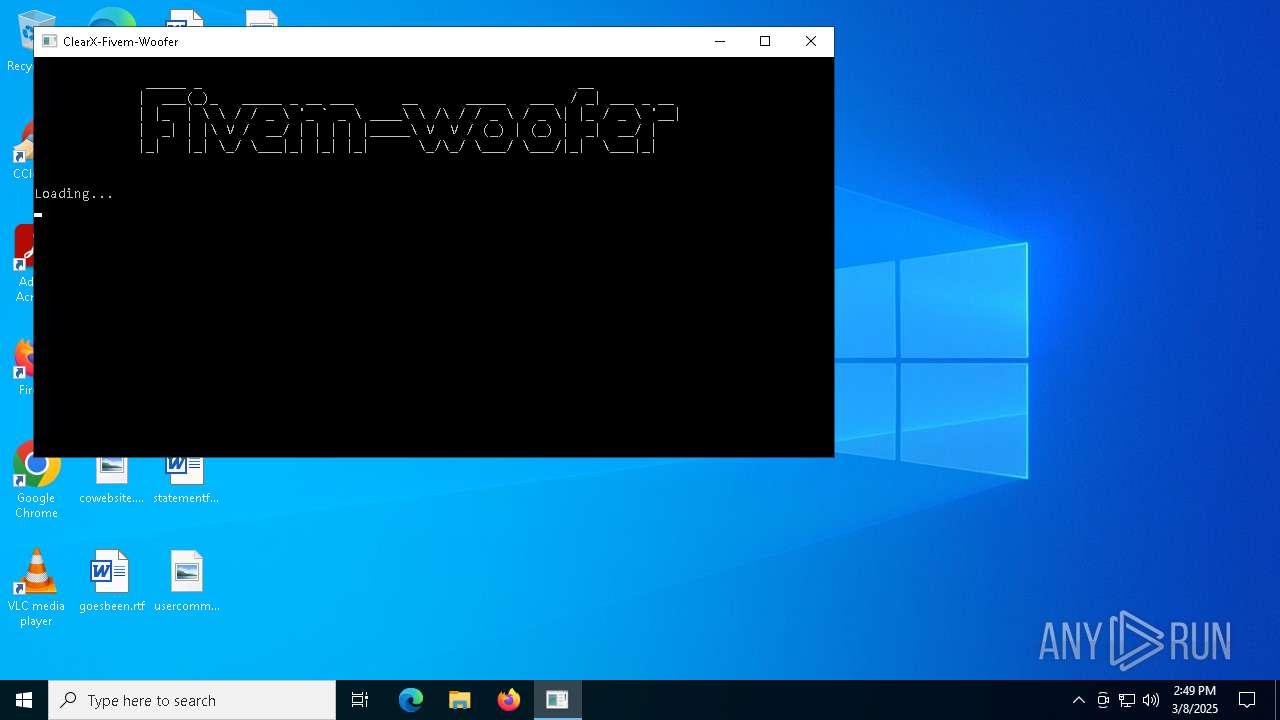
| File name: | Fivem-Woofer.exe |
| Full analysis: | https://app.any.run/tasks/7277dccd-0a7a-4d56-9b51-1340f120a963 |
| Verdict: | Malicious activity |
| Threats: | DCrat, also known as Dark Crystal RAT, is a remote access trojan (RAT), which was first introduced in 2018. It is a modular malware that can be customized to perform different tasks. For instance, it can steal passwords, crypto wallet information, hijack Telegram and Steam accounts, and more. Attackers may use a variety of methods to distribute DCrat, but phishing email campaigns are the most common. |
| Analysis date: | March 08, 2025, 14:48:51 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32+ executable (console) x86-64, for MS Windows, 6 sections |
| MD5: | 53FB0718A29D94340A747782F758CDB3 |
| SHA1: | 5C7B1B6C23EFBE21525053330F2E23D70EE5D119 |
| SHA256: | 8E14D235CAAAFBA051492C6B173364286A57F8D7C51C4B7201362FB7AF18F34E |
| SSDEEP: | 98304:adq6fDBNDMrrM7ZjcCfMNFxYVPVDG73vm7qoVHNorJ/egyxU3w5Yvaxo+YFiOlHq:n6HPnu |
MALICIOUS
DCRAT has been found (auto)
- Fivem-Woofer.exe (PID: 5008)
- ntoskrnl2.exe (PID: 5204)
Adds path to the Windows Defender exclusion list
- ntoskrnl2.exe (PID: 5204)
SUSPICIOUS
Starts CMD.EXE for commands execution
- Fivem-Woofer.exe (PID: 5008)
- ntoskrnl2.exe (PID: 5204)
Reads the date of Windows installation
- Fivem-Woofer.exe (PID: 5008)
- ntoskrnl2.exe (PID: 5204)
Reads security settings of Internet Explorer
- Fivem-Woofer.exe (PID: 5008)
- ntoskrnl2.exe (PID: 5204)
Executable content was dropped or overwritten
- Fivem-Woofer.exe (PID: 5008)
- ntoskrnl2.exe (PID: 5204)
- slui.exe (PID: 8116)
The process creates files with name similar to system file names
- ntoskrnl2.exe (PID: 5204)
Executed via WMI
- schtasks.exe (PID: 5408)
- schtasks.exe (PID: 2108)
- schtasks.exe (PID: 3240)
- schtasks.exe (PID: 4892)
- schtasks.exe (PID: 6388)
- schtasks.exe (PID: 7052)
- schtasks.exe (PID: 3100)
- schtasks.exe (PID: 4120)
- schtasks.exe (PID: 1056)
- schtasks.exe (PID: 4220)
- schtasks.exe (PID: 3304)
- schtasks.exe (PID: 4428)
- schtasks.exe (PID: 2852)
- schtasks.exe (PID: 1280)
- schtasks.exe (PID: 4408)
- schtasks.exe (PID: 6388)
- schtasks.exe (PID: 5416)
- schtasks.exe (PID: 5112)
Executing commands from a ".bat" file
- ntoskrnl2.exe (PID: 5204)
Starts application with an unusual extension
- cmd.exe (PID: 7392)
Runs PING.EXE to delay simulation
- cmd.exe (PID: 7392)
Script adds exclusion path to Windows Defender
- ntoskrnl2.exe (PID: 5204)
Starts POWERSHELL.EXE for commands execution
- ntoskrnl2.exe (PID: 5204)
INFO
Checks supported languages
- mode.com (PID: 1188)
- Fivem-Woofer.exe (PID: 5008)
- ntoskrnl2.exe (PID: 5204)
- chcp.com (PID: 7588)
- slui.exe (PID: 8116)
Gets the hash of the file via CERTUTIL.EXE
- certutil.exe (PID: 1324)
Reads the computer name
- Fivem-Woofer.exe (PID: 5008)
- ntoskrnl2.exe (PID: 5204)
- slui.exe (PID: 8116)
Process checks computer location settings
- Fivem-Woofer.exe (PID: 5008)
- ntoskrnl2.exe (PID: 5204)
Starts MODE.COM to configure console settings
- mode.com (PID: 1188)
Reads the machine GUID from the registry
- ntoskrnl2.exe (PID: 5204)
- slui.exe (PID: 8116)
Reads Environment values
- ntoskrnl2.exe (PID: 5204)
