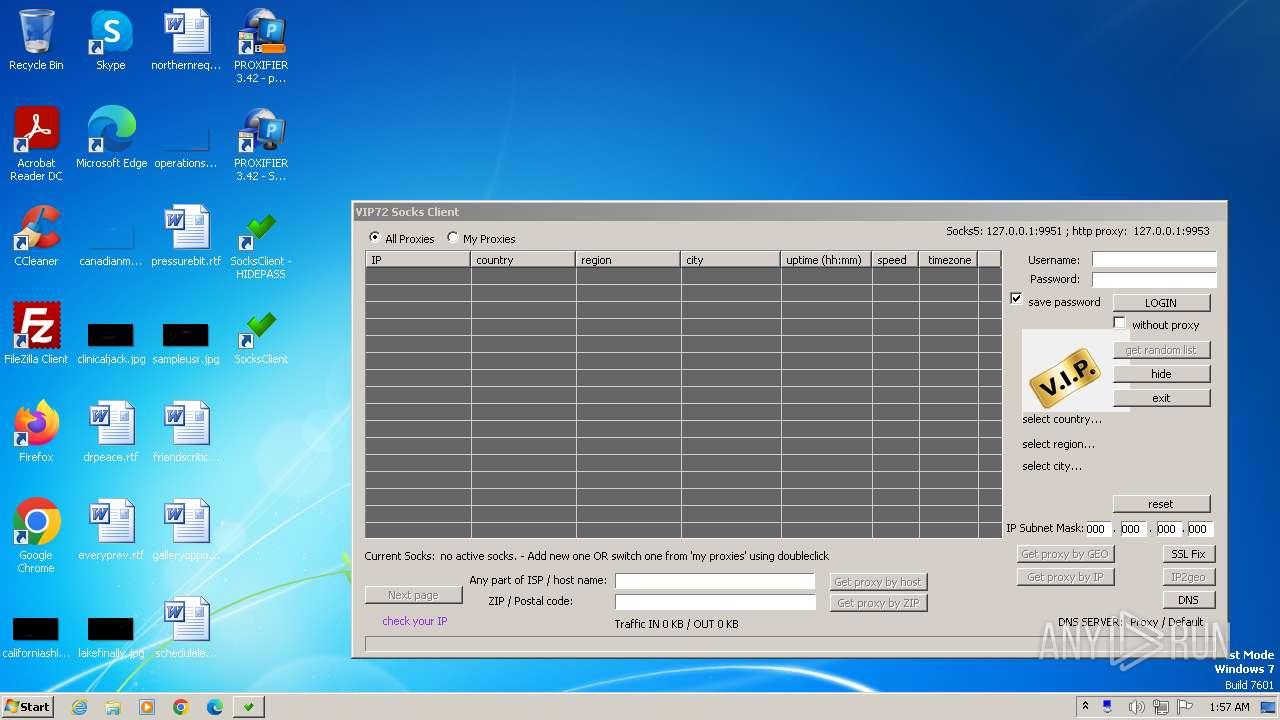
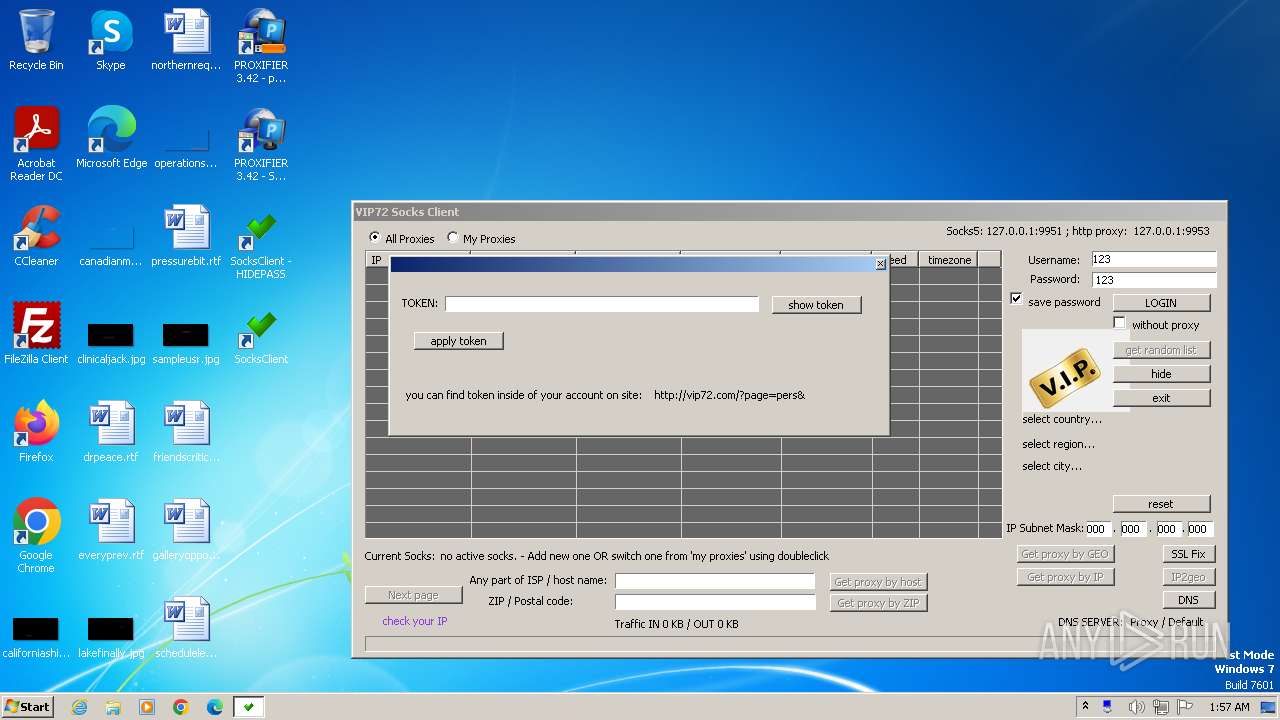
| File name: | vip72socks-set-x5.exe |
| Full analysis: | https://app.any.run/tasks/964e188c-fd61-462f-a7cd-2820239afb40 |
| Verdict: | Malicious activity |
| Analysis date: | November 29, 2023, 01:56:31 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows |
| MD5: | C26C8DB0A4C41D0C5E729E145F597F58 |
| SHA1: | 9C600B2D4FC5BAF3D88FCE713EF01F456C5AA25B |
| SHA256: | 8E704BE5B85D219A9AFF3FD493D00D287DBB55AAE4D2DF530AA361E04723716A |
| SSDEEP: | 98304:bmpyFPPEw6SDVAXxnLjfiiQe+IDYDdH/sRvdGi3h7qnn22jWW7IZi1ESaOP5kmGN:wT/xGYEq0odTZ |
MALICIOUS
Drops the executable file immediately after the start
- vip72socks-set-x5.exe (PID: 2692)
- vip72socks-set-x5.exe (PID: 2232)
- vip72socks-set-x5.tmp (PID: 1444)
Creates a writable file in the system directory
- vip72socks-set-x5.tmp (PID: 1444)
Actions looks like stealing of personal data
- vip72socks.exe (PID: 580)
Steals credentials from Web Browsers
- vip72socks.exe (PID: 580)
SUSPICIOUS
Reads the Windows owner or organization settings
- vip72socks-set-x5.tmp (PID: 1444)
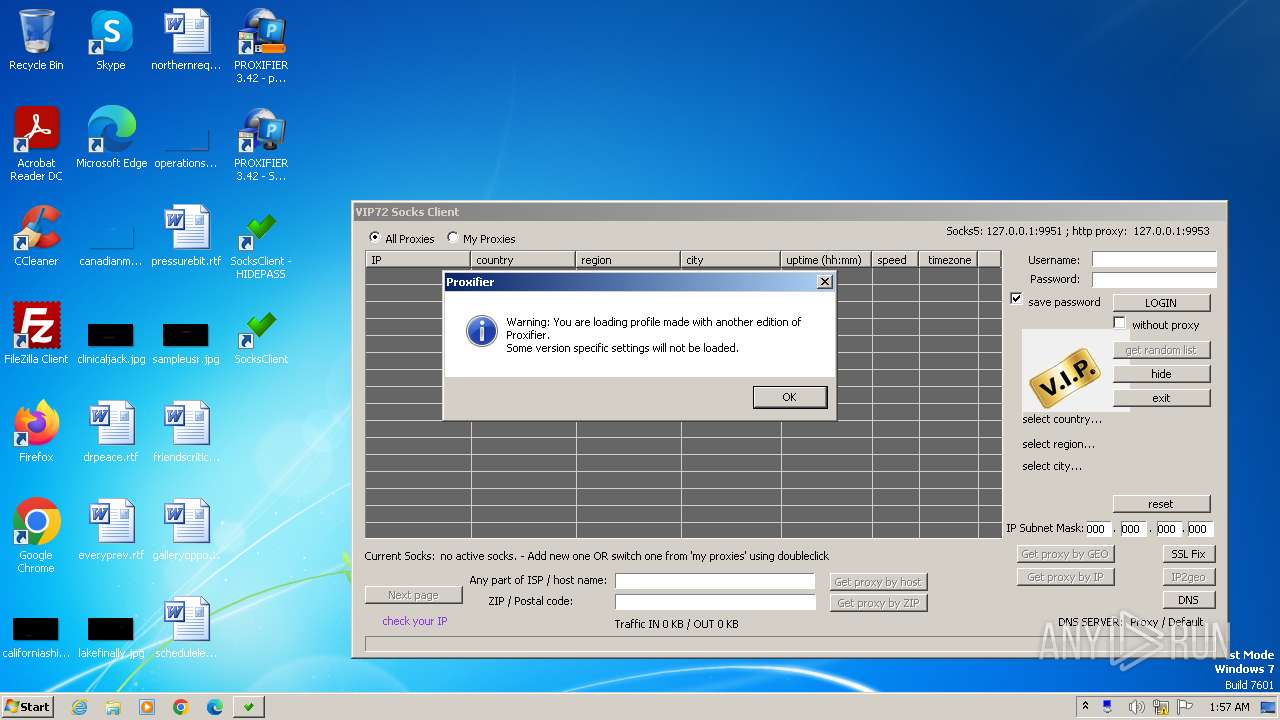
Process drops legitimate windows executable
- vip72socks-set-x5.tmp (PID: 1444)
Reads the Internet Settings
- Proxifier.exe (PID: 3380)
INFO
Checks supported languages
- vip72socks-set-x5.exe (PID: 2692)
- vip72socks-set-x5.tmp (PID: 3060)
- vip72socks-set-x5.exe (PID: 2232)
- vip72socks-set-x5.tmp (PID: 1444)
- SysSettings32.exe (PID: 924)
- vip72socks.exe (PID: 580)
- Proxifier.exe (PID: 3380)
- wmpnscfg.exe (PID: 3924)
- vip72socks.exe (PID: 944)
- SysSettings32.exe (PID: 1660)
Create files in a temporary directory
- vip72socks-set-x5.exe (PID: 2232)
