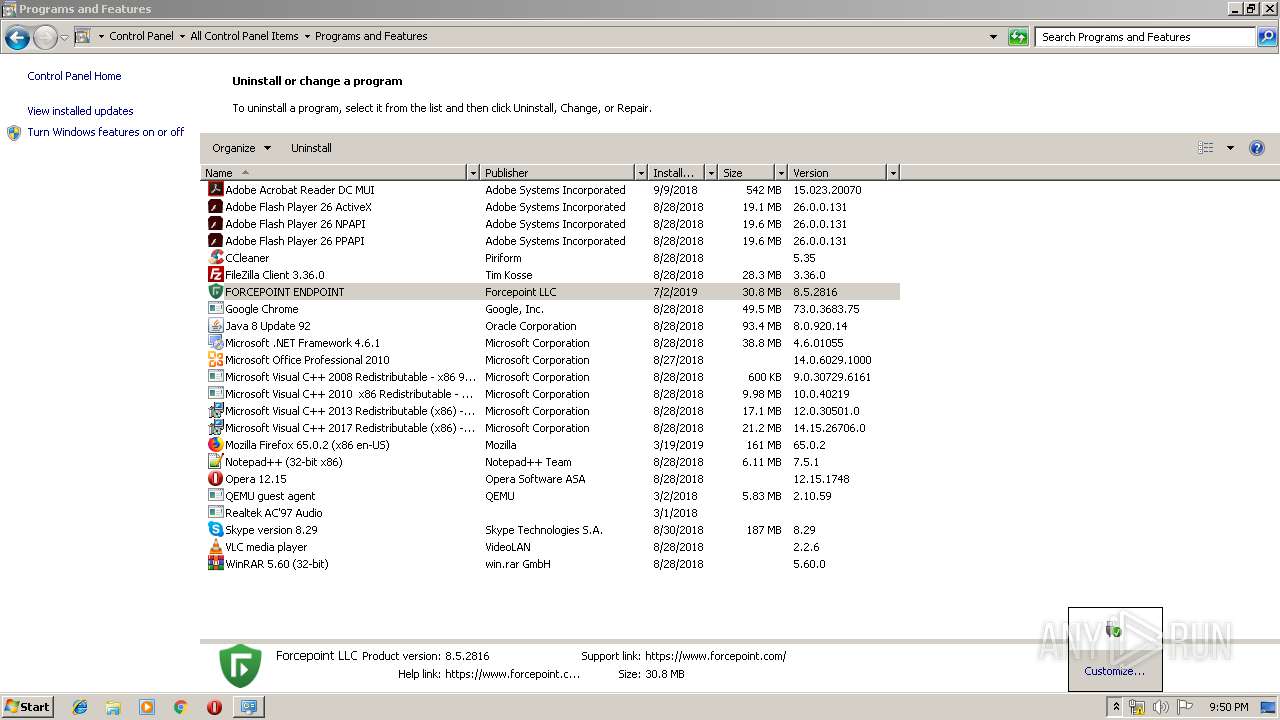
| File name: | asdo3234jfm3r34sa.exe |
| Full analysis: | https://app.any.run/tasks/e52f64b3-fb1c-427b-bb33-2e120e8d3e0c |
| Verdict: | Malicious activity |
| Analysis date: | July 02, 2019, 20:47:51 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, InstallShield self-extracting archive |
| MD5: | BE3FDC7659A62E68D207F3BE2700C559 |
| SHA1: | 14388D849E94B1924A44B608B2B7AE0648DC6681 |
| SHA256: | 8E4E95547EB53C170D439A775CBDEC49E6457BDC90A3E5F6A8F3694EEB501B70 |
| SSDEEP: | 196608:XVZr5MVjRez230jGb/8Mv0pqa6+MiRCRCwyboaLmyJkblv77Gthm+Wf98M:XVZr6GGb/f0pqFFtR93bl7+hmT9 |
MALICIOUS
Application was dropped or rewritten from another process
- setup.exe (PID: 3284)
- wepsvc.exe (PID: 2660)
- wepsvc.exe (PID: 3192)
- wepsvc.exe (PID: 776)
- wepsvc.exe (PID: 3552)
Changes settings of System certificates
- setup.exe (PID: 3284)
Starts NET.EXE for service management
- MsiExec.exe (PID: 2900)
Loads dropped or rewritten executable
- wepsvc.exe (PID: 2660)
- wepsvc.exe (PID: 776)
- wepsvc.exe (PID: 3192)
- wepsvc.exe (PID: 3552)
SUSPICIOUS
Adds / modifies Windows certificates
- setup.exe (PID: 3284)
Removes files from Windows directory
- MsiExec.exe (PID: 3592)
- MsiExec.exe (PID: 2900)
Creates files in the driver directory
- MsiExec.exe (PID: 2900)
Executable content was dropped or overwritten
- MsiExec.exe (PID: 2900)
- asdo3234jfm3r34sa.exe (PID: 2708)
- msiexec.exe (PID: 2664)
Starts Microsoft Installer
- setup.exe (PID: 3284)
Creates files in the Windows directory
- MsiExec.exe (PID: 3592)
- MsiExec.exe (PID: 2900)
Starts SC.EXE for service management
- MsiExec.exe (PID: 3592)
Creates COM task schedule object
- msiexec.exe (PID: 2664)
Creates files in the program directory
- wepsvc.exe (PID: 3552)
INFO
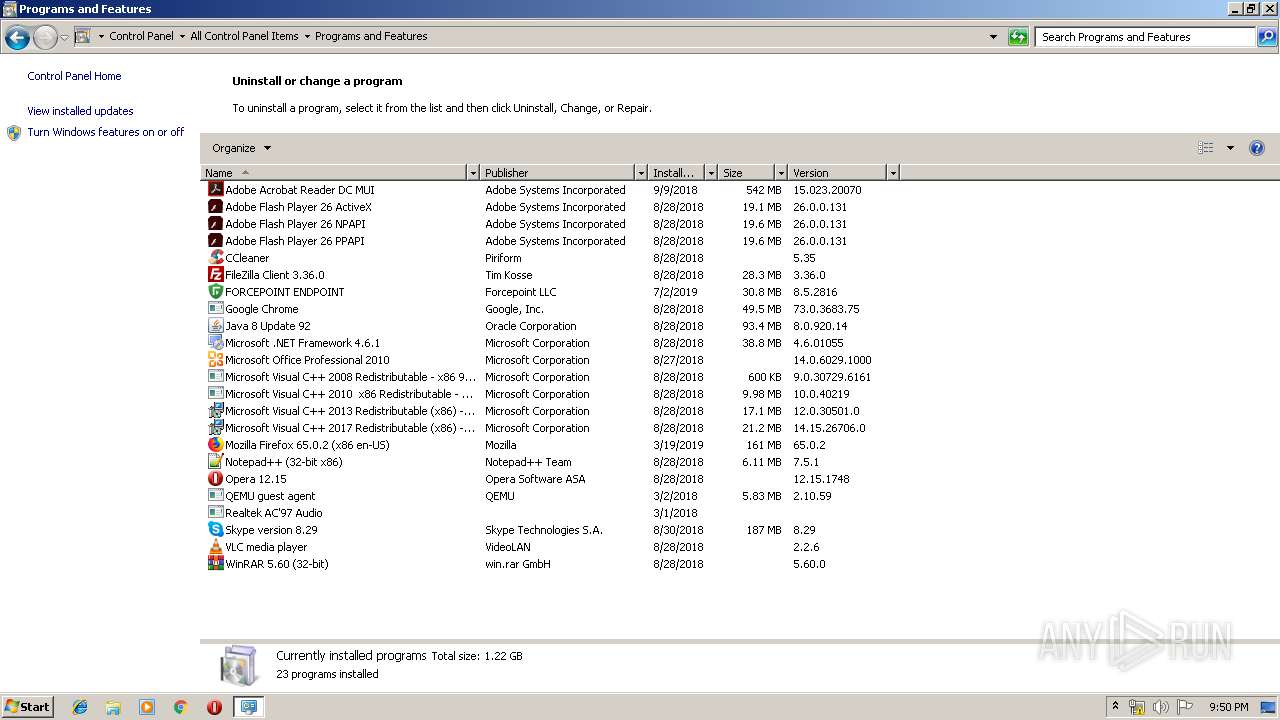
Creates a software uninstall entry
- msiexec.exe (PID: 2664)
Dropped object may contain Bitcoin addresses
- msiexec.exe (PID: 2664)
- iexplore.exe (PID: 3456)
Application launched itself
- msiexec.exe (PID: 2664)
- iexplore.exe (PID: 3116)
Creates files in the program directory
- MsiExec.exe (PID: 2900)
- msiexec.exe (PID: 2664)
Loads dropped or rewritten executable
- msiexec.exe (PID: 2664)
Manual execution by user
- iexplore.exe (PID: 3116)
- taskmgr.exe (PID: 2744)
Changes internet zones settings
- iexplore.exe (PID: 3116)
Creates or modifies windows services
- MsiExec.exe (PID: 3592)
Reads Internet Cache Settings
- iexplore.exe (PID: 3456)
- iexplore.exe (PID: 3116)
Reads internet explorer settings
- iexplore.exe (PID: 3456)
Creates files in the user directory
