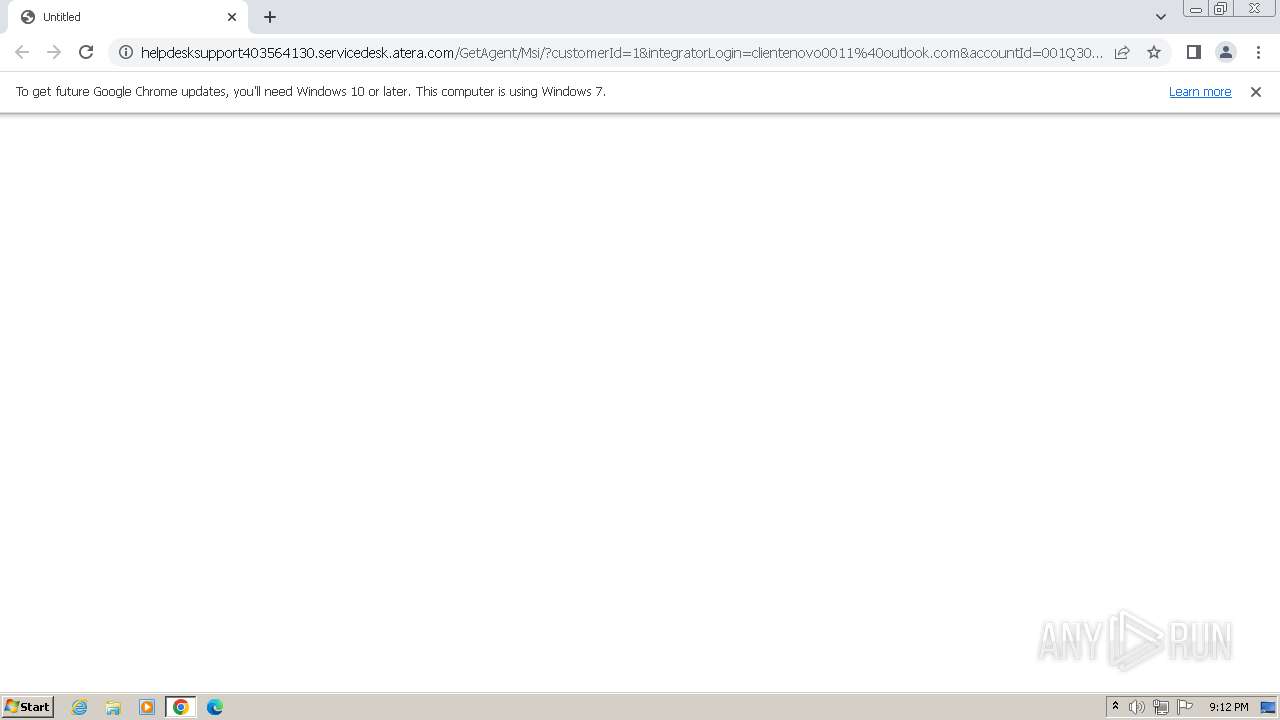
| URL: | https://HelpdeskSupport403564130.servicedesk.atera.com/GetAgent/Msi/?customerId=1&integratorLogin=clientenovo0011%40outlook.com&accountId=001Q3000002mS8vIAE |
| Full analysis: | https://app.any.run/tasks/cccd0e8f-3ce1-481a-9af2-4d1f501c3735 |
| Verdict: | Malicious activity |
| Analysis date: | December 04, 2023, 21:11:20 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MD5: | 8F7186C625B32B6C5589CD6B08DE717B |
| SHA1: | 48F75A716942E79C83E5D7033106A5B33436D70E |
| SHA256: | 8E349233E6252C61948B86E973C6E054CE8CC3D6A665AE95BF95C4E89F3C251A |
| SSDEEP: | 3:N8D46VVKnBd1VJJUyG6lK1s9HACUl0TAAKT6UvVKJG8R/a42VVGkg:2D3VgnLN6yblKu9HAL6AbNK1/Qxg |
MALICIOUS
Starts NET.EXE for service management
- msiexec.exe (PID: 2852)
- net.exe (PID: 3232)
Creates a writable file in the system directory
- AteraAgent.exe (PID: 3660)
- AteraAgent.exe (PID: 3304)
- msiexec.exe (PID: 2092)
- SRManager.exe (PID: 3568)
- SRServer.exe (PID: 1152)
Drops the executable file immediately after the start
- AteraAgent.exe (PID: 3304)
- msiexec.exe (PID: 1928)
- AgentPackageTicketing.exe (PID: 544)
- AgentPackageUpgradeAgent.exe (PID: 3832)
- AteraAgent.exe (PID: 2428)
- SplashtopStreamer.exe (PID: 1992)
- PreVerCheck.exe (PID: 1028)
- msiexec.exe (PID: 2092)
- SetupUtil.exe (PID: 1592)
- Splashtop_Software_Updater.exe (PID: 3668)
- uninst.exe (PID: 1128)
- Au_.exe (PID: 448)
Accesses system services(Win32_Service) via WMI (SCRIPT)
- cscript.exe (PID: 2248)
- cscript.exe (PID: 4056)
- cscript.exe (PID: 916)
- cscript.exe (PID: 3472)
- cscript.exe (PID: 3196)
- cscript.exe (PID: 2248)
- cscript.exe (PID: 680)
SUSPICIOUS
Process drops legitimate windows executable
- chrome.exe (PID: 280)
- rundll32.exe (PID: 2440)
- msiexec.exe (PID: 1928)
- AteraAgent.exe (PID: 2428)
- AgentPackageUpgradeAgent.exe (PID: 3832)
Executes as Windows Service
- VSSVC.exe (PID: 3800)
- AteraAgent.exe (PID: 3304)
- AteraAgent.exe (PID: 2428)
- SSUService.exe (PID: 1860)
- SRService.exe (PID: 3648)
Checks Windows Trust Settings
- msiexec.exe (PID: 1928)
- AteraAgent.exe (PID: 3660)
- SRManager.exe (PID: 3568)
Uses RUNDLL32.EXE to load library
- msiexec.exe (PID: 1828)
Uses TASKKILL.EXE to kill process
- msiexec.exe (PID: 2852)
- cmd.exe (PID: 3872)
- cmd.exe (PID: 904)
- cmd.exe (PID: 2852)
- cmd.exe (PID: 600)
- cmd.exe (PID: 2968)
- cmd.exe (PID: 2948)
- cmd.exe (PID: 3372)
- cmd.exe (PID: 4080)
Starts SC.EXE for service management
- AteraAgent.exe (PID: 3304)
- AteraAgent.exe (PID: 2428)
- cmd.exe (PID: 3972)
- cmd.exe (PID: 3660)
Starts CMD.EXE for commands execution
- AgentPackageAgentInformation.exe (PID: 3908)
- AgentPackageAgentInformation.exe (PID: 2508)
- AgentPackageAgentInformation.exe (PID: 1640)
- AgentPackageAgentInformation.exe (PID: 2648)
- msiexec.exe (PID: 2092)
- SetupUtil.exe (PID: 1592)
- SRServer.exe (PID: 1152)
Searches for installed software
- AgentPackageAgentInformation.exe (PID: 1640)
- AgentPackageAgentInformation.exe (PID: 2508)
- AgentPackageAgentInformation.exe (PID: 3908)
- AgentPackageProgramManagement.exe (PID: 2028)
- AgentPackageAgentInformation.exe (PID: 2648)
The process executes VB scripts
- cmd.exe (PID: 752)
- cmd.exe (PID: 3664)
- cmd.exe (PID: 3380)
- cmd.exe (PID: 2232)
- cmd.exe (PID: 668)
- cmd.exe (PID: 3348)
- cmd.exe (PID: 2720)
Gets a collection of all available drive names (SCRIPT)
- cscript.exe (PID: 2248)
- cscript.exe (PID: 4056)
- cscript.exe (PID: 916)
- cscript.exe (PID: 3196)
- cscript.exe (PID: 3472)