- vip72socks-set-x5.exe (PID: 2692)
- Proxifier.exe (PID: 3380)
Reads the computer name
- vip72socks-set-x5.tmp (PID: 3060)
- vip72socks-set-x5.tmp (PID: 1444)
- Proxifier.exe (PID: 3380)
- vip72socks.exe (PID: 580)
- wmpnscfg.exe (PID: 3924)
Creates files or folders in the user directory
- vip72socks-set-x5.tmp (PID: 1444)
- vip72socks.exe (PID: 580)
Creates files in the program directory
- vip72socks-set-x5.tmp (PID: 1444)
Manual execution by a user
- vip72socks.exe (PID: 580)
- vip72socks.exe (PID: 944)
- Proxifier.exe (PID: 3380)
- wmpnscfg.exe (PID: 3924)
Reads the machine GUID from the registry
- Proxifier.exe (PID: 3380)
- wmpnscfg.exe (PID: 3924)
Checks proxy server information
- Proxifier.exe (PID: 3380)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Inno Setup installer (77.7) |
|---|---|---|
| .exe | | | Win32 Executable Delphi generic (10) |
| .dll | | | Win32 Dynamic Link Library (generic) (4.6) |
| .exe | | | Win32 Executable (generic) (3.1) |
| .exe | | | Win16/32 Executable Delphi generic (1.4) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 1992:06:20 00:22:17+02:00 |
| ImageFileCharacteristics: | No relocs, Executable, No line numbers, No symbols, Bytes reversed lo, 32-bit, Bytes reversed hi |
| PEType: | PE32 |
| LinkerVersion: | 2.25 |
| CodeSize: | 41984 |
| InitializedDataSize: | 17920 |
| UninitializedDataSize: | - |
| EntryPoint: | 0xaad0 |
| OSVersion: | 1 |
| ImageVersion: | 6 |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 1.8.7.14 |
| ProductVersionNumber: | 1.8.7.14 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | Neutral |
| CharacterSet: | Unicode |
| Comments: | This installation was built with Inno Setup. |
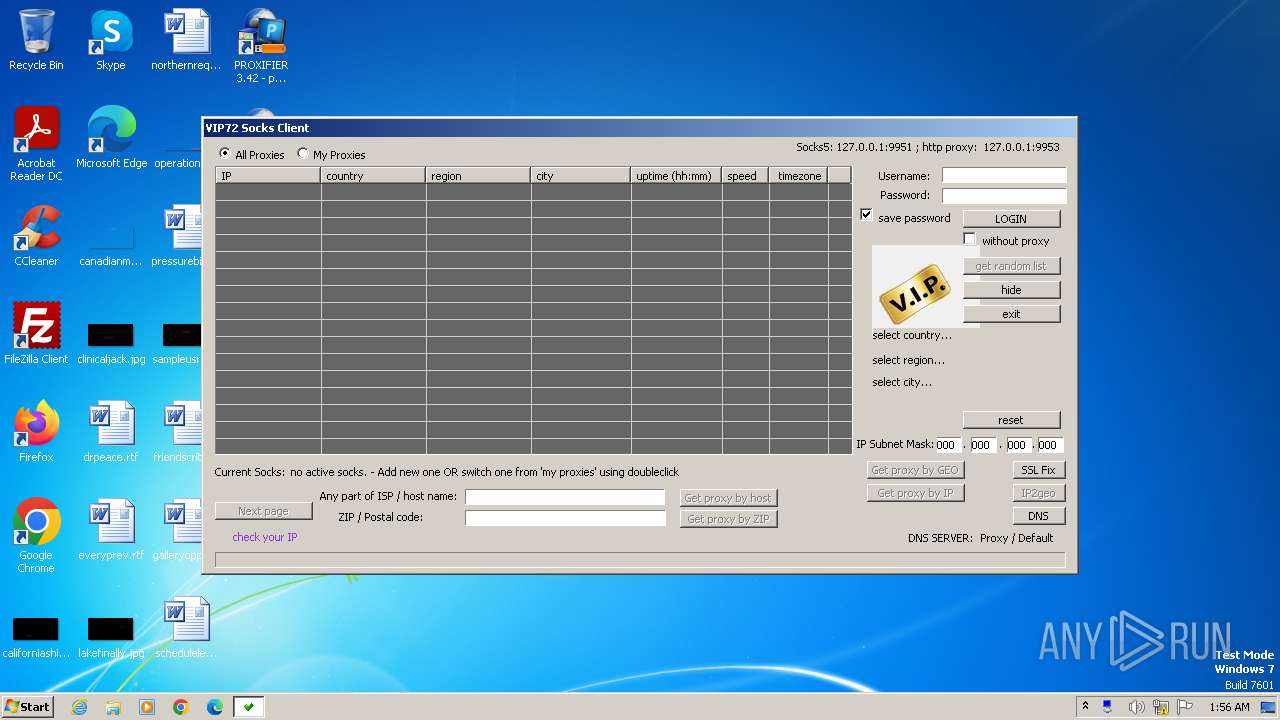