- iexplore.exe (PID: 3456)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 EXE PECompact compressed (generic) (22.8) |
|---|---|---|
| .exe | | | Win32 Executable MS Visual C++ (generic) (17.1) |
| .exe | | | Win64 Executable (generic) (15.1) |
| .exe | | | UPX compressed Win32 Executable (14.8) |
| .exe | | | Win32 EXE Yoda's Crypter (14.5) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2009:02:03 08:21:10+01:00 |
| PEType: | PE32 |
| LinkerVersion: | 6 |
| CodeSize: | 99328 |
| InitializedDataSize: | 33280 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x13254 |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 8.5.2816.1 |
| ProductVersionNumber: | 8.5.2816.1 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Windows NT 32-bit |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | English (U.S.) |
| CharacterSet: | Unicode |
| CompanyName: | Forcepoint LLC |
| FileDescription: | Forcepoint™ TRITON® AP-ENDPOINT |
| FileVersion: | 8.5.2816.1 |
| LegalCopyright: | Copyright (c) 1996 - 2017 Forcepoint LLC All Rights Reserved. |
| ProductName: | Forcepoint™ TRITON® AP-ENDPOINT |
| ProductVersion: | 8.5.2816.1 |
Summary
| Architecture: | IMAGE_FILE_MACHINE_I386 |
|---|---|
| Subsystem: | IMAGE_SUBSYSTEM_WINDOWS_GUI |
| Compilation Date: | 03-Feb-2009 07:21:10 |
| Detected languages: |
|
| CompanyName: | Forcepoint LLC |
| FileDescription: | Forcepoint™ TRITON® AP-ENDPOINT |
| FileVersion: | 8.5.2816.1 |
| LegalCopyright: | Copyright (c) 1996 - 2017 Forcepoint LLC All Rights Reserved. |
| ProductName: | Forcepoint™ TRITON® AP-ENDPOINT |
| ProductVersion: | 8.5.2816.1 |
DOS Header
| Magic number: | MZ |
|---|---|
| Bytes on last page of file: | 0x0090 |
| Pages in file: | 0x0003 |
| Relocations: | 0x0000 |
| Size of header: | 0x0004 |
| Min extra paragraphs: | 0x0000 |
| Max extra paragraphs: | 0xFFFF |
| Initial SS value: | 0x0000 |
| Initial SP value: | 0x00B8 |
| Checksum: | 0x0000 |
| Initial IP value: | 0x0000 |
| Initial CS value: | 0x0000 |
| Overlay number: | 0x0000 |
| OEM identifier: | 0x0000 |
| OEM information: | 0x0000 |
| Address of NE header: | 0x000000E8 |
PE Headers
| Signature: | PE |
|---|---|
| Machine: | IMAGE_FILE_MACHINE_I386 |
| Number of sections: | 4 |
| Time date stamp: | 03-Feb-2009 07:21:10 |
| Pointer to Symbol Table: | 0x00000000 |
| Number of symbols: | 0 |
| Size of Optional Header: | 0x00E0 |
| Characteristics: |
|
Sections
Name | Virtual Address | Virtual Size | Raw Size | Charateristics | Entropy |
|---|---|---|---|---|---|
.text | 0x00001000 | 0x000182F2 | 0x00018400 | IMAGE_SCN_CNT_CODE, IMAGE_SCN_MEM_EXECUTE, IMAGE_SCN_MEM_READ | 6.60298 |
