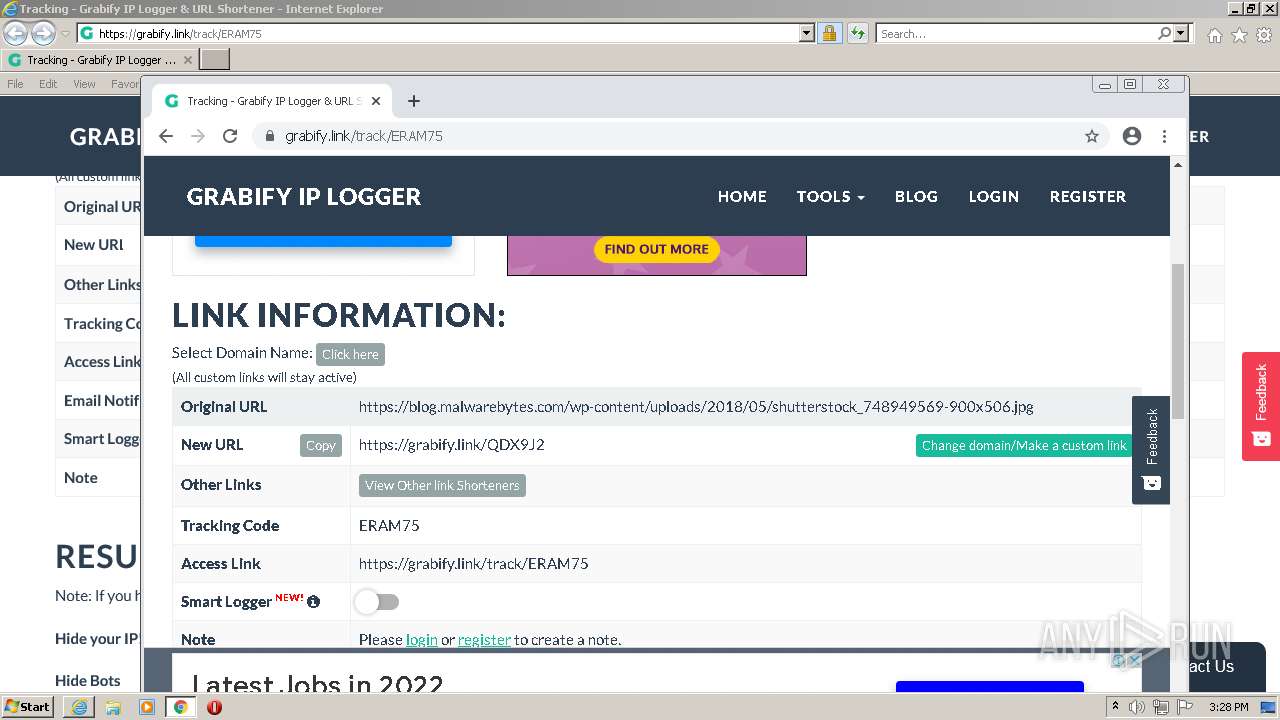
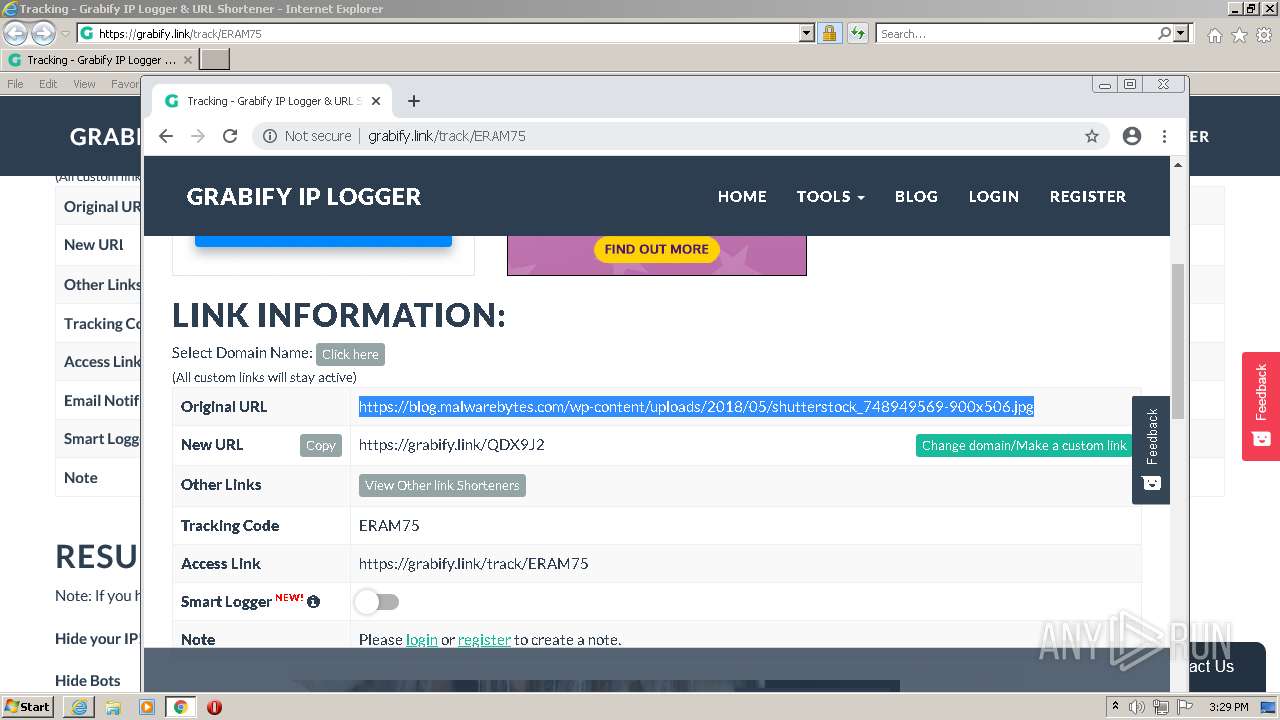
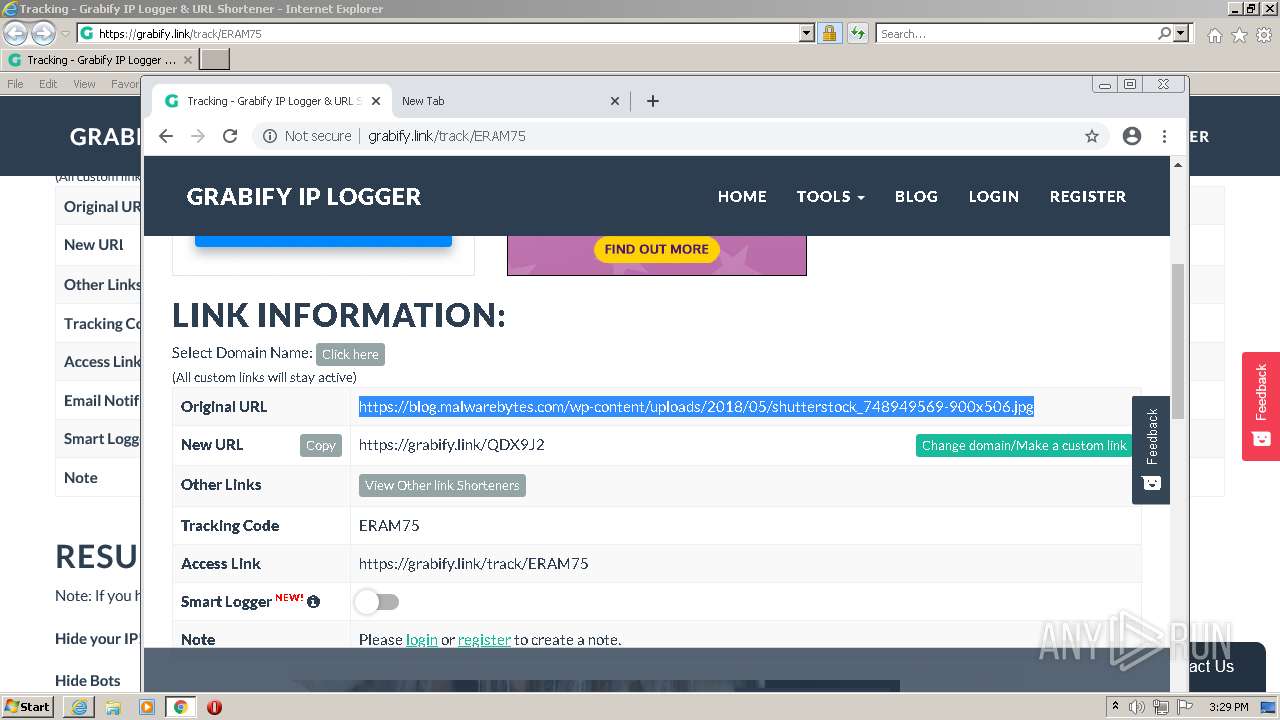
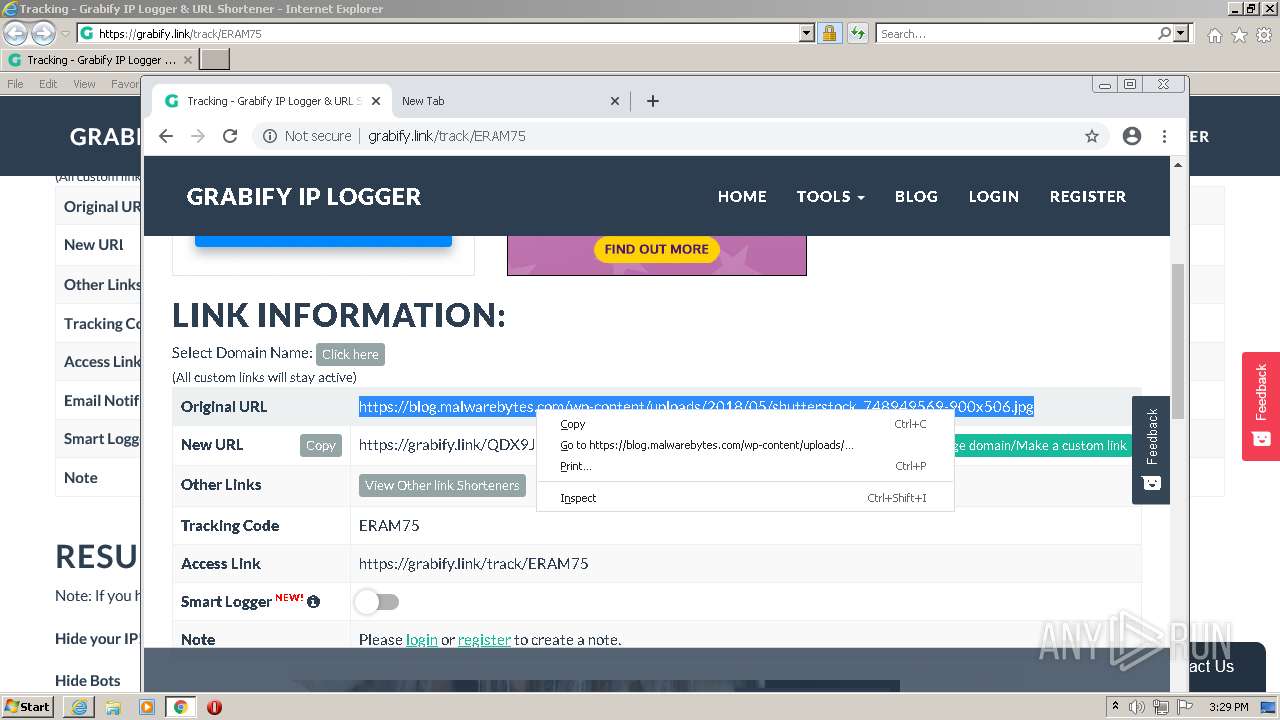
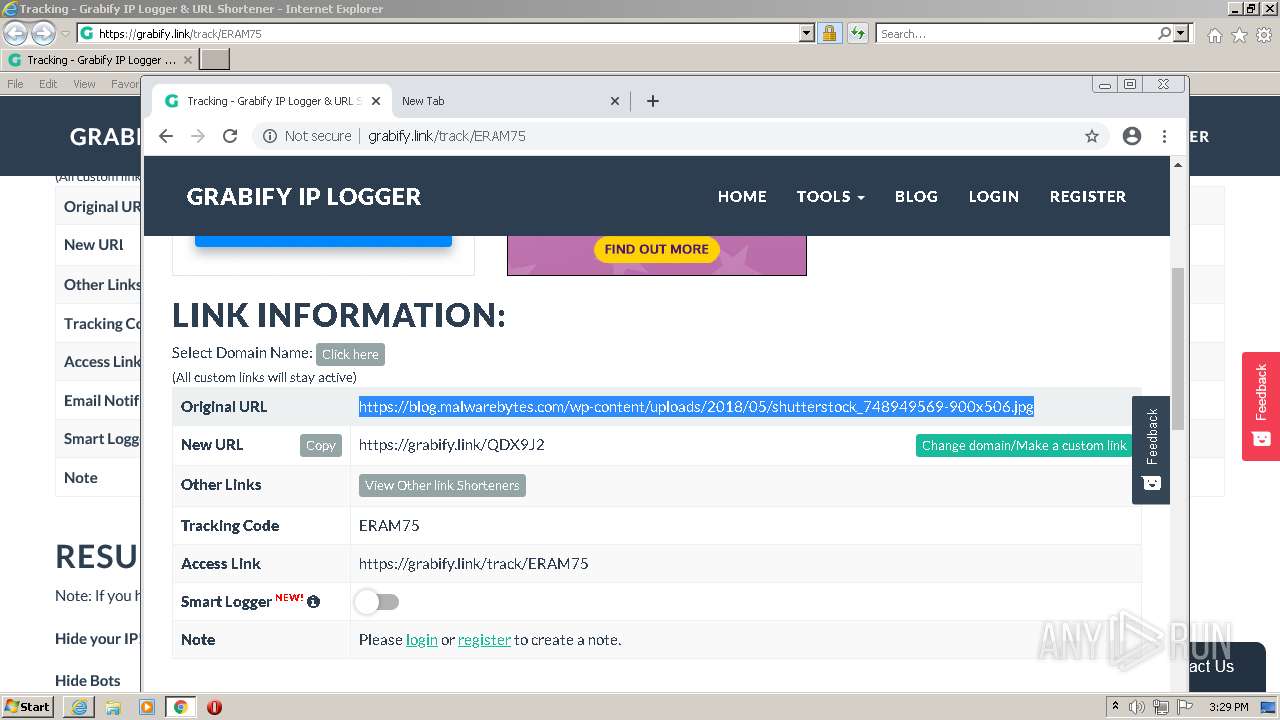
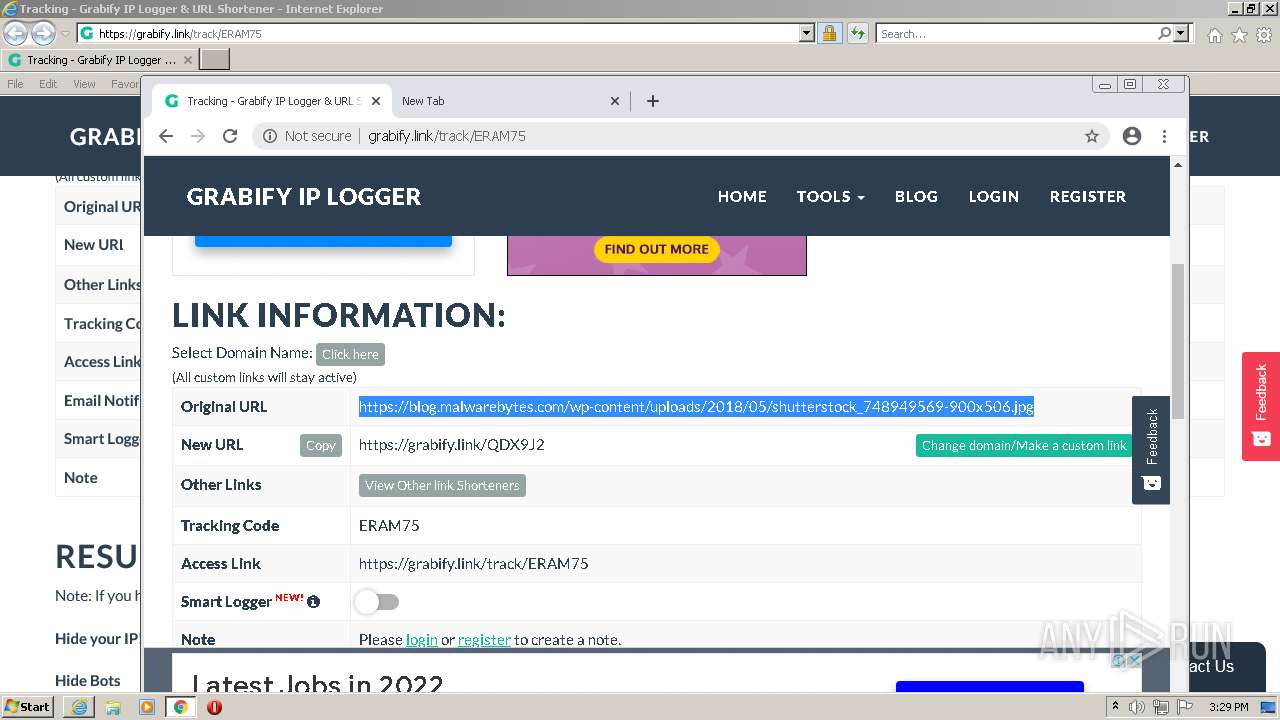
| URL: | https://grabify.link/track/ERAM75 |
| Full analysis: | https://app.any.run/tasks/5f044a50-699b-40bc-b334-bbe631660970 |
| Verdict: | Malicious activity |
| Analysis date: | February 12, 2022, 15:26:41 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MD5: | 9DBB3B9F79226C59A8BDDD07A566013A |
| SHA1: | 4F877FFE8E290357DB52F75C70ABD9D8278BFAF3 |
| SHA256: | 8E6596F425932BB9D7C829E3A59E0AF5BD8C58329452649A863B7C1EA55EA11E |
| SSDEEP: | 3:N82EicLJVMEPn:22fcLx |
MALICIOUS
No malicious indicators.SUSPICIOUS
Reads Microsoft Outlook installation path
- iexplore.exe (PID: 4088)
Modifies files in Chrome extension folder
- chrome.exe (PID: 2784)
INFO
Checks supported languages
- iexplore.exe (PID: 3648)
- iexplore.exe (PID: 4088)
- chrome.exe (PID: 560)
- chrome.exe (PID: 2784)
- chrome.exe (PID: 2812)
- chrome.exe (PID: 1968)
- chrome.exe (PID: 2920)
- chrome.exe (PID: 524)
- chrome.exe (PID: 2788)
- chrome.exe (PID: 1816)
- chrome.exe (PID: 2460)
- chrome.exe (PID: 2792)
- chrome.exe (PID: 3744)
- chrome.exe (PID: 2820)
- chrome.exe (PID: 3240)
- chrome.exe (PID: 400)
- chrome.exe (PID: 1208)
- chrome.exe (PID: 588)
- chrome.exe (PID: 2544)
- chrome.exe (PID: 1208)
- chrome.exe (PID: 468)
- chrome.exe (PID: 2516)
- chrome.exe (PID: 3304)
- chrome.exe (PID: 3264)
- chrome.exe (PID: 2056)
- chrome.exe (PID: 3160)
- chrome.exe (PID: 1124)
- chrome.exe (PID: 3164)
- chrome.exe (PID: 3120)
- chrome.exe (PID: 3328)
- chrome.exe (PID: 3300)
- chrome.exe (PID: 3752)
- chrome.exe (PID: 3880)
- chrome.exe (PID: 3396)