| CompanyName: | VIP Technologies |
| FileDescription: | VIP72 Socks Client Setup |
| FileVersion: | 1.8.7.14 |
| LegalCopyright: | |
| ProductName: | VIP72 Socks Client |
| ProductVersion: | 1.8.7.14 |
Total processes
50
Monitored processes
10
Malicious processes
4
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 580 | "C:\Users\admin\AppData\Roaming\VIP72 Socks Client\vip72socks.exe" | C:\Users\admin\AppData\Roaming\VIP72 Socks Client\vip72socks.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 924 | "C:\Users\admin\AppData\Roaming\VIP72 Socks Client\proxifier-standart\SysSettings32.exe" silent-install | C:\Users\admin\AppData\Roaming\VIP72 Socks Client\proxifier-standart\SysSettings32.exe | — | vip72socks-set-x5.tmp | |||||||||||
User: admin Company: Initex Integrity Level: HIGH Description: Proxifier System Settings Exit code: 0 Version: 3.42.0.1 Modules
| |||||||||||||||
| 944 | "C:\Users\admin\AppData\Roaming\VIP72 Socks Client\vip72socks.exe" -hidepass | C:\Users\admin\AppData\Roaming\VIP72 Socks Client\vip72socks.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 1444 | "C:\Users\admin\AppData\Local\Temp\is-2VEU5.tmp\vip72socks-set-x5.tmp" /SL5="$E0182,4505720,58368,C:\Users\admin\AppData\Local\Temp\vip72socks-set-x5.exe" /SPAWNWND=$9016A /NOTIFYWND=$7019C | C:\Users\admin\AppData\Local\Temp\is-2VEU5.tmp\vip72socks-set-x5.tmp | — | vip72socks-set-x5.exe | |||||||||||
User: admin Integrity Level: HIGH Description: Setup/Uninstall Exit code: 0 Version: 51.52.0.0 Modules
| |||||||||||||||
| 1660 | "C:\Users\admin\AppData\Roaming\VIP72 Socks Client\proxifier-standart\SysSettings32.exe" silent-check | C:\Users\admin\AppData\Roaming\VIP72 Socks Client\proxifier-standart\SysSettings32.exe | — | Proxifier.exe | |||||||||||