.rdata | 0x0001A000 | 0x00004192 | 0x00004200 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ | 4.44948 |
.data | 0x0001F000 | 0x00005948 | 0x00003200 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 1.30618 |
.rsrc | 0x00025000 | 0x00000CB8 | 0x00000E00 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ | 4.05159 |
Resources
Title | Entropy | Size | Codepage | Language | Type |
|---|---|---|---|---|---|
1 | 4.81618 | 492 | Latin 1 / Western European | English - United States | RT_MANIFEST |
2 | 3.18403 | 296 | Latin 1 / Western European | English - United States | RT_ICON |
5 | 1.43775 | 52 | Latin 1 / Western European | English - United States | RT_STRING |
159 | 2.37086 | 34 | Latin 1 / Western European | English - United States | RT_GROUP_ICON |
500 | 3.07919 | 184 | Latin 1 / Western European | English - United States | RT_DIALOG |
Imports
COMCTL32.dll |
KERNEL32.dll |
OLEAUT32.dll |
SHELL32.dll |
USER32.dll |
Total processes
65
Monitored processes
17
Malicious processes
5
Suspicious processes
4
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 776 | "C:\Program Files\Websense\Websense Endpoint\wepsvc.exe" -start WSTS | C:\Program Files\Websense\Websense Endpoint\wepsvc.exe | — | MsiExec.exe | |||||||||||
User: admin Company: Forcepoint LLC Integrity Level: HIGH Description: Forcepoint Endpoint Exit code: 2147487746 Version: 8, 5, 2816, 17 Modules
| |||||||||||||||
| 2352 | "C:\Users\admin\Desktop\asdo3234jfm3r34sa.exe" /v"/qn WSCONTEXT=a620e1dbf4232ec021cabf5ca7583af9-1" | C:\Users\admin\Desktop\asdo3234jfm3r34sa.exe | — | explorer.exe | |||||||||||
User: admin Company: Forcepoint LLC Integrity Level: MEDIUM Description: Forcepoint™ TRITON® AP-ENDPOINT Exit code: 3221226540 Version: 8.5.2816.1 Modules
| |||||||||||||||
| 2560 | net stop nep /y | C:\Windows\system32\net.exe | — | MsiExec.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Net Command Exit code: 2 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2660 | "C:\Program Files\Websense\Websense Endpoint\wepsvc.exe" -start WSPXY | C:\Program Files\Websense\Websense Endpoint\wepsvc.exe | — | MsiExec.exe | |||||||||||
User: admin Company: Forcepoint LLC Integrity Level: HIGH Description: Forcepoint Endpoint Exit code: 2147487747 Version: 8, 5, 2816, 17 Modules
| |||||||||||||||
| 2664 | C:\Windows\system32\msiexec.exe /V | C:\Windows\system32\msiexec.exe | services.exe | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows® installer Exit code: 0 Version: 5.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2708 | "C:\Users\admin\Desktop\asdo3234jfm3r34sa.exe" /v"/qn WSCONTEXT=a620e1dbf4232ec021cabf5ca7583af9-1" | C:\Users\admin\Desktop\asdo3234jfm3r34sa.exe | explorer.exe | ||||||||||||