- cscript.exe (PID: 2248)
- cscript.exe (PID: 680)
Gets full path of the running script (SCRIPT)
- cscript.exe (PID: 916)
- cscript.exe (PID: 4056)
- cscript.exe (PID: 2248)
- cscript.exe (PID: 3196)
- cscript.exe (PID: 3472)
- cscript.exe (PID: 2248)
- cscript.exe (PID: 680)
Checks whether a specific file exists (SCRIPT)
- cscript.exe (PID: 4056)
- cscript.exe (PID: 916)
- cscript.exe (PID: 2248)
- cscript.exe (PID: 3472)
- cscript.exe (PID: 3196)
- cscript.exe (PID: 2248)
- cscript.exe (PID: 680)
Creates FileSystem object to access computer's file system (SCRIPT)
- cscript.exe (PID: 2248)
- cscript.exe (PID: 4056)
- cscript.exe (PID: 916)
- cscript.exe (PID: 3196)
- cscript.exe (PID: 2248)
- cscript.exe (PID: 3472)
- cscript.exe (PID: 680)
Accesses computer name via WMI (SCRIPT)
- cscript.exe (PID: 916)
- cscript.exe (PID: 2248)
- cscript.exe (PID: 4056)
- cscript.exe (PID: 3196)
- cscript.exe (PID: 3472)
- cscript.exe (PID: 2248)
- cscript.exe (PID: 680)
Gets the drive type (SCRIPT)
- cscript.exe (PID: 4056)
- cscript.exe (PID: 916)
- cscript.exe (PID: 2248)
- cscript.exe (PID: 3196)
- cscript.exe (PID: 3472)
- cscript.exe (PID: 2248)
- cscript.exe (PID: 680)
Accesses WMI object, sets custom ImpersonationLevel (SCRIPT)
- cscript.exe (PID: 916)
- cscript.exe (PID: 4056)
- cscript.exe (PID: 2248)
- cscript.exe (PID: 3472)
- cscript.exe (PID: 3196)
- cscript.exe (PID: 2248)
- cscript.exe (PID: 680)
Executes WMI query (SCRIPT)
- cscript.exe (PID: 916)
- cscript.exe (PID: 2248)
- cscript.exe (PID: 4056)
- cscript.exe (PID: 3472)
- cscript.exe (PID: 3196)
- cscript.exe (PID: 2248)
- cscript.exe (PID: 680)
Accesses OperatingSystem(Win32_OperatingSystem) via WMI (SCRIPT)
- cscript.exe (PID: 916)
- cscript.exe (PID: 4056)
- cscript.exe (PID: 2248)
The process creates files with name similar to system file names
- AteraAgent.exe (PID: 2428)
- msiexec.exe (PID: 1928)
- Splashtop_Software_Updater.exe (PID: 3668)
- Au_.exe (PID: 448)
Starts itself from another location
- AgentPackageUpgradeAgent.exe (PID: 3832)
- uninst.exe (PID: 1128)
Reads the Windows owner or organization settings
- msiexec.exe (PID: 1928)
Drops a system driver (possible attempt to evade defenses)
- msiexec.exe (PID: 1928)
Uses REG/REGEDIT.EXE to modify registry
- msiexec.exe (PID: 2092)
Creates/Modifies COM task schedule object
- SRService.exe (PID: 3540)
Creates or modifies Windows services
- SRManager.exe (PID: 3568)
INFO
Manual execution by a user
- wmpnscfg.exe (PID: 3944)
Application launched itself
- chrome.exe (PID: 280)
- msiexec.exe (PID: 1928)
Checks supported languages
- wmpnscfg.exe (PID: 3944)
- msiexec.exe (PID: 1928)
- msiexec.exe (PID: 1828)
- AteraAgent.exe (PID: 3660)
- msiexec.exe (PID: 2852)
- AteraAgent.exe (PID: 3304)
- AgentPackageAgentInformation.exe (PID: 1860)
- AgentPackageAgentInformation.exe (PID: 2688)
- AgentPackageAgentInformation.exe (PID: 1036)
- AgentPackageAgentInformation.exe (PID: 3004)
- AgentPackageAgentInformation.exe (PID: 2508)
- AteraAgent.exe (PID: 2428)
- AgentPackageAgentInformation.exe (PID: 3908)
- AgentPackageAgentInformation.exe (PID: 1640)
- AgentPackageSTRemote.exe (PID: 944)
- AgentPackageADRemote.exe (PID: 1416)
- AgentPackageTicketing.exe (PID: 544)
- AgentPackageProgramManagement.exe (PID: 2028)
- AgentPackageOsUpdates.exe (PID: 300)
- AgentPackageInternalPoller.exe (PID: 3704)
- AgentPackageUpgradeAgent.exe (PID: 3340)
- AgentPackageSystemTools.exe (PID: 3876)
- AgentPackageUpgradeAgent.exe (PID: 3832)
