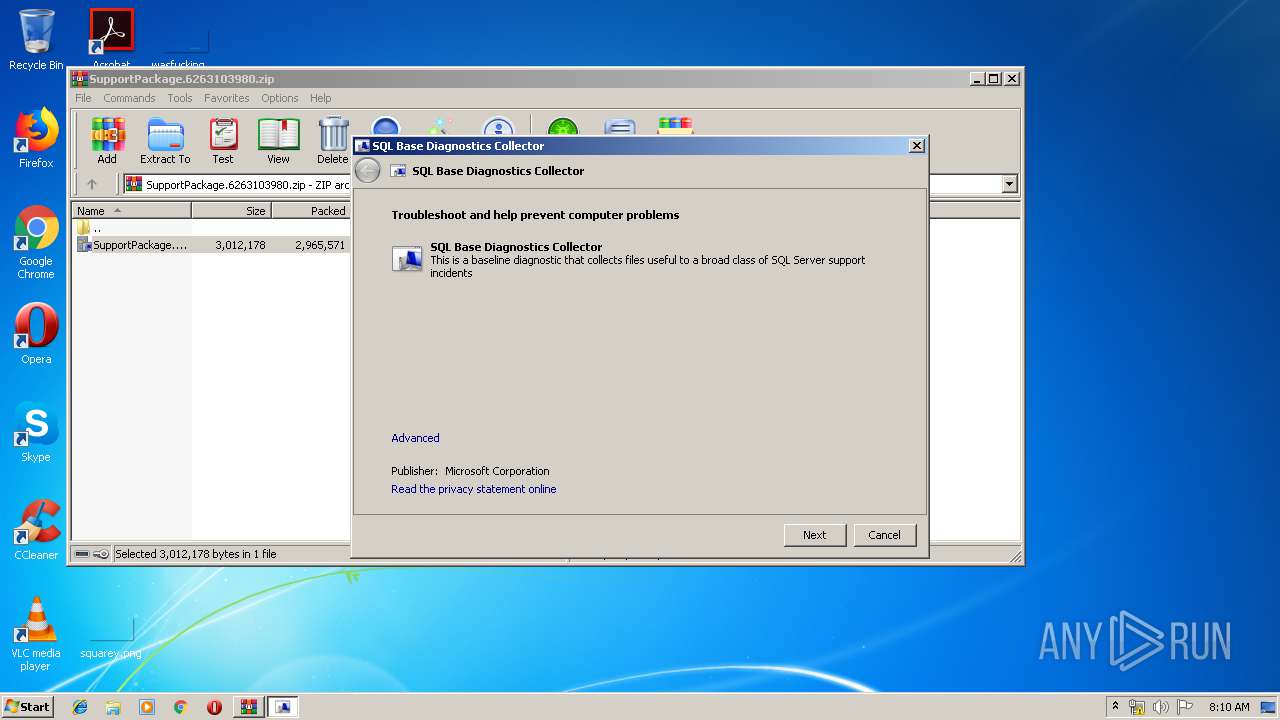
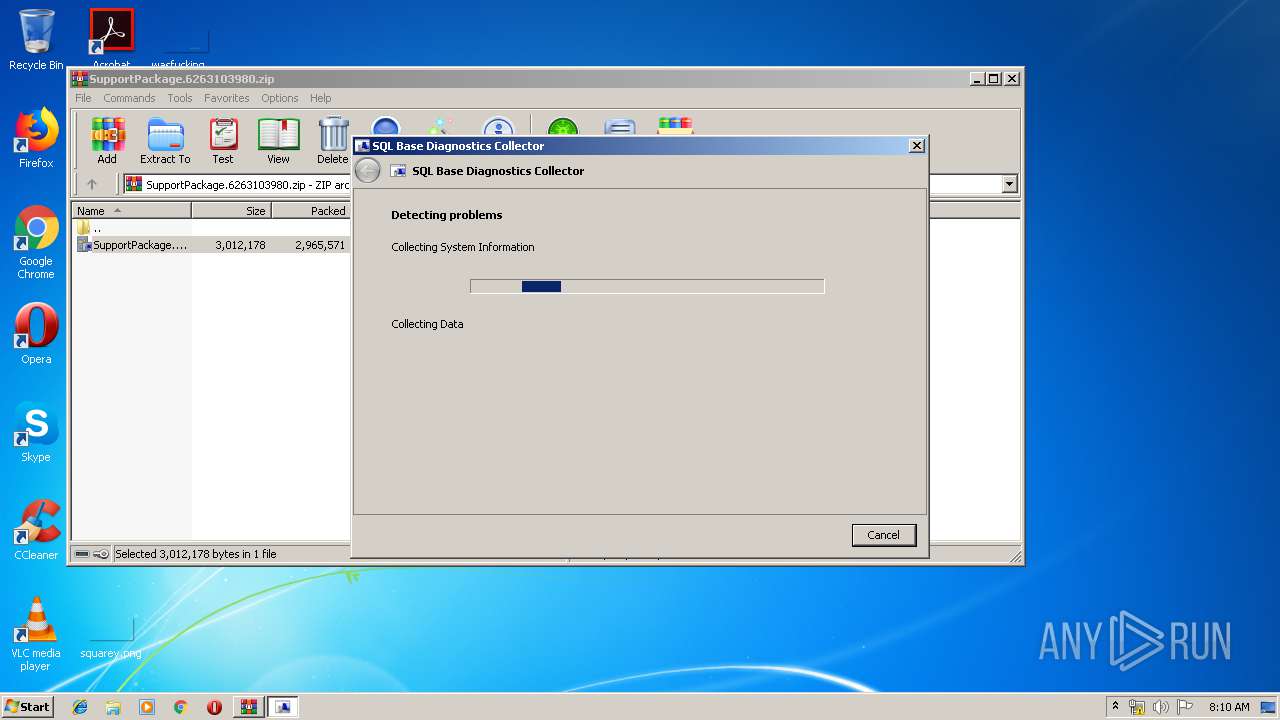
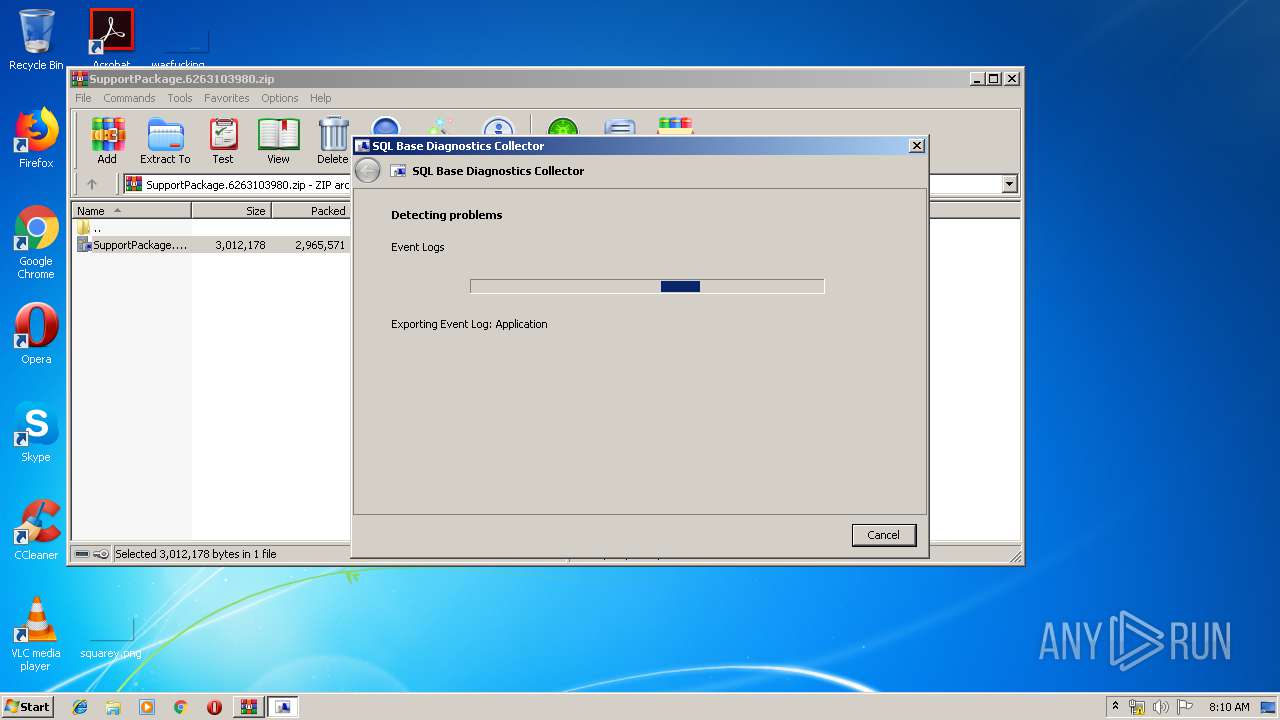
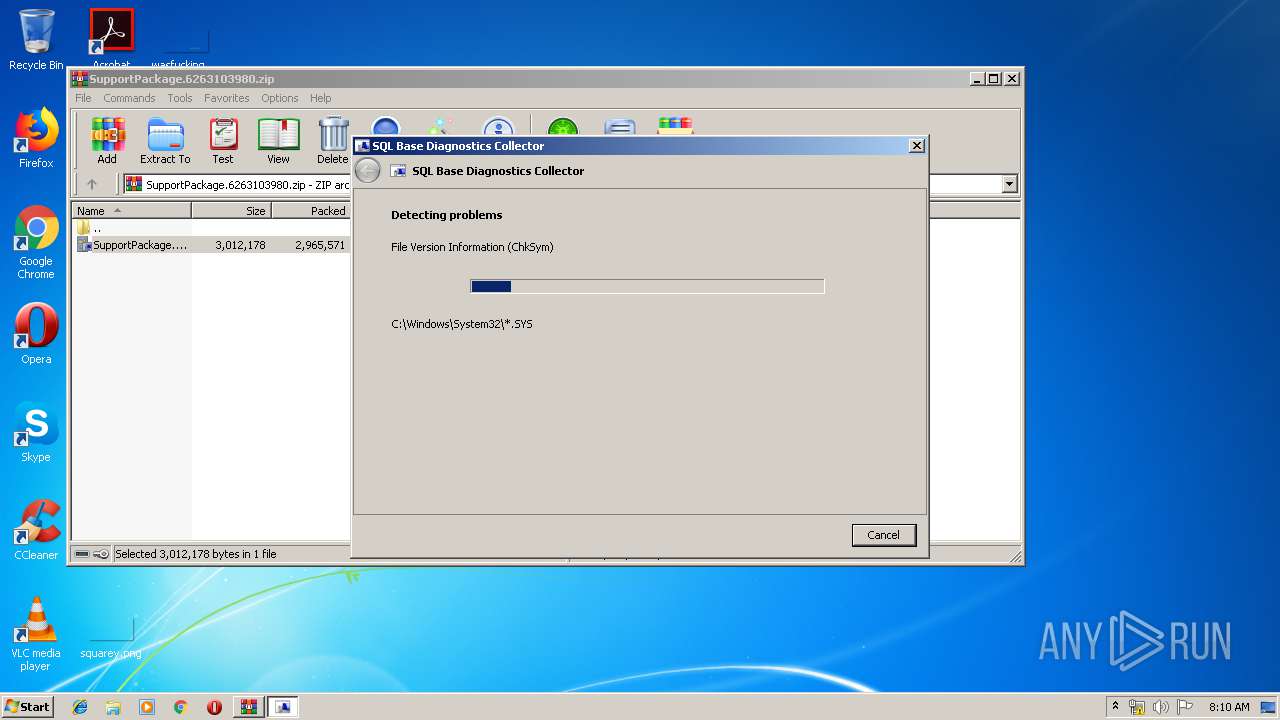
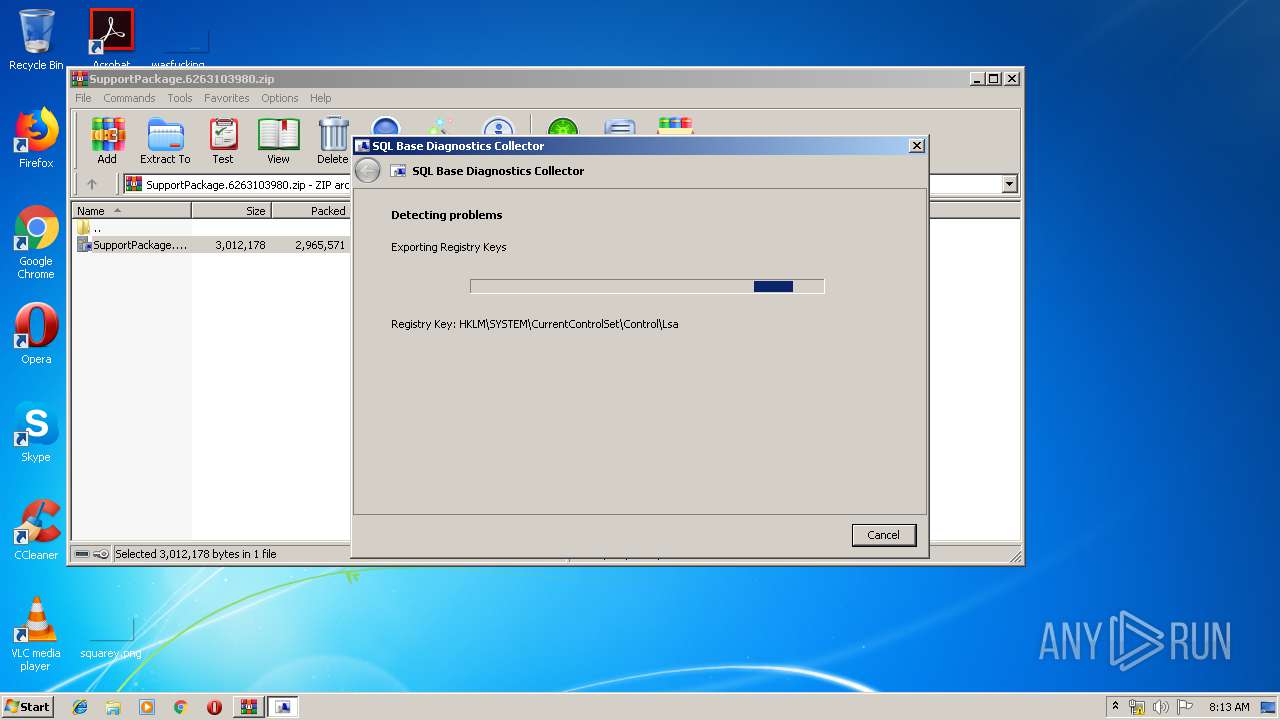
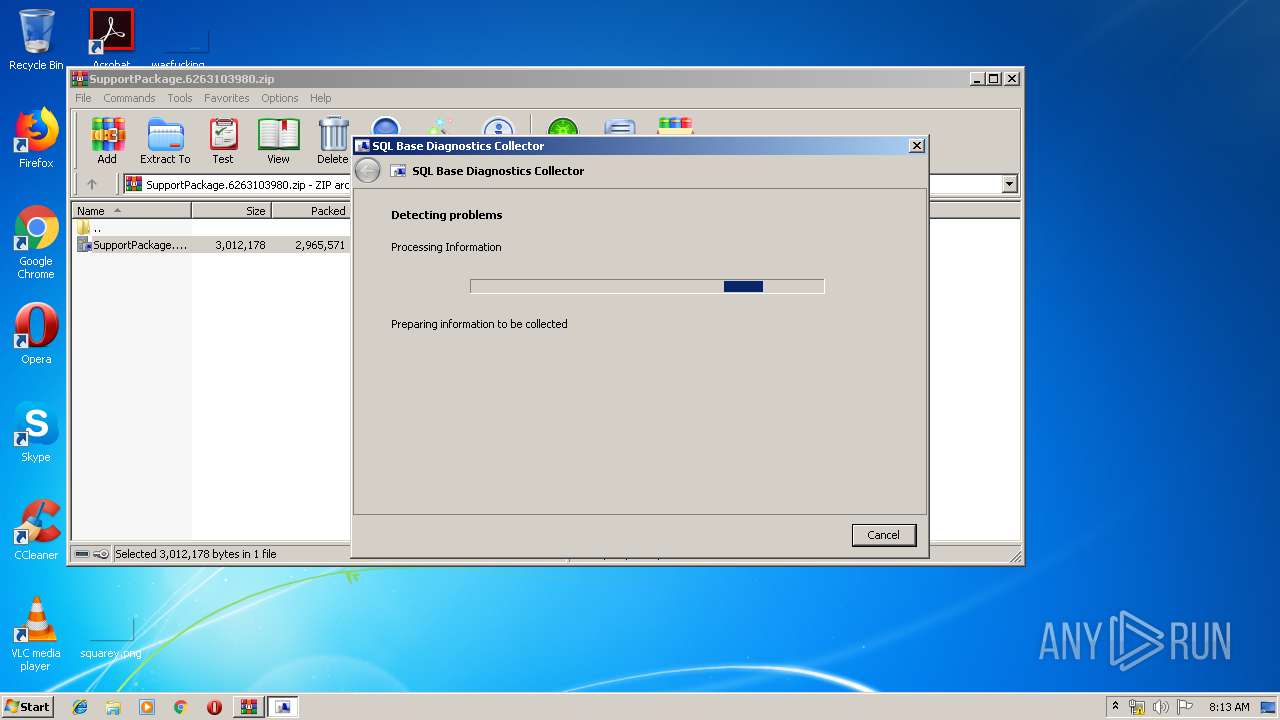
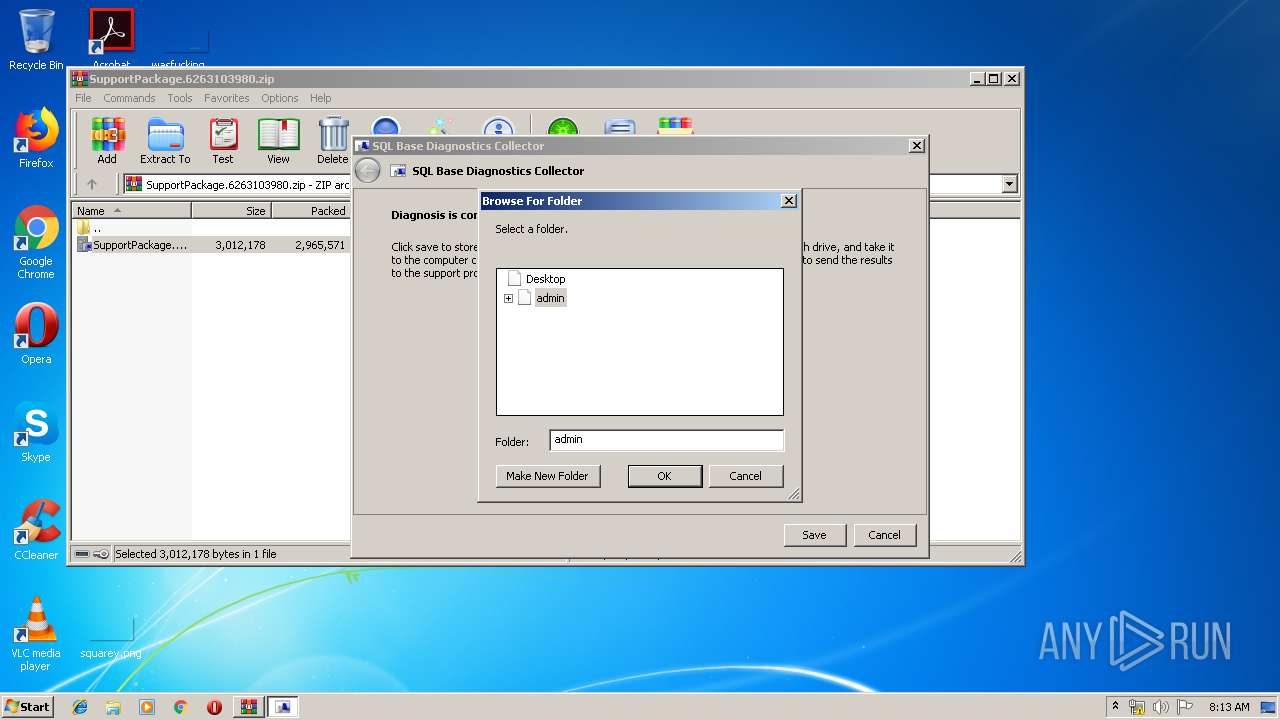
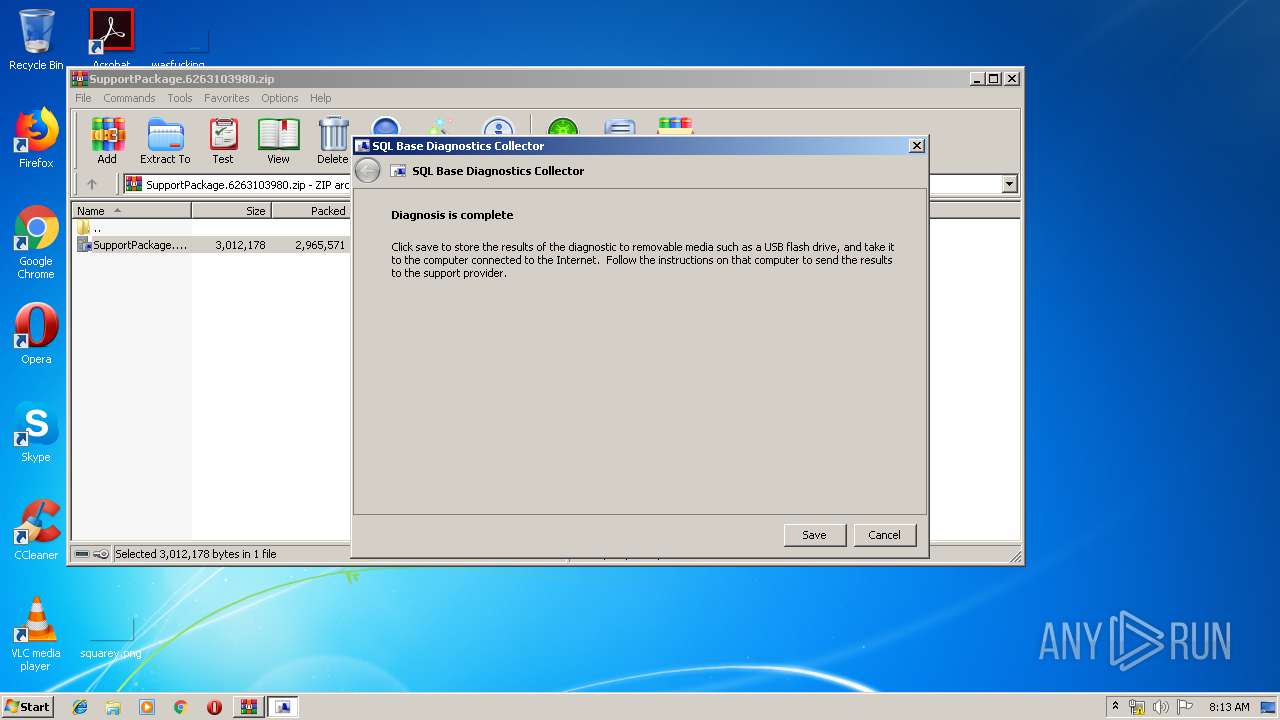
| File name: | SupportPackage.6263103980.zip |
| Full analysis: | https://app.any.run/tasks/6475a0b9-7b22-44f4-b8e9-9e7ce0c538ef |
| Verdict: | Malicious activity |
| Analysis date: | April 10, 2019, 07:09:56 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract |
| MD5: | 505285A1C72A5A749763A4C9ED3A44EA |
| SHA1: | A46536F3FD9DC557C783A924A8B703C5EF7C8EB6 |
| SHA256: | 8E74E83C017FD3E2E9C50AB958EB2D90D06890C496A3BA3850988C21BF4E3146 |
| SSDEEP: | 49152:INHfubpo7MqQ9GQc0z9DRyIZ3l0BoeXCwTgeGD9B+TN5Qksb98S3teYhyqc/LSzX:4Hf/7EpRLlCBj/Tu+TEvJ3tePqc/e3jH |
MALICIOUS
Changes settings of System certificates
- msdt.exe (PID: 3712)
- Autorunsc.exe (PID: 3876)
Application was dropped or rewritten from another process
- ChecksymX86.exe (PID: 3940)
- ChecksymX86.exe (PID: 2388)
- ChecksymX86.exe (PID: 1760)
- ChecksymX86.exe (PID: 1380)
- ChecksymX86.exe (PID: 2148)
- ChecksymX86.exe (PID: 3984)
- ChecksymX86.exe (PID: 3968)
- PstatX86.exe (PID: 3716)
- Autorunsc.exe (PID: 3876)
- fltrfind.exe (PID: 1140)
- Showpriv.exe (PID: 788)
- Showpriv.exe (PID: 2920)
- Showpriv.exe (PID: 1296)
- Showpriv.exe (PID: 3532)
- Showpriv.exe (PID: 3204)
- Showpriv.exe (PID: 3508)
- Showpriv.exe (PID: 2852)
- Showpriv.exe (PID: 2956)
- Showpriv.exe (PID: 2104)
- Showpriv.exe (PID: 3748)
- Showpriv.exe (PID: 3692)
- Showpriv.exe (PID: 4080)
- Showpriv.exe (PID: 2788)
- Showpriv.exe (PID: 2988)
- Showpriv.exe (PID: 1920)