User: admin Company: Forcepoint LLC Integrity Level: HIGH Description: Forcepoint™ TRITON® AP-ENDPOINT Exit code: 0 Version: 8.5.2816.1 Modules
| |||||||||||||||
| 2744 | "C:\Windows\system32\taskmgr.exe" /4 | C:\Windows\system32\taskmgr.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Task Manager Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2900 | C:\Windows\system32\MsiExec.exe -Embedding 382EF3F5B249A47602D9DA5C944205A3 M Global\MSI0000 | C:\Windows\system32\MsiExec.exe | msiexec.exe | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows® installer Exit code: 0 Version: 5.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3116 | "C:\Program Files\Internet Explorer\iexplore.exe" | C:\Program Files\Internet Explorer\iexplore.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 1 Version: 8.00.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3192 | "C:\Program Files\Websense\Websense Endpoint\wepsvc.exe" -start WSRF | C:\Program Files\Websense\Websense Endpoint\wepsvc.exe | — | MsiExec.exe | |||||||||||
User: admin Company: Forcepoint LLC Integrity Level: HIGH Description: Forcepoint Endpoint Exit code: 2147487746 Version: 8, 5, 2816, 17 Modules
| |||||||||||||||
Total events
1 095
Read events
755
Write events
320
Delete events
20
Modification events
| (PID) Process: | (3284) setup.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\62\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3284) setup.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\SystemCertificates\AuthRoot\Certificates\91C6D6EE3E8AC86384E548C299295C756C817B81 |
| Operation: | write | Name: | Blob |
Value: 0F000000010000001400000085FEF11B4F47FE3952F98301C9F98976FEFEE0CE09000000010000002A000000302806082B0601050507030106082B0601050507030206082B0601050507030406082B0601050507030353000000010000002500000030233021060B6086480186F8450107300130123010060A2B0601040182373C0101030200C01400000001000000140000007B5B45CFAFCECB7AFD31921A6AB6F346EB5748501D00000001000000100000005B3B67000EEB80022E42605B6B3B72400B000000010000000E000000740068006100770074006500000003000000010000001400000091C6D6EE3E8AC86384E548C299295C756C817B812000000001000000240400003082042030820308A0030201020210344ED55720D5EDEC49F42FCE37DB2B6D300D06092A864886F70D01010505003081A9310B300906035504061302555331153013060355040A130C7468617774652C20496E632E31283026060355040B131F43657274696669636174696F6E205365727669636573204469766973696F6E31383036060355040B132F2863292032303036207468617774652C20496E632E202D20466F7220617574686F72697A656420757365206F6