User: admin Company: Initex Integrity Level: MEDIUM Description: Proxifier System Settings Exit code: 0 Version: 3.42.0.1 Modules
| |||||||||||||||
| 2232 | "C:\Users\admin\AppData\Local\Temp\vip72socks-set-x5.exe" /SPAWNWND=$9016A /NOTIFYWND=$7019C | C:\Users\admin\AppData\Local\Temp\vip72socks-set-x5.exe | vip72socks-set-x5.tmp | ||||||||||||
User: admin Company: VIP Technologies Integrity Level: HIGH Description: VIP72 Socks Client Setup Exit code: 0 Version: 1.8.7.14 Modules
| |||||||||||||||
| 2692 | "C:\Users\admin\AppData\Local\Temp\vip72socks-set-x5.exe" | C:\Users\admin\AppData\Local\Temp\vip72socks-set-x5.exe | — | explorer.exe | |||||||||||
User: admin Company: VIP Technologies Integrity Level: MEDIUM Description: VIP72 Socks Client Setup Exit code: 0 Version: 1.8.7.14 Modules
| |||||||||||||||
| 3060 | "C:\Users\admin\AppData\Local\Temp\is-QFMBV.tmp\vip72socks-set-x5.tmp" /SL5="$7019C,4505720,58368,C:\Users\admin\AppData\Local\Temp\vip72socks-set-x5.exe" | C:\Users\admin\AppData\Local\Temp\is-QFMBV.tmp\vip72socks-set-x5.tmp | — | vip72socks-set-x5.exe | |||||||||||
User: admin Integrity Level: MEDIUM Description: Setup/Uninstall Exit code: 0 Version: 51.52.0.0 Modules
| |||||||||||||||
| 3380 | "C:\Users\admin\AppData\Roaming\VIP72 Socks Client\proxifier-standart\Proxifier.exe" | C:\Users\admin\AppData\Roaming\VIP72 Socks Client\proxifier-standart\Proxifier.exe | explorer.exe | ||||||||||||
User: admin Company: Initex Integrity Level: MEDIUM Description: Proxifier Standard Edition v3.42 Exit code: 0 Version: 3.42.0.1 Modules
| |||||||||||||||
