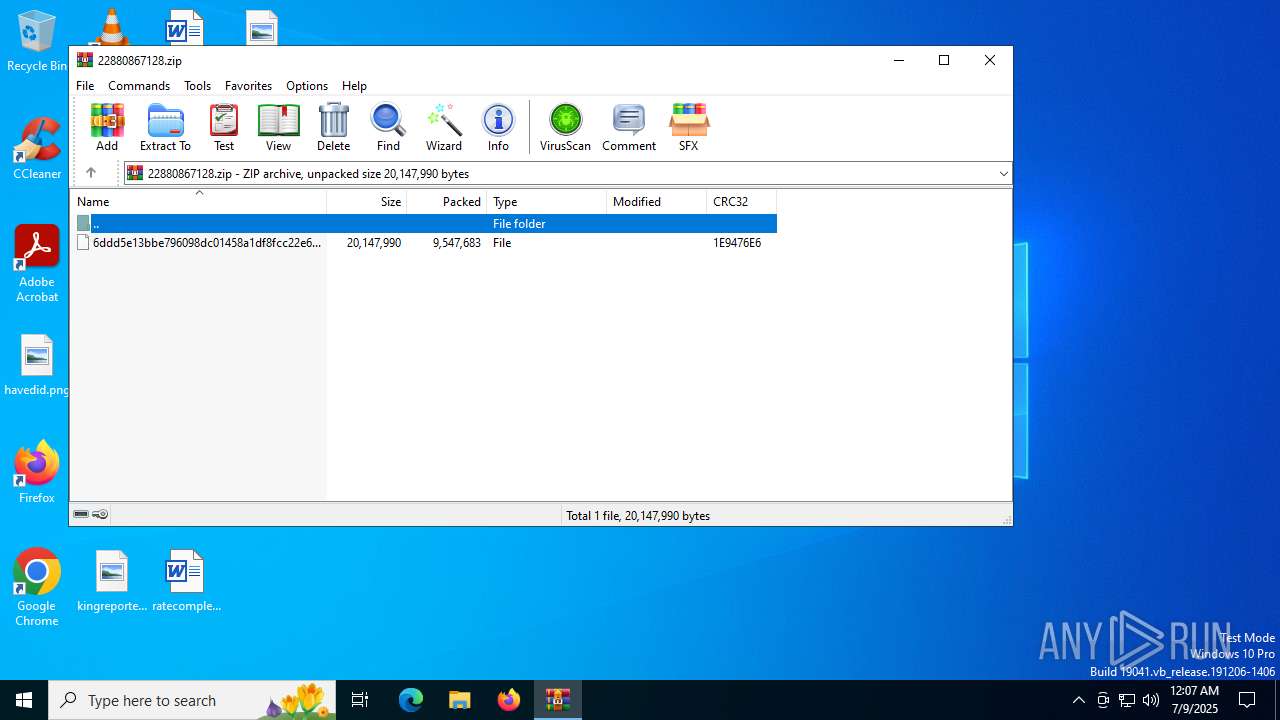
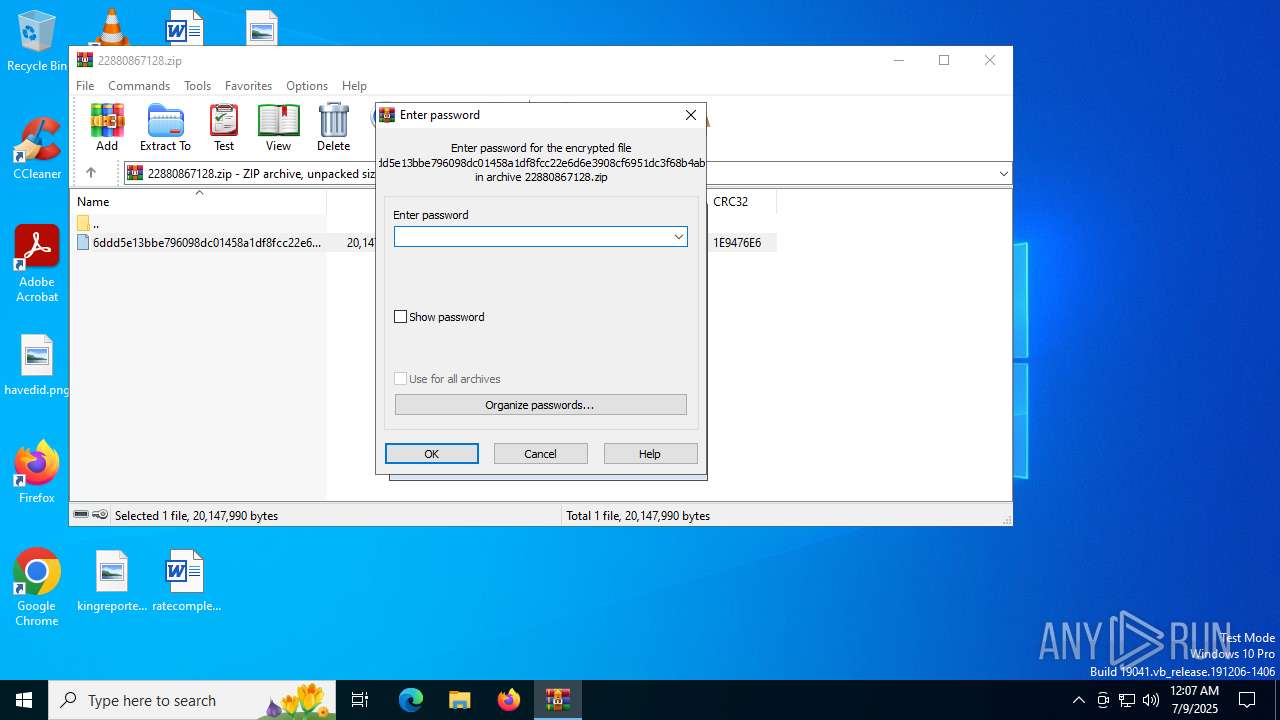
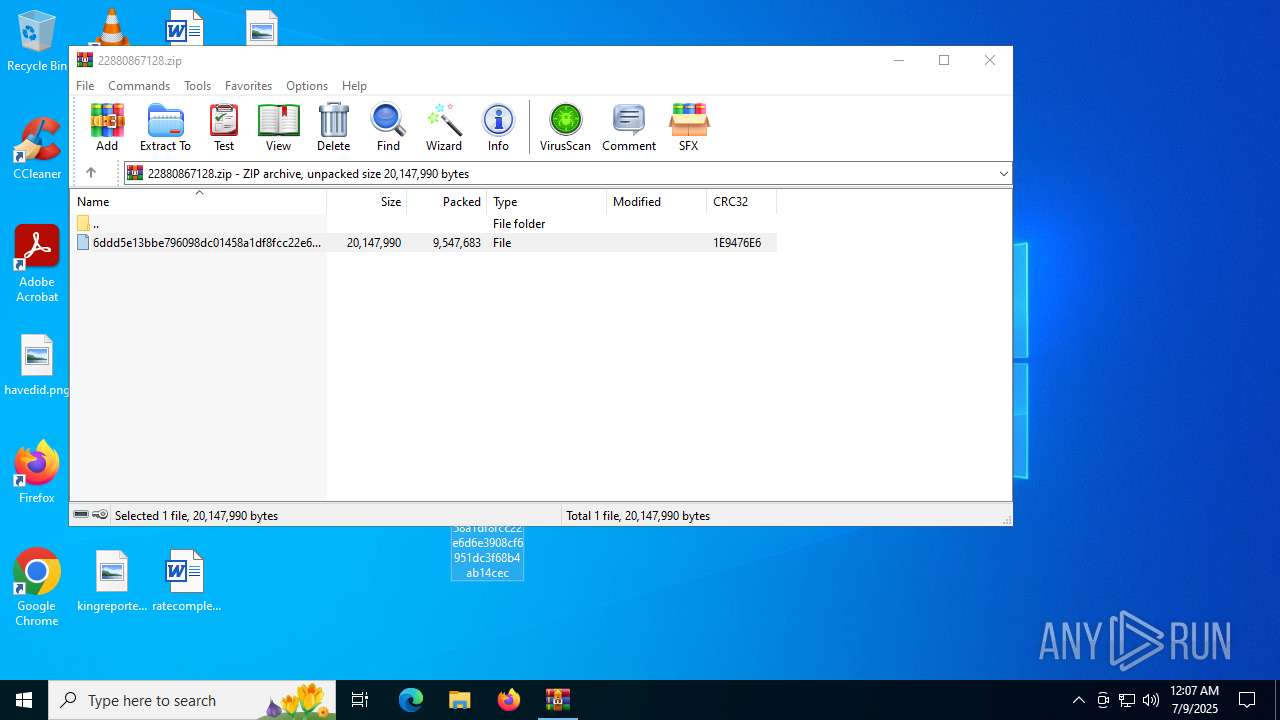
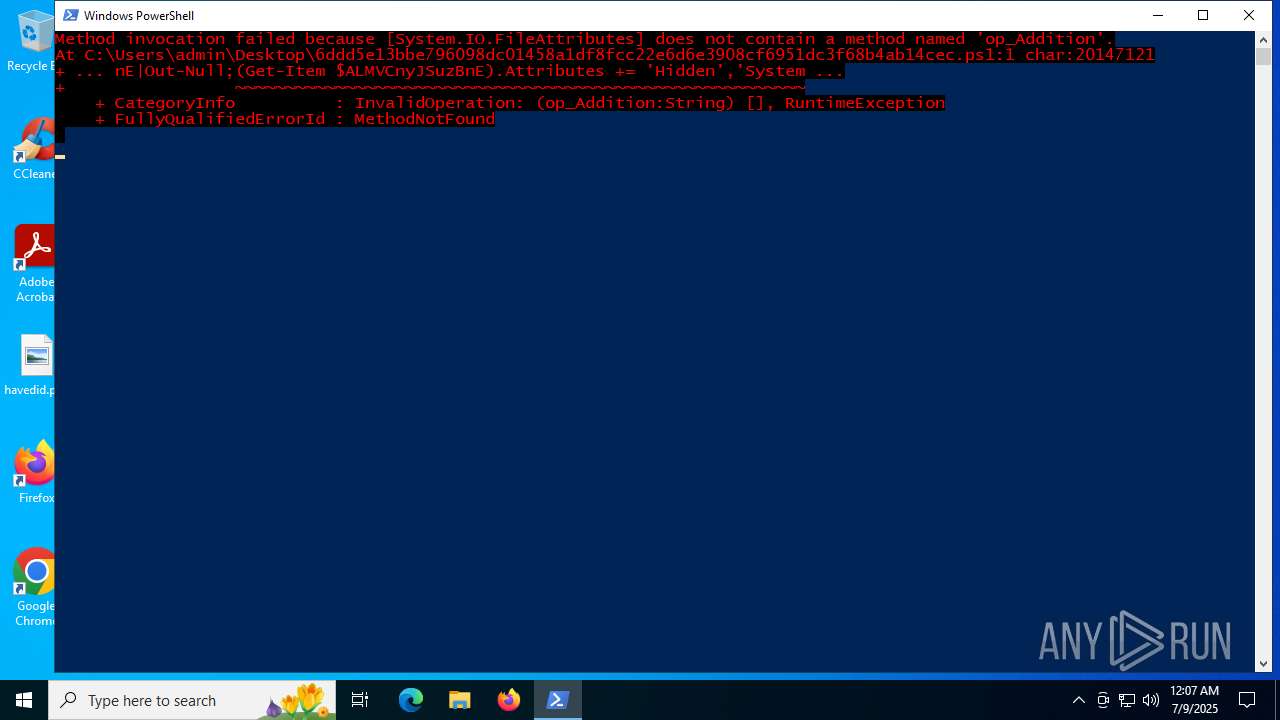
| File name: | 22880867128.zip |
| Full analysis: | https://app.any.run/tasks/f355af62-9d7f-4943-b803-1d92f615c95b |
| Verdict: | Malicious activity |
| Analysis date: | July 09, 2025, 00:07:00 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract, compression method=deflate |
| MD5: | 724C29FAE5338E887EBE666632A210EC |
| SHA1: | A1475BB69D9DA61DF6E607DA2E5B1D339CD235A0 |
| SHA256: | 8E44E63FBC23FCC12B9058163CF7BC221A450FD7975261D350EC0EDD669F7900 |
| SSDEEP: | 98304:1N6+fQj8D6KSZUdslQ6jtK1liRNi5DRVy/b/lHNmLkqZGuFcL9MtkBq3K4PbKGb1:d6lwC/CJwMu2I9U |
MALICIOUS
Bypass execution policy to execute commands
- powershell.exe (PID: 3944)
Changes the autorun value in the registry
- setup.exe (PID: 4456)
SUSPICIOUS
Uses base64 encoding (POWERSHELL)
- powershell.exe (PID: 3944)
Executable content was dropped or overwritten
- powershell.exe (PID: 3944)
- updater.exe (PID: 2032)
- updater.exe (PID: 3572)
- 138.0.7204.97_chrome_installer_uncompressed.exe (PID: 3880)
- setup.exe (PID: 4456)
- updater.exe (PID: 5960)
- updater.exe (PID: 1512)
The executable file from the user directory is run by the CMD process
- chrome.exe (PID: 6004)
Writes data into a file (POWERSHELL)
- powershell.exe (PID: 3944)
Executing commands from ".cmd" file
- powershell.exe (PID: 3944)
Reads security settings of Internet Explorer
- chrome.exe (PID: 6004)
- updater.exe (PID: 2032)
Starts CMD.EXE for commands execution
- powershell.exe (PID: 3944)
Application launched itself
- chrome.exe (PID: 6004)
- updater.exe (PID: 2032)
- updater.exe (PID: 3572)
- updater.exe (PID: 3704)
- setup.exe (PID: 4456)
- setup.exe (PID: 5288)
- updater.exe (PID: 5960)
- updater.exe (PID: 1512)
Executes as Windows Service
- updater.exe (PID: 3572)
- updater.exe (PID: 3704)
- updater.exe (PID: 5960)
Creates a software uninstall entry
- setup.exe (PID: 4456)
Searches for installed software