- AgentPackageHeartbeat.exe (PID: 2692)
- AgentPackageMarketplace.exe (PID: 2940)
- AgentPackageAgentInformation.exe (PID: 2648)
- AgentPackageRuntimeInstaller.exe (PID: 2840)
- AgentPackageHeartbeat.exe (PID: 3116)
- SplashtopStreamer.exe (PID: 1992)
- AgentPackageHeartbeat.exe (PID: 276)
- PreVerCheck.exe (PID: 1028)
- msiexec.exe (PID: 2092)
- AgentPackageHeartbeat.exe (PID: 2688)
- AgentPackageInternalPoller.exe (PID: 3008)
- AgentPackageHeartbeat.exe (PID: 3088)
- SetupUtil.exe (PID: 3268)
- SetupUtil.exe (PID: 2128)
- SetupUtil.exe (PID: 1592)
- SRSelfSignCertUtil.exe (PID: 2776)
- Splashtop_Software_Updater.exe (PID: 3668)
- SSUService.exe (PID: 1860)
- SRService.exe (PID: 3540)
- SRService.exe (PID: 3220)
- SRManager.exe (PID: 3568)
- SRServer.exe (PID: 1152)
- SRService.exe (PID: 3648)
- SRAppPB.exe (PID: 2840)
- SRFeature.exe (PID: 2060)
- uninst.exe (PID: 1128)
- Au_.exe (PID: 448)
- SRAgent.exe (PID: 1864)
- SRUtility.exe (PID: 2348)
- BdEpSDK_x86.exe (PID: 3044)
- SRVirtualDisplay.exe (PID: 2456)
- AgentPackageHeartbeat.exe (PID: 1348)
- AgentPackageHeartbeat.exe (PID: 3684)
- SRDetect.exe (PID: 3804)
- SRUtility.exe (PID: 3976)
- AgentPackageHeartbeat.exe (PID: 2676)
Reads the computer name
- wmpnscfg.exe (PID: 3944)
- msiexec.exe (PID: 1928)
- msiexec.exe (PID: 1828)
- msiexec.exe (PID: 2852)
- AteraAgent.exe (PID: 3660)
- AteraAgent.exe (PID: 3304)
- AgentPackageAgentInformation.exe (PID: 2688)
- AgentPackageAgentInformation.exe (PID: 1860)
- AgentPackageAgentInformation.exe (PID: 1036)
- AgentPackageAgentInformation.exe (PID: 3004)
- AgentPackageAgentInformation.exe (PID: 2508)
- AteraAgent.exe (PID: 2428)
- AgentPackageAgentInformation.exe (PID: 3908)
- AgentPackageAgentInformation.exe (PID: 1640)
- AgentPackageSTRemote.exe (PID: 944)
- AgentPackageADRemote.exe (PID: 1416)
- AgentPackageTicketing.exe (PID: 544)
- AgentPackageProgramManagement.exe (PID: 2028)
- AgentPackageOsUpdates.exe (PID: 300)
- AgentPackageInternalPoller.exe (PID: 3704)
- AgentPackageUpgradeAgent.exe (PID: 3832)
- AgentPackageSystemTools.exe (PID: 3876)
- AgentPackageUpgradeAgent.exe (PID: 3340)
- AgentPackageHeartbeat.exe (PID: 2692)
- AgentPackageRuntimeInstaller.exe (PID: 2840)
- AgentPackageAgentInformation.exe (PID: 2648)
- AgentPackageMarketplace.exe (PID: 2940)
- AgentPackageHeartbeat.exe (PID: 3116)
- AgentPackageHeartbeat.exe (PID: 2688)
- AgentPackageHeartbeat.exe (PID: 276)
- SplashtopStreamer.exe (PID: 1992)
- msiexec.exe (PID: 2092)
- SetupUtil.exe (PID: 2128)
- SetupUtil.exe (PID: 3268)
- SetupUtil.exe (PID: 1592)
- AgentPackageInternalPoller.exe (PID: 3008)
- AgentPackageHeartbeat.exe (PID: 3088)
- SRSelfSignCertUtil.exe (PID: 2776)
- Splashtop_Software_Updater.exe (PID: 3668)
- SSUService.exe (PID: 1860)
- SRService.exe (PID: 3540)
- SRService.exe (PID: 3648)
- SRManager.exe (PID: 3568)
- SRServer.exe (PID: 1152)
- SRService.exe (PID: 3220)
- SRAppPB.exe (PID: 2840)
- SRFeature.exe (PID: 2060)
- uninst.exe (PID: 1128)
- Au_.exe (PID: 448)
- SRAgent.exe (PID: 1864)
- AgentPackageHeartbeat.exe (PID: 1348)
- AgentPackageHeartbeat.exe (PID: 3684)
- AgentPackageHeartbeat.exe (PID: 2676)
Drops the executable file immediately after the start
- chrome.exe (PID: 280)
- rundll32.exe (PID: 2440)
The process uses the downloaded file
- chrome.exe (PID: 3608)
- chrome.exe (PID: 1784)
- chrome.exe (PID: 280)
- chrome.exe (PID: 3596)
- chrome.exe (PID: 1276)
Reads security settings of Internet Explorer
- msiexec.exe (PID: 1600)
Reads the machine GUID from the registry