| 3924 | "C:\Program Files\Windows Media Player\wmpnscfg.exe" | C:\Program Files\Windows Media Player\wmpnscfg.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Media Player Network Sharing Service Configuration Application Exit code: 0 Version: 12.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
4 990
Read events
4 701
Write events
70
Delete events
219
Modification events
| (PID) Process: | (924) SysSettings32.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\WinSock2\Parameters\Protocol_Catalog9\Catalog_Entries\000000000001 |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (924) SysSettings32.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\WinSock2\Parameters\Protocol_Catalog9\Catalog_Entries\000000000002 |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (924) SysSettings32.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\WinSock2\Parameters\Protocol_Catalog9\Catalog_Entries\000000000003 |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (924) SysSettings32.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\WinSock2\Parameters\Protocol_Catalog9\Catalog_Entries\000000000004 |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (924) SysSettings32.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\WinSock2\Parameters\Protocol_Catalog9\Catalog_Entries\000000000005 |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (924) SysSettings32.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\WinSock2\Parameters\Protocol_Catalog9\Catalog_Entries\000000000006 |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (924) SysSettings32.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\WinSock2\Parameters\Protocol_Catalog9\Catalog_Entries\000000000007 |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (924) SysSettings32.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\WinSock2\Parameters\Protocol_Catalog9\Catalog_Entries\000000000008 |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (924) SysSettings32.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\WinSock2\Parameters\Protocol_Catalog9\Catalog_Entries\000000000009 |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (924) SysSettings32.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\WinSock2\Parameters\Protocol_Catalog9\Catalog_Entries\000000000010 |
| Operation: | delete key | Name: | (default) |
Value: | |||
Executable files
50
Suspicious files
26
Text files
24
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1444 | vip72socks-set-x5.tmp | C:\Users\admin\AppData\Roaming\VIP72 Socks Client\is-BI6U6.tmp | — | |
MD5:— | SHA256:— | |||
| 1444 | vip72socks-set-x5.tmp | C:\Users\admin\AppData\Roaming\VIP72 Socks Client\somd.dat | — | |
MD5:— | SHA256:— | |||
| 1444 | vip72socks-set-x5.tmp | C:\Users\admin\AppData\Roaming\VIP72 Socks Client\is-ANUH4.tmp | — | |
MD5:— | SHA256:— | |||
| 1444 | vip72socks-set-x5.tmp | C:\Users\admin\AppData\Roaming\VIP72 Socks Client\some.dat | — | |
MD5:— | SHA256:— | |||
| 1444 | vip72socks-set-x5.tmp | C:\Users\admin\AppData\Roaming\VIP72 Socks Client\is-OVMB7.tmp | text | |
MD5:70AB18142DFE5BE95E0705C80B58853E | SHA256:A6D435140F1CC9989ED1B739A2AF926A9D30E53E09D53A39DD714E7D80A0CD86 | |||
| 1444 | vip72socks-set-x5.tmp | C:\Users\admin\AppData\Roaming\VIP72 Socks Client\unins000.exe | executable | |
MD5:46F30F84294B0822214B46E59A261418 | SHA256:A86A17C9ED29752E24155559AAB2975D1FF45363F1640BA2F08A780B33F00374 | |||
| 2232 | vip72socks-set-x5.exe | C:\Users\admin\AppData\Local\Temp\is-2VEU5.tmp\vip72socks-set-x5.tmp | executable | |