- slui.exe (PID: 8116)
Creates files in the program directory
- ntoskrnl2.exe (PID: 5204)
Create files in a temporary directory
- ntoskrnl2.exe (PID: 5204)
Changes the display of characters in the console
- cmd.exe (PID: 7392)
Checks if a key exists in the options dictionary (POWERSHELL)
- powershell.exe (PID: 4112)
- powershell.exe (PID: 5352)
- powershell.exe (PID: 6372)
- powershell.exe (PID: 6264)
- powershell.exe (PID: 4428)
- powershell.exe (PID: 2852)
Script raised an exception (POWERSHELL)
- powershell.exe (PID: 6372)
- powershell.exe (PID: 5352)
- powershell.exe (PID: 4428)
- powershell.exe (PID: 2852)
- powershell.exe (PID: 6264)
- powershell.exe (PID: 4112)
Disables trace logs
- slui.exe (PID: 8116)
Checks proxy server information
- slui.exe (PID: 8116)
- slui.exe (PID: 6576)
Reads the software policy settings
- slui.exe (PID: 6576)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win64 Executable (generic) (64.6) |
|---|---|---|
| .dll | | | Win32 Dynamic Link Library (generic) (15.4) |
| .exe | | | Win32 Executable (generic) (10.5) |
| .exe | | | Generic Win/DOS Executable (4.6) |
| .exe | | | DOS Executable Generic (4.6) |
EXIF
EXE
| MachineType: | AMD AMD64 |
|---|---|
| TimeStamp: | 2025:02:03 18:33:29+00:00 |
| ImageFileCharacteristics: | Executable, Large address aware |
| PEType: | PE32+ |
| LinkerVersion: | 14.42 |
| CodeSize: | 503296 |
| InitializedDataSize: | 2063360 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x78548 |
| OSVersion: | 6 |
| ImageVersion: | - |
| SubsystemVersion: | 6 |
| Subsystem: | Windows command line |
Total processes
171
Monitored processes
47
Malicious processes
3
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1056 | schtasks.exe /create /tn "OfficeClickToRunO" /sc MINUTE /mo 7 /tr "'C:\Program Files (x86)\Opera\OfficeClickToRun.exe'" /f | C:\Windows\System32\schtasks.exe | — | WmiPrvSE.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Task Scheduler Configuration Tool Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1188 | mode con cols=100 lines=25 | C:\Windows\System32\mode.com | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: DOS Device MODE Utility Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1188 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1280 | C:\WINDOWS\system32\cmd.exe /c mode con cols=100 lines=25 | C:\Windows\System32\cmd.exe | — | Fivem-Woofer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1280 | schtasks.exe /create /tn "lsassl" /sc MINUTE /mo 6 /tr "'C:\found.000\dir0001.chk\lsass.exe'" /f | C:\Windows\System32\schtasks.exe | — | WmiPrvSE.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Task Scheduler Configuration Tool Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1324 | certutil -hashfile "C:\Users\admin\Desktop\Fivem-Woofer.exe" MD5 | C:\Windows\System32\certutil.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: CertUtil.exe Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1616 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2108 | schtasks.exe /create /tn "Idle" /sc ONLOGON /tr "'C:\Windows\Installer\{420AE50D-8B07-4845-8592-3BECCD71DE80}\Idle.exe'" /rl HIGHEST /f | C:\Windows\System32\schtasks.exe | — | WmiPrvSE.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Task Scheduler Configuration Tool Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2196 | C:\WINDOWS\system32\svchost.exe -k NetworkService -p -s Dnscache | C:\Windows\System32\svchost.exe | services.exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2236 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