- setup.exe (PID: 4456)
INFO
Manual execution by a user
- powershell.exe (PID: 3944)
- chrome.exe (PID: 5600)
Script raised an exception (POWERSHELL)
- powershell.exe (PID: 3944)
The sample compiled with english language support
- powershell.exe (PID: 3944)
- updater.exe (PID: 2032)
- updater.exe (PID: 3572)
- 138.0.7204.97_chrome_installer_uncompressed.exe (PID: 3880)
- setup.exe (PID: 4456)
- updater.exe (PID: 5960)
- updater.exe (PID: 1512)
Checks supported languages
- chrome.exe (PID: 4372)
- chrome.exe (PID: 6004)
- updater.exe (PID: 2032)
- updater.exe (PID: 3572)
- updater.exe (PID: 1512)
- updater.exe (PID: 3580)
- updater.exe (PID: 3704)
- updater.exe (PID: 3388)
- 138.0.7204.97_chrome_installer_uncompressed.exe (PID: 3880)
- setup.exe (PID: 4456)
- setup.exe (PID: 3668)
- setup.exe (PID: 5288)
- setup.exe (PID: 5768)
- elevation_service.exe (PID: 4324)
- updater.exe (PID: 7116)
- updater.exe (PID: 5960)
- UpdaterSetup.exe (PID: 3936)
- updater.exe (PID: 756)
- updater.exe (PID: 1512)
Reads the computer name
- chrome.exe (PID: 6004)
- chrome.exe (PID: 4372)
- updater.exe (PID: 2032)
- updater.exe (PID: 3572)
- updater.exe (PID: 3704)
- 138.0.7204.97_chrome_installer_uncompressed.exe (PID: 3880)
- setup.exe (PID: 4456)
- setup.exe (PID: 5288)
- elevation_service.exe (PID: 4324)
- updater.exe (PID: 5960)
- updater.exe (PID: 1512)
Process checks computer location settings
- chrome.exe (PID: 6004)
Create files in a temporary directory
- chrome.exe (PID: 4372)
- updater.exe (PID: 2032)
Creates files in the program directory
- updater.exe (PID: 1512)
- updater.exe (PID: 2032)
- updater.exe (PID: 3572)
- updater.exe (PID: 3704)
- setup.exe (PID: 4456)
- setup.exe (PID: 5288)
- updater.exe (PID: 5960)
- updater.exe (PID: 1512)
- updater.exe (PID: 756)
Process checks whether UAC notifications are on
- updater.exe (PID: 2032)
- updater.exe (PID: 3572)
- updater.exe (PID: 3704)
- updater.exe (PID: 5960)
- updater.exe (PID: 1512)
Reads the software policy settings
- updater.exe (PID: 2032)