- msiexec.exe (PID: 1928)
- msiexec.exe (PID: 2852)
- AteraAgent.exe (PID: 3660)
- msiexec.exe (PID: 1828)
- AteraAgent.exe (PID: 3304)
- AgentPackageAgentInformation.exe (PID: 1860)
- AgentPackageAgentInformation.exe (PID: 3004)
- AgentPackageAgentInformation.exe (PID: 1036)
- AgentPackageAgentInformation.exe (PID: 2508)
- AgentPackageAgentInformation.exe (PID: 2688)
- AgentPackageAgentInformation.exe (PID: 3908)
- AgentPackageAgentInformation.exe (PID: 1640)
- AteraAgent.exe (PID: 2428)
- AgentPackageSTRemote.exe (PID: 944)
- AgentPackageADRemote.exe (PID: 1416)
- AgentPackageTicketing.exe (PID: 544)
- AgentPackageProgramManagement.exe (PID: 2028)
- AgentPackageUpgradeAgent.exe (PID: 3832)
- AgentPackageSystemTools.exe (PID: 3876)
- AgentPackageInternalPoller.exe (PID: 3704)
- AgentPackageUpgradeAgent.exe (PID: 3340)
- AgentPackageHeartbeat.exe (PID: 2692)
- AgentPackageMarketplace.exe (PID: 2940)
- AgentPackageRuntimeInstaller.exe (PID: 2840)
- AgentPackageAgentInformation.exe (PID: 2648)
- AgentPackageHeartbeat.exe (PID: 3116)
- AgentPackageHeartbeat.exe (PID: 2688)
- AgentPackageHeartbeat.exe (PID: 276)
- msiexec.exe (PID: 2092)
- SetupUtil.exe (PID: 1592)
- AgentPackageHeartbeat.exe (PID: 3088)
- AgentPackageInternalPoller.exe (PID: 3008)
- SRSelfSignCertUtil.exe (PID: 2776)
- SRManager.exe (PID: 3568)
- SSUService.exe (PID: 1860)
- SRAgent.exe (PID: 1864)
- AgentPackageHeartbeat.exe (PID: 1348)
- AgentPackageHeartbeat.exe (PID: 2676)
- AgentPackageHeartbeat.exe (PID: 3684)
- AgentPackageOsUpdates.exe (PID: 300)
Create files in a temporary directory
- msiexec.exe (PID: 1928)
- rundll32.exe (PID: 2440)
Reads Environment values
- AteraAgent.exe (PID: 3660)
- AteraAgent.exe (PID: 3304)
- AgentPackageAgentInformation.exe (PID: 1036)
- AgentPackageAgentInformation.exe (PID: 3004)
- AgentPackageAgentInformation.exe (PID: 2508)
- AgentPackageAgentInformation.exe (PID: 2688)
- AgentPackageAgentInformation.exe (PID: 1860)
- AgentPackageAgentInformation.exe (PID: 3908)
- AgentPackageAgentInformation.exe (PID: 1640)
- AteraAgent.exe (PID: 2428)
- AgentPackageSTRemote.exe (PID: 944)
- AgentPackageADRemote.exe (PID: 1416)
- AgentPackageTicketing.exe (PID: 544)
- AgentPackageProgramManagement.exe (PID: 2028)
- AgentPackageOsUpdates.exe (PID: 300)
- AgentPackageInternalPoller.exe (PID: 3704)
- AgentPackageUpgradeAgent.exe (PID: 3832)
- AgentPackageUpgradeAgent.exe (PID: 3340)
- AgentPackageSystemTools.exe (PID: 3876)
- AgentPackageHeartbeat.exe (PID: 2692)
- AgentPackageAgentInformation.exe (PID: 2648)
- AgentPackageMarketplace.exe (PID: 2940)
- AgentPackageHeartbeat.exe (PID: 3116)
- AgentPackageHeartbeat.exe (PID: 276)
- AgentPackageHeartbeat.exe (PID: 2688)
- AgentPackageInternalPoller.exe (PID: 3008)
- AgentPackageHeartbeat.exe (PID: 3088)
- AgentPackageHeartbeat.exe (PID: 1348)
- AgentPackageHeartbeat.exe (PID: 3684)
- SRManager.exe (PID: 3568)
- AgentPackageHeartbeat.exe (PID: 2676)
Creates files in the program directory
- AteraAgent.exe (PID: 3660)
- AteraAgent.exe (PID: 3304)
- AgentPackageAgentInformation.exe (PID: 3908)
- AgentPackageAgentInformation.exe (PID: 1640)
- AteraAgent.exe (PID: 2428)
- AgentPackageSTRemote.exe (PID: 944)
- AgentPackageAgentInformation.exe (PID: 2508)
- AgentPackageTicketing.exe (PID: 544)
- AgentPackageProgramManagement.exe (PID: 2028)
- AgentPackageInternalPoller.exe (PID: 3704)
- AgentPackageOsUpdates.exe (PID: 300)
- AgentPackageRuntimeInstaller.exe (PID: 2840)
- SetupUtil.exe (PID: 1592)
