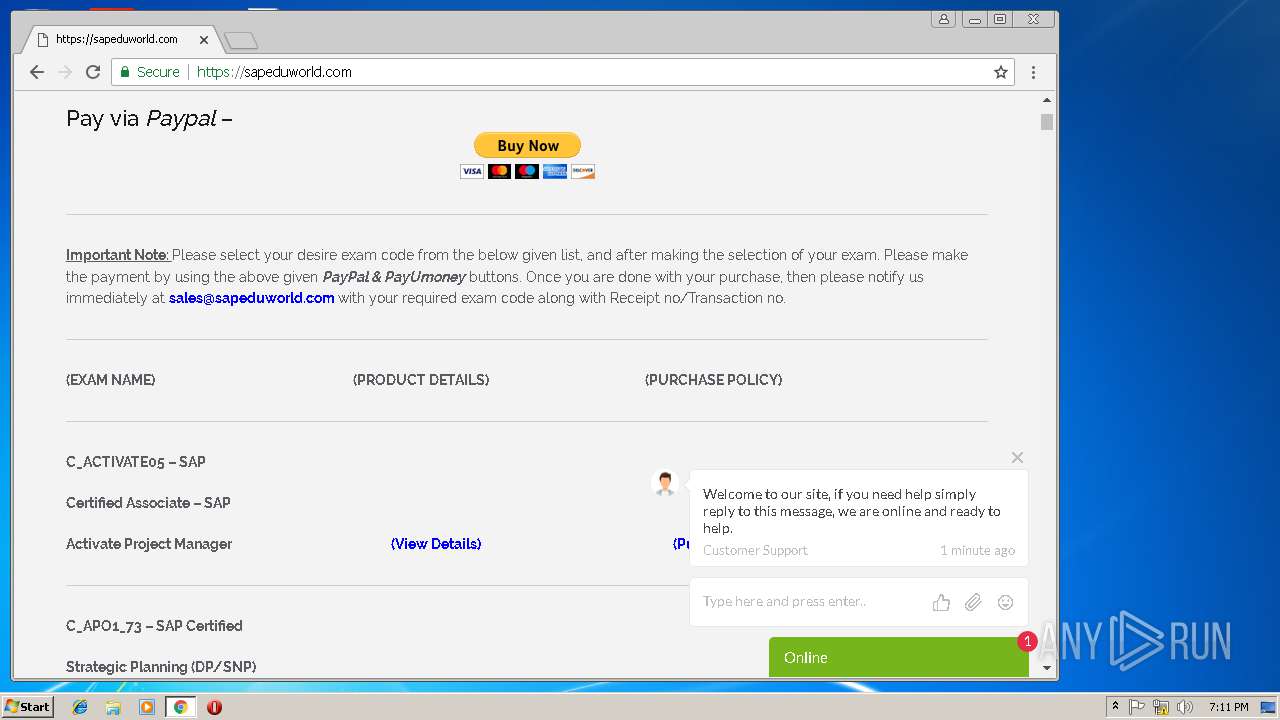
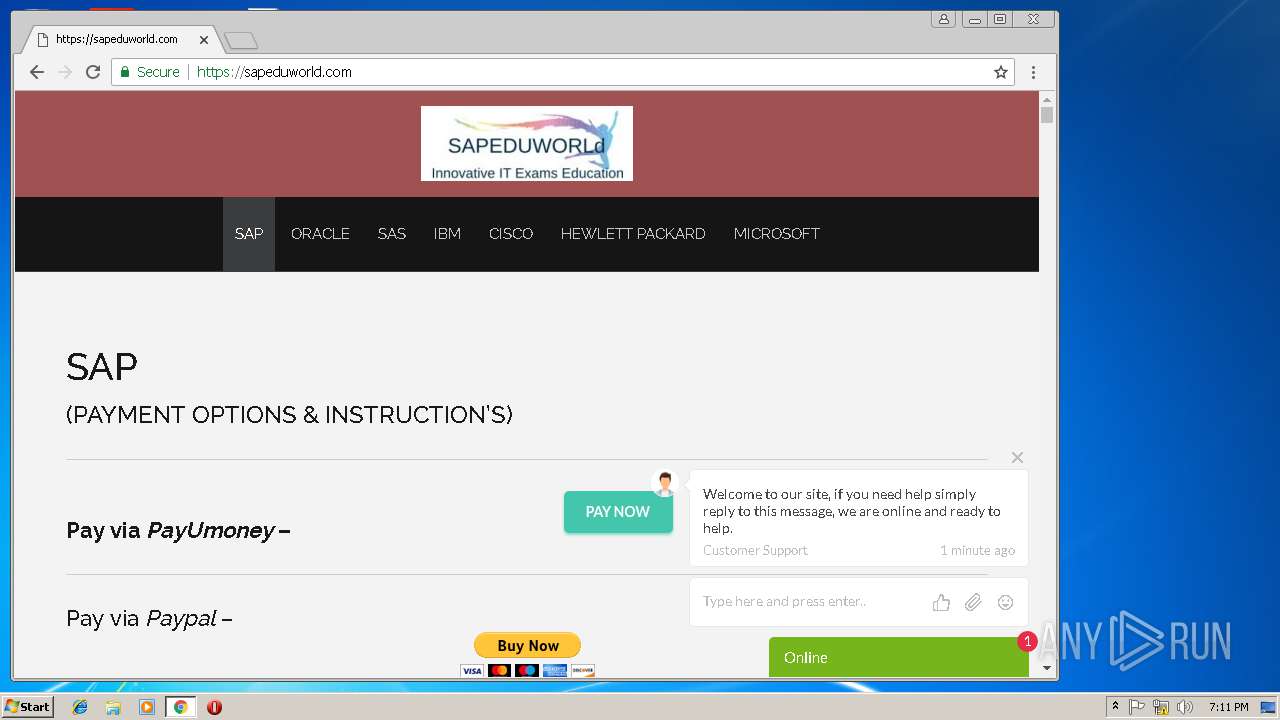
| URL: | http://sapeduworld.com/Clients_information/2019-01 |
| Full analysis: | https://app.any.run/tasks/40304217-b91f-4947-bf98-471022481a63 |
| Verdict: | Malicious activity |
| Threats: | Emotet is one of the most dangerous trojans ever created. Over the course of its lifetime, it was upgraded to become a very destructive malware. It targets mostly corporate victims but even private users get infected in mass spam email campaigns. |
| Analysis date: | January 22, 2019, 19:07:34 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MD5: | C164C6AF3CD1E52536B4E371D9711707 |
| SHA1: | C297035104D6E66E36D674093DA859E6BE8FCAA3 |
| SHA256: | 8E7E3EE3D355EB7CA9C2D7EABFDE0C8A49451FBDB2277560F87F5AE100E79E64 |
| SSDEEP: | 3:N1KNEVABsqKIKmXRW3MI4MKLKFy+:CWqBslmgKMK+Fy+ |
MALICIOUS
No malicious indicators.SUSPICIOUS
No suspicious indicators.INFO
Changes internet zones settings
- iexplore.exe (PID: 3000)
Application launched itself
- iexplore.exe (PID: 3000)
- chrome.exe (PID: 3256)
Reads internet explorer settings
- iexplore.exe (PID: 3296)
Reads Internet Cache Settings
- iexplore.exe (PID: 3296)
Changes settings of System certificates
- chrome.exe (PID: 3256)
Reads settings of System Certificates
- chrome.exe (PID: 3256)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
48
Monitored processes
18
Malicious processes
0
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 896 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=gpu-process --field-trial-handle=976,5155504341040494669,13447804381796605670,131072 --enable-features=PasswordImport --gpu-preferences=KAAAAAAAAACAAwBAAQAAAAAAAAAAAGAAEAAAAAAAAAAAAAAAAAAAACgAAAAEAAAAIAAAAAAAAAAoAAAAAAAAADAAAAAAAAAAOAAAAAAAAAAQAAAAAAAAAAAAAAAKAAAAEAAAAAAAAAAAAAAACwAAABAAAAAAAAAAAQAAAAoAAAAQAAAAAAAAAAEAAAALAAAA --service-request-channel-token=21F36403827F66576941728A7970F846 --mojo-platform-channel-handle=1032 --ignored=" --type=renderer " /prefetch:2 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google Inc. Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 68.0.3440.106 Modules
| |||||||||||||||
| 1204 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=976,5155504341040494669,13447804381796605670,131072 --enable-features=PasswordImport --disable-gpu-compositing --service-pipe-token=3A723B96D58005D312237752AFE513CD --lang=en-US --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=3A723B96D58005D312237752AFE513CD --renderer-client-id=11 --mojo-platform-channel-handle=3696 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google Inc. Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 68.0.3440.106 Modules
| |||||||||||||||
| 2352 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=976,5155504341040494669,13447804381796605670,131072 --enable-features=PasswordImport --disable-gpu-compositing --service-pipe-token=09DFEF9AD9FDB23C511F6D136A51657D --lang=en-US --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=09DFEF9AD9FDB23C511F6D136A51657D --renderer-client-id=7 --mojo-platform-channel-handle=3628 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google Inc. Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 68.0.3440.106 Modules
| |||||||||||||||
| 2440 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=976,5155504341040494669,13447804381796605670,131072 --enable-features=PasswordImport --disable-gpu-compositing --service-pipe-token=413159DF00BCEED083023CF27508CE69 --lang=en-US --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=413159DF00BCEED083023CF27508CE69 --renderer-client-id=10 --mojo-platform-channel-handle=2348 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google Inc. Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 68.0.3440.106 Modules