- updater.exe (PID: 3704)
- updater.exe (PID: 5960)
- slui.exe (PID: 320)
Reads the machine GUID from the registry
- updater.exe (PID: 2032)
Checks proxy server information
- updater.exe (PID: 2032)
- slui.exe (PID: 320)
Creates files or folders in the user directory
- updater.exe (PID: 2032)
Launching a file from a Registry key
- setup.exe (PID: 4456)
Application launched itself
- chrome.exe (PID: 5600)
Executes as Windows Service
- elevation_service.exe (PID: 4324)
Connects to unusual port
- chrome.exe (PID: 1216)
Converts byte array into ASCII string (POWERSHELL)
- powershell.exe (PID: 3944)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | 0x0009 |
| ZipCompression: | Deflated |
| ZipModifyDate: | 1980:00:00 00:00:00 |
| ZipCRC: | 0x1e9476e6 |
| ZipCompressedSize: | 9547683 |
| ZipUncompressedSize: | 20147990 |
| ZipFileName: | 6ddd5e13bbe796098dc01458a1df8fcc22e6d6e3908cf6951dc3f68b4ab14cec |
Total processes
215
Monitored processes
71
Malicious processes
4
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 236 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=unzip.mojom.Unzipper --lang=en-US --service-sandbox-type=service --disable-quic --force-high-res-timeticks=disabled --field-trial-handle=508,i,16961385965078290687,8397202734358535627,262144 --variations-seed-version --mojo-platform-channel-handle=6692 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 138.0.7204.97 Modules
| |||||||||||||||
| 320 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 756 | C:\WINDOWS\SystemTemp\Google3936_657751466\bin\updater.exe --crash-handler --system "--database=C:\Program Files (x86)\Google\GoogleUpdater\140.0.7272.0\Crashpad" --url=https://clients2.google.com/cr/report --annotation=prod=Update4 --annotation=ver=140.0.7272.0 "--attachment=C:\Program Files (x86)\Google\GoogleUpdater\updater.log" --initial-client-data=0x258,0x25c,0x260,0x234,0x264,0x7ff617ce1a78,0x7ff617ce1a84,0x7ff617ce1a90 | C:\Windows\SystemTemp\Google3936_657751466\bin\updater.exe | — | updater.exe | |||||||||||