- SRSelfSignCertUtil.exe (PID: 2776)
- Splashtop_Software_Updater.exe (PID: 3668)
- SRService.exe (PID: 3540)
- SRManager.exe (PID: 3568)
- SRServer.exe (PID: 1152)
- SRAgent.exe (PID: 1864)
- SRVirtualDisplay.exe (PID: 2456)
Reads Microsoft Office registry keys
- AgentPackageAgentInformation.exe (PID: 3908)
- AgentPackageAgentInformation.exe (PID: 1640)
- AgentPackageAgentInformation.exe (PID: 2508)
- AgentPackageAgentInformation.exe (PID: 2648)
Dropped object may contain TOR URL's
- msiexec.exe (PID: 1928)
Reads product name
- SRManager.exe (PID: 3568)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
227
Monitored processes
125
Malicious processes
24
Suspicious processes
8
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 124 | "C:\Windows\system32\cmd.exe" /C "C:\Windows\system32\wevtutil.exe" im "C:\ProgramData\Splashtop\Common\Event\stevt_srs_provider.man" | C:\Windows\System32\cmd.exe | — | SetupUtil.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Command Processor Exit code: 1 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 240 | reg.exe import "C:\Windows\TEMP\{9F154C7C-476C-4B8B-8D80-6DB365F3BBF7}\CredProvider_Inst.reg" /reg:32 | C:\Windows\System32\reg.exe | — | msiexec.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Registry Console Tool Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 276 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=unzip.mojom.Unzipper --lang=en-US --service-sandbox-type=service --disable-quic --mojo-platform-channel-handle=2896 --field-trial-handle=1184,i,1183984934595418030,4306363098254453211,131072 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 109.0.5414.120 Modules
| |||||||||||||||
| 276 | "C:\Program Files\ATERA Networks\AteraAgent\Packages\AgentPackageHeartbeat\AgentPackageHeartbeat.exe" b2942a04-b7d2-4312-b511-e43610f4f738 "c6b1190c-95c8-42c5-88ff-b88fcc274881" agent-api.atera.com/Production 443 or8ixLi90Mf "heartbeat" | C:\Program Files\ATERA Networks\AteraAgent\Packages\AgentPackageHeartbeat\AgentPackageHeartbeat.exe | AteraAgent.exe | ||||||||||||
User: SYSTEM Company: Atera Networks Integrity Level: SYSTEM Description: AgentPackageHeartbeat Exit code: 0 Version: 17.11.0.0 Modules
| |||||||||||||||
| 280 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --disk-cache-dir=null --disk-cache-size=1 --media-cache-size=1 --disable-gpu-shader-disk-cache --disable-background-networking "https://HelpdeskSupport403564130.servicedesk.atera.com/GetAgent/Msi/?customerId=1&integratorLogin=clientenovo0011%40outlook.com&accountId=001Q3000002mS8vIAE" | C:\Program Files\Google\Chrome\Application\chrome.exe | explorer.exe | ||||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 109.0.5414.120 Modules
| |||||||||||||||
| 300 | "C:\Program Files\ATERA Networks\AteraAgent\Packages\AgentPackageOsUpdates\AgentPackageOsUpdates.exe" b2942a04-b7d2-4312-b511-e43610f4f738 "c3dea8d9-7143-41cc-b913-9f37d73a0166" agent-api.atera.com/Production 443 or8ixLi90Mf "getlistofallupdates" | C:\Program Files\ATERA Networks\AteraAgent\Packages\AgentPackageOsUpdates\AgentPackageOsUpdates.exe | — | AteraAgent.exe | |||||||||||
User: SYSTEM Integrity Level: SYSTEM Description: AgentPackageOsUpdates Exit code: 0 Version: 18.1.0.0 Modules
| |||||||||||||||
| 448 | "C:\Windows\TEMP\~nsuA.tmp\Au_.exe" /S _?=C:\Program Files\Splashtop\Splashtop Software Updater\ | C:\Windows\Temp\~nsuA.tmp\Au_.exe | — | uninst.exe | |||||||||||