| |||||||||||||||
| 2500 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=976,5155504341040494669,13447804381796605670,131072 --enable-features=PasswordImport --service-pipe-token=7D79C3E55D4D725892D4F85948EB4620 --lang=en-US --instant-process --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=7D79C3E55D4D725892D4F85948EB4620 --renderer-client-id=5 --mojo-platform-channel-handle=1900 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google Inc. Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 68.0.3440.106 Modules
| |||||||||||||||
| 2616 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=976,5155504341040494669,13447804381796605670,131072 --enable-features=PasswordImport --disable-gpu-compositing --service-pipe-token=16EDA6ABB5F4C7BB2B7D123F9E82A4D1 --lang=en-US --instant-process --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=16EDA6ABB5F4C7BB2B7D123F9E82A4D1 --renderer-client-id=6 --mojo-platform-channel-handle=3528 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google Inc. Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 68.0.3440.106 Modules
| |||||||||||||||
| 2620 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --field-trial-handle=976,5155504341040494669,13447804381796605670,131072 --enable-features=PasswordImport --lang=en-US --no-sandbox --service-request-channel-token=2077F20032D41AD7F1B686C5CBB84314 --mojo-platform-channel-handle=3796 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google Inc. Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 68.0.3440.106 Modules
| |||||||||||||||
| 2676 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=976,5155504341040494669,13447804381796605670,131072 --enable-features=PasswordImport --disable-gpu-compositing --service-pipe-token=F3277D155F94DE6B5C56DF99C215C1E6 --lang=en-US --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=F3277D155F94DE6B5C56DF99C215C1E6 --renderer-client-id=14 --mojo-platform-channel-handle=2084 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google Inc. Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 68.0.3440.106 Modules
| |||||||||||||||
| 2780 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --field-trial-handle=976,5155504341040494669,13447804381796605670,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --service-request-channel-token=E893622EDDFF1240FCE31F1B135BF072 --mojo-platform-channel-handle=608 --ignored=" --type=renderer " /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google Inc. Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 68.0.3440.106 Modules
| |||||||||||||||
| 2804 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=976,5155504341040494669,13447804381796605670,131072 --enable-features=PasswordImport --service-pipe-token=BA2B5DD86D5C5AFA6A4DBEC5CDE0EF80 --lang=en-US --extension-process --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=BA2B5DD86D5C5AFA6A4DBEC5CDE0EF80 --renderer-client-id=3 --mojo-platform-channel-handle=2076 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google Inc. Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 68.0.3440.106 Modules
| |||||||||||||||
Total events
901
Read events
782
Write events
114
Delete events
5
Modification events
| (PID) Process: | (3000) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
| (PID) Process: | (3000) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
| (PID) Process: | (3000) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 1 | |||