User: SYSTEM Company: Google LLC Integrity Level: SYSTEM Description: Google Updater (x64) Exit code: 0 Version: 140.0.7272.0 Modules
| |||||||||||||||
| 984 | C:\WINDOWS\system32\cmd.exe /c ""C:\Users\admin\AppData\Local\Temp\tmpB323.cmd" " | C:\Windows\System32\cmd.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1212 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1216 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=network.mojom.NetworkService --lang=en-US --service-sandbox-type=none --disable-quic --force-high-res-timeticks=disabled --field-trial-handle=508,i,16961385965078290687,8397202734358535627,262144 --variations-seed-version --mojo-platform-channel-handle=2188 /prefetch:3 | C:\Program Files\Google\Chrome\Application\chrome.exe | chrome.exe | ||||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Version: 138.0.7204.97 Modules
| |||||||||||||||
| 1332 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=quarantine.mojom.Quarantine --lang=en-US --service-sandbox-type=none --disable-quic --force-high-res-timeticks=disabled --field-trial-handle=508,i,16961385965078290687,8397202734358535627,262144 --variations-seed-version --mojo-platform-channel-handle=6804 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 138.0.7204.97 Modules
| |||||||||||||||
| 1380 | "C:\Program Files\WinRAR\WinRAR.exe" C:\Users\admin\AppData\Local\Temp\22880867128.zip | C:\Program Files\WinRAR\WinRAR.exe | — | explorer.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 1512 | C:\Users\admin\AppData\Local\Temp\Google4372_647670890\bin\updater.exe --crash-handler --system "--database=C:\Program Files (x86)\Google\GoogleUpdater\138.0.7194.0\Crashpad" --url=https://clients2.google.com/cr/report --annotation=prod=Update4 --annotation=ver=138.0.7194.0 "--attachment=C:\Program Files (x86)\Google\GoogleUpdater\updater.log" --initial-client-data=0x2a8,0x2ac,0x2b0,0x100,0x2b4,0xdf29c0,0xdf29cc,0xdf29d8 | C:\Users\admin\AppData\Local\Temp\Google4372_647670890\bin\updater.exe | — | updater.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: HIGH Description: Google Updater (x86) Exit code: 0 Version: 138.0.7194.0 Modules