E6C79311F301D06035504031316746861777465205072696D61727920526F6F74204341301E170D3036313131373030303030305A170D3336303731363233353935395A3081A9310B300906035504061302555331153013060355040A130C7468617774652C20496E632E31283026060355040B131F43657274696669636174696F6E205365727669636573204469766973696F6E31383036060355040B132F2863292032303036207468617774652C20496E632E202D20466F7220617574686F72697A656420757365206F6E6C79311F301D06035504031316746861777465205072696D61727920526F6F7420434130820122300D06092A864886F70D01010105000382010F003082010A0282010100ACA0F0FB8059D49CC7A4CF9DA159730910450C0D2C6E68F16C5B4868495937FC0B3319C2777FCC102D95341CE6EB4D09A71CD2B8C9973602B789D4245F06C0CC4494948D02626FEB5ADD118D289A5C8490107A0DBD74662F6A38A0E2D55444EB1D079F07BA6FEEE9FD4E0B29F53E84A001F19CABF81C7E89A4E8A1D871650DA3517BEEBCD222600DB95B9DDFBAFC515B0BAF98B2E92EE904E86287DE2BC8D74EC14C641EDDCF8758BA4A4FCA68071D1C9D4AC6D52F91CC7C71721CC5C067EB32FDC9925C94DA85C09BBF537D2B09F48C9D911F976A52CBDE0936A477D87B875044D53E6E2969FB3949261E09A5807B402DEBE82785C9FE61FD7EE67C971DD59D0203010001A3423040300F0603551D130101FF040530030101FF300E0603551D0F0101FF040403020106301D0603551D0E041604147B5B45CFAFCECB7AFD31921A6AB6F346EB574850300D06092A864886F70D010105050003820101007911C04BB391B6FCF0E967D40D6E45BE55E893D2CE033FEDDA25B01D57CB1E3A76A04CEC5076E864720CA4A9F1B88BD6D68784BB32E54111C077D9B3609DEB1BD5D16E4444A9A601EC55621D77B85C8E48497C9C3B5711ACAD73378E2F785C906847D96060E6FC073D222017C4F716E9C4D872F9C8737CDF162F15A93EFD6A27B6A1EB5ABA981FD5E34D640A9D13C861BAF5391C87BAB8BD7B227FF6FEAC4079E5AC106F3D8F1B79768BC437B3211884E53600EB632099B9E9FE3304BB41C8C102F94463209E81CE42D3D63F2C76D3639C59DD8FA6E10EA02E41F72E9547CFBCFD33F3F60B617E7E912B8147C22730EEA7105D378F5C392BE404F07B8D568C68 | |||
| (PID) Process: | (3284) setup.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\SystemCertificates\AuthRoot\Certificates\91C6D6EE3E8AC86384E548C299295C756C817B81 |
| Operation: | write | Name: | Blob |
Value: 190000000100000010000000DC73F9B71E16D51D26527D32B11A6A3D03000000010000001400000091C6D6EE3E8AC86384E548C299295C756C817B810B000000010000000E00000074006800610077007400650000001D00000001000000100000005B3B67000EEB80022E42605B6B3B72401400000001000000140000007B5B45CFAFCECB7AFD31921A6AB6F346EB57485053000000010000002500000030233021060B6086480186F8450107300130123010060A2B0601040182373C0101030200C009000000010000002A000000302806082B0601050507030106082B0601050507030206082B0601050507030406082B060105050703030F000000010000001400000085FEF11B4F47FE3952F98301C9F98976FEFEE0CE2000000001000000240400003082042030820308A0030201020210344ED55720D5EDEC49F42FCE37