User: SYSTEM Company: Splashtop Inc. Integrity Level: SYSTEM Description: Splashtop software updater enables updates and enhancements to the SmartView browser extension. Exit code: 0 Version: 1.5.6.23 Modules
| |||||||||||||||
| 544 | "C:\Program Files\ATERA Networks\AteraAgent\Packages\AgentPackageTicketing\AgentPackageTicketing.exe" b2942a04-b7d2-4312-b511-e43610f4f738 "b769898a-a76c-4215-9247-6b853fcf3228" agent-api.atera.com/Production 443 or8ixLi90Mf "maintain" | C:\Program Files\ATERA Networks\AteraAgent\Packages\AgentPackageTicketing\AgentPackageTicketing.exe | AteraAgent.exe | ||||||||||||
User: SYSTEM Integrity Level: SYSTEM Description: AgentPackageTicketing Exit code: 0 Version: 24.11.0.0 Modules
| |||||||||||||||
| 600 | C:\Windows\System32\cmd.exe /C "taskkill.exe /F /IM SRFeatMini.exe /T" | C:\Windows\System32\cmd.exe | — | msiexec.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Command Processor Exit code: 128 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 668 | "C:\Windows\System32\cmd.exe" /c cscript "C:\Program Files\Microsoft Office\Office14\ospp.vbs" /dstatus | C:\Windows\System32\cmd.exe | — | AgentPackageAgentInformation.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
Total events
114 335
Read events
113 776
Write events
528
Delete events
31
Modification events
| (PID) Process: | (280) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BLBeacon |
| Operation: | write | Name: | failed_count |
Value: 0 | |||
| (PID) Process: | (280) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 1 | |||
| (PID) Process: | (280) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\ThirdParty |
| Operation: | write | Name: | StatusCodes |
Value: 01000000 | |||
| (PID) Process: | (280) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 2 | |||
| (PID) Process: | (280) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Update\ClientState\{8A69D345-D564-463c-AFF1-A69D9E530F96} |
| Operation: | write | Name: | dr |
Value: 1 | |||
| (PID) Process: | (280) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\StabilityMetrics |
| Operation: | write | Name: | user_experience_metrics.stability.exited_cleanly |
Value: 1 | |||
| (PID) Process: | (280) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome |
| Operation: | write | Name: | UsageStatsInSample |
Value: 0 | |||
| (PID) Process: | (280) chrome.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Google\Update\ClientStateMedium\{8A69D345-D564-463C-AFF1-A69D9E530F96} |
| Operation: | write | Name: | usagestats |
Value: 0 | |||
| (PID) Process: | (280) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Update\ClientState\{8A69D345-D564-463c-AFF1-A69D9E530F96} |
| Operation: | write | Name: | metricsid_installdate |
Value: 0 | |||
| (PID) Process: | (280) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Update\ClientState\{8A69D345-D564-463c-AFF1-A69D9E530F96} |
| Operation: | write | Name: | metricsid_enableddate |
Value: 0 | |||
Executable files
616
Suspicious files
229
Text files
206
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 280 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\commerce_subscription_db\LOG.old~RF20fa52.TMP | — | |
MD5:— | SHA256:— | |||
| 280 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\commerce_subscription_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 280 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Variations | binary | |
MD5:961E3604F228B0D10541EBF921500C86 | SHA256:F7B24F2EB3D5EB0550527490395D2F61C3D2FE74BB9CB345197DAD81B58B5FED | |||