| |||||||||||||||
| 1512 | "C:\WINDOWS\SystemTemp\Google3936_657751466\bin\updater.exe" --enable-ceca-experiment --update --system --enable-logging --vmodule=*/chrome/updater/*=2 | C:\Windows\SystemTemp\Google3936_657751466\bin\updater.exe | — | UpdaterSetup.exe | |||||||||||
User: SYSTEM Company: Google LLC Integrity Level: SYSTEM Description: Google Updater (x64) Exit code: 0 Version: 140.0.7272.0 Modules
| |||||||||||||||
Total events
27 648
Read events
27 432
Write events
197
Delete events
19
Modification events
| (PID) Process: | (1380) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (1380) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (1380) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (1380) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (1380) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (1380) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\22880867128.zip | |||
| (PID) Process: | (1380) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (1380) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (1380) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (1380) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
Executable files
11
Suspicious files
223
Text files
84
Unknown types
239
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1380 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb1380.44214\6ddd5e13bbe796098dc01458a1df8fcc22e6d6e3908cf6951dc3f68b4ab14cec | — | |
MD5:— | SHA256:— | |||
| 4372 | chrome.exe | C:\Users\admin\AppData\Local\Temp\Google4372_1285956141\UPDATER.PACKED.7Z | — | |
MD5:— | SHA256:— | |||
| 3944 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\590aee7bdd69b59b.customDestinations-ms | binary | |
MD5:BFF9D4070B1C2F1B2EE11693C921F0B8 | SHA256:6E4680AFDC91CFC72C72E7955562F22DF55F3ACB79697478BC2BA8059DFE35E6 | |||