38 640
Read events
38 620
Write events
20
Delete events
0
Modification events
| (PID) Process: | (1324) certutil.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Cryptography\OID\EncodingType 0\CryptDllFindOIDInfo\1.3.6.1.4.1.311.60.3.1!7 |
| Operation: | write | Name: | Name |
Value: szOID_ROOT_PROGRAM_AUTO_UPDATE_CA_REVOCATION | |||
| (PID) Process: | (1324) certutil.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Cryptography\OID\EncodingType 0\CryptDllFindOIDInfo\1.3.6.1.4.1.311.60.3.2!7 |
| Operation: | write | Name: | Name |
Value: szOID_ROOT_PROGRAM_AUTO_UPDATE_END_REVOCATION | |||
| (PID) Process: | (1324) certutil.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Cryptography\OID\EncodingType 0\CryptDllFindOIDInfo\1.3.6.1.4.1.311.60.3.3!7 |
| Operation: | write | Name: | Name |
Value: szOID_ROOT_PROGRAM_NO_OCSP_FAILOVER_TO_CRL | |||
| (PID) Process: | (5204) ntoskrnl2.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\7455cbbde3db12daf8b799e881ef1ad4f24d6f79 |
| Operation: | write | Name: | da52f2ad8763e29d9bb815ac843e67d0b85e338e |
Value: H4sIAAAAAAAEAI2QMU/DMBSE/0rUiUokctOEGjaaBMGAWpVKDDwGE7+0ll9s5OeIIsR/p+1QdanEdMt9p7t7G1V3AK/Gaf/FAE+OoyLCAPBT5OK+KUWdyrmYpYUsylSWt3k6nTdVVc8mdSPF7x7RhBnucHR9jFoGvwmqTx4MISdXO3kzBlh8YlAAH6q1m+AHp9eK7aPn+E9w0XWmxYpMa9d+NbhL2GlJ8jxQND1qo5Ilqdj50AMwDeYM7Q5NMiEEgDZhr5Os3VoAYsV85ju98/LNEftpDuCiZxsc5Ufb+x8IjV1qRgEAAA== | |||
| (PID) Process: | (5204) ntoskrnl2.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\MuiCache |
| Operation: | write | Name: | C:\WINDOWS\System32\cmd.exe.FriendlyAppName |
Value: Windows Command Processor | |||
| (PID) Process: | (5204) ntoskrnl2.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\MuiCache |
| Operation: | write | Name: | C:\WINDOWS\System32\cmd.exe.ApplicationCompany |
Value: Microsoft Corporation | |||
| (PID) Process: | (8116) slui.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\slui_RASAPI32 |
| Operation: | write | Name: | EnableFileTracing |
Value: 0 | |||
| (PID) Process: | (8116) slui.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\slui_RASAPI32 |
| Operation: | write | Name: | EnableAutoFileTracing |
Value: 0 | |||
| (PID) Process: | (8116) slui.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\slui_RASAPI32 |
| Operation: | write | Name: | EnableConsoleTracing |
Value: 0 | |||
| (PID) Process: | (8116) slui.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\slui_RASAPI32 |
| Operation: | write | Name: | FileTracingMask |
Value: | |||
Executable files
12
Suspicious files
1
Text files
20
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 5008 | Fivem-Woofer.exe | C:\Windows\System32\ntoskrnl2.exe | executable | |
MD5:C8848D70C25CF0A1E0A4122CAB55E5F8 | SHA256:6EBED9F6DE82360A3724C5148EAACED3273CE3E48826492D87DA9D7E978EB6FC | |||
| 5204 | ntoskrnl2.exe | C:\Users\admin\Desktop\wUKOhLVl.log | executable | |