- Showpriv.exe (PID: 2268)
- Showpriv.exe (PID: 2896)
- Showpriv.exe (PID: 2008)
- Showpriv.exe (PID: 2564)
- Showpriv.exe (PID: 3332)
- Showpriv.exe (PID: 3728)
- Showpriv.exe (PID: 2712)
- Showpriv.exe (PID: 2064)
- Showpriv.exe (PID: 4028)
- Showpriv.exe (PID: 3240)
- Showpriv.exe (PID: 3428)
- Showpriv.exe (PID: 2364)
- Showpriv.exe (PID: 2968)
- Showpriv.exe (PID: 3608)
- Showpriv.exe (PID: 2948)
- Showpriv.exe (PID: 1952)
- Showpriv.exe (PID: 988)
- Showpriv.exe (PID: 1424)
- Showpriv.exe (PID: 2464)
- Showpriv.exe (PID: 3140)
- Showpriv.exe (PID: 3520)
- Showpriv.exe (PID: 1684)
- Showpriv.exe (PID: 3708)
- Showpriv.exe (PID: 3972)
- Showpriv.exe (PID: 2720)
- Showpriv.exe (PID: 2124)
- Showpriv.exe (PID: 676)
- Showpriv.exe (PID: 2844)
- Showpriv.exe (PID: 3044)
- Showpriv.exe (PID: 2600)
Loads the Task Scheduler COM API
- ChecksymX86.exe (PID: 3984)
- schtasks.exe (PID: 3820)
- schtasks.exe (PID: 4088)
- sdiagnhost.exe (PID: 2796)
- rundll32.exe (PID: 1276)
- ChecksymX86.exe (PID: 1760)
- Autorunsc.exe (PID: 3876)
Uses Task Scheduler to run other applications
- cmd.exe (PID: 3212)
- cmd.exe (PID: 2520)
Loads the Task Scheduler DLL interface
- ChecksymX86.exe (PID: 1760)
Application was injected by another process
- svchost.exe (PID: 1224)
Runs injected code in another process
- rundll32.exe (PID: 1276)
Starts NET.EXE to view/change login properties
- cmd.exe (PID: 1296)
Starts NET.EXE to view/change shared resources
- cmd.exe (PID: 1440)
SUSPICIOUS
Executable content was dropped or overwritten
- msdt.exe (PID: 3712)
- msdt.exe (PID: 3952)
Application launched itself
- msdt.exe (PID: 3952)
Adds / modifies Windows certificates
- msdt.exe (PID: 3712)
- Autorunsc.exe (PID: 3876)
Executes PowerShell scripts