| 3944 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_eh24wku3.k2i.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 3944 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\RN5EYINIFOVRCDCQVYF7.temp | binary | |
MD5:BFF9D4070B1C2F1B2EE11693C921F0B8 | SHA256:6E4680AFDC91CFC72C72E7955562F22DF55F3ACB79697478BC2BA8059DFE35E6 | |||
| 2032 | updater.exe | C:\Program Files (x86)\Google\GoogleUpdater\updater.log | text | |
MD5:5B70D9B442B83B0DC6881702738DBAA1 | SHA256:711292F761A776C350CE88775C09372C5FB5B6CD9C20B3965B1EC38533556D0D | |||
| 2032 | updater.exe | C:\Program Files (x86)\Google\GoogleUpdater\138.0.7194.0\updater.exe | executable | |
MD5:A1044445F76098186DE3B146ABDA9876 | SHA256:8CA4F944172F0904B4D70E40A5D61B54439109502E7E3E20D71F8A83BEAD9CE8 | |||
| 3944 | powershell.exe | C:\Users\admin\AppData\Local\Temp\tmpB323.cmd | text | |
MD5:30D9AA7B36B406647A4C48B28E946FE6 | SHA256:1E48A7D1C9D06913209FE958433C3ED4E9DF4769EAF3496DA718CA7053F0A141 | |||
| 3944 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_inm5q300.spr.psm1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 2032 | updater.exe | C:\Program Files (x86)\Google\GoogleUpdater\138.0.7194.0\uninstall.cmd | text | |
MD5:FBC297EE9060D4256192E4EDB98CAD1B | SHA256:099592FFA867124D16C0C6D868AF1214FD2B7180FA76E4EEE01ABF2A5CF8F044 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
32
TCP/UDP connections
73
DNS requests
79
Threats
3
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1268 | svchost.exe | GET | 200 | 2.20.245.136:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
1268 | svchost.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
2148 | svchost.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
5824 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
5824 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
2032 | updater.exe | GET | 200 | 216.58.206.67:80 | http://c.pki.goog/r/gsr1.crl | unknown | — | — | whitelisted |
2032 | updater.exe | GET | 200 | 216.58.206.67:80 | http://c.pki.goog/r/r4.crl | unknown | — | — | whitelisted |