| (PID) Process: | (3000) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\Zones |
| Operation: | write | Name: | SecuritySafe |
Value: 1 | |||
| (PID) Process: | (3000) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings |
| Operation: | write | Name: | ProxyEnable |
Value: 0 | |||
| (PID) Process: | (3000) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\Connections |
| Operation: | write | Name: | SavedLegacySettings |
Value: 4600000069000000010000000000000000000000000000000000000000000000C0E333BBEAB1D301000000000000000000000000020000001700000000000000FE800000000000007D6CB050D9C573F70B000000000000006D00330032005C004D00530049004D004700330032002E0064006C000100000004AA400014AA4000040000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000002000000C0A8016400000000000000000000000000000000000000000800000000000000805D3F00983740000008000002000000000000600000002060040000B8A94000020000008802000060040000B8A9400004000000F8010000B284000088B64000B84B400043003A000000000000000000000000000000000000000000 | |||
| (PID) Process: | (3000) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Recovery\Active |
| Operation: | write | Name: | {0286DE23-1E79-11E9-AA93-5254004A04AF} |
Value: 0 | |||
| (PID) Process: | (3000) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Ext\Stats\{2670000A-7350-4F3C-8081-5663EE0C6C49}\iexplore |
| Operation: | write | Name: | Type |
Value: 4 | |||
| (PID) Process: | (3000) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Ext\Stats\{2670000A-7350-4F3C-8081-5663EE0C6C49}\iexplore |
| Operation: | write | Name: | Count |
Value: 3 | |||
| (PID) Process: | (3000) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Ext\Stats\{2670000A-7350-4F3C-8081-5663EE0C6C49}\iexplore |
| Operation: | write | Name: | Time |