- sdiagnhost.exe (PID: 2796)
Creates files in the Windows directory
- powershell.exe (PID: 572)
- sdiagnhost.exe (PID: 2796)
- cscript.exe (PID: 4016)
- cscript.exe (PID: 3208)
- cmd.exe (PID: 1892)
- cmd.exe (PID: 392)
- cmd.exe (PID: 2408)
- msdt.exe (PID: 3712)
- cmd.exe (PID: 3956)
- cmd.exe (PID: 3216)
- ChecksymX86.exe (PID: 1380)
- ChecksymX86.exe (PID: 2148)
- cscript.exe (PID: 3640)
- ChecksymX86.exe (PID: 3940)
- ChecksymX86.exe (PID: 3968)
- cmd.exe (PID: 3212)
- ChecksymX86.exe (PID: 2388)
- CMD.EXE (PID: 2580)
- cmd.exe (PID: 2520)
- cmd.exe (PID: 300)
- cmd.exe (PID: 2696)
- ChecksymX86.exe (PID: 3984)
- rundll32.exe (PID: 1276)
- ChecksymX86.exe (PID: 1760)
- cscript.exe (PID: 1404)
- tracerpt.exe (PID: 4072)
- cmd.exe (PID: 3692)
- gpresult.exe (PID: 3724)
- netsh.exe (PID: 1356)
- netsh.exe (PID: 2568)
- netsh.exe (PID: 2708)
- cscript.exe (PID: 324)
- netsh.exe (PID: 1076)
- netsh.exe (PID: 728)
- netsh.exe (PID: 3800)
- reg.exe (PID: 1492)
Creates files in the user directory
- powershell.exe (PID: 572)
Starts CMD.EXE for commands execution
- cscript.exe (PID: 4016)
- cscript.exe (PID: 3208)
- sdiagnhost.exe (PID: 2796)
- cscript.exe (PID: 1404)
- cscript.exe (PID: 3328)
- cscript.exe (PID: 3752)
- cscript.exe (PID: 324)
- cscript.exe (PID: 3732)
Executes scripts
- sdiagnhost.exe (PID: 2796)
Removes files from Windows directory
- sdiagnhost.exe (PID: 2796)
- rundll32.exe (PID: 1276)
- tracerpt.exe (PID: 4072)
- reg.exe (PID: 1492)
- msdt.exe (PID: 3712)
Uses NETSH.EXE for network configuration
- cmd.exe (PID: 1828)
- cmd.exe (PID: 3576)
- cmd.exe (PID: 3788)
- cmd.exe (PID: 3324)
- cmd.exe (PID: 1896)
- cmd.exe (PID: 2856)
- cmd.exe (PID: 996)
- cmd.exe (PID: 1752)
- cmd.exe (PID: 1784)