| 280 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Last Version | text | |
MD5:9F941EA08DBDCA2EB3CFA1DBBBA6F5DC | SHA256:127F71DF0D2AD895D4F293E62284D85971AE047CA15F90B87BF6335898B0B655 | |||
| 280 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Platform Notifications\LOG.old | text | |
MD5:05387A3C4FCF1F3B992FF9FBF045AA1A | SHA256:B01E9451B8F6ABF03C9CD2E158C02D0A6BFDF771944F5D0B96DAD2DA6A7E3C8F | |||
| 280 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Crashpad\settings.dat | binary | |
MD5:9C016064A1F864C8140915D77CF3389A | SHA256:0E7265D4A8C16223538EDD8CD620B8820611C74538E420A88E333BE7F62AC787 | |||
| 280 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\LOG.old~RF20ff92.TMP | — | |
MD5:— | SHA256:— | |||
| 280 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\LOG.old | — | |
MD5:— | SHA256:— | |||
| 280 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Sync Data\LevelDB\LOG.old~RF20fa62.TMP | text | |
MD5:E91E138A25FD7E5BCA5E60111F39C91A | SHA256:B1F7E3537A31A4B847F862858E5D2581993CC9372F19ABF19EA2A9185FE42A4F | |||
| 280 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\shared_proto_db\metadata\LOG.old~RF20fb0d.TMP | text | |
MD5:8268A4D53A6A9432A8266584CBD7D624 | SHA256:F785C42945CFE320C52C763837CD41541A8CAAB3E5FD567999EED5343CF0FD7A | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
33
TCP/UDP connections
81
DNS requests
52
Threats
50
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3660 | AteraAgent.exe | GET | 200 | 93.184.221.240:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?b454a8c8ee2f9d16 | unknown | compressed | 4.66 Kb | unknown |
3660 | AteraAgent.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBT3xL4LQLXDRDM9P665TW442vrsUQQUReuir%2FSSy4IxLVGLp6chnfNtyA8CEA6bGI750C3n79tQ4ghAGFo%3D | unknown | binary | 471 b | unknown |
3660 | AteraAgent.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSRXerF0eFeSWRripTgTkcJWMm7iQQUaDfg67Y7%2BF8Rhvv%2BYXsIiGX0TkICEAZ%2FYEeVZiSnFZlhdD2BlJM%3D | unknown | binary | 727 b | unknown |
3660 | AteraAgent.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTfIs%2BLjDtGwQ09XEB1Yeq%2BtX%2BBgQQU7NfjgtJxXWRM3y5nP%2Be6mK4cD08CEAitQLJg0pxMn17Nqb2Trtk%3D | unknown | binary | 727 b | unknown |
868 | svchost.exe | HEAD | 200 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/adhioj45hzjkfunn7ccrbqyyhu3q_20230916.567854667.14/obedbbhbpmojnkanicioggnmelmoomoc_20230916.567854667.14_all_ENUS500000_lr7434qyx46lykosg2elaepqdi.crx3 | unknown | — | — | unknown |
3304 | AteraAgent.exe | GET | 200 | 192.229.221.95:80 | http://cacerts.digicert.com/DigiCertTrustedG4CodeSigningRSA4096SHA3842021CA1.crt | unknown | binary | 1.68 Kb | unknown |
868 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/adhioj45hzjkfunn7ccrbqyyhu3q_20230916.567854667.14/obedbbhbpmojnkanicioggnmelmoomoc_20230916.567854667.14_all_ENUS500000_lr7434qyx46lykosg2elaepqdi.crx3 | unknown | binary | 6.20 Kb | unknown |
868 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/adhioj45hzjkfunn7ccrbqyyhu3q_20230916.567854667.14/obedbbhbpmojnkanicioggnmelmoomoc_20230916.567854667.14_all_ENUS500000_lr7434qyx46lykosg2elaepqdi.crx3 | unknown | binary | 8.89 Kb | unknown |
3568 | SRManager.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSRXerF0eFeSWRripTgTkcJWMm7iQQUaDfg67Y7%2BF8Rhvv%2BYXsIiGX0TkICEAx%2B7MjF4dH7UpJWotMQ8HE%3D | unknown | binary | 727 b | unknown |
868 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/adhioj45hzjkfunn7ccrbqyyhu3q_20230916.567854667.14/obedbbhbpmojnkanicioggnmelmoomoc_20230916.567854667.14_all_ENUS500000_lr7434qyx46lykosg2elaepqdi.crx3 | unknown | binary | 8.16 Kb | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