DB2B6D300D06092A864886F70D01010505003081A9310B300906035504061302555331153013060355040A130C7468617774652C20496E632E31283026060355040B131F43657274696669636174696F6E205365727669636573204469766973696F6E31383036060355040B132F2863292032303036207468617774652C20496E632E202D20466F7220617574686F72697A656420757365206F6E6C79311F301D06035504031316746861777465205072696D61727920526F6F74204341301E170D3036313131373030303030305A170D3336303731363233353935395A3081A9310B300906035504061302555331153013060355040A130C7468617774652C20496E632E31283026060355040B131F43657274696669636174696F6E205365727669636573204469766973696F6E31383036060355040B132F2863292032303036207468617774652C20496E632E202D20466F7220617574686F72697A656420757365206F6E6C79311F301D06035504031316746861777465205072696D61727920526F6F7420434130820122300D06092A864886F70D01010105000382010F003082010A0282010100ACA0F0FB8059D49CC7A4CF9DA159730910450C0D2C6E68F16C5B4868495937FC0B3319C2777FCC102D95341CE6EB4D09A71CD2B8C9973602B789D4245F06C0CC4494948D02626FEB5ADD118D289A5C8490107A0DBD74662F6A38A0E2D55444EB1D079F07BA6FEEE9FD4E0B29F53E84A001F19CABF81C7E89A4E8A1D871650DA3517BEEBCD222600DB95B9DDFBAFC515B0BAF98B2E92EE904E86287DE2BC8D74EC14C641EDDCF8758BA4A4FCA68071D1C9D4AC6D52F91CC7C71721CC5C067EB32FDC9925C94DA85C09BBF537D2B09F48C9D911F976A52CBDE0936A477D87B875044D53E6E2969FB3949261E09A5807B402DEBE82785C9FE61FD7EE67C971DD59D0203010001A3423040300F0603551D130101FF040530030101FF300E0603551D0F0101FF040403020106301D0603551D0E041604147B5B45CFAFCECB7AFD31921A6AB6F346EB574850300D06092A864886F70D010105050003820101007911C04BB391B6FCF0E967D40D6E45BE55E893D2CE033FEDDA25B01D57CB1E3A76A04CEC5076E864720CA4A9F1B88BD6D68784BB32E54111C077D9B3609DEB1BD5D16E4444A9A601EC55621D77B85C8E48497C9C3B5711ACAD73378E2F785C906847D96060E6FC073D222017C4F716E9C4D872F9C8737CDF162F15A93EFD6A27B6A1EB5ABA981FD5E34D640A9D13C861BAF5391C87BAB8BD7B227FF6FEAC4079E5AC106F3D8F1B79768BC437B3211884E53600EB632099B9E9FE3304BB41C8C102F94463209E81CE42D3D63F2C76D3639C59DD8FA6E10EA02E41F72E9547CFBCFD33F3F60B617E7E912B8147C22730EEA7105D378F5C392BE404F07B8D568C68 | |||
| (PID) Process: | (2664) msiexec.exe | Key: | HKEY_USERS\S-1-5-21-1302019708-1500728564-335382590-1000_CLASSES\Local Settings\MuiCache\62\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (2664) msiexec.exe | Key: | HKEY_USERS\S-1-5-21-1302019708-1500728564-335382590-1000\Software\Microsoft\RestartManager\Session0000 |
| Operation: | write | Name: | Owner |
Value: 680A0000C0698F7C1731D501 | |||
| (PID) Process: | (2664) msiexec.exe | Key: | HKEY_USERS\S-1-5-21-1302019708-1500728564-335382590-1000\Software\Microsoft\RestartManager\Session0000 |