- cmd.exe (PID: 2348)
- cmd.exe (PID: 2840)
- cmd.exe (PID: 344)
- cmd.exe (PID: 408)
- cmd.exe (PID: 2404)
- cmd.exe (PID: 288)
- cmd.exe (PID: 2152)
- cmd.exe (PID: 308)
- cmd.exe (PID: 2008)
- cmd.exe (PID: 788)
- sdiagnhost.exe (PID: 2796)
- cmd.exe (PID: 1136)
Uses NETSTAT.EXE to discover network connections
- cmd.exe (PID: 2080)
- cmd.exe (PID: 2148)
- cmd.exe (PID: 2572)
- cmd.exe (PID: 2056)
Uses TASKLIST.EXE to query information about running processes
- sdiagnhost.exe (PID: 2796)
Starts SC.EXE for service management
- cmd.exe (PID: 2636)
Uses SYSTEMINFO.EXE to read environment
- cmd.exe (PID: 2140)
Low-level read access rights to disk partition
- bcdedit.exe (PID: 3448)
- bcdedit.exe (PID: 3160)
- bcdedit.exe (PID: 3424)
Uses REG.EXE to modify Windows registry
- cmd.exe (PID: 2964)
- cmd.exe (PID: 2400)
- cmd.exe (PID: 4080)
- cmd.exe (PID: 3004)
- cmd.exe (PID: 3532)
- cmd.exe (PID: 1452)
- cmd.exe (PID: 764)
- cmd.exe (PID: 1752)
- cmd.exe (PID: 3160)
- cmd.exe (PID: 2144)
- cmd.exe (PID: 1864)
- cmd.exe (PID: 1664)
- cmd.exe (PID: 3100)
- cmd.exe (PID: 3432)
- cmd.exe (PID: 3172)
- cmd.exe (PID: 3660)
- cmd.exe (PID: 2884)
- cmd.exe (PID: 1704)
- sdiagnhost.exe (PID: 2796)
- cmd.exe (PID: 2760)
Uses IPCONFIG.EXE to discover IP address
- cmd.exe (PID: 2488)
- cmd.exe (PID: 2748)
INFO
Dropped object may contain Bitcoin addresses
- msdt.exe (PID: 3952)
- msdt.exe (PID: 3712)
Low-level read access rights to disk partition
- vssvc.exe (PID: 768)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2018:09:03 09:55:12 |
| ZipCRC: | 0x816e32c7 |
| ZipCompressedSize: | 2965571 |
| ZipUncompressedSize: | 3012178 |
| ZipFileName: | SupportPackage.6263103980.diagcab |
Total processes
320
Monitored processes
276