- chrome.exe (PID: 948)
- chrome.exe (PID: 3360)
- chrome.exe (PID: 2700)
- chrome.exe (PID: 1972)
- chrome.exe (PID: 484)
- chrome.exe (PID: 3884)
- chrome.exe (PID: 860)
- chrome.exe (PID: 548)
- chrome.exe (PID: 1264)
- chrome.exe (PID: 1716)
- chrome.exe (PID: 3860)
- chrome.exe (PID: 3796)
- chrome.exe (PID: 912)
- chrome.exe (PID: 2540)
- chrome.exe (PID: 4924)
- chrome.exe (PID: 5024)
- chrome.exe (PID: 5308)
- chrome.exe (PID: 2900)
- chrome.exe (PID: 5636)
- chrome.exe (PID: 3784)
- chrome.exe (PID: 5732)
- chrome.exe (PID: 5916)
- chrome.exe (PID: 5440)
- chrome.exe (PID: 2244)
- chrome.exe (PID: 3420)
- chrome.exe (PID: 4300)
- chrome.exe (PID: 4216)
- chrome.exe (PID: 4612)
- chrome.exe (PID: 4920)
- chrome.exe (PID: 4772)
- chrome.exe (PID: 5052)
- chrome.exe (PID: 5168)
- chrome.exe (PID: 5200)
- chrome.exe (PID: 5304)
- chrome.exe (PID: 5220)
- chrome.exe (PID: 1104)
- chrome.exe (PID: 5980)
- chrome.exe (PID: 3140)
- chrome.exe (PID: 4724)
- chrome.exe (PID: 6012)
- chrome.exe (PID: 5708)
- chrome.exe (PID: 5768)
- chrome.exe (PID: 5580)
- chrome.exe (PID: 5580)
- chrome.exe (PID: 5212)
- chrome.exe (PID: 5844)
- chrome.exe (PID: 2860)
- chrome.exe (PID: 4264)
- chrome.exe (PID: 6012)
- chrome.exe (PID: 4452)
- chrome.exe (PID: 6076)
Changes internet zones settings
- iexplore.exe (PID: 3648)
Reads the computer name
- iexplore.exe (PID: 3648)
- chrome.exe (PID: 2784)
- iexplore.exe (PID: 4088)
- chrome.exe (PID: 560)
- chrome.exe (PID: 1968)
- chrome.exe (PID: 2460)
- chrome.exe (PID: 3744)
- chrome.exe (PID: 1208)
- chrome.exe (PID: 468)
- chrome.exe (PID: 1124)
- chrome.exe (PID: 1972)
Application launched itself
- iexplore.exe (PID: 3648)
- chrome.exe (PID: 2784)
Reads settings of System Certificates
- iexplore.exe (PID: 3648)
- chrome.exe (PID: 560)