3704 | updater.exe | GET | — | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/diffgen-puffin/%7B8a69d345-d564-463c-aff1-a69d9e530f96%7D/f11035a609826e842104c6a00f39912a0d6a8ea396d32d9c6dc7fa62167cab8a | unknown | — | — | whitelisted |
2032 | updater.exe | GET | 200 | 142.250.186.131:80 | http://o.pki.goog/we2/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTuMJxAT2trYla0jia%2F5EUSmLrk3QQUdb7Ed66J9kQ3fc%2BxaB8dGuvcNFkCECdz283NVEpjCi5UeCEUBvs%3D | unknown | — | — | whitelisted |
1216 | chrome.exe | GET | 200 | 142.250.186.46:80 | http://clients2.google.com/time/1/current?cup2key=9:9abD5mSgzU1mQgG3JYnC5mVI5rmxtNh8lNE5x0qF2uk&cup2hreq=e3b0c44298fc1c149afbf4c8996fb92427ae41e4649b934ca495991b7852b855 | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
1268 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
5944 | MoUsoCoreWorker.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
3936 | RUXIMICS.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1268 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
1268 | svchost.exe | 2.20.245.136:80 | crl.microsoft.com | Akamai International B.V. | NL | whitelisted |
1268 | svchost.exe | 95.101.149.131:80 | www.microsoft.com | Akamai International B.V. | NL | whitelisted |
2148 | svchost.exe | 20.190.159.68:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
2148 | svchost.exe | 2.23.77.188:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
nexusrules.officeapps.live.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
update.googleapis.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
— | — | Unknown Traffic | ET USER_AGENTS Microsoft Dr Watson User-Agent (MSDW) |
1216 | chrome.exe | Not Suspicious Traffic | INFO [ANY.RUN] Google Tag Manager analytics (googletagmanager .com) |
1216 | chrome.exe | Not Suspicious Traffic | INFO [ANY.RUN] Google Tag Manager analytics (googletagmanager .com) |
Process | Message |
|---|---|
chrome.exe | I0000 00:00:1752019703.732019 1180 voice_transcription.cc:58] Registering VoiceTranscriptionCapability
|