Malicious processes
13
Suspicious processes
17
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 276 | "C:\Windows\system32\cmd.exe" /c Fltmc.exe Filters | C:\Windows\system32\cmd.exe | — | sdiagnhost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 288 | "C:\Windows\system32\cmd.exe" /c netsh.exe advfirewall monitor show consec verbose | C:\Windows\system32\cmd.exe | — | sdiagnhost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 1 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 296 | netsh.exe advfirewall consec show rule all any static verbose | C:\Windows\system32\netsh.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Network Command Shell Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 300 | "cmd.exe" /c FltrFind.exe > USER-PC_FltrFind.txt | C:\Windows\System32\cmd.exe | — | sdiagnhost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 308 | "C:\Windows\system32\cmd.exe" /c netsh.exe wfp show options optionsfor=netevents | C:\Windows\system32\cmd.exe | — | sdiagnhost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 324 | "C:\Windows\system32\cscript.exe" //E:vbscript GetEvents.VBS "Microsoft-Windows-Windows Firewall With Advanced Security/Firewall" /channel /TXT /CSV /evtx /evt C:\Windows\TEMP\SDIAG_da99e268-7a54-44f7-895b-c9ddd499a19a\EventLogs /noextended /prefix:USER-PC_evt_ /suffix:_evt_ | C:\Windows\system32\cscript.exe | — | sdiagnhost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft ® Console Based Script Host Exit code: 0 Version: 5.8.7600.16385 Modules
| |||||||||||||||