- iexplore.exe (PID: 4088)
Reads the hosts file
- chrome.exe (PID: 2784)
- chrome.exe (PID: 560)
Creates files in the user directory
- iexplore.exe (PID: 4088)
- iexplore.exe (PID: 3648)
Reads internet explorer settings
- iexplore.exe (PID: 4088)
Manual execution by user
- chrome.exe (PID: 2784)
Checks Windows Trust Settings
- iexplore.exe (PID: 3648)
- iexplore.exe (PID: 4088)
Adds / modifies Windows certificates
- iexplore.exe (PID: 3648)
Changes settings of System certificates
- iexplore.exe (PID: 3648)
Reads the date of Windows installation
- chrome.exe (PID: 468)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
122
Monitored processes
85
Malicious processes
0
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process |
|---|---|---|---|---|
| 400 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1060,11228539819070443337,14521514353996492678,131072 --enable-features=PasswordImport --disable-gpu-compositing --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=15 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=2408 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe |
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 | ||||
| 468 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=chrome.mojom.UtilWin --field-trial-handle=1060,11228539819070443337,14521514353996492678,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=none --mojo-platform-channel-handle=1856 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe |
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 | ||||
| 484 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1060,11228539819070443337,14521514353996492678,131072 --enable-features=PasswordImport --disable-gpu-compositing --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=36 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=5112 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe |
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 | ||||
| 524 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1060,11228539819070443337,14521514353996492678,131072 --enable-features=PasswordImport --lang=en-US --extension-process --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=4 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=2324 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe |
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 | ||||
| 548 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1060,11228539819070443337,14521514353996492678,131072 --enable-features=PasswordImport --disable-gpu-compositing --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=41 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=4204 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe |
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 | ||||
| 560 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=network.mojom.NetworkService --field-trial-handle=1060,11228539819070443337,14521514353996492678,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=network --mojo-platform-channel-handle=1344 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | chrome.exe | |
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 | ||||
| 588 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --field-trial-handle=1060,11228539819070443337,14521514353996492678,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --mojo-platform-channel-handle=3256 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe |
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 | ||||
| 860 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1060,11228539819070443337,14521514353996492678,131072 --enable-features=PasswordImport --disable-gpu-compositing --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=35 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=4952 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe |
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 | ||||
| 912 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1060,11228539819070443337,14521514353996492678,131072 --enable-features=PasswordImport --disable-gpu-compositing --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=42 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=4756 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe |
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 | ||||
| 948 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1060,11228539819070443337,14521514353996492678,131072 --enable-features=PasswordImport --disable-gpu-compositing --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=31 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=4536 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe |
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 | ||||
Total events
0
Read events
0
Write events
0
Delete events
0
Modification events
Executable files
0
Suspicious files
306
Text files
265
Unknown types
48
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3648 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\6BADA8974A10C4BD62CC921D13E43B18_711ED44619924BA6DC33E69F97E7FF63 | binary | |
MD5:— | SHA256:— | |||
| 4088 | iexplore.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Cookies\Low\S6N2RMUG.txt | text | |
MD5:— | SHA256:— | |||
| 4088 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\57C8EDB95DF3F0AD4EE2DC2B8CFD4157 | binary | |
MD5:— | SHA256:— | |||