Value: E3070100020016001300070032007D03 | |||
Executable files
0
Suspicious files
74
Text files
86
Unknown types
16
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3000 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\RB73MZ6Y\favicon[1].ico | — | |
MD5:— | SHA256:— | |||
| 3000 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\Internet Explorer\Services\search_{0633EE93-D776-472f-A0FF-E1416B8B2E3A}.ico | — | |
MD5:— | SHA256:— | |||
| 3000 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\~DFAC9100E125420E85.TMP | — | |
MD5:— | SHA256:— | |||
| 3000 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\~DF4178F4847B4B92EB.TMP | — | |
MD5:— | SHA256:— | |||
| 3000 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Internet Explorer\Recovery\Active\RecoveryStore.{0286DE23-1E79-11E9-AA93-5254004A04AF}.dat | — | |
MD5:— | SHA256:— | |||
| 3256 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\0c65a3a6-d376-4821-aa89-4ca4e1aaac94.tmp | — | |
MD5:— | SHA256:— | |||
| 3256 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Download Service\EntryDB\000016.dbtmp | — | |
MD5:— | SHA256:— | |||
| 3256 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\data_reduction_proxy_leveldb\000016.dbtmp | — | |
MD5:— | SHA256:— | |||
| 3000 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Internet Explorer\Recovery\Active\{0286DE24-1E79-11E9-AA93-5254004A04AF}.dat | binary | |
MD5:— | SHA256:— | |||
| 3296 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\Low\JavaDeployReg.log | text | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
13
TCP/UDP connections
49
DNS requests
32
Threats
1
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
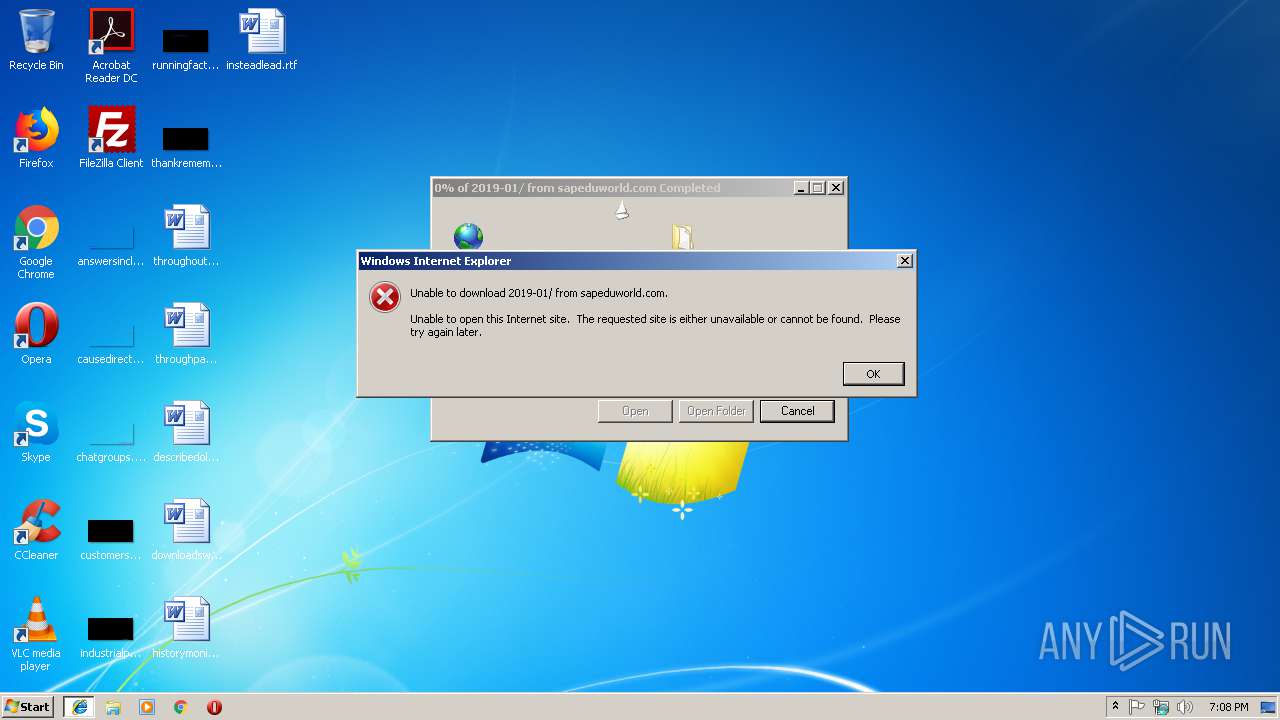
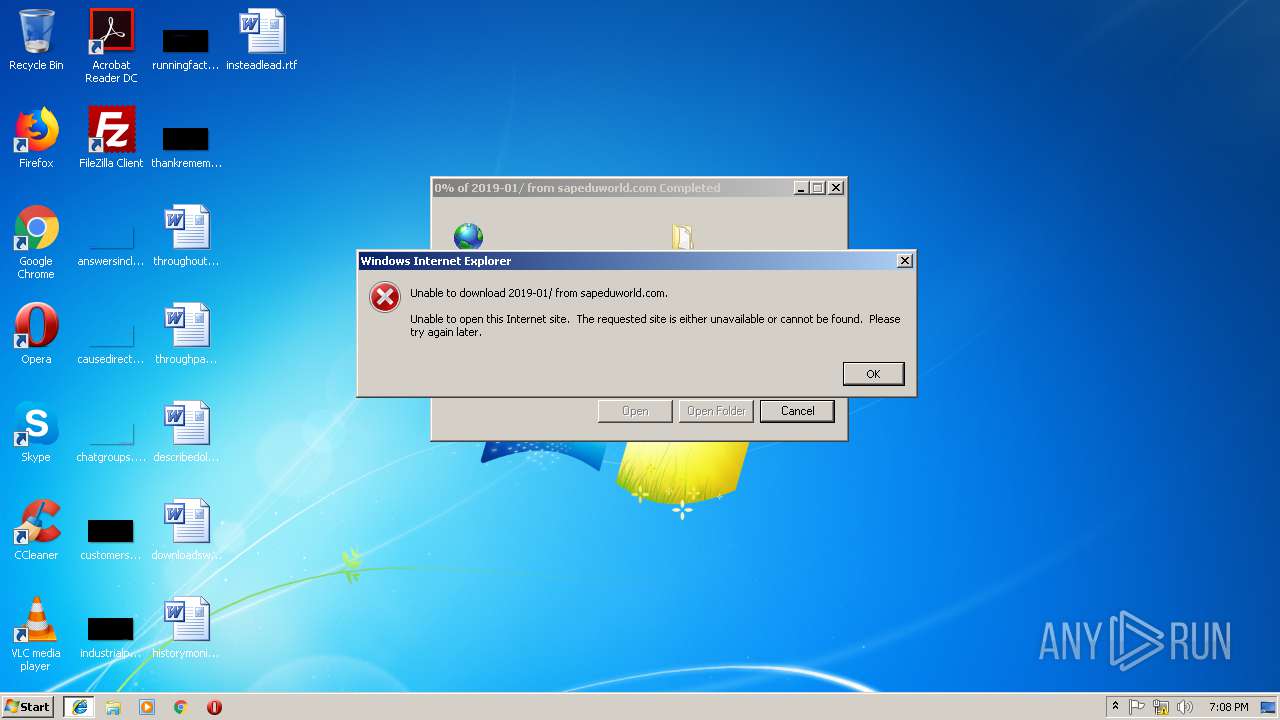
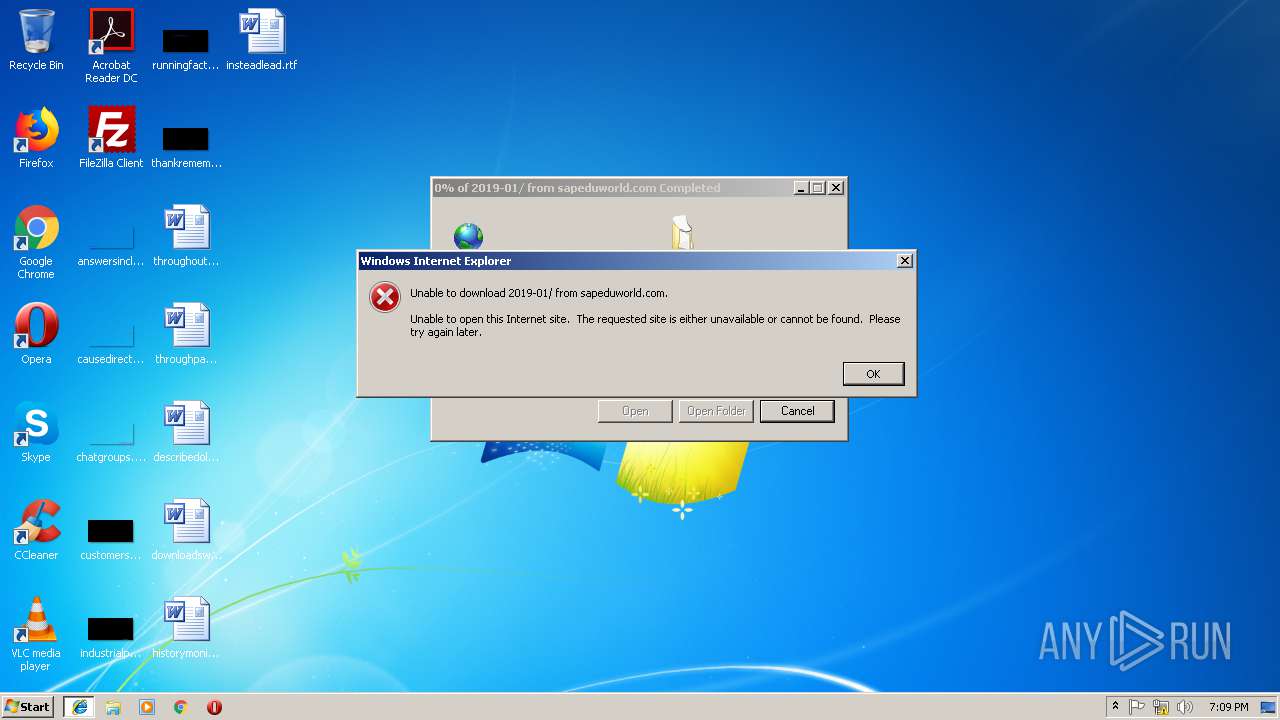