MD5:1AFBD25DB5C9A90FE05309F7C4FBCF09 | SHA256:3BB0EE5569FE5453C6B3FA25AA517B925D4F8D1F7BA3475E58FA09C46290658C | |||
| 1444 | vip72socks-set-x5.tmp | C:\Users\admin\AppData\Roaming\VIP72 Socks Client\is-ISMDJ.tmp | text | |
MD5:808FDD68D49871F0DF9EAE0E8885F7B4 | SHA256:2AF01746E5EA361756CD746D5B300CFE21F9EA7275826835C1E292927BAD1C56 | |||
| 1444 | vip72socks-set-x5.tmp | C:\Users\admin\AppData\Roaming\VIP72 Socks Client\dnslist.txt | text | |
MD5:70AB18142DFE5BE95E0705C80B58853E | SHA256:A6D435140F1CC9989ED1B739A2AF926A9D30E53E09D53A39DD714E7D80A0CD86 | |||
| 1444 | vip72socks-set-x5.tmp | C:\Users\admin\AppData\Roaming\VIP72 Socks Client\is-HSQ7U.tmp | executable | |
MD5:1343900E72947CB87CB1898B5E7B8F93 | SHA256:B6F77009A87F91251CA7EF0B74EEE9A4FC9C22E47897C2A3FC3855A2CFF21B22 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
2
TCP/UDP connections
7
DNS requests
2
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
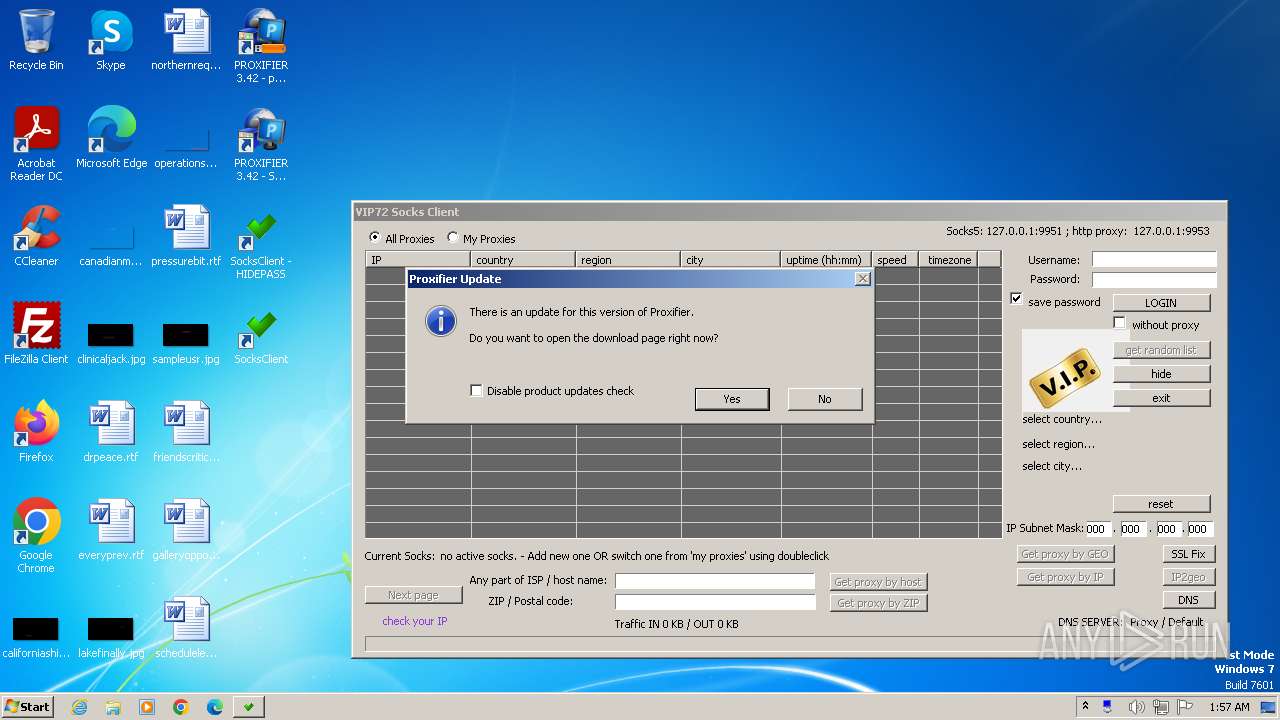
3380 | Proxifier.exe | GET | 200 | 172.104.17.238:80 | http://www.proxifier.com/distr/last_versions/ProxifierStandard/?nocache=9ABCF1836B53806BB8 | unknown | text | 47 b | unknown |
580 | vip72socks.exe | GET | 301 | 31.184.242.16:80 | http://vip72.org/version.text | unknown | html | 169 b | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
2588 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
580 | vip72socks.exe | 31.184.242.16:80 | vip72.org | MIRholding B.V. | RU | unknown |
3380 | Proxifier.exe | 172.104.17.238:80 | www.proxifier.com | Linode, LLC | US | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
vip72.org |
| unknown |
www.proxifier.com |
| unknown |