280 | chrome.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
2300 | chrome.exe | 74.125.133.84:443 | accounts.google.com | GOOGLE | US | unknown |
2300 | chrome.exe | 20.101.44.219:443 | helpdesksupport403564130.servicedesk.atera.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | unknown |
2588 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
280 | chrome.exe | 224.0.0.251:5353 | — | — | — | unknown |
2300 | chrome.exe | 142.250.184.238:443 | sb-ssl.google.com | GOOGLE | US | whitelisted |
2300 | chrome.exe | 216.58.212.132:443 | www.google.com | GOOGLE | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
accounts.google.com |
| shared |
helpdesksupport403564130.servicedesk.atera.com |
| unknown |
sb-ssl.google.com |
| whitelisted |
www.google.com |
| whitelisted |
optimizationguide-pa.googleapis.com |
| whitelisted |
www.googleapis.com |
| whitelisted |
ctldl.windowsupdate.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
agent-api.atera.com |
| unknown |
ps.pndsn.com |
| unknown |
Threats
PID | Process | Class | Message |
|---|---|---|---|
1080 | svchost.exe | Misc activity | ET INFO Splashtop Domain in DNS Lookup (splashtop .com) |
944 | AgentPackageSTRemote.exe | Misc activity | ET INFO Splashtop Domain (splashtop .com) in TLS SNI |
1080 | svchost.exe | Misc activity | ET INFO Splashtop Domain in DNS Lookup (splashtop .com) |
944 | AgentPackageSTRemote.exe | Misc activity | ET INFO Splashtop Domain (splashtop .com) in TLS SNI |
1080 | svchost.exe | Misc activity | ET INFO Splashtop Domain in DNS Lookup (splashtop .com) |
3568 | SRManager.exe | Misc activity | ET INFO Splashtop Domain (splashtop .com) in TLS SNI |
3568 | SRManager.exe | Misc activity | ET INFO Splashtop Domain (splashtop .com) in TLS SNI |
1080 | svchost.exe | Misc activity | ET INFO Splashtop Domain in DNS Lookup (splashtop .com) |
1080 | svchost.exe | Misc activity | ET INFO Splashtop Domain in DNS Lookup (splashtop .com) |
3568 | SRManager.exe | Misc activity | ET INFO Splashtop Domain (splashtop .com) in TLS SNI |
30 ETPRO signatures available at the full report
Process | Message |
|---|---|
SplashtopStreamer.exe | [1992]2023-12-04 21:14:49 [CUnPack::FindHeader] Sign Size:10248 (Last=0) |
SplashtopStreamer.exe | [1992]2023-12-04 21:14:49 [CUnPack::FindHeader] Header offset:433664 (Last=183) |
SplashtopStreamer.exe | [1992]2023-12-04 21:14:49 [CUnPack::FindHeader] Name:C:\Windows\TEMP\SplashtopStreamer.exe (Last=0) |
SplashtopStreamer.exe | [1992]2023-12-04 21:14:49 [CUnPack::UnPackFiles] (1/5)UnPack file name:C:\Windows\TEMP\unpack\setup.msi (52934656) (Last=0) |
SplashtopStreamer.exe | [1992]2023-12-04 21:14:49 [CUtility::OSInfo] OS 6.1(7601) Service Pack 1 x64:0 (Last=0) |
SplashtopStreamer.exe | [1992]2023-12-04 21:14:49 [CUnPack::UnPackFiles] FreeSpace:233006727168 FileSize:52934656 (Last=0) |
SplashtopStreamer.exe | [1992]2023-12-04 21:14:49 [CUnPack::UnPackFiles] (4/5)UnPack file name:C:\Windows\TEMP\unpack\PreVerCheck.exe (2739720) (Last=122) |
SplashtopStreamer.exe | [1992]2023-12-04 21:14:49 [CUnPack::UnPackFiles] UnPack count:2 len:15 File:(null) (Last=0) |
SplashtopStreamer.exe | [1992]2023-12-04 21:14:49 [CUnPack::UnPackFiles] UnPack count:3 len:1528 File:(null) (Last=0) |
SplashtopStreamer.exe | [1992]2023-12-04 21:14:49 [CUnPack::UnPackFiles] FreeSpace:232953782272 FileSize:2739720 (Last=183) |