| 344 | "C:\Windows\system32\cmd.exe" /c netsh.exe advfirewall show publicprofile | C:\Windows\system32\cmd.exe | — | sdiagnhost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 388 | reg.exe query "HKLM\SYSTEM\CurrentControlSet\Services\MpsSvc" /s | C:\Windows\system32\reg.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Registry Console Tool Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 392 | "cmd.exe" /c Checksymx86.exe -F "C:\Windows\System32\*.EXE;" -R -S -O2 "USER-PC_sym_System32_EXE.CSV" > "USER-PC_sym_System32_EXE.TXT" | C:\Windows\System32\cmd.exe | — | sdiagnhost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 408 | "C:\Windows\system32\cmd.exe" /c netsh.exe advfirewall show store | C:\Windows\system32\cmd.exe | — | sdiagnhost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
Total events
5 333
Read events
3 490
Write events
1 834
Delete events
9
Modification events
| (PID) Process: | (3388) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (3388) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (3388) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\62\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3388) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\SupportPackage.6263103980.zip | |||
| (PID) Process: | (3388) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (3388) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (3388) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (3388) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (3388) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\62\52C64B7E |
| Operation: | write | Name: | @C:\Windows\system32\msdt.exe,-10012 |
Value: Troubleshooting Pack Cabinet | |||
| (PID) Process: | (3952) msdt.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\62\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
Executable files
52
Suspicious files
17
Text files
3 238
Unknown types
50