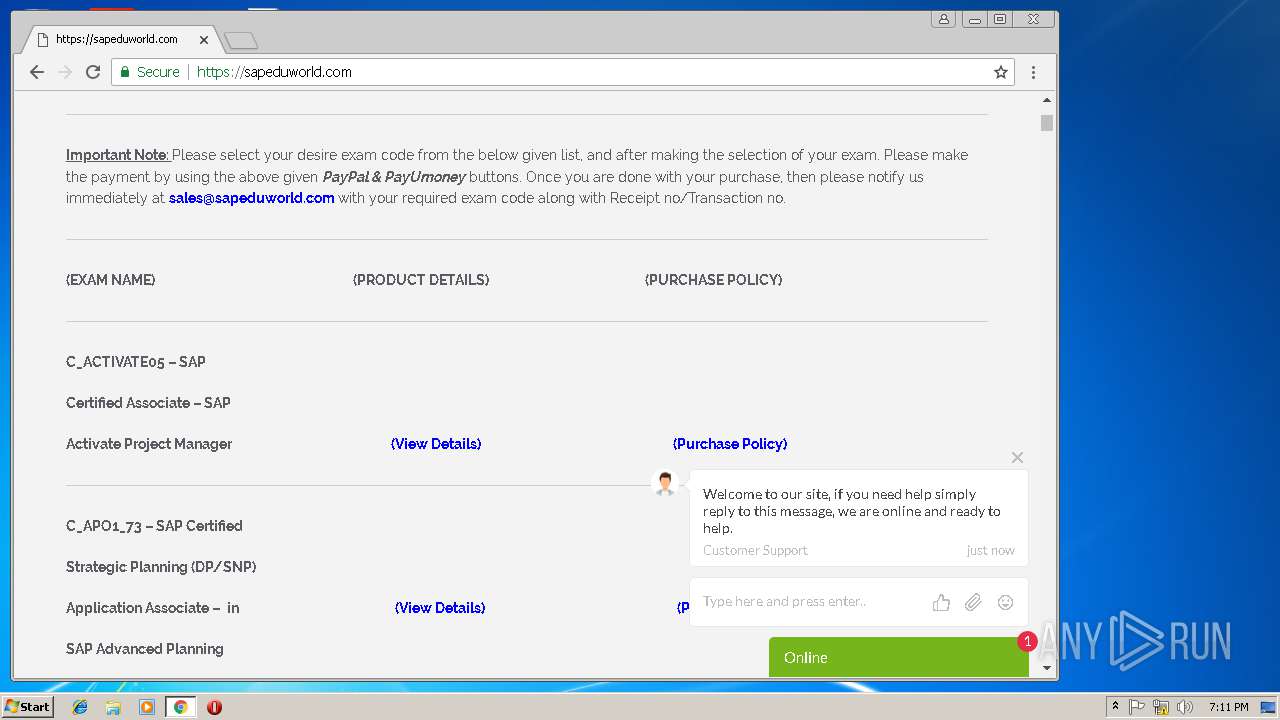
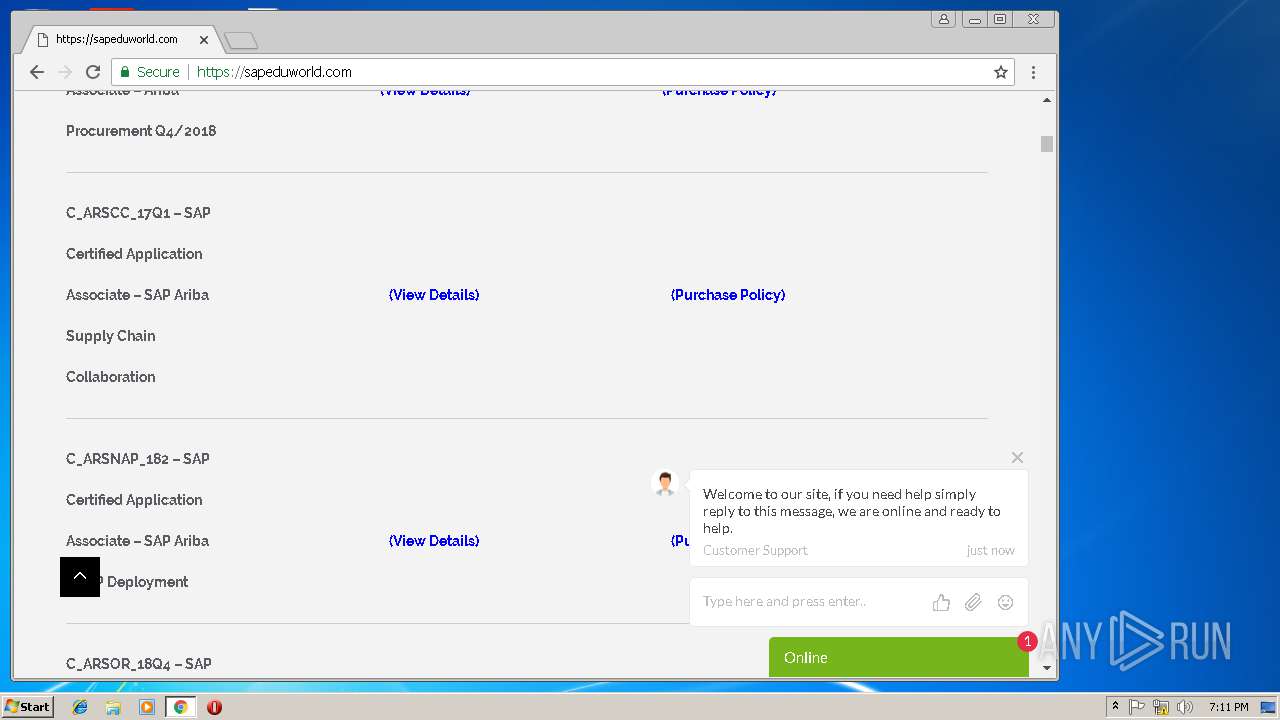
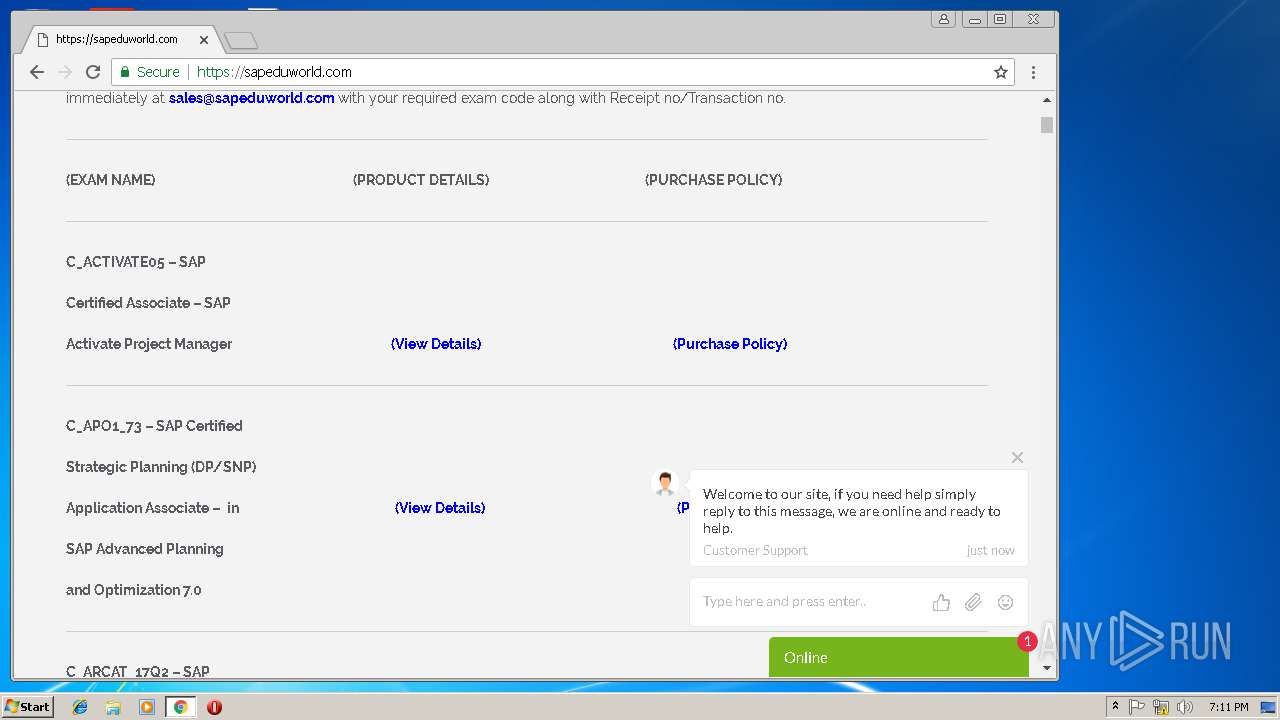
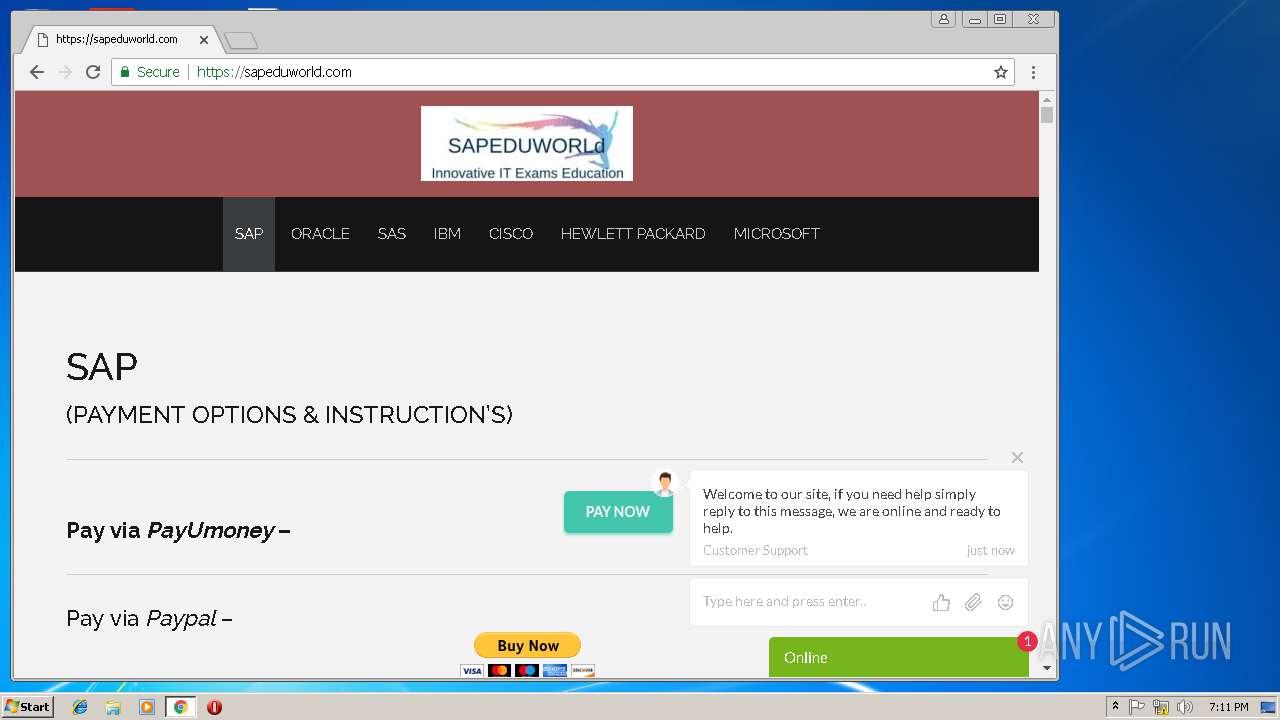
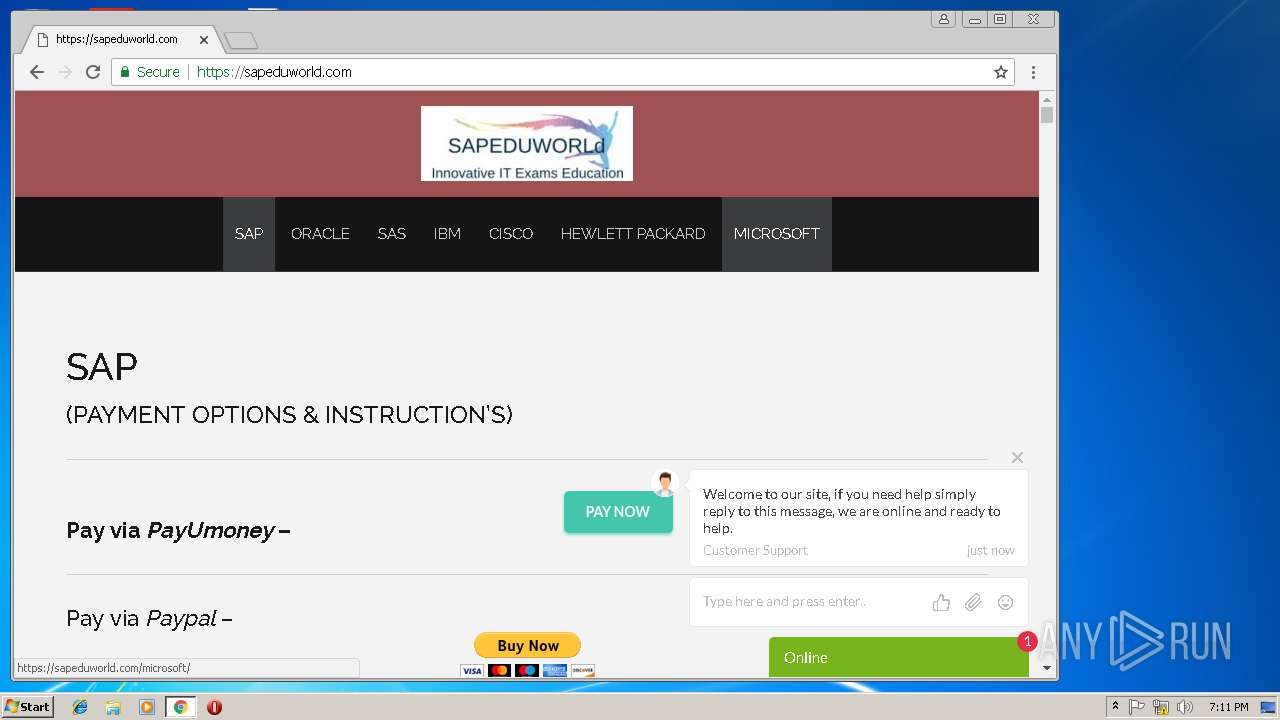
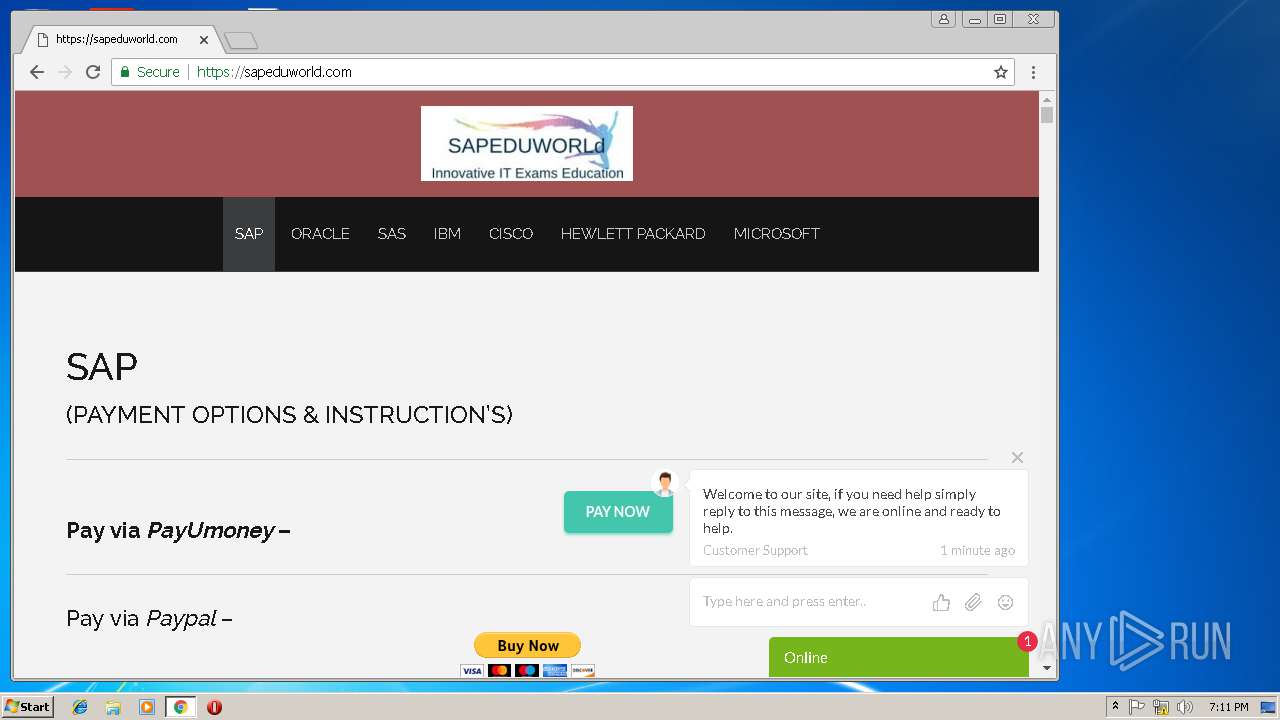
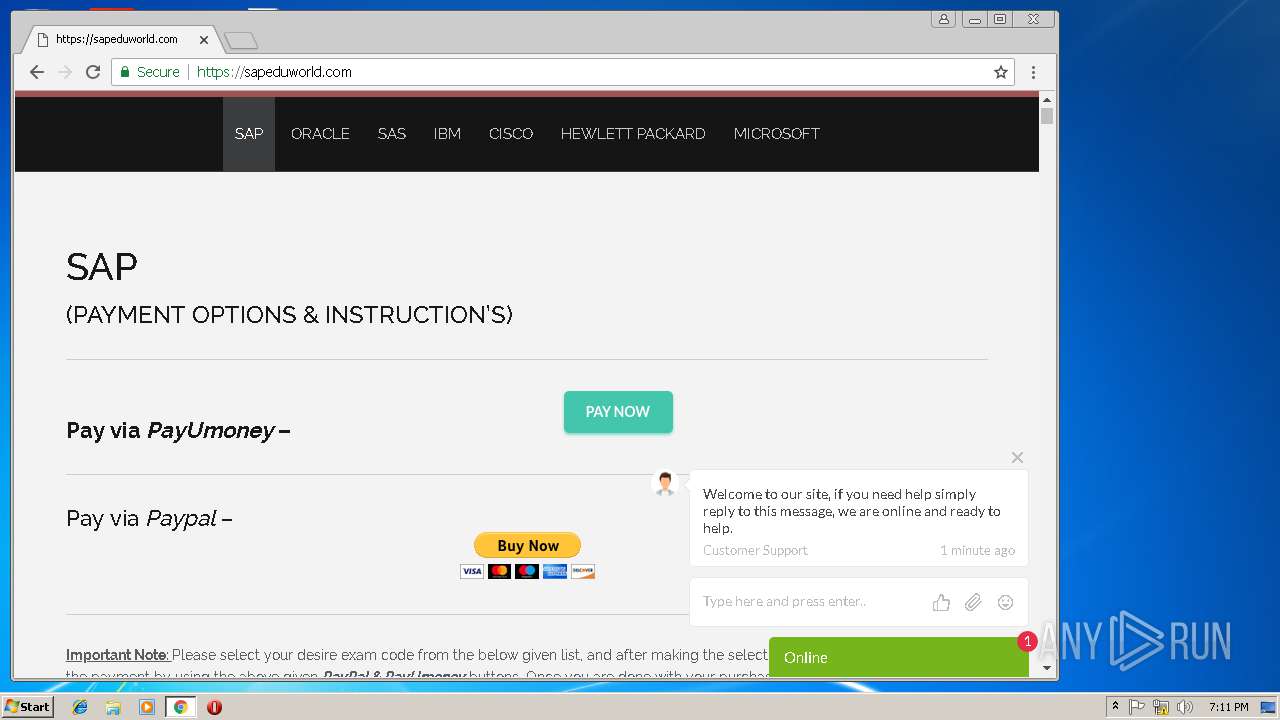
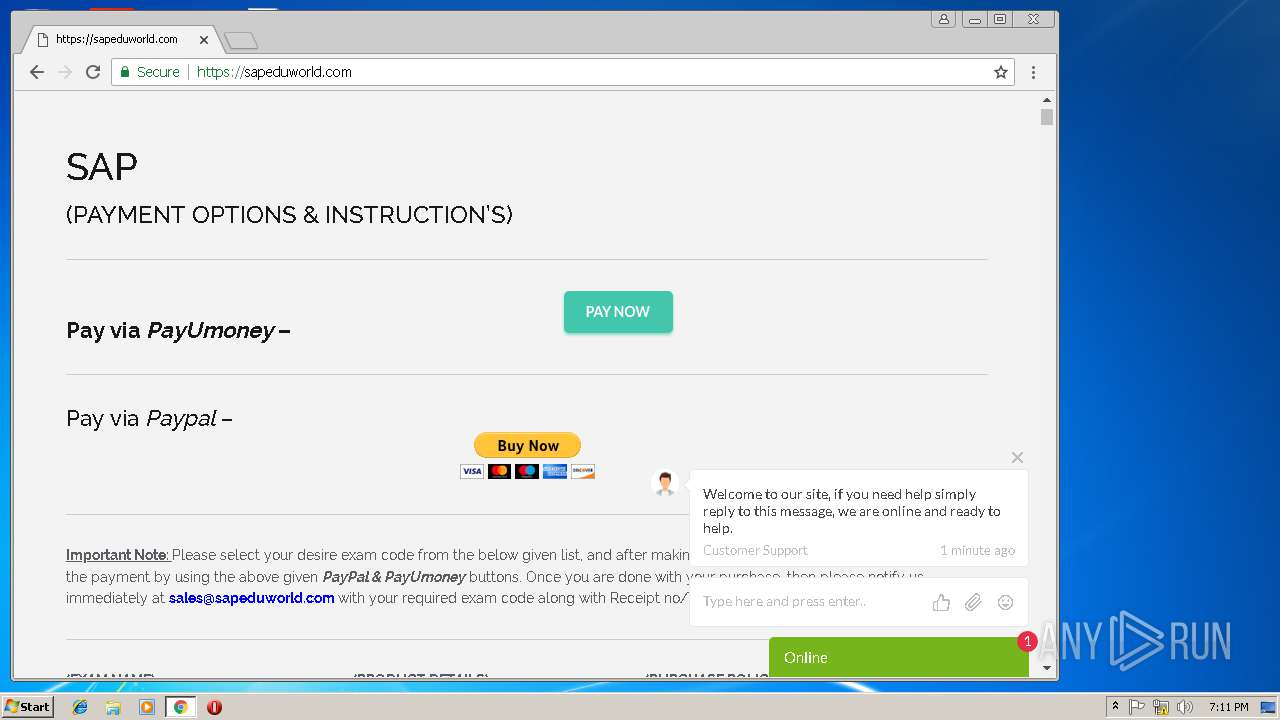
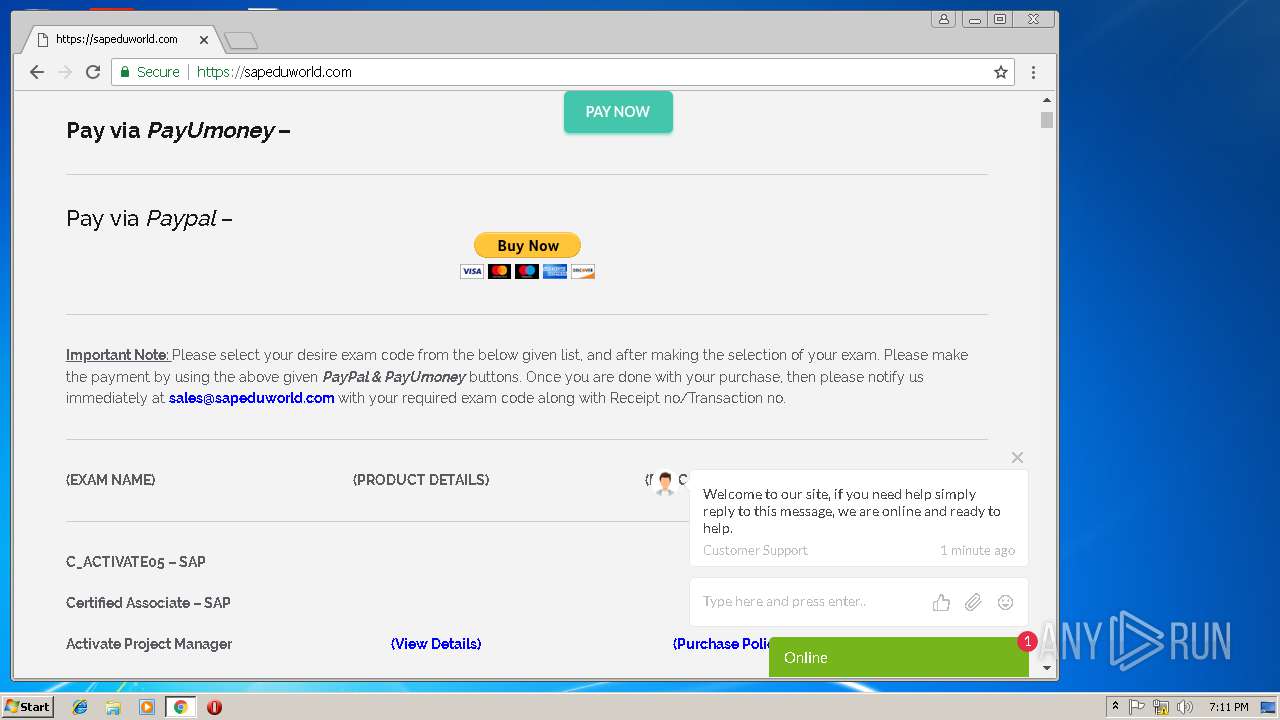
3296 | iexplore.exe | GET | 200 | 51.15.160.40:80 | http://sapeduworld.com/Clients_information/2019-01/ | FR | xml | 199 Kb | malicious |
3256 | chrome.exe | GET | 200 | 93.184.220.29:80 | http://status.geotrust.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTIyCPRUzvKHRw7iRE1lF%2BfcLu%2FjgQUypJnUmHervy6Iit%2FHIdMJftvmVgCEAUl1nAlam2BKXpyow8ex1A%3D | US | der | 471 b | whitelisted |
3296 | iexplore.exe | GET | 301 | 51.15.160.40:80 | http://sapeduworld.com/Clients_information/2019-01 | FR | html | 259 b | malicious |
3256 | chrome.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQu7Xbjq6rqggE7PFAsQRgy8Q8tzwQUkEeKG4TToN%2BkJNYZtBf1IaOym6gCEA7fr0YLsTZHJYxFeyuWNYA%3D | US | der | 471 b | whitelisted |
3256 | chrome.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTfqhLjKLEJQZPin0KCzkdAQpVYowQUsT7DaQP4v0cB1JgmGggC72NkK8MCEAx5qUSwjBGVIJJhX%2BJrHYM%3D | US | der | 471 b | whitelisted |
3256 | chrome.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTfqhLjKLEJQZPin0KCzkdAQpVYowQUsT7DaQP4v0cB1JgmGggC72NkK8MCEAP%2B7xu1tkg0miCVD4vGl1M%3D | US | der | 471 b | whitelisted |
3256 | chrome.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTfqhLjKLEJQZPin0KCzkdAQpVYowQUsT7DaQP4v0cB1JgmGggC72NkK8MCEAx5qUSwjBGVIJJhX%2BJrHYM%3D | US | der | 471 b | whitelisted |
3000 | iexplore.exe | GET | 200 | 13.107.21.200:80 | http://www.bing.com/favicon.ico | US | image | 237 b | whitelisted |