| 4088 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\82CB34DD3343FE727DF8890D352E0D8F | der | |
MD5:— | SHA256:— | |||
| 4088 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\82CB34DD3343FE727DF8890D352E0D8F | binary | |
MD5:— | SHA256:— | |||
| 3648 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\6BADA8974A10C4BD62CC921D13E43B18_711ED44619924BA6DC33E69F97E7FF63 | der | |
MD5:— | SHA256:— | |||
| 4088 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\5IWPIAR9\all[1].css | text | |
MD5:— | SHA256:— | |||
| 4088 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\MFAQUS6V\tpage[1].js | text | |
MD5:— | SHA256:— | |||
| 4088 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\DY534W2X\ERAM75[1].htm | html | |
MD5:— | SHA256:— | |||
| 4088 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\5IWPIAR9\all[1].js | text | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
78
TCP/UDP connections
350
DNS requests
252
Threats
11
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
4088 | iexplore.exe | GET | 200 | 142.250.186.131:80 | http://ocsp.pki.goog/gts1c3/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTHLnmK3f9hNLO67UdCuLvGwCQHYwQUinR%2Fr4XN7pXNPZzQ4kYU83E1HScCEH8SKh5qcwxcCgAAAAEvj7Q%3D | US | der | 471 b | whitelisted |
4088 | iexplore.exe | GET | 200 | 142.250.186.131:80 | http://ocsp.pki.goog/gsr1/MFEwTzBNMEswSTAJBgUrDgMCGgUABBS3V7W2nAf4FiMTjpDJKg6%2BMgGqMQQUYHtmGkUNl8qJUC99BM00qP%2F8%2FUsCEHe9DWzbNvka6iEPxPBY0w0%3D | US | der | 1.41 Kb | whitelisted |
4088 | iexplore.exe | GET | 200 | 142.250.186.131:80 | http://ocsp.pki.goog/gts1c3/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTHLnmK3f9hNLO67UdCuLvGwCQHYwQUinR%2Fr4XN7pXNPZzQ4kYU83E1HScCEEVS5fQOl%2FjiCgAAAAEvj9s%3D | US | der | 471 b | whitelisted |