| Operation: | write | Name: | SessionHash |
Value: 31906118B73D9BD83ABA272967431BD014F86C1B83148DC99A32E6ADF6424674 | |||
| (PID) Process: | (2664) msiexec.exe | Key: | HKEY_USERS\S-1-5-21-1302019708-1500728564-335382590-1000\Software\Microsoft\RestartManager\Session0000 |
| Operation: | write | Name: | Sequence |
Value: 1 | |||
| (PID) Process: | (2664) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Installer\InProgress |
| Operation: | write | Name: | |
Value: C:\Windows\Installer\150c9e.ipi | |||
| (PID) Process: | (2664) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Installer\Folders |
| Operation: | write | Name: | C:\Config.Msi\ |
Value: | |||
| (PID) Process: | (2664) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Installer\Rollback\Scripts |
| Operation: | write | Name: | C:\Config.Msi\150c9f.rbs |
Value: 30748959 | |||
Executable files
97
Suspicious files
40
Text files
107
Unknown types
16
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3284 | setup.exe | C:\Users\admin\AppData\Local\Temp\Cab6EF.tmp | — | |
MD5:— | SHA256:— | |||
| 3284 | setup.exe | C:\Users\admin\AppData\Local\Temp\Tar6F0.tmp | — | |
MD5:— | SHA256:— | |||
| 3284 | setup.exe | C:\Users\admin\AppData\Local\Temp\Cab700.tmp | — | |
MD5:— | SHA256:— | |||
| 3284 | setup.exe | C:\Users\admin\AppData\Local\Temp\Tar701.tmp | — | |
MD5:— | SHA256:— | |||
| 3284 | setup.exe | C:\Users\admin\AppData\Local\Temp\Cab7BE.tmp | — | |
MD5:— | SHA256:— | |||
| 3284 | setup.exe | C:\Users\admin\AppData\Local\Temp\Tar7BF.tmp | — | |
MD5:— | SHA256:— | |||
| 2664 | msiexec.exe | C:\Users\admin\AppData\Local\Temp\CabD09.tmp | — | |
MD5:— | SHA256:— | |||
| 2664 | msiexec.exe | C:\Users\admin\AppData\Local\Temp\TarD0A.tmp | — | |
MD5:— | SHA256:— | |||
| 2664 | msiexec.exe | C:\Windows\Installer\MSIED1.tmp | — | |
MD5:— | SHA256:— | |||
| 2664 | msiexec.exe | C:\Windows\Installer\MSIEE2.tmp | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
66
TCP/UDP connections
29
DNS requests
9
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3456 | iexplore.exe | GET | 301 | 185.88.181.11:80 | http://xvideos.com/ | NL | — | — | whitelisted |
3456 | iexplore.exe | GET | 200 | 141.0.168.14:80 | http://static-ss.xvideos-cdn.com/v-01318270519/v3/fonts/skins/common/iconfont/iconfont.eot?itvls8 | NL | eot | 16.1 Kb | suspicious |
3456 | iexplore.exe | GET | 200 | 141.0.168.14:80 | http://static-ss.xvideos-cdn.com/v-5c81fae2fcc/v3/css/default/main2.css | NL | text | 19.7 Kb | suspicious |
3456 | iexplore.exe | GET | 200 | 185.88.181.5:80 | http://www.xvideos.com/ | NL | html | 39.0 Kb | whitelisted |