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3952 | msdt.exe | C:\Users\admin\AppData\Local\Temp\msdt\_27B4A713-3AD1-4D34-9878-4DA9008AB289_\cabpkg\Package_0\Autoruns.vbs | text | |
MD5:13A797E90810F1B6C1B97D44AD248428 | SHA256:AB96E5A2994B1630EE8E95CE521054A72DD080D9A9A26B0CC8A6D301E5628ECC | |||
| 3952 | msdt.exe | C:\Users\admin\AppData\Local\Temp\msdt\_27B4A713-3AD1-4D34-9878-4DA9008AB289_\cabpkg\Package_0\Autorunsc.exe | executable | |
MD5:07A5B1FD29084D54B0B0AFBAF1F37187 | SHA256:86D2C5F48A671CBBFDA4C51C516A9A866D148F2854DB33AFDBB4CB83C0D833B3 | |||
| 3388 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DIa3388.23259\SupportPackage.6263103980.diagcab | compressed | |
MD5:58635119FBA98FD29C681853D124332D | SHA256:971728A68F875A8F8869B9F1F8990DA230368EF4ACF2E26DFCAF3CACA6C877AB | |||
| 3952 | msdt.exe | C:\Users\admin\AppData\Local\Temp\msdt\_27B4A713-3AD1-4D34-9878-4DA9008AB289_\cabpkg\Package_0\ConfigXPLSchema.xml | xml | |
MD5:19BFC27690306A484E50D44C9F3252E0 | SHA256:89BCC5518BC537BEB771AB724BE97FE63DEE78E7A2273EA48B9B0EB4D4272212 | |||
| 3952 | msdt.exe | C:\Users\admin\AppData\Local\Temp\msdt\_27B4A713-3AD1-4D34-9878-4DA9008AB289_\cabpkg\Package_0\ConfigExplorerClientView.xslt | xml | |
MD5:D6F8B2D91E1316A5A31C57687C957FE1 | SHA256:9ABBFCEF90CFA62AF1FAFF8CEB9ECDF1502327C6D1CE5E4F639335E9E1F8EF7B | |||
| 3952 | msdt.exe | C:\Users\admin\AppData\Local\Temp\msdt\_27B4A713-3AD1-4D34-9878-4DA9008AB289_\cabpkg\Package_0\clusmps.exe | executable | |
MD5:F35C648EDD1245C561AA4885A4599A34 | SHA256:25E4A75F21EEB1E1E4FA3FDBC6E45FFFB2FDA7B669BA6AFA8AB1CA0E15B59ACC | |||
| 3952 | msdt.exe | C:\Users\admin\AppData\Local\Temp\msdt\_27B4A713-3AD1-4D34-9878-4DA9008AB289_\cabpkg\Package_0\DC_BCDInfo.ps1 | text | |