4088 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://crl3.digicert.com/Omniroot2025.crl | US | der | 7.68 Kb | whitelisted |
4088 | iexplore.exe | GET | 200 | 142.250.186.131:80 | http://ocsp.pki.goog/gts1c3/MFIwUDBOMEwwSjAJBgUrDgMCGgUABBTHLnmK3f9hNLO67UdCuLvGwCQHYwQUinR%2Fr4XN7pXNPZzQ4kYU83E1HScCEQCi%2B7O9F%2Fm8IwoAAAABL5ZN | US | der | 472 b | whitelisted |
4088 | iexplore.exe | GET | 200 | 142.250.186.131:80 | http://ocsp.pki.goog/gts1c3/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTHLnmK3f9hNLO67UdCuLvGwCQHYwQUinR%2Fr4XN7pXNPZzQ4kYU83E1HScCED4mh8m0t01JCgAAAAEvkro%3D | US | der | 471 b | whitelisted |
4088 | iexplore.exe | GET | 200 | 142.250.186.131:80 | http://ocsp.pki.goog/gtsr1/ME4wTDBKMEgwRjAJBgUrDgMCGgUABBQwkcLWD4LqGJ7bE7B1XZsEbmfwUAQU5K8rJnEaK0gnhS9SZizv8IkTcT4CDQIDvFNZazTHGPUBUGY%3D | US | der | 724 b | whitelisted |
4088 | iexplore.exe | GET | 200 | 142.250.186.131:80 | http://ocsp.pki.goog/gts1c3/MFIwUDBOMEwwSjAJBgUrDgMCGgUABBTHLnmK3f9hNLO67UdCuLvGwCQHYwQUinR%2Fr4XN7pXNPZzQ4kYU83E1HScCEQC9xJ9s74KAqgoAAAABL5UT | US | der | 472 b | whitelisted |
4088 | iexplore.exe | GET | 200 | 142.250.186.131:80 | http://ocsp.pki.goog/gts1c3/MFIwUDBOMEwwSjAJBgUrDgMCGgUABBTHLnmK3f9hNLO67UdCuLvGwCQHYwQUinR%2Fr4XN7pXNPZzQ4kYU83E1HScCEQCi%2B7O9F%2Fm8IwoAAAABL5ZN | US | der | 472 b | whitelisted |
3648 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | US | der | 471 b | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4088 | iexplore.exe | 2.16.186.19:443 | cdn.fuseplatform.net | Akamai International B.V. | — | whitelisted |
— | — | 2.16.186.19:443 | cdn.fuseplatform.net | Akamai International B.V. | — | whitelisted |
4088 | iexplore.exe | 104.27.41.48:443 | grabify.link | Cloudflare Inc | US | shared |
4088 | iexplore.exe | 23.32.238.201:80 | ctldl.windowsupdate.com | XO Communications | US | suspicious |