MD5:0B2AFABFAF0DD55AD21AC76FBF03B8A0 | SHA256:DD4560987BD87EF3E6E8FAE220BA22AA08812E9743352523C846553BD99E4254 | |||
| 5204 | ntoskrnl2.exe | C:\Program Files\Windows Multimedia Platform\a29f4157103644 | text | |
MD5:00210ED5E67EDA283E84C63C4D71A785 | SHA256:86EC437B81D30807AB6A64AF7FC26780370C1A97EB136C6E942FD8664DD262EE | |||
| 5204 | ntoskrnl2.exe | C:\Windows\Installer\{420AE50D-8B07-4845-8592-3BECCD71DE80}\Idle.exe | executable | |
MD5:C8848D70C25CF0A1E0A4122CAB55E5F8 | SHA256:6EBED9F6DE82360A3724C5148EAACED3273CE3E48826492D87DA9D7E978EB6FC | |||
| 5204 | ntoskrnl2.exe | C:\Users\admin\Desktop\oZvGiwLC.log | executable | |
MD5:D8BF2A0481C0A17A634D066A711C12E9 | SHA256:2B93377EA087225820A9F8E4F331005A0C600D557242366F06E0C1EAE003D669 | |||
| 5204 | ntoskrnl2.exe | C:\Program Files (x86)\Opera\OfficeClickToRun.exe | executable | |
MD5:C8848D70C25CF0A1E0A4122CAB55E5F8 | SHA256:6EBED9F6DE82360A3724C5148EAACED3273CE3E48826492D87DA9D7E978EB6FC | |||
| 5204 | ntoskrnl2.exe | C:\Program Files\Windows Multimedia Platform\slui.exe | executable | |
MD5:C8848D70C25CF0A1E0A4122CAB55E5F8 | SHA256:6EBED9F6DE82360A3724C5148EAACED3273CE3E48826492D87DA9D7E978EB6FC | |||
| 5204 | ntoskrnl2.exe | C:\Users\admin\Desktop\OgmUAhqA.log | executable | |
MD5:2E116FC64103D0F0CF47890FD571561E | SHA256:25EEEA99DCA05BF7651264FA0C07E0E91D89E0DA401C387284E9BE9AFDF79625 | |||
| 5204 | ntoskrnl2.exe | C:\Program Files (x86)\Opera\e6c9b481da804f | text | |
MD5:AE4328F7AAEEA0D22D2528F5E32D32EE | SHA256:9454FB7409C64D279DF8E571835360845AD06F8275BED1C21ED3411182823AF0 | |||
| 5204 | ntoskrnl2.exe | C:\found.000\dir0001.chk\6203df4a6bafc7 | text | |
MD5:730926E7BCC869DC90156EA6D6FB9B0A | SHA256:F5E03F472B5B2AF08F59414841CFB4BD6F3F47D42DEFCB9850C6CBC7C4E0D704 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
2
TCP/UDP connections
19
DNS requests
5
Threats
3
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | POST | 500 | 40.91.76.224:443 | https://activation-v2.sls.microsoft.com/SLActivateProduct/SLActivateProduct.asmx?configextension=Retail | unknown | xml | 512 b | whitelisted |
— | — | POST | 500 | 40.91.76.224:443 | https://activation-v2.sls.microsoft.com/SLActivateProduct/SLActivateProduct.asmx?configextension=Retail | unknown | xml | 512 b | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 192.168.100.255:138 | — | — | — | whitelisted |
3304 | RUXIMICS.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5008 | Fivem-Woofer.exe | 104.26.0.5:443 | keyauth.win | CLOUDFLARENET | US | malicious |
5280 | slui.exe | 40.91.76.224:443 | activation-v2.sls.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
6576 | slui.exe | 40.91.76.224:443 | activation-v2.sls.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
keyauth.win |
| malicious |
128538cm.n9shteam3.top |
| malicious |
activation-v2.sls.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
5008 | Fivem-Woofer.exe | Potentially Bad Traffic | ET INFO KeyAuth Open-source Authentication System Domain (keyauth .win) in TLS SNI |
2196 | svchost.exe | Potentially Bad Traffic | ET INFO KeyAuth Open-source Authentication System Domain in DNS Lookup (keyauth .win) |
2196 | svchost.exe | Potentially Bad Traffic | ET DNS Query to a *.top domain - Likely Hostile |