MD5:4037A0716CC227F21F052145D8A84FCB | SHA256:B3D2867B12FD1E0C49EE716722B2445FE70D3C7C4CEF1D0D4CDF492C8DD19820 | |||
| 3952 | msdt.exe | C:\Users\admin\AppData\Local\Temp\msdt\_27B4A713-3AD1-4D34-9878-4DA9008AB289_\cabpkg\Package_0\DC_Autoruns.psd1 | text | |
MD5:22F0108BDBBA26DDAEC2BDBF9AF708F1 | SHA256:A0123A7F75539898BE2ED4CDA095611C2651C334BC8086D87E76EAA03D842042 | |||
| 3952 | msdt.exe | C:\Users\admin\AppData\Local\Temp\msdt\_27B4A713-3AD1-4D34-9878-4DA9008AB289_\cabpkg\Package_0\dbgeng.dll | executable | |
MD5:7E3C64CEADD26EA4764525DCC8943AC7 | SHA256:83F7F92F20C7AFF57DC3FADC3246E0747BA1BF810414D7713254A3514C72376E | |||
| 3952 | msdt.exe | C:\Users\admin\AppData\Local\Temp\msdt\_27B4A713-3AD1-4D34-9878-4DA9008AB289_\cabpkg\Package_0\DC_Autoruns.ps1 | text | |
MD5:07B265BA925F9672FD44FA3FC10498DA | SHA256:7DC79DE4C39E3F010321FB3D8CF10D69C0918AB9DCBCDF7F59F070F7B3B4A3AD | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
2
TCP/UDP connections
2
DNS requests
2
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3876 | Autorunsc.exe | GET | 200 | 91.199.212.52:80 | http://crt.comodoca.com/COMODORSAAddTrustCA.crt | GB | der | 1.37 Kb | whitelisted |
3876 | Autorunsc.exe | GET | 200 | 205.185.216.10:80 | http://www.download.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authrootstl.cab | US | compressed | 55.6 Kb | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3876 | Autorunsc.exe | 205.185.216.10:80 | www.download.windowsupdate.com | Highwinds Network Group, Inc. | US | whitelisted |
3876 | Autorunsc.exe | 91.199.212.52:80 | crt.comodoca.com | Comodo CA Ltd | GB | suspicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
www.download.windowsupdate.com |
| whitelisted |
crt.comodoca.com |
| whitelisted |