3256 | chrome.exe | GET | 200 | 91.199.212.52:80 | http://crt.comodoca.com/COMODOECCAddTrustCA.crt | GB | der | 980 b | whitelisted |
3256 | chrome.exe | GET | 301 | 51.15.160.40:80 | http://sapeduworld.com/ | FR | — | — | malicious |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3296 | iexplore.exe | 51.15.160.40:80 | sapeduworld.com | Online S.a.s. | FR | suspicious |
3256 | chrome.exe | 216.58.208.35:443 | clientservices.googleapis.com | Google Inc. | US | whitelisted |
3000 | iexplore.exe | 204.79.197.200:80 | www.bing.com | Microsoft Corporation | US | whitelisted |
3000 | iexplore.exe | 13.107.21.200:80 | www.bing.com | Microsoft Corporation | US | whitelisted |
3256 | chrome.exe | 172.217.23.163:443 | www.gstatic.com | Google Inc. | US | whitelisted |
3256 | chrome.exe | 172.217.22.42:443 | safebrowsing.googleapis.com | Google Inc. | US | whitelisted |
3256 | chrome.exe | 172.217.16.163:443 | www.google.de | Google Inc. | US | whitelisted |
3256 | chrome.exe | 172.217.18.174:443 | apis.google.com | Google Inc. | US | whitelisted |
3256 | chrome.exe | 172.217.18.100:443 | www.google.com | Google Inc. | US | whitelisted |
3256 | chrome.exe | 172.217.16.173:443 | accounts.google.com | Google Inc. | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
www.bing.com |
| whitelisted |
sapeduworld.com |
| malicious |
www.google.de |
| whitelisted |
clientservices.googleapis.com |
| whitelisted |
www.gstatic.com |
| whitelisted |
safebrowsing.googleapis.com |
| whitelisted |
accounts.google.com |
| shared |
ssl.gstatic.com |
| whitelisted |
apis.google.com |
| whitelisted |
www.google.com |
| malicious |
Threats
PID | Process | Class | Message |
|---|---|---|---|
3296 | iexplore.exe | A Network Trojan was detected | ET TROJAN Possible malicious Office doc hidden in XML file |