3284 | setup.exe | GET | 200 | 93.184.221.240:80 | http://www.download.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authrootstl.cab | US | compressed | 56.2 Kb | whitelisted |
3456 | iexplore.exe | GET | 200 | 141.0.168.14:80 | http://static-ss.xvideos-cdn.com/v-78a00364843/v3/js/skins/min/default.header.static.js | NL | text | 26.4 Kb | suspicious |
3456 | iexplore.exe | GET | 200 | 141.0.168.14:80 | http://static-ss.xvideos-cdn.com/v-5c81fae2fcc/v3/img/flags/flat/flags-16.png | NL | image | 13.0 Kb | suspicious |
3456 | iexplore.exe | GET | 200 | 141.0.168.14:80 | http://static-ss.xvideos-cdn.com/v-cf1dc178160/v3/js/i18n/front/english.js | NL | text | 12.8 Kb | suspicious |
3456 | iexplore.exe | GET | 200 | 141.0.168.14:80 | http://static-ss.xvideos-cdn.com/v3/img/skins/default/favicon.png | NL | image | 311 b | suspicious |
3456 | iexplore.exe | GET | 200 | 152.195.133.74:80 | http://img-egc.xvideos-cdn.com/videos/thumbs169/08/e1/fa/08e1fa612c406e7ca3315b85731024a4/08e1fa612c406e7ca3315b85731024a4.3.jpg | US | image | 8.81 Kb | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3456 | iexplore.exe | 209.197.3.84:80 | img-hw.xvideos-cdn.com | Highwinds Network Group, Inc. | US | suspicious |
3456 | iexplore.exe | 152.195.133.74:80 | img-egc.xvideos-cdn.com | MCI Communications Services, Inc. d/b/a Verizon Business | US | whitelisted |
3116 | iexplore.exe | 185.88.181.5:80 | xvideos.com | ServerStack, Inc. | NL | suspicious |
3456 | iexplore.exe | 141.0.168.14:80 | static-ss.xvideos-cdn.com | ServerStack, Inc. | NL | suspicious |
3456 | iexplore.exe | 185.88.181.5:80 | xvideos.com | ServerStack, Inc. | NL | suspicious |
3456 | iexplore.exe | 8.252.22.243:80 | img-l3.xvideos-cdn.com | Level 3 Communications, Inc. | US | malicious |
3456 | iexplore.exe | 195.181.170.25:443 | cdn77-pic.xvideos-cdn.com | Datacamp Limited | DE | suspicious |
3284 | setup.exe | 93.184.221.240:80 | www.download.windowsupdate.com | MCI Communications Services, Inc. d/b/a Verizon Business | US | whitelisted |
3116 | iexplore.exe | 204.79.197.200:80 | www.bing.com | Microsoft Corporation | US | whitelisted |
3456 | iexplore.exe | 185.88.181.11:80 | xvideos.com | ServerStack, Inc. | NL | suspicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
www.download.windowsupdate.com |
| whitelisted |
www.bing.com |
| whitelisted |
xvideos.com |
| whitelisted |
www.xvideos.com |
| whitelisted |
static-ss.xvideos-cdn.com |
| suspicious |
img-l3.xvideos-cdn.com |
| whitelisted |
img-egc.xvideos-cdn.com |
| unknown |
img-hw.xvideos-cdn.com |
| whitelisted |
cdn77-pic.xvideos-cdn.com |
| suspicious |