4088 | iexplore.exe | 93.184.220.29:80 | ocsp.digicert.com | MCI Communications Services, Inc. d/b/a Verizon Business | US | whitelisted |
4088 | iexplore.exe | 142.250.186.98:443 | adservice.google.be | Google Inc. | US | suspicious |
4088 | iexplore.exe | 104.16.94.65:443 | static.cloudflareinsights.com | Cloudflare Inc | US | shared |
4088 | iexplore.exe | 142.250.74.194:443 | adservice.google.com | Google Inc. | US | suspicious |
4088 | iexplore.exe | 142.250.185.67:443 | fonts.gstatic.com | Google Inc. | US | whitelisted |
4088 | iexplore.exe | 142.250.186.33:443 | 795810be272098ae6eeb828b7fd7494c.safeframe.googlesyndication.com | Google Inc. | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
grabify.link |
| whitelisted |
ctldl.windowsupdate.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
api.bing.com |
| whitelisted |
www.bing.com |
| whitelisted |
crl3.digicert.com |
| whitelisted |
cdn.fuseplatform.net |
| whitelisted |
securepubads.g.doubleclick.net |
| whitelisted |
ocsp.pki.goog |
| whitelisted |
static.cloudflareinsights.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
4088 | iexplore.exe | Potentially Bad Traffic | ET INFO TLS Handshake Failure |
— | — | Potentially Bad Traffic | ET DNS Query for .to TLD |
— | — | Potentially Bad Traffic | ET DNS Query for .to TLD |
— | — | Potentially Bad Traffic | ET DNS Query for .to TLD |
— | — | Potentially Bad Traffic | ET DNS Query for .to TLD |
— | — | Potentially Bad Traffic | ET DNS Query for .to TLD |
— | — | Potentially Bad Traffic | ET DNS Query for .to TLD |
560 | chrome.exe | Potentially Bad Traffic | ET INFO TLS Handshake Failure |
560 | chrome.exe | Potentially Bad Traffic | ET INFO TLS Handshake Failure |
— | — | Potentially Bad Traffic | ET DNS Query for .to TLD |